A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Advertisement
A literature survey of security issues in Cloud, Fog, and Edge IT infrastructure
- Published: 18 October 2022
Cite this article

- Patricia Akello 1 , 2 ,
- Nicole Lang Beebe 1 , 2 &
- Kim-Kwang Raymond Choo ORCID: orcid.org/0000-0001-9208-5336 1 , 2
614 Accesses
Explore all metrics
Increasing complexity in and interconnectivity between technologies and systems (e.g., cloud computing, Internet of Things (IoT), fog and edge computing) can complicate data processing and security requirements. Thus, in this paper we review existing literature survey articles focusing on cloud, fog and edge computing platforms and infrastructures. We then present the result of a systematic survey of existing literature surveys. Our research uses the PRISMA methodology and grounded theory to guide the review process, along with grounded theory for the classification of identified issues. The issues together with research trends and future research recommendations are then discussed, with the objective of informing future research agenda.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

A Comprehensive Survey on Security of Single Source Cloud to Distributed Enviroments Edge and Fog Computing

A Pragmatic Analysis of Security Concerns in Cloud, Fog, and Edge Environment

An Overview on Security Challenges in Cloud, Fog, and Edge Computing
Mell, P., & Grance, T. (2011). “The NIST definition of cloud computing,”
Ramachandra, G., Iftikhar, M., & Khan, F. A. (Jan. 2017). A Comprehensive Survey on Security in Cloud Computing. Procedia Comput Sci , 110 , 465–472. doi: https://doi.org/10.1016/j.procs.2017.06.124
Biswas, A. R., & Giaffreda, R. (2014). “IoT and cloud convergence: Opportunities and challenges,” in 2014 IEEE World Forum on Internet of Things (WF-IoT), Mar. pp. 375–376. doi: https://doi.org/10.1109/WF-IoT.2014.6803194
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012). “Fog Computing and Its Role in the Internet of Things,” in Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, New York, NY, USA, pp. 13–16. doi: https://doi.org/10.1145/2342509.2342513
Khan, S., Parkinson, S., & Qin, Y. (Aug. 2017). Fog computing security: a review of current applications and security solutions. J Cloud Comput , 6 (1), 19. doi: https://doi.org/10.1186/s13677-017-0090-3
Rodero-Merino, L., Vaquero, L. M., Caron, E., Muresan, A., & Desprez, F. (Feb. 2012). Building Safe PaaS Clouds: A Survey on Security in Multitenant Software Platforms. Comput Secur , 31 (1), 96–108. doi: https://doi.org/10.1016/j.cose.2011.10.006
Pearce, M., Zeadally, S., Hunt, R., “Virtualization: Issues, Security Threats, and, & Solutions (2013). ” ACM Comput Surv, vol. 45, no. 2, p. 17:1–17:39, Mar. doi: https://doi.org/10.1145/2431211.2431216
Pande, V. K., Marlecha, C., & Kayte, S. (2016). “A Review-Fog Computing and Its Role in the Internet of Things,”
Moher, D., Liberati, A., Tetzlaff, J., Altman, D. G., & Group, T. P. (2009). “Preferred Reporting Items for Systematic Reviews and Meta-Analyses: The PRISMA Statement,” PLOS Med., vol. 6, no. 7, p. e1000097, Jul. doi: https://doi.org/10.1371/journal.pmed.1000097
Corbin, J. M., & Strauss, A. (1990). “Grounded theory research: Procedures, canons, and evaluative criteria,” Qual. Sociol., vol. 13, no. 1, pp. 3–21, Mar. doi: https://doi.org/10.1007/BF00988593
Chukwu, E., & Garg, L. (2020). A Systematic Review of Blockchain in Healthcare: Frameworks, Prototypes, and Implementations. Ieee Access : Practical Innovations, Open Solutions , 8 , 21196–21214. doi: https://doi.org/10.1109/ACCESS.2020.2969881
Article Google Scholar
Maphosa, M., Doorsamy, W., & Paul, B. S. (2022). Factors Influencing Students’ Choice of and Success in STEM: A Bibliometric Analysis and Topic Modeling Approach. Ieee Transactions On Education , 1–13. doi: https://doi.org/10.1109/TE.2022.3160935
Wilson, M., Sampson, M., Barrowman, N., & Doja, A. (Apr. 2021). Bibliometric Analysis of Neurology Articles Published in General Medicine Journals. JAMA Netw Open , 4 (4), e215840. doi: https://doi.org/10.1001/jamanetworkopen.2021.5840
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (Feb. 2013). An analysis of security issues for cloud computing. J Internet Serv Appl , 4 (1, p. 5,), doi: https://doi.org/10.1186/1869-0238-4-5
Jouini, M., & Rabai, L. B. A. (2014). “Surveying and Analyzing Security Problems in Cloud Computing Environments,” in 2014 Tenth International Conference on Computational Intelligence and Security, Nov. pp. 689–693. doi: https://doi.org/10.1109/CIS.2014.169
Patel, A., Taghavi, M., Bakhtiyari, K., Celestino, J., & Júnior (Jan. 2013). An intrusion detection and prevention system in cloud computing: A systematic review. J Netw Comput Appl , 36 (1), 25–41. doi: https://doi.org/10.1016/j.jnca.2012.08.007
Rebollo, O., Mellado, D., & Fernández-Medina, E., “A Systematic Review of Information Security Governance Frameworks in the Cloud Computing Environment,” p.18
Wolfswinkel, J. F., Furtmueller, E., & Wilderom, C. P. M. (2013). “Using grounded theory as a method for rigorously reviewing literature,” Eur. J. Inf. Syst., vol. 22, no. 1, pp. 45–55, Jan. doi: https://doi.org/10.1057/ejis.2011.51
Birkmeier, D., & Overhage, S. (2009). “On Component Identification Approaches – Classification, State of the Art, and Comparison,”in Component-Based Software Engineering, pp.1–18
Osanaiye, O., Choo, K. K. R., & Dlodlo, M. (2016). “Distributed Denial of Service (DDoS) Resilience in Cloud,” J Netw Comput Appl, vol. 67, no. C, pp. 147–165, May doi: https://doi.org/10.1016/j.jnca.2016.01.001
Stojmenovic, I., & Wen, S. (2014). “The Fog computing paradigm: Scenarios and security issues,” in 2014 Federated Conference on Computer Science and Information Systems, Sep. pp. 1–8. doi: https://doi.org/10.15439/2014F503
Hong, J. B., Nhlabatsi, A., Kim, D. S., Hussein, A., Fetais, N., & Khan, K. M. (Feb. 2019). Systematic identification of threats in the cloud: A survey. Computer Networks , 150 , 46–69. doi: https://doi.org/10.1016/j.comnet.2018.12.009
Patil, R., & Modi, C. (2019). “An Exhaustive Survey on Security Concerns and Solutions at Different Components of Virtualization,” ACM Comput. Surv. CSUR, vol. 52, no. 1, p. 12:1–12:38, Feb. doi: https://doi.org/10.1145/3287306
Kumar, R., & Goyal, R. (Aug. 2019). On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput Sci Rev , 33 , 1–48. doi: https://doi.org/10.1016/j.cosrev.2019.05.002
Subramanian, N., & Jeyaraj, A. (Oct. 2018). Recent security challenges in cloud computing. Computers & Electrical Engineering , 71 , 28–42. doi: https://doi.org/10.1016/j.compeleceng.2018.06.006
Singh, A., & Chatterjee, K. (Feb. 2017). Cloud security issues and challenges: A survey. J Netw Comput Appl , 79 , 88–115. doi: https://doi.org/10.1016/j.jnca.2016.11.027
Coppolino, L., D’Antonio, S., Mazzeo, G., & Romano, L. (Apr. 2017). Cloud security: Emerging threats and current solutions. Computers & Electrical Engineering , 59 , 126–140. doi: https://doi.org/10.1016/j.compeleceng.2016.03.004
Tari, Z., Yi, X., Premarathne, U. S., Bertok, P., & Khalil, I. (2015). “Security and Privacy in Cloud Computing: Vision, Trends, and Challenges,” IEEE Cloud Comput., vol. 2, no. 2, pp. 30–38, Mar. doi: https://doi.org/10.1109/MCC.2015.45
Ali, M., Khan, S. U., & Vasilakos, A. V. (Jun. 2015). Security in cloud computing: Opportunities and challenges. Information Sciences , 305 , 357–383. doi: https://doi.org/10.1016/j.ins.2015.01.025
Singh, S., Jeong, Y. S., & Park, J. H. (Nov. 2016). A survey on cloud computing security: Issues, threats, and solutions. J Netw Comput Appl , 75 , 200–222. doi: https://doi.org/10.1016/j.jnca.2016.09.002
Fernandes, D. A. B., Soares, L. F. B., Gomes, J. V., Freire, M. M., & Inácio, P. R. M. (2014). “Security issues in cloud environments: a survey,” Int. J. Inf. Secur., vol. 13, no. 2, pp. 113–170, Apr. doi: https://doi.org/10.1007/s10207-013-0208-7
Abbas, A., & Khan, S. U. (2014). “A Review on the State-of-the-Art Privacy-Preserving Approaches in the e-Health Clouds,” IEEE J. Biomed. Health Inform., vol. 18, no. 4, pp. 1431–1441, Jul. doi: https://doi.org/10.1109/JBHI.2014.2300846
Aguiar, E., Zhang, Y., & Blanton, M. (2014). “An Overview of Issues and Recent Developments in Cloud Computing and Storage Security,”. In K. J. Han, B. Y. Choi, & S. Song (Eds.), High Performance Cloud Auditing and Applications (pp. 3–33). New York, NY: Springer. doi: https://doi.org/10.1007/978-1-4614-3296-8_1
Chapter Google Scholar
Oktay, U., & Sahingoz, O. K. (2013). “Proxy Network Intrusion Detection System for cloud computing,” in 2013 The International Conference on Technological Advances in Electrical, Electronics and Computer Engineering (TAEECE), May pp. 98–104. doi: https://doi.org/10.1109/TAEECE.2013.6557203
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (Feb. 2013). A Survey on Security Issues and Solutions at Different Layers of Cloud Computing. J Supercomput , 63 (2), 561–592. doi: https://doi.org/10.1007/s11227-012-0831-5
Rong, C., Nguyen, S. T., & Jaatun, M. G. (Jan. 2013). Beyond lightning: A survey on security challenges in cloud computing. Computers & Electrical Engineering , 39 (1), 47–54. doi: https://doi.org/10.1016/j.compeleceng.2012.04.015
Pearson, S. (2013). “Privacy, Security and Trust in Cloud Computing. In S. Pearson, & G. Yee (Eds.), ” in Privacy and Security for Cloud Computing (pp. 3–42). London: Springer London. doi: https://doi.org/10.1007/978-1-4471-4189-1_1
Xiao, Z., & Xiao, Y. (Second 2013). Security and Privacy in Cloud Computing. Ieee Communication Surveys And Tutorials , 15 (2), 843–859. doi: https://doi.org/10.1109/SURV.2012.060912.00182
Perez-Botero, D., Szefer, J., & Lee, R. B. (2013). “Characterizing Hypervisor Vulnerabilities in Cloud Computing Servers,” in Proceedings of the 2013 International Workshop on Security in Cloud Computing, New York, NY, USA, pp. 3–10. doi: https://doi.org/10.1145/2484402.2484406
Kulkarni, G., Gambhir, J., Patil, T., & Dongare, A. (2012). “A security aspects in cloud computing,” in IEEE International Conference on Computer Science and Automation Engineering, Jun. 2012, pp. 547–550. doi: https://doi.org/10.1109/ICSESS.2012.6269525
Zissis, D., & Lekkas, D. (2012). Addressing cloud computing security issues. Future Gener Comput Syst , 28 (3), 583–592
Vaquero, L. M., Rodero-Merino, L., & Morán, D. (Jan. 2011). Locking the Sky: A Survey on IaaS Cloud Security. Computing , 91 (1), 93–118. doi: https://doi.org/10.1007/s00607-010-0140-x
Che, J., Duan, Y., Zhang, T., & Fan, J. (Jan. 2011). Study on the Security Models and Strategies of Cloud Computing. Procedia Engineering , 23 , 586–593. doi: https://doi.org/10.1016/j.proeng.2011.11.2551
Behl, A., & Behl, K. (2012). “An analysis of cloud computing security issues,” in 2012 World Congress on Information and Communication Technologies, Oct. pp. 109–114. doi: https://doi.org/10.1109/WICT.2012.6409059
Grobauer, B., Walloschek, T., & Stocker, E. (2011). “Understanding Cloud Computing Vulnerabilities,” IEEE Secur. Priv., vol. 9, no. 2, pp. 50–57, Mar. doi: https://doi.org/10.1109/MSP.2010.115
Subashini, S., & Kavitha, V. (Jan. 2011). A survey on security issues in service delivery models of cloud computing. J Netw Comput Appl , 34 (1), 1–11. doi: https://doi.org/10.1016/j.jnca.2010.07.006
Zhou, M., Zhang, R., Xie, W., Qian, W., & Zhou, A. (2010). “Security and Privacy in Cloud Computing: A Survey,” in 2010 Sixth International Conference on Semantics, Knowledge and Grids, Nov. pp. 105–112. doi: https://doi.org/10.1109/SKG.2010.19
Takabi, H., Joshi, J. B. D., & Ahn, G. J. (2010). “Security and Privacy Challenges in Cloud Computing Environments,” IEEE Secur. Priv., vol. 8, no. 6, pp. 24–31, Nov. doi: https://doi.org/10.1109/MSP.2010.186
Zhang, P., Zhou, M., & Fortino, G. (Nov. 2018). Security and trust issues in Fog computing: A survey. Future Gener Comput Syst , 88 , 16–27. doi: https://doi.org/10.1016/j.future.2018.05.008
Roman, R., Lopez, J., Mambo, M., et al. (Jan. 2018). : A survey and analysis of security threats and challenges,” Future Gener. Comput. Syst., vol. 78, pp. 680–698, doi: https://doi.org/10.1016/j.future.2016.11.009
Mukherjee, M., et al. (2017). Security and Privacy in Fog Computing: Challenges. Ieee Access : Practical Innovations, Open Solutions , 5 , 19293–19304. doi: https://doi.org/10.1109/ACCESS.2017.2749422
Alrawais, A., Alhothaily, A., Hu, C., & Cheng, X. (2017). “Fog Computing for the Internet of Things: Security and Privacy Issues,” IEEE Internet Comput., vol. 21, no. 2, pp. 34–42, Mar. doi: https://doi.org/10.1109/MIC.2017.37
Stojmenovic, I., Wen, S., Huang, X., & Luan, H. (2016). An overview of Fog computing and its security issues. Concurr Comput Pract Exp , 28 (10), 2991–3005. doi: https://doi.org/10.1002/cpe.3485
Yi, S., Qin, Z., & Li, Q. (2015). “Security and Privacy Issues of Fog Computing: A Survey,” in Wireless Algorithms, Systems, and Applications, pp. 685–695
Yi, S., Li, C., & Li, Q. (2015). “A Survey of Fog Computing: Concepts, Applications and Issues,” in Proceedings of the 2015 Workshop on Mobile Big Data, New York, NY, USA, pp. 37–42. doi: https://doi.org/10.1145/2757384.2757397
Lee, K., Kim, D., Ha, D., Rajput, U., & Oh, H. (2015). “On security and privacy issues of fog computing supported Internet of Things environment,” in 2015 6th International Conference on the Network of the Future (NOF), Sep. pp. 1–3. doi: https://doi.org/10.1109/NOF.2015.7333287
Wang, Y., Uehara, T., & Sasaki, R. (2015). “Fog Computing: Issues and Challenges in Security and Forensics,” in 2015 IEEE 39th Annual Computer Software and Applications Conference, Jul. vol. 3, pp. 53–59. doi: https://doi.org/10.1109/COMPSAC.2015.173
Kolhar, M., Abu-Alhaj, M. M., & Abd El-atty, S. M. (Jan. 2017). Cloud Data Auditing Techniques with a Focus on Privacy and Security. Ieee Security And Privacy , 15 (1), 42–51. doi: https://doi.org/10.1109/MSP.2017.16
“NVD - CVE (2020). -2018-18808.” https://nvd.nist.gov/vuln/detail/CVE-2018-18808 (accessed Feb. 14,
Fazzini, K., “A Technical Slip-up Exposes Cloud Collaboration Risks,” Wall Street Journal, Jun. 13, 2017. Accessed: Feb. 04, 2020. [Online]. Available: https://www.wsj.com/articles/a-technical-slip-up-exposes-cloud-collaboration-risks-1497353313
Sgandurra, D., & Lupu, E. (2016). Evolution of Attacks, Threat Models, and Solutions for Virtualized Systems. ACM Comput Surv , 48 (3), 1. doi: https://doi.org/10.1145/2856126 . 46:38, Feb
Chaudhary, D., Bhushan, K., & Gupta, B. B. (2018). “Survey on DDoS Attacks and Defense Mechanisms in Cloud and Fog Computing,” Int. J. E-Serv. Mob. Appl. IJESMA, vol. 10, no. 3, pp. 61–83, Jul. doi: https://doi.org/10.4018/IJESMA.2018070104
Gupta, B. B., & Badve, O. P. (2017). “Taxonomy of DoS and DDoS attacks and desirable defense mechanism in a Cloud computing environment,” Neural Comput. Appl., vol. 28, no. 12, pp. 3655–3682, Dec. doi: https://doi.org/10.1007/s00521-016-2317-5
“Vulnerability and Threat Trends Research Report,” Skybox Security, Jul. 11 (2019). https://www.skyboxsecurity.com/trends-report (accessed Feb. 14, 2020)
Muncaster, P. (2019). “Over a Third of Firms Have Suffered a Cloud Attack,” Infosecurity Magazine, Aug. 22, https://www.infosecurity-magazine.com:443/news/over-third-firms-have-suffered/ (accessed Feb. 14, 2020)
d Silva, C. M. R., d Silva, J. L. C., Rodrigues, R. B., Campos, G. M. M., Nascimento, L. M., & Garcia, V. C. (2013). “Security Threats in Cloud Computing Models: Domains and Proposals,” in IEEE Sixth International Conference on Cloud Computing, Jun. 2013, pp. 383–389. doi: https://doi.org/10.1109/CLOUD.2013.125
“Top Threats to Cloud Computing (2019). : Egregious,” Cloud Security Alliance. https://cloudsecurityalliance.org/artifacts/top-threats-to-cloud-computing-egregious-eleven/ (accessed Sep.13,
“Top Threats to Cloud Computing Plus: (accessed Apr. 01, 2019). ” Cloud Security Alliance. https://cloudsecurityalliance.org/artifacts/top-threats-cloud-computing-plus-industry-insights/
Akello, P., Beebe, N. L., & Raymond, K. K. C., “Volitional non-malicious insider threats: At the intersection of COVID-19, WFH and cloud-facilitated shadow-apps,” 27th Annu. Am. Conf. Inf. Syst. AMCIS 2021, 2021, Accessed: May 27, 2022. [Online]. Available: https://pesquisa.bvsalud.org/global-literature-on-novel-coronavirus-2019-ncov/resource/pt/covidwho-1513605
Silic, M., & Back, A. (Sep. 2014). Shadow IT – A view from behind the curtain. Comput Secur , 45 , 274–283. doi: https://doi.org/10.1016/j.cose.2014.06.007
Mallmann, G. L., Maçada, A. C. G., & Oliveira, M. (2018). “The influence of shadow IT usage on knowledge sharing: An exploratory study with IT users,” Bus. Inf. Rev., vol. 35, no. 1, pp. 17–28, Mar. doi: https://doi.org/10.1177/0266382118760143
Shaikh, A., “Shadow-IT System and Insider Threat: An Assessment of an Opportunity Dimension for the Identity Theft,” in HCI International 2018 – Posters’ Extended Abstracts, Cham, 2018, pp. 314–317. doi: https://doi.org/10.1007/978-3-319-92285-0_44
Silic, M., Barlow, J. B., & Back, A. (2017). “A new perspective on neutralization and deterrence: Predicting shadow IT usage,” Inf. Manage., vol. 54, no. 8, pp. 1023–1037, Dec. doi: https://doi.org/10.1016/j.im.2017.02.007
Walterbusch, M., Fietz, A., & Teuteberg, F. (2017). Missing cloud security awareness: investigating risk exposure in shadow IT. J Enterp Inf Manag Jul . doi: https://doi.org/10.1108/JEIM-07-2015-0066
Cappelli, D. M., Moore, A. P., & Trzeciak, R. F. (2012). The CERT Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud) . Addison-Wesley
Barona, R., & Anita, E. A. M. (2017). “A survey on data breach challenges in cloud computing security: Issues and threats,” in 2017 International Conference on Circuit,Power and Computing Technologies (ICCPCT), Apr. pp. 1–8. doi: https://doi.org/10.1109/ICCPCT.2017.8074287
“Study Finds (2020). ‘Lurking Malice’ in Cloud Hosting Services.” https://www.news.gatech.edu/2016/10/19/study-finds-lurking-malice-cloud-hosting-services (accessed Feb. 14,
Korolov, M. (2016). “Ransomware prevalent in cloud-based malware,” CSO Online, Sep. 08, https://www.csoonline.com/article/3117751/ransomware-prevalent-in-cloud-based-malware.html (accessed Feb. 04, 2020)
Pearson, S., & Benameur, A. (2010). “Privacy, Security and Trust Issues Arising from Cloud Computing,” in 2010 IEEE Second International Conference on Cloud Computing Technology and Science, Nov. pp. 693–702. doi: https://doi.org/10.1109/CloudCom.2010.66
Ranger, S. (2020). “GitHub hit with the largest DDoS attack ever seen,” ZDNet. https://www.zdnet.com/article/github-was-hit-with-the-largest-ddos-attack-ever-seen/ (accessed Feb.15,
“Web attack knocks BBC websites offline - BBC News (2020). ” https://www.bbc.com/news/technology-35204915 (accessed Feb. 15,
Luo, S., Lin, Z., Chen, X., Yang, Z., & Chen, J. (2011). “Virtualization security for cloud computing service,” in 2011 International Conference on Cloud and Service Computing, Dec. pp. 174–179. doi: https://doi.org/10.1109/CSC.2011.6138516
ssd-researcher (2018). “SSD Advisory – Oracle VirtualBox Multiple Guest to Host Escape Vulnerabilities,” SSD Secure Disclosure, Jan. 24, https://ssd-disclosure.com/archives/3649/ssd-advisory-oracle-virtualbox-multiple-guest-to-host-escape-vulnerabilities (accessed Feb. 06, 2020)
Ahmed, U., Raza, I., & Hussain, S. A. (2019). “Trust Evaluation in Cross-Cloud Federation: Survey and Requirement Analysis,” ACM Comput Surv, vol. 52, no. 1, p. 19:1–19:37, Feb. doi: https://doi.org/10.1145/3292499
“Top 6 Cloud Security Issues in Cloud Computing (2020). ” https://www.skyhighnetworks.com/cloud-security-blog/6-cloud-security-issues-that-businesses-experience/ (accessed Feb.15,
Huang, J., & Nicol, D. M. (Apr. 2013). Trust mechanisms for cloud computing. J Cloud Comput Adv Syst Appl , 2 (1, p. 9,), doi: https://doi.org/10.1186/2192-113X-2-9
vurukonda, N., Rao, B. T., & “A Study on Data Storage Security Issues in Cloud Computing. (Jan. 2016).” Procedia Comput. Sci., 92,128–135, doi: https://doi.org/10.1016/j.procs.2016.07.335 .
Rao, R. V., & Selvamani, K. (Jan. 2015). Data Security Challenges and Its Solutions in Cloud Computing. Procedia Comput Sci , 48 , 204–209. doi: https://doi.org/10.1016/j.procs.2015.04.171
“2019 Data Breaches (2020). : 4 Billion Records Breached So Far | Norton.” https://us.norton.com/internetsecurity-emerging-threats-2019-data-breaches.html (accessed Feb. 15,
B. G. Rama and 11/21/2017, “Uber Discloses Year-Old AWS Data Breach, Exposing Millions of Users -,” AWSInsider. https://awsinsider.net/articles/2017/11/21/uber-aws-data-breach.aspx
Chang, V., & Ramachandran, M. (Jan. 2016). “Towards Achieving Data Security with the Cloud Computing Adoption Framework,” IEEE Trans. Serv. Comput., 9, 1,138–151, doi: https://doi.org/10.1109/TSC.2015.2491281 .
Kandias, M., Stavrou, V., Bozovic, N., & Gritzalis, D. (2013). “Proactive Insider Threat Detection Through Social Media: The YouTube Case,” in Proceedings of the 12th ACM Workshop on Workshop on Privacy in the Electronic Society, New York, NY, USA, pp. 261–266. doi: https://doi.org/10.1145/2517840.2517865
Rundle, J., “Human Error Often the Culprit in Cloud Data Breaches,” Wall Street Journal, Aug. 27, 2019. Accessed: Feb. 15, 2020. [Online]. Available: https://www.wsj.com/articles/human-error-often-the-culprit-in-cloud-data-breaches-11566898203
Duncan, A. J., Creese, S., & Goldsmith, M. (2012). “Insider Attacks in Cloud Computing,” in IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Jun. 2012, pp. 857–862. doi: https://doi.org/10.1109/TrustCom.2012.188
Esposito, C., Santis, A. D., Tortora, G., Chang, H., & Choo, K. R. (Jan. 2018). “Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy?,” IEEE Cloud Comput., 5, 1,31–37, doi: https://doi.org/10.1109/MCC.2018.011791712 .
“Security Update - About Facebook (2020). ” https://about.fb.com/news/2018/09/security-update/ (accessed Feb. 15,
“Expect, A. P. I. (accessed Feb. 15, 2020). Breaches to Accelerate.” https://www.darkreading.com/application-security/expect-api-breaches-to-accelerate/d/d-id/1332504
“Why Cloud Computing Cyber Security Risks Are On The Rise (2020). :Report.” https://www.forbes.com/sites/jeanbaptiste/2019/07/25/why-cloud-computing-cyber-security-risks-are-on-the-rise-report/#71c281ea5621 (accessed Feb. 15,
de Carvalho, C. A. B., de Andrade, R. M., de Castro, M. F., Coutinho, E. F., & Agoulmine, N. (Apr. 2017). State of the art and challenges of security SLA for cloud computing. Computers & Electrical Engineering , 59 , 141–152. doi: https://doi.org/10.1016/j.compeleceng.2016.12.030
“Resource Library | McAfee (2020). ” https://www.mcafee.com/enterprise/en-us/resource-library.html (accessed Feb.15,
TerryLanfear (accessed Nov. 21, 2019). “Shared responsibility in the cloud - Microsoft Azure.” https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
Aluvalu, R., & Muddana, L., “A Survey on Access Control Models in Cloud Computing,” in Emerging ICT for Bridging the Future - Proceedings of the 49th Annual Convention of the Computer Society of India (CSI) Volume 1, Cham, 2015, pp. 653–664. doi: https://doi.org/10.1007/978-3-319-13728-5_73
L. H et al., “Risk based access control in cloud computing,” in 2015 International Conference on Green Computing and Internet of Things (ICGCIoT), pp. 1502–1505. doi: https://doi.org/10.1109/ICGCIoT.2015.7380704
Tsidulko, J. (2017). “AWS Warns Users To Secure Storage Buckets,” CRN, Jul. 19, https://www.crn.com/news/cloud/300089076/aws-warns-users-to-secure-storage-buckets.htm (accessed Feb. 15, 2020)
“Latest Cloud Security Trends Report From RedLock CSI Team Highlights Serious Growth in Cryptojacking (accessed Feb. 15, 2020). Continuing Lack of Compliance with Industry Standards.” https://redlock.io/news/redlock-cloud-security-trends-report-highlights-lack-of-compliance-with-industry-standards
Hong, J. I., & Landay, J. A. (2004). “An architecture for privacy-sensitive ubiquitous computing,” in Proceedings of the 2nd international conference on Mobile systems, applications, and services, Boston, MA, USA, Jun. pp. 177–189. doi: https://doi.org/10.1145/990064.990087
Aloraini, A., & Hammoudeh, M. (2017). “A Survey on Data Confidentiality and Privacy in Cloud Computing,” in Proceedings of the International Conference on Future Networks and Distributed Systems, New York, NY, USA, p. 10:1–10:7. doi: https://doi.org/10.1145/3102304.3102314
Rocha, F., “Insider threat: memory confidentiality and integrity in the cloud,” Ph.D., University of Newcastle Upon Tyne (United Kingdom), England, 2015. Accessed: Sep. 22, 2018. [Online]. Available: https://search.proquest.com/docview/1827514860/?pq-origsite=primo
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (Jan. 2015). Security, privacy and trust in Internet of Things: The road ahead. Computer Networks , 76 , 146–164. doi: https://doi.org/10.1016/j.comnet.2014.11.008
“Exploring container (2019). security: the shared responsibility model in GKE,”Google Cloud Blog. https://cloud.google.com/blog/products/containers-kubernetes/exploring-container-security-the-shared-responsibility-model-in-gke-container-security-shared-responsibility-model-gke/ (accessed Nov. 21,
Zhang, G., Li, T., Li, Y., Hui, P., & Jin, D. (2018). “Blockchain-Based Data Sharing System for AI-Powered Network Operations,” J. Commun. Inf. Netw., vol. 3, no. 3, pp. 1–8, Sep. doi: https://doi.org/10.1007/s41650-018-0024-3
Bakshi, A., & Dujodwala, Y. B. (2010). “Securing Cloud from DDOS Attacks Using Intrusion Detection System in Virtual Machine,” in 2010 Second International Conference on Communication Software and Networks, Feb. pp. 260–264. doi: https://doi.org/10.1109/ICCSN.2010.56
Chonka, A., Xiang, Y., Zhou, W., & Bonti, A. (2011). “Cloud security defence to protect cloud computing against HTTP-DoS and XML-DoS attacks,” J. Netw. Comput. Appl., vol. 34, no. 4, pp. 1097–1107, Jul. doi: https://doi.org/10.1016/j.jnca.2010.06.004
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (Jan. 2013). A survey of intrusion detection techniques in Cloud. J Netw Comput Appl , 36 (1), 42–57. doi: https://doi.org/10.1016/j.jnca.2012.05.003
Patel, A., Taghavi, M., Bakhtiyari, K., & Júnior, J. C. (2012). “Taxonomy and Proposed Architecture of Intrusion Detection and Prevention Systems for Cloud Computing,” in Proceedings of the 4th International Conference on Cyberspace Safety and Security, Berlin, Heidelberg, pp. 441–458. doi: https://doi.org/10.1007/978-3-642-35362-8_33
Wang, J., Wu, L., Choo, K. K. R., & He, D. (2020). “Blockchain-Based Anonymous Authentication With Key Management for Smart Grid Edge Computing Infrastructure,” IEEE Trans. Ind. Inform., vol. 16, no. 3, pp. 1984–1992, Mar. doi: https://doi.org/10.1109/TII.2019.2936278
Ahmed, M., & Litchfield, A. T. (Jan. 2018). Taxonomy for Identification of Security Issues in Cloud Computing Environments. J Comput Inf Syst , 58 (1), 79–88. doi: https://doi.org/10.1080/08874417.2016.1192520
Hassan, B. M., Fouad, K. M., & Hassan, M. F. (2015). “Keystroke Dynamics Authentication in Cloud Computing: A Survey,” Int J Enterp Inf Syst, vol. 11, no. 4, pp. 99–120, Oct. doi: https://doi.org/10.4018/IJEIS.2015100105
Khan, M. A. (Aug. 2016). A survey of security issues for cloud computing. J Netw Comput Appl , 71 , 11–29. doi: https://doi.org/10.1016/j.jnca.2016.05.010
Li, H., Lu, R., Misic, J., & Mahmoud, M. (May 2018). Security and Privacy of Connected Vehicular Cloud Computing. IEEE Netw , 32 (3), 4–6. doi: https://doi.org/10.1109/MNET.2018.8370870
Mollah, M. B., Azad, M. A. K., & Vasilakos, A. (Apr. 2017). Security and privacy challenges in mobile cloud computing: Survey and way ahead. J Netw Comput Appl , 84 , 38–54. doi: https://doi.org/10.1016/j.jnca.2017.02.001
Jayasinghe, U., Lee, G. M., MacDermott, Á., & Rhee, W. S. (2019). “TrustChain: A Privacy Preserving Blockchain with Edge Computing,” Wireless Communications and Mobile Computing, https://www.hindawi.com/journals/wcmc/2019/2014697/ (accessed Feb. 14, 2020)
Bhatia, T., & Verma, A. K. (Jun. 2017). Data Security in Mobile Cloud Computing Paradigm: A Survey, Taxonomy and Open Research Issues. J Supercomput , 73 (6), 2558–2631. doi: https://doi.org/10.1007/s11227-016-1945-y
Shin, Y., Koo, D., & Hur, J. (2017). “A Survey of Secure Data Deduplication Schemes for Cloud Storage Systems,” ACM Comput Surv, vol. 49, no. 4, p. 74:1–74:38, Jan. doi: https://doi.org/10.1145/3017428
Sookhak, M., et al., “Remote Data Auditing in Cloud Computing Environments: A Survey, Taxonomy, and Open Issues,”ACM Comput. Surv., vol. 47, no. 4, p. 65:1–65:34, May 2015, doi: https://doi.org/10.1145/2764465
Stolfo, S. J., Salem, M. B., & Keromytis, A. D. (2012). “Fog computing: Mitigating insider data theft attacks in the cloud,” in Security and Privacy Workshops (SPW), 2012 IEEE Symposium on, pp. 125–128. Accessed: Feb. 21, 2017. [Online]. Available: http://ieeexplore.ieee.org/abstract/document/6227695/
Tang, J., Cui, Y., Li, Q., Ren, K., Liu, J., & Buyya, R. (2016). “Ensuring Security and Privacy Preservation for Cloud Data Services,”ACM Comput Surv, 49, 1,p. 13:1–13:39, Jun. doi: https://doi.org/10.1145/2906153 .
Faniyi, F., & Bahsoon, R. (2016). A Systematic Review of Service Level Management in the Cloud. ACM Comput Surv , 48 (3), 1. doi: https://doi.org/10.1145/2843890 . 43:27, Feb
Chen, L., Lee, W. K., Chang, C. C., Choo, K. K. R., & Zhang, N. (2019). “Blockchain based searchable encryption for electronic health record sharing,” Future Gener. Comput. Syst., vol. 95, pp. 420–429, Jun. doi: https://doi.org/10.1016/j.future.2019.01.018
Zhen, P., Zhao, G., Min, L., & Li, X. (2014). “A Survey of Chaos-Based Cryptography,” in Proceedings of the 2014 Ninth International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, Washington, DC, USA, pp. 237–244. doi: https://doi.org/10.1109/3PGCIC.2014.69
Bishop, M., & Gates, C. (2008). Defining the insider threat . ACM
Li, X., Zhao, X., International Conference on Cloud Computing and, & Data, B. (“Survey on Access Control Model in Cloud Computing Environment,” in Proceedings of the 2013). Washington, DC, USA, 2013, pp. 340–345. doi: https://doi.org/10.1109/CLOUDCOM-ASIA.2013.103
Liang, X., Zhao, J., Shetty, S., Liu, J., & Li, D. (2017). “Integrating blockchain for data sharing and collaboration in mobile healthcare applications,” in 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Oct. pp. 1–5. doi: https://doi.org/10.1109/PIMRC.2017.8292361
Hammi, M. T., Hammi, B., Bellot, P., & Serhrouchni, A. (Sep. 2018). Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput Secur , 78 , 126–142. doi: https://doi.org/10.1016/j.cose.2018.06.004
Nguyen, T. D. T., Pham, H. A., & Thai, M. T. (2018). “Leveraging Blockchain to Enhance Data Privacy in IoT-Based Applications,” in Computational Data and Social Networks, Cham, pp.211–221. doi: https://doi.org/10.1007/978-3-030-04648-4_18
Sohal, A. S., Sandhu, R., Sood, S. K., & Chang, V. (May 2018). A cybersecurity framework to identify malicious edge device in fog computing and cloud-of-things environments. Comput Secur , 74 , 340–354. doi: https://doi.org/10.1016/j.cose.2017.08.016
Wang, Y. L., & Yang, S. C. (2014). “A Method of Evaluation for Insider Threat,” in 2014 International Symposium on Computer, Consumer and Control, Jun. pp. 438–441. doi: https://doi.org/10.1109/IS3C.2014.121
Sharma, P. K., Singh, S., Jeong, Y. S., & Park, J. H. (2017). “DistBlockNet: A Distributed Blockchains-Based Secure SDN Architecture for IoT Networks,” IEEE Commun. Mag., vol. 55, no. 9, pp. 78–85, Sep. doi: https://doi.org/10.1109/MCOM.2017.1700041
Dorri, A., Kanhere, S. S., & Jurdak, R. (2017). “Towards an Optimized BlockChain for IoT,” in 2017 IEEE/ACM Second International Conference on Internet-of-Things Design and Implementation (IoTDI), Apr. pp. 173–178
“BlockPro | Proceedings of the 1st Workshop on Blockchain-enabled Networked Sensor Systems (accessed Feb. 15, 2020). ” https://dl.acm.org/doi/abs/10.1145/3282278.3282281
“Healthcare Data Gateways (accessed Feb. 16, 2020). : Found Healthcare Intelligence on Blockchain with Novel Privacy Risk Control | SpringerLink.” https://link.springer.com/article/10.1007 /s10916-016-0574-6
Download references
Acknowledgements
This work is partially supported by NSF CREST Grant HRD-1736209.

Author information
Authors and affiliations.
Department of Management Information Systems, University of Montana, 59812, Missoula, MT, USA
Patricia Akello, Nicole Lang Beebe & Kim-Kwang Raymond Choo
Department of Information Systems and Cyber Security, University of Texas,, San Antonio, 78249, TX, USA
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Patricia Akello .
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Supplementary Material 1
Rights and permissions.
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Akello, P., Beebe, N.L. & Choo, KK.R. A literature survey of security issues in Cloud, Fog, and Edge IT infrastructure. Electron Commer Res (2022). https://doi.org/10.1007/s10660-022-09615-y
Download citation
Published : 18 October 2022
DOI : https://doi.org/10.1007/s10660-022-09615-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing security
- Fog Computing Security
- Edge Computing Security
- Systematic review
- Literature Survey
- Find a journal
- Publish with us
- Track your research
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Cloud Computing: Security Issues and Research Challenges

Related Papers
VIJAY GACHANDE
Blessing Mambo
IJCSMC Journal
In today’s era almost all the organizations are preferring to use cloud as their primary storage. Once the organization uploads its data to cloud, then the organization has no control over it. Then comes the security challenges in handling data to cloud service providers. While selecting a Cloud Service Provider we need to be aware about that service provider before giving our data because as from now you will not have all the control. This paper gives a better understanding on the concept of cloud computing and the risks that came up after outsourcing data handling tasks. Section 1 is Introduction, Section 2 discusses on various Service Models in Cloud Computing, Section 3 contains Cloud Deployment Models, Section 4 focuses on Security Issues and Challenges in Cloud Computing.
Kartheek D N
Jitender Grover
Cloud Computing is one of the popular techniques in distributed computing due to its ability to minimize the cost of computing when scalability and flexibility of computer process get increased. Cloud Computing provides shared resources and services via internet. Services are delivered through data center. Cloud Computing allows an interesting business proposal for IT industries to provide IT services without any extra investment. Client is able to perform heavy computer processes with low capable device (like mobile) which has resource to run the web browser. But cloud computing is crowded with many security related issues. When client saves his data to the company’s cloud, there may be chance of data breaching. So the purpose of this paper is to search out various issues in cloud computing where all computing is done on the server side and both data & tasks are stored on the data centers.
Innovative Research Publications
Victor Ginsburgh
Comptes Rendus De L Academie Des Sciences Serie Ii Fascicule B-mecanique Physique Astronomie - C R ACAD SCI SER II B
Frédéric Reverdy
Acoustic waves propagate at group velocity which is, for anisotropic media, different of phase velocity. When acoustic waves are generated by laser impact, the complex shape of the ray curve makes the interpretation of the signals obtained after propagation through this kind of media difficult. In order to avoid such difficulties, a method is presented which allows the synthesis of acoustical plane wavefronts for which the phase velocity is easily accessible, using signals obtained for various source-detector positions.
Eugeniusz Koda
Dendri Lusi
Hanya oleh karena anugerah Tuhan, sehingga kita boleh layak dihadapan-Nya
RELATED PAPERS
2021 IEEE International Symposium on Information Theory (ISIT)
Mahdi Cheraghchi
Catherine Dargemont
M.C. Cabrera
Indian Journal of Science and Technology
Lowell Quisumbing
2015 7th International IEEE/EMBS Conference on Neural Engineering (NER)
Journal of Investigative Dermatology
Journal of Applied Physics
Thierry de LAROCHELAMBERT
Rafael Guerrero
Alexandre Cozer
BMJ case reports
Hemant Kumar
Higher Education in Portugal 1974-2009
Maria E Gonçalves
A publication of school of Arts and social sciences , College of Education, Agbor
Agidi Pally
kedar Sharma
The International Spectator
Stimmen der Zeit
Ingeborg Gabriel
Revista Latinoamericana De Psicopatologia Fundamental
Doris Luz Rinaldi
BMC Nursing
peter palamara
F1000Research
GUSTAVO BEOJONE MESSI
International Journal of Speech Technology
Dominique Estival
The Astrophysical Journal
H. Kjeldsen
hbgjfgf hyetgwerf
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

IMAGES
VIDEO
COMMENTS
Cloud computing has become a widely exploited research area in academia and industry. Cloud computing benefits both cloud services providers (CSPs) and consumers. The security challenges associated with cloud computing have been widely studied in the literature. This systematic literature review (SLR) is aimed to review the existing research studies on cloud computing security, threats, and ...
This research report systematically investigates various challenges and vulnerabilities in cloud computing, focusing on security and privacy issues. This study comprehensively examines potential ...
associated with cloud computing have been widely studied in the literature. This systematic literature. review (SLR) is aimed to re view the existing research studies on cloud computing security ...
Security issues is one of t he biggest concerns that has bee n. affecting the gro wth of cloud computing .It adds complications with d ata privac y and data protection continues. to affect the mar ...
7.1. Challenges. Via analysis and contrast, we observe that cloud computing security protection work has achieved satisfactory research results. However, many problems remain, which prompt the consideration of a variety of security factors and continuous improvements in defense technology and security strategies. 1.
This research paper outlines what cloud computing is, the various cloud models and the main security risks and issues that are currently present within the cloud computing industry and offers best practices to service providers as well as enterprises hoping to leverage cloud service to improve their bottom line in this severe economic climate.
Cloud computing has gained huge attention over the past decades because of continuously increasing demands. There are several advantages to organizations moving toward cloud-based data storage solutions. These include simplified IT infrastructure and management, remote access from effectively anywhere in the world with a stable Internet connection and the cost efficiencies that cloud computing ...
gained from the cloud computing model, the model still has a lot of open issues that impact the model creditability and pervasiveness. Vendor lock -in, multitenancy and isolation, data management, service portability, elasticity engines, SLA management, and cloud security are well known open research problems in the cloud computing model.
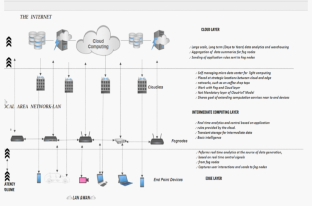
Cloud model. Later, we will analyze the security issues in Cloud Computing identifying the main vulnerabilities for clouds, the most important threats in clouds, and all available countermeasures for these threats and vulner-abilities. Finally, we provide some conclusions. 1.1 Systematic review of security issues for cloud computing
Section 3 discussed a brief overview of existing survey papers about cloud computing and its security concerns. The design and service models of cloud computing are explained in Sect. 4. Cloud computing threats are categorized and discussed in Sect. 5. Section 6 explained the threats and security risks related to cloud computing.
Issues related to cloud computing, including complications with data privacy and data protection continues to affect the market, are highlighted. Cloud computing has become one of the most interesting topics in the IT world today. Cloud model of computing as a resource has changed the landscape of computing as it promises of increased greater reliability, massive scalability, and decreased ...
The 2023 Cloud Security Report highlights the critical cybersecurity concerns, incidents, and ... These findings indicate a growing recognition of the bene fits of cloud computing, leading ... (37%). This is followed by legal and regulatory compliance issues (30%) and data security and leakage risks (29%). To overcome these barriers ...
access and storage of data. Several issues are there related to cloud security as: vendor lock-in, multi-tenancy, loss of control, service disruption, data loss etc. are some of the research problems in cloud computing [2]. In this paper we analyze the security issues related to cloud computing model.
adoption of cloud computing securi ty factor plays a. key role to the user's perspective [8], be cause of. following reasons: Loss of control [9] - transfers the security. management to third ...
This paper focuses on the deployment model of cloud which consists of private cloud, public cloud, hybrid cloud, community cloud .This paper also focuses on architectural components of cloud which consists of Saas, Paas, Iaas. This paper also focuses on security issues and security challenges. Download Free PDF.
This research paper outlines what cloud computing is, the various cloud models and the main security risks and issues that are currently present within the cloud computing industry and offers best practices to service providers as well as enterprises hoping to leverage cloud service to improve their bottom line in this severe economic climate.
occupancy security issue. Keywords: Cloud Computing, Cloud security, Distributed Computing, Framework 1. INTRODUCTION Cloud computing is an appropriate design which concentrates server assets on a versatile stage in order to give on request figuring assets and administrations.
This paper reviews the cloud security issues and concerns , while addressing various key topics like vulnerabilities, threats and mitigations, and cloud models. Architectural framework of Cloud ...
Increasing complexity in and interconnectivity between technologies and systems (e.g., cloud computing, Internet of Things (IoT), fog and edge computing) can complicate data processing and security requirements. Thus, in this paper we review existing literature survey articles focusing on cloud, fog and edge computing platforms and infrastructures. We then present the result of a systematic ...
f [email protected]. du.sa. ABSTRACT. Cloud computing has drawn attention in the current. technological world due to its many benefits in contrast to. traditional information technology (IT ...
This paper gives a better understanding on the concept of cloud computing and the risks that came up after outsourcing data handling tasks. Section 1 is Introduction, Section 2 discusses on various Service Models in Cloud Computing, Section 3 contains Cloud Deployment Models, Section 4 focuses on Security Issues and Challenges in Cloud Computing.
This research paper aims to provide a comprehensive comparison of cloud security issues, examining the common threats, vulnerabilities, and mitigation strategies across various cloud deployment ...