61 Internet Privacy Essay Topic Ideas & Examples
🏆 best internet privacy topic ideas & essay examples, 💡 good research topics about internet privacy, 📌 interesting topics to write about internet privacy.
- Privacy and Safety on the Internet The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information. The final security measure to ensure safety […]
- The Internet of Things: Revolutionizing Connectivity, Privacy, and Security The information that the devices may collect is first stored in the internal memory of a device and then sent into the gateway of IoT.
- The Decision of PIPA and SOPA and Internet Privacy Timm Trevor uses a lot of arguments against PIPA and SOPA and aims at the reader’s persuasion of the importance of this issue and he wants to impel the public to stop these bills.
- Ethical Issues of Internet Privacy Some of the methods include the use of interview schedules, where respondents are asked questions and the respondents respond directly while the researcher records the answers.
- Privacy and Fair Use Issues in Social Networking Sites Conceptually, section 2i of the “Terms of Use” grants Classmates.com the sweeping right to use any and all personal information in advertising on third-party sites: “Classmates may create applications or other tools for use on […]
- Personal Privacy of Employees at Workplaces: Internet Usage It is thus highly important that the employees of an organization understand the importance of the internet as a resource and efficiently utilize it for the betterment of the organization.
- Facebook as a Social Network and Its Privacy Policy The case study explains that the privacy policy and privacy settings on Facebook are such that they considerably violate the privacy of the social network’s users by selling their data to third parties for a […]
- Internet Issues: Teens, Social Media and Privacy I argue that it is our understanding of privacy that provides the solution and that the Internet is the biggest factor that influences it.
- Privacy Threats in Internet, Work and Drug Testing The analysis of the factors mentioned above and exploration of the way they influence one’s life is crucial to understanding the scope of activities violating one of the primary human rights the right to keep […]
- Internet Usage and Privacy in the Army Historically, the army had been banned from the use of the internet for communication or for socialization. From this time onwards, the army has been able to use the internet for communication and well as […]
- Web Privacy: What’s Happening Now? In addition, he has noted that the government and other stakeholders are not in a position to control or regulate the use of the internet in their area.
- PIPA and SOPA’ Decision on Internet Privacy The right to access information is fundamental in any open society, the and so is the protection of intellectual property. Gillmor’s sentiments are on point and I agree that the intention of the lawmakers was […]
- Social Network Services: Privacy Issues Drip’s first point is that the owners of the SNS can use targeted advertisements to gather information about users for greedy marketers, and the user is not protected against this.
- Effects of Social Networking on Privacy This has been attributed to the fact that on social networking sites, people do not need to meet physically to communicate.
- Government Internet Surveillance: Privacy Threat Perhaps the most troubling applications of the internet in current times are the mass surveillance efforts by the US government. The internet age has dramatically increased the ability of government to engage in surveillance.
- Computer Science: Threats to Internet Privacy Allegedly, the use of the Internet is considered to be a potential threat to the privacy of individuals and organizations. Internet privacy may be threatened by the ease of access to personal information as well […]
- The Privacy and Trust for Wireless Network Security Aim The aim of this project is to design and implement a completely secure wireless sensor network into each node of the wireless sensor network.
- Privacy on the Internet: A Critical Analysis The present paper looks into the issues of privacy on the Internet by analyzing literature on how to protect your computer and confidential information from such vulnerabilities.
- Web Privacy – Reliance on Internet Internet regulation imposes strict policies regarding the nature of the data collected, the specific purpose that does not serve to violate the interest of the users and using the data without the knowledge of the […]
- What Are the Causes of the Increased Lack of Internet Privacy? Although every individual has the right to accuse the government and internet service providing companies over their failure to protect their customers’ privacy, individuals should recognize, they have a crucial duty to play as far […]
- Anonymity and Internet Privacy: Reality or Myth
- Internet Privacy and the Threats of Internet Privacy
- Computer Ethical Controversies: Porn and the Right to Internet Privacy
- The Problem of Cookies and Internet Privacy
- Controversies About Cyberbullying and Internet Privacy
- The Relationships Between Cyberspace and Internet Privacy
- Correlation Between Data Protection and Internet Privacy
- Digital Freedom: The Question of Internet Privacy
- Reasons Why America Needs Internet Privacy Laws
- Google and Its Role in Internet Privacy
- Relations Between Internet Privacy and Business Ethics
- Overview of Internet Privacy and Email Issues
- Internet Privacy and Its Effects on the Internet
- The Link Between Internet Privacy and Personal Rights
- Internet Privacy and Its Importance
- Collisions of Internet Privacy and Personal Safety
- The Relationships Between Internet Privacy and Social Media Websites
- Internet Privacy and Security in the Digital Age
- The Problem of Internet Privacy Cookies and Privacy on the Internet
- Internet Privacy Concerns Versus Behavior: A Protection Motivation Approach
- Analysis of Moral Issues With Internet Privacy
- Internet Privacy, Cookies, and Data Mining Practices
- Perceived Internet Privacy Concerns on Social Network in Europe
- Internet Privacy: The Case of Edward Snowden
- Conflicts Between Personalized Ads and Internet Privacy
- Evaluating the Importance of Regulating Internet Privacy
- Internet Privacy: Government Should Not Regulate Encryption or Cryptography
- Linking Social Media Postings and the Internet Privacy
- Internet Privacy: How Long Until We Lose It All
- Stronger Internet Privacy Laws Are Unnecessary
- Internet Privacy: How Secure Are You When You’re Browsing the Internet
- The Digital Panopticon: Foucault and Internet Privacy
- Internet Privacy Policy and the Job That the Government Is Taking On
- Overview of the Issue Around Internet Privacy
- Internet Privacy: Analysis of Pros and Cons
- The Role and Importance of Internet Privacy Policy
- Internet Privacy Protection Laws: Have They Been Useful
- Why Internet Privacy Matters to Consumer
- Internet Privacy: Should More Be Done to Protect Privacy
- Internet Privacy vs. Job Seeking: Analysis of Contradictions
- Internet of Things Topics
- Online Shopping Questions
- Viruses Research Topics
- Cyber Security Topics
- Safety Essay Ideas
- Cyberspace Topics
- Google Paper Topics
- Social Networking Essay Ideas
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 28). 61 Internet Privacy Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/
"61 Internet Privacy Essay Topic Ideas & Examples." IvyPanda , 28 Feb. 2024, ivypanda.com/essays/topic/internet-privacy-essay-topics/.
IvyPanda . (2024) '61 Internet Privacy Essay Topic Ideas & Examples'. 28 February.
IvyPanda . 2024. "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.
1. IvyPanda . "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.
Bibliography
IvyPanda . "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.

Presentations made painless
- Get Premium

112 Internet Privacy Essay Topic Ideas & Examples
Inside This Article
In today's digital age, internet privacy has become a major concern for many individuals. With the increasing amount of personal information being shared online, it's important to understand the different aspects of internet privacy and how it can impact our daily lives. To help you navigate this complex topic, we've compiled a list of 112 internet privacy essay topic ideas and examples to inspire your writing.
- The importance of internet privacy in the modern world
- How social media platforms collect and use personal data
- The impact of data breaches on internet privacy
- The role of government regulations in protecting internet privacy
- The ethical implications of online tracking and data collection
- Privacy concerns surrounding smart devices and the Internet of Things
- The effects of targeted advertising on consumer privacy
- The relationship between online anonymity and internet privacy
- The risks of sharing personal information on social media
- The impact of online surveillance on freedom of expression
- The challenges of balancing security and privacy in the digital age
- The role of encryption in protecting online privacy
- The implications of facial recognition technology on privacy rights
- The effects of data mining on individual privacy
- The role of internet service providers in protecting user privacy
- The impact of online tracking on consumer behavior
- The risks of using public Wi-Fi networks for personal information
- The implications of cloud computing on data privacy
- The role of cookies in tracking user behavior online
- The challenges of enforcing internet privacy laws across borders
- The impact of online censorship on internet privacy
- The risks of identity theft in the digital age
- The role of social media influencers in shaping online privacy norms
- The implications of data profiling on individual privacy rights
- The challenges of protecting children's online privacy
- The risks of using voice-activated devices for personal information
- The impact of geolocation tracking on user privacy
- The role of artificial intelligence in monitoring online behavior
- The effects of data breaches on consumer trust in online services
- The implications of online dating apps on user privacy
- The challenges of securing personal information in the age of social media
- The risks of sharing personal photos and videos online
- The impact of online harassment on user privacy
- The role of cybersecurity in protecting internet privacy
- The effects of data retention policies on user privacy rights
- The implications of online payment systems on financial privacy
- The challenges of protecting medical records online
- The risks of using public computers for online activities
- The impact of social credit systems on individual privacy rights
- The role of data brokers in collecting and selling personal information
- The effects of online quizzes and surveys on user privacy
- The implications of biometric data collection on privacy rights
- The challenges of protecting personal information on social networking sites
- The risks of using public search engines for sensitive information
- The impact of online gaming on user privacy
- The role of online reviews in shaping consumer privacy norms
- The effects of data leaks on user privacy
- The implications of online job searches on personal information
- The challenges of protecting intellectual property online
- The risks of using public forums for personal discussions
- The impact of online forums on user privacy
- The role of internet cookies in tracking user behavior
- The effects of data breaches on user trust in online services
- The implications of online shopping on consumer privacy
- The challenges of protecting personal information on social media
- The risks of using public Wi-Fi networks for personal data
- The impact of online advertising on user privacy
- The role of online tracking in shaping user behavior
- The effects of data profiling on individual privacy rights
- The implications of online quizzes and surveys on user privacy
From social media platforms to online shopping, internet privacy touches every aspect of our lives. By exploring these essay topics and examples, you can gain a deeper understanding of the importance of protecting your personal information online. Remember, your privacy is valuable ''' so take the necessary steps to safeguard it in the digital age.
Want to create a presentation now?
Instantly Create A Deck
Let PitchGrade do this for me
Hassle Free
We will create your text and designs for you. Sit back and relax while we do the work.
Explore More Content
- Privacy Policy
- Terms of Service
© 2023 Pitchgrade
Privacy in the digital age: comparing and contrasting individual versus social approaches towards privacy
- Original Paper
- Open access
- Published: 17 July 2019
- Volume 21 , pages 307–317, ( 2019 )
Cite this article
You have full access to this open access article

- Marcel Becker ORCID: orcid.org/0000-0003-2848-5305 1
19 Citations
19 Altmetric
Explore all metrics
This paper takes as a starting point a recent development in privacy-debates: the emphasis on social and institutional environments in the definition and the defence of privacy. Recognizing the merits of this approach I supplement it in two respects. First, an analysis of the relation between privacy and autonomy teaches that in the digital age more than ever individual autonomy is threatened. The striking contrast between on the one hand offline vocabulary, where autonomy and individual decision making prevail, and on the other online practices is a challenge that cannot be met in a social approach. Secondly, I elucidate the background of the social approach. Its importance is not exclusively related to the digital age. In public life we regularly face privacy-moments, when in a small distinguished social domain few people are commonly involved in common experiences. In the digital age the contextual integrity model of Helen Nissenbaum has become very influential. However this model has some problems. Nissenbaum refers to a variety of sources and uses several terms to explain the normativity in her model. The notion ‘context’ is not specific and faces the reproach of conservatism. We elaborate on the most promising suggestion: an elaboration on the notion ‘goods’ as it can be found in the works of Michael Walzer and Alisdair Macintyre. Developing criteria for defining a normative framework requires making explicit the substantive goods that are at stake in a context, and take them as the starting point for decisions about the flow of information. Doing so delivers stronger and more specific orientations that are indispensible in discussions about digital privacy.
Similar content being viewed by others

Digital technologies: tensions in privacy and data

Societal and ethical issues of digitization
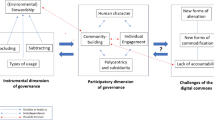
The Ethics of Commons Organizing: A Critical Reading
Avoid common mistakes on your manuscript.
Introduction
Rethinking the concept of privacy in the digital age inevitably entangles the descriptive and the normative dimensions of this concept. Theoretically these two dimensions of privacy can be distinguished. One dimension can describe the degree of privacy people enjoy, without taking a normative stance about the desirable degree of privacy. In normative discussions, the focus is on the reasons why privacy is important for leading a fulfilling life. This distinction should not distract us from the fact that privacy is not a completely neutral concept; instead, it has a positive connotation. For example, an invasion of privacy is a violation of or intrusion into something valuable that should be protected. Discussion of the concept, however, brings into question why privacy should be cherished and protected. In the digital age, the normative dimension is the object of intense discussion. Existing dangers to privacy—because of big data applications, cloud computing, and profiling—are widely recognized, but feelings of resignation and why should we bother lie dormant. Defenders of privacy are regularly faced with scepticism, which is fueled by Schmidt’s ‘Innocent people have nothing to hide’ (Esguerra 2009 ) and Zuckerberg’s ‘Having two identities for yourself is a lack of integrity’ (Boyd 2014 ).
Traditionally in defences of privacy the focus has been on the individual (Rule 2015 ). Privacy was defined in terms of an individual’s space , which was seen as necessary for meeting the individual’s vital interests. In the last decade, however, we have seen a shift in the emphasis. A view of privacy as the norm that regulates and structures social life (the social dimension of privacy) has gained importance in both law and philosophical literature. For instance, the European Court of Human Rights previously stressed that data protection was an individual’s right not to be interfered with. However, more and more the Court is focusing on individuals’ privacy as protection of their relationships with other human beings (van der Sloot 2014 ). In philosophical literature on privacy, many scholars have explicitly distanced themselves from the individual approach and instead study the social dimensions of privacy (Roessler and Mokrosinska 2015 ). Helen Nissenbaum is by far the most important spokesperson for the social approach. She has introduced the notion of contextual integrity as an alternative to what she describes as too much focus on individuals’ rights based notions of privacy (Nissenbaum 2009 ). Nissenbaum criticizes the so-called interest-based approach, which defines conflicts in terms of (violated) interests of the parties involved. For instance, ‘Uncontroversial acceptance of healthcare monitoring systems can be explained by pointing to the roughly even service to the interest of patients, hospitals, healthcare professionals and so on’. The problem with this approach, according to Nissenbaum, is that it sooner or later leads to ‘hard fought interest brawls’, which more often than not are settled to the advantage of the more powerful parties (Nissenbaum 2009 , p. 8). It is necessary to create a justificatory platform to reason in moral terms. As a rights-based approach is not satisfactory, she proposes a normative approach that does more justice to the social dimension.
The distinction between a focus on the individual and privacy as social value is not only of academic importance. For policies on privacy, this makes quite a difference. On the one hand, the emphasis can be on an individual’s right to decide about personal interests and transparency for empowering the individual , as for instance the European Data Protection Supervisor asserts (EDPS Opinion 2015 ). On the other hand, the emphasis can also be on institutional arrangements that protect social relationships. The fact that good privacy policies require measures should not be a reason to overlook their fundamental differences.
In this paper, we compare individual-based justifications of privacy with the social approach. We open with a discussion of the strengths of the individual-focused approach by relating privacy to a concept that has a strong normative sense and is most closely associated with individual-based privacy conceptions: autonomy. As we will see, a defence of privacy along these lines is both possible and necessary. In our discussion of the social approach, we focus on Helen Nissenbaum’s model. A critical discussion of the normative dimension will lead to suggestions for strengthening this model.
The individual approach
The importance of privacy: autonomy.
The history of justifications of privacy starts with Warren and Brandeis’s ( 1890 ) legal definition of privacy as the right to be left alone ( 1890 ). This classic definition is completely in line with the literal meaning of privacy. The word is a negativum (related to deprive ) of public . The right to privacy is essentially the right of individuals to have their own domain , separated from the public (Solove 2015 ). The basic way to describe this right to be left alone is in terms of access to a person. In classic articles, Gavison and Reiman characterize privacy as the degree of access that others have to you through information, attendance, and proximity (Gavison 1984 ; Reiman 1984 ).
Discussion about the importance of privacy for the individual intensified in the second half of the twentieth century, as patterns of living in societies became more and more individualistic. Privacy became linked to the valued notion of autonomy and the underlying idea of individual freedom. In both literature on privacy and judicial statements, this connection between privacy and autonomy has been a topic of intense discussion. Sometimes the two concepts were even blended together, even though they should remain distinct. A sharp distinction between privacy and autonomy is necessary to get to grips with the normative dimension of privacy.
The concept autonomy is derived from the ancient Greek words autos (self) and nomos (law). Especially within the Kantian framework, the concept is explicated in terms of a rational individual who, reflecting independently, takes his own decisions. Being autonomous was thus understood mainly as having control over one’s own life. In many domains of professional ethics (healthcare, consumer protection, and scientific research), autonomy is a key concept in defining how human beings should be treated. The right of individuals to control their own life should always be respected. The patient, the consumer, and the research participant each must be able to make his or her own choices (Strandburg 2014 ). Physicians are supposed to fully inform patients; advertisers who are caught lying are censured; and informed consent is a standard requirement of research ethics. In each of these cases, persons should not be forced, tempted, or seduced into performing actions they do not want to do.
When privacy and autonomy are connected, privacy is described as a way of controlling one’s own personal environment. An invasion of privacy disturbs control over (or access to) one’s personal sphere. This notion of privacy is closely related to secrecy. A person who deliberately gains access to information that the other person wants to keep secret is violating the other person’s autonomy through information control. We see the emphasis on privacy as control over information in, for instance, Marmor’s description of privacy as ‘grounded in people’s interest in having a reasonable measure of control over the ways in which they can present themselves to others’ (Marmor 2015 ). Autonomy, however, does not entail an exhaustive description of privacy. It is possible that someone could have the ability to control, yet he or she lacks privacy. For instance, a woman who frequently absentmindedly forgets to close the curtains before she undresses enables her neighbour to watch her. If the neighbour does so, we can speak about a loss of the woman’s privacy. Nevertheless, the woman still has the ability to control. At any moment, she could choose to close the curtains. Thus, privacy requires more than just autonomy.
The distinction between privacy and autonomy becomes clearer in Judith Jarvis Thompson’s classic thought experiment (Taylor 2002 ). Imagine that my neighbour invented some elaborate X-ray device that enabled him to look through the walls. I would thereby lose control over who can look at me, but my privacy would not be violated until my neighbour actually started to look through the walls. It is the actual looking that violates privacy, not the acquisition of the power to look. If my neighbour starts observing through the walls but I’m not aware of it and believe that I am carrying out my duties in the privacy of my own home, my autonomy would not be directly undermined. Not only in thought experiments, but also in literature and everyday life, we witness the difference between autonomy and privacy. Taylor refers to Scrooge in Dickens’ A Christmas Carol who is present as a ghost at family parties. His covert observation of the intimate Christmas dinner party implies a breach of privacy, although he does not influence the behaviour of the other people. In everyday life, we do not experience an inadvertent breach of privacy (for instance, a passer by randomly picking up some information) as loss of autonomy.
These examples make it clear that there is a difference between autonomy, which is about control, and privacy, which is about knowledge and access to information. The most natural way to connect the two concepts is to consider privacy as a tool that fosters and encourages autonomy. Privacy thus understood contributes to demarcation of a personal sphere , which makes it easier for a person to make decisions independently of other people. But a loss of privacy does not automatically imply loss of autonomy. A violation of privacy will result in autonomy being undermined only when at least one additional condition is met: the observing (privacy-violating) person is in one way or another influencing the other person (Taylor 2002 ). Such a violation of privacy can take various forms. For instance, the person involved might feel pressure to alter her behaviour just because she knows she is being observed. Or a person who is not aware of being observed is being manipulated. This, in fact, occurs more than ever before in the digital age.
Loss of autonomy in the digital age
In the more than 100 years following Warren and Brandeis’ publication of their definition, privacy was mainly considered to be a spatial notion. For example, the right to be left alone was the right to have one’s own space in a territorial sense, e.g., at home behind closed curtains, where other people were not allowed. An important topic in discussions of privacy was the embarrassment experienced when someone else entered the private spatial domain. Consider, for example, public figures whose privacy is invaded by obtrusive photographers or people who feel invaded when someone unexpectedly enters their home (Roessler 2009 ; Gavison 1984 ).
The digital age is characterized by the omnipresence of hidden cameras and other surveillance devices. This kind of observation and the corresponding embarrassment that it can cause have changed our ideas about privacy. The main concern is not the intrusive eye of another person, but the constant observation, which can lead to the panopticon experience of the interiorized gaze of the other. It is self-evident that the additional conditions are now being met, viz., the person’s autonomy is threatened. In situations in which the observed person feels impeded to follow his impulses (Van Otterloo 2014 ), the loss of privacy leads to diminished autonomy.
The loss of autonomy resulting from persistent surveillance becomes even more striking when we take into consideration the unprecedented collection and storage of non-visual information. Collecting data on individuals, such as through the activity of profiling, offers commercial parties and other institutions endless possibilities for approaching people in ways that meet the institution’s own interests. Driven by invisible algorithms, these institutions temp, nudge, seduce, and convince individuals to participate for reasons that are advantageous to the institution. The widespread application of algorithms in decision-making processes intensifies the problem of loss of autonomy in at least two respects. First, when algorithms are used to track people’s behaviour, there is no ‘observer’ in the strict sense of the word; no human (or other ‘cognitive entity’) actually ever checks the individual’s search profile. Nevertheless, the invisibility of the watchful entity does not diminish the precision with which the behaviour is being tracked; in fact, it is quite the opposite. Second, in the digital age mere awareness of the possibility that surveillance techniques exist has an impact on human behaviour, independently of whether there is actually an observing entity. More than ever before, Foucault’s ( 1975 ) addition to Bentham’s panopticon model is relevant. The gaze of the other person is internalized.
This brings us to the conclusion that, despite the fact that a loss of privacy does not necessarily involve a loss of autonomy, in the digital age when privacy is under threat, the independence of individual decisions is typically also compromised.
These observations are striking when we consider that Western societies in particular focus on the individual person, whose autonomy is esteemed very highly. We can contrast the self-image and ego vocabulary that prevail in everyday life with online situations where an individual’s autonomy is lost. There are two examples of this from domains where autonomy has traditionally been considered to be very important and where it has come under threat.
Advertising
In consumer and advertising ethics, the consumer’s free choice is the moral cornerstone. In the online world, this ethical value is scarcely met. Digitalisation facilitates customised advertising, which originally was presented as a service for the individual. Tailored information was supposed to strengthen a person’s capacities to make choices to his own advantage. But now the procedure has become degenerated; people are placed into a filter bubble based on algorithms and corporate policies that are unknown to the target persons. Individuals’ control and knowledge about the flow of information are lost. As we all are keenly aware, requiring people to agree with terms and conditions does nothing to solve the problem. In the first place, very few people even read them. This kind of autonomy is apparently too demanding for most people to exercise. Secondly, the terms and conditions do not themselves say anything about the algorithms. Today’s consumer finds himself in a grey area, where he struggles between exercising autonomy and being influenced by others.
Of course, it is an empirical question as to what degree the algorithms influence customers’ behaviour. The least we can say is that the wide application of algorithms suggests that they must have a substantial effect. Following the critical study of Sunstein ( 2009 ) in which he warns that the political landscape might become fragmented (‘cyberbalkanization’), much research has been undertaken on the influence of algorithms on political opinions. This has resulted in a nuanced view of the widespread existence of ‘confirmation bias’. For instance, it has been shown that the need for information that confirms one’s opinion differs from other kinds of information and that it is stronger in those people who have more extreme political opinions. Furthermore, there turns out to be a major difference between how often individuals actively search for opinions similar to their own (what people usually do) and how often they consciously avoid noticing opinions that differ from their own (which are far more infrequent). People surfing the Internet often encounter news they were not consciously looking for, but which they nevertheless take seriously. This is called ‘inadvertent’ attention for news (Garret 2009 ; Tewksbury and Rittenberg 2009 ; Becker 2015 , Chap. 4).
The question how online networks influence exposure to perspectives that cut across ideological lines received a lot of attention after the Brexit referendum and Trump election. Using data of 10.1 million Facebook users Bakshy et al. confirm that digital technologies have the potential to limit exposure to attitude-challenging information. The authors observed substantial polarization among hard content shared by users, with the most frequently shared links clearly aligned with largely liberal or conservative populations. But one-sided algorithms are not always of decisive importance. The flow of information on Facebook is structured by how individuals are connected in the network. How much cross-cutting content an individual encounters depends on who his friends are and what information those friends share. According to Bakshy et al. on average more than 20% of an individual’s Facebook friends who report an ideological affiliation are from the opposing party, leaving substantial room for exposure to opposing viewpoints (Bakshy et al. 2015 ). Dubois and Blank, using a nationally representative survey of adult internet users in the UK found that individuals do tend to expose themselves to information and ideas they agree with. But they do not tend to avoid information and ideas that are conflicting. Particularly those who are interested in politics and those with diverse media diets tend to avoid echo chambers. Dubois & Blank observe that many studies are single platform studies, whereas most individuals use a variety of media in their news and political information seeking practices. Measuring exposure to conflicting ideas on one platform does not account for the ways in with individuals collect information across the entire media environment. Even individuals who have a strong partisan affiliation report using both general newssites which are largely non-partisan and include a variety of issues (Dubois and Blank 2018 , see also Alcott et al.). These findings are consistent with other studies that indicate that only a subset of Americans have heavily skewed media consumption patterns (Guess et al. 2016 ).
Research ethics
Corporations such as Google and Facebook, as well as data brokers use people’s personal information in their research activities. One disturbing example is the research that Facebook conducted in 2014. The corporation experimented on hundreds of thousands of unwitting users, attempting to induce an emotional state in them by selectively showing either positive or negative stories in their news feeds (Kramer et al. 2014 ; Fiske and Hauser 2014 ). Acquiring information by manipulating people without their informed consent and without debriefing them is a gross violation of the ethical standards that established research institutions must follow.
Such violations of people’s autonomy indicate a striking contrast between the offline ideals of most users and their online practices. Whereas in the offline world we typically take autonomy as a moral cornerstone, on the Internet this ideal is not upheld. How to deal with this discrepancy in values upheld in the real world and on the Internet is one of the central challenges in discussions about privacy. When we do not strive for more clarity and transparency in the flow of information, we relinquish autonomy, a value that is deeply embedded in Western cultures.
The social approach
We might be tempted to associate the emergence of the social approach in discussions about privacy with the digital age, as if only in these times of rapid information flow reflection on the social dimension of privacy is justified. This, however, would be a false suggestion. During the twentieth century, an important undercurrent in discussions of privacy was an emphasis on the importance of privacy for social relationships. Privacy was seen as a component of a well- functioning society (Regan 2015 ), in that it plays an important role in what is described as a differentiated society. Privacy guarantees social boundaries that help to maintain the variety of social environments. Because privacy provides contexts for people to develop in different kinds of relationships, respect for privacy enriches social life. Privacy also facilitates interactions among people along generally agreed patterns (Schoemann 1984 ). As the poet Robert Frost remarked in Mending Wall ( 1914 ), Good fences make good neighbors .
This characteristic of privacy is important not only at an institutional level. In people’s private lives the creation and maintenance of different kinds of relationships is possible only when subtle differences in patterns of social behaviour and social expectations are recognized (Rachels 1984 , Marmor 2015 ). Remarkably, this subtlety becomes clearest in examples of intrusions of privacy in unoccupied public places. Consider (a) someone who deliberately attempts to sit beside lovers who are sitting together on a park bench, or (b) intrusive bystanders at the scene of a car accident. In both cases, the intrusions of the privacy of the persons involved are very important. The most trivial words and gestures can reflect a deep dedication and intense relationship between two people. In one of the first descriptions of the core of privacy, the English jurist and philosopher Stephens depicted it as an observation which is sympathetic (Schoemann 1984 ). Sympathetic is derived from the Greek word sympathein , which means being involved with the same. Indeed, in private situations, different people experience the same things as important. A small, clearly distinguished domain is created, and the events should be shared only by those who directly participate in them. The persons involved are tied together by having undergone common experiences. They have an immediate relationship to what is at stake, and in this relationship they are deeply engrossed. An outside observer who has not participated in the common experience is viewed as invading their privacy. He cannot share the meaning of what is going on because he has not been directly involved.
When understood this way the concept of privacy is helpful in explaining the difference between occasionally being noticed and being eavesdropped upon. In cases involving eavesdropping, someone participates in an indirect and corrupt way in what is going on. The participation is indirect because the person acquires knowledge without participating directly; the things that are at stake should not concern him. The participation is corrupt because the indirect participant is not genuinely interested in what is going on. He sees the others involved not primarily as people with their own sensibilities, goals, and aspirations, but as the objects of his own curiosity. When the other people become aware that they are being observed, they begin to see themselves through the eyes of the observing person, and they thereby lose spontaneity. Their direct involvement in the meaning of what is at stake is lost.
In cases like these, neither the content of the action nor the secrecy surrounding it qualifies the actions as belonging to the private sphere. The content might be very trivial, but it would be offensive to the lovers sitting on the park bench to suggest that what they are expressing to each other could be made public. The most commonplace of actions—for instance, walking with one’s children down the street—can be private. Note the indignation of people in the public eye about obtrusive photographers who take photographs of public figures while they are doing ordinary things like we all do. The essence of secrecy is intentional concealment, but the private situations that we discuss here concern behaviour, inward emotions, and convictions that can be shown and experienced in various places that are accessible to everyone, as for instance in the case of the young couple we saw sitting in the park (Belsey 1992 ).
This characteristic of privacy in social relationships cannot be captured by the concept of autonomy in the sense of an individual independently and deliberately making his or her own choices. What is at stake in situations like these is not a lack of transparency. There is no question about the autonomy of an independent individual. The person would be deeply engrossed in precarious and delicate situations involving social relationships. An intrusion on this person’s privacy would mean that he feels inhibited in being immersed in the social interaction and share the meaning at stake.
In order to do justice to this notion of privacy, other strategies for protecting privacy are required. It is not primarily an individual’s mastery that must be protected; rather, it is the possibility for the individual to be properly embedded in social relationships. To answer the question of how this concept of privacy manifests itself in the digital age, we turn to Helen Nissenbaum’s contextual integrity model, which is an elaboration of socially embedded privacy in the digital age.
Helen Nissenbaum’s contextual integrity model
After having conducted several preliminary studies, Helen Nissenbaum published Privacy in Context (2009), a book that became very influential in philosophical and political debates on privacy. It inspired the Obama administration in the United States to focus on the principle of respect for context as an important notion in a document on the privacy of consumer data (Nissenbaum 2015 ). The core idea of Nissenbaum’s model is presented in the opening pages of her book: ‘What people care most about is not simply restricting the flow of information but ensuring that it flows appropriately .’ In Nissenbaum’s view, the notion ‘appropriate’ can be understood to mean that normative standards are not determined by an abstract, theoretically developed default. The criteria for people’s actions and the expectations of the actions of other people are developed in the context of social structures that have evolved over time, and which are experienced in daily life. As examples of contexts, Nissenbaum mentions health care, education, religion, and family. The storage, monitoring, and tracking of data are allowed insofar as they serve the goals of the context. Privacy rules are characterized by an emphasis on data security and confidentiality, in order to ensure that the flow of information is limited only to the people directly involved. The key players in the context have the responsibility to prevent the data from falling into the wrong hands.
Nissenbaum’s model is well-suited for the information age. It describes privacy in terms of the flow of information, and the model is easy to apply to institutional gatekeepers who deal with data streams. At the same time, the contextual approach deviates from the classical view of autonomy. The personal control of information loses ground, and shared responsibility that is expressed through broader principles becomes more important. Nissenbaum considers it a serious disadvantage of the autonomy approach that it is usually associated with notions of privacy that are based on individuals’ rights. In the articulation of justificatory frameworks in policymaking and the legal arena, we often see major conflicts among parties who insist that their rights and interests should be protected. She also distances herself from the connection between privacy and secrecy (for a recent description of this connection, see Solove 2015 ). Privacy is not forfeited by the fact that someone knows something about another person. Within contexts, information about persons might flow relatively freely. In line with this, Nissenbaum puts into perspective the classic distinction between the private and the public realm. Contexts might transgress borders between the public and the private. For instance, professionals in social healthcare work with information that comes from intimate spheres. As professionals, they are, however, part of the public domain. It is their professional responsibility to deal properly with the flow of information within the realm of their own activities.
Normative weakness and the threat of conservatism
Nissenbaum’s rejection of autonomy as the basis for privacy raises questions about the normative strength of her model. Does she indeed deliver the justificatory platform or framework to reason in moral terms? She asserts that her model does do so when she claims that the context procures a clear orientation, which can guide policies on privacy. This claim suggests that it is completely clear what a context is, as is the way in which it delivers a normative framework. In this respect, Nissenbaum’s work has some flaws.
In her description of context as a structured social setting that guides behaviour, Nissenbaum refers to a wide array of scholars from social theory and philosophy. Nissenbaum ( 2009 ), for instance, reviews Bourdieu’s field theory, Schatzki’s notion of practice in which activities are structured teleologically, and Walzer’s Spheres of Justice . There are, however, major differences among these authors. Schatzki focuses on action theory and the way in which people develop meaningful activities; Walzer describes the plural distribution of social goods in different spheres of human activity; and Bourdieu focuses on power relationships. When searching for a normative framework, it matters which of these approaches is being taken as the starting point. The theories also differ in their emphasis on a descriptive (Bourdieu) versus a normative (Walzer) analysis.
This vagueness about the normative framework is a serious problem because protection of privacy in the digital age requires systemic criteria to measure new developments against established customs. Nissenbaum assumes at the start that online technologies change the way in which information flows, but they do not change the principles that guide the flow of information. The principles by which digital information flows must be derived from the institutions as they function in the off-line world, i.e., the background social institutions (Nissenbaum 2009 ). Consider online banking as an example. In the digital age, contacts between costumers and banks have completely changed. Impressive buildings in which people previously made financial transactions have been partly replaced by the digital flow of information. But the core principles regarding the actions of the actors (the so called information and transmission principles) have not changed. This implies that people working within the context are familiar with the sensible issues, and they have the final say. The only thing that must be done is to translate the principles to the new situation. In case the novel practice results in a departure from entrenched norms, as Nissenbaum says, the novel practice is flagged as a breach, and we have prima facie evidence that contextual integrity has been violated (Nissenbaum 2009 ). Indeed, Nissenbaum admits that this starting point is inherently conservative, and she flags departures from entrenched practice as problematic ( 2009 ). She leaves open the possibility that completely new developments can lead to a revision of existing standards, and she gives ample guidelines about how to implement such a revision (Nissenbaum 2015 ).
Nissenbaum’s emphasis on existing practices must be understood in the context of a non-philosophical and non-sociological source, e.g., the notion of reasonable expectation, which plays an important role in United States jurisprudence on privacy. In the conclusion of her book, Nissenbaum ( 2009 ) describes privacy as ‘a right to live in a world in which our expectations about the flow of personal information are, for the most part, met’. Reasonable expectation was the core notion in the famous case of Katz versus United States , which laid the foundation for privacy discussions in the United States. Before Katz , it had already been recognized that within one ’ s own home, there was a justified expectation of privacy. Katz dealt with the kind of privacy situations in the public sphere that was described in the preceding paragraph. In this case, a phone call had been made from a public phone booth while enforcement agents used an external listening device to listen to the conversation. The Court considered this to be unjustified. The Fourth Amendment to the United States Constitution protects people, but not places; therefore, the actions of the enforcement agents constituted an intrusion. Regardless of location, oral statements are protected if there is a reasonable expectation of privacy. This extension of privacy was a revolutionary development, and the notion of reasonable expectation turned out to work well. For instance, in cases where the distinction between hard-to-obtain information and information that is in plain view plays an important role. In many cases, however, just because information is in plain view does not mean there is a reasonable expectation of privacy. Consider the situation where the police accidentally uncover illegal drugs concealed in an automobile. In cases like this, an appeal to privacy to protect criminals cannot be justified.
However, the normative strength of the notion reasonable expectation is weak. The notion refers to existing practices; reasonable is what in a society counts as reasonable. In many cases, this might work out well. We usually do not need polls to make it clear what reasonable means. Eavesdropping is despised, yet video surveillance in a taxi is generally accepted. Police arbitrarily invading a house is not justified; however, police actively working to find concealed drugs are justified. In times of rapid development, referring to existing practices to find ultimate normative justification is not a good strategy, for at least two reasons. First, the danger of rigid conservatism might be just around the corner. This danger was already present in Nissenbaum’s idea that standards for online intrusions of privacy must be derived from the offline world. In times of technological developments new problems make their appearance, and new technologies change the effects of existing rules. Particularly in the digital age, practices and normative conceptions are under pressure; existing frameworks cannot be used unequivocally. In the times of Katz , the distinction between hard-to-obtain information and information in plain view was based on how easy it was to access the information, irrespective of the type of information. This distinction is out-of-date in the digital age. The revolution in techniques of surveillance makes almost all information that is in plain view information. Any development in surveillance or monitoring, if communicated well, might be placed under the umbrella of reasonable expectation. Suppose a government takes highly questionably measures (for instance, it collects all metadata on phone calls) and is completely honest about doing so. The government does not want to surprise its citizens, so it duly informs the public that this is how things are being done. Anyone who makes a phone call has the expectation that her data will be stored. We all know this is not simply a hypothetical example. The same pattern can be distinguished in the way Google and Facebook justify their practices. Thanks to Mark Zuckerberg’s and Eric Schmidt’s statements, Facebook and Google users do not have expectations about privacy. Ironically, the insistence on transparency, which is so often heard in debates on privacy, takes the sting out of the idea of reasonable expectation. Transparency implies that data streams can flow in all directions, as long as the responsible persons are open and honest about it (Schoonmaker 2016 ).
Some would suggest that the word reasonable (as opposed to unreasonable ) has a certain normative strength. The word refers to standards that have a certain degree of plausibility and are widely shared. Again, however, in order to guarantee protection of privacy, we need more guidance about what these standards mean, for the concept itself does not provide this guidance. The matter is turned upside down when we search for normative strengths simply by referring to current practices.
The threat of conservatism in the digital age and the failure of the notion reasonable expectation lead us to the conclusion that strong anchors, which meet certain criteria, are needed. This is first of all apparent in the conservative-progressive dimension. The standards must be related to existing frameworks; alienation from these hampers acceptance. On the other hand, they shouldn’t be so rigid that promising new developments are impeded. Second, it is apparent in the general-specific dimension. To motivate people, they must be so general that a wide range of applications is possible. Nevertheless, they should not be too vague; they must be specific enough to contain guidelines for action.
A variety of notions that describe normative standards accompany Nissenbaum’s reference to various philosophical and sociological sources. As far as the dimension conservative-progressive is concerned, she switches, on the one hand, between internal logic of and settled rationale for social systems, and she pleads, on the other hand, for the moral superiority of new practices (Lever 2015 ). Nissenbaum also speaks about ultimate criteria as delivered by the purposes and ends of the context. This description is too concrete in times of rapid technological developments. Today’s targets become outmoded tomorrow. Some more general notion is required. In a recent refinement of her model, Nissenbaum ( 2015 ) provides more clarity. For example, she mentions a few domains of cooperative activities that need not count as context per se. The business model for instance does not count as context, because in business the core value is earning money. When everything is for sale, it is impossible to develop independent, substantive landmarks. She also makes it clear that a describing context as a technological system is highly problematic. It leads to technological determinism, and therefore is a petitio principi . Normative standards about how to deal with technological problems are derived from technological developments. A proper context can count as what she describes as a social domain. Remarkably, she hardly considers this notion.
The search for independent substantive landmarks might be guided by the expression norms and values, which Nissenbaum uses in her book. Norms are fixed standards. Usually they are concrete descriptions of particular things that must be realised or derived. Norms are necessary for guiding actions, but in times of fast changes they are too rigid. Values, on the other hand, are very general, even though they are not vague. Values such as justice, responsibility, and efficiency are used in a wide variety of contexts. This is especially true for the group of values (e.g., justice, respect, integrity, decency) that is concerned with the way in which we treat other people. These values surpass the context; they are important in society as a whole. They are, therefore, too general to deliver a normative orientation for actions within a context. One way to solve this problem would be to rewrite the values in a context-specific sense. This requires orientation points that refer to characteristics of the contexts.
At the end of her book, Nissenbaum admits that her description of context is deficient; she acknowledges that further research on the concept is necessary. We suggest following a suggestion that Nissenbaum herself made. In a short paragraph in Privacy in context , she refers to Michael Walzer’s conception of goods as constitutive for contexts. It is the only notion to which she devotes a full paragraph; intriguingly, however, she does not elaborate on this concept in her later work. This notion could be very useful for making more explicit the underlying normativeness in contexts.
The concept of substantial goods
In his famous Spheres of Justice , Walzer ( 1983 ) stresses that he does not include material objects of transaction in his definition of goods. Instead, he uses a broader and more abstract notion of goods. They are immaterial qualities that people conceive and create in the course of their actions. In his book, he comments on goods such as security, education, health, kinship, and life. While performing an action, people are oriented towards goods such as these. The goods come into people’s minds before they come into their hands. Goods are, moreover, crucial for social relationships (Walzer 1983 ). The development of goods takes place in social contexts. For people to be able to live together, they must have more or less shared conceptions about the meaning of vital goods. The main goal of Walzer’s book is to show that different spheres of actions are characterized by different conceptions of goods, and subsequently different distributions of principles. The book turned out to be a very important expression of an idea that became very influential in determining standards for professional conduct: When human beings closely share an orientation on good actions with other human beings, this leads to a proper professional life. Only when goods are determined is it possible to adjust the standards. Without going into detail, we can point to two lines of thought that have contributed to elucidation and specification of the notion good .
Both Charles Taylor and Bernard Williams have distinguished goods from objects of impulsive desires and wishes by explaining that goods have an impact on a deep level of motivation. Goods ‘are judged as belonging to qualitatively different modes of living’ (Taylor 1999 ). They are the fulfilment of deeper commitments and engagements. Not the intensity of the desire but the sense of worth that makes life meaningful is characteristic of human attitudes towards goods. Attachment to and engagement with goods extend over a longer period and lead to a deeper fulfilment when satisfied. Goods give meaning to professional life (Williams 1981 ).
For professional ethics, Alisdair MacIntyre’s contributions have been of great importance. He elaborated on a distinctive characteristic of the concept good, which professionals have very often used in dealing with moral dilemmas. In socially established cooperative activities—MacIntyre mentions various examples of these, such as chess, portrait-painting, and education—people are guided by internal goods, which are defined as abstract qualities that are realised in the course of an active life. MacIntyre distinguishes between internal goods and external goods such as money, power, and prestige. External goods are necessary only for maintaining organizations and institutions, so that the kernel for a practice exists in realising internal goods. The distinction between internal and external goods can be made along two lines. First, external goods are called external as they also can be acquired through activities that are not restricted to the practice. This is true in the sense that in activities outside the practices money, power, and prestige play a role, but it is also true in the sense that within practices it is possible to acquire money, power, and prestige through dishonest means. In opposition to this internal goods can be acquired only by excelling in activities that belong to the practice. Secondly, external goods are always in some individual’s possession. The more someone has of them, the less there is for other people. They are always objects for competition. Internal goods, on the other hand, are not in short supply. Their achievement is good for the whole community whose members participate in the practice; they can be shared in the full sense of the word. Many people can be orientated towards acquiring them without being in conflict with one another. In fact, a common orientation strengthens the motivation of each member of the community.
The differences among these authors do not invalidate their common focus. The distinctions they make are insightful for understanding how certain kinds of activities contribute to a meaningful life. We describe them under the heading ‘substantial goods’, which furnish us with a normative framework that can be used to evaluate activities. During recent decades, this line of thought has played an important role in public administration (Becker and Talsma 2015 ), journalism (Borden 2007 ), business (Solomon 1992 ), healthcare (Day 2007 ), and science. It has been particularly helpful to distinguish between qualities that are related to the content of a work and institutional and external pressures. For instance, the appropriate task for a variety of professions that stress quantitative performance measures can be elucidated using the emphasis on substantial goods; they include journalists working in a democracy, scientists working in academic institutions, and public administrators who must answer to higher-level management. The ultimate goal of their actions does not lie in complying with external standards, but in realising goods that are themselves recognized as being of substantive importance.
Substantial goods in Helen Nissenbaum’s model
In the application of this line of thought to Helen Nissenbaum’s model, we make explicit the goods that are at stake in a context, and we take them as the starting point for decisions about the flow of information. This strategy can contribute to the solution of several problems that currently stand in the way of further applying Nissenbaum’s model.
A more explicit articulation of the goods at stake will be helpful in solving the problem of conservatism. We have discussed how the notion of ‘reasonable expectation’ and Nissenbaum’s model might evoke the reproach of someone with a conservative orientation to fixed standards that do not do justice to new developments. The notion of substantial goods enables us to describe activities under a normative perspective without being restricted to certain activities. The meaning of goods can be translated in various activities. New developments lead to new interpretations of the goods involved, which, in turn, facilitate innovation. Take, for instance, education. Under the umbrella of having a good education, a wide variety of patterns of education can be developed, and new trends can be incorporated.
Another advantage of elaboration of the notion of goods is that it contributes to a sharper context-specific meaning of broad, general values, such as justice, respect, and integrity. These values are very important throughout society as a whole. But the price they have to pay for the overall appreciation is that they are vague and abstract. A more precise meaning requires them to be applied in concrete contexts. This is exactly what Michael Walzer does with the value ‘justice’ in Spheres of Justice . He shows that the criteria for distribution are dependent on standards that differ from one context to another. Likewise, a precise description of the meaning of the notion ‘respect’ in education (i.e. respect for the student or the teacher) differs from respect as understood in healthcare (i.e. respect for the patient). Knowledge of the substantial goods at stake is helpful when it comes to concretizing these broad notions. And this is not simply a superfluous luxury in the digital age. For instance, in healthcare explicit awareness of the meaning of ‘respect’ for the patient helps to determine the appropriate flow of information that benefits the patient’s health. It is, therefore, helpful in protecting the interests of the patient from institutional pressures or pressures from special interest groups.
In addition to these merits, an articulation of the substantial goods delivers a welcomed intervention in an otherwise awkward debate about the different roles that privacy can play. Privacy is not exclusively positive. It can, for instance, be used to conceal poor practices. Hiding information is a central feature of deception. For instance, feminists have stated that privacy is the enemy of equality… placing ordinary people at the mercy of powerful people (Marx 2015 ). For criminals, privacy is a cover-up for their activities. Relating privacy to the substantial goods it serves is helpful in these debates, in which privacy seems to be a double-edged sword. When it is clear which kinds of goods privacy serves (e.g. goods of particular interest groups; emancipation; the common good), a context-specific discussion on the value of privacy is possible.
Finally, the notion of goods importantly contains a normative orientation, which is distinguished from, for instance, economic imperatives. After all, commercial interests are increasingly hampering privacy. A stronger awareness of the substantial goods at stake strengthens arguments against commodification. This is even more important as privacy is increasingly encroached upon in terms of trade-offs. People are being seduced to choose between, for instance, more privacy versus more customized offers from corporations or more privacy versus paying a lower insurance premium. In such trade-offs, privacy is described as a luxury that only wealthy people can afford (Criado and Such 2015 ). How far can we go without spoiling what is vital for leading a good life? A strong articulation of substantive goods will be helpful placing a barrier between commercial pressures and leading a good life.
Conclusions
During the past decade, we have witnessed the emergence of the so-called social approach to privacy. This approach must be clearly distinguished from an autonomy approach. These two approaches rely on different normative frameworks and different justification strategies. Both of them have their merit in the digital age. Changing technologies threaten autonomy, and autonomy is indispensable for making clear what is at stake in discussions of privacy. Neglecting autonomy and the processes that threaten to undermine it is harmful for individuals. The social approach, which has been an undercurrent for decades, gains importance in the digital age. When privacy is defined in terms of control over flows of information, an approach is required that surpasses the perspective of the individual. The right to privacy provides protection in relationships with other human beings and with institutions, where the fulfilment and development of one’s personal identity can be realised. The normative strength of this approach can be improved by a more explicit elaboration of the goods that are at stake.
Bakshy, E., Messing, S., & Adamic, L. (2015). Exposure to ideologically diverse news and opinion on Facebook. Science, 348 (6239), 1130–1132.
Article MathSciNet Google Scholar
Becker, M. (2015). Ethiek van de digitale Media . Amsterdam: Boom.
Google Scholar
Becker, M., & Talsma, J. (2015). Adding colours to the shades of grey: Enriching the integrity discourse with virtue ethics concepts. In A. Lawton, Z. Van der Wal, & L. Huberts (Eds.), Ethics in public policy and management: A global Research companion (pp. 33–49). London & New York: Routlegde.
Chapter Google Scholar
Belsey, A. (1992). Privacy, publicity and politics. In A. Belsey & R. Chadwick (Eds.), Ethical issues in journalism and the media (pp. 77–92). London: Routledge.
Borden, S. (2007). Journalism as a practice: Macintyre, virtue ethics and the press . Farnham: Ashgate.
Boyd, D. (2014). It’s complicated: The social Lives of networked Teens . New Haven, London: Yale University Press.
Criado, N., Such, J. M. (2015). Towards implicit contextual integrity. The Second International Workshop on Agents and CyberSecurity (ACySE), pp. 23–26.
Day, L. (2007). Courage as a virtue necessary to good nursing practice. American Journal of Critical Care, 16 (6), 613–616.
Dubois, E., & Blank, G. (2018). The echo chamber is overstated: The moderating effect of political interest and diverse media. Information, Communication & Society, 21 (5), 729–745.
Article Google Scholar
Esguerra, R. (2009). Google CEO Eric Schmidt dismisses the importance of privacy. Blog Posting. Electronic Frontier Foundation. Retrieved January 10, 2014 from https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy .
European Data Protection Supervisor (EDPS) Opinion 4/2015 ‘Towards a new digital Ethics’.
Fiske, S., & Hauser, R. M. (2014). Protecting human research participants in the age of big data. PNAS, 111 (38), 1375–1376.
Foucault, M. (1975). Surveiller et Punir. Naissance de la Prison . Paris: Gallimard.
Frost, R. (1914). Mending Wall. Poem in online collection. Retrieved March 13, 2014 from http://writing.upenn.edu/~afilreis/88/frost-mending.html .
Garrett, G. (2009). Echo chambers online? Politically motivated selective exposure among internet news users. Journal of Computer-mediated Communication, 14, 265–285.
Gavison, R. (1984). Privacy and the Limits of Law. In F. A. Schoemann (Eds.), Philosophical Dimensions of Privacy: An Anthology (pp. 347–402). Cambridge: Cambridge University Press. (Repr. From Gavison, R. (1980). Privacy and the limits of law. The Yale Law Journal, 89(3), 421–471).
Guess, A., Brendan, N., Reifler, J. (2016). Selective exposure to misinformation: Evidence from the consumption of fake news during the 2016 U.S. presidential campaign. Paper European Research Council, https://www.dartmouth.edu/~nyhan/fake-news-2016.pdf .
Kramer, A. D. I., Guillory, J. E., & Hancock, J. T. (2014). Experimental evidence of massive-scale emotional contagion through social networks. PNAS, 111 (24), 8788–8790.
Lever, A. (2015). Privacy, democracy and freedom of expression. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 162–183). Cambridge: Cambridge University Press.
Marmor, A. (2015). What is the right to privacy? Philosophy & Public Affairs, 43 (1), 4–26.
Marx, G. T. (2015). Coming to terms: The kaleidoscope of privacy and surveillance. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 32–49). Cambridge: Cambridge universiy Press.
Nissenbaum, H. (2009). Privacy in context: Technology, policy and the integrity of social life . Stanford: Stanford University Press.
Nissenbaum, H. (2015). Respect for context as a benchmark for privacy online: What it is and isn’t. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 278–302). Cambridge: Cambridge University Press.
Rachels, J. (1984). Why privacy is important. In F. A. Schoemann (Ed.), Philosophical dimensions of privacy: An anthology (pp. 290–294). Cambridge: Cambridge University Press.
Regan, P. (2015). Privacy and the common good: Revisited. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 50–70). Cambridge: Cambridge University Press.
Reiman, J. (1984). Privacy, intimacy and personhood. In F. A. Schoemann (Ed.), Philosophical dimensions of privacy: An anthology (pp. 300–316). Cambridge: Cambridge University Press.
Roessler, B. (2009). De glazen samenleving en de waarde van privacy. Filosofie & Praktijk, 30 (5), 20–29.
Roessler, B., & Mokrosinska, D. (2015). Introduction. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 1–8). Cambridge: Cambridge University Press.
Rule, J. B. (2015). Privacy: The longue durée. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 11–31). Cambridge: Cambridge University Press.
Schoeman, F. A. (1984). Privacy: Philosophical dimensions of the literature. In F. A. Schoemann (Ed.), Philosophical dimensions of privacy: An anthology (pp. 1–33). Cambridge: Cambridge University Press.
Schoonmaker, J. (2016). Proactive privacy for a driverless age. Information & Communications Technology Law, 25 (2), 96–128.
Solomon, R. (1992). Ethics and excellence: Cooperation and integrity in business . New York: Oxford University Press.
Solove, D. J. (2015). The meaning and value of privacy. In B. Roessler & D. Mokrosinska (Eds.), Social dimensions of privacy: Interdisciplinary perspectives (pp. 71–82). Cambridge: Cambridge University Press.
Strandburg, K. (2014). Monitoring, datafication and consent: Legal approaches to privacy in the big data context. In J. Lane, V. Stodden, S. Bender, & H. Nissenbaum (Eds.), Privacy, big data and the public good: Frameworks for engagement . Cambridge: Cambridge University Press.
Sunstein, C. (2009). Republic 2.0 . New Jersey: Princeton University Press.
Taylor, C. (1999). Human agency and language: Philosophical papers 1 . Cambridge: Cambridge University Press.
Taylor, J. S. (2002). Privacy and autonomy: A reappraisal. Southern Journal of Philosophy, 40 (4), 587–604.
Tewksbury, D., & Rittenberg, J. (2009). Online news creation and consumption. Implication for modern democracies. In A. Chadwick & P. Howard (Eds.), The Routledge handbook of internet politics (pp. 186–200). London: Routledge.
van der Sloot, B. (2014). Privacy as human flourishing: Could a shift towards virtue ethics strengthen privacy protection in the age of Big Data? Journal of Intellectual Property, Information Technology and Electronic Commerce Law, 5 (3), 230–244.
van Otterlo, M. (2014). Automated experimentation in Walden 3.0: The next step in profiling, predicting, control and surveillance. Surveillance and Society, 12, 255–272.
Walzer, M. (1983). Spheres of justice: A defence of pluralism and equality . Oxford: Blackwell.
Warren, S., & Brandeis, L. (1890). The right to privacy. Harvard Law Review , 4 (5), 193–220.
Williams, B. (1981). Persons, character and morality. In J. Rachels (Ed.), Moral luck . Cambridge: Cambridge University Press.
Download references
Author information
Authors and affiliations.
Radboud University Nijmegen, Nijmegen, The Netherlands
Marcel Becker
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Marcel Becker .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Becker, M. Privacy in the digital age: comparing and contrasting individual versus social approaches towards privacy. Ethics Inf Technol 21 , 307–317 (2019). https://doi.org/10.1007/s10676-019-09508-z
Download citation
Published : 17 July 2019
Issue Date : December 2019
DOI : https://doi.org/10.1007/s10676-019-09508-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Contextual integrity
- Find a journal
- Publish with us
- Track your research
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
How Americans View Data Privacy
3. a deep dive into online privacy choices, table of contents.
- Role of social media, tech companies and government regulation
- Americans’ day-to-day experiences with online privacy
- Personal data and information
- Feelings of concern, confusion and a lack of control over one’s data
- Privacy laws and regulation
- Americans largely favor more regulation to protect personal information
- Trust in social media executives
- Children’s online privacy: Concerns and responsibility
- Law enforcement and surveillance
- AI and data collection
- Trust in companies that use AI
- How people approach privacy policies
- How people are protecting their digital privacy
- How Americans handle their passwords
- Data breaches and hacks
- Identifying the most and least knowledgeable, confident and concerned
- Knowledge and privacy choices
- Confidence and privacy choices
- Concern and privacy choices
- The case of privacy policies
- Acknowledgments
- The American Trends Panel survey methodology
- Appendix A: Law enforcement’s use of technology in investigations
- Appendix B: Privacy outcomes by knowledge, confidence and concern
- Appendix C: Confident and independent use of digital devices, by age and education
People face a number of choices in managing their online privacy, and each person approaches these from a different angle.
Some people are tech-savvy and confident in their ability to protect their data. Others are overwhelmed trying to navigate the privacy settings that tech companies make available. And while many are concerned about their privacy, translating that concern into action can be complicated.
No single factor explains the ins and outs of people’s privacy choices. We explored three things that might matter: knowledge about privacy and cybersecurity topics; confidence in their tech skills; and concern about companies’ data collection. Each sheds light on potential reasons why people do what they do online.
Some overall takeaways:
- Knowledge and privacy choices : More privacy knowledge translates into more steps taken to protect data, but also more skepticism about whether those steps are actually useful.
- Confidence and privacy choices : Those who are most confident using digital devices generally trust themselves to make privacy decisions. They’re less overwhelmed than others. And they are more likely to take steps to protect their data.
- Concern and privacy choices : Concern about how companies use one’s data often goes hand in hand with action. But the most concerned tend to be especially overwhelmed, and not everyone who’s concerned takes these steps. Privacy policies are one example of a place where regardless of concern, Americans are largely inattentive.
In the sections that follow, we explore how privacy actions and feelings vary by six key groups:
- The most versus least knowledgeable about privacy and cybersecurity;
- The most versus least confident using technology; and
- The most versus least concerned about what companies are doing with people’s data. 3
The first two concepts relate to digital literacy. This can be defined in many ways but is widely agreed upon as critical in today’s world – including for technical, daunting topics like managing online privacy. 4 The third relates to an ongoing debate: Whether the “privacy paradox” exists . We walk through each of these below.
First, we included five questions that were part of a larger series of questions about tech knowledge .
Three of these questions were related to cybersecurity and best practices for “digital hygiene”: identifying the most secure password from a list, knowing that cookies track users’ visits and activity on websites, and being able to identify an example of two-factor authentication.
Two were about privacy regulations: knowing that the U.S. does not have a comprehensive national privacy law and knowing that websites in the U.S. are prohibited from collecting data from children under age 13 without a parent’s consent.
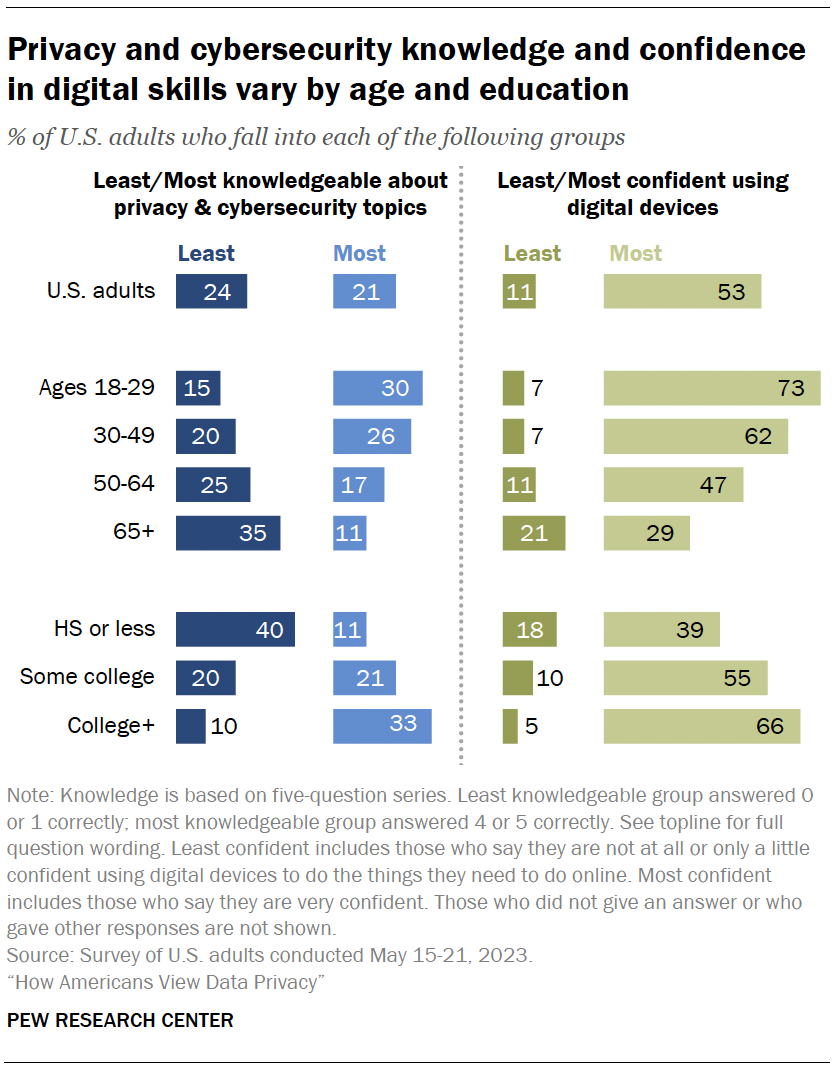
- 21% of Americans can correctly answer at least four of the five items. We refer to this group as most knowledgeable about privacy and cybersecurity topics. 5
- 55% give two or three correct answers.
- 24% answer zero or one item correctly; we call this group least knowledgeable.
Levels of knowledge vary notably by age and education.
Aside from knowledge, we also explored how people feel about their tech skills. 6 Specifically, we asked about people’s confidence using computers, smartphones or other electronic devices to do the things they need to do online. 7
- 53% of Americans say they are very confident in these abilities – we refer to them as the most confident.
- 36% are somewhat confident.
- 11% have little to no confidence – the least confident in this report.
And like privacy knowledge, confidence in tech skills varies notably across demographic groups.
We further looked at people’s concerns about how their data is being used. A large body of research has explored the possibility of a “privacy paradox”: Namely, worry about privacy doesn’t always translate into action.
Whether and why this “paradox” exists are up for debate. Some say convenience wins out even if you have to give up data. Others say people’s behaviors are more about being resigned to the realities of modern digital life .
When it comes to concern:
- 35% of Americans say they are very concerned about how companies are using the data they collect about them. We refer to them as the most concerned about this.
- 46% are somewhat concerned.
- 19% are not at all or not too concerned. We call them the least concerned.
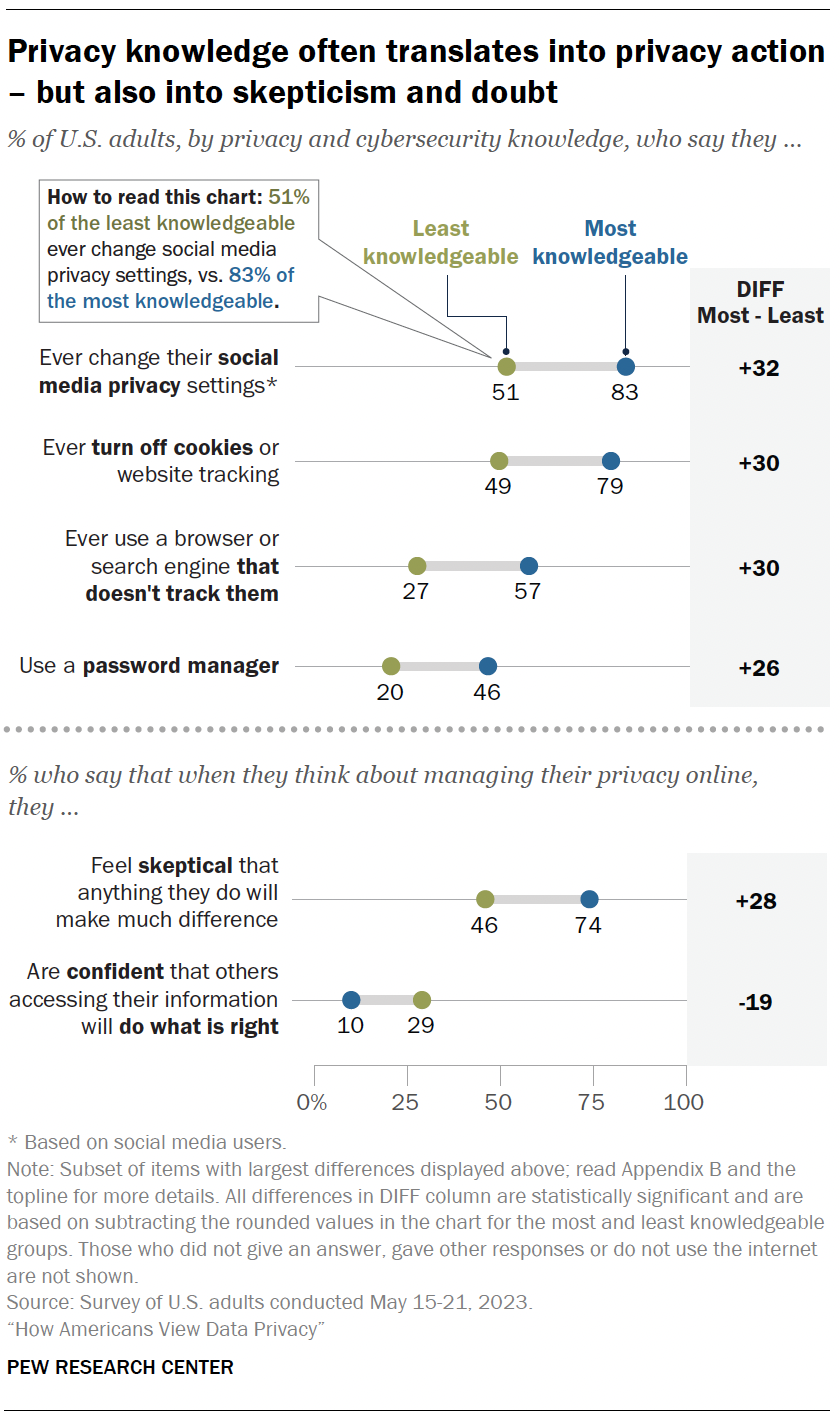
Those who know a great deal about privacy and cybersecurity are consistently more likely than those who know little to take actions to protect their data. 8
This pattern shows up across a number of items we examined. Some of the largest differences are in adjusting social media privacy settings, avoiding cookies, using a private browser or search engine and using a password manager.
Yet knowledge breeds doubt as well. The most knowledgeable Americans are far more skeptical than the least knowledgeable that their actions will make a difference. And they are less confident that others who can access their data will do what is right with it.
Age and knowledge
Even among the highly knowledgeable, some digital habits still vary by age.
Among the most knowledgeable social media users:
- 86% of the most knowledgeable users ages 18 to 49 ever change their social media privacy settings.
- This drops to 74% of those 50 and older.
There are also age differences among the most savvy in using password managers:
- Half of highly knowledgeable adults under 50 use a password manager.
- This compares with 40% of those 50 to 64 and 33% of those 65 and up.
Like knowledge, confidence also relates to how people act and feel about their online privacy.
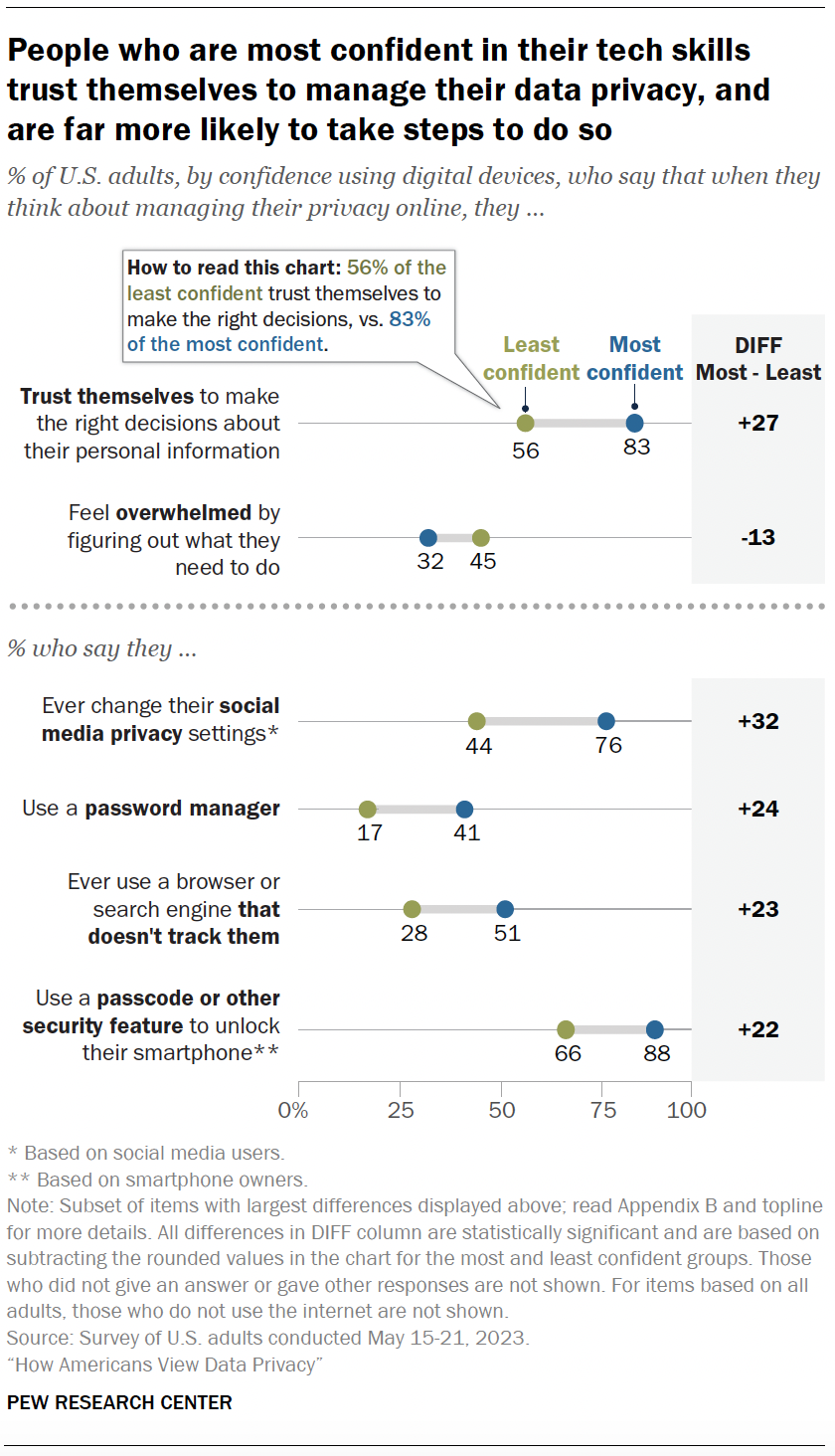
Americans who are most confident in their tech skills are most likely to trust themselves with privacy decisions. Fully 83% of the most confident say so. Still, more than half – 56% – of the least confident trust themselves with these kinds of calls.
The most confident are also far more likely to ever take each of the actions we explored. For example, 41% of the most confident Americans use a password manager, versus just 17% of those least confident in their tech skills.
The most confident are least likely to be overwhelmed by the task of managing online privacy. Those with moderate or low levels of confidence are both more overwhelmed, by comparison.
Even so, those with little to no confidence take some steps to protect their data:
- 66% of the least confident use a passcode lock on their phone, if they own one.
- 55% of the least confident ever decline cookies or other tracking on websites.
Skepticism also is widespread across confidence levels. A majority of the most confident say they’re skeptical that anything they do will make much difference, and about half of the least confident say the same.
Concern about what companies are doing with people’s data is related to the actions people take to protect their information – but still, not all of these steps are widely adopted.
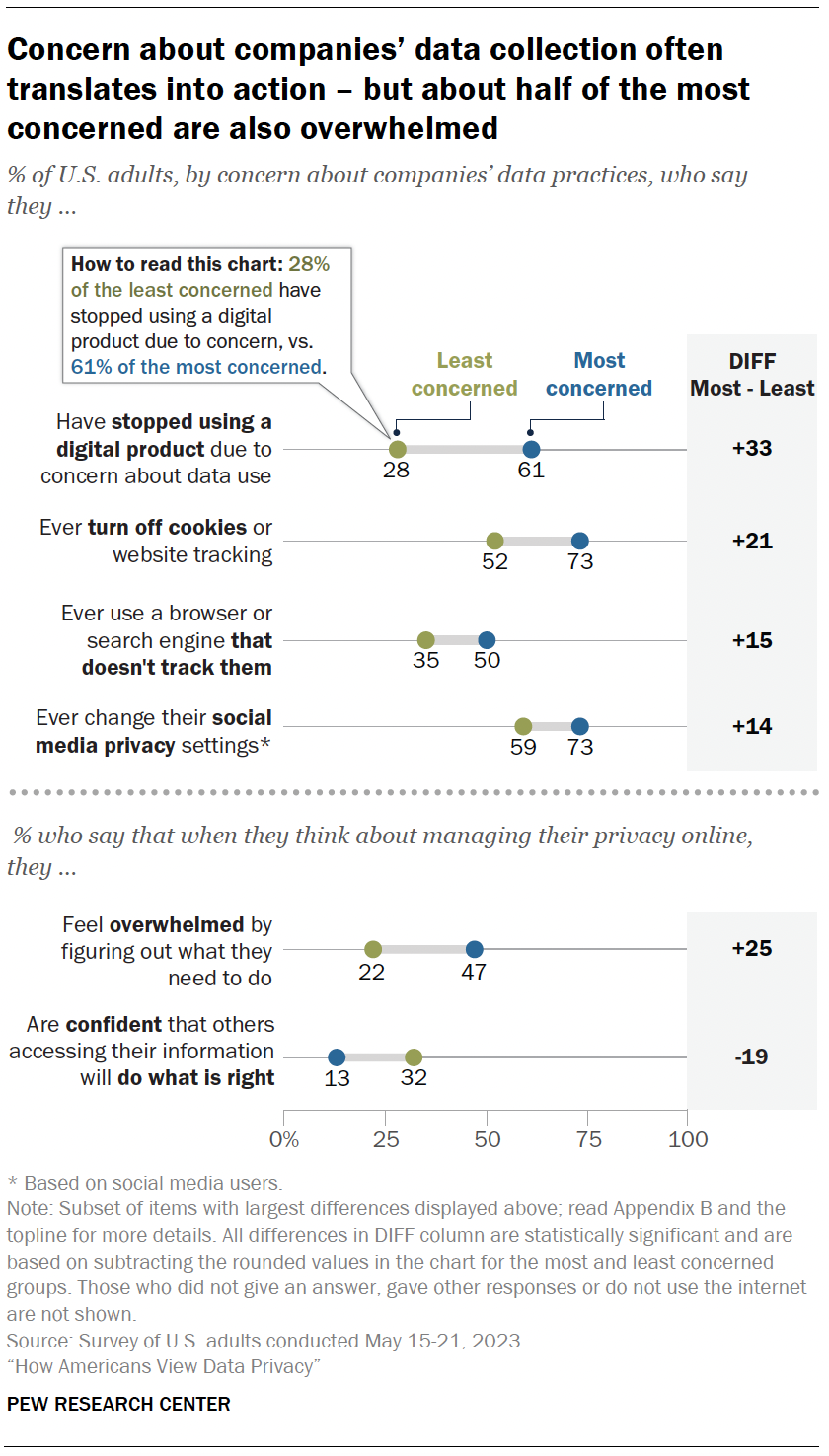
There are several large differences between the most and the least concerned.
For example, the most concerned are far more likely to have stopped using a digital device, website or app due to worry about how their personal information is being used. They’re also more likely to decline cookies, use a private browser or change social media privacy settings.
Yet this doesn’t mean everyone who is most concerned takes these steps. Half or fewer of the most concerned ever use a browser where they can’t be tracked or use encrypted messaging. And while a majority of the most concerned have changed up the digital products they use because of this, another 34% of this group have not done so.
It can be daunting to figure out how to address privacy concerns, and some of the emotional reactions we explored illustrate this.
The most concerned are far more overwhelmed managing their privacy, compared with those with little to no concern. About half of those who are highly concerned about companies’ data collection say they feel overwhelmed figuring out what to do.
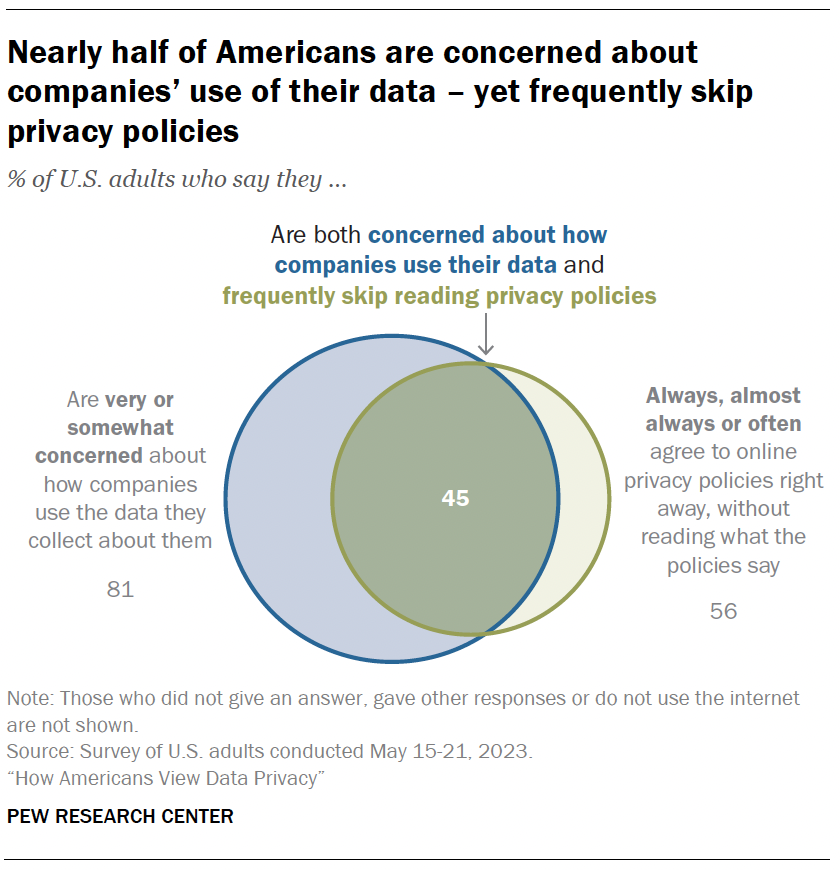
Americans’ approach to privacy policies illustrates these tensions between concern and action.
A notable share of Americans – 45% – are very or somewhat concerned about how companies use data they collect about them and, at the same time, say they frequently agree to privacy policies without reading them.
The survey was not designed to explore why people don’t take the time to read these policies despite their concern about what’s being done with their data. But majorities of Americans say they find them ineffective and just something to get past , suggesting that companies’ preferred method of communicating important details isn’t working for many.
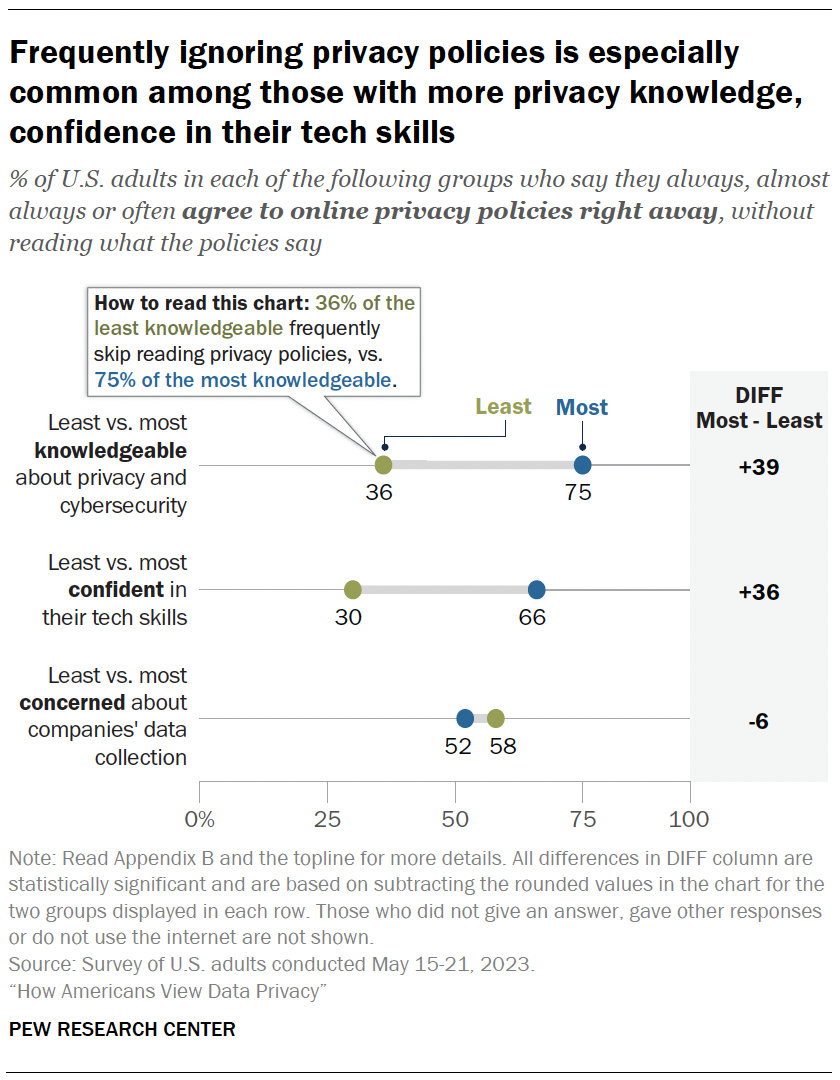
How concerned people are is less of a factor here: About half of Americans or more skip privacy policies frequently, regardless of concern about data use.
Ignoring privacy policies is especially common among those who are most knowledgeable or confident.
For example, three-quarters of the most knowledgeable say they frequently click “agree” without reading privacy policies. Among the least knowledgeable, that share drops to 36%.
This mirrors patterns by age and education discussed in Chapter 2. Younger adults and those with higher levels of formal education are especially likely to ignore online privacy policies . These groups also have more knowledge and confidence.
Within the most knowledgeable group, we still see that age matters:
- Some 84% of highly knowledgeable 18- to 29-year-olds frequently skip privacy policies.
- That share is 75% among those ages 30 to 49 and 70% of those 50 to 64.
- And it drops further to 59% among those 65 and older.
- For results among “moderately” knowledgeable, confident and concerned Americans, read Appendix B . ↩
- Researchers and practitioners have taken a number of approaches to defining digital literacy. While this analysis explores only a limited number of measures, we acknowledge the broader body of literature around these topics relevant to privacy and online life generally. ↩
- All questions were multiple choice. For purposes of this analysis, answers were counted as “not answered correctly” if the respondent chose an incorrect answer, said they were not sure, or skipped the question. For more on how these individual shares break down – for example, the share of Americans who were not sure – refer to the topline or read our report on Americans’ knowledge of AI, cybersecurity and Big Tech . ↩
- Read Appendix C for details on Americans’ ability to independently set up and use digital devices, which was covered in the survey but is not a focus of the analysis presented here. ↩
- The measures of knowledge and confidence are related, but not completely interchangeable. For example, just 3% of the most knowledgeable have little to no confidence in their tech skills. But at the other end of the spectrum, 31% of the least knowledgeable about privacy have a high level of confidence in their tech skills generally. ↩
- General conclusions presented in these sections largely remain unchanged when running analyses that control for demographic factors. ↩
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Artificial Intelligence
- Online Privacy & Security
- Social Media
- Tech Companies
Social Media Fact Sheet
Teens and social media fact sheet, more americans are getting news on tiktok, bucking the trend seen on most other social media sites, life on social media platforms, in users’ own words, charting congress on social media in the 2016 and 2020 elections, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Home — Essay Samples — Law, Crime & Punishment — Privacy & Security — Internet Privacy
Essays on Internet Privacy
The importance of writing an essay on internet privacy.
Writing an essay on internet privacy is crucial in today's digital age. With the increasing use of the internet for communication, social networking, and online transactions, the issue of privacy has become more important than ever. It is essential to educate people about the potential risks and threats to their privacy online and to advocate for stronger privacy protections.
Internet privacy is a fundamental human right, and writing an essay on this topic can help raise awareness about the importance of protecting personal information online. It can also encourage individuals to take steps to safeguard their privacy and advocate for laws and regulations that protect their rights.
When writing an essay on internet privacy, it is important to research and gather relevant information from credible sources. This may include academic journals, government reports, and reputable news outlets. It is also important to consider different perspectives and arguments on the topic to provide a well-rounded and comprehensive analysis.
Additionally, it is crucial to clearly articulate the potential risks and threats to internet privacy, such as data breaches, online surveillance, and identity theft. Providing real-life examples and case studies can help illustrate the impact of these issues on individuals and society as a whole.
Furthermore, it is essential to offer practical tips and solutions for protecting internet privacy, such as using strong passwords, enabling two-factor authentication, and being cautious about sharing personal information online. By empowering individuals with the knowledge and tools to protect their privacy, the essay can have a positive impact on the reader and the broader community.
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy-conscious and informed society.
- The importance of internet privacy in the digital age
In today's technology-driven world, internet privacy has become a major concern for individuals and businesses alike. With the increasing amount of personal information being shared online, it is important to understand the importance of protecting one's privacy on the internet. This essay will delve into the reasons why internet privacy is important and the potential consequences of not safeguarding one's online information.
- The evolution of internet privacy laws
Over the years, there have been significant developments in internet privacy laws as governments and regulatory bodies have recognized the need to protect individuals' personal information online. This essay will explore the evolution of internet privacy laws, including the landmark legislation and regulations that have been enacted to safeguard online privacy rights.
- The impact of social media on internet privacy
Social media has revolutionized the way we communicate and share information, but it has also raised concerns about internet privacy. This essay will examine the impact of social media on internet privacy, including the risks associated with sharing personal information on social networking platforms and the measures individuals can take to protect their privacy online.
- The role of technology in internet privacy
Advancements in technology have both enhanced and compromised internet privacy. This essay will discuss the role of technology in internet privacy, including the development of encryption tools, the rise of data breaches, and the potential implications of emerging technologies on online privacy rights.
- The ethical considerations of internet privacy
As individuals and businesses navigate the digital landscape, ethical considerations surrounding internet privacy have come to the forefront. This essay will explore the ethical implications of internet privacy, including the ethical responsibilities of organizations to protect user data and the ethical dilemmas individuals face when sharing personal information online.
- The impact of data breaches on internet privacy
Data breaches have become a prevalent threat to internet privacy, as cybercriminals continue to target organizations to access sensitive personal information. This essay will examine the impact of data breaches on internet privacy, including the potential consequences for individuals and businesses and the measures that can be taken to mitigate the risks of data breaches.
- The future of internet privacy
As technology continues to evolve, the future of internet privacy remains uncertain. This essay will speculate on the future of internet privacy, including the potential challenges and opportunities that lie ahead as individuals and organizations strive to protect their online privacy rights.
- The intersection of internet privacy and cybersecurity
Internet privacy and cybersecurity are closely intertwined, as both are essential for protecting personal information online. This essay will explore the intersection of internet privacy and cybersecurity, including the measures that can be taken to safeguard online privacy and the role of cybersecurity in mitigating privacy risks.
- The global perspective on internet privacy
Internet privacy is a universal concern, and different countries have varying approaches to protecting online privacy rights. This essay will provide a global perspective on internet privacy, including the international laws and regulations that govern internet privacy and the challenges of ensuring privacy rights in a global digital landscape.
- The responsibility of individuals in protecting their internet privacy
Ultimately, individuals play a crucial role in protecting their internet privacy. This essay will discuss the responsibility of individuals in safeguarding their online privacy, including the best practices for maintaining internet privacy and the potential consequences of neglecting online privacy protection.
The Internet Makes Children Smarter
Is google making usupid summary, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
The Importance of Internet Privacy and Net Neutrality to Internet Users in The Modern Era
Why internet privacy should be protected, the importance of internet privacy, the importance of staying safe on social media, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Cyber Crime and Internet Privacy
The crucial role of internet privacy for a user, a privacy aspect to the internet of things, identifying threats and vulnerabilities in home internet connection, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Human Rights on The Digital Era
Brief history of cyber security, privacy issues in a smart city, the concepts and outcomes of net neutrality, the singaporean government's ideologically conservative view on the internet, enhancing online security: qr code-based authentication for banking, secure online auction system, iot: addressing security challenges and possible solutions, analysis of the benefits of internet censorship, internet censorship as a modern way to protect the youth, internet censorship as the new 'norm', internet censorship: beneficial, but restrictive, personal outlook on the issue of internet censorship, useful alternatives for internet censorship, wikipedia censorship: the advantage for governments authorities, the data protection: how your personal information is used by organisations, businesses or the government, protect your data. then hope for a tech revolution, how technological advancement is going to affect us, should the internet be regulated: exploring possibilites to follow, should the internet be regulated: is it about net neutrality, relevant topics.
- Domestic Violence
- War on Drugs
- School Shooting
- Drunk Driving
- Animal Cruelty
- Identity Theft
- Broken Windows Theory
- Gang Violence
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Follow us on Facebook
- Follow us on Twitter
- Criminal Justice
- Environment
- Politics & Government
- Race & Gender
Expert Commentary
Data security: Research on privacy in the digital age
Research on consumer attitudes toward digital privacy and the practices of tech companies that shape data collection and use policies.

Republish this article

This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License .
by Chloe Reichel, The Journalist's Resource April 12, 2018
This <a target="_blank" href="https://journalistsresource.org/economics/data-digital-privacy-cambridge-analytica/">article</a> first appeared on <a target="_blank" href="https://journalistsresource.org">The Journalist's Resource</a> and is republished here under a Creative Commons license.<img src="https://journalistsresource.org/wp-content/uploads/2020/11/cropped-jr-favicon-150x150.png" style="width:1em;height:1em;margin-left:10px;">
On your smartphone, you’re not much more than a data machine, generating reams of valuable information that tech companies can mine for insights, sell to advertisers and use to optimize their products.
The Cambridge Analytica scandal, which involves a third-party Facebook app that harvested data well beyond the scope of the 270,000 users who initially consented to its terms of service for use in political campaigns (including Donald Trump’s 2016 bid for the presidency), highlights anew the vulnerability of consumer data in this digital age.
But it’s easy to forget these risks to personal privacy and security while tapping out messages to friends or scrolling endlessly through the web. The distraction machines at our fingertips ask for access and we give it up quickly, hastily agreeing to unread privacy policies and terms of service in exchange for a fresh jolt of content.
Studies highlight this “digital privacy paradox,” in which people express concerns over their privacy but then act in ways that undermine these beliefs , for example, offering up personal data for a small incentive. This review features research on this topic — consumer attitudes toward digital privacy — as well as studies of the supply-side — that is, research on the practices of app developers and other tech companies that shape data collection and use policies.
“ Artificial Intelligence and Consumer Privacy ” Jin, Ginger Zhe. National Bureau of Economic Research working paper, 2018. DOI: 10.3386/w24253.
Summary: This paper looks at the risks big data poses to consumer privacy. The author describes the causes and consequences of data breaches and the ways in which technological tools can be used for data misuse. She then explores the interaction between privacy risks and the U.S. market. For example, the author highlights the “self-conflicting” views consumers hold about their privacy, citing literature in which consumers give away personal data for small incentives despite attitudes that might indicate otherwise. On the supply side, similar paradoxes exist — for example, despite an awareness of cyber risks, firms “tend to deploy new technology… before adopting security measures to protect them.” The author discusses how market forces might motivate firms to strengthen privacy settings in response to consumer concerns, but also mentions how market mechanisms can have the opposite effect, using the example of password policies and consumers’ demand for convenience (in the form of weaker password requirements). The author then describes how artificial intelligence might be used to mitigate data security and privacy risks. Lastly, she provides an overview of U.S. policy on consumer privacy and data security and describes future challenges in the field.
“ The Digital Privacy Paradox: Small Money, Small Costs, Small Talk ” Athey, Susan; Catalini, Christian; Tucker, Catherine. National Bureau of Economic Research working paper, 2017. DOI: 10.3386/w23488.
Abstract: “‘Notice and Choice’ has been a mainstay of policies designed to safeguard consumer privacy. This paper investigates distortions in consumer behavior when faced with notice and choice which may limit the ability of consumers to safeguard their privacy using field experiment data from the MIT digital currency experiment. There are three findings. First, the effect small incentives have on disclosure may explain the privacy paradox: Whereas people say they care about privacy, they are willing to relinquish private data quite easily when incentivized to do so. Second, small navigation costs have a tangible effect on how privacy-protective consumers’ choices are, often in sharp contrast with individual stated preferences about privacy. Third, the introduction of irrelevant, but reassuring information about privacy protection makes consumers less likely to avoid surveillance, regardless of their stated preferences towards privacy.”
“ Mobile Applications and Access to Private Data: The Supply Side of the Android Ecosystem ” Kesler, Reinhold; Kummer, Michael E.; Schulte, Patrick. SSRN Electronic Journal , 2017. DOI: 10.2139/ssrn.3106571.
Summary: This paper looks at strategies mobile app developers use to collect data, which apps are most likely to practice intrusive data collection, and what factors predict problematic personal data usage. By examining the variations in data collection strategies of different apps created by the same developers over a period of four years, the researchers uncover three trends. 1) With time and experience, developers adopt more intrusive data collection tactics. 2) Apps with intrusive data collection strategies most commonly target adolescents. 3) Apps that request “critical and atypical permissions” (i.e., access to various data sources) are linked with an increased risk of problematic data practices later on.
“ Consumer Privacy Choice in Online Advertising: Who Opts Out and at What Cost to Industry? ” Johnson, Garrett A.; Shriver, Scott; Du, Shaoyin. SSRN Electronic Journal , 2017. DOI: 10.2139/ssrn.3020503.
Abstract: “We study consumer privacy choice in the context of online display advertising, where advertisers track consumers’ browsing to improve ad targeting. In 2010, the American ad industry implemented a self-regulation mechanism that overlaid ‘AdChoices’ icons on ads, which consumers could click to opt out of online behavioral advertising. We examine the real-world uptake of AdChoices using transaction data from an ad exchange. Though consumers express strong privacy concerns in surveys, we find that only 0.23 percent of American ad impressions arise from users who opted out of online behavioral advertising. We also find that opt-out user ads fetch 59.2 percent less revenue on the exchange than do comparable ads for users who allow behavioral targeting. These findings are broadly consistent with evidence from the European Union and Canada, where industry subsequently implemented the AdChoices program. We calculate an upper bound for the industry’s value of the average opt-out user’s browsing information to be $8 per capita annually in the US. We find that opt-out users tend to be more technologically sophisticated, though opt-out rates are higher in American states with lower income. These results inform the privacy policy discussion by illuminating the real-world consequences of an opt-out privacy mechanism.”
“ The Economics of Privacy ” Acquisti, Alessandro; Taylor, Curtis R.; Wagman, Liad. Journal of Economic Literature , 2016. DOI: 10.2139/ssrn.2580411.
Abstract: “This article summarizes and draws connections among diverse streams of theoretical and empirical research on the economics of privacy. We focus on the economic value and consequences of protecting and disclosing personal information, and on consumers’ understanding and decisions regarding the trade-offs associated with the privacy and the sharing of personal data. We highlight how the economic analysis of privacy evolved over time, as advancements in information technology raised increasingly nuanced and complex issues associated with the protection and sharing of personal information. We find and highlight three themes that connect diverse insights from the literature. First, characterizing a single unifying economic theory of privacy is hard, because privacy issues of economic relevance arise in widely diverse contexts. Second, there are theoretical and empirical situations where the protection of privacy can both enhance, and detract from, individual and societal welfare. Third, in digital economies, consumers’ ability to make informed decisions about their privacy is severely hindered, because consumers are often in a position of imperfect or asymmetric information regarding when their data is collected, for what purposes, and with what consequences. We conclude the article by highlighting some of the ongoing issues in the privacy debate of interest to economists.”
About The Author
Chloe Reichel
Articles on Online privacy
Displaying 1 - 20 of 263 articles.

Online child safety laws could help or hurt – 2 pediatricians explain what’s likely to work and what isn’t
Megan Moreno , University of Wisconsin-Madison and Jenny Radesky , University of Michigan

Canada should not fall behind on implementing safety measures for children online
Azfar Adib , Concordia University

Family vlogs can entertain, empower and exploit
Rebecca Hall , Queen's University, Ontario and Christina Pilgrim , Queen's University, Ontario

The UK just passed an online safety law that could make people less safe
Benjamin Dowling , University of Sheffield

Fear trumps anger when it comes to data breaches – angry customers vent, but fearful customers don’t come back
Rajendran Murthy , Rochester Institute of Technology

A TikTok ban isn’t a data security solution. It will be difficult to enforce – and could end up hurting users
Milovan Savic , Swinburne University of Technology

Consumer Privacy Protection Act could lead to fines for deceptive designs in apps and websites
Jonathan Obar , York University, Canada

Should you pay for Meta’s and Twitter’s verified identity subscriptions? A social media researcher explains how the choice you face affects everyone else
Anjana Susarla , Michigan State University

Protecting privacy online begins with tackling ‘digital resignation’
Meiling Fong , Concordia University and Zeynep Arsel , Concordia University

Dozens of US schools, universities move to ban TikTok
Nir Kshetri , University of North Carolina – Greensboro

Even if TikTok and other apps are collecting your data, what are the actual consequences?
Ausma Bernot , Griffith University


Browser cookies make people more cautious online, study finds
Elizabeth Stoycheff , Wayne State University

Insurance firms can skim your online data to price your insurance — and there’s little in the law to stop this
Zofia Bednarz , University of Sydney ; Kayleen Manwaring , UNSW Sydney , and Kimberlee Weatherall , University of Sydney

ACCC says consumers need more choices about what online marketplaces are doing with their data
Katharine Kemp , UNSW Sydney

Mandatory logins for ABC iview could open an intimate window onto your life
Michael Cowling , CQUniversity Australia

A new proposed privacy code promises tough rules and $10 million penalties for tech giants
Katharine Kemp , UNSW Sydney and Graham Greenleaf , UNSW Sydney

How one simple rule change could curb online retailers’ snooping on you

Is your phone really listening to your conversations? Well, turns out it doesn’t have to
Dana Rezazadegan , Swinburne University of Technology

ACIC thinks there are no legitimate uses of encryption. They’re wrong, and here’s why it matters
Gernot Heiser , UNSW Sydney ; Lyria Bennett Moses , UNSW Sydney , and Vanessa Teague , Australian National University

Apple’s new ‘app tracking transparency’ has angered Facebook. How does it work, what’s all the fuss about, and should you use it?
Paul Haskell-Dowland , Edith Cowan University and Nikolai Hampton , Edith Cowan University
Related Topics
- Cybersecurity
- Data privacy
- Digital economy
- Digital privacy
- Privacy law
- Social media
- Surveillance
Top contributors
Professor of Cybersecurity, School of Computer Science and Informatics, De Montfort University
Associate Professor, Faculty of Law & Justice, UNSW Sydney
Associate Professor, School of Law, University of Canberra
Head, The Cyber Academy, Edinburgh Napier University
Director of UWA Centre for Software Practice, The University of Western Australia
Associate Professor in Telecommunications Engineering, Swinburne University of Technology
Senior Lecturer, Communications and Media Studies, Monash University
Senior Lecturer in Technology, The Open University
Professor of Global Politics and Cybersecurity, UCL
Professor specialising in Internet law, Bond University
Survey Research Fellow, Oxford Internet Institute, University of Oxford
Professor of Internet Studies, Curtin University
Senior Lecturer in Networking, The Open University
Dean of Global Business, The Fletcher School, Tufts University
Professor of Global Media and Politics, Goldsmiths, University of London
- X (Twitter)
- Unfollow topic Follow topic
Internet Privacy - Essay Examples And Topic Ideas For Free
Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online tracking, the impact of laws and regulations on privacy, or the ways in which individuals and organizations can protect privacy online. They might also explore the ethical, social, and political implications of privacy in the digital age, or the tensions between privacy, security, and convenience online. A substantial compilation of free essay instances related to Internet Privacy you can find at PapersOwl Website. You can use our samples for inspiration to write your own essay, research paper, or just to explore a new topic for yourself.
Impact of Technology on Privacy
The 21st Century is characterized by the heavy impact technology has on us as a society while it continues to develop new devices and modernize technology. Millions of individuals around the world are now connected digitally, in other words, people globally rely heavily on smartphones tablets, and/ or computers that store or save a majority of their personal information. Critical and extremely personal data is available and collected in these smart technology such as credit card details, fingerprint layout, and […]
A World Without Internet
On the street is the 21st century. Almost all people on our planet have access to the Internet. And they are actively using it. But they forget that they use it almost around the clock. From watching the weather in the morning to texting on social media in the evening. Instead of writing an essay by hand, a modern student simply downloads it. People on the Internet are already looking for work, pay for housing and communal services, participate in […]
Positive and Negative Effects of Internet
The topic of the pros and cons of the Internet is one of the most controversial topics. People often cannot give a definite answer to it. The topic of the Internet is quite versatile. Let's look at it from the positive side first. The Internet is the greatest invention of mankind, which made life easier and continues to do it for us hundreds of times. Its first plus is, of course, the available information. Now you can find out any […]
We will write an essay sample crafted to your needs.
Security Versus Freedom?
Welcome to the Digital Age. In today’s connected world, we are living much of our live online. As a result, companies everywhere are creating large storehouses of data on all of us. The most obvious information being collected is social media data. Everything we post publicly and some cases privately, is being stored and analysed. But it is not just social media, there is now a digital record of everything we buy, everything we watch, where we go and what […]
Internet Access Restrictions May Vary
Fantastic. In most instances, they are placed on search quarries and are most prominent at education centers. This is simply to keep minds safe from content unsuitable for most ages (Gonchar). Although this is an effective plan with good intentions, it can become more effective by being enforced on younger ages rather than those who have already been exposed to the negative side of the internet. As you enter high school you have nearly done and seen everything there […]
Securing Cyberspace: Crafting Tomorrow’s Internet Privacy Laws
In an era where digital footprints shape our daily lives, the quest to safeguard personal privacy in the vast expanse of the internet has become more critical than ever before. Transitioning from the pixels that construct our online world to the intricate policies governing its boundaries signifies a pivotal juncture in the evolution of digital governance. As we navigate through this landscape of data, the formulation of robust internet privacy legislation emerges as a beacon of protection against the perils […]
Silent Struggle: Assessing Threats to Internet Privacy and Security
In today's digital age, the internet serves as the cornerstone of modern communication, commerce, and entertainment. However, amidst the convenience and connectivity it offers, lurks a pervasive and often invisible battle for privacy and security. From data breaches to surveillance, the threats to our online well-being are manifold and ever-evolving. One of the most concerning threats is the rampant collection and misuse of personal data by corporations and governments alike. Every click, search, and purchase leaves a digital footprint, eagerly […]
Safeguarding Cyberspace: the Vital Role of AI in Preserving Online Privacy
In an era where our digital footprints grow larger with every click, the question of how to protect our online privacy becomes increasingly pertinent. Enter Artificial Intelligence, our modern-day guardians in the complex realm of cyberspace. Far beyond mere machines crunching numbers, AI has evolved into a formidable force in the fight against privacy breaches. The first and foremost duty of AI guardians is to fortify our virtual boundaries. Picture them as vigilant sentinels stationed at the gates of our […]
Preserving Digital Integrity: a Scholarly Evaluation of Internet Privacy
In the contemporary digital epoch, where the internet serves as an omnipotent conduit for global interaction, commerce, and information dissemination, the concept of cyber privacy emerges as a pivotal concern. As an academic critic, entrusted with scrutinizing the intricacies of cyber privacy, it becomes essential to unravel the diverse facets of this intricate matter, ranging from its legal and ethical dimensions to its societal and technological reverberations. Cyber privacy fundamentally entails the right of individuals to govern their personal information […]
Additional Example Essays
- Positive Effects of Social Media
- Instagram and body dysmorphia
- The Negative Effects of Social Media On Mental Health
- The Mental Health Stigma
- How the Roles of Women and Men Were Portrayed in "A Doll's House"
- Psychiatric Nurse Practitioner
- Substance Abuse and Mental Illnesses
- Importance Of Accountability
- Are Electric Cars Better Than Petrol Diesel Cars?
- "A Doll's House" as a Modern Tragedy
- Poems “The Negro Speaks of Rivers” and “Still I Rise”
- The Unique Use of Literary Devices in The Tell-Tale Heart
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
- Galileo Galilei: sample essay
- Kids and violence: sample essay
- Sample essay about Muhammad Ali
- Learning for adults: essay sample
- Breast cancer: sample essay
- Ulysses S. Grant: essay sample
- Sample essay about muckrakers
- Teen pragnency: essay sample
- Sample essay aabout a soul
- Paper sample about happiness
- Schizophrenia: essay sample
- Essay example about death penalty
- Sample paper about corruption
- Gender on business: sample essay
- Mozart: essay sample
- An essay sample on Illicit traffic in drugs
- Analyzing the generation gap
- Pit bulls and fighting
- Reasons for a belief in God
- Italian dessert Tiramisu
- Terrorism in Pakistan
- Lives on the boundary
- History of fingerprints
- If I were Lyndon Johnson
- The Western expansion
- Workplace violence
- Compare & contrast paper ideas
- College cause and effect essay topics
- Good descriptive paper topics
- GED paper topics
- Catchy essay paper topics
- Capital punishment essay topics
- Ideas for your descriptive paper
- Choosing topics for a law paper
- Death of a Salesman essay ideas
- Huckleberry Finn: argument paper topics
- College persuasive essay topic ideas
- Unique illustration essay topic prompts
- Topics for an essay on Nicholas Sparks
- Business cause and effect essay topics
- Informative essay topic ideas
- Choosing topics for a profile essay
- Argumentative essay topics on politics
- Selecting paper topics about the military
- Process analysis essay topics
- College essay topics in accounting
- Ideas about violent video games
- Argumentative paper topic suggestions
- Offbeat topic ideas on Macbeth
- Essay prompts on Streetcar Named Desire
- Selection of topics about Dorian Gray
- Argumentative essay ideas on bullying
- 23 topics on a Midsummer Night’s Dream
- Essay ideas on yourself in 10 years
- Choosing topics about global warming
- Environmental science essay prompts
- Argumentative essay ideas on psychology
- Picking topics about religion & belief
- Best essay ideas on euthanasia
- Writing service
- Essay on a book
- Writing companies
writing rogue
Acute essay topics on internet privacy: 20 expert suggestions.
Internet privacy is a very important topic nowadays. Many people are afraid that they’re watched by the government through the Internet and these suspicions aren’t always baseless. If your teacher assigned you to write an essay on Internet privacy, there are many narrow topics that you may choose from.
Topics on Internet Privacy
- The history of Internet privacy.
- Levels of Internet privacy.
- Risks to Internet privacy.
- Internet privacy and HTTP cookies.
- Device fingerprinting and Internet privacy.
- Photos in social networks and Internet privacy.
- Search engines and Internet privacy.
- Reducing the risks to Internet privacy.
- Real life implications related to Internet privacy.
- Global policies about Internet privacy.
- User-generated content and Internet privacy costs.
- Internet privacy and social media.
- Effects of privacy seals and warnings on online privacy behavior.
- Damages for Internet privacy violations.
- Internet privacy and politics.
- The installment of malware on your computer by major companies.
- The lack of regulation in Internet privacy.
- Internet privacy and intellectual property.
- Weak passwords and Internet privacy.
- The future of Internet privacy.
Writing an Essay
A good topic isn’t enough to get an excellent mark for your work. You should conduct thorough research and present your points or arguments properly. Ask your teacher about sources that you should use to succeed. Acquire these sources and find there, at least, three points that can support your main idea. It’s important to defend your statements using factual evidence rather than just your opinion. Before you start writing your paper, it’s advisable to make a good outline. This will help you structure your text properly. Compose your essay using appropriate writing techniques and transitions between paragraphs to make your text flow smoothly. Proofread your paper to eliminate errors made during the process of writing. Come up with your title after your paper has been complete to make it 100% relevant to the text.
Getting Help
If you aren’t sure that you’ll be able to write an impressive paper by yourself, you should ask other people to help you. If you cannot spend money on this, just regularly visit your instructor and ask them to consult you about your next steps. If you can pay for assistance, you may hire a professional tutor who will teach you how to deal with academic assignments. You may also contact essay writing companies to compose papers for you in exchange for payment. Services of professional agencies won’t disappoint you.
Writing Ideas
- Personal statement writing guide
- Boosting geography essay writing skills
- Literary essay about Animal Farm
- Document based question essay
- How to settle down with a good service
- Writing about Tommy Hilfiger
- Paper writing help: disadvantages
- Looking for a cheap custom essay
- Writing a literary essay conclusion
- Informative explanatory essay
- Essay about school environment
Writing help
Popular essay writing service for generation Z - Zessay.com - very quality service and nice website.
Hints for beginners
- Ways to improve your grades
- Pay someone to write my paper
- Free pesuasive paper
- Life without technology paper
- Finding trusted paper writing help
- Long essay about summer vacation
- Finding a paper sample about market
- Pros and cons of writing services
- Where to buy cheap papers?
- How to complete an IB literary essay
Paper topics
- Persuasive essay topics for 5th grade
- High school paper ideas
- Choosing definition essay topics
- Informative essay topics on caffeine
- Medical argumentative essay topics
- Picking topics related to entertainment
- Essay topics on Scottish independence
- Good ideas about Internet privacy
May 28, 2024 © WritingRogue.com. | Developing Strong Writing Habits For Students

Choose Your Test
Sat / act prep online guides and tips, 113 great research paper topics.
General Education

One of the hardest parts of writing a research paper can be just finding a good topic to write about. Fortunately we've done the hard work for you and have compiled a list of 113 interesting research paper topics. They've been organized into ten categories and cover a wide range of subjects so you can easily find the best topic for you.
In addition to the list of good research topics, we've included advice on what makes a good research paper topic and how you can use your topic to start writing a great paper.
What Makes a Good Research Paper Topic?
Not all research paper topics are created equal, and you want to make sure you choose a great topic before you start writing. Below are the three most important factors to consider to make sure you choose the best research paper topics.
#1: It's Something You're Interested In
A paper is always easier to write if you're interested in the topic, and you'll be more motivated to do in-depth research and write a paper that really covers the entire subject. Even if a certain research paper topic is getting a lot of buzz right now or other people seem interested in writing about it, don't feel tempted to make it your topic unless you genuinely have some sort of interest in it as well.
#2: There's Enough Information to Write a Paper
Even if you come up with the absolute best research paper topic and you're so excited to write about it, you won't be able to produce a good paper if there isn't enough research about the topic. This can happen for very specific or specialized topics, as well as topics that are too new to have enough research done on them at the moment. Easy research paper topics will always be topics with enough information to write a full-length paper.
Trying to write a research paper on a topic that doesn't have much research on it is incredibly hard, so before you decide on a topic, do a bit of preliminary searching and make sure you'll have all the information you need to write your paper.
#3: It Fits Your Teacher's Guidelines
Don't get so carried away looking at lists of research paper topics that you forget any requirements or restrictions your teacher may have put on research topic ideas. If you're writing a research paper on a health-related topic, deciding to write about the impact of rap on the music scene probably won't be allowed, but there may be some sort of leeway. For example, if you're really interested in current events but your teacher wants you to write a research paper on a history topic, you may be able to choose a topic that fits both categories, like exploring the relationship between the US and North Korea. No matter what, always get your research paper topic approved by your teacher first before you begin writing.
113 Good Research Paper Topics
Below are 113 good research topics to help you get you started on your paper. We've organized them into ten categories to make it easier to find the type of research paper topics you're looking for.
Arts/Culture
- Discuss the main differences in art from the Italian Renaissance and the Northern Renaissance .
- Analyze the impact a famous artist had on the world.
- How is sexism portrayed in different types of media (music, film, video games, etc.)? Has the amount/type of sexism changed over the years?
- How has the music of slaves brought over from Africa shaped modern American music?
- How has rap music evolved in the past decade?
- How has the portrayal of minorities in the media changed?

Current Events
- What have been the impacts of China's one child policy?
- How have the goals of feminists changed over the decades?
- How has the Trump presidency changed international relations?
- Analyze the history of the relationship between the United States and North Korea.
- What factors contributed to the current decline in the rate of unemployment?
- What have been the impacts of states which have increased their minimum wage?
- How do US immigration laws compare to immigration laws of other countries?
- How have the US's immigration laws changed in the past few years/decades?
- How has the Black Lives Matter movement affected discussions and view about racism in the US?
- What impact has the Affordable Care Act had on healthcare in the US?
- What factors contributed to the UK deciding to leave the EU (Brexit)?
- What factors contributed to China becoming an economic power?
- Discuss the history of Bitcoin or other cryptocurrencies (some of which tokenize the S&P 500 Index on the blockchain) .
- Do students in schools that eliminate grades do better in college and their careers?
- Do students from wealthier backgrounds score higher on standardized tests?
- Do students who receive free meals at school get higher grades compared to when they weren't receiving a free meal?
- Do students who attend charter schools score higher on standardized tests than students in public schools?
- Do students learn better in same-sex classrooms?
- How does giving each student access to an iPad or laptop affect their studies?
- What are the benefits and drawbacks of the Montessori Method ?
- Do children who attend preschool do better in school later on?
- What was the impact of the No Child Left Behind act?
- How does the US education system compare to education systems in other countries?
- What impact does mandatory physical education classes have on students' health?
- Which methods are most effective at reducing bullying in schools?
- Do homeschoolers who attend college do as well as students who attended traditional schools?
- Does offering tenure increase or decrease quality of teaching?
- How does college debt affect future life choices of students?
- Should graduate students be able to form unions?

- What are different ways to lower gun-related deaths in the US?
- How and why have divorce rates changed over time?
- Is affirmative action still necessary in education and/or the workplace?
- Should physician-assisted suicide be legal?
- How has stem cell research impacted the medical field?
- How can human trafficking be reduced in the United States/world?
- Should people be able to donate organs in exchange for money?
- Which types of juvenile punishment have proven most effective at preventing future crimes?
- Has the increase in US airport security made passengers safer?
- Analyze the immigration policies of certain countries and how they are similar and different from one another.
- Several states have legalized recreational marijuana. What positive and negative impacts have they experienced as a result?
- Do tariffs increase the number of domestic jobs?
- Which prison reforms have proven most effective?
- Should governments be able to censor certain information on the internet?
- Which methods/programs have been most effective at reducing teen pregnancy?
- What are the benefits and drawbacks of the Keto diet?
- How effective are different exercise regimes for losing weight and maintaining weight loss?
- How do the healthcare plans of various countries differ from each other?
- What are the most effective ways to treat depression ?
- What are the pros and cons of genetically modified foods?
- Which methods are most effective for improving memory?
- What can be done to lower healthcare costs in the US?
- What factors contributed to the current opioid crisis?
- Analyze the history and impact of the HIV/AIDS epidemic .
- Are low-carbohydrate or low-fat diets more effective for weight loss?
- How much exercise should the average adult be getting each week?
- Which methods are most effective to get parents to vaccinate their children?
- What are the pros and cons of clean needle programs?
- How does stress affect the body?
- Discuss the history of the conflict between Israel and the Palestinians.
- What were the causes and effects of the Salem Witch Trials?
- Who was responsible for the Iran-Contra situation?
- How has New Orleans and the government's response to natural disasters changed since Hurricane Katrina?
- What events led to the fall of the Roman Empire?
- What were the impacts of British rule in India ?
- Was the atomic bombing of Hiroshima and Nagasaki necessary?
- What were the successes and failures of the women's suffrage movement in the United States?
- What were the causes of the Civil War?
- How did Abraham Lincoln's assassination impact the country and reconstruction after the Civil War?
- Which factors contributed to the colonies winning the American Revolution?
- What caused Hitler's rise to power?
- Discuss how a specific invention impacted history.
- What led to Cleopatra's fall as ruler of Egypt?
- How has Japan changed and evolved over the centuries?
- What were the causes of the Rwandan genocide ?

- Why did Martin Luther decide to split with the Catholic Church?
- Analyze the history and impact of a well-known cult (Jonestown, Manson family, etc.)
- How did the sexual abuse scandal impact how people view the Catholic Church?
- How has the Catholic church's power changed over the past decades/centuries?
- What are the causes behind the rise in atheism/ agnosticism in the United States?
- What were the influences in Siddhartha's life resulted in him becoming the Buddha?
- How has media portrayal of Islam/Muslims changed since September 11th?
Science/Environment
- How has the earth's climate changed in the past few decades?
- How has the use and elimination of DDT affected bird populations in the US?
- Analyze how the number and severity of natural disasters have increased in the past few decades.
- Analyze deforestation rates in a certain area or globally over a period of time.
- How have past oil spills changed regulations and cleanup methods?
- How has the Flint water crisis changed water regulation safety?
- What are the pros and cons of fracking?
- What impact has the Paris Climate Agreement had so far?
- What have NASA's biggest successes and failures been?
- How can we improve access to clean water around the world?
- Does ecotourism actually have a positive impact on the environment?
- Should the US rely on nuclear energy more?
- What can be done to save amphibian species currently at risk of extinction?
- What impact has climate change had on coral reefs?
- How are black holes created?
- Are teens who spend more time on social media more likely to suffer anxiety and/or depression?
- How will the loss of net neutrality affect internet users?
- Analyze the history and progress of self-driving vehicles.
- How has the use of drones changed surveillance and warfare methods?
- Has social media made people more or less connected?
- What progress has currently been made with artificial intelligence ?
- Do smartphones increase or decrease workplace productivity?
- What are the most effective ways to use technology in the classroom?
- How is Google search affecting our intelligence?
- When is the best age for a child to begin owning a smartphone?
- Has frequent texting reduced teen literacy rates?

How to Write a Great Research Paper
Even great research paper topics won't give you a great research paper if you don't hone your topic before and during the writing process. Follow these three tips to turn good research paper topics into great papers.
#1: Figure Out Your Thesis Early
Before you start writing a single word of your paper, you first need to know what your thesis will be. Your thesis is a statement that explains what you intend to prove/show in your paper. Every sentence in your research paper will relate back to your thesis, so you don't want to start writing without it!
As some examples, if you're writing a research paper on if students learn better in same-sex classrooms, your thesis might be "Research has shown that elementary-age students in same-sex classrooms score higher on standardized tests and report feeling more comfortable in the classroom."
If you're writing a paper on the causes of the Civil War, your thesis might be "While the dispute between the North and South over slavery is the most well-known cause of the Civil War, other key causes include differences in the economies of the North and South, states' rights, and territorial expansion."
#2: Back Every Statement Up With Research
Remember, this is a research paper you're writing, so you'll need to use lots of research to make your points. Every statement you give must be backed up with research, properly cited the way your teacher requested. You're allowed to include opinions of your own, but they must also be supported by the research you give.
#3: Do Your Research Before You Begin Writing
You don't want to start writing your research paper and then learn that there isn't enough research to back up the points you're making, or, even worse, that the research contradicts the points you're trying to make!
Get most of your research on your good research topics done before you begin writing. Then use the research you've collected to create a rough outline of what your paper will cover and the key points you're going to make. This will help keep your paper clear and organized, and it'll ensure you have enough research to produce a strong paper.
What's Next?
Are you also learning about dynamic equilibrium in your science class? We break this sometimes tricky concept down so it's easy to understand in our complete guide to dynamic equilibrium .
Thinking about becoming a nurse practitioner? Nurse practitioners have one of the fastest growing careers in the country, and we have all the information you need to know about what to expect from nurse practitioner school .
Want to know the fastest and easiest ways to convert between Fahrenheit and Celsius? We've got you covered! Check out our guide to the best ways to convert Celsius to Fahrenheit (or vice versa).
These recommendations are based solely on our knowledge and experience. If you purchase an item through one of our links, PrepScholar may receive a commission.

Christine graduated from Michigan State University with degrees in Environmental Biology and Geography and received her Master's from Duke University. In high school she scored in the 99th percentile on the SAT and was named a National Merit Finalist. She has taught English and biology in several countries.
Ask a Question Below
Have any questions about this article or other topics? Ask below and we'll reply!
Improve With Our Famous Guides
- For All Students
The 5 Strategies You Must Be Using to Improve 160+ SAT Points
How to Get a Perfect 1600, by a Perfect Scorer
Series: How to Get 800 on Each SAT Section:
Score 800 on SAT Math
Score 800 on SAT Reading
Score 800 on SAT Writing
Series: How to Get to 600 on Each SAT Section:
Score 600 on SAT Math
Score 600 on SAT Reading
Score 600 on SAT Writing
Free Complete Official SAT Practice Tests
What SAT Target Score Should You Be Aiming For?
15 Strategies to Improve Your SAT Essay
The 5 Strategies You Must Be Using to Improve 4+ ACT Points
How to Get a Perfect 36 ACT, by a Perfect Scorer
Series: How to Get 36 on Each ACT Section:
36 on ACT English
36 on ACT Math
36 on ACT Reading
36 on ACT Science
Series: How to Get to 24 on Each ACT Section:
24 on ACT English
24 on ACT Math
24 on ACT Reading
24 on ACT Science
What ACT target score should you be aiming for?
ACT Vocabulary You Must Know
ACT Writing: 15 Tips to Raise Your Essay Score
How to Get Into Harvard and the Ivy League
How to Get a Perfect 4.0 GPA
How to Write an Amazing College Essay
What Exactly Are Colleges Looking For?
Is the ACT easier than the SAT? A Comprehensive Guide
Should you retake your SAT or ACT?
When should you take the SAT or ACT?
Stay Informed
Get the latest articles and test prep tips!
Looking for Graduate School Test Prep?
Check out our top-rated graduate blogs here:
GRE Online Prep Blog
GMAT Online Prep Blog
TOEFL Online Prep Blog
Holly R. "I am absolutely overjoyed and cannot thank you enough for helping me!”

COMMENTS
The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information.
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
With the increasing amount of personal information being shared online, it's important to understand the different aspects of internet privacy and how it can impact our daily lives. To help you navigate this complex topic, we've compiled a list of 112 internet privacy essay topic ideas and examples to inspire your writing.
The share of Americans who say they are very or somewhat concerned about government use of people's data has increased from 64% in 2019 to 71% today. Two-thirds (67%) of adults say they understand little to nothing about what companies are doing with their personal data, up from 59%. reportAug 17, 2023.
Given the ubiquity of personal information and online behavior collected, one of the biggest challenges facing firms is large-scale data breaches where a significant amount of data is either accidentally or deliberately released to external parties (Goode et al., 2017).In light of the recent scandals such as security breaches by Cambridge Analytica, there is a growing concern about social ...
This paper takes as a starting point a recent development in privacy-debates: the emphasis on social and institutional environments in the definition and the defence of privacy. Recognizing the merits of this approach I supplement it in two respects. First, an analysis of the relation between privacy and autonomy teaches that in the digital age more than ever individual autonomy is threatened ...
1. Views of data privacy risks, personal data and digital privacy laws. Online privacy is complex, encompassing debates over law enforcement's data access, government regulation and what information companies can collect. This chapter examines Americans' perspectives on these issues and highlights how views vary across different groups ...
INTERNET PRIV ACY IN 2020. MICHAEL IHEANYICHUKWU GODWIN ONUGHA (S5230136) Computing Department, Bournemouth University. Fern Barrow, Poole, BH12 5BB, United Kingdom. [email protected] ...
While many Internet users are unaware how cookies function and the potential harm cookies may cause, for others, cookies are the source of multiple privacy concerns. This paper will define cookies, describe cookie types, describe privacy risks associated with cookies, describe laws and compliance requirements associated with cookies, and ...
The first two concepts relate to digital literacy. This can be defined in many ways but is widely agreed upon as critical in today's world - including for technical, daunting topics like managing online privacy. 4 The third relates to an ongoing debate: Whether the "privacy paradox" exists. We walk through each of these below. Knowledge
When writing an essay on internet privacy, it is important to research and gather relevant information from credible sources. This may include academic journals, government reports, and reputable news outlets. It is also important to consider different perspectives and arguments on the topic to provide a well-rounded and comprehensive analysis.
This paper provides an interdisciplinary review of privacy-related. research in order to enable a more cohesive treatm ent. With a sample of 320 privacy articles and 128 books. and book sections ...
National Bureau of Economic Research working paper, 2018. DOI: 10.3386/w24253. Summary: This paper looks at the risks big data poses to consumer privacy. The author describes the causes and consequences of data breaches and the ways in which technological tools can be used for data misuse. She then explores the interaction between privacy risks ...
A new proposed privacy code promises tough rules and $10 million penalties for tech giants. Katharine Kemp, UNSW Sydney and Graham Greenleaf, UNSW Sydney. A proposed online privacy code would give ...
After learning about the information that has come to light, students need the opportunity to explore their own thoughts and feelings on this important issue. These 50 new journal prompts offer students the chance to think about their own right to privacy, the government's motives for surveillance, and the ramifications of wide-scale public ...
9 essay samples found. Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online ...
Internet privacy and HTTP cookies. Device fingerprinting and Internet privacy. Photos in social networks and Internet privacy. Search engines and Internet privacy. Reducing the risks to Internet privacy. Real life implications related to Internet privacy. Global policies about Internet privacy.
The Internet has become a great tool that is used almost by every person in the world. It changed the way how people live. With surfing the web, people share data about themselves.
113 Great Research Paper Topics. One of the hardest parts of writing a research paper can be just finding a good topic to write about. Fortunately we've done the hard work for you and have compiled a list of 113 interesting research paper topics. They've been organized into ten categories and cover a wide range of subjects so you can easily ...
The most challenging part of writing a paper is often coming up with the initial idea. To help you get started, here are numerous research paper ideas that can inspire you, and enable you to draft a paper with a fresh perspective. The ideas are categorized into fields of study or areas of interest, so you can explore a new angle in your ...
NIAID's biodefense and emerging infectious disease pathogen list is periodically reviewed and is subject to revision in conjunction with our federal partners, including the U.S. Department of Homeland Security, which determines threat assessments, and the Centers for Disease Control and Prevention, which is responsible for responding to emerging pathogen threats in the United States.
Don't miss us this week at Microsoft Build in Seattle and online, May 21-23, 2024, to learn more and chat about creating copilots from SharePoint and other AI innovations we're bringing to our maker community. • KEY01: Opening keynote with Satya Nadella, Kevin Scott, Rajesh Jha, and me.