Cybersecurity Guide

From scholar to expert: Cybersecurity PhD options
In this guide
- Industry demand
- 2024 rankings
- Preparation
- Considerations
- School listings
The cybersecurity landscape is not just growing—it’s evolving at a breakneck pace. And what better way to stay ahead of the curve than by pursuing a PhD in cybersecurity?
This advanced degree is no longer confined to the realm of computer science. Today, it branches into diverse fields like law, policy, management, and strategy, reflecting the multifaceted nature of modern cyber threats.
If you’re looking to become a thought leader in this dynamic industry, a PhD in cybersecurity offers an unparalleled opportunity to deepen your expertise and broaden your horizons.
This guide is designed to give prospective cybersecurity PhD students a general overview of available cybersecurity PhD programs. It will also outline some of the factors to consider when trying to find the right PhD program fit, such as course requirements and tuition costs.
Industry demand for PhDs in cybersecurity
Like other cutting-edge technology fields, until recently, cybersecurity PhD programs were often training grounds for niche positions and specialized research, often for government agencies (like the CIA, NSA, and FBI), or closely adjacent research organizations or institutions.
Today, however, as the cybersecurity field grows to become more pervasive and consumer-oriented, there are opportunities for cybersecurity PhDs to work at public-facing companies like startups and name-brand financial, software, infrastructure, and digital service firms.
One trend that is emerging in the cybersecurity field is that cybersecurity experts need to be well-versed in a variety of growing threats. If recent headlines about cybersecurity breaches are any indication, there are a number of new attack vectors and opportunities for cybercrime and related issues. Historically, committing cybercrime took resources and a level of sophistication that required specialized training or skill.
But now, because of the pervasiveness of the internet, committing cybercrime is becoming more commonplace. So training in a cybersecurity PhD program allows students to become an experts in one part of a growing and multi-layered field.
In fact, this trend of needing well-trained, but adaptable cybersecurity professionals is reflected by the move by cybersecurity graduate schools to offer specialized master’s degrees , and many companies and professional organizations offer certifications in cybersecurity that focus on particular issues related to cybersecurity technology, cybersecurity law , digital forensics , policy, or related topics.
That said, traditional research-oriented cybersecurity positions continue to be in demand in academia and elsewhere — a trend that will likely continue.
One interesting facet of the cybersecurity field is trying to predict what future cybersecurity threats might look like and then develop tools and systems to protect against those threats.
As new technologies and services are developed and as more of the global population begins using Internet services for everything from healthcare to banking — new ways of protecting those services will be required. Often, it’s up to academic researchers to think ahead and examine various threats and opportunities to insulate against those threats.
Another key trend coming out of academic circles is that cybersecurity students are becoming increasingly multidisciplinary.
As cybersecurity hacks impact more parts of people’s everyday lives, so too do the academic programs that are designed to prepare the next generation of cybersecurity professionals. This emerging trend creates an enormous amount of opportunity for students who have a variety of interests and who are looking to create a non-traditional career path.
The best cybersecurity PhD programs for 2024
Capella university, georgia institute of technology, northeastern university, marymount university, school of technology and innovation, nova southeastern university, college of computing & engineering, purdue university, stevens institute of technology, worcester polytechnic institute, university of illinois at urbana-champaign, mississippi state university, new york institute of technology.
These rankings were compiled from data accessed in November 2023 from the Integrated Post-Secondary Education Data System (IPEDS) and College Navigator (both services National Center for Education Statistics). Tuition data was pulled from individual university websites and is current as of November 2023.
What is required to get a PhD in cybersecurity?
Good news first: Obtaining a PhD in a field related to cybersecurity will likely create tremendous employment opportunities and lead to interesting and dynamic career options.
Bad news: Getting a PhD requires a lot of investment of time and energy, and comes with a big opportunity cost (meaning you have to invest four to five years, or longer, or pursue other opportunities to obtain a doctoral degree.
Here’s a quick breakdown of what is required to get a PhD in cybersecurity. Of course, specific degree requirements will vary by program. One growing trend in the field is that students can now obtain degrees in a variety of formats, including traditional on-campus programs, online degree programs , and hybrid graduate degree programs that combine both on-campus learning with online learning.
Related resources
- Online PhD in cybersecurity – A guide to finding the right program
- Cybersecurity degree programs
- Podcast episodes and expert interviews
Preparing for a cybersecurity doctorate program
Cybersecurity is a relatively new formalized technology field, nonetheless, there are several ways that students or prospective PhD candidates can get involved or explore the field before and during a graduate school program. A few examples of ways to start networking and finding opportunities include:
Join cybersecurity organizations with professional networks
Specialized professional organizations are a good place to find the latest in career advice and guidance. Often they publish newsletters or other kinds of information that provide insights into the emerging trends and issues facing cybersecurity professionals. A couple of examples include:
The Center for Internet Security (CIS) is a non-profit dedicated to training cybersecurity professionals and fostering a sense of collaboration. The organization also publishes information and analysis of the latest cybersecurity threats and issues facing the professional community.
The SANS Institute runs several different kinds of courses for students (including certification programs) as well as ongoing professional cybersecurity education and training for people working in the field. The organization has several options including webinars, online training, and live in-person seminars. Additionally, SANS also publishes newsletters and maintains forums for cybersecurity professionals to interact and share information.
Leverage your social network
Places like LinkedIn and Twitter are good places to start to find news and information about what is happening in the field, who the main leaders and influencers are, and what kinds of jobs and opportunities are available.
Starting a professional network early is also a great opportunity. Often professionals and members of the industry are willing to provide guidance and help to students who are genuinely interested in the field and looking for career opportunities.
Cybersecurity competitions
Cybersecurity competitions are a great way to get hands-on experience working on real cybersecurity problems and issues. As a PhD student or prospective student, cybersecurity competitions that are sponsored by industry groups are a great way to meet other cybersecurity professionals while getting working on projects that will help flesh out a resume or become talking points in later job interviews.
The US Cyber Challenge , for example, is a series of competitions and hackathon-style events hosted by the Department of Homeland Security Science and Technology Directorate and the Center for Internet Security to prepare the next generation of cybersecurity professionals.
Internships
Internships also continue to be a tried and true way to gain professional experience. Internships in technical fields like cybersecurity can also pay well. Like the industry itself, cybersecurity internships are available across a wide range of industries and can range from academic research-oriented to more corporate kinds of work.
Things to consider when choosing a cybersecurity PhD program
There are many considerations to evaluate when considering any kind of graduate degree, but proper planning is essential to be able to obtain a doctoral degree. It’s also important to note that these are just guidelines and that each graduate program will have specific requirements, so be sure to double-check.
What you will need before applying to a cybersecurity PhD program:
- All undergraduate and graduate transcripts
- A statement of intent, which is like a cover letter outlining interest
- Letters of reference
- Application fee
- Online application
- A resume or CV outlining professional and academic accomplishments
What does a cybersecurity PhD program cost?
Obtaining a PhD is a massive investment, both in terms of time and money. Cybersecurity PhD students are weighing the cost of becoming an expert in the field with the payoff of having interesting and potentially lucrative career opportunities on the other side.
Degree requirements are usually satisfied in 60-75 hours, so the cost of a doctoral degree can be well into the six-figure range. Here’s a more specific breakdown:
Tuition rates
The Cybersecurity Guide research team looked at 26 programs that offer a cybersecurity-related PhD degree. Here’s a breakdown of tuition rates (all figures are based on out-of-state tuition).
$17,580 is the most affordable PhD program option and it is available at the Georgia Institute of Technology.
$86,833 is the average cost of a cybersecurity PhD and is based on tuition rates from all 26 schools.
$197,820 is the most expensive cybersecurity PhD program and is available at Indiana University Bloomington.
The good news is that by the time students get to the PhD level there are a lot of funding options — including some graduate programs that are completely funded by the university or academic departments themselves.
Additionally, funding in the form of research grants and other kinds of scholarships is available for students interested in pursuing cybersecurity studies.
One example is the CyberCorps: Scholarships for Service program. Administered by the National Science Foundation, PhD students studying cybersecurity are eligible for a $34,000 a year scholarship, along with a professional stipend of $6,000 to attend conferences in exchange for agreeing to work for a government agency in the cybersecurity space after the PhD program.
Frequently asked questions about cybersecurity PhD programs
Most traditional and online cybersecurity graduate programs require a minimum number of credits that need to be completed to obtain a degree. On average, it takes 71 credits to graduate with a PhD in cybersecurity — far longer (almost double) than traditional master’s degree programs. In addition to coursework, most PhD students also have research and teaching responsibilities that can be simultaneously demanding and great career preparation.
At the core of a cybersecurity doctoral program is a data science doctoral program, you’ll be expected to learn many skills and also how to apply them across domains and disciplines. Core curriculums will vary from program to program, but almost all will have a core foundation of statistics.
All PhD candidates will have to take a series of exams that act as checkpoints during the lengthy PhD process. The actual exam process and timing can vary depending on the university and the program, but the basic idea is that cybersecurity PhD candidates generally have to sit for a qualifying exam, which comes earlier in the program (usually the winter or spring of the second year of study), a preliminary exam, which a candidate takes to show they are ready to start the dissertation or research portion of the PhD program, and a final exam where PhD students present and defend their research and complete their degree requirements.
A cybersecurity PhD dissertation is the capstone of a doctoral program. The dissertation is the name of a formal paper that presents the findings of original research that the PhD candidate conducted during the program under the guidance of faculty advisors. Some example cybersecurity research topics that could potentially be turned into dissertation ideas include: * Policies and best practices around passwords * Ways to defend against the rise of bots * Policies around encryption and privacy * Corporate responsibility for employee security * Internet advertising targeting and privacy * The new frontier of social engineering attacks * Operation security (OpSec) strategy and policy * Network infrastructure and defense * Cybersecurity law and policy * The vulnerabilities of biometrics * The role of ethical hacking * Cybersecurity forensics and enforcement
A complete listing of cybersecurity PhD programs
The following is a list of cybersecurity PhD programs. The listing is intended to work as a high-level index that provides enough basic information to make quick side-by-side comparisons easy.
You should find basic data about what each school requires (such as a GRE score or prior academic work) as well as the number of credits required, estimated costs, and a link to the program.
Arizona State University
- Aim: Equip students with in-depth expertise in cybersecurity.
- Study Modules: Delve into advanced computer science subjects and specific cybersecurity courses.
- Research Component: Students undertake groundbreaking research in the cybersecurity domain.
Carnegie Mellon University
- CNBC Collaboration: A joint effort between Carnegie Mellon and the University of Pittsburgh to train students in understanding the brain's role in cognition.
- Training Program: Students take four main neuroscience courses and participate in seminars and ethics training.
- Course Integration: Whether students have a B.S. or M.S. degree, they can combine the CNBC and ECE Ph.D. courses without extra workload.
Colorado School of Mines
- Research Focus: Cybersecurity: Studying online security and privacy.
- Cost and Financial Aid: Provides details on program costs and available financial support.
- Current Mines Community: Offers specific information for those already affiliated with Mines.
Indiana University Bloomington
- Focus Areas: Options include Animal Informatics, Bioinformatics, Computer Design, and more.
- Information Sessions: The university holds events to guide potential students about admissions and study options.
- Minor Requirement: All Ph.D. students must complete a minor, which can be from within the Luddy School of Informatics or from another approved school at IU Bloomington.
Iowa State University
- Details: The program is open to both domestic and international students.
- Time to Complete: Ph.D.: About 5.2 years
- Goals: Students should gain deep knowledge, follow ethics, share their findings, and do advanced research if they're writing a thesis.
- Learning Goals: Master core areas of Computer Science, achieve in-depth knowledge in a chosen subfield, obtain expertise to perform original research, and demonstrate the ability to communicate technical concepts and research results.
- Duration: Median time to earn the doctorate is 5.8 years.
- Application Information: The program is open to both domestic and international students.
- Program's Aim: The Ph.D. program is tailored to produce scholars proficient in leading research initiatives, undertaking rigorous industrial research, or imparting high-level computer science education.
- Entry Routes: The program welcomes both students holding a B.S. degree for direct admission and those with an M.S. degree.
- Dissertation's Role: It stands as the pivotal component of the Ph.D. journey. Collaboration between the student, their dissertation director, and the guiding committee is essential.
Naval Postgraduate School
- Program Essence: The Computer Science Ph.D. is a top-tier academic program in the U.S.
- Admission Criteria: Open to military officers from the U.S. and abroad, U.S. governmental employees, and staff of foreign governments.
- Curriculum: Designed to deepen knowledge in computing, with a focus on the needs of the U.S. Department of Defense.
- Emphasis on Research: The college showcases its strength in research through sections dedicated to Research Areas, affiliated Institutes & Centers, ongoing Research Projects, and specialized Labs & Groups.
- Holistic Student Growth: The college promotes a comprehensive student experience, spotlighting Clubs & Organizations, campus Facilities, and tech Systems.
- Guidance for Future Students: Provides tailored insights for students considering joining at various academic levels, from Undergraduate to PhD.
- Broad Learning: The program covers many areas, from software and policy to psychology and ethics, reflecting the wide scope of cybersecurity.
- Course Design: Students learn foundational security topics first and then dive into specialized areas, like cyber forensics.
- Successful Alumni: Past students now work in places like NASA, Amazon, and Google.
- Feature: Students can apply to up to three different campuses and/or majors using a single application and fee payment.
- Preparing for a Globalized World: Courses such as Global Supply Chain Management equip students for international careers.
- Tech-Forward Curriculum: Purdue's commitment to advanced technology is evident.
Rochester Institute of Technology
- Cyberinfrastructure Focus: The program dives deep into how hardware, data, and networks work together to create secure and efficient digital tools.
- Broad Applications: The program uses computing to solve problems in fields like science, arts, and business.
- Success Rate: All RIT graduates from this program have found relevant roles, especially in the Internet and Software sectors.
Sam Houston State University
- Program's Objective: The course aims to nurture students to be technically adept and also to take on leadership roles in the digital and cyber forensic domain across various industries.
- Assessments: Students undergo comprehensive tests to evaluate their understanding.
- Research Paper (Dissertation): Once students reach the doctoral candidacy phase, they must produce and defend a significant research paper or dissertation.
- Funding: All Ph.D. students get financial help, so they can start their research right away.
- Teachers: The program has top experts, including those who've made big discoveries in computer science.
- Research Areas: Students can study the latest topics like AI, computer vision, and online security.
The University of Tennessee
- Study Areas: Options include Cybersecurity, Data Analytics, Computer Vision, and more.
- Tests: You'll have to pass a few exams, including one when you start, one before your final project, and then present your final project.
- Courses: Some specific courses are needed, and your main professor will help decide which ones.
- Big Exam: Before moving forward, you'll take a detailed exam about your research topic.
- Final Step: You'll present and defend your research project to experts.
- Overview: This program is for those with a degree in Computer Science or similar fields. It has special focus areas like Cybersecurity and Machine Learning.
University of Arizona
- Study Plan: Students start with learning research basics and then dive into modern tech topics.
- Support for Students: All PhD students get funding that covers their studies, a stipend, and health insurance. Money for travel to conferences is also available.
- After Graduation: Alumni work at top universities and big companies like Google and Microsoft.
University of California-Davis
- About the Program: Students engage in deep research, ending with a dissertation.
- Jobs After Graduation: Roles in companies or academic positions.
- Vibrant Community: Beyond academics, students join a supportive community, enriching their Ph.D. experience.
University of Colorado - Colorado Springs
- Recognition: UCCS is recognized by the National Security Agency (NSA) and the Department of Homeland Security for excellence in Information Assurance Education.
- Course Approval: The NSA has approved UCCS's courses as meeting national security training standards.
- Overview: This program focuses on vital areas like cyber security, physical security, and homeland security.
University of Idaho
- Partnership with NSA and DHS: The university is part of a program to boost cyber defense education.
- Recognition: The University of Idaho is among the institutions recognized as Centers of Academic Excellence in Cyber Defense.
- Objective: To minimize vulnerabilities in the national information infrastructure.
- Overview: This program is meticulously crafted to deliver premier legal education to its students.
- Courses: Encompasses a balanced mix of traditional legal doctrines, theoretical viewpoints, and hands-on practical experiences.
- Aim: The primary objective is to equip students with top-notch legal education.
University of Missouri-Columbia
- Seminars: PhD students should attend 20 seminars. If they were previously Master's students, their past attendance counts.
- Timeline Requirements: Comprehensive Exam must be completed within five years of starting the program.
- Dissertation and Publication: At least one journal paper must be submitted, accepted, or published.
University of North Carolina at Charlotte
- Faculty: The faculty members are renowned for their impactful research contributions on a global scale.
- Curriculum: The curriculum is versatile, catering to individuals aiming for academia as well as those targeting roles in the corporate, commerce, or public sectors.
- Program: A blend of theoretical and hands-on research is emphasized, offering a well-rounded educational experience.
Virginia Tech
- Seminars and Ethics: Students attend special seminars and complete training on scholarly ethics and diversity.
- Guidance: Each student gets a faculty advisor. A group of faculty members, called a committee, also guides them.
- Major Exams: Students go through four main stages: a qualifying process, a preliminary proposal, a research presentation, and a final defense.
- Strong Research: WPI's PhD program is recognized for its excellent research contributions.
- Practical Focus: The program teaches students to tackle real tech challenges.
- Modern Labs: Students use the latest labs like the Human-Robot Interaction Lab.
Dakota State University
- Program Goal: Train students to handle and prevent cyber threats.
- Awards: The university has received top cybersecurity awards.
- What You'll Learn: Research skills, cyber defense techniques, and ethical decision-making.
New Jersey City University, College of Professional Studies
- About: Focuses on best practices in areas like national security, cyber defense, and crisis communication.
- Recognitions: The program has been honored by the National Security Agency since 2009 and was recognized for excellence in intelligence studies.
- Jobs: Graduates are prepared for top roles in sectors like government and education.
- Program Content: The course dives deep into modern cybersecurity topics, from new tech and artificial intelligence to specialized research areas.
- Location Benefits: The university is near many cybersecurity companies and government agencies, giving students unique opportunities.
- For Working People: It's crafted for professionals, allowing them to experience various cybersecurity roles, from tech firms to government.
- Completion Time: Students have up to ten years from starting to finish their dissertation.
- Program: Trains students for roles in academia, government, and business.
- Multidisciplinary Approach: The program combines both technical and managerial aspects of cybersecurity, offering a comprehensive understanding of the field.
The University of Rhode Island
- Research Focus: The Ph.D. program is centered around a big research project in Computer Science.
- Qualifying Exams: Students take exams on core topics, but some might get exemptions if they're already skilled in certain areas.
- Equal Opportunity: The University of Rhode Island is committed to the principles of affirmative action and is an equal opportunity employer.
University of North Texas
- Team Effort: The program is a collaboration between various UNT departments for a well-rounded view of cybersecurity.
- Goals: The course aims to develop critical thinkers who are passionate about the role of information in our lives and can work across different fields.
- Skills Gained: Students will learn about research, teaching methods, decision-making, leadership, and analyzing data.
New York University Tandon School of Engineering
- Scholarships: Many students get scholarships that pay for tuition and give a monthly allowance.
- Research Interest: Research areas include cybersecurity, computer games, web search, graphics, and more.
- Experience: Students can also research in NYU's campuses in Shanghai or Abu Dhabi.
- One Degree for All: Every student gets the same Ph.D., regardless of their specific area of study.
- Research Focus: The program emphasizes deep research and prepares students for advanced roles.
- Major Project: Students work on a big research project, adding new knowledge to the computing world.
- Program: Prepares students for leadership roles in different sectors.
- Opportunities: Qualified students might get opportunities as Research or Teaching Assistants.
- Overview: Focuses on advanced research and modern technologies.
Augusta University
- Goal: The program prepares students for research roles and to make new discoveries in tech.
- Benefits: A Ph.D. opens up leadership opportunities in tech sectors.
- Overview: It focuses on new discoveries in areas like security, artificial intelligence, and virtual reality.
University of Texas at San Antonio
- Financial Support: Full-time students can get funding, which covers tuition and offers roles like teaching assistants.
- Job Prospects: UTSA trains students for jobs that are in high demand, using data from official sources.
- Overview: The program focuses on in-depth research and teaching.
University of Central Florida
- Mix of Subjects: Students can take courses from different areas, giving them a broad view of security topics.
- Many Job Options: Graduates can work in government, big companies, or teach in universities.
- Hands-on Learning: The program offers research, study projects, and internships for real-world experience.

Security Studies Ph.D.
The Security Studies PhD program at UCF is a fast-paced, focused program for people who have already completed an MA in a related field. Students complete coursework and write their dissertation in as little as three years, which makes it well-suited for advanced students, people with professional experience, and military officers who want to improve their skills in their field or make a career shift. Our students have found academic and professional success. In the past couple of years, despite the small size of our program, our PhD students have published in quality, peer-reviewed publications, both on their own ( Civil Wars , Intelligence and National Security, and others) and with faculty ( Conflict Management and Peace Science, African Affairs, Journal of Conflict Resolution, etc . ) Our students have been placed in research positions with respected organizations and government bureaucracies, and won a nationally competitive fellowship.
Program Timeline
First year students develop basic research skills and receive a grounding in the literature. By the end of the year, when they hold their first meeting with the Dissertation Committee, they should be making progress towards developing their dissertation topic.
Second year students complete their coursework and qualifying exams and start work on their dissertation proposal. Ideally, students will complete the proposal by the end of the second year.
Third year students work on their dissertation. Those who chose to do so also have opportunities to teach undergraduate courses in the department. Depending on the student and their topic, some students will complete their dissertation by the end of the third year. Others may need continue working on it beyond the third year.
Applying to the Security Studies PhD program
Fall 2023 applications must be completed by December 1, 2022 for International Applicants and January 15, 2023 for Domestic Applicants
Applicants to our PhD program must complete an earned Master’s Degree in Political Science, International Politics/Affairs/Relations, or a clearly related discipline before enrolling.
- Students who expect to complete their degree before beginning the program may also apply.
- Masters degrees from accredited Professional Military Education institutions (War Colleges, the Naval Post Graduate School, etc.) are usually sufficient to meet this requirement.
Students must apply on line using UCF’s online graduate applications system, and should expect to submit:
- One official transcript (in a sealed envelope) from each college/university attended.*
- A 500 word personal statement that describes their preparation for PhD-level study, research interests, and post-degree career goals
- A 2500-word writing sample that demonstrates their ability to conduct graduate-level research
- An updated resume
- Three letters of references, at least one of which must be from a faculty member associated with their MA degree.
- If a student is not a native English speaker, a TOEFL score of 90 or better on the internet-based test (iBT); or a score of 232 or better on the TOEFL computer-based test; or a score of 575 or better on the TOEFL paper-based test; or a score of 7.0 or better on the IELTS
- Program statistics and admissions data can be found by visiting the College of Graduate Studies’ website .
*Applicants applying to this program who have attended a college/university outside the United States must provide a course-by-course credential evaluation with GPA calculation. Credential evaluations are accepted from World Education Services (WES) or Josef Silny and Associates, Inc. only.
The political science department makes funding offers to most students admitted to the program. Usually these are GTA positions that are guaranteed for three years, conditional on academic progress. Depending on budgetary constraints, students who are making good progress may be funded in their fourth year. We nominate our best applicants for UCF’s university fellowships. The Presidential and Trustees Fellowships fund students for four years of study; other fellowships may be shorter but will be combined with department GTA positions to support students for at least 3 years of study. We encourage applicants to apply for outside fellowships that they may also be eligible for.
Our faculty includes world-class researchers and teachers who have published in topic journals including the American Political Science Review , International Organization , International Security , International Studies Quarterly , The Journal of Conflict Resolution, African Affairs , and other top journals. We have a strong record of collaborating with students and guiding them as they develop their research.
Student Highlights
Our PhD students have published in high quality journals, both on their own and in collaboration with faculty members.

UCF Class Spotlight: Political Psychology
BY JENNA MARINA LEE Class Name POS 4206 – Political Psychology Description The psychological analysis of political behavior, with emphasis on the individual rather than the…

Students’ Papers Sweep Competition
The UCF Political Science Department is proud to announce that Jennifer L. Hudson, a graduate student in the Political Science master’s program, won the FPSA…
Frequently Asked Questions
Does the department fund PhD students in the summer?
Yes, PhD students who are enrolled during the summer are funded through GTA positions. During the summer, students may enroll in our online graduate courses or do independent work with individual faculty.
Do students typically secure funding in their fourth year, if they take more than a year to finish their dissertation?
The department makes every effort to support students in their fourth year. However, the department cannot guarantee 4 th year funding, and depending on budgetary constraints that vary year by year, may not be able to fund some or all students in their fourth year.
Do I need to be in Orlando during the summers?
No. The department offers online graduate courses in the summer to allow students to continue their studies while travelling. We encourage students to use the summer time to pursue additional training through summer graduate workshops (ICPSR, IQRM, SWAMOS, SIPP, EITM, etc.), do field research work, or engage in professional opportunities with government agencies, research institutes, or the private sector.
How important is quantitative (i.e., statistical) training for your program?
All students in our program receive basic quantitative training and basic qualitative training. Students can pursue further training in our department, through other UCF departments, and other training programs like ICPSR. While some experience with statistical methods is useful, we do not require students to have well developed methodological skills on entry.
- Request Information
- Find Faculty & Staff
- Info For Toggle Info Return to Menu Menu
- Search Open Search Close Search
- Message from the Chair
- Department Directory
- Undergraduate Studies
- Graduate Studies
- Co-op & Experiential Learning
- Research Areas
- Research Centers and Institutes
- Faculty and Staff Directory
- Part-Time Faculty
- Annual Reports
- Honors & Distinctions
- Faculty Hiring
- Student Groups
- ECE Diversity, Equity and Inclusion
- Industrial Advisory Board
- Resources for Current Students
- In the Media
- ECE Student Stories

PhD in Cybersecurity
A research-based, interdisciplinary Doctor of Philosophy (PhD) in Cybersecurity combines a strong security technical foundation with a security policy and social sciences perspective. It seeks to prepare graduates to advance the state of the art of security in systems networks and the internet in industry, academia, and government. The interdisciplinary nature of the program distinguishes it from traditional doctoral degree programs in computer science, engineering, or social sciences and makes it unique in the Boston area.
Innovative Curriculum - Cybersecurity PhD
Students who choose the PhD in Cybersecurity program have a strong desire to purse academic research solving critical cybersecurity challenges facing today’s society. The PhD program is a natural path for students in the Master of Science in Cybersecurity program who want to pursue research and students with bachelor’s degrees and an interest in research-focused careers. Students who pursue careers in advancing the state of the art of cybersecurity have an opportunity to gain:
- A strong technical foundation in cybersecurity and an interdisciplinary perspective based on policy and social science
- A path to a research-focused career coupled with depth in information assurance research at a leading institution, one of the earliest designees by NSA/DHS as a National Center of Academic Excellence in Information Assurance Research, Information Assurance/Cyber Defense, and Cyber Operations
- The opportunity to work with and learn from faculty who are recognized internationally for their expertise and contributions in information assurance from Northeastern’s Khoury College of Computer Sciences , the Department of Electrical and Computer Engineering, and the College of Social Sciences and Humanities
- The Institute of Information Assurance (IIA) , an interdisciplinary research center overseen by both the Khoury College of Computer Sciences and the department of Electrical and Computer Engineering in the College of Engineering and the recipient of a National Science Foundation grant to train the country’s next generation of cybercorps
- The International Secure Systems Lab , affiliated with Northeastern, a collaborative effort of European and U.S. researchers focused on web security, malware and vulnerability analysis, intrusion detection, and other computer security issues
- The ALERT Center , where Northeastern is the lead institution, a multiuniversity Department of Homeland Security Center of Excellence involved in research, education, and technology related to threats from explosives
- Learn more.
Experiential Learning
Northeastern combines rigorous academics with experiential learning and research to prepare students for real-world engineering challenges. The Cooperative Education Program , also known as a “co-op,” is one of the largest and most innovative in the world, and Northeastern is one of only a few that offers a Co-op Program for Graduate Students. Through this program students gain industry experience in a wide variety of organizations, from large companies to entrepreneurial start-ups, while helping to finance their education. Students also have the option to participate in the university’s Experiential PhD program .

Academic Advising
The Academic Advisors in the Graduate Student Services office can help answer many of your questions and assist with various concerns regarding your program and student record. Use the link below to also determine which questions can be answered by your Faculty Program Advisors and OGS Advisors.
- Graduate Student Services
Admissions & Aid
Ready to take the next step? Review degree requirements to see courses needed to complete this degree. Then, explore ways to fund your education. Finally, review admissions information to see our deadlines and gather the materials you need to Apply.
- Degree Requirements
- Degree Requirements - Advanced Entry
- Tuition & Financial Aid
- Admissions Information

NAU’S VIRTUAL COMMENCEMENT
Join Program Dean Dr. Moore and explore the NAU Ed.D. program:
Meet the NAU Team See the Course/Program Sequence Explore the NAU Dissertation Path Find Out How to Start Your Personal Ed.D. Journey
Wednesday Jun 12, 2024 04:30 PM CT (US and Canada) Register

- 800-209-0182
- Apply Online
Request Information
- College of Undergraduate Studies
- Henley-Putnam School of Strategic Security
- Harold D. Buckingham Graduate School
- College of Legal Studies
- Get Started
- First-Time Students
- Graduate Students
- Military Students
- Transfer Students
- Academic Partners
- Admissions FAQ
- Tuition and Fees
- Financial Aid and Funding Options
- Military & Veteran Funding Options
- Cost of Attendance
- Mission, Purpose, Vision & History
- Careers at NAU
- Information & Disclosures
- Student Portal
- Desire2Learn
- Transcript Request
NAU’S RESPONSE TO COVID-19
Doctor of Strategic Security (DSS)
Gain the strategic and practical knowledge to counter threats to a safe and secure environment..

NAU offers a 100% online Doctor of Strategic Security program that expands the boundaries of the traditional security studies program, to educate the mid-and senior-level government, corporate, and defense industry professionals on how to ensure organizations thrive in a safe and secure environment. Specialized industry-relevant coursework centers around what you need to forestall reasonable and probable threats to organizational long-term or essential aims and interests. As you focus on your education which is designed to provide practical working knowledge to thwart threats to meet organizational goals, our team of professionals will help you with the individualized attention needed to reach your own.
The online Doctor of Strategic Security degree from National American University’s Henley-Putnam School of Strategic Security equips you with the confidence and global perspective you need to successfully lead your organization through today’s complex strategic and security challenges.
Online Doctor of Strategic Security Degree Overview
This 100% online DSS program will provide you with the advanced knowledge, skills, and insights you need to address emerging threat-based challenges to protect others, organizations, and the global strategic environment. You’ll learn how to make a positive impact on the safety and security of others from experts in the field including instructors and guest speakers. This unique program is focused on deterring and preventing threats to safety and security while also providing you the opportunity to engage with faculty and experts who share their practical and relevant real-world experiences and solutions. As a graduate you’ll be able to:
- Use critical thinking and problem-solving skills to produce preventive, deterrent and response actions necessary for engaging issues in strategic security
- Produce quantitative and qualitative research to address gaps in knowledge about strategic security matters.
- Effectively communicate key concepts and ideas in a variety of mediums to influence diverse audiences and decision-makers about strategic security matters.
- Work collaboratively in diverse groups to produce a conceptual framework that incorporates the key variables of the security environment to prevent and forestall emerging threats.
- Promote strategic security leadership relative to effective and ethical security outcomes.
Doctor of Strategic Security Degree Classes and Curriculum
The Doctor of Strategic Security degree program consists of three phase requirements: major core courses, a comprehensive exam, and dissertation research. These classes total 90 quarter credits
67.5 credits
Comprehensive Exam
Dissertation Research
22.5 credits
You are estimated to complete your Doctor of Strategic Security degree within five years of beginning the program, however many students complete it within three years.
Online Doctor of Strategic Security Degree Prerequisite Requirements
- A master’s degree or a bachelor’s degree and 45 graduate-level quarter credits (30 semester hours) in strategic security or related field.
- Five years of documented work experience in a security-related field or letter of recommendation from a professional attesting to the applicant’s leadership potential.
- Participation in a verbal interview with the dean of the DSS program (or a designee).
- A writing sample or the completion of a timed writing assessment.
- Note: GRE scores will not be required
Online Doctor of Strategic Security Tuition and Fees
- Regular tuition: $475.00*
- Military tuition: $450.00*
- Matriculation Fee: $75.00
- Comprehensive Exam Fee: $200.00
*Per credit hour
Learn more about our tuition schedule .
Online Doctor of Strategic Security Career Outcomes
The online Doctor of Strategic Security program prepares you to deal with the threats to personal or organizational safety and security. You will develop advanced skills in areas such as intelligence analysis, counterterrorism techniques, change management, and ethical decision making, and you will also learn how to create security strategies and policies to help your organization reach its long-range or essential objectives. Most importantly, you will demonstrate to employers that you have the skills to effectively lead security teams in any operational environment.
Who Is a Good Candidate for the Online Doctor of Strategic Security?
- Current mid-and senior-level professionals: If you are a security professional ready to advance your career at your organization, the online DSS program is a great fit. You will develop the skills and knowledge you need to address all kinds of threats in most any industry or professional environment.
- Future professionals: If you are able to collect and analyze data, think through solutions, provide insights, and make bias-free recommendations to decision-makers on threats against organizational goals, then this may be the degree for you. If you want to start a career as a strategic security professional and are excited to develop highly marketable skills valued in every field, the online DSS program can help you achieve your goals.
Course Listing
Doctor of strategic security core.
DSS700 – Advanced Strategic Security Analysis and Critique DSS710 – Advanced Counterterrorism Research Methods DSS720 – Strategic Security Information Literacy DSS730 – Applied Research Methodology DSS740 – Topics in the History of Strategic Security DSS750 – Briefings, De – briefings, and Presentations DSS760 – Advanced Leadership and Management DSS770 – Case Studies in Intelligence Regulation and Reform DSS780 – The Strategic Intelligence Process and Policy DSS790 – The Strategic Security Community DSS800 – Protection and Operations Management DSS810 – Advanced Business Communications DSS820 – Advanced Research in Terrorism/Counterterrorism DSS830 – Intelligence Practicum DSS840 – Protection Practicum
Doctoral practicum courses DSS830 Intelligence Practicum and DSS840 Protection Practicum may be substituted for upcoming internship work or upcoming student-employee projects related to strategic security.
DISSERTATION COURSES
DSS861 – Directed Dissertation Research I DSS862 – Directed Dissertation Research II DSS863 – Directed Dissertation Research III DSS864 – Directed Dissertation Research IV DSS865 – Directed Dissertation Research V
Course availability is subject to minimum class size requirements.
- First Name *
- Last Name *
- Phone Number *
- Do you have a military status? * Select One None Active Duty Veteran Reserve Guard Spouse Dependent National Guard
- Program of interest * Select a Program Arabic Certificate Dari Certificate Farsi Certificate French Certificate Hindi Certificate Mandarin Chinese Certificate Portuguese Certificate Russian Certificate Spanish Certificate Urdu Certificate Certificate Accounting, Bookkeeping and Auditing Certificate Aviation Management Certificate Business Administration Certificate Computer Support Specialist Certificate Construction Management Certificate Homeland Security Certificate Human Resource Management Certificate Legal Secretary Certificate Management Certificate Marketing Certificate Network and Server Administrator Certificate Office Applications and Software Support Certificate Physical Security and Risk Assessment Certificate Small Business Management and Entrepreneurship Certificate Web Development Entry-Level Certificate Counterterrorism Mid-Level Certificate Counterterrorism Entry-Level Certificate Executive Protection Mid-Level Certificate Executive Protection Entry-Level Certificate Intelligence Analysis Mid-Level Certificate Intelligence Analysis Graduate Certificate Accounting Graduate Certificate E-Marketing Graduate Certificate Global Supply Chain Management Graduate Certificate Human Resource Management Diploma Healthcare Coding Diploma Medical Billing and Coding A.A. Interdisciplinary Studies A.A.S. Accounting A.A.S. Business Administration A.A.S. Business Logistics A.A.S. Construction Management A.A.S. Criminal Justice A.A.S. Health and Beauty Management A.A.S. Information Technology A.A.S. Management A.A.S. Medical Administrative Assistant A.A.S. Medical Staff Services Management A.A.S. Paralegal Studies A.A.S. Professional Legal Studies A.A.S. Small Business Management B.A. Interdisciplinary Studies B.S. Accounting B.S. Aviation Management B.S. Business Administration B.S. Construction Management B.S. Criminal Justice B.S. Energy Management B.S. Healthcare Management B.S. Human Resource Management B.S. Information Technology B.S. Information Technology Emphasis Cybersecurity and Forensics B.S. Intelligence Management B.S. Management B.S. Nuclear Enterprise Security Studies B.S. Paralegal Studies B.S. Professional Legal Studies B.S. Strategic Security and Protection Management B.S. Terrorism and Counterterrorism Studies Master of Business Administration + COGS Master of Business Administration - Accelerated Master of Management Master of Management - Accelerated Master of Science Intelligence Management Master of Science Strategic Security and Protection Management Master of Science Terrorism and Counterterrorism Studies Doctor of Education Doctor of Strategic Security
- Hidden clientCampusValue
- By requesting information, I consent, without obligation, to be contacted by NAU via email, telephone, and text, using automated technology, at any telephone number and email address that I provide.
- Email This field is for validation purposes and should be left unchanged.
DSS-PLO1: Use critical thinking and problem-solving skills to produce preventive, deterrent and response actions necessary for engaging issues in strategic security DSS-PLO2: Produce quantitative and qualitative research to address gaps in knowledge about strategic security matters. DSS-PLO3: Effectively communicate key concepts and ideas in a variety of mediums to influence diverse audiences and decision-makers about strategic security matters. DSS-PLO4: Working collaboratively in diverse groups to produce a conceptual framework that incorporates the key variables of the security environment to prevent and forestall emerging threats. DSS-PLO5: Promote strategic security leadership relative to effective and ethical security outcomes.
Need some help?
Accreditation
National American University is accredited by the Higher Learning Commission - hlcommission.org - 800-621-7440 .
Mail: PO Box 677 Rapid City, SD 57709 Privacy Policy
- Investor Relations
- NAU Canada Online
- Request Transcript
- NAU Gear Shop


Academic Catalog 2023-2024
Cybersecurity, phd.
A research-based, interdisciplinary Doctor of Philosophy (PhD) in Cybersecurity combines a strong security technical foundation with a security policy and social sciences perspective. It seeks to prepare graduates to advance the state of the art of security in systems, networks, and the internet in industry, academia, and government. The interdisciplinary nature of the program distinguishes it from traditional doctoral degree programs in computer science, engineering, or social sciences and makes it unique in the Boston area.
Students who choose the PhD in Cybersecurity program have a strong desire to pursue academic research solving critical cybersecurity challenges facing today’s society. The PhD program is a natural path for students in the college’s Master of Science in Cybersecurity program who want to pursue research and students with bachelor’s degrees and an interest in research-focused careers. Students who pursue careers in advancing the state of the art of cybersecurity have an opportunity to gain:
- A strong technical foundation in cybersecurity and an interdisciplinary perspective based on policy and social science
A path to a research-focused career coupled with depth in information assurance research at a leading institution, one of the earliest designees by NSA/DHS as a National Center of Academic Excellence in Information Assurance Research, Information Assurance/Cyber Defense, and Cyber Operations
The opportunity to work with and learn from faculty who are recognized internationally for their expertise and contributions in information assurance from Northeastern University’s Khoury College of Computer Sciences, the Department of Electrical and Computer Engineering, and the College of Social Sciences and Humanities
Access to research projects at Northeastern’s research centers focused on security:
The Cybersecurity and Privacy Institute : The mission of Northeastern's Cybersecurity and Privacy Institute is to safeguard critical technology. Forging partnerships with experts in industry, government, and academia worldwide, the Institute’s faculty and students develop, protect, and enhance technologies on which the world relies—from mobile devices and “smart” IoT applications to tomorrow’s self-driving cars and delivery drones. Their expertise spans algorithm auditing; cloud security; cryptography; differential privacy; embedded device security; internet-scale security measurements; machine learning; big data; security, malware, and advanced threats; network protocols and security; web and mobile security; and wireless network security.
The International Secure Systems Lab , affiliated with Northeastern, a collaborative effort of European and U.S. researchers focused on web security, malware, and vulnerability analysis; intrusion detection; and other computer security issues.
The ALERT Center , where Northeastern is the lead institution, a multiuniversity Department of Homeland Security Center of Excellence involved in research, education, and technology related to threats from explosives.
The benefits of the Boston area:
- World-renowned for academic and research excellence, the Boston area is also home to some of the nation’s largest Department of Defense contractors and government and independent labs such as MIT Lincoln Lab, MITRE, and Draper Lab.
Degree Requirements
The PhD in Cybersecurity degree requires completion of at least 48 semester credit hours beyond a bachelor’s degree. Students who enter with an undergraduate degree will typically need four to five years to complete the program, and they will be awarded a master’s degree en route to the PhD.
Doctoral Degree Candidacy
A student is considered a PhD degree candidate after completing the core courses with at least a 3.500 GPA, with no grades lower than a B in the core courses, and either publishing a paper in a strong conference or journal or passing an oral exam that is conducted by a committee of three cybersecurity faculty members and based on paper(s) written by the student.
One year of continuous full-time study is required after admission to the PhD candidacy. During this period, the student will be expected to make substantial progress in preparing for the comprehensive examination.
Teaching Requirement
All cybersecurity PhD students must satisfy the teaching requirement in order to graduate. This requirement is fulfilled when the student works as a teaching assistant or instructor of record for one semester and during this semester:
- Teaches at least three hours of classes
- Prepares at least one assignment or quiz or equivalent
PhD students are expected to satisfy the teaching requirement some time after completing their first year and at least one semester prior to scheduling their PhD defense.
Dissertation Advising
The doctoral dissertation advising team for each student consists of two cybersecurity faculty members, one in a technical area. When appropriate, the second faculty advisor will be from the policy/social science area.
Dissertation Committee
With the help of the advisor, a student selects the committee, consisting of at least four members, to be approved by the PhD cybersecurity curriculum committee. The four members must include the advisor, two internal members, and an external member.
Comprehensive Examination
A PhD student must submit a written dissertation proposal and present it to the dissertation committee. The proposal should identify the research problem, the research plan, and the potential impact of the research on the field. The presentation of the proposal will be made in an open forum, and the student must successfully defend it before the dissertation committee after the public presentation.
Dissertation Defense
A PhD student must complete and defend a dissertation that involves original research in cybersecurity.
Awarding of Master’s Degrees
Students who enter the PhD in Cybersecurity program with a bachelor’s degree have the option of obtaining a master's degree from one of the departments participating in the program. To do so, they must meet all of the department’s degree requirements.
Bachelor’s Degree Entrance
Complete all courses and requirements listed below unless otherwise indicated.
Teaching Qualifying exam and area exam Annual review Dissertation proposal Dissertation committee Dissertation defense
Core Requirements
A grade of B or higher is required in each core course. A cumulative 3.500 grade-point average is required for the core requirement.
Electives and Tracks
Dissertation, program credit/gpa requirements.
48 total semester hours required Minimum 3.000 GPA required
Incoming PhD in cybersecurity students who have already completed a Master of Science in an adjacent field may petition to the graduate program administration for advanced entry. Advanced entry petitions are reviewed by the program administration on a case-by-case basis. Please note that advanced entry does not waive by itself any part of the PhD coursework requirements. As a degree conferral requirement, a minimum of 16 semester hours of coursework beyond the 32 semester hours of the master’s degree is required of advanced entry PhD students (48 semester hours is required of standard entry PhD students). A grade of B or higher is required in each course. A cumulative 3.500 GPA is required for the core requirement.
Refer to the PhD Cybersecurity overview for admission to candidacy requirements.
Refer to the PhD Cybersecurity overview for residency requirements.
Refer to the PhD Cybersecurity overview for teaching requirements.
Refer to the PhD Cybersecurity overview for dissertation advising requirements.
Refer to the PhD Cybersecurity overview for dissertation committee requirements.
Refer to the PhD Cybersecurity overview for comprehensive examination requirements.
Refer to the PhD Cybersecurity overview for dissertation defense and completion requirements.
Core Requirement
Students are required to take all core courses unless otherwise determined by the program. Students must maintain a minimum GPA of 3.500 as well as earn a grade of B or better in each core course.
Students are required to take all courses unless otherwise determined by the program.
Minimum 16 semester hours required Minimum 3.000 GPA required
Print Options
Send Page to Printer
Print this page.
Download Page (PDF)
The PDF will include all information unique to this page.
2023-24 Undergraduate Day PDF
2023-24 CPS Undergraduate PDF
2023-24 Graduate/Law PDF
2023-24 Course Descriptions PDF

Security and Crime Science MPhil/PhD
London, Bloomsbury
UCL Security and Crime Science is widely recognised for the impact of its research on real-world crime problems. The Department has long-standing links with police forces, policy makers, academic research centres of excellence and security organisations in the UK and internationally.
A PhD with us allows you to pursue original research and make a distinct and significant contribution to your field.
UK tuition fees (2024/25)
Overseas tuition fees (2024/25), programme starts, applications accepted.
- Entry requirements
Evidence of graduate research experience, for example a Master's degree, and a minimum of an upper second-class UK Bachelor's degree, or an overseas qualification of an equivalent standard. Applicants must also consider whether the Department of Security and Crime Science has the relevant expertise available to offer sufficient supervision in their chosen area of research. You will be expected to identify two UCL academics to supervise your research before applying. Ideally you will have contacted them before applying to ensure they are able to support your application. Following consideration of applications at the department's Graduate Research Committee, students may be requested to attend an interview with prospective supervisors (either in person or by telephone).
The English language level for this programme is: Level 3
UCL Pre-Master's and Pre-sessional English courses are for international students who are aiming to study for a postgraduate degree at UCL. The courses will develop your academic English and academic skills required to succeed at postgraduate level.
Further information can be found on our English language requirements page.
Equivalent qualifications
Country-specific information, including details of when UCL representatives are visiting your part of the world, can be obtained from the International Students website .
International applicants can find out the equivalent qualification for their country by selecting from the list below. Please note that the equivalency will correspond to the broad UK degree classification stated on this page (e.g. upper second-class). Where a specific overall percentage is required in the UK qualification, the international equivalency will be higher than that stated below. Please contact Graduate Admissions should you require further advice.
About this degree
The Department of Security and Crime Science is organised into five centres of excellence:
- Geographical analysis
- The "Designing Out Crime" group
- The crime policy and evaluation group
- Terrorism and organised crime
- Forensic science
Staff and students work across these groups, across UCL and in the wider research community, which includes active international collaborations.
Who this course is for
Security and Crime Science is a multi-disciplinary subject, drawing on expertise in psychology, social science, statistics, mathematics, architecture, forensic sciences, design, geography and computing. This is reflected in our students, who come from a variety of backgrounds. This makes the department an interesting and stimulating environment in which to study.
We seek graduates from all disciplines who want to solve real-world security and crime problems.
What this course will give you
UCL Security and Crime Science is devoted specifically to reducing crime through teaching, research, public policy analysis and by the dissemination of evidence-based information on crime reduction. Our mission is to change crime policy and practice.
At UCL Security and Crime Science, we are committed to the quality and relevance of the research supervision we offer. As an MPhil/PhD student, you will work with academics at the cutting edge of scholarship. You will also be an integral part of our thriving and collaborative research community, in the department and more widely at UCL.
The foundation of your career
This PhD programme is a well-established programme that draws in students from around the world who have gone on to exciting careers in security and crime sectors.
Graduates from our research programmes go on to research careers and to take up lecturing posts in academic institutions. Others have taken up policy-related positions in the public and private security sectors.
Employability
This is the first Phd programme of its kind to combine a multidisciplinary crime or security doctoral degree with a programme of taught modules (focusing on the application of scientific method to crime reduction) and professional skills training.
Our aim is to produce a new generation of crime and security practitioners with the skills to tackle modern and evolving crime threats. With over 60 partners in industry and the public sector and some of the world's leading academics at UCL working in these areas, we provide excellent supervision and career prospects.
We have long-established links with police forces, policy makers at all levels, academic research centres of excellence and security organisations in both the UK and internationally
The department attracts leading figures in the field to our extensive programme of events which inform debates around crime prevention. Regular events include the Women in Security showcase, annual International Crime Science conference, regular seminars and outside speakers.
These events provide a platform for students to connect with crime science practitioners and researchers across academia, government, and industry, offering a chance to learn from their expertise and establish valuable contacts.
Collaborative working at UCL is also an important aspect of our multidisciplinary research programme.The MPhil/PhD in Security and Crime Science gives students the opportunity to mix with peers from backgrounds including architecture, computer science, statistics, electronic engineering, chemistry, forensic sciences, psychology, philosophy, ethics and laws.
Teaching and learning
The initial registration on the programme will be on an MPhil basis. In order to progress to the PhD, students are required to pass an ‘upgrade’. The purpose of the upgrade is to assess your progress and ability to complete your PhD programme to a good standard and in a reasonable time frame.
The Doctor of Philosophy (PhD) consists of a piece of supervised research, normally undertaken over a period of three years of full-time or five years of part-time study. Assessment is by means of a thesis, which should demonstrate your capacity to pursue original research based upon a good understanding of the research techniques and concepts appropriate to the discipline.
You should meet frequently with your supervisors and engage with the departmental and UCL communities more widely through events, training, and networking opportunities.
The PhD is examined by a viva committee comprising two experts in the field, an external examiner, and an internal examiner. Your supervisor nominates suitable examiners during your final year, in consultation with you, and the nominations are scrutinised by UCL’s examinations office who may approve or reject them. You should not have had prior contact with either examiner. The viva usually takes two to three hours.
As a full-time student you are expected to devote at least 35 hours per week to your studies for the full duration of your programme. If you are studying part-time, you should expect to spend at least 17.5 hours per week.
As a research student, your principal supervisor will establish a timetable of regular meetings where all matters relating to your work can be discussed.
These meetings should take place at least once per month. Subsidiary supervisors should stay acquainted with the progress of your work and be present at annual supervisory meetings, as a minimum.
Research areas and structure
The department has five main research groups:
- Counter-terrorism: situational prevention of terrorism; technology for counter-terrorism; transferable training between crime and terrorism
- Crime mapping: innovation in crime mapping methods; prospective crime mapping
- Crime policy analysis and evaluation: evaluation of crime prevention schemes; knowledge transfer
- Designing out crime: role of design in crime prevention; environmental design; crime risk and administrative procedure design
- Forensic sciences: forensic science reconstruction; interpretation of evidence; trace evidence dynamics (including DNA, residues/particulates, environmental evidence etc.).
UCL Security and Crime Science hosts the UCL Security Science Doctoral Research Training Centre (UCL SECReT), an international centre for PhD training in security and crime science.
We offer an integrated PhD programme for students wishing to pursue multi-disciplinary security or crime-related research degrees. We expect their research to be interdisciplinary and to involve some 'hard science' element. Our research is underpinned by a methodology combining science and engineering expertise with expertise from wider disciplines including the social sciences. We see four research 'domains' which can interact:
- Science and technology innovation: to create the next generation of security technologies
- People factors: understanding and incorporating human factors (via behavioural science, decision-making techniques, etc.) into the development of security solutions
- Process factors: enhancing security processes by increasing our understanding of the operational processes of activities, organisations or infrastructures under threat
- Policy: contributing to the development of government policy through research findings.
Research environment
Our department has a distinctly interdisciplinary outlook on the prevention of crime, terrorism and organised crime. We have long-established links with police forces, policy makers, academic research centres of excellence, and security organisations in the UK and internationally.
The department has a successful track record of working closely with practitioners and is widely recognised for its knowledge transfer and exchange activities, as well as the impact of its research on real world crime problems.
In the 2021 Research Excellence Framework (REF) exercise, the department’s research environment was deemed to be 87.5% ‘world-leading' and 12.5% ‘internationally excellent’, placing it 6th in this area of REF assessment.
As a Security and Crime Science MPhil/PhD student, you will have the opportunity to learn from, and contribute to, this thriving research culture.
The length of registration for ourresearch degree programmes is three years for full-time study and five years for part-time study.
You are required to register initially for the MPhil degree with the expectation of transfer to PhD after successful completion of an upgrade viva 9-18 months after initial registration.
Upon successful completion of your approved period of registration, you may start a writing period called Completing Research Status (CRS), within which you write up your thesis.
To successfully upgrade to a PhD, you are required to submit a piece of writing demonstrating sufficient theoretical, conceptual, and methodological development as well as a clearly articulated plan to finish the thesis.
You are also required to present and answer questions about this work to a panel consisting of your subsidiary supervisor and another member of the faculty who acts as an independent assessor.
You are required to register initially for the MPhil degree with the expectation of transfer to PhD after successful completion of an upgrade viva 24 months after initial registration.
Accessibility
Details of the accessibility of UCL buildings can be obtained from AccessAble accessable.co.uk . Further information can also be obtained from the UCL Student Support and Wellbeing team .
Online - Open day
Security and Crime Science PhD Open Evening
Join our open event series to learn more about our PhD programme, future career opportunities and what it's like to be part of our fantastic community. There are also questions for our academics, admission tutors and current students.
Fees and funding
Fees for this course.
The tuition fees shown are for the year indicated above. Fees for subsequent years may increase or otherwise vary. Where the programme is offered on a flexible/modular basis, fees are charged pro-rata to the appropriate full-time Master's fee taken in an academic session. Further information on fee status, fee increases and the fee schedule can be viewed on the UCL Students website: ucl.ac.uk/students/fees .
Additional costs
There are no additional costs associated with this programme.
For more information on additional costs for prospective students please go to our estimated cost of essential expenditure at Accommodation and living costs .
Funding your studies
For a comprehensive list of the funding opportunities available at UCL, including funding relevant to your nationality, please visit the Scholarships and Funding website .
CSC-UCL Joint Research Scholarship
Value: Fees, maintenance and travel (Duration of programme) Criteria Based on academic merit Eligibility: EU, Overseas
If you meet the entry requirements, you will need to identify at least two UCL academics with the expertise needed to assess your technical skills and act as your supervisors. To support with this, we suggest you check our departmental website to identify the interests and areas of expertise of current academics.
Before applying, please ensure you focus on a research proposal of approximately 3000 words which introduces the research questions and hypotheses you would like to investigate, and the research methods you would like to apply in your work. Clearly indicate how the required data will be obtained, and what resources you need for your project. You can find guidance on writing a research proposal online.
Deadlines and start dates are usually dictated by funding arrangements, so please check with the department or academic unit before applying to see if you need to consider these. In most cases, you should identify and contact potential supervisors before making your application.
For more information see our How to apply page and ensure you visit our website.
Please note that you may submit applications for a maximum of two graduate programmes (or one application for the Law LLM) in any application cycle.
Choose your programme
Please read the Application Guidance before proceeding with your application.
Year of entry: 2024-2025
Got questions get in touch.

Security and Crime Science
UCL is regulated by the Office for Students .
Prospective Students Graduate
- Graduate degrees
- Taught degrees
- Taught Degrees
- Applying for Graduate Taught Study at UCL
- Research degrees
- Research Degrees
- Funded Research Opportunities
- Doctoral School
- Funded Doctoral Training Programmes
- Applying for Graduate Research Study at UCL
- Teacher training
- Teacher Training
- Early Years PGCE programmes
- Primary PGCE programmes
- Secondary PGCE programmes
- Further Education PGCE programme
- How to apply
- The IOE approach
- Teacher training in the heart of London
- Why choose UCL?
- Entrepreneurship
- Inspiring facilities and resources
- Careers and employability
- Your global alumni community
- Your wellbeing
- Postgraduate Students' Association
- Your life in London
- Accommodation
- Funding your Master's

College of Professional Studies
Security and intelligence studies.
The Master of Arts in Security and Intelligence Studies program prepares you to take a leadership role in the security field. You’ll be ready to anticipate and lead responses to security threats in an ever-changing, challenging global environment.
Global security continues to be an evolving and critical issue facing countries, companies, and communities. Successful security and intelligence experts need to possess the critical thinking and problem-solving skills to effectively lead in responding to today’s challenging threat environment.
The Master of Arts in Security and Intelligence Studies program offers a unique interdisciplinary approach that merges security, law, diplomacy, politics, and constitutional rights to create well-rounded security leaders. You’ll gain and hone skills in intelligence collection and dissemination, analysis, research, threat assessment, and evaluation of information and policy development while focusing on the importance of civil liberties in pursuing security in civil society.
You will be learning from security experts, each with at least 20 years of teaching and real-world experience. They’ll share their experiences as constitutional lawyers, White House advisors, CIA operatives, military intelligence officers, and more.
More Details
Unique features.
Benefit from a unique multidisciplinary approach that merges security leadership skills and an understanding of civil liberties.
Learn from faculty security experts who bring their real-world experience as constitutional lawyers, White House advisors, CIA operatives, military intelligence officers, and more to the classroom.
Gain a whole-of-government approach to security studies with a set of required foundational courses and a broad range of electives to choose from.
Focus your degree with three tracks: Corporate Security Management, Homeland Security & Emergency Management, and Strategic Intelligence & Analysis
Career Outlook
- Prepare for security roles such as intelligence analyst, special agent, information security officer, corporate security specialist and manager, criminal investigator, or fraud investigator.
- Security and intelligence-related occupations are projected to grow much faster than the average. New positions combined with replacements are expected to produce more than 200,000 openings per year across the United States. (JobsEQ)
- Federal employment has grown for most security-related occupations over the past five years. Emergency management specialists reported the highest growth (178%), followed by investigative analysis (48%). ( opm.gov )
- Top Boston employers for security professionals include Humana, MassMutual Financial Group, Deloitte, State Street Corporation, Commonwealth of Massachusetts, and MIT Lincoln Laboratory. (JobsEQ)
Testimonials
- jack mcdevitt, phd, faculty director, looking for something different.
A graduate degree or certificate from Northeastern—a top-ranked university—can accelerate your career through rigorous academic coursework and hands-on professional experience in the area of your interest. Apply now—and take your career to the next level.
Program Costs
Finance Your Education We offer a variety of resources, including scholarships and assistantships.
How to Apply Learn more about the application process and requirements.
Requirements
- Online application
- Statement of purpose (500–1000 words): Identify your educational goals and expectations of the program. Please be aware that Northeastern University's academic policy on plagiarism applies to your statement of purpose.
- Professional resumé
- Unofficial undergraduate transcripts; official transcripts required at the time of admission
- Two letters of recommendation from individuals who have either academic or professional knowledge of your capabilities such as a faculty member, colleague, or mentor, preferably one from your current employer
- Official associate or bachelor's degree transcript from an accredited college or university in the U.S., stating degree conferral and date
- TOEFL, IELTS, PTE, Duolingo, or NU Global Exam scores
Are You an International Student? Find out what additional documents are required to apply.
Admissions Details Learn more about the College of Professional Studies admissions process, policies, and required materials.
Admissions Dates
Our admissions process operates on a rolling basis; however, we do recommend the application guidelines below to ensure you can begin during your desired start term:
Domestic Application Guidelines
International Application Guidelines *
*International deadlines are only applicable if the program is F1 compliant.
Industry-aligned courses for in-demand careers.
For 100+ years, we’ve designed our programs with one thing in mind—your success. Explore the current program requirements and course descriptions, all designed to meet today’s industry needs and must-have skills.
View curriculum
Northeastern's signature experience-powered learning model has been at the heart of the university for more than a century. It combines world-class academics with professional practice, allowing you to acquire relevant, real-world skills you can immediately put into action in your current workplace. This makes a Northeastern education a dynamic, transformative experience, giving you countless opportunities to grow as a professional and person.
Learn About Getting Real World Experience
Our Faculty
Northeastern University faculty represents a broad cross-section of professional practices and fields, including finance, education, biomedical science, management, and the U.S. military. They serve as mentors and advisors and collaborate alongside you to solve the most pressing global challenges facing established and emerging markets.

John Terpinas

Edward Barr

David Hagen
By enrolling in Northeastern, you’ll gain access to students at 13 campus locations, 300,000+ alumni, and 3,000 employer partners worldwide. Our global university system provides students unique opportunities to think locally and act globally while serving as a platform for scaling ideas, talent, and solutions.
Related Articles

5 Tips for Choosing Your DLP Dissertation Topic

Northeastern’s Online DMSc Program: What To Expect

Doctor of Health Science vs. Medical Science: Which Is Better?
Our cookies
We use cookies for three reasons: to give you the best experience on PGS, to make sure the PGS ads you see on other sites are relevant , and to measure website usage. Some of these cookies are necessary to help the site work properly and can’t be switched off. Cookies also support us to provide our services for free, and by click on “Accept” below, you are agreeing to our use of cookies .You can manage your preferences now or at any time.
Privacy overview
We use cookies, which are small text files placed on your computer, to allow the site to work for you, improve your user experience, to provide us with information about how our site is used, and to deliver personalised ads which help fund our work and deliver our service to you for free.
The information does not usually directly identify you, but it can give you a more personalised web experience.
You can accept all, or else manage cookies individually. However, blocking some types of cookies may affect your experience of the site and the services we are able to offer.
You can change your cookies preference at any time by visiting our Cookies Notice page. Please remember to clear your browsing data and cookies when you change your cookies preferences. This will remove all cookies previously placed on your browser.
For more detailed information about the cookies we use, or how to clear your browser cookies data see our Cookies Notice
Manage consent preferences
Strictly necessary cookies
These cookies are necessary for the website to function and cannot be switched off in our systems.
They are essential for you to browse the website and use its features.
You can set your browser to block or alert you about these cookies, but some parts of the site will not then work. We can’t identify you from these cookies.
Functional cookies
These help us personalise our sites for you by remembering your preferences and settings. They may be set by us or by third party providers, whose services we have added to our pages. If you do not allow these cookies, then these services may not function properly.
Performance cookies
These cookies allow us to count visits and see where our traffic comes from, so we can measure and improve the performance of our site. They help us to know which pages are popular and see how visitors move around the site. The cookies cannot directly identify any individual users.
If you do not allow these cookies we will not know when you have visited our site and will not be able to improve its performance for you.
Marketing cookies
These cookies may be set through our site by social media services or our advertising partners. Social media cookies enable you to share our content with your friends and networks. They can track your browser across other sites and build up a profile of your interests. If you do not allow these cookies you may not be able to see or use the content sharing tools.
Advertising cookies may be used to build a profile of your interests and show you relevant adverts on other sites. They do not store directly personal information, but work by uniquely identifying your browser and internet device. If you do not allow these cookies, you will still see ads, but they won’t be tailored to your interests.
Course type
Qualification, university name, doctorate degrees in security.
7 degrees at 6 universities in the UK.
Customise your search
Select the start date, qualification, and how you want to study

Related subjects:
- Doctorate Security

- Course title (A-Z)
- Course title (Z-A)
- Price: high - low
- Price: low - high
Intelligence and Security Studies PhD
Brunel university london.
Research profile The Brunel's Centre for Intelligence and Security Studies Team conduct research in most areas connected with intelligence Read more...
- 3 years Full time degree: £4,712 per year (UK)
- 6 years Part time degree: £2,356 per year (UK)
Security Science MRes and MPhil/PhD
Ucl (university college london).
Security and Crime Science (SCS) uses evidence-based techniques to prevent and control crime and security problems, and to detect Read more...
- 3 years Full time degree: £6,035 per year (UK)
- 5 years Part time degree: £2,930 per year (UK)
Professional Doctorate Emergency Services Management (DESM)
Edge hill university.
Professionalisation of the emergency services workforce and the development of strategic leadership within the blue lights, namely the Read more...
- 4.5 years Part time degree: £3,720 per year (UK)
Crime, Policy and Security - Prof Doc
London metropolitan university.
Make a difference to the criminal justice, national and international security sectors, while having the opportunity to enhance your Read more...
- 4 years Part time degree
Security and Crime Science MPhil/PhD
The department of security and crime sciences is organised into five centres of excellence Geographical Analysis; The Designing Out Crime Read more...
PhD Strategy and Security
University of exeter.
Research degrees in this area of interest provide opportunities to study with leading academics and practitioners who are specialists in Read more...
- 4 years Full time degree: £4,900 per year (UK)
- 8 years Part time degree
Leadership Studies with reference to Security & Development PhD, or option of joint PhD with University of Pretoria.
King's college london, university of london.
Leadership plays a significant role in both development and security processes and outcomes. The Leadership Studies with reference to Read more...
- 3 years Full time degree: £6,936 per year (UK)
- 6 years Part time degree: £3,468 per year (UK)
Course type:
- Full time Doctorate
- Part time Doctorate
Qualification:
Related subjects:.
- Cranfield University
Taught degrees
- Why study for an MSc at Cranfield?
- Application guide
- Find a course
- Search bursaries
- Fees and funding
- Make a payment

Research degrees
- Why study for a research degree at Cranfield?
- Research opportunities
Apprenticeships
- Apprenticeship programmes
- Apprentices
- MKU Apprenticeships
Professional development
- Professional and technical development
- Level 7 Apprenticeships
- Open Executive Programmes
- Find a programme
Studying at Cranfield
International students.
- Life at Cranfield
- Life at Shrivenham
- Careers and Employability Service
- IT services
- View our prospectus
Choose Cranfield
- Why work with Cranfield
- Who we work with
- Entrepreneurship
- Corporate Sustainability Consultancy
- Networking opportunities
- Access our facilities
- Business facilities and support services
Develop your people
- Short courses and executive development
- Customised programmes
- Recruit our students
Develop your technology and products
- Access funding
- Knowledge Transfer Partnerships
- Work with our students
- License our technology
- Business incubation
- Cranfield spin-out and start-up companies
Our research publications and data
- Case studies
- Research projects
Why research at Cranfield?
- Sustainability at Cranfield
- Theme Research Strategies
- Hydrogen Gateway
- Research Excellence Framework
- Access our world class facilities
- Current research projects
- Cranfield Doctoral Network
- Applying for a research degree
- Entry requirements
Engage with us
- Industry collaboration
- Find an expert
Research and Innovation Office
- Open research
- Fellowships
- Energy and Sustainability
- Manufacturing and Materials
- Transport Systems
Defence and Security
- Environment and Agrifood
- Cranfield School of Management
- Centres and institutes
- Academic disciplines
- Virtual Experience
International activity and reach
- Partnerships
- Cranfield in India
- European Partnership Programme
- Global impact
- Information for your region
- Visas and immigration
- Life on campus
- Pre-sessional English for Academic Purposes
- About Cranfield University
- Our structure
- Rankings and awards
- Building on our heritage
- Community and public engagement
- Facts and figures
- History and heritage
Governance and policies
- University management
- Council and Senate
- Corporate responsibility
- Environmental credentials
- Research integrity
- Staff and students
- Work at Cranfield
- School of Management
- Research and Innovation at Cranfield
PhDs in Defence and Security: Leadership, Management and Governance
The Centre for Defence Management and Leadership (CDML) is a specialised research and teaching unit, comprising experienced and dedicated researchers. It has developed a world class reputation in defence and security studies, and is lauded for the rigour, originality, international perspective and policy relevance of its doctoral programme.
The Centre has delivered short training and long degree-bearing courses in over 100 countries. Students are typically employed in central government, defence industry and the Armed Forces, and their doctoral studies resonate with their professional activities, including, for example, defence engagement, conflict resolution, gender studies, humanitarian and relief operations, international conflict and security law, defence budgeting and public finance. PhD candidates are required to attend an initial one-week induction programme. Thereafter, regular progress reviews are undertaken to ensure students receive continuous advice and guidance. Cranfield is well-known for providing close and supportive supervision, and students will be allocated primary and associate supervisors to offer mentorship across the entire period of doctoral registration.
Research thematics
Doctoral research programmes are offered in a broad array of defence and security leadership, law and management fields. Candidates are invited to submit research proposals that fit into any of the following broad subject areas:

Potential supervisors
Interested applicants are encouraged to consult with Centre academics regarding interest in supervising particular research projects. It is advisable that contact is made prior to formal submission of an application. Please see below for academic names, respective e-mail addresses, broad disciplinary fields and also URL links for access to their teaching, research and publication details.
Leadership and Management
- Bryan Watters [email protected]
- Iftikhar Zaidi [email protected]
- Robby Allen [email protected]
International Law
- David Turns (Visiting Fellow) [email protected]
Policy, Strategy and Governance
- Ron Matthews (Visiting Professor) [email protected]
- Dr Lloyd Parsons [email protected]
- Dr Caroline Micklewright [email protected]
Economic and Financial Management
- Irfan Ansari [email protected]
Research Students
Find out more about our current research students and their areas of research .
Mode of study
Students can register for a three-year full-time PhD programme, and may be based at either Cranfield Defence and Security, Shrivenham or in their home country
Part-time registration is also available. The study period extends to six years, though it is possible for students to submit their doctoral thesis for examination from the three-year point. Candidates will not be based at Shrivenham and may undertake their doctoral studies while in full-time employment at any location in the United Kingdom or overseas.
Annual fees
How to apply.
CDML is one of seven focused Centres that form part of the Cranfield Defence and Security (CDS) Faculty. It is located on the edge of England’s beautiful Cotswold region, just an hour West of London. The application process is uncomplicated, having the following requirements:
- Completion of an online application form
- A clear and concise research aim/problem/question
- Reference to the original contribution to knowledge
- Brief identification of the seminal literature in the chosen field
- Explanation of the research methodology for data collection
- Emphasis on the research programme’s policy relevance
- Compliance with the minimum entry requirements: a 2.1 first degree and/or master’s qualification, along with at least five years relevant professional experience
For further application information, please access more details about applying for a research degree.
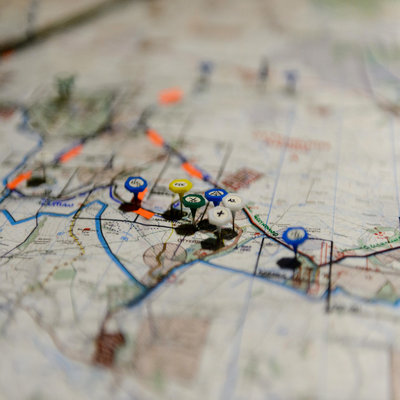
Centre for Defence Management and Leadership

Download Research Yearbook


Professional Doctorate in Security Risk Management
The Professional Doctorate in Security Risk Management (D.SyRM) is a structured, part-time programme targeted towards security professionals in the UK and overseas, delivered through a small number of workshops in Portsmouth for the first two years and then two years of supervised research leading to a thesis.
Key information
- 4-7 years part-time
- October 2024
Course information
Please select the page of your interest
Showing content for section Overview
Benefits of a Prof Doc in Security Risk Management (DSyRM)
The Professional Doctorate in Security Risk Management (D.SyRM) is a structured, part-time programme targeted towards security professionals in the UK and overseas. It comprises a taught element delivered through a small number of workshops in Portsmouth for the first two years and then up to five years of supervised research leading to a thesis.
The aim of the course is to provide a framework for security professionals to reflect on and contribute to practice in their area of work. Its emphasis is on developing researching professionals (which is distinct from the more traditional PhD route which aims to develop professional researchers).
Students on the programme welcome the opportunity to enhance their professional standing in their areas of expertise while developing important new knowledge in those areas. They are drawn from a variety of backgrounds including:
- Corporate security
- Commercial security
- International security
- Security training sector
- Business continuity and crisis management
The overall aim of the course is to develop security professionals whose work informs, and is informed by, original research in the field. Current research topics include:
- Managing complex crises
- Securing the oil and gas sector
- Security of tax havens
Contact information
+44 (0) 23 9284 5566
Structure and teaching
A central feature of this programme is that you will be studying with the same cohort of people throughout. The interaction that this provides will give you the opportunity to work, learn and develop together. This avoids the sense of isolation that some PhD students experience.
For students who require a Visa to enter the UK then it must be noted that ID checks will take place at the start of the academic year on campus with the University UK Visa and Immigration Team as part of the normal student registration process.
Core modules
Professional review and development - 30 credits on this module, we'll introduce you to professional doctorate studies..
You'll reflect critically on your skills and experience, using professional knowledge models and literature to identify any areas for improvement.
You'll join your fellow students for discussion groups where you'll analyse complex theories relating to professionalism and practice.
This module gives you the essential foundations, analytical abilities and autonomy to shape your own doctoral path.
Advanced Research Techniques - 30 credits This module will give you a grounding in qualitative and quantitative research techniques appropriate for doctoral-level work - regardless of your final methods.
You'll examine relevant literature on methodology and strategies, evaluating their strengths and weaknesses.
You'll then identify and justify methods for a particular project, design a relevant research instrument, and complete ethical review documentation.
Publication and Dissemination - 30 credits On this module, you'll learn how to write an academic article suitable for publication in a journal of your choice and present to your fellow students in a style that mimics an academic conference.
You'll get to grips with the academic experience of journal searching, targeting, writing and conference presenting first-hand.
You'll also reflect on your academic learning and development needs while preparing original research that meets peer review standards and merits publication.
Proposal for Professional Research and Development Project - 30 credits In this module, you'll reflect on and consolidate your prior learning to draft your own professional research or development proposal.
When preparing your proposal, you'll identify practice-based questions, critically appraise literature gaps, make informed methodological judgments, appraise ethical issues, and apply advanced writing skills.
With staff and peer review to support you, you'll produce a well-structured, coherent, realistic, achievable and costed proposal ready for the research phase of your course.
Professional Research and Development Project - 360 credits This doctoral thesis module enables you to undertake primary, secondary or literature-based research within criminal justice, examined through a 50,000-word thesis.
Within your thesis, you'll interpret new knowledge that contributes to the field of criminal justice, satisfies peer-review and merits publication.
You'll also present your ideas via a formal presentation to a specialist audience of practitioners and academics.
Professional Research and Development Project - 240 credits On this module, you'll complete an original research project and substantial written thesis.
You'll design, plan and implement your research to uncover new knowledge, to a standard that satisfies peer review, contributes to the field of criminal justice and merits publication.
You'll use a range of advanced research techniques and communicate your ideas clearly to a specialist audience of experts and academics through your written thesis and a formal presentation.
Teaching and assessment
The doctoral programme aims to develop your research ability in the broad area of security risk management to an advanced level and promote evidence-based practice development. The development of the quality and value of your practice and research will be enhanced through:
- Seminars and workshops on critical research and security-related issues specifically focused on the development needs of security professionals
- Support from staff and peers to support you in reaching the necessary (doctoral) standard
- Supervision from a team with a very wide range of development and research interests and many years of professional experience
- Access to University of Portsmouth library facilities including a large number of e-books, journals and databases accessed electronically
- Access to additional, targeted training courses delivered through our Graduate School to meet any specific learning needs related to your individual research
- The use of an online learning environment enabling you to keep in easy touch with your peers and the course team
- Development of wider national and international perspectives through networking with your peer group
- Building ongoing productive links between security organisations
- Raising the profile, credibility and influence of your profession in both academic and practice contexts
How you're assessed
You will be assessed on the strength of your thesis, which is up to 50,000 words. The assessment includes two elements: i) a 50 minute presentation with an invited audience (plus 10 minutes of Q and As); followed by ii) a Viva Voce conducted by external and internal examiners.
Entry requirements
October 2024 start.
A master’s degree in an appropriate subject. Applicants must be professionally engaged in a security related area. All applicants will be invited to attend a face-to-face or telephone interview.
English language proficiency at a minimum of IELTS band 6.5 with no component score below 6.0.
If you don't meet the English language requirements yet, you can achieve the level you need by successfully completing a pre-sessional English programme before you start your course.
Course costs and funding
Tuition fees.
- Home/CI students: £5,400 p/a*
- EU students: £5,400 p/a* (including Transition Scholarship )
- International students: £9,050 p/a*
Home/EU/CI students on this course may be eligible for the Government Doctoral Loan .
*All fees are subject to annual increase
How to apply
Before you start your application, you'll need to have the following documentation ready:
- A research proposal and personal statement
- Proof of your first degree and grades (officially certified and translated copies if not in English)
- Proof of a relevant postgraduate degree with at least 60 credits having been completed
- Details of 2 referees or 2 references on official headed paper, one of which should ideally be an academic reference
- Proof of your English language proficiency (if English is not your first language)
- An up-to-date copy of your CV
Apply now for 2024

Graduate Student Awarded Boren Fellowship by the National Security Education Program
May 23, 2024

A University of Maryland graduate student in information management and community planning is among 102 recipients nationwide to earn the David L. Boren Fellowship to study critical languages overseas.
Alanna Leshea Anderson will receive $25,000 to travel to Brazil for a year to take intensive Brazilian Portuguese classes and live with a host family who will give her more practice and a better understanding of life and culture in the country. She plans to become proficient enough to pursue a sustainable development internship at a nonprofit.
“I’ll have the linguistic ability to reach a broader domestic and global audience than I’m currently capable of,” Anderson said. “My goal is to apply my knowledge from this award into a career in my passions: sustainable development and disaster management.”
The Boren Awards program by the National Security Education Program’s Institute of International Education grants undergraduate and graduate students with resources and support to develop language skills and experience in overseas locations important to the future security and stability of the United States. Recipients will work in the federal government for at least one year in exchange for funding. NSEP is a federal initiative and a component of the Defense Language and National Security Education Office (DLNSEO). Its goal is to increase the number of qualified U.S. citizens with foreign language and international skills.
UMD students have earned 22 Boren fellowships in the past 10 years.
Since 1994, over 7,800 students have received Boren Awards and applied their skills to support the missions of federal government agencies. Dawn Jourdan, the dean of the School of Architecture, Planning, and Preservation, is proud to have Anderson represent MAPP on a global scale.
“Alanna is committed to ensuring that language does not stand in the way of building resilient, inclusive communities,” she said. “We are so proud of her and this achievement.”
Information for... -->
- Admitted Students
- Current Students
- Prospective & Future Students
- Faculty & Staff
- School Counselors
- Admitted Student Site
- Career Outcomes
- Contact Admissions
- Connect with Other Admitted Students
- Deposit Now
- Office Directory
- Office of Financial Aid
- Visit Campus
Visit Admitted Student Central for more resources & info…
Resources for Online Students
- Academic Support / SMART Space
- Campus Public Safety
- Cash Card/ID
- Champ Support
- College Catalog
- Compass Student Services
- Dates & Deadlines
- School Dude (facilities request)
- Self-Service
- Shuttle Bus Locator
- Student Affairs, Diversity & Inclusion
Visit Current Student Central for more resources & info…
- Admissions & Aid
- Open House Events
- How to Apply
- Majors & Programs
- Financial Aid
- Request Information
Visit Prospective & Future Student Central for more resources & info…
- Office of Alumni Relations
- Update Your Info
- Make a Gift
- Champlain Weekend
- Desktop Calendar
- Office & People Directory
Visit Alumni Central for more resources & info…
- Academic Affairs
- News: The View
- People Center
- Reserve a Room (EMS)
- Self Service
Visit Faculty & Staff Center for more resources & info…
- Prospective Parents
- Visit & Events
- Career Success Statistics
- Tuition & Cost
- Parent & Family Relations
- Student Health Center
- Add Funds to Cash Card
- Billing & Payment Options
Visit Parent Central for more resources & info…
- School Counselors Admissions Page
- Arrange a Group Tour
- Meet the Admissions & Aid Team
- Types of Aid
- Tuition & Cost of Attendance
Visit School Counselor Central for more resources & info…
Are you looking for...
- Academic Calendar
- Office & People Directory
2023 Career Outcomes
- On Campus Undergraduate
- Online Undergraduate & Graduate
- About Us Our Story, Facts & More
Different by Design
- Career-Focused Academics
- Schools & Divisions
- Study Abroad
- Academic Support Resources
- Graduate School Partnerships & Partner Programs
- Our Faculty
- Why Champlain?
- Meet the Team
- Our Community
- Housing & Dining
- Get Involved
- Burlington, VT
- Student Services
- On-Campus Student Employment
- Places & Spaces
- Career Ready
- Experiential Learning
- Career Pathways
- Career Collaborative
- Office & People Directory
Champlain College Online offers 100% online undergraduate and graduate degrees and certificates.
- Online Degrees & Certificates
- Online Tuition & Aid
- Online Admissions
- Apply to Champlain College Online
- Request Info
- This is Champlain College
- Quick Facts
- Academics & Competencies
- Diversity, Equity & Inclusion
- Global Impact
- Professional Services
- Work with Us
Computer Networking & Cybersecurity
For our digital future to be secure, information must be safe. Earn real-world experience in computer networking and cybersecurity at Champlain College, and prepare yourself for a vital role protecting society from cyber threats.
- Champlain App
- Common App for Transfers

National Recognition
Champlain College is a designated National Center of Academic Excellence in Cybersecurity (NCAE-C) by the National Security Agency (NSA).
Safeguard the Future.
The digital technology explosion has reshaped our society, and we need experts to make sure its benefits outweigh its risks. With data breaches and security threats on the rise, there’s a growing need for professionals who can protect against cyber attacks. If you’re interested in safeguarding systems and being at the forefront of this vital field, Champlain’s Computer Networking & Cybersecurity program could be for you. Read More
What Is Computer & Digital Forensics?
Computer Networking & Cybersecurity is a field that focuses on protecting computer systems, networks, and data from unauthorized access, attacks, and potential threats. It involves understanding how computer networks work, designing secure systems, implementing protective measures, and detecting/responding to security incidents. With increasing reliance on technology and the Internet, cybersecurity has become critical to protecting sensitive information and ensuring the smooth operation of businesses and organizations. Exploring this field can open up exciting opportunities to help protect digital infrastructure and make a meaningful impact in the world of technology.
Why Study it at Champlain?
Champlain College’s Computer Networking & Cybersecurity program equips you with cutting-edge skills to protect the Internet and the digital realm. Our labs and virtual infrastructure provide hands-on experience in securing sensitive data for individuals and government agencies. You’ll learn to identify network vulnerabilities, implement robust security measures, and defend against cyberattacks.
Our Upside-Down Curriculum allows you to begin taking networking and cybersecurity courses in your first semester, and gain in-depth knowledge over the course of four years. Through projects, internships, and experiential learning, you’ll immerse yourself in the profession and develop skills in designing, building, and securing enterprise networks.
Highlights of our program include extensive training in server software, systems administration, networking, and protocols, all in small-sized classes to ensure a rich and personalized educational experience. Located in a city with ample job opportunities, our program sets you up for success in the field during and after college.
Senator Patrick Leahy Center for Digital Forensics & Cybersecurity
At the Senator Patrick Leahy Center for Digital Forensics & Cybersecurity, you’ll work on network security, cyber threat response, and critical cybersecurity research. In this leading digital lab, you’ll participate in groundbreaking research and support the cybersecurity needs of government agencies and organizations. You’ll play a critical role in developing training protocols for law enforcement and examining the network security of emerging technologies. Through hands-on work at the Leahy Center, you’ll hone your skills as a Champlain cybersecurity student, contribute to the field, and graduate as a cybersecurity professional with real-world experience.

Leading the Way
Our program is nationally recognized and was one of the first programs in the country designated as a Center of Academic Excellence by the National Security Agency and the Department of Homeland Security.
Specialized Cybersecurity Education
With a focus on adapting to the ever-changing landscape and new technologies in the field, our cybersecurity program was built from the ground up as a specialized degree designed specifically for the purpose of cybersecurity education.
Our program was ranked No. 1 by industry experts in SC Magazine’s list of top cybersecurity college programs.
- SC Magazine
Hands-On Experiences
Beginning in your first year, you’ll gain hands-on experience through projects, internships, service to local nonprofits and organizations, and partnerships with industry experts at the Leahy Center.
Facts & Stats
of Computer Networking & Cybersecurity majors in the Class of 2023 achieved career success within six months of graduation. That’s success you can see.
The median yearly pay for networking professionals according to the U.S. Bureau of Labor Statistics .
Cybersecurity students competed against a team of professional hackers in a two-day cyber defense competition during the annual Northeast Collegiate Cyber Defense Competition (NECCDC) taking 2nd place overall.
Sample Courses in the Computer Networking & Cybersecurity Major
Check out some of the engaging and hands-on courses in the program. Our Upside-Down Curriculum puts you in your major right away.
Second Year
Fourth year.
See the Learning Outcomes for the Computer Networking & Cybersecurity major.
SYS 140 Systems Fundamentals
This course will introduce students to operating system concepts and other forms of systems software. Students will learn about standard operating systems functional components such as memory, process/thread, file system, input/output, storage and device management. Additional topics include data representation, imaging, virtualization, and the history/future of systems software. Hands-on experiential learning will be used to reinforce concepts.
SEC 250 Computer & Network Security
This course provides an introduction to computer and data network security. Students will examine the rationale and necessity for securing computer systems and data networks, as well as methodologies for implementing security, security policies, best current practices, testing security, and incident response.
NET 215 Network Protocols
This course is a thorough review of the foundational protocols used on the Internet and modern enterprise networks. With a focus on protocols aligned with the Transmission Control Protocol/Internet Protocol (TCP/IP) and OSI models, students will explore the development and structure of protocols, their role in data communications, and integration within network-based applications. Students will engage in hands-on activities aimed at protocol analysis, network troubleshooting, and protocol-related security concerns.
SYS 265 System Admin. & Network Services II
This project-oriented course focuses on the tasks and issues involved in the administration of distributed computing environments. Authentication, Authorization, and Accounting (AAA) systems are covered, with emphasis on using cross-platform authentication. Network services including host based firewalls, DHCP, DNS, Mail, and Web services are covered. Content includes Enterprise File Services, Distributed administration of multiple systems, and network monitoring and management tools. Hands-on experience will include projects based upon representative technology from each of these areas.
SYS 320 Automation and Scripting
Students will learn how to integrate programming into operating system management. They will learn how to automate systems administration functions and connectivity testing. Powershell and Linux shell scripting will be explored to manage and monitor operating system processes and functions. Students will create programs that can be reused in production networks.
SEC 350 Enterprise and Network Security Controls
Students will examine network-based threats, whether originating from the Internet or the local LAN, and learn about ways to protect, detect, and defend the enterprise network from such attacks. The relationship between user network policy and securing the network will also be explored. Students will participate in hands-on experiments and demonstrate their understanding of subject matter via labs, projects and presentations
CRJ 225 The Law of Searching, Seizing and Using Digital Evidence
Computer evidence (digital evidence) is being used every day in our country to convict criminals of crimes ranging from possession of child pornography to embezzlement to murder. Every competent, modern law enforcement officer understands the significance of digital evidence in every case submitted for prosecution. Students will be required to learn, and apply, legal principles that govern how this vital evidence is recovered (and used) to insure that it will be legally admissible in court.
CSI 320 Global IT & Ethics
Students look at the positive and negative effects of changes and advancements in technology, with particular attention given to the relationships between technology, ethics, culture, and humanity. Through readings, discussions, debates, presentations and other learning methods, students will explore the evolution of technology and ethics. Students will investigate the ways technology is used and how information affects, and is affected by, society and the global community.
You might also be interested in these…
Based on your interest in the Computer Networking & Cybersecurity major, we thought you also might like to check out these other academic programs and opportunities
Digital Forensics
Release your digital investigation skills. Adopt the investigator’s mindset, solve mysteries, and master artifact discovery with Digital Forensics at Champlain College.
Computer Science & Innovation
Help create the digital future. Free your creativity, do real work right away, and fuel your passion for technology and innovation.
Applied Mathematics
Use math to tell stories, crack real-world issues, explore diverse applications, and gain problem-solving skills for future success in many industries.
Criminology & Criminal Justice
Build a better system. Be an agent of organizational change.
Study law as an undergraduate at Champlain College and start your legal education right away, during your first semester. Go on to law school afterward or choose a different path; either way, you’ll be ready.
Computer & Digital Forensics Minor
Analyze digital information, navigate the realm of digital security, and form a strong foundation working with computers in the Computer & Digital Forensics minor.
Computer Science Minor
Analyze problems, develop software systems, and use a variety of tools to evaluate computer programs and bring your innovations to realization in the Computer Science minor.
Information Technology Minor
Identify core computer networking and infrastructure components and the roles they serve to supplement business, finance, creative, and other professional pursuits.
Law Minor
A strong base understanding of law and the legal system is a valuable asset to any résumé. Tailor your classes to focus on the specific kind of law that applies to your chosen career and get ahead.
Criminal Justice Minor
Justice at all levels is a keystone of a functional society. Learn the criminal justice process at multiple levels and how your knowledge of this system can benefit your career.
Cybersecurity, Computer Science & Digital Technology
Solve everyday problems to build a better future.
Law & Society
Uphold a system of justice through meaningful public service.
Individualized Studies & Undeclared
Learn what you love, and love what you learn.
Business & Data Analytics
Drive change at the intersection of information and impact.

Since 2007, Champlain College has proudly held a Cyber Defense (CAE-CD) designation, which is renewed periodically. Our cybersecurity curriculum meets the rigorous criteria set by the NSA, FBI, and Department of Defense, helping to strengthen the nation’s information infrastructure. As an active participant in the NCAE program, we set a high standard for cybersecurity education, producing confident professionals with extensive cyber defense expertise.
- Visit the NSA’s Website
- Visit the CAE Community Website

Cybersecurity Advisory Board: Leading education with industry engagement
Composed of external experts, this group provides Champlain with guidance on educational objectives, learning outcomes, and preparing students for the evolving cybersecurity workforce. The board also evaluates the quality of experiential learning and internship opportunities, with members representing various industry sectors.

Seamless Transition to Grad School
Are you thinking about going to graduate school? Through Champlain College Online, you can seamlessly go from undergraduate to graduate student, enhancing your skills and career opportunities.
Sign Up To Get Stickers + Helpful Info

Ready to be inspired? Fill out the form and sign up to receive helpful information about Champlain College—plus, we’ll send you a full sheet of high quality stickers designed by one of our Graphic Design & Visual Communication graduates.
Career Success
The Computer Networking & Cybersecurity program prepares graduates for the workplace. 97% of CNCS majors in the Class of 2023 were employed within six months of graduation.
- Internships
- On-Campus Employment Opportunities
- Study Abroad

Your Career Outlook
Learn more about our career-focused education
By the time you graduate, you will…
- Have a solid grasp of cybersecurity fundamentals and be able to analyze architectures, identify vulnerabilities, and recommend controls to mitigate threats.
- Have hands-on experience configuring and managing security controls, such as configuring host firewalls, user access controls, intrusion detection and prevention systems, and encryption mechanisms at various levels.
- Have a deep understanding of networking protocols, such as Open Systems Interconnection (OSI) and Transmission Control Protocol/Internet Protocol (TCP/IP), and how they facilitate communication between networked hosts and applications. Be able to design and implement network solutions based on business requirements.
- Understand the components and roles of computer systems, including CPUs, memory, storage, and networking. You will be able to manage operating systems, network services, and security controls to troubleshoot problems and ensure optimal performance.
- Develop strong teamwork and communication skills. You will actively collaborate with others as a member or leader of project-based teams and learn how to effectively communicate technical information through formal documentation, presentations, and interpersonal interactions.
You’ll Find a Career In…
- Network Engineering
- IT Security and Cybersecurity
- Cybersecurity Consulting
- Security Operations and Incident Response
- Systems Architecture
- Digital Forensics
- Cloud Security Engineering
Latest News from The View

Cybersecurity Partnership Gives Students A Unique Opportunity

Women in Cybersecurity Conference: If They Can Do It, So Can I

Champlain College Named Best Cybersecurity Higher Education Program

Senator Leahy Tours The Leahy Center for Digital Forensics & Cybersecurity
More inside computer networking & cybersecurity, overview , curriculum .
With our Upside-Down Curriculum, you'll get hands-on learning in web technology, networking, and security, as well as valuable experience through internships.
Faculty
Our Computer Networking and Cybersecurity faculty go above and beyond to inspire your curiosity, learning, and growth. Small class sizes foster personal connections and mastery.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 23 May 2024
Integrating blockchain and ZK-ROLLUP for efficient healthcare data privacy protection system via IPFS
- Shengchen Ma 1 &
- Xing Zhang 2
Scientific Reports volume 14 , Article number: 11746 ( 2024 ) Cite this article
1 Altmetric
Metrics details
- Electrical and electronic engineering
- Engineering
With the rapid development of modern medical technology and the dramatic increase in the amount of medical data, traditional centralized medical information management is facing many challenges. In recent years blockchain, which is a peer-to-peer distributed database, has been increasingly accepted and adopted by different industries and use cases. Key areas of healthcare blockchain applications include electronic medical record (EMR) management, medical device supply chain management, remote condition monitoring, insurance claims and personal health data (PHD) management, among others. Even so, there are a number of challenges in applying blockchain concepts to healthcare and its data, including interoperability, data security privacy, scalability, TPS and so on. While these challenges may hinder the development of blockchain in healthcare scenarios, they can be improved with existing technologies In this paper, we propose a blockchain-based healthcare operations management framework that is combined with the Interplanetary File System (IPFS) for managing EMRs, protects data privacy through a distributed approach while ensuring that this medical ledger is tamper-proof. Doctors act as full nodes, patients can participate in network maintenance either as light nodes or as full nodes, and the hospital acts as the endpoint database of data, i.e., the IPFS node, which saves the arithmetic power of nodes and allows the data stored in the hospitals and departments to be shared with the other organizations that have uploaded the data. Therefore, the integration of blockchain and zero-knowledge proof proposed in this paper helps to protect data privacy and is efficient, better scalable, and more throughput.
Similar content being viewed by others
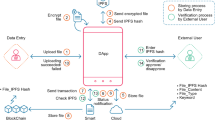
SVBE: searchable and verifiable blockchain-based electronic medical records system
Blockchain vehicles for efficient Medical Record management
Federated blockchain system (FBS) for the healthcare industry
Introduction.
After decades of development, healthcare management systems 1 have hitched a ride on the great wave of Internet development and have made tremendous progress in various technologies, including front- and back-end. Naturally, this has facilitated the development of traditional record-keeping methods for patient management, diagnosis, treatment, equipment management, and so on. However, electronic medical records or electronic personal healthcare 2 data is the trend, the maintenance of EMR 3 , EPHD is one of the important tasks of hospitals at this stage, not only its lies in the protection of patient privacy aspects, but also in the academic exchanges of hospitals with each other, the ultimate beneficiaries of the data flow is still the patients themselves, so it is necessary to solve the problem of data silos as an important issue in order to provide patients with quality services, accurate diagnosis and treatment. In summary, the contributions are summarized as follows:
This article combines traditional blockchain with IPFS network and proposes a scalable medical data privacy protection framework, which can ensure data security while enhancing data utilization.
This article focuses on data and makes all processes serve data. Although the power of doctors is appropriately increased, submitting smart contracts for identity verification ensures security. At the same time, standardizing the medical data process in the model eliminates the problem of data silos in academia. We also found that this model produces better results, especially in relatively closed scenes.
Under the same gas, our method outperforms other methods in terms of gas consumption and speed. Multiple experiments have shown that the proposed method has better applicability and lower consumption compared to cloud services and other scaling methods.
Traditional systems
Traditional healthcare systems 4 are highly centralized with multiple data privacy and security risk factors. It may act as a single point of failure paving the way for potential losses, data, tampering, alteration of records, etc. due to which the data is centralized. For organizations, a patient may need to repeat the same test when he goes to another hospital leading to financial loss. Policies and data standards followed by different organizations vary widely, hampering interoperability between organizations. Data breaches have been documented in the past in various healthcare organizations. This requires better healthcare data infrastructure. Some of the studies conducted have concluded that healthcare systems have become active targets of cyber attacks 5 by malicious adversaries. The presence of healthcare data in a centralized client–server architecture within an organization makes it very challenging to collaborate with data across various providers.
Cloud based
The centralization of data in the traditional model suffers from accessibility, scalability, privacy and security issues; it also acts as a single point of failure with limited recovery options. Cloud computing 6 comes to the rescue and allows healthcare networks to store their data in the cloud infrastructure, which solves the accessibility, scalability and some privacy and security-related constraints. Patients and organizations such as hospitals retrieve patients’ health data remotely through cloud-based servers. Cloud-based systems may offer several advantages over traditional healthcare systems; however, they still have potential risks due to centralization. Unauthorized agencies may have access to cloud-based systems, which could affect the privacy and security of stored data. Another aspect is that cloud-based approaches fully trust third-party 7 cloud service providers, allowing them to manage access control permissions for patient-generated health data. Healthcare data is very sensitive and cloud providers may utilize it for commercial gain without patient’s consent. The centralized nature of the cloud infrastructure could lead to potential bias and corruption when disputes arise between stakeholders such as patients, healthcare providers, and research organizations.
Necessity of healthcare requiring blockchain
As the healthcare industry continues to grow, the volume and importance of healthcare data continues to increase. However, the traditional centralized storage method has a high risk of leakage. Blockchain technology 8 can achieve the protection of medical data through decentralization. First, data backup can be established using blockchain technology, avoiding the risk of data loss due to the failure of a single node. At the same time, due to the distributed nature of blockchain, data can be stored on multiple nodes, increasing the security of data. Secondly, blockchain technology can realize data encryption. By using advanced encryption algorithms 9 , medical data can be encrypted and stored to ensure that only authorized people can access and manipulate the data. Blockchain technology combines advanced encryption algorithms to encrypt and store medical data. Through the setting of public and private keys, only authorized people can access and manipulate the data. This mechanism effectively protects the privacy and rights of patients and avoids data leakage and misuse. At the same time, it also sets a higher standard of trust for healthcare organizations, providing a strong guarantee for the healthy development of the healthcare industry and the safety of patients’ data. In addition, blockchain’s smart contracts 10 can be used to restrict data access and operating privileges, avoiding unauthorized access and data leakage. As the data on the blockchain is not tamperable, data can be avoided from being maliciously modified or deleted. Meanwhile, using smart contracts on blockchain, automatic verification 11 , sharing and exchange of data can be realized through set rules, which improves data interoperability between different healthcare institutions and ensures that only operations that comply with the rules can be executed, thus protecting the authenticity and integrity of data. In conclusion, it is of great significance to use blockchain technology to address the risk of leakage of centralized medical data. In addition, smart contracts can be used to automate the payment and sharing of data, bringing more business value to the healthcare industry. These features provide a more convenient way for collaboration between medical institutions, which is conducive to the optimal allocation of medical resources and the enhancement of the patient experience. In short, the security and reliability of medical data can be greatly improved by establishing data backup, realizing data encryption and ensuring data integrity. In the future, with the continuous progress of technology and the expansion of application scenarios, it is believed that blockchain technology will play a greater role in the medical field.
Blockchain fundamentals in healthcare sector
Merkle tree.
Merkle Tree (Merkle Tree) is a data structure based on blockchain technology that allows us to group large amounts of data into a tree structure, making it possible to verify the integrity of the data without having to download the entire dataset in its entirety. Merkle trees work by grouping and hashing raw data and then recursively linking these hashes together to form a tree structure. Each node contains the hash values of its children, and each node’s hash value is derived by hashing its children. In this way, the hash value of the root node represents the integrity of the entire data set. In a Merkel tree, any change in the data results in a change in its hash value, so the integrity of the data can be verified by simply comparing the hash values of the root nodes of two Merkel trees 12 . If the root node hashes of the two Merkel trees are the same, then they represent the same data set. If different, then at least one of the datasets is incomplete. Merkle trees have a wide range of applications in blockchain technology, such as in cryptocurrencies like Bitcoin 13 and Ether, where they are used to verify the legitimacy and security of transactions. Also, Merkle trees can be used for distributed storage and data integrity verification, among other things.
Time stamping
Time stamping 14 technology is an important mechanism used to ensure data integrity and security. It ensures the immutability and authenticity of data by adding a time stamp to the data and associating the data with a specific time. In this article, we will introduce timestamping technology in blockchain in detail. The main application area of timestamping technology is to record and verify the existence and time of occurrence of data. It can be used in areas such as copyright protection of digital files, precise recording of the time of occurrence of events, digital twins, etc. Timestamping technology is particularly important in blockchain technology because the blockchain itself is a distributed ledger that needs to ensure the authenticity and tamperability of all data. Timestamping technology works by binding data to time to form a timestamp. This timestamp is generated by multiple nodes of the blockchain network, each of which has a local clock and is involved in the timestamp generation process. Specifically, when a transaction is added to the blockchain, in addition to the transaction itself, it will include information such as the hash value of the previous block, the timestamp, and a random number. Together, this information is packaged into a new block and added to the blockchain. Since each node’s clock is independent, timestamping ensures that all nodes have recorded this transaction information at the same point in time. Timestamping technology has a wide range of applications. For example, in the field of copyright protection, timestamps can be used to mark the creation time and copyright attribution of digital files; in the field of healthcare, timestamps can be used to record the patient’s condition and the doctor’s diagnosis results to ensure the authenticity and tamper-proofness of the medical data; in the field of finance, timestamps can be used to record detailed information about the transaction to improve the security and transparency of financial transactions. The advantage of timestamping technology is that it can effectively ensure the integrity and security of data. Since timestamps can associate data with a specific time, they can prevent data from being tampered with or falsified. In addition, timestamps can be used to track the origin and destination of data, thus helping people to quickly locate problems and take appropriate measures.
POW (Proof of Work) 15 is a common consensus algorithm that earns the right to add a new block by requiring participants to prove their workload by solving an intractable mathematical problem. In a blockchain network, when a node wants to add a new block to the chain, it needs to first verify that the transactions in the block are legitimate and that the block conforms to the rules of the blockchain network. If the node cannot verify this information, then it will be denied to add a new block to the chain. The node also needs to generate a new block by solving an intractable math problem and broadcast the block to other nodes. The other nodes will validate the block to ensure that it complies with the rules and protocols of the blockchain network. If the block passes the validation, then it will be added to the chain. In order to prevent malicious nodes from attacking the blockchain network, the POW consensus algorithm constantly increases the difficulty of the math problem 16 . This makes it necessary for malicious nodes to pay more time and computational resources to solve the math problem, thus increasing the cost and difficulty of the attack.
Public and private keys
Asymmetric encryption plays a crucial role in blockchain technology. It provides security and trust mechanisms for the blockchain, allowing us to use digital assets for transactions and storage with peace of mind. Asymmetric cryptography is based on public and private keys 17 . The public key is publicly shareable and can be used by anyone to encrypt messages or verify digital signatures. The private key, on the other hand, is highly confidential, accessible only to the owner, and it can be used to decrypt messages or generate digital signatures 18 . In blockchain transactions, the use of public–private key pairs provides security for participants. When a participant wants to send an asset to another participant, he can use his private key to sign the transaction and broadcast the signed transaction to the entire network. The receiver can verify the legitimacy of the transaction using the broadcasted transaction and the sender’s public key. If the verification is successful, the transaction is considered reputable and the asset transfer is confirmed and added to the blockchain. Another application of asymmetric encryption in blockchain is to achieve anonymity and privacy protection. The nature of public and private keys allows participants to protect their privacy and identity. The use of public keys for transactions allows others to verify the legitimacy of the transaction, but there is no way to know who initiated the transaction. The confidentiality of the private key allows only the true owner to access and manipulate the asset.
Related work
Nguyen et al. 19 Technologies such as blockchain, sidechain, cloud platform, and IPFS are shining in various fields, especially in the IoT industry, where blockchain is deeply bound to it. The proposed framework utilizes distributed technologies such as blockchain, exploits the potential of sidechain, provides reliable access control through smart contracts and ensures system security. Its evaluation methodology highlights performance improvements to the blockchain, cuts down on network consumption, and greatly improves the security of the system. Meanwhile, the framework can be extended, but using third-party cloud services can lead to trust or mischief issues, and when the content service provider is not fully trusted, the data can be easily tampered with and the system can be in danger. In different scenarios, the use of blockchain to solve different problems, in this article, although the deployment of the system on cloud services is a centralized behavior, but all other indicators are more efficient and faster than the general decentralized system architecture 20 , then so in some of the areas where decentralization is not too important, can make a big difference 21 . This thesis provides a patient with a treatment log, which is trusted, while accessing it is uncomplicated, participants can make changes to the medical data, and privacy is ensured by utilizing smart contracts for participant interaction. Using blockchain technology, MedRec demonstrates how the principle of decentralization can be applied to large-scale data management in electronic medical record systems. But one of its drawbacks is that the component about miners is not very clear. Also the generalization of the framework is not yet well developed 22 . This article utilizes blockchain technology to deal with the problem of data management in electronic medical record healthcare systems. Patients can easily access the medical records of different hospitals through its framework, thus eliminating the data silo problem, and the interaction through blockchain can help the doctors of the hospitals to have first-hand data to understand the patient’s medical history during consultation. The proposed blockchain-based efficient privacy protection scheme utilizes access control protocols and encryption to ensure data security. Its feature of not uploading data to a third party increases security. However, this framework has a more important problem that needs to be solved urgently, that is, it doesn’t use smart contracts to process the data but directly uses the blockchain to solve it, which creates a problem that the TPS will be very low, and at the same time, the ability to process the data is very inefficient because the throughput of the framework with no off-chain storage is only about a dozen of transactions per second, so the speed is a hard hit.
This solution also uses the blockchain + IPFS architecture to process data, where the advantages are similar and the disadvantages are also similar. Again, the lack of integration of smart contracts leads to a low TPS 23 .
In this paper, blockchain technology is combined with an attribute-based access control model, which makes full use of blockchain technology to break the information silos in medical data, and safeguard the security and privacy of medical information 24 . In addition, the star file system is used for storage to alleviate the storage pressure of blockchain. The article also utilizes smart contracts to process data in specific intervals, but its IPFS is only an alternative to the on-chain space and another as a distributed database, which only alleviates the problem of small throughput and does not actually solve it, which is of course its focus to be researched in the future 25 . The paper proposes a user-centric healthcare data-sharing scheme for privacy-preserving machine learning, which implements encrypted data storage, blockchain-based data resource allocation, data authorization, and machine learning model training. It also designs an auditing mechanism to help users audit the data-sharing process. Compared with existing schemes, our proposed scheme ensures the privacy and security of user data, guarantees user data ownership, and achieves data exclusivity and non-visualization. Finally, the functionality of the solution is realized through simulation experiments, and the experimental results prove the feasibility and effectiveness of the solution. But throughput is also an urgent problem for this article 26 . It focuses on the blockchain-based medical data-sharing solution and proposes the B-SSMD system solution. By combining the three-chain model with IPFS technology and adopting the method of storing data on the chain and indexing paths of the chain, it realizes highly distributed data storage and solves the defects of centralized storage in traditional medical systems. In addition, using three-layer encryption and fine-grained access control, the P/MSISP data-sharing process is proposed to protect user privacy and improve data security. Finally, the security analysis proves that the paper’s scheme is secure, and simulation experiments demonstrate the feasibility. For further research work, one possible improvement is the transferability of the B-SMD system. How to use the triple-chain model to solve the data sharing problem not only in healthcare environment but also in other scenarios is a future work that can be explored. However, in this framework, its three-layer encryption and fine-grained access control are slightly redundant. The cost of more processes is high network consumption 27 . In the model proposed in this article, the access control mechanism is a good choice to reach the purpose of data sharing security, but the limitations of scalability and expansion mechanism lead to the low throughput of this model, and consequently the usability is not as high 28 . Unlike other articles, the framework in this article, gives the data owner to the patient, which has the advantage of opening access to its own data based on choice, but this breaks the rules of sharing. At the same time, its efficiency in terms of expandability, data availability, and security gets reduced to different degrees.
This paper proposes a holochain-based privacy-preserving secure communication scheme for distributed IoT healthcare applications, which utilizes the inherent autonomy of the holochain architecture and protocol 29 . Contrary to blockchain, holochain frees communication agents from any form of centralized control by running applications (hApps) entirely on the user’s end. As a result, there is no central point of failure. Comparative performance results and analysis show that the time and space complexity of the new chain framework is significantly reduced compared to competing blockchain solutions, suggesting the promise of real-world deployment of large-scale IoT healthcare systems. Although the problem of processing GAS in real-time has not been effectively addressed, the paper breaks with tradition and the efficiency of the newly proposed model is indeed improved 30 . The proposed method is based on the availability and accessibility characteristics of blockchain for distributed service response. The proposed method is based on the availability and accessibility characteristics of blockchain, which will be used for distributed service response. There has been a breakthrough in IoT, but the consensus mechanism has been a headache for non-arithmetic devices 31 . Disease prediction is also more effective than other deep learning models as the proposed model yields higher prediction accuracy. But fails to consider data protection issues and other attacks in lost data scenarios, though its combination with deep learning models is a highlight 32 . This framework discusses privacy issues in the rapid establishment of medical progress monitoring in decentralized communication systems in the medical Internet of Things. It adopts a hybrid hash design and integrates homomorphic encryption algorithms to support smart contracts with decentralized applicability. The proposed method has high mobility.
As shown in Table 1 , the attributes and characteristics of some references are listed, from which it can be seen that the existing methods have some shortcomings in various indicators, but the control of access and distribution are basically necessary, and many of them increase the speed, but also lead to the ultimate problem in the blockchain expansion.
As shown in Fig. 1 , the trilemma. it can be seen that if both decentralization and scalability are considered, security must not be guaranteed. In fact, all papers in related work guarantee security, but because they all have this commonality, they are not reflected in the table. Therefore, while ensuring security, scalability or decentralization must be abandoned to ensure the completeness of the other feature.
Scalability trilemma.
Components of proposed decentralized storage
IPFS (InterPlanetary File System) is a peer-to-peer distributed file system designed to change the way files are stored and transferred on the Internet. Unlike traditional file systems, IPFS uses content addressing to identify and retrieve files, rather than being based on file paths. The basic concept of IPFS is to store files in chunks and generate unique fingerprints (hashes) for each file chunk. These fingerprints are used as addresses for the files rather than file paths based on the server and directory structure. This means that identical blocks of files will only be saved once, no matter how many users request access to them, thus increasing file-sharing efficiency and reliability. IPFS utilizes a distributed network model in which nodes communicate with each other and replicate data via a coherent protocol. Each node can store and transfer blocks of files without the need for a centralized server. When a node requests a file, it looks up the file’s blocks by hash value and fetches the required data. If a node is offline or unable to provide file blocks, IPFS automatically looks for other nodes to get the required data. Interplanetary File System (IPFS) 33 is a sub-protocol package and project driven by Protocol Labs.IPFS is designed to improve the efficiency of the network and make it more decentralized and resilient.IPFS uses content-based addressing, where content is not addressed by its location but by its content.IPFS achieves this through its deduplication feature of storing and addressing data in a manner that efficient storage of data. With IPFS, files can be stored and shared in a decentralized manner, increasing the resistance to censorship of their content.IPFS can be deployed to build websites with a distributed web. It is used as a storage service that complements the blockchain by supporting different applications on top of IPFS. Since IPFS uses content-based addressing, it focuses primarily on immutable data. However, IPFS supports updatable addressing of content through the Integration of the Interplanetary Name System (IPNS).IPNS allows to link a name (a hash of a public key) to the content identifier of a file. IPNS entries are signed by a private key and can be arbitrarily (re)published to the web (default 4 ℎ ). Each peer maintains its own LRU cache of parsed entries (default 128 entries). IPNS entries have a specific lifetime, after which they are deleted from the cache (default 24 ℎ ). File updates can be achieved by changing the mapping of fixed names to content identifiers. Note that content identifiers are unique and file-specific. In addition, IPFS uses its own incentive layer, Filecoin 34 , to ensure the availability of files in the network. However, IPFS works independently of Filecoin and vice versa. This is a typical example of how cryptocurrencies can be integrated to incentivize peers.
ZK and ZK-rollup
ZK Proof Using cryptography allows someone (the prover) to prove to someone else (the verifier) that the facts are 100% true, but without revealing any additional information beyond the statement of specific truth. That is, it can be kept secret and still be believed. For example, a ZK proof 35 can be used to prove the validity of an Ether transaction that sends a Token from Account A to Account B without revealing the Token balance of either account or the amount sent. The next is ZK-rollup. The principle is to compress and store the user state on the chain in a Merkel tree, and dedicate the changes of the user state to the chain, and at the same time, guarantee the correctness of the user state change process under the chain through the proof of ZK-snark/ It is costly to deal with the changes of the user state directly on the chain, but costly to utilize the smart contract to verify the correctness of a zero-knowledge proof of the PROOF, and the transfer information and the proof will also be submitted to the smart contract together. The transfer information and proof will also be submitted to the smart contract together to facilitate the checking of accounts.
Simple Non-Interactive Knowledge Base (SNARK) allows to provide verifiers concise proofs, i.e., proofs that can be verified in logarithmic time. There have been many improvements to this type of scheme since the first practical protocol. In particular, Groth allows to provide fixed-size (less than 200 bytes) proofs that can be verified in constant time, regardless of the program to be proved. The main drawback of this scheme is that it relies on a trusted setup that must be performed for each different program, resulting in a common reference string 36 (CRS), also known as the verifier and prover keys. The verifier key is sometimes different from the prover key, since precomputation can be performed for the verifier. The prover key is the same as the CRS. Even if SNARK is subject to a trusted setup, it is possible to divide the trusted setup into two parts: one part that depends on the program to be checked but has no trusted third party, and another part that is independent of the program and on which security is based. This independent part can consist of several participants, distributes security among them, and can be used for any program up to a certain number of operations. The result of this multiparty protocol is the same as the classical trusted setup, but trust is no longer based on a single participant. The idea is that security can be ensured if at least one participant is honest during the ceremony. Repeated use of completed rituals that include many well-known people helps build confidence in this model.
The Scalable Transparent Knowledge Base (STARK) differs from SNARK in the lack of a trusted setting. Scalability also implies that, in addition to being logarithmic in verification time, like SNARK, STARK must also be at most linear in proof time. Furthermore, STARK relies only on the properties of hash functions and Reed-Solomon codes, which makes them post-quantum (post-quantum cryptography aims to secure information against attackers equipped with quantum computers). However, STARK is the most recent proposal, and due to its proof length, more research is still needed to compete with SNARK in certain areas, and more precisely in blockchain.46267267.
Proposed model
The proposed model ensures that the rightful owner has the required access control over their health data, in our case the patient. Patients use cryptography applied within the system to protect their data from unauthorized access, misuse or fraud. Patients don’t need to know how cryptography works or how encryption is done. They can use the front-end system like any other web application and provide access to the physician/hospital entity when needed. When the access is over, they may revoke it. In this way, any user with basic computer knowledge can join this proposed network and protect their health data. All the cryptography, consensus mechanism, storage and retrieval is done within the system by design. Figure 2 shows the integration of blockchain with IPFS, while data generated by individuals or hospitals is given to TX Batch, and then this data (TX) is uploaded to a zero-knowledge proof smart contract, and the index of the aggregated information is placed on the main chain, with the specific details of the data being held by IPFS together with the smart contract (there is a high degree of freedom, there is no focus, and it doesn’t matter which one stores more or less).
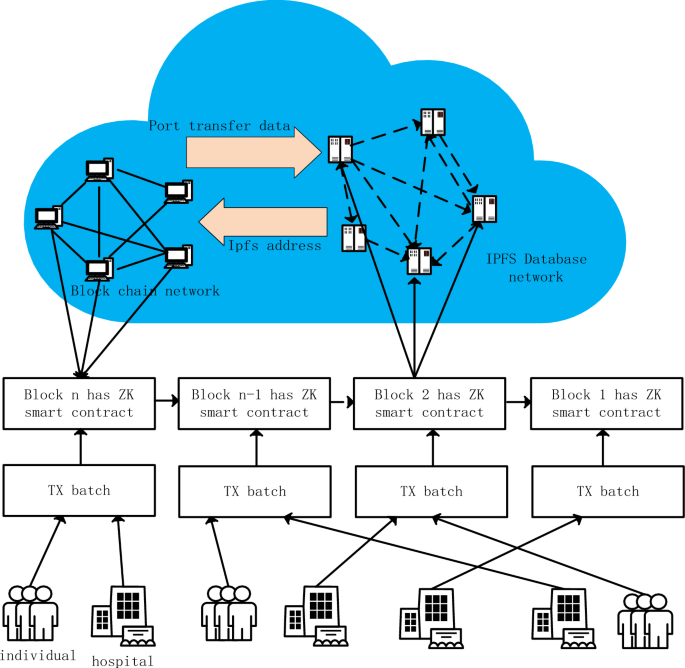
Framework overview and process.
Figure 2 shows the integration of blockchain and IPFS, while providing personal or hospital-generated data to TX Batch, which is then uploaded to a zero-knowledge proof smart contract, and the index of aggregated information is placed on the main chain. The EMR generated by communication between patients and doctors is directly written into it as key-value pairs according to scientific research needs or all settings. Doctors directly upload the file to the IPFS network through command-line tools or customized client software to obtain the corresponding CID (content identifier). But it is connected by the main chain in the middle, and users call the smart contract deployed on the Ethereum main chain and provide it with the CID obtained from IPFS and any related metadata or transaction information. Smart contracts may include logic to verify the validity of CIDs, such as checking for existence in the IPFS network, or performing operations involving file ownership transfer. Afterward, relevant transactions are submitted to ZK Rollup through the Layer 2 interface, including CID, transaction details, and zero-knowledge proof (proof that the files have been successfully stored on IPFS). ZK Rollup batch processes these transactions and generates validity proofs, and then writes the summary results and proofs into the Ethereum main chain. The following is the classification and detailed division of labor of nodes in this process. (In Fig. 2 , individuals and hospital can refer to individuals and organizations. In this article, individuals refer to patients and doctors, aiming to emphasize universality.)
Doctor nodes
The doctor node is different from the hospital node in that when a patient visits the hospital, a non-contested electronic medical record is generated according to certain rules, which is uploaded by the doctor to ZK’s smart contract and signed with his own private key, and then transmitted to the main chain through the smart contract. When the doctor visits or performs other activities that require reading medical data, he or she has to upload a smart contract that merely verifies his or her identity to prove that he or she is not an evil node, thus ensuring the security of the data. And then a series of operations such as adding, deleting, changing and checking can be performed. Doctors must be full nodes, although the data does not belong to anyone, patients and doctors have the right to use it, but the patient nodes do not need to be deeply involved in the construction of the network, and need the doctor nodes to maintain the operation of the blockchain. In addition, the doctor node is a contract user, each doctor has to interact with various contracts, so it must be a contract user, although there is a generated public and private key, but the key account is not in the scope of consideration.
Patient nodes
Half of the patient nodes are light nodes 37 unless there are special requirements, they are necessarily light nodes because they join the network generally temporary, most people use this network for less than a few hours or more than a few days, and the depth of participation is not enough, so they can only carry out the release of their own medical data and modify the transaction according to the doctor’s recommendations. Of course, the generation of electronic medical records is also based on the medical recommendations of doctors. But this data belongs neither to the patient nor to the hospital; the data is just data, it just happens to be medical data. In addition, every patient is a contract user and interacts with contracts, especially ZK contracts. They are not full nodes and therefore only store block headers.
Hospital nodes(IPFS)
The hospital node is different from the doctor node, its main function is to maintain the system operation, provide arithmetic power, so that the whole system has a strong robustness, so the hospital node is necessarily a full node. It is equivalent to a Server in C/S architecture, but in this system it is decentralized, no institution or unit can be the traditional centralized database, only the blockchain serves this job. After the data OR transaction is uploaded to the chain by the smart contract, the returned summary will exist in IPFS, which not only improves the uploading speed but also ensures the security of the summary taken back from the blockchain and placed in IPFS after hashing.
Overall, the nodes that perform ZK are not a particular class of nodes, but rather nodes that have the ability and arithmetic power to perform ZK. Some of the patient nodes, all of the doctor nodes, and the hospital nodes are ZK nodes, in contrast to the patient nodes, which sometimes have too little depth into the system and variable time to complete ZK proofs in real-time. Individual contracts on the main chain are used to hold all the money and keep a concise cryptographic promise that points to the state of the "sidechain" (typically a Merkle tree of accounts, account balances, etc.)
Data flow and process
The following is a description using pseudocode.

Submit transactions through the API or SDK provided by ZK Rollup await ZK-Rollup.submitTransaction (userWallet, functionCallData);
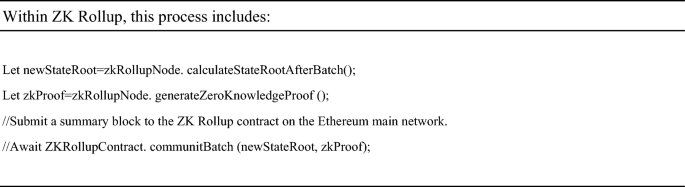
At this point, the smart contract on the Ethereum main chain will verify the proof and record the new state root. a) Add the transaction to the state machine of Layer 2 and wait for batch processing b) Generate a proof of validity for this transaction using a zero-knowledge proof algorithm.(Next is the logic of the ZK Rollup layer, and doctors usually do not directly participate in this step).When a batch of transactions is completed, the ZK Rollup node will calculate a new state root and proof.

It includes applying transactions to the state tree and then generating proofs using the zk SNARK toolchain. Submit the compressed state and proof to the ZK Rollup smart contract on the Ethereum main network. ‘The submitBatch’ method is fictional and may involve multiple steps in practice, such as packaging the proof of multiple transactions into one batch, verifying batch integrity, and executing specific commit functions on the chain. After verification, the smart contract will update its stored latest status root. In this way, the Ethereum main chain only stores a small amount of validity proof data, while most of the calculation and transaction data is retained on Layer 2, thereby improving the scalability of the entire system.
Figure 3 shows some specific processes. a good random source generates the public and private keys (RSA is used in the experiments and can be replaced depending on the actual.) Distributed to the patient and the doctor so that they each keep their own information, based on the visit information, the doctor determines the EMR, according to the order of uploading the data was submitted to the ZK Smart contract, after the contract processing, after queuing to the Ethernet main chain, at this time the information on the Ethernet is just the index (summary) of these data. Later, the index of these data can be placed in IPFS to further free up the contents of the chain and keep the data flow smooth.
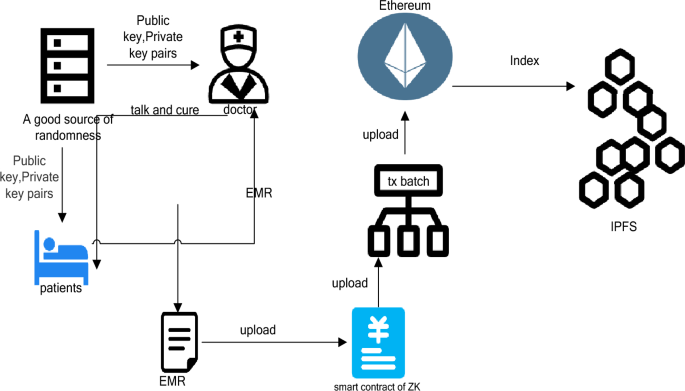
Data process details.
Figure 4 shows the process when either the patient or the doctor seeks medical data, by uploading their own proof of public–private key pairs to ensure their legitimacy and security, and then the request will be processed in the contract, and after submitting it to the main chain to generate an index, the index can be used to look for the required data in the framework.
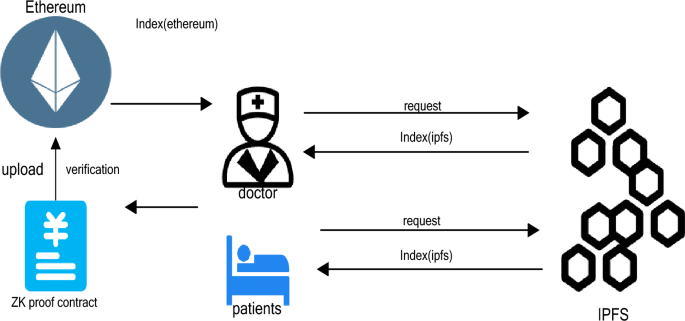
Patient and doctor node interaction with blockchain and IPFS network.
Performance evaluation
The metrics in Fig. 5 show the response time in cloud servers, other blockchains with authentication methods i.e., the model proposed in this paper for different numbers of REQUESTS, the response time varies due to the different locations of the cloud servers, in this paper Amazon cloud is used in the experiments.
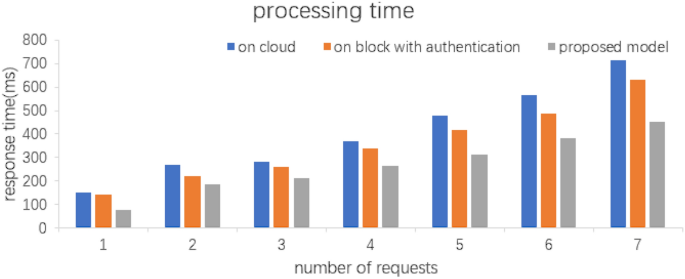
Comparison of processing time.
The metrics in Fig. 6 show the number of transactions the system can handle as the number of blocks grows, which doesn’t work well because Ether is simply too inefficient.
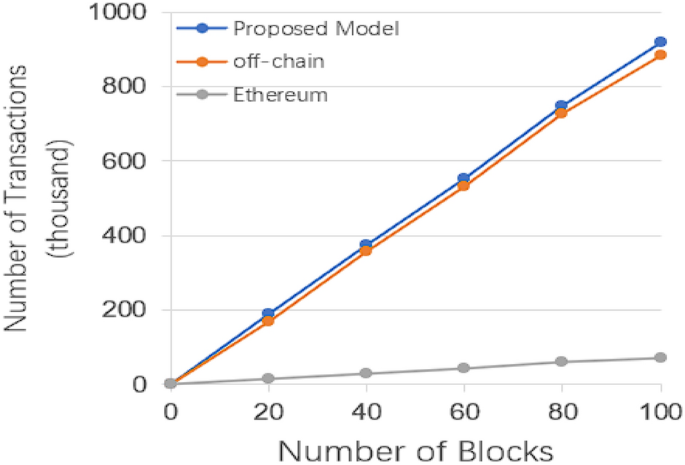
Number of transactions that can be handled by the number of blocks in different ways.
Figure 7 demonstrates that the proposed model is less delayed and faster for a fixed amount of data, and the distributed storage is general blockchain integration IPFS, which is not too inefficient.
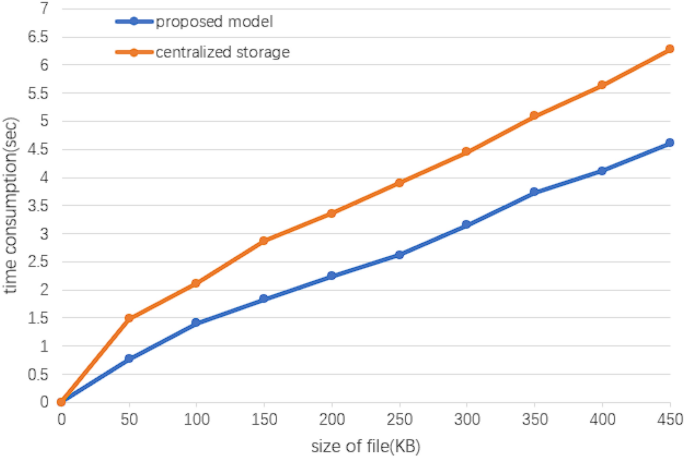
Response time in processing data.
Figure 8 shows the number of transactions corresponding to several data processing methods under the same gas fee. The proposed model mainly depends on the consumption of the verification part when submitting ZK proof. Plasma is another popular expansion method, and its fraud-proof time (usually at least one minute, which can be roughly understood as one block per minute) is a weakness in blockchain networks. Therefore, this article did not use the comparison with Plasma in terms of time. At the same time, through experiments and testing, the average gas consumption using Ethereum reached 22–25 wei, and the number of processed data was around 1500. At its peak, the gas consumption could even reach $100, which is approximately 0.04 ETH or 40 million wei.
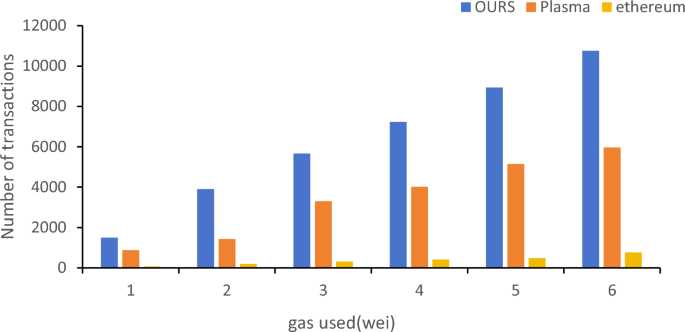
Comparison of Number of transactions under the same gas-used scenario.
We chose the evaluation indicators based on the following reasons: firstly, reaction time is one of the necessary indicators, which directly reflects the superiority of the model or module. At the same time, it is necessary to demonstrate the scalability of the model, so that the number of blocks and transaction volume can prove the volume that the model can accommodate. Secondly, the storage rate per unit file size is also of concern to us. Finally, uploading more data and transactions with the same gas fee is a crucial part of the entire blockchain research, and we have included it in our evaluation metrics.
Conclusion and future work
In order to efficiently manage EHRs in a healthcare data network, a blockchain-based ZK-rollup framework is introduced and integrated with IPFS 33 , both of which are used for off-chain storage in the framework. The framework enables EHR storage to secure data in a decentralized architecture. Instead of being patient-centric or institution-centric, we let the system itself store the data and let the data belong to the data. The built-in design of the blockchain provides security and privacy through the effective application of cryptography. An additional layer of security is provided by storing encrypted data in IPFS storage. The encrypted EHRs are present in the smart contract and the data after the contract is uploaded to the chain is placed in IPFS, making the system lightweight yet efficient. The paper combines the scalability of IPFS and ZK-rollup to propose a network operation model with the ability to handle a large amount of data, which can directly find a good random source assigned to the doctor’s public–private key, and the whole system stores all the data, and there is no trustworthy third party involved, so that there is no need to worry about privacy leakage. Then verified by experiments, the results show that the algorithm in this paper can effectively verify the roles that need to apply for additions, deletions, and checks to ensure security. The limitation of this system lies in its popularity due to the relatively complex operating environment and lack of integrated configuration files, making it temporarily difficult to operate. From a system perspective, the underlying principles of expanding the system are all based on Ethereum, so some functions are difficult to implement without being constrained by Ethereum, such as the time of smart contract on chain, and so on. At the same time, the system has a mechanism that needs to be improved or perfected. If NFTs are added, it will greatly save time in verifying roles, but how to use them as credentials remains to be experimented with. For future work, our team will consider whether the verification process is faster and more efficient if we utilize the NFT 38 participation verification approach. At the same time, smart contracts are more emerging than blockchain, the standard is still not perfect, and the mainstream is now mainly dominated by the Ethereum standard, so the arithmetic problem of ZK and some other minor problems still exist, and there are still metrics and techniques that have not yet been evaluated outside of the experiments. Finally, a model for integrating blockchain technology with machine learning and artificial intelligence (AI) solutions will ensure that our healthcare data management system can interact in a highly confidential and almost completely private environment, laying a solid foundation for personalized healthcare solutions and management.
Data availability
Data sets generated during the current study are available from the corresponding author on reasonable request. The data are available from Xing Zhang ([email protected]). But restrictions apply to the availability of these data, which were used under license for the current study, and so are not publicly available.
Junaid, S. B. et al. Recent advancements in emerging technologies for healthcare management systems: A survey. Healthcare https://doi.org/10.3390/healthcare10101940 (2022).
Article PubMed PubMed Central Google Scholar
Crameri, K.-A., Maher, L., Van Dam, P. & Prior, S. Personal electronic healthcare records: What influences consumers to engage with their clinical data online? A literature review. Health Inf. Manag. J. 51 (1), 3–12. https://doi.org/10.1177/1833358319895369 (2022).
Article Google Scholar
Alrebdi, N., Alabdulatif, A., Iwendi, C. & Lian, Z. SVBE: Searchable and verifiable blockchain-based electronic medical records system. Sci. Rep. https://doi.org/10.1038/s41598-021-04124-8 (2022).
Luk, C. Y. The impact of digital health on traditional healthcare systems and doctor–patient relationships: the case study of Singapore. in Innovative Perspectives on Public Administration in the Digital Age . https://doi.org/10.4018/978-1-5225-5966-5.ch008 (2018).
Duo, W., Zhou, M. & Abusorrah, A. A survey of cyber attacks on cyber physical systems: recent advances and challenges. IEEE/CAA J. Autom. Sin. https://doi.org/10.1109/jas.2022.105548 (2022).
Armbrust, M. et al. A view of cloud computing. Commun. ACM https://doi.org/10.1145/1721654.1721672 (2010).
Cao, C. & Huang, S. How can SMEs boost trust through third-party means? Tracing the multi-dimensional institutional basis of online trust. IEEE Access 10 , 127149–127167. https://doi.org/10.1109/access.2022.3226889 (2022).
Kouhizadeh, M., Saberi, S. & Sarkis, J. Blockchain technology and the sustainable supply chain: Theoretically exploring adoption barriers. Int. J. Prod. Econ. https://doi.org/10.1016/j.ijpe.2020.107831 (2021).
Olanrewaju, R.F., Abdullah, K., & Darwis, H. Enhancing cloud data security using hybrid of advanced encryption standard and blowfish encryption algorithms. in 2018 2nd East Indonesia Conference on Computer and Information Technology (EIConCIT) , Makassar, Indonesia. https://doi.org/10.1109/eiconcit.2018.8878629 . (2018).
Hewa, T., Ylianttila, M. & Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. https://doi.org/10.1016/j.jnca.2020.102857 (2021).
Cui, Z., Kuang, W. & Liu, Y. Automatic Verification of Sound Abstractions for Generalized Planning. arXiv preprint https://doi.org/10.48550/arXiv.2205.11898 (2022).
Muñoz, M. C. & Moh, M. Authentication of smart grid. Cryptography https://doi.org/10.4018/978-1-7998-1763-5.ch015 (2020).
Nerurkar, P. et al. Dissecting bitcoin blockchain: Empirical analysis of bitcoin network (2009–2020). J. Netw. Comput. Appl. 177 , 102940. https://doi.org/10.1016/j.jnca.2020.102940 (2021).
Annaiyappa, P., Macpherson, J., & Cayeux, E. Best practices to improve accurate time stamping of data at the well site. in Day 3 Thu, March 10, 2022, Galveston, Texas, USA . https://doi.org/10.2118/208732-ms . (2022).
Nair, P. R., & Dorai, D. R. Evaluation of performance and security of proof of work and proof of stake using blockchain. in 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV) , Tirunelveli, India. https://doi.org/10.1109/icicv50876.2021.9388487 (2021).
Jie, Z., Luong, T., Zhang, X., Jin, X. & Li, H. Design of chain-of-thought in math problem solving. arXiv preprint https://doi.org/10.48550/arXiv.2309.11054 (2023).
Galal, H., Mannan, M. & Youssef, A. Blindfold: Keeping private keys in PKIs and CDNs out of sight. Comput. Secur. 118 , 102731. https://doi.org/10.1016/j.cose.2022.102731 (2022).
Alzubi, J. A. Blockchain-based lamport merkle digital signature: Authentication tool in IoT healthcare. Comput. Commun. https://doi.org/10.1016/j.comcom.2021.02.002 (2021).
Nguyen, D. C., Pathirana, P. N., Ding, M. & Seneviratne, A. Blockchain for secure EHRs sharing of mobile cloud based E-health systems. IEEE Access https://doi.org/10.1109/access.2019.2917555 (2019).
Coronado-Garcia, L. C., Gonzalez-Fuentes, J. A., Hernandez-Torres, P. J., & Perez-Leguizamo, C. An autonomous decentralized system architecture using a software-based secure data field. in 2011 Tenth International Symposium on Autonomous Decentralized Systems , Tokyo, Japan. https://doi.org/10.1109/isads.2011.50 (2011).
Azaria, A., Ekblaw, A., Vieira, T., & Lippman, A. MedRec: Using blockchain for medical data access and permission management. in 2016 2nd International Conference on Open and Big Data (OBD) , Vienna, Austria. https://doi.org/10.1109/obd.2016.11 . (2016).
Fan, K., Wang, S., Ren, Y., Li, H. & Yang, Y. MedBlock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. https://doi.org/10.1007/s10916-018-0993-7 (2018).
Article PubMed Google Scholar
Sun, J. et al. Blockchain-based secure storage and access scheme for electronic medical records in IPFS. IEEE Access https://doi.org/10.1109/ACCESS.2020.2982964 (2020).
Sun, Z. et al. A blockchain-based secure storage scheme for medical information. Eurasip J. Wirel. Commun. Netw. https://doi.org/10.21203/rs.3.rs-1201585/v1 (2022).
Wang, L. et al. A user-centered medical data sharing scheme for privacy-preserving machine learning. Secur. Commun. Netw. 2022 , 1–16 (2022).
Yuan, J., Ma, Y., Luo, W. & Han, G. B-SSMD: A fine-grained secure sharing scheme of medical data based on blockchain. Secur. Commun. Netw. 2022 , 1–14. https://doi.org/10.1155/2022/2719951 (2022).
Article CAS Google Scholar
Chen, Y., Ding, S., Xu, Z., Zheng, H. & Yang, S. Blockchain-based medical records secure storage and medical service framework. J. Med. Syst. https://doi.org/10.1007/s10916-018-1121-4 (2019).
Yue, X., Wang, H., Jin, D., Li, M. & Jiang, W. Healthcare data gateways: Found healthcare intelligence on blockchain with novel privacy risk control. J. Med. Syst. https://doi.org/10.1007/s10916-016-0574-6 (2016).
Zaman, S. et al. Thinking out of the blocks: holochain for distributed security in IoT healthcare. IEEE Access 10 , 37064 (2021).
Arul, R. et al. IoT-enabled healthcare systems using block chain-dependent adaptable services. Pers. Ubiquit. Comput. https://doi.org/10.1007/s00779-021-01584-7 (2021).
Shanthapriya, R. & Vaithianathan, V. Block-healthnet: security based healthcare system using block-chain technology. Secur. J. 35 (1), 19–37. https://doi.org/10.1057/s41284-020-00265-z (2022).
Dhasarathan, C. et al. User privacy prevention model using supervised federated learning-based block chain approach for internet of Medical Things. CAAI Trans. Intell. Technol. https://doi.org/10.1049/cit2.12218 (2023).
Kumar, R. et al. A secured distributed detection system based on IPFS and blockchain for industrial image and video data security. J. Parallel Distrib. Comput. https://doi.org/10.1016/j.jpdc.2021.02.022 (2021).
Sai, C. S., & Subramanian, N. Covert communication on IPFS using secured filecoin-slate blockchain. in 2022 IEEE 19th India Council International Conference (INDICON) , Kochi, India. https://doi.org/10.1109/indicon56171.2022.10039703 . (2022).
Reddy, B. A ZK-SNARK based proof of assets protocol for bitcoin exchanges. in 2023 15th International Conference on COMmunication Systems & NETworkS (COMSNETS). https://doi.org/10.1109/COMSNETS56262.2023.10041328 (2022).
Fischlin, M. Round-optimal composable blind signatures in the common reference string model. in Lecture Notes in Computer Science,Advances in Cryptology - CRYPTO 2006 , pp. 60–77. https://doi.org/10.1007/11818175_4 . (2006).
Zhao, M., Dai, C., Zhao, Y., & Guo, B. Efficient electronic transaction query model for light nodes based on optimized blockchain structure. in 2022 IEEE 24th Int Conf on High Performance Computing & Communications; 8th Int Conf on Data Science & Systems; 20th Int Conf on Smart City; 8th Int Conf on Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Hainan, China . https://doi.org/10.1109/hpcc-dss-smartcity-dependsys57074.2022.00056 . (2022).
Ante, L. The non-fungible token (NFT) market and its relationship with Bitcoin and Ethereum. SSRN Electron. J. https://doi.org/10.2139/ssrn.3861106 (2021).
Download references
Acknowledgements
This paper was supported in part by Applied Basic Research Project of Liaoning Province under Grant 2022JH2/101300280, Scientific Research Fund Project of Education Department of Liaoning Province under Grant LJKZ0625.
Author information
Authors and affiliations.
Liaoning University of Technology, Jinzhou, China
Shengchen Ma
Key Laboratory of Security for Network and Data in Industrial Internet of Liaoning Province, Jinzhou, 121000, China
You can also search for this author in PubMed Google Scholar
Contributions
Innovation point discussion, Analysis of the current study, Concept and Design: S.-C.M, X.Z. Recommend References: S.-C.M, X.Z. Data collection: S.-C.M. Statistical analyses: S.-C.M. Literature summary: S.-C.M. Writing: S.-C.M. Critical review and Provide writing advice: S.-C.M, X.Z.
Corresponding author
Correspondence to Xing Zhang .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Ma, S., Zhang, X. Integrating blockchain and ZK-ROLLUP for efficient healthcare data privacy protection system via IPFS. Sci Rep 14 , 11746 (2024). https://doi.org/10.1038/s41598-024-62292-9
Download citation
Received : 19 December 2023
Accepted : 15 May 2024
Published : 23 May 2024
DOI : https://doi.org/10.1038/s41598-024-62292-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Zero-knowledge proofs
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.

IMAGES
VIDEO
COMMENTS
A Ph.D. in cybersecurity provides students with a comprehensive education encompassing technology, data science, leadership, management, ethics and policy. Requirements, course loads and ...
Security Studies. This five-year program is designed to prepare Ph.D. students for rigorous, policy-relevant research on the major threats to international and national security and the relevant strategies, institutions, and capabilities that will be needed to confront those threats. Topics of study include: Grand strategies of the major powers.
A graduate with a Ph.D. in Cybersecurity Management will have the ability to: acquire advanced knowledge and deeper understanding of the field of information assurance; communicate professionally and ethically about information assurance research issues;
Here's a breakdown of tuition rates (all figures are based on out-of-state tuition). $17,580 is the most affordable PhD program option and it is available at the Georgia Institute of Technology. $86,833 is the average cost of a cybersecurity PhD and is based on tuition rates from all 26 schools.
As a graduate of National University's Doctor of Philosophy in Cybersecurity (PhD-CY), you'll be able to: Advance theory and practical applications of cybersecurity. Formulate cybersecurity governance, policy, risk, and compliance. Assess internal and external threats and vulnerabilities to reduce organizational cyber risk.
Tuition & Fees. Doctor of Global Security Total Costs: $50,054 plus dissertation credits. Year One= $20,022 (3 terms x $6,674) Year Two= $20,022 (3 terms x $6,674) Plus all residency costs for a personalized international experience. Year Three = $10,010 (2 terms x $5,005)
In the past couple of years, despite the small size of our program, our PhD students have published in quality, peer-reviewed publications, both on their own (Civil Wars, Intelligence and National Security, and others) and with faculty (Conflict Management and Peace Science, African Affairs, Journal of Conflict Resolution, etc.
Overview. A research-based, interdisciplinary Doctor of Philosophy (PhD) in Cybersecurity combines a strong security technical foundation with a security policy and social sciences perspective. It seeks to prepare graduates to advance the state of the art of security in systems networks and the internet in industry, academia, and government.
Online Doctor of Strategic Security Degree Overview. This 100% online DSS program will provide you with the advanced knowledge, skills, and insights you need to address emerging threat-based challenges to protect others, organizations, and the global strategic environment. You'll learn how to make a positive impact on the safety and security ...
Cybersecurity, PhD. A research-based, interdisciplinary Doctor of Philosophy (PhD) in Cybersecurity combines a strong security technical foundation with a security policy and social sciences perspective. It seeks to prepare graduates to advance the state of the art of security in systems, networks, and the internet in industry, academia, and ...
The limited-in-residency program is designed for working professionals seeking to pursue a doctoral degree in Homeland Security on a part-time basis. To accommodate participants' time constraints, the DPS will only require students to be in residence for one week for each academic year of the program. The residency requirement will lay the ...
The program adopts the engaged scholarship model. Students learn to apply current research to information security problems. Designed for executives with 7-10 years of cybersecurity management or consulting experience, the EDBA-IS is a three-year, part-time program. Students can transfer up to 12 graduate credits to the first-of-its-kind degree.
UCL Security and Crime Science is widely recognised for the impact of its research on real-world crime problems. The Department has long-standing links with police forces, policy makers, academic research centres of excellence and security organisations in the UK and internationally. A PhD with us allows you to pursue original research and make a distinct and significant
Focus your degree with three tracks: Corporate Security Management, Homeland Security & Emergency Management, and Strategic Intelligence & Analysis ... A graduate degree or certificate from Northeastern—a top-ranked university—can accelerate your career through rigorous academic coursework and hands-on professional experience in the area of ...
The department of security and crime sciences is organised into five centres of excellence Geographical Analysis; The Designing Out Crime Read more... 3 years Full time degree: £6,035 per year (UK) 5 years Part time degree: £2,930 per year (UK) Apply now Visit website Request info. View 4 additional courses. Compare.
With APU's graduate certificate in security management, you will learn about strategic decision making and how to evaluate security programs, while conducting risk-assessment analysis of computer facilities, including identifying types of threats and probabilities of occurrences. This online program covers material typically needed by those ...
The Centre for Defence Management and Leadership (CDML) is a specialised research and teaching unit, comprising experienced and dedicated researchers. It has developed a world class reputation in defence and security studies, and is lauded for the rigour, originality, international perspective and policy relevance of its doctoral programme.
Apply now for 2024. The Professional Doctorate in Security Risk Management (D.SyRM) is a structured, part-time programme targeted towards security professionals in the UK and overseas, delivered through a small number of workshops in Portsmouth for the first two years and then two years of supervised research leading to a thesis.
Doctor of Strategic Intelligence Total Costs: $50,054 plus dissertation credits. Year One= $20,022 (3 terms x $6,674) Year Two= $20,022 (3 terms x $6,674) Plus all residency costs. Year Three = $10,010 (2 terms x $5,005) Continuing registration during the dissertation phase is $863 per term. Includes book grant for course materials.
A University of Maryland graduate student in information management and community planning is among 102 recipients nationwide to earn the David L. Boren Fellowship to study critical languages overseas. ... The Boren Awards program by the National Security Education Program's Institute of International Education grants undergraduate and ...
You'll play a critical role in developing training protocols for law enforcement and examining the network security of emerging technologies. Through hands-on work at the Leahy Center, you'll hone your skills as a Champlain cybersecurity student, contribute to the field, and graduate as a cybersecurity professional with real-world experience.
After decades of development, healthcare management systems 1 have hitched a ride on the great wave of Internet development and have made tremendous progress in various technologies, including ...
Area of educational buildings - 59861 m2. 14 lectures halls for 1300 seats. 79 specialized audiences. 3 hostels, 2000 places dining room, canteens, volleyball and football grounds, 8 specialized gyms as well as shooting and multimedia ranges operate at the territory of the University. The combination of scientific achievements and experience ...
At the university, more than 10,000 cadets, students and trainees in the specialties "Law", "Law Enforcement" and "Management" study, acquire vocational training and improve their qualifications. Each year the university admits for training about 1800 persons who after graduation receive state standard diplomas of education and qualification ...
Dnipropetrovsk State University of Internal Affairs (DSUIA) is a multi-profile higher educational establishment that is dually subordinated to the Ministry of Internal Affairs of Ukraine and the Ministry of Education of Ukraine with specific study conditions. Number of faculty staff (250 full-time + 58/part-time) Number of faculty staff with PhD (154 full-time + 45 part-time)
Dnipropetrovsk State University of Internal Affairs is a multi-profile higher educational establishment of the MIA of Ukraine system, which embraces all stages of education: Bachelor, Master ...