- Browse All Articles
- Newsletter Sign-Up

InformationTechnology →
No results found in working knowledge.
- Were any results found in one of the other content buckets on the left?
- Try removing some search filters.
- Use different search filters.
- Research article
- Open access
- Published: 10 September 2020
Enhancing the roles of information and communication technologies in doctoral research processes
- Sarah J. Stein ORCID: orcid.org/0000-0003-0024-1675 1 &
- Kwong Nui Sim 2
International Journal of Educational Technology in Higher Education volume 17 , Article number: 34 ( 2020 ) Cite this article
15k Accesses
5 Citations
3 Altmetric
Metrics details
While information and communication technologies (ICT) are prominent in educational practices at most levels of formal learning, there is relatively little known about the skills and understandings that underlie their effective and efficient use in research higher degree settings. This project aimed to identify doctoral supervisors’ and students’ perceptions of their roles in using ICT. Data were gathered through participative drawing and individual discussion sessions. Participants included 11 students and two supervisors from two New Zealand universities. Focus of the thematic analysis was on the views expressed by students about their ideas, practices and beliefs, in relation to their drawings. The major finding was that individuals hold assumptions and expectations about ICT and their use; they make judgements and take action based on those expectations and assumptions. Knowing about ICT and knowing about research processes separately form only part of the work of doctoral study. Just as supervision cannot be considered independently of the research project and the student involved, ICT skills and the use of ICT cannot be considered in the absence of the people and the project. What is more important in terms of facilitating the doctoral research process is students getting their “flow” right. This indicates a need to provide explicit support to enable students to embed ICT within their own research processes.
Background/context
Information and communication technologies (ICT) can bring either joy or challenge to well-versed academic practices, and either create barriers to learning and development or be the answer to needs. While some grasp and pursue opportunities to make use of various ICT for study, research and teaching, others struggle. Despite documented and anecdotal positive urges to adopt ICT to increase and improve efficiency and effectiveness, staff and students struggle experience ICT as needless and difficult-to-use interruptions. There is often little need seen to change practices by introducing ICT into ways of working. Exploring these views and experiences was the focus of this project. Being empathetic to views such as those expressed by Castañeda and Selwyn ( 2018 ), we did not approach this investigation from a position that assumes that ICT are natural and needed solutions to problems related to improving and facilitating effective learning, teaching and research. Rather, we took a more neutral stance, wishing to explore the experiences of those involved, namely, students and staff, through discussion with them about their ICT practices and views, and with a specific focus on doctoral study and supervision.
Doctoral supervision and the role, place and nature of the doctorate are receiving increasing attention in higher education research literature. A wide range of topics have been covered from, for example, the importance and types of support for students throughout candidature (e.g., Zhou & Okahana, 2019 ); to the teaching and supervision aspects of doctoral supervision (e.g., Åkerlind & McAlpine, 2017 ; Cotterall, 2011 ; Lee, 2008 ).
With advancements in, accessibility to, and development of, ICT within education settings has come a plethora of research into online and blended learning. These studies often highlight the capacity of ICT for facilitating teaching, learning and administrative activity within educational institutions and systems (e.g., Marshall & Shepherd, 2016 ). They cover numerous areas of importance from theoretical, practical, and philosophical angles and include the perspectives and needs of learners, educators and institutions (e.g., Nichols, Anderson, Campbell, & Thompson, 2014 ).
There are also studies on student use of ICT, though not necessarily doctoral students, and these cover a wide range of topics including specific ICT skills (e.g., Stensaker, Maassen, Borgan, Oftebro, & Karseth, 2007 ). Where postgraduate research students are concerned, some studies on ICT skill development and support provide some insights about students (e.g., Dowling & Wilson, 2017 ), and institutional ICT systems (Aghaee et al., 2016 ).
Notable about the many of these studies cited above is the use of self-reporting tools as mechanisms for gathering data about student use and views about ICT. While self-reports are valuable ways to collect such data about self-efficacy, they do have limits. In online learning environments, the role of self-efficacy, for example, is still being contested. It has been argued that learners from a variety of disciplines and learning settings will tend to overestimate claims about their performance and/or knowledge and skills (e.g., Mahmood, 2016 ).
All these studies help to ‘map the territory’ of ICT, their use at individual and institutional levels and related practices. Much advice and guidance can be gleaned from the literature as well, although relatively little for the specific integration of ICT within the doctoral research and supervision environment. Based on the literature that is available though, all indications are that (doctoral) students adopt educational practices incorporating limited ICT use, even though the use of ICT has grown enormously in the last 10 to 20 years. With the current interest in ensuring success of students and completion of doctoral degrees being closely related to high quality supervision, there is a need to improve supervision practices and within that, advance understandings about how to support students in their use of ICT for their doctoral research.
This project
This project aimed to explore doctoral student and supervisor views and use of ICT within the doctoral process. The intention was to bring to light perceptions that could give clues as to how to make practical modifications to the content and scope of professional development support for supervisors and students, in order to help them to make best use of ICT. In addition, consideration was given to the way data would be collected to ensure that more than just the self-reported perspectives of the participants were included.
An interpretivist research approach (Erickson, 2012 ) framed this study to support a focus on understanding the world from the perspectives of those who live it. Thus, the approach was well-suited to exploring perceptions about the use of ICT in our context.
Thus, this study did not commence with any hypotheses related to the influence of ICT in doctoral research in mind. Instead, as the interpretive frame of the research implies, this study investigated ways in which participants expressed their experiences of engaging and integrating ICT in support of their doctoral research processes. The data tapped into the participants’ (PhD students and doctoral supervisors) perspectives, as they expressed them. The research approach thus defined and shaped all aspects of the data gathering, analyses and presentation. In this way, alignment was ensured among the ontological, epistemological and practical implementation of the research project.
The study took place in two New Zealand universities where participants were either employees or students. Both universities are research-intensive, with histories of producing high-level research across many disciplines. Both institutions have clear and well-formulated policies and practices governing doctoral study - PhD and professional doctorate - and these include supporting that study through supervision. A specialised unit in each institution manages the administration of the doctoral degree. Couching “supervision” as essentially a (specialised) teaching activity, each unit also provides or coordinates professional development for staff in the art of supervision, and for students in the skills and processes of undertaking doctoral degree study.
Participants
Participants included doctoral students and supervisors from the two universities. As a result of an invitation to all students and supervisors, in total, 11 students and two supervisors responded. The students were PhD students at varying levels of completion. There was a mix of part time and full-time students from a variety of discipline backgrounds including health sciences, sciences, commerce and humanities. The supervisors were experienced and were from humanities and sciences.
Data sources
Data were collected using a 3-tier participative drawing process (Wetton & McWhirter, 1998 ). This strategy involved a series of two or three interview/discussions, along with participant-made drawings, which formed the focus of the interview/discussions.
This strategy generated two sources of data - interview transcripts and participant drawings – and involved the following (3-tier) phases:
Initial semi-structured interview/discussion to ascertain information about participants’ backgrounds and other details they saw relevant to share. In addition, they were asked about their use of ICT generally as well as within the doctoral process. It was a chance for the researchers to gain some understanding of participants’ views and practices in relation to ICT and their doctoral/supervision journeys.
Participant drawing . The participants were asked to make a drawing in their own time and before the second interview/discussion. Guidelines for the drawing suggested that they think of a way to illustrate their research process first, then to add onto the drawing any ICT (such as devices, websites, programmes, applications) that they make use of in the process.
Follow-up interview/discussion . During this phase, each participant was asked to explain the drawing’s features and how it made sense in terms of the project he or she was undertaking. This included discussion about how their supervision was working, how they worked with supervisors, and how the ICT they had included in the drawing worked within the process. They were also asked about elements that were not in the drawing, for example, certain ICT or activities that might have appeared in a typical account of a doctoral research process but were not included.
All interview/discussions were audio recorded and transcriptions of the recordings were returned to the participants for checking. The drawings were scanned and stored electronically.
In line with the interpretive approach that framed and governed our study, the data were analysed shortly after being gathered. Analysis of the data contributed to the development of ideas about participants’ perceptions, and these were refined progressively across the instances that researchers met with participants. Perceptions were thus checked, rechecked and refined against each data set.
This iterative and inductive approach (Thomas, 2006 ) involved thematic analysis (Silverman, 2001 ) and the capture of major and common ideas (Mayring, 2000 ) expressed by participants about how ICT are perceived and used in doctoral research processes. This approach helped to operationalise a process of co-construction between researchers and participants. Through checking, rechecking, refining and confirming, the researchers were able to articulate their understanding of participant perceptions that matched participants’ expressed thoughts.
The outcome of the analysis process was four assertions concerning ways the students perceived and understood ICT within doctoral study. Because there were only two supervisor participants, the data from the supervisors served to support the assertions we were more confidently able to make about student perceptions.
Research approach, quality assurance conditions and context
Despite the (what might be argued, small) number of volunteer participants who showed interest in, and committed themselves to, this study (i.e., no drop-outs or selection being made from a pool), it is worth noting that the researchers worked with each participant over an extended period of time (prolonged engagement), focused on investigating and gathering identifiable, as well as documentable, aspects of the participants’ ICT understandings and practices (persistent observation), and employed analysis techniques that incorporated peer debriefing, member checking, and fair presentation of assertions (Guba & Lincoln, 1989 ).
The aim was to unlock and identify views of reality held by the participants. The empirical evidence was used to help develop commentary and critique of the phenomenon which was the focus of the study (i.e., ICT use), including what the phenomenon is and how it occurs/is enacted/revealed in a particular context (viz., in doctoral research). This was, therefore, a different kind of study from one that might commence with a hypothesis, which would be concerned more with objectivity, explanation and testable propositions. In short, the methods employed in the current study fitted the intention to solve a “puzzle” about a phenomenon in relation to a particular context.
As this study involved human participants, ethical approval was gained through the institutional processes. This approval (University of Otago Human Ethics Committee reference number D17/414 and Victoria University of Wellington, Ethics Committee reference number 0000023415) enabled data collection methods described in the previous section to be carried out for any doctoral students and supervisors who volunteered to participate in this study. Ethical consent, use and care of the data as well as the ethical treatment of students and staff as participants were integral to the research design, planning and implementation of the whole study.
Findings and discussion
The four assertions are now presented. Each assertion is described and quotations from the interview/discussions along with examples of drawings from the student participants are used to illustrate aspects of each assertion.
Assertion 1: ICT are impartial tools; it does not matter how ICT are used, because the endpoint, that is, thesis completion, is the justification. ICT and people are separate and separated entities.
Students talked about how they worked on their thesis document and on the process of the study they were undertaking. Comments focused on various ICT being used and often on skills needed in order to use them. Some students expressed the view that ICT were tools, separate from the project and the person involved, to be used to achieve an endpoint. For example,
So long as it's formatted – it shouldn't matter - that's their [editors’] responsibility, not mine.
There’s probably a bit more about Zoom [web conferencing application] I could learn but again for me unless it’s a problem, I’m not going to go looking for it… not just for the sake of it at the moment.
Motivation to achieve an outcome was a focus of comments that support this assertion. For many participants, the aim to complete the study and write a thesis was, naturally, a large driver for how they were managing their study. Time was precious, and they would do what they had to do to reach their goal. To be motivated to learn about a new ICT, there needed to be a purpose that sharply focussed on achieving that end.
If the technologies are suddenly not available] I’m happy to sit down with a typewriter and learn it… If I’m not driven, I won’t bother.
This focus is illustrated in Fig. 1 . The drawing shows clearly identified components that make up major elements within the stages of producing the research for the thesis. ICT are listed in relation to those components.
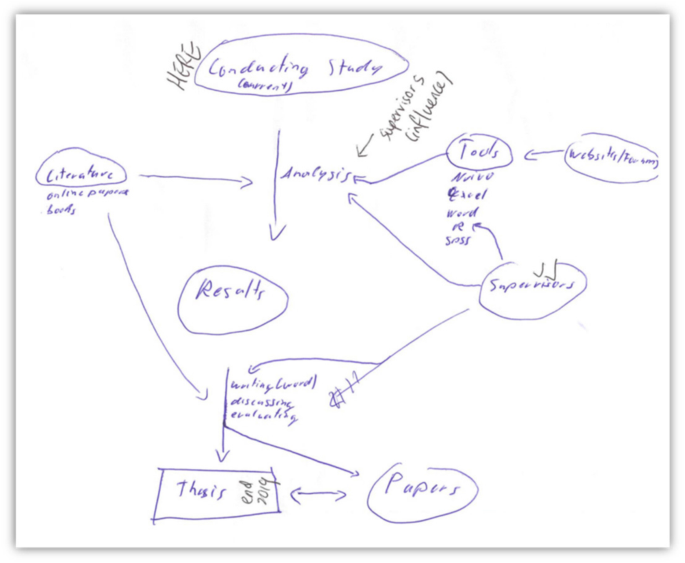
ICT and people are separate and separated entities
Supervisors too, tended to focus on thesis production rather than on the process of producing a thesis that includes the use of ICT (i.e., as opposed to their very clear and explicit focus on the research process). An example illustrating this is:
Generally, people think the standard of the people getting or earning a PhD is that this person should be an independent researcher. [But no] After all, we only examine a particular thesis [and] there are lots of inputs from supports and supervision from supervisors.
In summary, this assertion focusses strongly on the experience of doctoral study being about getting the project done within a research journey that gives minimal regard to the affordances of ICT. ICT are framed as necessary but also fraught, especially due to the effort and time that draw attention away from the primary goal.
Assertion 2: ICT are tools or mechanisms that prompt active thought on practices with respect to planning and managing thesis writing and project execution. ICT and individuals work alongside each other.
Views that expressed notions of there being a close interactive relationship between students and ICT came through in several of the discussions with the participants. The focus on achieving goals and endpoints was strong, but the expression of how to achieve those goals, capitalising upon the affordances that ICT present, was different from the way views were expressed in relation to Assertion 1.
On a simple level, this student describes the checking he did when weighing up the merits of a piece of software to meet his needs.
I normally do a trial version… have a play with it. And if I think they are useful then I might try it on a project. And if then I feel it’s definitely worth investing… then I’ll go buy it.
Others simply liked to explore, to see whether there was potential in any ICT they encountered, as in,
Sometimes I just like playing with stuff to see what they can do and then if they tick my boxes then I keep them and if they don't, I move on. So it's more kind of ‘search and discover’ than kind of looking for something, you know.
Describing a deeper level of activity, a degree of critique and active reflection were indicated by another student when he said,
…we tried an electronic version of putting together a programme for a New Zealand conference and I was surprised how long it took us. Whereas in the past I’ve worked with [colleagues] and we’ve just moved pieces of paper around on the floor for abstracts and we were done really quickly.
These sentiments are well-captured in Fig. 2 . Here, the focus is on experimenting with ICT rather than the research process. The process of working things out to suit the individual is foregrounded.
ICT and individuals work alongside each other
Whereas Assertion 1-type expressions presented effort in a generally negative light, Assertion 2-type expressions couched effort as an assumed part of learning something new. There was a sense expressed in comments that there will be a way to manage the “problem” to be solved, which then generated the necessary motivation to engage effort. For example,
You just know what you know when you start off; when you're unsure about what you need to do. There's a bit of a barrier in front of you. It feels a bit intimidating and overwhelming, and then you get into it and it just works. And you just kind of put all the pieces together and get something out at the end.
There was a sense that supervisors’ perspectives of ICT might support this assertion too. For instance,
[ICT are] integral to everything now – there's no such thing as doing it without [them] anymore – these are the tools with which we do all the things we do.
In summary, this assertion captures the views of students who engage actively in making decisions about which, how and why they incorporate ICT into doctoral research practices.
Assertion 3: Knowing about ICT is only part of the thinking; what is more important is getting the “flow” right. ICT and the individual are in a complementary partnership.
Perhaps prompted by the nature of the drawing task, which was to illustrate how ICT fitted within the whole process of doctoral study, several students described the challenges to bringing everything together into one process made up of many parts, sections and subsections. One participant focussed on her “workflow” in order to manage the multiple documents, tasks and schedule involved in her doctoral research journey.
What systems do I use, what's my workflow? So, I actually spent some weeks looking at … ideas from other PhD students about their workflows and how they manage it.
Similar to Assertion 2-type comments, ‘getting one’s flow right’ involved exploration and an amount of reflective decision-making. For example,
So I did a play around with that [ICT] and found it was quite useful … So I’m trying to be quite disciplined about when I’ve got a document, entering it at the time, reading an article, throw in heaps of tags rather than not …And I simply keep a note, cross referencing to the actual articles. I like to have the articles and for some key ones I like to make a note. So, if it’s a seminal paper that I know I’ll be referring back to.
Thus, students talked about how hard they worked to set up routines and processes to enable them to manage time and their research projects. As in the above excerpts, they referred to categorising documents, searching for resources, undertaking analysis, managing data, and producing the thesis itself.
In working out one’s system or flow, this student highlighted the need to know about the affordances of ICT and how others had made use of them.
…you do need to know a bit about each of the individual … capabilities of the different systems to know what's even possible… but alongside that you're kind of reading other people's ideas of how they did it, and you think that bit might work for me oh, but that bit won't… so then you can kind of mix and match a bit.
The drawing in Fig. 3 highlights the “flow”. Absent of all words, this illustration draws attention to the movement of ideas, thoughts, processes and actions, from a number of different points but all ultimately converging or contributing to the one path.

ICT and the individual are in a complementary partnership
There was a hint that at least one of the supervisors saw the need for a workflow in this same vein: “So long as [the students are] happy with what they’re using – they should use ‘a’ system,”
In summary, this assertion highlights that what is important with respect to ICT and the doctoral process is how it all comes together within one’s flow. That flow incorporates active effort on the part of the individual in finding ICT and practices that suit the individual’s approaches as well as their project demands.
Assertion 4: ICT are not neutral; there is a two-way interaction between technologies as artefacts and the use of them to achieve ends. ICT and the person are intricately linked through multiple active, practical, goal-oriented connections.
This assertion draws attention to the nature of technology as a phenomenon; that technology is not an impartial tool that has no influence on the way humans act and react. This assertion presents ICT as an artefact of technological design activity; as a source of improving efforts to achieve an endpoint; but also as an influencer and even determiner of the thinking and practices of the person interacting with the ICT (e.g., Baird, 2002 ).
On what could be argued a superficial level, this student noted some active connection between the person and the software application, beyond simple use, when he commented:
I think it goes both ways, the product has to be intuitive and you’ve got to have a little bit of inclination to try out different things.
Others went beyond the superficial to describe more in-depth relationships between themselves and the ICT they were using. When discussing her use of software to help her manage her project and her time, this student talked about how the ICT she was using supported and enhanced her thinking.
Using the application] really changed the way I started to think about [my research]. I started to be less worried about the big overwhelming long term stuff that was out there and just think, okay, this week, what am I going to do this week, how am I going to be really efficient and targeted, and I think that really helped me.
Following is another example of how ICT helped solve a problem while simultaneously having an influence on behaviour; in this instance with organising notes, ideas and documents.
“… and it's the same with my note-taking because [the programme] that I use has a similar sort of functionality that it can search text that you've written but also search notes and PDF docs and those kind of things, so it means that when you've had a random thought and put it somewhere you can find it again. Which is huge for me, so I guess that … the power of the search engine is probably the thing that drove me to become paperless, so it helps me to organize myself much better. … filing paper is a skill that I have not mastered whereas filing digital stuff is not as important because you can always just find it again.
Figure 4 illustrates this intricately intertwined interactivity among person, purpose, project, ICT and outcomes.

ICT and the person are intricately linked through multiple active, practical, goal-oriented connections
While we did not find strong evidence for supervisors’ thoughts about this integrated and embedded notion of ICT, one supervisor did note “I could probably build them into my system, but I just never have”.
In summary, Assertion 4 highlights the integral role that ICT can be perceived to play in doctoral research processes. This is more than the working-alongside connection illustrated by Assertion 2 and the complementary partnership characterised by Assertion 3.
Assertions 1 and 2 highlight that individuals hold assumptions about, and have expectations of, ICT use; and those expectations and assumptions influence and determine their judgements about ICT and their use of ICT. The assertions point to connections between perceptions and practices. Assertion 1 describes a perception that ICT are separate from the person and the task-at-hand, while Assertion 2 presents a perception in which the person and the ICT are working alongside each other in harmony or at least in a loose partnership. Both assertions focus on endpoints, but the endpoints vary according to the perception of where ICT fit into the journey towards their achievement. For Assertion 1-type expressions, there is one major endpoint. For Assertion 2-type expressions, there are multiple, shorter-term endpoints that build towards achieving the major goal of completing the thesis.
Building on Assertions 1 and 2 are Assertions 3 and 4, which highlight what may be argued as more complex levels of perceiving and working with ICT. Both assertions give some focus to inter-connections, where people and ICT partner or collaborate. Assertion 3 depICT a perception that is about complementarity; where ICT affordances are seen as worthwhile when they support and enhance the work of the individual in ways that make sense to that individual. Assertion 4 builds on Assertion 3 by bringing to light the relationship in which the person alters and changes thinking or practices because of the influence that ICT affordances can have. No evidence was found to support a possible additional claim that as well as ICT causing individuals to alter and modify thinking and behaviours due to their existence, ICT, in turn, are perceived to be able to alter their ways of responding to the people who use them. This is not out of the realms of possibility of course, with ICT increasingly being designed and built to be able to respond to users’ needs.
It is also worth mentioning that the ‘types’ of ICT and the extent of their use by the participants was not the focus of this study. However, the findings suggested that the participants’ ICT use, regardless of their PhD phase and broad discipline background, might have reflected their inability to realise the advantages of learning how to use current ICT-related devices, tools, and applications to enhance the process of undertaking their doctoral research. The evidence that emerged in this study indicated that participants’ perspectives of ICT determined their adoption practices in general (i.e., as illustrated through the four assertions). The boarder higher education context including the specific institution and supervisors, might have neglected the explicit support of PhD students’ ICT capability development in this process.
In addition, while there is no similar study being found thus far, the insights gained from this study are actually similar to the findings in the research studies into the role of ICT in undergraduate education (Butson & Sim, 2013 ; Sim & Butson, 2013 , 2014 ). Results in those studies, demonstrated students’ low levels of ICT use, may be an indication that digital devices and digital tools do not play a significant role in daily study practices. Researchers such as Esposito, Sangrà & Maina ( 2013 ) also show that the PhD students’ learning to become researchers in the digital age is much more complex than is often suggested (e.g., the skills of Prenksy ( 2001 ) “digital natives”). Becoming a researcher involves developing a complex set of knowledge, intellectual abilities, techniques and professional standards. The Researcher Development Framework (Careers Research and Advisory Centre (CRAC), 2010 ) illustrates one useful attempt at mapping out that complexity. It could be that both students’ and supervisors’ adoption of ICT for academic purposes has been overshadowed or taken for granted as a consequence of their advanced academic level.
Implications
The four assertions can be used to provide some guidance to those supporting and participating in doctoral research processes. Students and supervisors do possess a vast array of skills, knowledge and abilities. They have a variety of experiences as well as varying reasons and levels of motivation. Their skills and capacity to make use of ICT to support their roles in the research process vary as well. The assertions that have emerged from this study will inform the planning for support activities to enhance supervisors’ and students’ professional development, whatever their background and needs.
Depending on the perceptions held about ICT and the relationship between ICT and the person in the context of the task and its goals (i.e., the doctoral study) within the doctoral research process as depicted in the four assertions, ICT tend to be seen as a challenge, a change or an opportunity. In the context of ICT use, doctoral students and supervisors may:
assume that if they do not already know how to use something it is not worth learning or exploring as that learning brings with it risk to quality, efficiency and effectiveness of the doctoral research process; and/or.
assume that students will work out the place that ICT play within the research process for themselves.
The findings of this study suggest the need to.
challenge existing ICT knowledge and skill, and to support acceptance of the need to change practices;
teach technological thinking, to enable choice and decision making about ICT;
embed ICT into practices in meaningful ways to suit individual and project needs;
highlight (explicit) responsibilities about thinking and planning skills with respect to making the best use of ICT, to ensure efficiency and effectiveness;
realise that the research process is as much about how it happens as what happens;
recast assumptions about the doctoral research process to embed ICT within it;
reflect on the meaning of effectiveness and efficiency in the context of doctoral research; and the effects of ICT in supporting and facilitating them;
understand that there is a link among ICT thinking and practice: using ICT can enhance or raise ideas that were never thought of before.
This study explored perceptions of doctoral supervisors and students of the role and place of ICT in supervision and study. It generated four assertions characterising those perceptions the relationships among people, ICT and the task-at-hand, that is, the supervised research process. As Castañeda and Selwyn ( 2018 ) argue, it is important that we have an active commitment to ‘think otherwise’ about how ICT might be better implemented across higher education settings” (p. 8). We should not assume that ICT are not important enough to let them fade into the background as they become normalised, without questioning the interrelationships that are happening between the person and the ICT. In the doctoral research setting, as one example of a higher education context, ICT do have a role to play. They cannot and should not be ignored. But seeing ICT in relationship to the person and to the setting is essential.
This project has provided insights into the doctoral students and supervisors’ perceptions of the roles played by ICT during doctoral research process. There are complex human factors, including assumptions, attitudes and conceptions about academic practices, influencing and determining perspectives as well as how ICT are incorporated into doctoral research process, behaviours and practices. Just as Kandiko and Kinchin ( 2012 ) argue that supervision cannot be looked at in the absence of the research work in which it occurs, we argue that doctoral students’ understanding and use of ICT cannot be considered independently of their research work; and that work includes relationships with their project, their supervisors, within the context of the institution, and with the ICT they do and could engage with.
Directly associated with the outcomes of this study, future studies and further exploration could focus on:
ICT use by larger and more diverse groups of doctoral students from a range of fields within discipline areas at institutions outside New Zealand;
building on the findings in order to determine how intensity of ICT use might change for students across the course of their candidature, and in relation to the nature of their research projects;
the role of supervisors, academic departments, and institutions in supporting and enhancing students’ practices and beliefs about ICT in research processes;
the ways in which supervisors engage ICT in their daily academic practices, with a view to exploring how, or if, their ICT use is an influence on PhD students’ beliefs and behaviours in using ICT.
Studying ICT in these directions could offer fresh perspectives and opportunities to think differently and reveal an active way of understanding the role of ICT in doctoral education.
Availability of data and materials
These are not available for open access as their access is bound by the ethical agreement approved by the two institutions and made with the participants in the study.
Aghaee, N., Jobe, W. B., Karunaratne, T., Smedberg, Å., Hansson, H., & Tee, M. (2016). Interaction gaps in PhD education and ICT as a way forward: Results from a study in Sweden. International Review of Research in Open and Distance Learning , 17 (3) Retrieved from https://search.proquest.com/docview/1805463156?accountid=14700 .
Åkerlind, G., & McAlpine, L. (2017). Supervising doctoral students: Variation in purpose and pedagogy. Studies in Higher Education , 42 (9), 1686–1698. https://doi.org/10.1080/03075079.2015.1118031 .
Article Google Scholar
Baird, D. (2002). Thing knowledge: Function and truth. Techné: Research in Philosophy and Technology , 6 (2), 96–105. https://scholar.lib.vt.edu/ejournals/SPT/v6n2/ .
MathSciNet Google Scholar
Butson, R., & Sim, K. N. (2013). The role of personal computers in undergraduate education. International Journal of Digital Literacy and Digital Competence , 4 (3), 1–9. https://doi.org/10.4018/ijdldc.201307010 .
Careers Research and Advisory Centre (CRAC) (2010). Researcher development framework , (pp. 1–22) Retrieved from https://www.vitae.ac.uk/vitae-publications/rdf- related/researcher-development-framework-rdf-vitae.pdf .
Castañeda, L., & Selwyn, N. (2018). More than tools? Making sense of the ongoing digitizations of higher education. International Journal of Educational Technology in Higher Education , 15 (22), 1–10. https://doi.org/10.1186/s41239-018-0109-y .
Cotterall, S. (2011). Doctoral students writing: Where's the pedagogy? Teaching in Higher Education , 16 (4), 413–425. https://doi.org/10.1080/13562517.2011.560381 .
Dowling, R., & Wilson, M. (2017). Digital doctorates? An exploratory study of PhD candidates’ use of online tools. Innovations in Education and Teaching International , 54 (1), 76–86. https://doi.org/10.1080/14703297.2015.1058720 .
Erickson F. (2012). Qualitative research methods for science education. In Fraser, B., Tobin, K., & McRobbie, C. J. (Eds.), Second international handbook of science education . (Springer International Handbooks of Education, Vol. 2, pp. 1451–69). Dordrecht: Springer. https://doi.org/10.1007/978-1-4020-9041-7_93 .
Google Scholar
Esposito, A., Sangrà, A., & Maina, M. (2013). How Italian PhD students reap the benefits of instiutional resources and digital services in the open web. Proceedings of the International technology, education and development (INTED) conference , pp. 6490-6500. Valencia: Spain. ISBN: 978-84-616-2661-8.
Guba, E. G., & Lincoln, Y. S. (1989). Fourth generation evaluation . Newbury Park: Sage.
Kandiko, C. B., & Kinchin, I. M. (2012). What is a doctorate? A concept-mapped analysis of process versus product in the supervision of lab-based PhDs. Educational Research , 54 (1), 3–16. https://doi.org/10.1080/00131881.2012.658196 .
Lee, A. (2008). How are doctoral students supervised? Concepts of doctoral research supervision. Studies in Higher Education , 33 (3), 267–281. https://doi.org/10.1080/03075070802049202 .
Mahmood, K. (2016). Do people overestimate their information literacy skills? A systematic review of empirical evidence on the Dunning-Kruger effect. Communications in Information Literacy , 10 (2), 199–212. https://doi.org/10.15760/comminfolit.2016.10.2.24 .
Marshall, S., & Shepherd, D. (2016). E-learning in tertiary education. Highlights from Ako Aotearoa projects . Wellington: Ako Aotearoa https://akoaotearoa.ac.nz/download/ng/file/group-4/e-learning-in-tertiary-education-highlights-from-ako-aotearoa-research.pdf .
Mayring, P. (2000). Qualitative content analysis. Forum: Qualitative Social Research , 1 (2) Retrieved from https://search.proquest.com/docview/867646667?accountid=14700 .
Nichols, M., Anderson, B., Campbell, M., & Thompson, J. (2014). An online orientation to open, flexible and distance learning Ako Aotearoa and the distance education Association of New Zealand (DEANZ). https://ako.ac.nz/knowledge-centre/an-online-orientation-to-open-flexible-and-distance-learning/ .
Prenksy, M. (2001). Digital natives, digital immigrants, part II. Do they really think differently? On the . Horizon , 9 (6), 1–6.
Silverman, D. (2001). Interpreting qualitative data. 2nd Ed. London: Sage.
Sim, K. N., & Butson, R. (2013). Do undergraduates use their personal computers to support learning? Procedia - Social and Behavioral Sciences , 103 , 330–339. https://doi.org/10.1016/j.sbspro.2013.10.341 .
Sim, K. N., & Butson, R. (2014). To what degree are undergraduate students using their personal computers to support their daily study practices? IAFOR Journal of Education , 2 (1), 158–171 Retrieved from http://search.ebscohost.com/login.aspx?direct=true&db=eric&AN=EJ1080348&site=ehost-live .
Stensaker, B., Maassen, P., Borgan, M., Oftebro, M., & Karseth, B. (2007). Use, updating and integration of ICT in higher education: Linking purpose, people and pedagogy. Higher Education , 54 , 417–433. https://doi.org/10.1007/s10734-006-9004-x .
Thomas, D. R. (2006). A general inductive approach for analyzing qualitative evaluation data. American Journal of Evaluation , 27 (2), 237–246. https://doi.org/10.1177/1098214005283748 .
Wetton, N. M., & McWhirter, J. (1998). Images and curriculum development in health education. In J. Prosser (Ed.), Image-based research: A sourcebook for qualitative researcher , (pp. 263–283). London: Falmer Press.
Zhou, E., & Okahana, H. (2019). The role of department supports on doctoral completion and time-to-degree. Journal of College Student Retention: Research, Theory & Practice , 20 (4), 511–529. https://doi.org/10.1177/1521025116682036 .
Download references
Acknowledgements
We thank the students and supervisors who shared their reflections and willingly engaged with us in this project.
We acknowledge the support of Ako Aotearoa, The National Centre for Tertiary Teaching Excellence, New Zealand through its Regional Hub Project Fund (RHPF), and the support of our institutions, University of Otago and Victoria University of Wellington.
Author information
Authors and affiliations.
Distance Learning, University of Otago, Dunedin, New Zealand
Sarah J. Stein
Centre for Academic Development, Victoria University of Wellington, Wellington, New Zealand
Kwong Nui Sim
You can also search for this author in PubMed Google Scholar
Contributions
The authors are responsible for the entire project that is reported in this paper. The writing of the manuscript was led by the first author in collaboration with the second author. The authors read and approved the final manuscript.
Corresponding author
Correspondence to Sarah J. Stein .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Stein, S.J., Sim, K.N. Enhancing the roles of information and communication technologies in doctoral research processes. Int J Educ Technol High Educ 17 , 34 (2020). https://doi.org/10.1186/s41239-020-00212-3
Download citation
Received : 02 February 2020
Accepted : 05 May 2020
Published : 10 September 2020
DOI : https://doi.org/10.1186/s41239-020-00212-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Doctoral research and supervision
- Information and communication technologies
- Participative drawing
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Technology articles from across Nature Portfolio
Latest research and reviews.
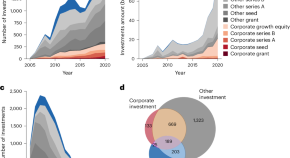
The effects of corporate investment and public grants on climate and energy startup outcomes
Investment in climate and energy startups is growing in the United States. Here the authors show that public grants back high-risk areas, and that publicly funded startups exit at higher rates with corporate backing than with other private investment.
- Kathleen M. Kennedy
- Morgan R. Edwards
- Kavita Surana
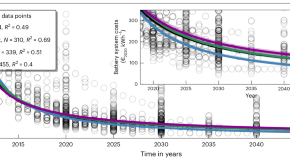
Rapidly declining costs of truck batteries and fuel cells enable large-scale road freight electrification
The costs of battery and fuel cell systems for zero-emission trucks are primed to decline much faster than expected, boosting prospects for their fast global diffusion and electrification of freight transport, with battery-electric trucks probably leading.
- Steffen Link
- Annegret Stephan
- Patrick Plötz
User factors affecting the use of digital services in five European regions and countries
- Joy Goodman-Deane
- Silvia Gaggi

Sync fast and solve things—best practices for responsible digital health
- Constantin Landers
- Alessandro Blasimme
- Effy Vayena
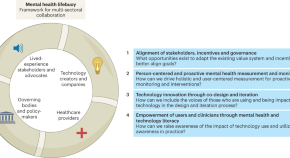
Rethinking technology innovation for mental health: framework for multi-sectoral collaboration
In this Perspective, the authors make recommendations on better aligning stakeholders, including those in technology, practitioners and researchers, to increase collaboration and governance in technology and mental health.
- Sachin R. Pendse
- Mary Czerwinski
The health risks of generative AI-based wellness apps
AI-enabled wellness apps exist in a regulatory gray area and may pose risks if used to manage mental health issues; this Perspective outlines the possible risks to users and the implications for app developers and regulators.
- Julian De Freitas
- I. Glenn Cohen
News and Comment

How does ChatGPT ‘think’? Psychology and neuroscience crack open AI large language models
Researchers are striving to reverse-engineer artificial intelligence and scan the ‘brains’ of LLMs to see what they are doing, how and why.
- Matthew Hutson

The US Congress is taking on AI — this computer scientist is helping
Kiri Wagstaff, who temporarily shelved her academic career to provide advice on federal AI legislation, talks about life inside the halls of power.
- Nicola Jones

Who’s making chips for AI? Chinese manufacturers lag behind US tech giants
Researchers in China say they are finding themselves five to ten years behind their US counterparts as export restrictions bite.
- Jonathan O'Callaghan
Smart food packaging commercialization
Smart food packaging technologies can actualize real-time, in situ food quality monitoring, increasing food safety and decreasing food waste. Here, we detail challenges that hinder the commercialization of such smart packaging systems and identify opportunities to facilitate their translation from prototype to product.
- Shadman Khan
- Zeinab Hosseinidoust
- Tohid F. Didar

Are robots the solution to the crisis in older-person care?
Social robots that promise companionship and stimulation for older people and those with dementia are attracting investment, but some question their benefits.
- Tammy Worth

NATO is boosting AI and climate research as scientific diplomacy remains on ice
As the military alliance created to counter the Soviet Union expands, it is prioritizing studies on how climate change affects security, cyberattacks and election interference.
- Natasha Gilbert
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Internet of things technology, research, and challenges: a survey
- Published: 02 May 2024
Cite this article

- Amit Kumar Vishwakarma 1 ,
- Soni Chaurasia 2 ,
- Kamal Kumar 3 ,
- Yatindra Nath Singh 4 &
- Renu Chaurasia 5
128 Accesses
Explore all metrics
The world of digitization is growing exponentially; data optimization, security of a network, and energy efficiency are becoming more prominent. The Internet of Things (IoT) is the core technology of modern society. This paper is based on a survey of recent and past technologies used for IoT optimization models, such as IoT with Blockchain, IoT with WSN, IoT with ML, and IoT with big data analysis. Suppose anyone wants to start core research on IoT technologies, research opportunities, challenges, and solutions. In that case, this paper will help me understand all the basics, such as security, interoperability, standards, scalability, complexity, data management, and quality of service (QoS). This paper also discusses some recent technologies and the challenges in implementation. Finally, this paper discusses research possibilities in basic and applied IoT Domains.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

IoT Reference Model

RETRACTED ARTICLE: A Review and State of Art of Internet of Things (IoT)

Blockchain for healthcare data management: opportunities, challenges, and future recommendations
Data availability.
Available on request.
Ghorbani HR, Ahmadzadegan MH (2017) Security challenges in internet of things: survey. In: 2017 IEEE conference on wireless sensors (ICWiSe)
Brock DL (2013) The electronic product code (EPC) a naming scheme for physical objects. http://www.autoidlabs.org/ uploads/media/MIT-AUTOID-WH-002.pdf
IoT Analytics (2014) Why the internet of things is called internet of things: definition, history, disambiguation. https://iot-analytics.com/internet-of-things-definition/
Internet of Things (2005) International telecommunication union (ITU), Geneva. https://www.itu.int/net/wsis/tunis/newsroom/stats/The-Internet-of-Things-2005.pdf
Internet of Things (2010) https://en.oxforddictionaries.com/definition/us/ internetofthings
Manyika Chui M, Bisson P, Woetzel J, Dobbs R, Bughin J, Aharon D (2015) Unlocking the potential of the internet of things. https://www.mckinsey.com/~/media/McKinsey
Vermesan O, Friess P, Guillemin P, Gusmeroli S, Sundmaeker H, Bassi A, Jubert IS, Mazura M, Harrison M, others (2011) Internet of things strategic research roadmap
Artik cloud (2017) https://developer.artik.cloud/documentation/getting-started/index.html
Fusion Connect (2014) https://autodeskfusionconnect.com/iot-devices
(2016) https://docs.aws.amazon.com/iot/latest/developerguide/what-is-aws-iot.html
Guth J, Breitenbücher U, Falkenthal M, Leymann F, Reinfurt L (2016) Comparison of IoT platform architectures: A field study based on a reference architecture. In: 2016 Cloudification of the internet of things (CIoT)
Balani, Naveen and Hathi, Rajeev, Enterprise IoT: A Definitive Handbook. In: CreateSpace Independent Publishing Platform, 2015
GE Predix (2017) https://docs.predix.io/en-US/platform
Soliman M, Abiodun T, Hamouda T, Zhou J, Lung CH, (2013) Smart home: integrating internet of things with web services and cloud computing. In: 2013 IEEE 5th International conference on cloud computing technology and science
Google Cloud (2016) https://cloud.google.com/solutions/iot-overview
Familiar B (2015) IoT and microservices. In: Microservices, IoT, and Azure. Apress, Berkeley, CA. In: Internet of Things;Web services:Azure IOT
Microsoft IoT platform (2015) https://docs.microsoft.com/en-us/rest/api/iothub/?redirectedfrom=MSDN
High R (2012) The era of cognitive systems: an inside look at ibm watson and how it works. In: Internet of Things;Web services:Azure IOT
IBM Watson IoT (2017) https://www.ibm.com/internet-of-things
Deering S, Hinden R (2017) Internet Protocol, Version 6 (IPv6) Specification. https://tools.ietf.org/html/rfc8200
WInter Ed T, Thubert P, Brandt A, Hui J, Kelsey R, Levis P, Pister K, Struik R (2012) ipv6 routing protocol for low-power and lossy networks. https://tools.ietf.org/html/rfc6550
Saputro N, Akkaya K, Uludag S (2012) A survey of routing protocols for smart grid communications. http://www.sciencedirect.com/science/article/pii/S1389128612001429 , vol 56
Yi P, Iwayemi A, Zhou C (2011) Building automation networks for smart grids. In: International journals of digital multimedia broadcasting
Fairhurst G Jones T (2018) Transport features of the user datagram protocol (UDP) and lightweight UDP (UDP-Lite). https://www.rfceditor.org/info/rfc8304
Palattella MR, Accettura N, Vilajosana X, Watteyne T, Grieco LA, Boggia G, Dohler M (2013) Standardized protocol stack for the internet of (Important) things. In: IEEE communications surveys tutorials, vol 15
Karagiannis V, Chatzimisios P, Vazquez-Gallego F, Alonso-Zarate J (2015) A survey on application layer protocols for the internet of things. Transaction on IoT and Cloud Computing
Banks A, Gupta R (2014) MQTT Version 3.1.1. Edited by Andrew Banks and Rahul Gupta. OASIS Committee Specification Draft 02 / Public Review Draft 02. http://docs.oasis-open.org/mqtt/mqtt/v3.1.1/csprd02/mqtt-v3.1.1-csprd02.html
Bormann C, Castellani AP, Shelby Z (2012) CoAP: An Application Protocol for Billions of Tiny Internet Nodes. IEEE Internet Computing
Shelby Z, Hartke K, Bormann C (2014) The constrained application protocol (CoAP). https://tools.ietf.org/html/rfc7252
Johansson P, Kazantzidis M, Kapoor R, Gerla M (2001) Bluetooth: an enabler for personal area networking. IEEE Network
Kirsche M, Klauck R (2012) Unify to bridge gaps: Bringing XMPP into the Internet of Things. In: 2012 IEEE international conference on pervasive computing and communications workshops
Naik N, Jenkins P (2016) Web protocols and challenges of Web latency in the Web of Things. In: 2016 Eighth international conference on ubiquitous and future networks (ICUFN)
Han Dm, Lim Jh (2010) Smart home energy management system using IEEE 802.15.4 and zigbee. IEEE Transactions on Consumer Electronics
Eriksson J, Balakrishnan H, Madden S (2008) Cabernet: vehicular content delivery using wifi. https://doi.org/10.1145/1409944.1409968
Ratasuk R, Vejlgaard B, Mangalvedhe N, Ghosh A (2016) NB-IoT system for M2M communication. In: 2016 IEEE Wireless communications and networking conference
ANDRIES MI, BOGDAN I, NICOLAESCU SV, SCRIPCARIU L (2007) WiMAX features and applications. http://www.agir.ro/buletine/687.pdf
Kucharzewski L, Kotulski Z (2014) WiMAX networks architecture and ata security. Annales UMCS Informatica AI X
Adams JT (2006) An introduction to IEEE STD 802.15.4. In: 2006 IEEE aerospace conference
Atzori L, Iera A, Morabito G (2010) The internet of things: a survey. journal = Computer Networks. http://www.sciencedirect.com/science/article/pii/S1389128610001568 , vol.54
Mainetti L, Patrono L Vilei A (2011) Evolution of wireless sensor networks towards the Internet of Things: A survey. In: SoftCOM 2011, 19th international conference on software, telecommunications and computer networks
Miorandi D, Sicari S, De Pellegrini F, Chlamtac I (2012) Internet of things: Vision, applications and research challenges. http://www.sciencedirect.com/science/article/pii/S1570870512000674 , vol 10, pp 1497–1516
Xu LD, He W, Li S (2014) Internet of things in industries: a survey. In: IEEE Transactions on industrial informatics, vol 10
Botta A, De Donato W, Persico V, Pescapé A (2016) Integration of cloud computing and internet of things: a survey. http://www.sciencedirect.com/science/article/pii/S0167739X15003015 , vol 56
Seyedzadegan M, Othman M (2013) IEEE 802.16: WiMAX Overview, WiMAX Architecture. http://www.ijcte.org/papers/796-Z1030.pdf
Abdulzahra AM, Al-Qurabat AK, Abdulzahra SA (2023) Optimizing energy consumption in WSN-based IoT using unequal clustering and sleep scheduling methods. Internet of Things 22:100765
Chaurasia S, Kumar K (2023) ACRA:Adaptive Meta-heuristic Based Clustering and Routing Algorithm for IoT-Assisted Wireless Sensor Network. Peer to Peer Networking and Application. Springer
Chaurasia S, Kumar K (2023) MBASE: Meta-heuristic Based optimized location allocation algorithm for baSE station in IoT assist wireless sensor networks. Multimedia Tools and Applications, pp 1–33
Senthil GA, Raaza A, Kumar N (2022) Internet of things energy efficient cluster-based routing using hybrid particle swarm optimization for wireless sensor network. Wirel Pers Commun 122.3: 2603-2619
Prasanth A, Jayachitra S (2020) A novel multi-objective optimization strategy for enhancing quality of service in IoT-enabled WSN applications. Peer Peer Netw Appl 13:1905–1920
Article Google Scholar
Vaiyapuri T, et al (2022) A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing. Wirel Pers Commun 127.1: 39-62
Dhiman G, Sharma R (2022) SHANN: an IoT and machine-learning-assisted edge cross-layered routing protocol using spotted hyena optimizer. Complex Intell Syst 8(5):3779–3787
Seyfollahi A, Taami T, Ghaffari A (2023) Towards developing a machine learning-metaheuristic-enhanced energy-sensitive routing framework for the internet of things. Microprocess Microsyst 96:104747
Donta PK et al (2023) iCoCoA: intelligent congestion control algorithm for CoAP using deep reinforcement learning. J Ambient Intell Humaniz Comput 14(3):2951–2966
Rosati R et al (2023) From knowledge-based to big data analytic model: a novel IoT and machine learning based decision support system for predictive maintenance in industry 4.0. J Intell Manuf 34.1:107–121
Babar M et al (2022) An optimized IoT-enabled big data analytics architecture for edge-cloud computing. IEEE Internet Things J 10(5):3995–4005
Article MathSciNet Google Scholar
Lv Z, Singh AK (2021) Big data analysis of internet of things system. ACM Trans Internet Technol 21(2):1–15
Qiu Y, Zhu X, Jing L (2021) Fitness monitoring system based on internet of things and big data analysis. IEEE Access 9:8054–8068
Rahman A et al (2021) Smartblock-sdn: An optimized blockchain-sdn framework for resource management in iot. IEEE Access 9:28361–28376
Zhao Y et al (2023) A lightweight model-based evolutionary consensus protocol in blockchain as a service for IoT. IEEE Transactions on Services Computing
Saba T et al (2023) Blockchain-enabled intelligent iot protocol for high-performance and secured big financial data transaction. IEEE Transactions on Computational Social Systems
Abed S, Reem J, Bassam JM (2023) A review on blockchain and IoT integration from energy, security and hardware perspectives. Wirel Pers Commun 129(3):2079–2122
Javanmardi S et al (2023) An SDN perspective IoT-Fog security: A survey. Comput Netw 229:109732
Qayyum A et al (2023) Secure and trustworthy artificial intelligence-extended reality (AI-XR) for metaverses. ACM Computing Surveys
Rawat P, Chauhan S (2021) Clustering protocols in wireless sensor network: A survey, classification, issues, and future directions. Comput Sci Rev 40:100396
Albouq SS et al (2023) A survey of interoperability challenges and solutions for dealing with them in IoT environment. IEEE Access 10:36416–36428
Rana B, Singh Y, Singh PK (2021) A systematic survey on internet of things: Energy efficiency and interoperability perspective. Trans Emerg Telecommun Technol 32(8):e4166
Sasaki Y (2021) A survey on IoT big data analytic systems: current and future. IEEE Internet of Things Journal 9(2):1024–1036
Alfandi O et al (2021) A survey on boosting IoT security and privacy through blockchain: Exploration, requirements, and open issues. Cluster Comput 24(1):37–55
Bian Jet al. Machine learning in real-time internet of things (iot) systems: A survey. IEEE Internet of Things J 9(11): 8364–8386
Donta PK et al (2022) Survey on recent advances in IoT application layer protocols and machine learning scope for research directions. Digital Commun Netw 8(5):727–744
Download references
No funding was received to carry out this work.
Author information
Authors and affiliations.
Management science and technology, Khalifa University, Abu Dhabi, UAE
Amit Kumar Vishwakarma
Computer science & Engineering, SGT University, Gurugram, India
Soni Chaurasia
Department of Information Technology, IGDTUW, New Delhi, India
Kamal Kumar
Electrical Engineering, IIT Kanpur, Kanpur, India
Yatindra Nath Singh
Computer science & Engineering, AIT, Rooma, Kanpur, India
Renu Chaurasia
You can also search for this author in PubMed Google Scholar
Contributions
Equally contributed.
Corresponding author
Correspondence to Soni Chaurasia .
Ethics declarations
Conflicts of interest.
No conflict of interest.
Consent to Publish
As per journal policy.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Vishwakarma, A.K., Chaurasia, S., Kumar, K. et al. Internet of things technology, research, and challenges: a survey. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-19278-6
Download citation
Received : 18 October 2023
Revised : 13 March 2024
Accepted : 18 April 2024
Published : 02 May 2024
DOI : https://doi.org/10.1007/s11042-024-19278-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Semantic intelligence
- IoT protocol
- IoT application
- Research possibilities
- IoT Platforms
- IoT optimization models
- Find a journal
- Publish with us
- Track your research
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Information Technology
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
- Last »
- Information Systems Follow Following
- Computer Science Follow Following
- Informatics Follow Following
- Education Follow Following
- Artificial Intelligence Follow Following
- Data Mining Follow Following
- E-learning Follow Following
- Social Media Follow Following
- Information Systems (Business Informatics) Follow Following
- Enterprise Architecture Follow Following
Enter the email address you signed up with and we'll email you a reset link.
- Academia.edu Publishing
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Elsevier - PMC COVID-19 Collection

Information technology solutions, challenges, and suggestions for tackling the COVID-19 pandemic
a Department of Information Technology & Decision Sciences, Old Dominion University, Norfolk, VA, 23529, USA
Zuopeng (Justin) Zhang
b Department of Management, Coggin College of Business, University of North Florida, Jacksonville, FL 32224, USA
Various technology innovations and applications have been developed to fight the coronavirus pandemic. The pandemic also has implications for the design, development, and use of technologies. There is an urgent need for a greater understanding of what roles information systems and technology researchers can play in this global pandemic. This paper examines emerging technologies used to mitigate the threats of COVID-19 and relevant challenges related to technology design, development, and use. It also provides insights and suggestions into how information systems and technology scholars can help fight the COVID-19 pandemic. This paper helps promote future research and technology development to produce better solutions for tackling the COVID-19 pandemic and future pandemics.
1. Introduction
The COVID-19 pandemic has caused an immense impact on hospital systems, businesses, schools, and the economy. Telemedicine, telework, and online education become essential to help society slow down the spread of the coronavirus ( Chavez & Kounang, 2020 ; Loh & Fishbane, 2020 ; Young, 2020 ). The pandemic has generated a rapid demand for efforts to use innovative technologies to cope with damage from COVID-19 on our life ( O’Leary, 2020 ).
The pandemic has not only raised opportunities to advance technology-based solutions but also provided a rare opportunity to study the research and practice of technology, including information management, work practices, and design and use of technologies ( Sein, 2020 ). The quick transition to telehealth, telework, and online education in response to the coronavirus threat is a reminder that digital technology brings many benefits and can play an essential role in managing and reducing the risks caused by the lockdown during the pandemic and even after the pandemic ( Richter, 2020 ). It is well known that information systems and information technology (IS/IT) play an important role in healthcare, clinical decision support, emergency/crisis response, and risk management ( Angst & Agarwal, 2009 ; Ben-Assuli & Padman, 2020 ; Chen, Sharman, Chakravarti, Rao, & Upadhyaya, 2008 ; Thompson, Whitaker, Kohli, & Jones, 2019 ). Many IS/IT professionals are working in various ways to help fight the pandemic, including developing products to combat the virus, tracking and predicting its spread, and protecting hospitals from cyberattacks ( Mingis, 2020 ). Information systems and technology scholars should contribute to this global effort to fight the COVID-19 and future pandemics ( Ågerfalk, Conboy, & Myers, 2020 ) by leveraging their previous experience and knowledge on responding to crises, decision making, remote working, managing virtual teams, analyzing large data sets, etc. There is currently a shortage of research contributions in the areas of information systems (IS) to help fight the COVID-19.
The pandemic has implications for the design, development, and use of information systems and technologies ( Sein, 2020 ). Information systems and technology researchers and practitioners can help conduct an analysis of the COVID-19 pandemic data and engage in potential emerging research topics, such as facilitating work while social distancing, contactless commerce, face recognition when wearing masks or in other crises, COVID-19 apps in terms of privacy, crowdsourcing, donating data, and tracking cases, robotics and their impact on organizations, monitoring vulnerable vs. non-vulnerable for their impact on work, changing patterns of supply and demand for fragile supply chains and autonomic systems, virtual communication tools, online education breakthroughs, and separation of work and private life ( O’Leary, 2020 ). Rai (2020) also identified some opportunities for IS research to contribute toward building resilience to pandemics and extreme events including (i) redesigning the public health system from reactive to proactive through the use of real-time surveillance systems and contact tracing tools to stem transmission, (ii) transforming organizations through enhancing crisis-driven agility and reducing crisis-revealed fragility, and (iii) empowering individuals and communities through adapting, coping, and stemming the infodemic. Dwivedi et al. (2020) present an assessment of critical challenges of COVID-19 through an information system and technological perspective and offer insights for research and recommendations studying the impact of COVID-19 on information management research and practice in transforming education, work, and life.
To reduce the overlap with O’Leary (2020) and Rai (2020) , this paper primarily focuses on technology integration from the data, system, and people perspectives to discuss how information systems and technology scholars could contribute knowledge and insights to help fight the pandemic. As information systems and technologies are becoming foundational to society, information systems and technology scholars are in an excellent position to leverage their experience and knowledge with information systems and various technologies to improve existing systems and technology practice and help the society become digitally resilient to future large-scale disruptions.
2. Existing IT solutions
This paper uses the data-people-system framework to examine technology solutions to mitigate the impact of the COVID-19 pandemic. The data-people-system framework by Bardhan, Chen, and Karahanna (2020) demonstrates a multidisciplinary roadmap for controlling and managing chronic diseases by focusing on the following three components: (1) extraction, integration, and delivery of health data; (2) interoperability of systems; and (3) guidelines and interface to guide people’s behavior. It must be noted that the original data-people-system framework was proposed for chronic disease management, which needs further development to be proactive and take account of the pandemic context.
The COVID-19 pandemic has revealed the urgent need to redesign the public health system from reactive to proactive and develop innovations that will provide real-time information for proactive decision-making at the local, state, and national levels of public health systems ( Rai, 2020 ). COVID-19 is different from chronic diseases as it is highly contagious, can pass from people to people, and has a high mortality rate. Additionally, as COVID-19 is a new disease, scientific understanding of the virus that causes it, medical response, and actions by governments and organizations continue to evolve. The impact of COVID-19 on people and society is changing daily in ways that would have been unthinkable. As the current pandemic situation and its consequence continue to remain fluid, combating the COVID-19 pandemic requires strong coordination of various resources.
In response to the threats and risks posed by COVID-19, this paper adopts the data-people-system framework to examine the existing technology solutions for fighting against the COVID-19 pandemic and identify their challenges and potential opportunities for information systems and technology researchers. In particular, we have conducted an extensive search using academic databases and web search engines with a variety of queries related to technology, coronavirus, and COVID-19, synthesizing the related discussions in newspapers, news websites, blogs, white papers, practitioner websites, grey literature or academic literature to help understand the existing information systems and technology solutions and the roles that they could play in this challenging time of the pandemic.
Some new technology applications such as mobile COVID-19 contact tracing apps and chatbots have been recently developed to fight this pandemic. Applying these technologies can help reduce the impact of the coronavirus pandemic on people, organizations, and society. Effective and innovative use of emerging technologies can help identify community spread of the coronavirus, monitor the condition of the infected patients, improve the treatment of COVID-19 infected patients, and help develop medical treatments and vaccines ( Johnstone, 2020 ). This section evaluates these technology applications based on the data-people-system framework by Bardhan et al. (2020) .
Technologies powered by artificial intelligence (AI) including machine learning, image recognition, and deep learning algorithms can be used for early detection and diagnosis of the infection, more rapid drug discovery for developing new treatments ( Brohi, Jhanjhi, Brohi, & Brohi, 2020 ). A few companies also repurposed existing AI systems that were initially designed for other areas to assist in social distancing enforcement and contract tracing ( Sipior, 2020 ).
3D Printing Technology can help make face masks and other Personal Protective Equipment (PPE) for healthcare workers. Markforged has partnered with Neurophotometrics to produce 3D printed rayon wrapped nasopharyngeal (NP) swabs for COVID-19 testing. The swabs take less than three minutes to make, can be much quicker at collecting viral particles ( Markforged, 2020 ).
Big Data Analytics can be used to identify people that need quarantine based on their travel history, predict the COVID-19 curve, speed up the development of antiviral drugs and vaccines, and advance the understanding of the COVID-19 spread across both time and space. In Taiwan, big data analytics has been successfully applied to help identify COVID-19 cases and generate real-time alerts through analyzing clinical visits, travel history, and clinical symptoms ( Wang, Ng, & Brook, 2020 ; Wang, Zha, et al., 2020 ; Watson, Ives, & Piccoli, 2020 ).
HPC infrastructures and supercomputers are needed to address complex scientific problems and process big datasets in shorter time frames in order to develop new drugs and vaccines. The COVID-19 High-Performance Computing Consortium was launched to leverage the computing resources and supercomputers in the US. The consortium includes 16 public and private entities such as the US Department of Energy (DoE), IBM, and other academic and industry leaders ( Woo, 2020 ).
Mobile apps via smartphones and video-conferencing tools can be used to track the movements of individuals, alert people from visiting COVID-19 hotspots, help doctors to diagnose patients through video services and telemedicine/telehealth, support people with online shopping, e-learning, online meetings, and telework ( Marr B., 2020 ). Various phone and network-powered apps have been developed to help healthcare workers and ordinary people in this crisis. For example, the U.S. National Science Foundation funded an award to support researchers at Princeton University in developing a system to deploy a firmware update to mobile phones to provide proximity tracking ability for health officials. To preserve users’ privacy, the key to the proximity data would be stored on the phone itself and could only be unlocked when the phone’s owner voluntarily provided it to health officials. Suppose a person tests positive for a disease such as COVID-19. In that case, health officials could then use the system to automatically identify all other cellphone users who were within a certain distance of the infected person for a certain time. The time and distance could be determined by health officials based on knowledge of the disease. Healthcare departments can contact those potentially infected people, advise them of the exposure, and instruct them to get tested for the disease and self-quarantine as needed ( WHO, 2020 ).
Robots have been applied to fight the coronavirus outbreak. For example, hospitals use robots as support systems to deliver food and medicine, disinfect rooms, and other hotspots without direct human interaction with patients. A CNN news report shows that doctors in Seattle have used a telepresence robot to treat the first confirmed patient who tests positive for coronavirus in the United States ( Chavez & Kounang, 2020 ). Drones also are used to deliver medical supplies, patrol public areas, track non-compliance to quarantine mandates, and so on ( Marr B., 2020 ; Marr N., 2020 ).
The Internet of Things (IoT) can be used for the surveillance of people infected by coronavirus to reduce the spread of the coronavirus ( Kumar, Kumar, & Shah, 2020 ). IoT consists of several functional components: data collection, transfer, analytics, and storage. IoT sensors installed on mobile phones, robots, or health monitors can be used to collect data. Next, sensor data would be sent to the cloud server for processing, analytics, and decision-making. As an example, IoT helps check whether patients follow quarantine requirements. IoT can also be used to take the remote patients’ temperatures and then transmit the data through mobile devices to the doctors to monitor, track, and alert while reducing the chance for coronavirus inflections ( He, 2020 ). Additional roles of IoT technologies include the use of smart wearable devices in response to COVID-19 in early diagnosis, quarantine time, and after recovery ( Nasajpour et al., 2020 ).
Blockchain is a distributed ledger technology that records online transactions. It is regulated through a consensus mechanism and is secured with cryptography ( Chong, Lim, Hua, Zheng, & Tan, 2019 ). As an example, a smartphone app that leverages blockchain technology and AI was developed to help fight the coronavirus pandemic. Blockchain technology enables the app to give each participant a "digital identity" controlled by a private key that brings access to a digital version of paper certificates issued by the government. These allow the confirmed healthy people to leave home to buy food or to work ( Sinclair, 2020 ). Blockchain has also been used to prevent the information from being manipulated by unauthorized parties. During the outbreak, a Chinese payment processor and financial services company used blockchain technology to monitor the process of processing claims and making payouts in a more secure and trustworthy way ( News Staff, 2020 ). Blockchain technology has been applied to resolve the tension and trust issues between maintaining privacy and addressing public health needs, such as tracking infected patients in the fight against COVID-19 ( Khurshid, 2020 ).
All the above technologies require the integration of data, people, and systems. Based on their primary focus and original design intention for use in practice, we broadly classify them into three categories. The data-centric technologies for combating COVID-19 include machine learning/deep learning, big data analytics, and HPC infrastructure. The people-centric technologies include robots and 3D printing technology; they are used to serve patients better and protect healthy people from infections with the support of specific systems. The system-centric technologies include digital contact tracing apps, the Internet of Things, and Blockchain; they are developed based on system concepts to monitor patients and prevent healthy people from contracting coronavirus. Some of these technologies are interrelated and may transcend multiple categories as they are being used in dealing with the pandemic, depending on how creative people are using them in varying contexts. For example, big data analytics that identify people who need quarantine could have system-centric or people-centric aspects depending on the specific purposes and use by different government agencies, health authorities, hospitals, and organizations. Table 1 summarizes the three categories of technologies and their required support from data, people, and systems.
Summary of technology solutions for COVID-19.
3. Challenges
The COVID-19 pandemic has exposed the weaknesses of existing public health systems. The use of technologies to combat the pandemic raises challenges in many aspects. The specific nature of the COVID-19 pandemic requires strong coordination of connected data, people, and systems ( Bardhan et al., 2020 ) to facilitate worldwide collaboration in fighting against it. Traditionally, public health agencies and healthcare stakeholders have not used the same systems, data formats, or standards, hampering the ability to identify trends and develop interventions against the pandemic. Public health researchers, epidemiologists, and government officials need to be connected via integrated systems with connected data to understand the evolving pandemic better and make collective decisions on addressing this crisis. As people play a crucial role in this fight against the COVID-19, it is essential to connect, coordinate, and support various stakeholders through innovative and integrated technologies.

3.1. Connecting systems to integrate technologies
Emerging technologies including the IoT, big-data analytics, AI, and blockchain can be integrated to develop smart strategies for addressing immediate challenges caused by the coronavirus. For example, Facebook has used artificial intelligence and big data technologies to tap into satellite imagery and census data to generate maps that display population density, demographics, and travel patterns in order to help decide where to send supplies or how to reduce the spread ( Holt, 2020 ). Big data analysis of geographic information systems (GIS) and IoT sensor data collected from infected patients can assist epidemiologists to trace patient zero and help identify close contacts of the infected patients ( He, 2020 ). The U.S. National Science Foundation recently funded a RAPID award that explores the capabilities and potential of integrating social media big data, geospatial data, and AI technologies to enable and transform spatial epidemiology research and risk communication. The emerging convergence of blockchain, the IoT, and AI holds great promise for addressing the issues of trust and security in public health ( Gurgu, Andronie, Andronie, & Dijmarescu, 2019 ; Singh, Rathore, & Park, 2020 ). For example, medical device data and non-personal sensor data collected by IoT can be stored and shared on the blockchains. Patients’ personal data can still be stored in the hospitals’ enterprise systems due to privacy regulations such as the GDPR ( Agbo, Mahmoud, & Eklund, 2019 ; Onik, Aich, Yang, Kim, & Kim, 2019 ). AI and big data technologies can be leveraged to analyze and visualize both on-chain and off-chain data and provide near real-time analytics and recommendations to relevant stakeholders through customized dashboards.
Currently, most systems and apps that have been used to deal with the pandemic are poorly inter-connected since they are developed by different government agencies, health authorities, and organizations. There is a lack of systematic frameworks and tools to accomplish systematic integration across various technologies in the global response against pandemic challenges.
To integrate these different technologies, guidelines and systematic efforts are required to coordinate the collection of large amounts of quality data related to coronavirus cases. The design of effective big data analytics and AI algorithms requires public health departments and hospitals to provide a large amount of reliable and high-quality data. Due to a lack of standards, the integration of multiple data sources for promoting interoperability is challenging. Some data sources may be well structured, while others are not ( Pham, Nguyen, Huynh-The, Hwang, & Pathirana, 2020 ). There is also a need to generate standardized protocols to facilitate communication across systems without compromising data security. Governments, leading tech firms, health organizations, and other relevant stakeholders need to collaborate efficiently and effectively to define the standard, protocols, data formats and types, etc.
Information systems and technology scholars have been examining system integration in enterprise or organizational environments over the past several decades ( Henningsson, Yetton, & Wynne, 2018 ; Ravichandran & Rai, 2000 ; Xu, 2011 ). Information systems and technology scholars also studied the role of information systems in crisis, disaster, and emergency response ( Chen et al., 2008 ; Pan, Pan, & Leidner, 2012 ; Valecha, Rao, Upadhyaya, & Sharman, 2019 ). Information systems and technology researchers should take the opportunity to offer their expertise in system integration and experience with emergency or crisis response systems to provide recommendations and strategies to help developers with various systems and technology integration efforts.
3.2. Connecting data to share best practices
As the World Health Organization (2020) suggests, new collaboration and knowledge sharing are needed to deliver targeted solutions through a coordinated effort to support countries facing stages of this epidemic in different ways and at different times. Faced with a global pandemic, countries need to work together to share data, information, resources, effective practices, and strategies to combat the coronavirus. In addition, global collaboration among relevant stakeholders between organizations and governments will be crucial to coordinating the sharing and use of data and knowledge to solve the problems we encountered during this pandemic. For example, China took extraordinary measures for the shutdown of Wuhan, a large city with millions of people, to control the spread of the coronavirus ( Lin et al., 2020 ). Useful experience and lessons related to its efficacy as a containment measure could be valuable for other countries who are considering similar measures. Data integration and knowledge management (KM) technologies such as web portals, knowledge repositories, and online communities of practice can be used to empower data connections to leverage resources more effectively and efficiently at a lower cost ( Bardhan et al., 2020 ; Pan, Cui, & Qian, 2020 ).
Knowledge-based systems such as expert systems and intelligent decision technologies have been used to support health workers in detecting and diagnosing patients, and providing decision-making support for relevant healthcare stakeholders and decision-makers in a pandemic crisis ( O’Leary, 2020 ; Rehfuess et al., 2019 ). Data mining and visualization technologies have been used to discover and visualize knowledge evolution across time and locations as the coronavirus outbreak continues to evolve. Online health communities have been established to help healthcare workers, patients, and other stakeholders learn about COVID-19, symptoms, and the effectiveness of treatments ( Yan & Tan, 2014 ; Ziebland et al., 2004 ). However, these systems often operate in a silo, and the data, information, and knowledge stored in their systems are not widely shared. To allow various systems and stakeholders in different communities of practice to share knowledge within and across their individual areas, we need to create an environment to encourage people across countries to share knowledge instead of keeping or holding the knowledge. In the context of a coronavirus outbreak, strategies could be developed to assess the quality of the knowledge and help systems break down silos that hinder communication and sharing data more efficiently.
Besides, behavioral issues need to be addressed to facilitate the sharing of data and best practices among stakeholders. Over the years, there have been a number of calls for information systems and technology researchers to consider the unintended or negative consequences of technologies ( Chiasson, Davidson, & Winter, 2018 ). IT professionals have been rushing to build apps, services, and systems for contact tracing, tracking, and quarantine monitoring. Some of these technologies are lightweight for short-term use, while others are pervasive and invasive ( O’Neill, Ryan-Mosley, & Johnson, 2020 ). For example, many researchers have advocated the use of digital contact tracing and health code apps ( Oxford Analytica, 2020 ) to reduce the spread of the disease. Some people are concerned that short-term fixes such as monitoring of infected people via an app could lead to a permanent state of surveillance by the government ( Lin & Martin, 2020 ). Digital contact tracing can be effective but is controversial because it could have disastrous consequences if not implemented with proper privacy checks and encryption ( Huang, Sun, & Sui, 2020 ). For example, some experts are questioning how anonymous the data is and whether it can be easily de-anonymized to identify or infer the personal identity of infected persons ( Lee & Roberts, 2020 ). Healthy authorities may misuse or abuse the data they collected from digital tracing mobile apps for long-term and other purposes. Many people are concerned about whether these coronavirus-fighting apps are secure to use, how these apps will preserve privacy, and what policies are needed to prevent the abuse ( O’Neill et al., 2020 ). These concerns are likely to undermine public trust and affect people’s adoption of emerging technologies. There is also a need for further research to investigate security, privacy, and ethics issues related to technologies developed for fighting this pandemic.
Knowing about coronavirus exposures is important for containing the spread of COVID-19. Governments around the world are introducing technologies such as mobile apps to help health officials trace contacts of people newly infected with the coronavirus. These mobile apps work by recording whom a person comes close to—then alerting those people if a person contracts COVID-19. Out of precaution to protect people’s privacy and reduce people’s concern on increased surveillance, Australia made it illegal for non-health officials to access data collected on smartphone software to trace the spread of the coronavirus. The European Data Protection Board (EDPB) has published guidance for the use of location data and contact tracing tools in order to mitigate privacy and security concerns. Apple and Google disclosed a series of changes including stronger privacy protections and accuracy to their COVID-19 contact tracing initiative.
On the other hand, some researchers think that it is justified to temporarily relax privacy measures for such technologies in the hopes of possibly saving lives, serving the public good, and protecting public health under pandemic circumstances. Many people have been engaged in self-disclosure on social media to share personal information such as health status and preventive behaviors (e.g., wearing masks and buying sanitizing products) because sharing such information contributes to the public good ( Nabity-Grover, Cheung, & Thatcher, 2020 ). Some researchers hold that privacy concerns should not decrease the usefulness of technology to protect public health ( Cho, Ippolito, & Yu, 2020 ). They do not think such technologies were designed to make a permanent change to society ( Ferretti et al., 2020 ). The lack of a consensus on privacy protection in technologies against COVID-19 indicates a strong need for establishing best practice guidelines to reassure citizens on data collection ( Fahey & Hino, 2020 ).
Public trust and confidence are necessary to people’s adoption of various technologies including sharing their data to address the challenges caused by this pandemic ( Ferretti et al., 2020 ). Currently, the adoption of digital contact tracing apps is voluntary in western countries. It has been recognized that these issues cause more controversy in Western countries with a culture of individualism such as Europe and the U.S. than in countries with a culture of collectivism. However, at least 60 percent of people with smartphones would need to opt-in for such apps to be effective ( Scott, 2020 ). How to incentivize mass user adoption of these apps is a challenge. In the context of this coronavirus pandemic with a lot of loss of life, information systems and technology scholars can help evaluate the use of digital data and technologies including AI-related algorithms in a responsible manner, provide oversight for user-related data, develop ways to incentivize users to share relevant data as needed, help develop mechanisms to ensure that technology design and use are guided by ethical principles in order to ensure transparency, equity, and security and increase public trust and confidence ( Ienca & Vayena, 2020 ; Lee & Roberts, 2020 ). Information systems and technology scholars can also help identify best practices to implement responsible data-collection and data-processing, and achieve a balance between privacy and utility of the proposed technologies.
3.3. Connecting people with enhanced collaborative tools and IT infrastructures
The COVID-19 outbreak is rapidly changing the workplace. Millions of people are moving their workspaces to their homes through teleworking. Many industries benefit as knowledge workers learn to operate virtually, work from home, and use cloud services to process and store files. We are witnessing wider acceptance of online services by people and diverse types of industries during this pandemic. The importance of IT infrastructure in enabling teleworking, online learning, e-government, e-commerce, and other online activities has been widely recognized. The pandemic is forcing a record number of employees to work remotely for an extended duration, which results in heavy traffic on remote connectivity networks. There are vital needs for society to continue investing in IT infrastructure and accelerate digital transformation efforts to deal with the impact of COVID-19 and future public health crises ( Watson, Ives, et al., 2020 ). Companies need to enhance their investments in tools such as video conferencing and group decision-making support systems ( Xu, Du, & Chen, 2015 ) to enable personnel and distributed teams to work remotely and collaborate virtually. On the other hand, costs for IT infrastructure are exploding as employees practice teleworking and students take online classes in light of the COVID-19 outbreak. It is necessary to understand the rise in hard costs of IT infrastructure associated with meeting spiking demand. As the pandemic continues to evolve, IT infrastructures need to be enhanced for workers to perform their duties safely and healthily ( CISA, 2020 ). Some critical tasks may not be executable from home, and workarounds need to be identified. It is particularly necessary to identify the factors that drive the cost of serving the increased demand due to teleworking, such as cloud server costs, video conferencing costs, additional licenses for support products. Cloud services should be further leveraged through existing infrastructures such as Google Cloud, Azure, AWS, or Salesforce. Strategies need to be developed to keep essential functions and services up and running. CIOs need to think about retrofitting the present for the new needs or creating new systems for new situations ( Watson, Ives, et al., 2020 ). Finally, digital infrastructure readiness and resilience are also important areas to explore ( Papagiannidis, Harris, & Morton, 2020 ).
Group decision-making is often needed for complicated situations involving much uncertainty and time constraints. Information systems and technology scholars can share their experience with group decision support systems to support collective decision making regarding the evolving pandemic, help connect stakeholders at different levels to build consensus, and support governments, health authorities, organizations, and the public to make culturally appropriate and sensitive decisions regarding the infection detection, infection prediction, and infection avoidance and when to reopen the economy. Information systems and technology scholars can also help build collaborative information systems, community-based information systems, talent, and volunteer networks to leverage the expertise and time of various stakeholders. As an example, an innovative application is a wastewater COVID-19 early warning detection system. Wastewater detection of COVID-19 could act not only as a supplement to medical testing but as an early warning system for community monitoring and prevention. Continued wastewater-based monitoring could alert public health officials whether the coronavirus is still circulating in a community ( Chakradhar, 2020 ). A lot of volunteers are needed to make the wastewater COVID-19 early warning detection system successful. Information systems and technology scholars can contribute by providing expertise to help the government, authorities, and local communities to design and develop a volunteer network to engage and organize a large number of volunteers, and help build a collaborative information system to deliver a national program in this area ( Thomas & Bertsch, 2020 ). As Rai (2020) points out, swift deployment of grassroots innovation could develop rapid solutions to meet urgent needs.
3.4. Studying human behavior with technologies and digital divide
It is important to study human behavior when designing, building, and using technologies as more COVID-19 related technologies are being developed, integrated, and used by governments, organizations, and people. Lots of efforts to combat the pandemic incorporate new technological advances and approaches in integrating various systems and innovations. However, we need to acknowledge that people’s misbehavior with technologies may reduce the eff ;ectiveness of the technology-related interventions or countermeasures on containing the coronavirus break. Information systems and technology scholars can contribute by incorporating their understanding of human behavior into the technology design and development process, leading to more effective technology ( Pfleeger & Caputo, 2012 ). A large number of theories and models such as the technology acceptance model, innovation diffusion theory, the theory of reasoned action, health belief models and theory of planned behavior, social cognitive theory, and motivation theory can be used to explore the acceptance and use of COVID-19 related technologies such as telehealth technologies, study the strategic role of various technologies in dealing with the COVID-19 pandemic, and also examine unintended consequences of using technologies. For example, information systems and technology scholars can examine online users’ information sharing behavior, study how online patient communities should be engaged and incentivized to share information and support COVID-19 patients and caregivers, and how to analyze data to reveal new insights to support policy-making for health departments and medical knowledge discovery ( Bardhan et al., 2020 ).
We have also witnessed a digital divide during the pandemic. The digital divide broadly refers to the uneven access to digital content and connection because of some people who do not own or have easy access to technology. People's ability to use technologies effectively remains inequitable ( Newman, Browne‐Yung, Raghavendra, Wood, & Grace, 2017 ). As emerging technologies such as mobile apps, AI, IoT, and big data analytics are increasingly used to fight the pandemic, existing disparities, inequality, and biases are further reinforced ( Park & Humphry, 2019 ). As people spent more time working, learning, socializing, and shopping online at home, this pandemic provides a chance to assess the issues and challenges faced by the rapid digital transformation of organizations and how the digital divide impacts people (e.g., underprivileged populations, women, workers in healthcare, elderly and those at-risk) ( Venkatesh, 2020 ). Therefore, information systems and technology scholars need to help develop strategies and approaches to addressing digital inequality and disparity, especially when the governments need to flatten the curve of infection.
Information systems and technology can play a significant role in improving the visibility of digital inequality and disparity at organizations and communities ( Bardhan et al., 2020 ). Data shows Black and Hispanic populations face higher exposure to coronavirus and more significant hurdles for medical treatment and level of care ( Nemo, 2020 ). People of color communities tend to have relatively lower public health literacy and less experience in finding and evaluating healthcare information. Information systems and technology scholars can investigate to what extent the marginalized, women, elderly, and people of color are engaged, included, and impacted by these COVID-19 technology-related applications and systems, including health information seeking tools, mobile contact tracing, and tracking apps, COVID-19 self-checking chatbots, quarantine monitors, and telemedicine in a sustainable manner. It would be valuable to understand the short, medium, and long-term impacts of the digital divide during the COVID-19 pandemic response on marginalized groups, women, the elderly, people of color and people in rural settings. Information systems and technology scholars can do their part to improve technology design and processes to promote digital inclusion, assist with efficient development and sustainable implementation of the proposed technology, particularly in underserved populations. For example, Goh, Gao, and Agarwal (2016)) showed that technology-mediated online health communities could share information and alleviate rural-urban health disparities. Online health communities can also support the most vulnerable family caregivers ( Friedman, Trail, Vaughan, & Tanielian, 2018 ). Information systems and technology scholars can explore factors affecting underserved populations and communities to adopt and effectively use emerging technologies, encourage information sharing behavior during this crisis, and identify strategies to incentivize the mass adoption of relevant coronavirus-fighting technologies by underserved populations. Understanding the underserved population's unique perspectives in this coronavirus outbreak can provide guidelines for future IT systems and applications design, development, and potentially improve the adoption and use of novel IT systems.
4. Conclusion
The COVID-19 pandemic has produced significant impacts on people, businesses, and society. The pandemic also has implications for the design, development, and use of technologies ( Sein, 2020 ). Technologies can be useful for reducing the severity of the coronavirus pandemic’s impact on people, organizations, and society. However, the use of technologies to combat the pandemic raises challenges such as security, privacy, biases, ethics, and the digital divide. This paper evaluates the technology applications based on the data-people-system framework and suggests that the specific nature of the COVID-19 pandemic requires strong coordination for connected data, people, and systems to facilitate worldwide collaboration.
Future pandemics are likely to come. While information systems and technology scholars might not be able to help with the scientific aspect of developing vaccination and treatment directly, we can contribute knowledge, experiences, and time to help society better prepare for future pandemics. To mitigate future pandemics’ costs and improve data sharing during global public health crises, Chin and Chin (2020) called for establishing a global common data space for highly infectious diseases. While it is very challenging to establish a global common data space for public health data sharing due to various reasons such as technical, geopolitical, and ethical barriers, we support this call for its promising benefits and broader social good. At this stage, information systems and technology scholars can at least help advocate and build a national common data space or health information systems for public health data sharing.
Solving grand challenges facing society requires significant financial and human resources. To increase the importance and relevance of information systems and technology research, we encourage scholars to actively apply for various government and industry grants, including various COVID-19 funding opportunities, to get financial support to put some of their research ideas into practice. For example, the U.S. National Science Foundation and National Institutes of Health have grants programs that support technology-related research to develop solutions to addressing challenges caused by the coronavirus. Information systems and technology scholars should get involved by leading or joining an interdisciplinary team to write grant proposals and get funding to directly work on some of these research ideas. Furthermore, many students including undergraduate and graduate students in information systems and technology are looking for internship opportunities. Since many small businesses in industries such as tourism, food service, and retail are being hit hardest by the pandemic, information systems and technology faculty could collect student resumes, put them on a Google drive or a website, and share the resumes with interested small business owners. This would help match information systems and technology students with interested small businesses or non-profit organizations to solve the technology and other issues they may have during the pandemic. We are glad that some of the information systems and technology faculty are doing this and mentoring small business owners on deploying digital technologies to deal with the challenges of business continuity ( Papadopoulos, Baltas, & Balta, 2020 ). Some professors were involved in digital solution development projects (e.g., tackling misinformation) and helped to organize events such as online hackathons to gather people with diverse skills to work on solutions to help society fight COVID-19 ( Bacq, Geoghegan, Josefy, Stevenson, & Williams, 2020 ; Pan & Zhang, 2020 ). We hope to see more information systems and technology scholars involved in building and expanding technology volunteer networks and mobilizing community resources and services to fight COVID-19. At last, some of the developed technologies and application for this pandemic may cease to be useful after the pandemic ends, but many will likely be retained, enhanced, or repurposed for other uses ( Oxford Analytica, 2020 ), in which information systems and technology scholars can continue to play a role after the pandemic. For example, will data collected from mobile contact tracing be destroyed after this pandemic? What data management policies are needed to prevent the abuse of the user data and guide the improved design, development, and use of future mobile contact tracing and tracking tools?
CRediT authorship contribution statement
Wu He: Conceptualization, Investigation, Writing - original draft, Writing - review & editing. Zuopeng (Justin) Zhang: Writing - original draft, Writing - review & editing. Wenzhuo Li: Writing - original draft, Writing - review & editing.
- Agbo C.C., Mahmoud Q.H., Eklund J.M. Healthcare (Vol. 7, No. 2, p. 56) Multidisciplinary Digital Publishing Institute; 2019. Blockchain technology in healthcare: A systematic review. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Ågerfalk P., Conboy K., Myers M. 2020. The european journal of information systems call for papers: Special communications on information systems in the age of pandemics. https://techjournals.wixsite.com/techjournals/ejis-is-pandemics Available at. [ Google Scholar ]
- Angst C.M., Agarwal R. Adoption of electronic health records in the presence of privacy concerns: The elaboration likelihood model and individual persuasion. MIS Quarterly. 2009; 33 (2):339–370. [ Google Scholar ]
- Bacq S., Geoghegan W., Josefy M., Stevenson R., Williams T.A. The COVID-19 Virtual Idea Blitz: Marshaling social entrepreneurship to rapidly respond to urgent grand challenges. Business Horizons. 2020; 63 (6):705–723. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Bansal A., Garg C., Padappayil R.P. Optimizing the Implementation of COVID-19 “Immunity Certificates” Using Blockchain. Journal of Medical Systems. 2020; 44 (9):1–2. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Bardhan I., Chen H., Karahanna E. Connecting systems, data, and people: A multidisciplinary research roadmap for chronic disease management. Management Information Systems Quarterly. 2020; 44 (1):185–200. [ Google Scholar ]
- Ben-Assuli O., Padman R. Trajectories of repeated readmissions of chronic disease patients: Risk stratification, profiling, and prediction. MIS Quarterly. 2020; 44 (1):201–226. [ Google Scholar ]
- Brohi S.N., Jhanjhi N.Z., Brohi N.N., Brohi M.N. 2020. Key applications of state-of-the-Art technologies to mitigate and eliminate COVID-19. https://www.techrxiv.org/articles/Key_Applications_of_State-of-the-Art_Technologies_to_Mitigate_and_Eliminate_COVID-19_pdf/12115596 Available at. [ Google Scholar ]
- Budd J., Miller B.S., Manning E.M., Lampos V., Zhuang M., Edelstein M. Digital technologies in the public-health response to COVID-19. Nature Medicine. 2020:1–10. [ PubMed ] [ Google Scholar ]
- Chakradhar S. 2020. New research examines wastewater to detect community spread of COVID-19. https://www.boston.com/news/health/2020/04/10/new-research-examines-wastewater-to-detect-community-spread-of-covid-19 Available at. [ Google Scholar ]
- Chavez N., Kounang N. 2020. A man diagnosed with Wuhan coronavirus near Seattle is being treated largely by a robot. https://www.cnn.com/2020/01/23/health/us-wuhan-coronavirus-doctor-interview/index.html Available at. [ Google Scholar ]
- Chen C.M., Jyan H.W., Chien S.C., Jen H.H., Hsu C.Y., Lee P.C. Containing COVID-19 among 627,386 persons in contact with the diamond princess cruise ship passengers who disembarked in Taiwan: big data analytics. Journal of Medical Internet Research. 2020; 22 (5) [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Chen R., Sharman R., Chakravarti N., Rao H.R., Upadhyaya S.J. Emergency response information system interoperability: Development of chemical incident response data model. Journal of the Association for Information Systems. 2008; 9 (3):200–230. [ Google Scholar ]
- Chiasson M., Davidson E., Winter J. Philosophical foundations for informing the future (S) through IS research. European Journal of Information Systems. 2018; 27 (3):367–379. [ Google Scholar ]
- Chin S., Chin C. 2020. To mitigate the costs of future pandemics, establish a common data space. https://www.brookings.edu/blog/techtank/2020/11/02/to-mitigate-the-costs-of-future-pandemics-establish-a-common-data-space/ Available at. [ Google Scholar ]
- Cho H., Ippolito D., Yu Y.W. Contact tracing mobile apps for COVID-19: Privacy considerations and related trade-offs. arXiv preprint arXiv. 2020 2003.11511. [ Google Scholar ]
- Chong A.Y.L., Lim E.T., Hua X., Zheng S., Tan C.W. Business on chain: A comparative case study of five blockchain-inspired business models. Journal of the Association for Information Systems. 2019; 20 (9):9. [ Google Scholar ]
- Choong Y.Y.C., Tan H.W., Patel D.C., Choong W.T.N., Chen C.H., Low H.Y. The global rise of 3D printing during the COVID-19 pandemic. Nature Reviews Materials. 2020:1–3. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- CISA . 2020. CISA releases version 3.0 of guidance on essential critical infrastructure workers during covid-19. https://www.cisa.gov/news/2020/04/17/cisa-releases-version-30-guidance-essential-critical-infrastructure-workers-during Available at. [ Google Scholar ]
- Dwivedi Y.K., Hughes D.L., Coombs C., Constantiou I., Duan Y., Edwards J.S. Impact of COVID-19 pandemic on information management research and practice: Transforming education, work and life. International Journal of Information Management. 2020; 55 [ Google Scholar ]
- Fahey R.A., Hino A. COVID-19, digital privacy, and the social limits on data-focused public health responses. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Ferretti L., Wymant C., Kendall M., Zhao L., Nurtay A., Abeler-Dörner L. Quantifying SARS-CoV-2 transmission suggests epidemic control with digital contact tracing. Science. 2020 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Friedman E.M., Trail T.E., Vaughan C.A., Tanielian T. Online Peer Support Groups for Family Caregivers: Are They Reaching the Caregivers with the Greatest Needs? Journal of the American Medical Informatics Association. 2018; 25 (9):1130–1136. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Goh J.M., Gao G., Agarwal R. The Creation of Social Value: Can an Online Health Community Reduce Rural– Urban Health Disparities? MIS Quarterly. 2016; 40 (1):247–263. [ Google Scholar ]
- Gurgu E., Andronie M., Andronie M., Dijmarescu I. International conference on economic sciences and business administration (Vol. 5, No. 1. Spiru Haret University.; 2019. Does the convergence of the blockchain, the internet of things and artificial intelligence changing our lives, education and the known world of the internet?! Some changes and perspectives for the International economy; pp. 69–88. [ Google Scholar ]
- He S. 2020. Using the internet of things to fight virus outbreaks. https://www.technologynetworks.com/immunology/articles/using-the-internet-of-things-to-fight-virus-outbreaks-331992 Available at. [ Google Scholar ]
- Henningsson S., Yetton P.W., Wynne P.J. A review of information system integration in mergers and acquisitions. Journal of Information Technology. 2018; 33 (4):255–303. [ Google Scholar ]
- Holt K. 2020. Facebook used its AI smarts to build detailed disease prevention maps. https://www.engadget.com/2019-05-20-facebook-ai-disease-prevention-maps-demographics-movement-network-coverage.html Available at. [ Google Scholar ]
- Huang Y., Sun M., Sui Y. 2020. How digital contact tracing slowed Covid-19 in East Asia. https://hbr.org/2020/04/how-digital-contact-tracing-slowed-covid-19-in-east-asia Available at. [ Google Scholar ]
- Ienca M., Vayena E. On the responsible use of digital data to tackle the COVID-19 pandemic. Nature Medicine. 2020; 26 (4):463–464. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Johnstone S. University of Hong Kong Faculty of Law Research Paper, (2020/005); 2020. A viral warning for change. COVID-19 versus the Red Cross: Better Solutions Via Blockchain and Artificial Intelligence (February 3, 2020) [ Google Scholar ]
- Khurshid A. Applying blockchain technology to address the crisis of trust during the COVID-19 pandemic. JMIR Medical Informatics. 2020; 8 (9) [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Kumar K., Kumar N., Shah R. Role of IoT to avoid spreading of COVID-19. International Journal of Intelligent Networks. 2020; 1 :32–35. [ Google Scholar ]
- Lee N.T., Roberts J. Managing health privacy and bias in COVID-19 public surveillance. Brookings. 2020 https://www.brookings.edu/blog/techtank/2020/04/21/managing-health-privacy-and-bias-in-covid-19-public-surveillance/?utm_campaign=Center%20for%20Technology%20Innovation&utm_source=hs_email&utm_medium=email&utm_content=87437298 Available at. [ Google Scholar ]
- Liang W., Yao J., Chen A., Lv Q., Zanin M., Liu J. Early triage of critically ill COVID-19 patients using deep learning. Nature Communications. 2020; 11 (1):1–7. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Lin L., Martin T. 2020. How coronavirus is eroding privacy. https://www.wsj.com/articles/coronavirus-paves-way-for-new-age-of-digital-surveillance-11586963028 Available at. [ Google Scholar ]
- Lin Q., Zhao S., Gao D., Lou Y., Yang S., Musa S.S. A conceptual model for the outbreak of Coronavirus disease 2019 (COVID-19) in Wuhan, China with individual reaction and governmental action. International Journal of Infectious Diseases. 2020; 93 :211–216. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Liu J. 2020. Deployment of health IT in China’s fight against the COVID-19 pandemic. https://www.itnonline.com/article/deployment-health-it-china%E2%80%99s-fight-against-covid-19-pandemic Available at: [ Google Scholar ]
- Loh T., Fishbane L. 2020. COVID-19 makes the benefits of telework obvious. https://www.brookings.edu/blog/the-avenue/2020/03/17/covid-19-makes-the-benefits-of-telework-obvious/ Available at. [ Google Scholar ]
- Markforged . 2020. Fiberflex: 3D printed nasal swabs for Covid-19 testing. https://markforged.com/covid-19/#swabs Available at. [ Google Scholar ]
- Marr B. 2020. Coronavirus: How artificial intelligence, data science and technology is used to fight the pandemic. https://www.forbes.com/sites/bernardmarr/2020/03/13/coronavirus-how-artificial-intelligence-data-science-and-technology-is-used-to-fight-the-pandemic/#34645abe5f5f Available at. [ Google Scholar ]
- Marr N. 2020. How the COVID-19 pandemic is fast-tracking digital transformation in companies. https://www.forbes.com/sites/bernardmarr/2020/03/17/how-the-covid-19-pandemic-is-fast-tracking-digital-transformation-in-companies/#60fc18caa8ee Available at. [ Google Scholar ]
- Mingis K. 2020. Tech pitches in to fight COVID-19 pandemic. https://www.computerworld.com/article/3534478/tech-pitches-in-to-fight-covid-19-pandemic.html Available at. [ Google Scholar ]
- Nabity-Grover T., Cheung C.M., Thatcher J.B. Inside out and outside in: How the COVID-19 pandemic affects self-disclosure on social media. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Nasajpour M., Pouriyeh S., Parizi R.M., Dorodchi M., Valero M., Arabnia H.R. Internet of Things for current COVID-19 and future pandemics: An exploratory study. Journal of Healthcare Informatics Research. 2020:1–40. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Nemo L. 2020. Why people of color are disproportionately hit by COVID-19. https://www.discovermagazine.com/health/why-people-of-color-are-disproportionately-hit-by-covid-19 Available at. [ Google Scholar ]
- Newman L., Browne‐Yung K., Raghavendra P., Wood D., Grace E. Applying a critical approach to investigate barriers to digital inclusion and online social networking among young people with disabilities. Information Systems Journal. 2017; 27 (5):559–588. [ Google Scholar ]
- News Staff . 2020. Blockchain emerges as useful tool in fight against coronavirus. https://www.govtech.com/products/Blockchain-Emerges-as-Useful-Tool-in-Fight-Against-Coronavirus.html Available at. [ Google Scholar ]
- O’Leary D.E. Evolving information systems and technology research issues for COVID-19 and other pandemics. Journal of Organizational Computing and Electronic Commerce. 2020 doi: 10.1080/10919392.2020.1755790. Available at. [ CrossRef ] [ Google Scholar ]
- O’Neill P.H., Ryan-Mosley T., Johnson B. 2020. A flood of coronavirus apps are tracking us. Now it’s time to keep track of them. https://www.technologyreview.com/2020/05/07/1000961/launching-mittr-covid-tracing-tracker/ Available at. [ Google Scholar ]
- Onik M.M.H., Aich S., Yang J., Kim C.S., Kim H.C. Big data analytics for intelligent healthcare management. Academic Press; 2019. Blockchain in healthcare: Challenges and solutions; pp. 197–226. [ Google Scholar ]
- Oxford Analytica . Emerald expert briefings. 2020. COVID-19 tech will expand surveillance state in China. Available at. [ CrossRef ] [ Google Scholar ]
- Ozturk T., Talo M., Yildirim E.A., Baloglu U.B., Yildirim O., Acharya U.R. Automated detection of COVID-19 cases using deep neural networks with X-ray images. Computers in Biology and Medicine. 2020 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Pan S.L., Cui M., Qian J. Information resource orchestration during the COVID-19 pandemic: A study of community lockdowns in China. International Journal of Information Management. 2020; 54 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Pan S.L., Pan G., Leidner D.E. Crisis response information networks. Journal of the Association for Information Systems. 2012; 13 (1):518–555. [ Google Scholar ]
- Pan S.L., Zhang S. From fighting COVID-19 pandemic to tackling sustainable development goals: An opportunity for responsible information systems research. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Papadopoulos T., Baltas K.N., Balta M.E. The use of digital technologies by small and medium enterprises during COVID-19: Implications for theory and practice. International Journal of Information Management. 2020; 55 doi: 10.1016/j.ijinfomgt.2020.102192. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Papagiannidis S., Harris J., Morton D. WHO led the digital transformation of your company? A reflection of IT related challenges during the pandemic. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Park S., Humphry J. Exclusion by design: Intersections of social, digital and data exclusion. Information, Communication and Society. 2019; 22 (7):934–953. [ Google Scholar ]
- Pfleeger S.L., Caputo D.D. Leveraging behavioral science to mitigate cyber security risk. Computers & Security. 2012; 31 (4):597–611. [ Google Scholar ]
- Pham Q., Nguyen D.C., Huynh-The T., Hwang W., Pathirana P.N. Artificial Intelligence (AI) and Big Data for Coronavirus (COVID-19) Pandemic: A Survey on the State-of-the-Arts. Preprints. 2020; 2020 doi: 10.20944/preprints202004.0383.v1). [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Punn N.S., Sonbhadra S.K., Agarwal S. COVID-19 epidemic analysis using machine learning and deep learning algorithms. medRxiv. 2020 [ Google Scholar ]
- Rahman M.S., Peeri N.C., Shrestha N., Zaki R., Haque U., Ab Hamid S.H. Defending against the Novel Coronavirus (COVID-19) Outbreak: How Can the Internet of Things (IoT) help to save the World? Health Policy and Technology. 2020; 9 (2):136–138. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Rai A. The COVID-19 pandemic: Building resilience with IS research. MIS Quarterly. 2020; 44 (2):02. [ Google Scholar ]
- Ravichandran T., Rai A. Quality management in systems development: An organizational system perspective. MIS Quarterly. 2000:381–415. [ Google Scholar ]
- Rehfuess E.A., Stratil J.M., Scheel I.B., Portela A., Norris S.L., Baltussen R. The WHO-INTEGRATE evidence to decision framework version 1.0: Integrating WHO norms and values and a complexity perspective. BMJ Global Health. 2019; 4 (Suppl 1) [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Richter A. Locked-down digital work. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Scott D. 2020. What good digital contact tracing might look like. https://www.vox.com/2020/4/22/21231443/coronavirus-contact-tracing-app-states Available at. [ Google Scholar ]
- Sein M.K. The serendipitous impact of COVID-19 pandemic: A rare opportunity for research and practice. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Sinclair S. 2020. Researchers in Spain are racing to develop a smartphone app that leverages blockchain technology and artificial intelligence to help stem the coronavirus pandemic. https://www.coindesk.com/spanish-researchers-working-to-curb-coronavirus-spread-with-blockchain-app Available at. [ Google Scholar ]
- Singh S.K., Rathore S., Park J.H. Blockiotintelligence: A blockchain-enabled intelligent IoT architecture with artificial intelligence. Future Generation Computer Systems. 2020; 110 :721–743. [ Google Scholar ]
- Sipior J.C. Considerations for development and use of AI in response to COVID-19. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Thomas K., Bertsch P. 2020. Australian researchers trace sewage for early warning COVID-19 spread. https://www.uq.edu.au/news/article/2020/04/australian-researchers-trace-sewage-early-warning-covid-19-spread Available at. [ Google Scholar ]
- Thompson S., Whitaker J., Kohli R., Jones C. Chronic disease management: How IT and analytics create healthcare value through the temporal displacement of care. MIS Quarterly. 2019; 44 (1):227–256. [ Google Scholar ]
- Ting D.S.W., Carin L., Dzau V., Wong T.Y. Digital technology and COVID-19. Nature Medicine. 2020; 26 (4):459–461. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Valecha R., Rao R., Upadhyaya S., Sharman R. An activity theory approach to modeling dispatch-mediated emergency response. Journal of the Association for Information Systems. 2019; 20 (1):33–57. [ Google Scholar ]
- Venkatesh V. Impacts of COVID-19: A research agenda to support people in their fight. International Journal of Information Management. 2020; 55 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Wang J. Fast identification of possible drug treatment of coronavirus disease-19 (COVID-19) through computational drug repurposing study. Journal of Chemical Information and Modeling. 2020; 60 (6):3277–3286. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Wang C.J., Ng C.Y., Brook R.H. Response to COVID-19 in Taiwan: Big data analytics, new technology, and proactive testing. Jama. 2020 [ PubMed ] [ Google Scholar ]
- Wang S., Zha Y., Li W., Wu Q., Li X., Niu M. A fully automatic deep learning system for COVID-19 diagnostic and prognostic analysis. The European Respiratory Journal. 2020 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Watson R., Ives B., Piccoli G. Guest editorial: Practice-oriented research contributions in the Covid-19 forged new normal. MIS Quarterly Executive. 2020; 19 (2):2. [ Google Scholar ]
- Woo T. Cloud players and research groups join the fight against COVID-19 with high-performance computing. Forrest. 2020 https://go.forrester.com/blogs/cloud-players-and-research-groups-join-the-fight-against-covid-19-with-high-performance-computing/ Available at. [ Google Scholar ]
- World Health Organization . 2020. Digital technology for COVID-19 response. https://www.who.int/news-room/detail/03-04-2020-digital-technology-for-covid-19-response Available at. [ Google Scholar ]
- Xu L. Enterprise systems: State-of-the-art and future trends. IEEE Transactions on Industrial Informatics. 2011; 7 (4):630–640. [ Google Scholar ]
- Xu X.H., Du Z.J., Chen X.H. Consensus model for multi-criteria large-group emergency decision making considering non-cooperative behaviors and minority opinions. Decision Support Systems. 2015; 79 :150–160. [ Google Scholar ]
- Yan L., Tan Y. Feeling blue? Go online: An empirical study of social support among patients. Information Systems Research. 2014; 25 (4):690–709. [ Google Scholar ]
- Yang G.Z., Nelson B.J., Murphy R.R., Choset H., Christensen H., Collins S.H. 2020. Combating COVID-19—The role of robotics in managing public health and infectious diseases. [ PubMed ] [ Google Scholar ]
- Young J. 2020. Scenes from college classes forced online by COVID-19. https://www.edsurge.com/news/2020-03-26-scenes-from-college-classes-forced-online-by-COVID-19 Available at. [ Google Scholar ]
- Ziebland S., Chapple A., Dumelow C., Evans J., Prinjha S., Rozmovits L. How the internet affects patients’ experience of Cancer: A qualitative study. BMJ. 2004; 328 :7439. [ PMC free article ] [ PubMed ] [ Google Scholar ]
Thesis Helpers
Find the best tips and advice to improve your writing. Or, have a top expert write your paper.
130 Information Technology Research Topics And Quick Writing Prompts

The field of information technology is one of the most recent developments of the 21st century. Scholars argue that we are living in a technological age. Despite this buzz, however, many students still find it challenging to compose an information technology research topic.
Nonetheless, we are here to show you the way and lead you accordingly. Let us explore professional topics in information technology together then.
Quality Information Technology Topics For Research Paper
- The effects of Artificial Intelligence on complex and tedious tasks
- Discuss the development of computational & synthetic biology in research
- What are the limitations to the study of computer architecture in colleges?
- Discuss the evolution of animation, computer graphics, and game science
- Critically analyze how computing is contributing to the development
- What are the emerging fields of study in computer data science?
- How to manage data in the age of the 5G technology
- The impact of human-computer interaction on innovations
- How is machine learning exposing students to more recent opportunities in life?
- Evaluate molecular information systems and their role in biotechnology
- How information technology has contributed to natural language processing
- What are the latest developments in programming languages and software engineering
- Analyze emerging opportunities in the field of Robotics
College Research Paper Topics in Information Technology
- The rising security and privacy concerns with technological advancements
- What are the considerations when setting up systems and networking?
- Discuss the theory of computation and its contribution to information technology
- Why is ubiquitous computing attracting fewer students?
- The role of wireless and sensor systems in making the world a safe place
- Reasons, why cloud computing has helped save on space and efficiency
- Why are most computer students comprised of the male?
- Discuss the essence of amorphous computing in the 21st century
- How has biomedical mining impacted the health sector?
- Can cyborgs relate well with the man?
- How neural networking is making brain surgery a swift process
- The role of swarm intelligence in collaboration and brainstorming
- How are companies maximizing the use of Big Data?
List of Topics For Research Paper in Information Technology
- Discuss how the Internet of Things is transforming how people conduct their activities
- Challenges to software-defined networking
- How are marketers and promoters taking up software as a service?
- The role of augmented reality and virtual reality in healthcare systems
- How intelligent apps are making life easier for man
- The role of information technology in detecting fake news and malicious viral content
- Long term effects of a technologically oriented world
- Technological advancements that made it possible for the SpaceX shuttle to land on the International Space Station
- How technology is making learning more practical and student-centered
- What role has technology played in the spread of world pandemics?
- How are governments able to shut down the Internet for their countries during particular events?
- Does social media make the world a global village or a divided universe?
- Discuss the implications of technological globalization
Unique Information Technology Research Topics
- Discuss the areas of life which have been least exploited using technology
- What are the considerations for setting up an educational curriculum on computer technology?
- Compare and contrast between different computer processing powers
- Why is Random Access Memory so crucial to the functioning of a computer?
- Should computer as a subject be mandatory for all students in college?
- How information technology has helped keep the world together during the quarantine period
- Discuss why most hackers manage to break firewalls of banks
- Are automated teller machine cards a safe way of keeping your bank details?
- Why should every institution incorporate automated systems in its functions?
- Who is more intelligent than the other? Man or Computer systems?
- How is NASA implementing the use of Information technology to explore space?
- The impact of automated message replies on smartphones.
- Do mobile phones contain radiations that cause cancer?
IT Research Topics For High School Students
- How does natural language processing compare with machine learning?
- What is the role of virtual reality in the entertainment industry?
- Discuss the application of computer vision technology in autonomous cars
- How have CCTVs assisted in keeping the world safe?
- Effects of phishing and spying on relationships
- Why cyber espionage is on the rise in the face of the 5G technology
- Compare and contrast between content-based recommendation vs. collaborative filtering
- Evaluate the interconnection between the Internet of things and artificial intelligence
- Analyze the amount of data generated from the Internet of things in devices
- Ethical and legal implications of various technological practices
- How technology has contributed to the formation of Genetically Modified Organisms
- Describe in detail the vaccine development process
- Why nanotechnology may be the only hope left in treating HIV
Hot Topics in IT
- How companies can incorporate information technologies in their policy management systems
- The role of IT in enhancing service delivery in customer care centers
- How IT has made advertising more appealing and authentic to the consumer
- Discuss the innovation of the Next Generation education systems
- Why are there fewer Information Technology colleges and universities in developing countries?
- Discuss WIFI connectivity in developed countries
- What are the considerations when purchasing a Bandwidth Monitor?
- How to create an effective Clinic Management System for intensive care
- Factors that necessitate the development of an Enterprise Level System Information Management
- Is it possible to develop fully functional Intelligent Car Transportation Systems?
- Why the world should adopt E-Waste Management systems ASAP
- Discuss the impact of weather and climate on internet strength and connectivity
- The role of advanced information technologies preserving classified documents
Interesting Information Technology Topics
- Human resource information management systems in large organizations
- Evaluate the effectiveness of online enterprise resource planning
- A critical analysis of object tracking using radial function networks
- How has Bluetooth mobile phone technology developed over time?
- Ethical challenges arising from new media information technologies
- How the computer has developed over the last decade
- The role of social media in enhancing communication strategies
- Why new media technologies have made physical newspapers obsolete
- The impact of the Internet of news sourcing, production, distribution, and sharing
- Discuss the structures of various communication structures
- How social media is making ads easily accessible
- The impact of social networking sites on personal contact
- Discuss the latest content marketing ideas in the wake of information technology
Topics Related To Information Technology
- The impact of media exposure to adolescents and teenagers
- How mass media is slowly but surely taking over the place of personal socialization
- How to use the Internet and interactive media as advertising tools
- Discuss the trends in music marketing in a digital world
- The use of hype in new media technologies
- The impact of using YouTube and video blogs in communication messages
- Discuss the challenges that are arising as a result of new media technologies
- How to build trustful relationships in virtual communication channels
- Why it is impossible to maintain privacy in social media
- Reasons why cyberbullying continues to persist in various communication technologies
- The change in interpersonal communication with the invention of information technology
- Is the future of information technologies right?
- Discuss how sensationalism is persisting in the wake of new media technologies
Research Proposal Topics in Information Technology
- Is it possible to live in a world without social media?
- The impact of mass media on morality and decency in the 21st century
- Advantages and disadvantages of renewable energy sources
- How effective is hydrogen power over others?
- An overview of renewable energy technologies
- The impact of robots in improving food safety
- How are drones useful in keeping large acres of land secure?
- The impact of 3D printing on the practice of medicine
- The effectiveness of having robots in infectious disease units
- The impact of hydroponic farming
- How to improve disease control using technology
- Eliminating poisonous substances in food using technology
- The effectiveness of robotic surgeries
Hot Topics in Computer Science
- Distinguish between virtual reality and human perception
- How are the inventions in the field of computer science transforming the world
- Evaluate the effectiveness of high-dimensional data modeling
- Limitations to the field of computer science
- Are colleges and universities producing competent computer scientists?
- How ethical hacking has turned out to be worse
- The essence of having specialized banking systems
- What is the most effective security measure: A serial code or fingerprint?
- The development of programming languages
- The effect of computational thinking on science
- Is it possible to eliminate stalking?
- Ways of improving patent rights for technological innovations
- An overview of the different types of software security
Did you find an IT topic for your assignment? If not, our expert thesis writers are here for you. Order a research paper from us today and get to enjoy professional services.

Make PhD experience your own
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
The green IT revolution: A blueprint for CIOs to combat climate change
Companies and governments looking to combat climate change are turning to tech for help. AI, new technologies, and some promising tech-driven business models have raised hopes for dramatic progress.
About the authors
This article is a collaborative effort by Gerrit Becker, Luca Bennici, Anamika Bhargava, Andrea Del Miglio , Jeffrey Lewis , and Pankaj Sachdeva, representing views from McKinsey Technology.
While many organizations’ climate goals are lofty, enterprise technology leaders—CIOs, chief digital innovation officers (CDIOs), and chief technology officers (CTOs), among others—have not always succeeded at turning climate ambitions into reality. One of the biggest reasons is that hard facts and clear paths of action are scarce. Misconceptions and misinformation have clouded the picture of what CIOs and tech leaders should do.
We have done extensive analysis of where technology can have the biggest impact on reducing emissions. To start, we divided technology’s role into two primary types of activities:
- offense—the use of technology and analytics to cut emissions by reducing (improving operational efficiency), replacing (shifting emission-generating activities to cleaner alternatives), and reusing (recycling material)
- defense—the actions IT can take to reduce emissions from the enterprise’s technology estate
Scope of the McKinsey analysis
McKinsey’s emissions analysis for this report focuses on enterprise technology emissions, which are the business IT emissions from the hardware, software, IT services, enterprise communications equipment, mobile devices, fixed and mobile network services, and internal technology teams that a company uses for its own operations and that a CIO has control over. These include the emissions related to the full life cycles of the products and services that an enterprise IT function uses, including their development, delivery, usage, and end of life (exhibit). Our internal services emissions' analysis assumes around 40 percent of IT workers are working from home.
The analysis does not include the emissions from the technology products and services that a company is selling (such as data center capacity sold by hyperscalers), operational technology devices (such as sensors and point-of-sale systems), and cryptocurrency mining.
The defense activities are where the CIO, as the head of IT, can act independently and quickly. This article focuses on defense, specifically the IT elements over which a CIO has direct control. We examined emissions from use of electricity for owned enterprise IT operations, such as the running of on-premises data centers and devices (classified as scope 2 by the Greenhouse Gas Protocol 1 Greenhouse Gas Protocol: Technical Guidance for Calculating Scope 3 Emissions: Supplement to the Corporate Value Chain (Scope 3) Accounting & Reporting Standard , World Resources Institute & World Business Council for Sustainable Development, 2013. Scope 1 emissions are direct emissions from the activities of an organization or under their control, including fuel combustion on site such as gas boilers, fleet vehicles, and air-conditioning leaks; scope 2 emissions are from electricity purchased and used by the organization; and scope 3 emissions are all indirect emissions not included in scope 2 that occur in the value chain of the reporting company, including both upstream and downstream emissions. ), and indirect emissions from technology devices that the CIO buys and disposes of (scope 3). 2 These calculations do not include emissions from technology-driven services sold, such as cloud capacity. (See sidebar, “Scope of the McKinsey analysis.”)
What the facts say
Our analysis has uncovered several facts that contravene some commonly held views about enterprise technology emissions. These facts involve the significant amount of tech-related emissions, the share of emissions from end-user devices, the variety of mitigation options available, and the favorable impact of shifting to cloud computing.
Enterprise technology generates significant emissions
Enterprise technology is responsible for emitting about 350 to 400 megatons of carbon dioxide equivalent gases (CO 2 e), accounting for about 1 percent of total global greenhouse gas (GHG) emissions. At first blush, this might not seem like a lot, but it equals about half of the emissions from aviation or shipping and is the equivalent of the total carbon emitted by the United Kingdom.
The industry sector that contributes the largest share of technology-related scope 2 and scope 3 GHG emissions is communications, media, and services (Exhibit 1). Enterprise technology’s contribution to total emissions is especially high for insurance (45 percent of total scope 2 emissions) and for banking and investment services (36 percent).
This amount of carbon dioxide and equivalent gases is a significant prize for companies under increasing pressure to cut emissions. Progress on climate change requires action on many fronts, and enterprise technology offers an important option that CIOs and companies can act on quickly.

You’re invited
To a McKinsey Technology webinar on the critical role of technology in building a sustainable enterprise on October 25, 9:30–10:30am ET.
The biggest carbon culprit is end-user devices, not on-premises data centers
End-user devices—laptops, tablets, smartphones, and printers—generate 1.5 to 2.0 times more carbon globally than data centers (Exhibit 2). 3 On-premises and co-located data centers used by enterprises, not including data center capacity sold by hyperscalers. One reason is that companies have significantly more end-user devices than servers in on-premises data centers. In addition, the devices typically are replaced much more often: smartphones have an average refresh cycle of two years, laptops four years, and printers five years. On average, servers are replaced every five years, though 19 percent of organizations wait longer. 4 Rhona Ascierto and Andy Lawrence, Uptime Institute global data center survey 2020 , Uptime Institute, July 2020.
More worrisome, emissions from end-user devices are on track to increase at a CAGR of 12.8 percent per year. 5 End-user computing market: Growth, trends, COVID-19 impact, and forecasts (2022–2027) , Mordor Intelligence, January 2022. Efforts to address this could target the major causes of emissions from these devices. About three-fourths of the emissions comes from manufacturing, upstream transportation, and disposal. A significant source of these emissions is the semiconductors that power the devices.
Plenty of low-cost/high-impact options exist, starting with improved sourcing
We have found that when it comes to going green, many CIOs think in terms of investments needed to replace items or upgrade facilities. Our analysis, however, finds that CIOs can capture significant carbon benefits without making a significant investment—and in some cases can even save money (Exhibit 3).
Overall, for example, 50 to 60 percent of emissions related to end-user devices can be addressed through sourcing changes, primarily by procuring fewer devices per person and extending the life cycle of each device through recycling. These options will not require any investment and will lower costs, though companies may want to evaluate the impact on employee experience.
In addition, companies can more aggressively recycle their devices; 89 percent of organizations recycle less than 10 percent of their hardware overall. 6 Sustainable IT: Why it’s time for a green revolution for your organization’s IT , Capgemini Research Institute, 2021. CIOs can put pressure on suppliers to use greener devices, especially as companies in the semiconductor sector are already increasing their commitments to emission reduction. Further low-cost, high-impact actions include optimizing business travel and data center computing needs, as well as increasing the use of cloud to manage workloads.
Moving to cloud has more impact than optimizing data centers
Optimizing an on-premises data center’s power usage effectiveness (PUE) 7 PUE describes how efficiently a computer data center uses energy, expressed as the ratio of total facility energy to IT equipment energy. is expensive and results in limited carbon abatement. If a company were to double what it spends on infrastructure and cloud to reduce PUE, it would cut carbon emissions by only 15 to 20 percent. Structural improvements in data centers and optimized layout can help, but the impact is limited, and many companies have already implemented them. More aggressive measures, such as moving data centers to cooler locations or investing in new cooling tech, are prohibitively expensive.
A more effective approach is to migrate workloads to the cloud. Hyperscalers (also known as cloud service providers) and co-locators are investing significantly to become greener through measures such as buying green energy themselves and investing in ultra-efficient data centers with a PUE equal to or less than 1.10, compared with the average PUE of 1.57 for an on-premises data center. 8 “Uptime Institute 11th annual Global Data Center Survey shows sustainability, outage, and efficiency challenges amid capacity growth,” Uptime Institute, September 14, 2021. (We estimate that companies could achieve just a 1.3 PUE score for their data center if they invested nearly 250 percent more, on average, over what they currently spend for their data centers and cloud presence.)
With thoughtful migration to and optimized usage of the cloud, companies could reduce the carbon emissions from their data centers by more than 55 percent—about 40 megatons of CO 2 e worldwide, the equivalent of the total carbon emissions from Switzerland.
Three steps to take now
With companies and governments under intensifying pressure to cut carbon emissions and with technology playing a key role in delivering on those goals, CIOs will find themselves on the front lines. The challenge will be to reduce IT’s carbon footprint while delivering high-quality, low-cost technology services to customers and employees.
On average, completion of the defensive steps might take three to four years. However, CIOs who act decisively and precisely can achieve 15 to 20 percent of carbon reduction potential in the first year with minimal investment.
CIOs can choose from among a wide array responses, particularly in conjunction with the CEO and the board. However, three measures they can take right now will prepare the organization for longer-term efforts. These measures involve sourcing strategies, key metrics, and a performance management system.

The net-zero transition: What it would cost, what it could bring
Move now on sourcing strategies.
Far and away the fastest and most effective defensive measure for reducing IT carbon emissions is to revise policies for technology sourcing. Optimizing the number of devices in line with standards followed by companies in the top quartile 9 Top quartile in terms of the ratio of devices to people is derived from the number of devices per person. Our analysis uses McKinsey Digital’s Ignite solutions and 2020 data. would reduce about 30 percent of end-user-device emissions, the amount of carbon emitted by Hong Kong. For example, top-quartile companies have one printer for every 16 people in the workplace; the overall average is one printer per eight people.
This sourcing shift does not necessarily lead to a degradation in user experience, because the rollout of 5G and increasingly advanced processing and compute power allow the main processing function to happen at the server. Therefore, devices can be less powerful and consume much less energy. Essentially, this is a software-as-a-service (SaaS) model where high-end and user-friendly experiences happen on the server, not the device. The effectiveness of this approach will depend on having stable networks, less resource-intensive coding at the device level, edge computing capabilities, and shifts of offerings to more efficient platforms (for example, cloud).
As part of this effort, the CIO and the business’s head of procurement will need to collaborate on reviewing and adjusting device refresh timelines and device-to-person ratios, as well as adjusting the basis for purchasing decisions. Procurement generally relies on cost/benefit calculations, and rightly so. That approach will need to expand to account for carbon dioxide emissions. The spirit of collaboration should extend to suppliers as well, with the parties working together to formulate plans that provide the greatest benefits for all.
A more thoughtful sourcing strategy extends beyond end-user devices. CIOs, for example, should look for green sources of the electricity IT uses. When these sources are unavailable, CIOs can direct procurement to power purchase agreements to offset carbon use. CIOs can also set green standards for their vendors and suppliers, requiring GHG emissions disclosures and incorporating them into their criteria for purchase decisions.
Establish a green ROI metric for technology costs
Any real progress on green technology can happen only when companies measure their “green returns.” But today, most green metrics omit cost and savings, which ultimately makes them impractical. A better metric focuses on cost per ton of carbon saved (accounting for costs saved as well). Sophisticated models calculate emissions throughout the full life cycle, including production, transportation, and disposal.
CIOs can further assess suppliers, manufacturers, and service providers based on how advanced they are in recycling and refurbishing electronics; designing circular components; extending product life cycles with better design, higher-quality manufacturing, and more robust materials; offering repair services; and reselling to consumers.
Decisions about IT spending need to consider a range of factors, including technical debt abatement and business strategy. Along with these factors, companies should institutionalize a green ROI metric that is transparent to everybody in the business as an element in IT decision making, including in requests for proposals (RFPs). Doing so will enable companies to better understand the true impact their technology is having on carbon emissions.
Put in place green measurement systems
Establishing a green ROI metric is only a start. CIOs need to establish a baseline of performance, measure progress against the baseline, and track impact in near real time, much as companies track real-time computer and network usage for applications in the cloud. This kind of measuring system ensures that CIOs know what’s working and what isn’t, so they can adjust quickly.
In practice, implementing green measurement can be challenging. Some companies have spent a year measuring their carbon footprint, ending up with an outdated analysis. This tends to happen when companies are determined to measure every bit of carbon emitted, a praiseworthy but time-consuming effort. CIOs can make substantial progress by instead prioritizing measurement where the impact is highest, such as tracking the number of end-user devices purchased and in use, the current duration of use for each device, and the ratio of devices per user. Another way CIOs can make quick progress is to embed emissions- and power-monitoring capabilities into large technology assets and work with external providers, such as electricity companies, to track usage in real time.
Effectively combating climate change won’t happen through one or two big wins; those don’t exist yet. To have real impact, companies and governments will need to act in many areas. Technology has a huge role to play in many of these areas, but CIOs and tech leaders need to act quickly and decisively.
This article is the first in a series about how CIOs can reduce emissions. The next article will explore how CIOs can drive the business’s sustainability agenda by playing offense and implementing reduce, replace, and reuse levers to decarbonize.
Gerrit Becker is an associate partner in McKinsey’s Frankfurt office, Luca Bennici is an associate partner in the Dubai office, Anamika Bhargava is a consultant in the Toronto office, Andrea Del Miglio is a senior partner in the Milan office, Jeffrey Lewis is a senior partner in the New Jersey office, and Pankaj Sachdeva is a partner in the Philadelphia office.
The authors wish to thank Bernardo Betley, Arjita Bhan, Raghuvar Choppakatla, Sebastian Hoffmann, Abdelrahman Mahfouz, Tom Pütz, Jürgen Sailer, Tim Vroman, Alice Yu, and Gisella Zapata for their contributions to this article.
Explore a career with us
Related articles.

It’s not easy buying green: How to win at sustainable sourcing
Sustainability in semiconductor operations: Toward net-zero production

Delivering the climate technologies needed for net zero
Information Technology
Search form.
- Technology Help Desk
- How-To Articles
- IT Services Portal
- Ticket Status
- Feature Articles
- Alerts & Announcements
- Customer Success Stories
- In the News
- IT Events Calendar
- Report a Security Concern
- Accounts & Access
- Data Classification & Compliance
- Security Awareness Training
- Vendor Risk Assessment
- Services by Category
- Software for Faculty
- Software for Staff
- Software for Students
- Software for Research
- IT Training & Development
- On-Demand Learning
- Instructor-Led Training
- Training Content Development
- Tech Ambassadors
- About Pitt IT
- Office of the CIO
- Leadership Team
- IT Vision and Strategy
- Community Engagement
- IT 10-Year Horizon
You are here
6 essential it tools for researchers.

Advances in research computing have propelled Pitt to the forefront of research, with the University ranking third nationally in NIH funding in FY23. Researchers utilize robust technology to collect, store, and analyze data; document and manage lab processes; and work with collaborators. Pitt IT supports the work of researchers, so they can focus on doing what they do best: making the University of Pittsburgh one of the top research institutions in the world! Here are the top six tools researchers at Pitt can start using today.
1. Collect Participant Data (Qualtrics)
For research involving self-reporting or participant feedback, you need a robust survey tool that is easy to use. The Online Survey System (Qualtrics) enables you to create and distribute surveys for everything from collecting demographic info or tracking daily activity, to monitoring symptoms or exploring participant beliefs. The system requires minimal experience or training, is extremely user-friendly, and is available at no cost to all Pitt researchers, faculty, staff, and students. Qualtrics securely gathers and stores survey data, allows for complex decision trees based on previous responses, provides easy access to raw data, compiles and analyzes results, and creates high-quality charts and graphs to visually present the data.
2. Document and Manage Lab Activities (LabArchives)
Pitt offers Electronic Research Notebooks (LabArchives) at no cost to help you keep track of all your notes, data, and findings in one place, from nearly any type of device. ELNs can be used to organize and manage all aspects of lab activity, from study protocols and testing progress to documenting results. Notebooks can include any kind of input, including text, tables, images, and sketches. You can also share and collaborate on notebooks with research partners and lab staff.
In addition, LabArchives Scheduler and Inventory modules help manage and organize all aspects of lab activity. Scheduler provides a calendar and scheduling service to simplify the management and booking of equipment and spaces, such as microscopes, flow cytometers, recording space, microphones, and other items. Inventory enables you to streamline inventory management via a simple, customizable solution that allows you to include inventory types and storage locations, add and manage lab inventory items, and generate shopping lists.
3. Store Large Data Sets (Enterprise Cloud Storage)
Enterprise Cloud Computing (ECC) gives researchers access to virtual computing resources in a safe and reliable way. The most widely used ECC platform for large-scale storage and robust compute power is Microsoft Azure . Azure provides resources to tailor specific solutions to your data storage needs, without the extra time or cost of purchasing, setting up and maintaining a server. Azure lets you archive data inexpensively, provide shared file storage, and store and compute data in an environment with HIPAA-compliant protections for data privacy.
4. Transfer Large Data Sets (Globus)
Research often generates very large data sets, which presents challenges when transferring and sharing the data with collaborators. Pitt’s Enterprise Data Transfer Service (Globus) subscription lets users transfer and share files with ease, no matter the location of you or your collaborators. You can move and share data between on-premises and cloud storage, with external institutions, and between endpoints/devices. Users can also develop applications and access gateways by leveraging Globus’s advanced identity management, single sign-on, search, authorization, and automation capabilities. A free Globus subscription is available to all Pitt researchers, faculty, and students.
5. Visualize Your Results (BioRender)
BioRender is used to create and edit scientific diagrams and illustrations for use in posters, papers, presentations, and publications. The web-based app has over 40,000 icons and a large stock image collection that spans subjects such as neuroscience, immunology, microbiology, and more. The app makes it easy to create sophisticated figures by using an intuitive interface with drag and drop tools—no artistic skills needed. BioRender also lets you work collaboratively on figures. Faculty and staff receive BioRender at a significantly discounted price (just $100/year for each user). Students have free access to help them learn how to visually present scientific concepts and data in their projects and papers.
6. Access Supercomputing Resources (ARCS)
The Center for Research Computing (CRC) and the Pittsburgh Supercomputing Center (PSC) work closely with Pitt IT to provide Pitt researchers with the computing power needed to engage in large-scale processing. They are used by researchers in STEM fields, who often engage in large-scale modeling and simulations, as well as those in the humanities, who need high-throughput computing to analyze large repositories of digitized source materials.
The CRC supports leading-edge research with free access to up to 25,000 computational hours on advanced computing hardware and software for fields across the entire research community, along with training and consultation by CRC research faculty. The PSC is a joint venture with Pitt and CMU, and provides forward-looking technology solutions to advance research nationwide while also coordinating the research endeavors of each university to enhance cooperation.
Get Started and Get Help
Learn more about the IT resources for researchers on the Pitt IT website, including what each app can do and how to access each service. If you need help with any of the resources or need advice about addressing a technical issue your research project is facing, contact Pitt IT’s Technology Help Desk . You can also access a wealth of information about support and training services through:
- Pitt Research and Office of Sponsored Programs (OSP)
- Clinical and Translational Science Institute (CTSI)
- Health Sciences Library System (HSLS)
Happy researching!
-- By Karen Beaudway, Pitt IT Blogger
Microsoft Research Blog
Microsoft at chi 2024: innovations in human-centered design.
Published May 15, 2024
Share this page
- Share on Facebook
- Share on Twitter
- Share on LinkedIn
- Share on Reddit
- Subscribe to our RSS feed

The ways people engage with technology, through its design and functionality, determine its utility and acceptance in everyday use, setting the stage for widespread adoption. When computing tools and services respect the diversity of people’s experiences and abilities, technology is not only functional but also universally accessible. Human-computer interaction (HCI) plays a crucial role in this process, examining how technology integrates into our daily lives and exploring ways digital tools can be shaped to meet individual needs and enhance our interactions with the world.
The ACM CHI Conference on Human Factors in Computing Systems is a premier forum that brings together researchers and experts in the field, and Microsoft is honored to support CHI 2024 as a returning sponsor. We’re pleased to announce that 33 papers by Microsoft researchers and their collaborators have been accepted this year, with four winning the Best Paper Award and seven receiving honorable mentions.
This research aims to redefine how people work, collaborate, and play using technology, with a focus on design innovation to create more personalized, engaging, and effective interactions. Several projects emphasize customizing the user experience to better meet individual needs, such as exploring the potential of large language models (LLMs) to help reduce procrastination. Others investigate ways to boost realism in virtual and mixed reality environments, using touch to create a more immersive experience. There are also studies that address the challenges of understanding how people interact with technology. These include applying psychology and cognitive science to examine the use of generative AI and social media, with the goal of using the insights to guide future research and design directions. This post highlights these projects.
MICROSOFT RESEARCH PODCAST

AI Frontiers: The future of scale with Ahmed Awadallah and Ashley Llorens
This episode features Senior Principal Research Manager Ahmed H. Awadallah , whose work improving the efficiency of large-scale AI models and efforts to help move advancements in the space from research to practice have put him at the forefront of this new era of AI.
Best Paper Award recipients
DynaVis: Dynamically Synthesized UI Widgets for Visualization Editing Priyan Vaithilingam, Elena L. Glassman, Jeevana Priya Inala , Chenglong Wang GUIs used for editing visualizations can overwhelm users or limit their interactions. To address this, the authors introduce DynaVis, which combines natural language interfaces with dynamically synthesized UI widgets, enabling people to initiate and refine edits using natural language.
Generative Echo Chamber? Effects of LLM-Powered Search Systems on Diverse Information Seeking Nikhil Sharma, Q. Vera Liao , Ziang Xiao Conversational search systems powered by LLMs potentially improve on traditional search methods, yet their influence on increasing selective exposure and fostering echo chambers remains underexplored. This research suggests that LLM-driven conversational search may enhance biased information querying, particularly when the LLM’s outputs reinforce user views, emphasizing significant implications for the development and regulation of these technologies.
Piet: Facilitating Color Authoring for Motion Graphics Video Xinyu Shi, Yinghou Wang, Yun Wang , Jian Zhao Motion graphic (MG) videos use animated visuals and color to effectively communicate complex ideas, yet existing color authoring tools are lacking. This work introduces Piet, a tool prototype that offers an interactive palette and support for quick theme changes and controlled focus, significantly streamlining the color design process.
The Metacognitive Demands and Opportunities of Generative AI Lev Tankelevitch , Viktor Kewenig, Auste Simkute, Ava Elizabeth Scott, Advait Sarkar , Abigail Sellen , Sean Rintel Generative AI systems offer unprecedented opportunities for transforming professional and personal work, yet they present challenges around prompting, evaluating and relying on outputs, and optimizing workflows. This paper shows that metacognition—the psychological ability to monitor and control one’s thoughts and behavior—offers a valuable lens through which to understand and design for these usability challenges.
Honorable Mentions
B ig or Small, It’s All in Your Head: Visuo-Haptic Illusion of Size-Change Using Finger-Repositioning Myung Jin Kim, Eyal Ofek, Michel Pahud , Mike J. Sinclair, Andrea Bianchi This research introduces a fixed-sized VR controller that uses finger repositioning to create a visuo-haptic illusion of dynamic size changes in handheld virtual objects, allowing users to perceive virtual objects as significantly smaller or larger than the actual device.
LLMR: Real-time Prompting of Interactive Worlds Using Large Language Models Fernanda De La Torre, Cathy Mengying Fang, Han Huang, Andrzej Banburski-Fahey, Judith Amores , Jaron Lanier Large Language Model for Mixed Reality (LLMR) is a framework for the real-time creation and modification of interactive mixed reality experiences using LLMs. It uses novel strategies to tackle difficult cases where ideal training data is scarce or where the design goal requires the synthesis of internal dynamics, intuitive analysis, or advanced interactivity.
Observer Effect in Social Media Use Koustuv Saha, Pranshu Gupta, Gloria Mark, Emre Kiciman , Munmun De Choudhury This work investigates the observer effect in behavioral assessments on social media use. The observer effect is a phenomenon in which individuals alter their behavior due to awareness of being monitored. Conducted over an average of 82 months (about 7 years) retrospectively and five months prospectively using Facebook data, the study found that deviations in expected behavior and language post-enrollment in the study reflected individual psychological traits. The authors recommend ways to mitigate the observer effect in these scenarios.
Reading Between the Lines: Modeling User Behavior and Costs in AI-Assisted Programming Hussein Mozannar, Gagan Bansal , Adam Fourney , Eric Horvitz By investigating how developers use GitHub Copilot, the authors created CUPS, a taxonomy of programmer activities during system interaction. This approach not only elucidates interaction patterns and inefficiencies but can also drive more effective metrics and UI design for code-recommendation systems with the goal of improving programmer productivity.
SharedNeRF: Leveraging Photorealistic and View-dependent Rendering for Real-time and Remote Collaboration Mose Sakashita, Bala Kumaravel, Nicolai Marquardt , Andrew D. Wilson SharedNeRF, a system for synchronous remote collaboration, utilizes neural radiance field (NeRF) technology to provide photorealistic, viewpoint-specific renderings that are seamlessly integrated with point clouds to capture dynamic movements and changes in a shared space. A preliminary study demonstrated its effectiveness, as participants used this high-fidelity, multi-perspective visualization to successfully complete a flower arrangement task.
Understanding the Role of Large Language Models in Personalizing and Scaffolding Strategies to Combat Academic Procrastination Ananya Bhattacharjee, Yuchen Zeng, Sarah Yi Xu, Dana Kulzhabayeva, Minyi Ma, Rachel Kornfield, Syed Ishtiaque Ahmed, Alex Mariakakis, Mary P. Czerwinski , Anastasia Kuzminykh, Michael Liut, Joseph Jay Williams In this study, the authors explore the potential of LLMs for customizing academic procrastination interventions, employing a technology probe to generate personalized advice. Their findings emphasize the need for LLMs to offer structured, deadline-oriented advice and adaptive questioning techniques, providing key design insights for LLM-based tools while highlighting cautions against their use for therapeutic guidance.
Where Are We So Far? Understanding Data Storytelling Tools from the Perspective of Human-AI Collaboration Haotian Li, Yun Wang , Huamin Qu This paper evaluates data storytelling tools using a dual framework to analyze the stages of the storytelling workflow—analysis, planning, implementation, communication—and the roles of humans and AI in each stage, such as creators, assistants, optimizers, and reviewers. The study identifies common collaboration patterns in existing tools, summarizes lessons from these patterns, and highlights future research opportunities for human-AI collaboration in data storytelling.
Learn more about our work and contributions to CHI 2024, including our full list of publications , on our conference webpage .
Related publications
Observer effect in social media use, where are we so far understanding data storytelling tools from the perspective of human-ai collaboration, the metacognitive demands and opportunities of generative ai, piet: facilitating color authoring for motion graphics video, dynavis: dynamically synthesized ui widgets for visualization editing, generative echo chamber effects of llm-powered search systems on diverse information seeking, understanding the role of large language models in personalizing and scaffolding strategies to combat academic procrastination, sharednerf: leveraging photorealistic and view-dependent rendering for real-time and remote collaboration, big or small, it’s all in your head: visuo-haptic illusion of size-change using finger-repositioning, llmr: real-time prompting of interactive worlds using large language models, reading between the lines: modeling user behavior and costs in ai-assisted programming, continue reading.

Research Focus: Week of May 13, 2024

Research Focus: Week of April 15, 2024

Research Focus: Week of March 18, 2024

Advancing human-centered AI: Updates on responsible AI research
Research areas.
Related events
- Microsoft at CHI 2024
Related labs
- Microsoft Research Lab - Cambridge
- Microsoft Research Lab - Redmond
- Microsoft Research Lab – Montréal
- AI Frontiers
- Microsoft Research Lab - Asia
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
Share this page:

IMAGES
VIDEO
COMMENTS
SUBMIT PAPER. The Journal of Information Technology (JIT) is a top-ranked journal, focused on new research addressing information, management, and communications technologies as applied to the digital worlds of business, government and non-governmental enterprises. View full journal description. This journal is a member of the Committee on ...
In the last years, scholarly attention was on a steady rise leading to a significant increase in the number of papers addressing different technological and organizational aspects of digital transformation. In this paper, we consolidate existing findings which mainly stem from the literature of information systems, map the territory by sharing important macro- and micro-level observations, and ...
These methods aid in increasing interest in research. This paper is brief about the need for digital technologies in education and discusses major applications and challenges in education. ... Aside from information resources, technology in education allows students to contact academic professionals worldwide. Technology in education is the ...
Information Technology. New research on information technology from Harvard Business School faculty on issues including the HealthCare.gov fiasco, online privacy concerns, and the civic benefits of technologies that utilize citizen-created data. Page 1 of 60 Results →. 23 Apr 2024.
identify the opportunities for future AI research in IS. The structure of the paper is as follows. First, an introduction to related work on AI in the IS field is presented. Then the methodology of the systematic literature review is explained, and limitations of the study are acknowledged. ... Journal of Information Technology: 3: P6, P8, P95 ...
The seventh paper, An exploratory study of the determinants of information technology hardware production: a country-level analysis, by Namchul Shin and Jason Dedrick examines the factors that impact hardware production in various countries. The results of this research indicate that hardware production in a country is related to its IT demand ...
In this research, information on trends in IT adoption is provided by examining related research works to provide insights and future direction on technology adoption for practitioners and researchers. This paper highlights future research paths that can be taken by researchers who wish to endeavor in technology adoption research.
This paper helps promote future research and technology development to produce better solutions for tackling the COVID-19 pandemic and future pandemics. Previous article in issue; ... To increase the importance and relevance of information systems and technology research, we encourage scholars to actively apply for various government and ...
Research Open Access 13 May 2024 Scientific Reports Volume: 14, P: 10909 Dual-branch information extraction and local attention anchor-free network for defect detection
While information and communication technologies (ICT) are prominent in educational practices at most levels of formal learning, there is relatively little known about the skills and understandings that underlie their effective and efficient use in research higher degree settings. This project aimed to identify doctoral supervisors' and students' perceptions of their roles in using ICT.
The paper draws mainly from the economics and human resources literature to describe trends in impact on jobs and skills development. It uses secondary sources and examples to explore policy options. This paper is structured as follows. The first section begins with a literature review of how technology impacts jobs and skills.
Although technology is a broad term, the paper focuses on the effects of computers, the Internet, and software such as computer assisted instruction, which are currently the most. relevant forms of new technology in education.3 The discussion focuses primarily on the impacts. of computers, the Internet and software on educational outcomes ...
Information technology (IT) is the technology which uses the computer to gather, process, store and precede information. A long way in an extraordinarily undersized time has been reached in the ...
This paper investigates the impact of investment in information technology on the return on assets (ROA) of selected private universities in Indonesia for the period 2008-2014 using Adapted ...
NATO is boosting AI and climate research as scientific diplomacy remains on ice. As the military alliance created to counter the Soviet Union expands, it is prioritizing studies on how climate ...
information society and industrial econom y to knowledge economy is a result of the impact of ICT. and Internet use. Ma in objective of this paper is to describe information technology ...
The world of digitization is growing exponentially; data optimization, security of a network, and energy efficiency are becoming more prominent. The Internet of Things (IoT) is the core technology of modern society. This paper is based on a survey of recent and past technologies used for IoT optimization models, such as IoT with Blockchain, IoT with WSN, IoT with ML, and IoT with big data ...
The Internet-of-Things: Review and Research Directions. This paper presents a review of the Internet-of-Things (IoT) through four conceptualizations: IoT as liquification and density of information of resources; IoT as digital materiality; IoT as assemblage or service system; and IoT as... more. Download.
It also provides insights and suggestions into how information systems and technology scholars can help fight the COVID-19 pandemic. This paper helps promote future research and technology development to produce better solutions for tackling the COVID-19 pandemic and future pandemics.
130 Information Technology Research Topics And Quick Writing Prompts. The field of information technology is one of the most recent developments of the 21st century. Scholars argue that we are living in a technological age. Despite this buzz, however, many students still find it challenging to compose an information technology research topic.
The industry sector that contributes the largest share of technology-related scope 2 and scope 3 GHG emissions is communications, media, and services (Exhibit 1). Enterprise technology's contribution to total emissions is especially high for insurance (45 percent of total scope 2 emissions) and for banking and investment services (36 percent).
Abstract. From elementary schooling to doctoral-level education, technology has become an integral part of the learning process in and out of the classroom. With the implementation of the Common Core Learning Standards, the skills required for research are more valuable than ever, for they are required to succeed in a college setting, as well ...
This paper discusses the various technological trends of information technology, evolving technologies, the percentage impact of technologies on business and government and finally a framework on ...
Advances in research computing have propelled Pitt to the forefront of research, with the University ranking third nationally in NIH funding in FY23. Researchers utilize robust technology to collect, store, and analyze data; document and manage lab processes; and work with collaborators. Pitt IT supports the work of researchers, so they can focus on doing what they do best: making the ...
As a representative of the scientific and technological achievements of the new era, the overall development of virtual reality (VR) technology is becoming increasingly refined, which provides new development ideas and technical support in the field of ancient building restoration and architectural heritage preservation. In this context, digital conservation and the practice of architectural ...
Technology will play an increasingly critical role in addressing these challenges. That is why at the State Department we have prioritized building capacity and expertise in cyber, digital, and emerging technology issues as part of our broader efforts to modernize diplomacy and ensure U.S. foreign policy delivers on the issues that matter most to the lives and livelihoods of the American people.
Honorable Mentions. B ig or Small, It's All in Your Head: Visuo-Haptic Illusion of Size-Change Using Finger-Repositioning Myung Jin Kim, Eyal Ofek, Michel Pahud, Mike J. Sinclair, Andrea Bianchi This research introduces a fixed-sized VR controller that uses finger repositioning to create a visuo-haptic illusion of dynamic size changes in handheld virtual objects, allowing users to perceive ...
Prior to GPT-4o, you could use Voice Mode to talk to ChatGPT with latencies of 2.8 seconds (GPT-3.5) and 5.4 seconds (GPT-4) on average. To achieve this, Voice Mode is a pipeline of three separate models: one simple model transcribes audio to text, GPT-3.5 or GPT-4 takes in text and outputs text, and a third simple model converts that text back to audio.