This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Back up files and directories - security policy setting
- 1 contributor
- Windows 11
- Windows 10
This article describes the recommended practices, location, values, policy management, and security considerations for the Back up files and directories security policy setting.
This user right determines which users can bypass file and directory, registry, and other persistent object permissions for the purposes of backing up the system. This user right is effective only when an application attempts access through the NTFS backup application programming interface (API) through a tool such as NTBACKUP.EXE. Otherwise, standard file and directory permissions apply.
This user right is similar to granting the following permissions to the user or group you selected on all files and folders on the system:
- Traverse Folder/Execute File
- List Folder/Read Data
- Read Attributes
- Read Extended Attributes
- Read Permissions
Default on workstations and servers:
- Administrators
- Backup Operators
Default on domain controllers:
- Server Operators
Constant: SeBackupPrivilege
Possible values
- User-defined list of accounts
- Not Defined
Best practices
- Restrict the Back up files and directories user right to members of the IT team who must back up organizational data as part of their daily job responsibilities. Because there's no way to be sure that a user is backing up data, stealing data, or copying data to be distributed, only assign this user right to trusted users.
- If your backup software runs under specific service accounts, only these accounts (and not the IT staff) should have the user right to back up files and directories.
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Default values
By default, this right is granted to Administrators and Backup Operators on workstations and servers. On domain controllers, Administrators, Backup Operators, and Server Operators have this right.
The following table lists the actual and effective default policy values for the server type or Group Policy Object (GPO). Default values are also listed on the policy’s property page.
Policy management
A restart of the device isn't required for this policy setting to be effective.
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Group Policy
Settings are applied in the following order through a GPO, which will overwrite settings on the local computer at the next Group Policy update:
- Local policy settings
- Site policy settings
- Domain policy settings
- OU policy settings
When a local setting is greyed out, it indicates that a GPO currently controls that setting.
Security considerations
This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Vulnerability
Users who can back up data from a device to separate media could take the media to a non-domain computer on which they have administrative privileges, and then restore the data. They could take ownership of the files and view any unencrypted data that is contained within the data set.
Countermeasure
Restrict the Back up files and directories user right to members of the IT team who must back up organizational data as part of their daily job responsibilities. If you use software that backs up data under specific service accounts, only these accounts (and not the IT staff) should have the right to back up files and directories.
Potential impact
Changes in the membership of the groups that have the user right to back up files and directories could limit the abilities of users who are assigned to specific administrative roles in your environment. Confirm that authorized administrators can still back up files and directories.
Related topics
- User Rights Assignment
Additional resources
WinSecWiki > Security Settings > Local Policies > User Rights > User Rights In-Depth > Backup Files & Directories
Back up files and directories
Note: This is an admin-equivalent right.
AKA: SeBackupPrivilege, Back up files and directories
Default assignment: Administrators and Backup Operators This right allows you access any persistent object (file, folder, registry key, et al) on the computer using the Win32 backup APIs. This is equivalent, from a security perspective, to giving the user the Read permission group to all objects on the entire system. Typically only backup application/service accounts need this right. There are occasional non-backup operations that an administrator might perform that would require this right. If you are directly running NTBackup under your account you will need this right.
Arne Vidstrom shows how you can use this right to make copies of objects to which you have no permissions. Click here.
The opposite of this right is the Restore files and directories right.
By default this right is not audited even if you enable Audit privilege use . See Full Privilege Auditing .
Back to top

Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

Windows Backup Operators group for family edition
On Windows pro versions, there is a "Backup Operators" group allowing to access every files for backup purposes.
On Windows 10 family I don't see this group (with the commande net localgroup ). I want to create a user dedicated to automated backups. But without this group the user can't backup files located in other's users home (which is the desired behaviour, even if the backup user is administrator).
There is probably a way to achieve this goal, because commercial backup softwares do it. Anyone has an idea?
- user-groups
- Have you given the backup user permission on the other user's home? – harrymc May 13, 2018 at 19:57
2 Answers 2
The simplest way to accomplish what you want is to make the backup process run as an administrator. Administrators have full access to all users' profile folders, but they must run elevated for this access control entry to apply.
If you can't run the backup elevated, make the backup user an administrator, log on as it, and try to navigate into other users' profile folders. Windows Explorer will inform you that access is denied, but it will give you a button that permanently grants the current user access to that folder. After that's done, the backup user will be able to access that other user's profile even without elevation.
Information on how to replicate the effect of the Backup Operators group follows below the line.
Much of what makes the Backup Operators group special is that, by default, it is granted a handful of privileges :
- SeBackupPrivilege , "back up files and directories"
- SeRestorePrivilege , "restore files and directories"
- SeShutdownPrivilege , "shut down the system"
- SeBatchLogonRight , "log on as a batch job"
Privileges can be assigned using the User Rights Assignment section of the Local Security Policy tool, secpol.msc . That tool might not exist on non-Pro editions of Windows, though. To adjust privileges on other editions, you can use the NTRights utility from the Windows Server 2003 Resource Kit . Despite the name, that kit can be installed on any modern version of Windows. You can use NTRights to grant a privilege by opening an administrative command prompt and running a command like this:
Replace YourBackupUser with the SAM account name of the user/group who should be able to back up and restore — the SAM account names are listed in the output of net user or net localgroup (ignore the asterisk before the group name). Replace SeSomePrivilege with the ID of the privilege to grant. If you want to revoke a privilege later, run the same command but with -r instead of +r .
Note, though, that only specially written software will be able to take advantage of these privileges. Even when granted, privileges must be enabled per process before they take effect, then the program must call special read/write APIs that bypass security checks. These privileges are also insufficient for creating shadow copies; to do that, a process must be running as a member of the Administrators group — even membership in the real Backup Operators group isn't enough for that.
- For Robocopy to work with the /B flag, you need all four of those rights. This lets me run /B on Win 10 Home. It won't work with just SeBackupPrivilege. – Jacob Bruinsma Jul 12, 2022 at 13:53
(Sorry, I don't have enough rep to make this a comment to @Ben N's response.)
Yes, adding SeBackupPrivilege , etc to a regular account is sufficient to use the FILE_FLAG_BACKUP_SEMANTICS flag to CreateFile and to use the BackupRead API call.
BUT it's not sufficient to take a VSS snapshot (something that a backup program would like to do).
To take a VSS snapshot, the user must either be
- Local System, or
- Local Service / Network Service (Server 2003 or later), or
- A member of the local Administrators group, or
- A member of the local Backup Operators group, or
- Have the program whitelisted in the registry in a certain way (although this didn't work in my testing).
- Nice catch! I suspect that fiddling with the DCOM configuration might allow the user to use the Volume Shadow Copy Service - I'll do some testing and update my answer if I find anything useful. – Ben N Jul 19, 2018 at 1:41
- Hmm, it looks like even being an elevated member of Backup Operators is insufficient to create shadow copies. Trying this code on a Pro machine as a backup operator doesn't produce an initialization error like by a normal user, but the $s1 response object indicates an access-denied error ( ReturnValue 1) and no shadow copy is created. I did some Registry shenanigans to create the real Backup Operators group on a Home edition and got the same effect there. – Ben N Jul 19, 2018 at 23:15
- (The downvote isn't mine, FWIW.) – Ben N Jul 19, 2018 at 23:59
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged windows-10 backup user-groups ..
- The Overflow Blog
- Between hyper-focus and burnout: Developing with ADHD
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- Series connection of diode and resistor. Why is there a constant voltage across the diode?
- Could Android go on PC?
- Advice on designing an inconsistent magic system
- Where is the mistake in the argument in favor of the (erroneous) claim "every Dedekind cut is a rational cut"?
- Customized equation referencing
- Strange behavior of `Subdivide`
- Can I swap a gravel wheel with 1x10 cassette for a new road wheel with 1x12?
- How far can you push Object Oriented Programming?
- How do couples "do it" on starships?
- What is the maximum contribution allowed to my HSA if my husband is enrolled in a PPO plan, while both my child and I are enrolled in a CDHP/HSA plan?
- Efficient C Tokenizer/Lexer in C++
- On Pareto functions
- Could a small (15km radius) planet (disregarding physics) have enough material for intelligient life to build on?
- Will Some Coal Burn at the Molecular Level at Room Temperature?
- Calculating engine air intake per minute
- How to make a call out after every DML in batch
- Geometry Node Socket Colors have Changed in V4.1. What does this signify?
- Extrude function not working right
- Using Mars inner moon Phobos as a brake
- Is it a bad idea to design a purposefully inconsistent magic system?
- Can I travel to the UK with a child accompanied visa without the adult named on my visa but with the consent from that adult to another adult?
- Shortest battleship game, to find number of battleships
- Short story in which humans are the first stage in a metamorphic cycle that advances when eating a particular substance?
- How many rolls are sufficient to ensure, with probability 99%, that the sum is greater than 100?
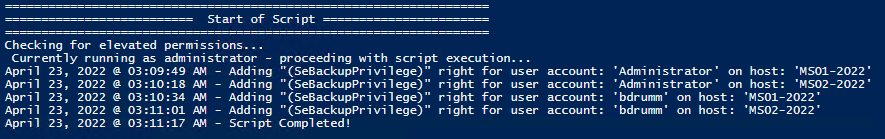
Set and Check User Rights Assignment via Powershell
You can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts..
Posted by : blakedrumm on Jan 5, 2022
Local Computer
Remote computer, output types.
This post was last updated on August 29th, 2022
I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights.
Set User Rights
How to get it.
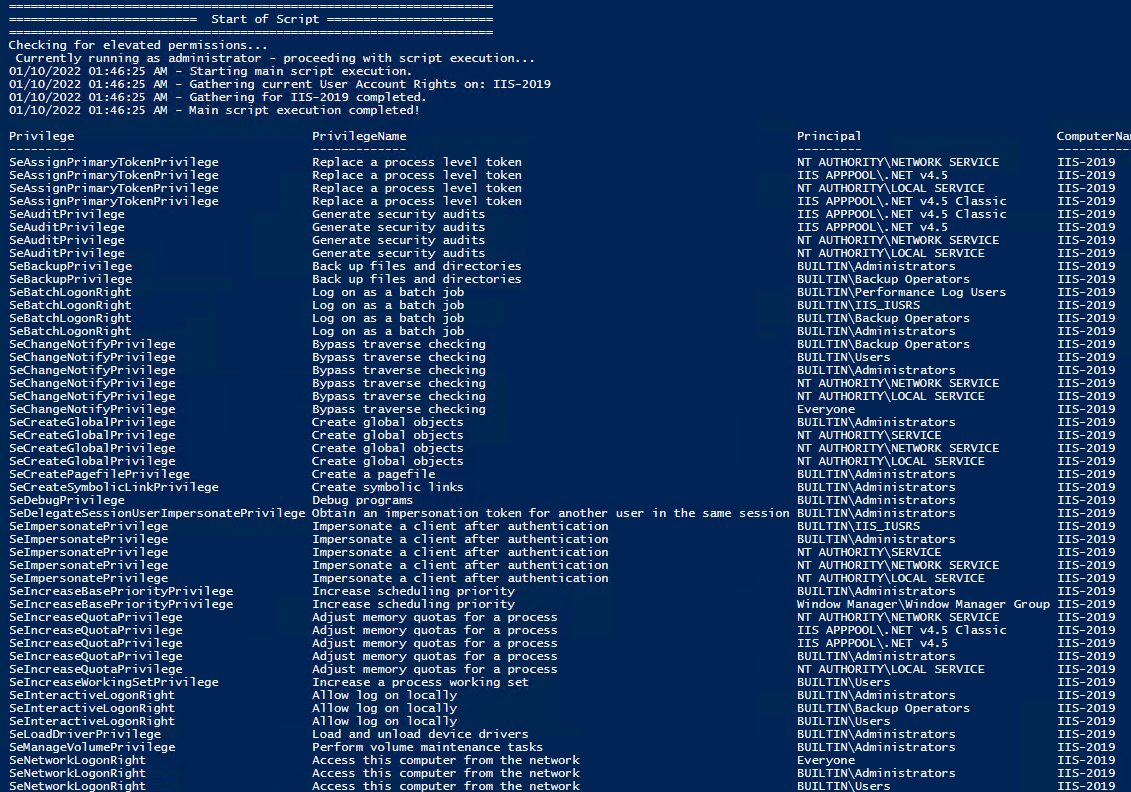
All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Here are a few examples:
Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Check User Rights
In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Get Local User Account Rights and output to text in console:
Get Remote SQL Server User Account Rights:
Get Local Machine and SQL Server User Account Rights:
Output Local User Rights on Local Machine as CSV in ‘C:\Temp’:
Output to Text in ‘C:\Temp’:
PassThru object to allow manipulation / filtering:
I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs.
Email : [email protected]
Website : https://blakedrumm.com
My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
- operationsManager
- troubleshooting
- certificates
User Rights and Privileges
User rights grant specific privileges and logon rights to users and groups in your computing environment. Administrators can assign specific rights to group accounts or to individual user accounts. These rights authorize users to perform specific actions, such as logging on to a system interactively or backing up files and directories.
To ease the task of user account administration, you should assign privileges primarily to group accounts, rather than to individual user accounts. When you assign privileges to a group account, users are automatically assigned those privileges when they become a member of that group. This method of administering privileges is far easier than assigning individual privileges to each user account when the account is created.
The following table lists and describes the privileges that can be granted to a user.
Some privileges can override permissions set on an object. For example, a user logged on to a domain account as a member of the Backup Operators group has the right to perform backup operations for all domain servers. However, this requires the ability to read all files on those servers, even files on which their owners have set permissions that explicitly deny access to all users, including members of the Backup Operators group. A user right—in this case, the right to perform a backup—takes precedence over all file and directory permissions. For more information, see Backup and Recovery (https://go.microsoft.com/fwlink/?LinkID=131606).
Table Of Contents
- Access Control Overview
- Checklist: Setting Access Controls on Objects
- What Are Permissions?
- File and Folder Permissions
- Share and NTFS Permissions on a File Server
- Inherited Permissions
- How Effective Permissions Are Determined
- Determine Where to Apply Permissions
- Set, View, Change, or Remove Permissions on Files and Folders
- View Effective Permissions on Files and Folders
- Set, View, Change, or Remove Special Permissions
- Set Permissions on a Shared Resource
- Take Ownership of a File or Folder
- Audit Policies
- Define or Modify Auditing Policy Settings for an Event Category
- Apply or Modify Auditing Policy Settings for a Local File or Folder
- View the Security Log
- Understanding User Account Control
- Resources for Access Control
- Security Settings Property Page
- Select Users, Computers, or Groups Dialog Box
- Object Types Dialog Box
- Select Users, Computers, or Groups Dialog Box - Advanced Page
- Permission Entry Dialog Box
- Advanced Security Settings Properties Page - Auditing Tab
- Advanced Security Settings Properties Page - Owner Tab
- Advanced Security Settings Properties Page - Permissions Tab
- Auditing Entry Dialog Box
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
What is the relationship between User Rights Assignment Policies vs. Membership of Local Groups
I just spent the better part of this morning on a support call with a vendor where we eventually resolved our issue by manually adding the service account their application was using to the following Computer Configuration/Policies/Windows Settings/Security Settings/Local Policies/User Rights Assignment policies which were being set by a Domain GPO:
- Back up files and directories
- Log on as a batch job
- Restore files and directories
After rebooting the server and getting the updated GPO our service account no longer generated the following Event 4625 - Logon Type 4 audit events when attempting to start the application:
The vendor's documentation instructed us to add the service account to the Backup Operators and Power User Local Groups - which we did. Reading the Explain tab for each one of the required User Right Assignment policies indicates that the Backup Operators have those Rights by default (TechNet seems to confirm this ). Incidentally, there's no mention of Power User being assigned those Rights that I can find so I'm not really sure why that was a requirement.
Why did we have to explicitly assign that service account those Rights ( Back up files and directories , Log on as a batch job , Restore files and directories ) when it already should of had them by virtue of being a member of the Backup Operators Local Group?
What is the relation between the User Rights Policies and the builtin Local Groups? Are User Rights Polices the constituent parts that make up the "meta"-rights of each builtin Local Groups? If so, where can I find which Rights belong to which bultin Local Groups?
As stated we resolved this issue by adding our service account to the Group Policy Object that is manually assigning a number of service accounts these specific Rights. I got the sense from the vendor's engineer that this GPO is interfering with the mapping of these constituent Rights to Local Groups. Is this hunch correct? Is assigning constituent User Rights this way a Bad Idea (TM)?
- windows-server-2008-r2
- group-policy
- windows-authentication
Members of local built-in groups (as well as domain groups) have whatever rights are assigned to the group. The default rights on a server for local built-in groups are set in the local security settings. To access the local security settings, click Start, type secpol.msc and hit enter. In the Local Security Policy editor, expand Local Policies, and click on User Rights Assignment. There you will see what groups/users are granted which rights.
The local User Rights Assignment settings can be overriden by domain group policy. If you create a domain group policy that grants certain groups/users a certain right, such as "Logon as a batch job", this will override the local policy for which users have that right.
From what you have written, here is what I am guessing happened: You had a GPO in your domain that granted certain users the rights that you mentioned. This policy did not grant these rights to local machine Backup Operators group. This policy overwrote the default policy on the server. Thus, adding the user to the Backup Operators group did not give them those rights because, due to the Domain GPO, the Backup Operators do not have them.
As to whether or not the vendor's solution is a good idea: I have found that it is usually easier to manage rights by using well-organized groups rather than granting them to individual accounts. This way, when you add a new user, you add the user to the logical groups to which he belongs, and he will immediately have all of the rights he needs rather than having to assign him each right one-by-one. That is what the Built-in groups were intended to do.
Instead of granting those three rights to an individual user, you could have granted the "Backup Operators" group those three rights in the GPO. Then adding the user to that group would have the intended effect.
I am curious why you would have a domain policy managing those rights in the first place. If the purpose was to grant certain users access to perform backup operations, it might have been a better idea to use the domain built-in Backup Operators group.
You must log in to answer this question.
- The Overflow Blog
- Between hyper-focus and burnout: Developing with ADHD
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- Which cognitive psychology findings are solid, that I can use to help my students?
- If the Earth stopped spinning, what's the ideal point for it to stop to ensure the most people survive?
- Is the largest root of a random polynomial more likely to be real than complex?
- Which formula do I use when calculating finite geometric series?
- When is it worthwhile to report academic misconduct of a referee?
- What's the story behind the "mysterious" 486DX3?
- how to replace the last n occurences of string using sed
- Whatd does 気づいたら at the end of a setnence alone mean?
- How can I determine whether a food or ingredient is "ultraprocessed"?
- Can I swap a gravel wheel with 1x10 cassette for a new road wheel with 1x12?
- How did White lose all their pieces?
- Can I travel to the UK with a child accompanied visa without the adult named on my visa but with the consent from that adult to another adult?
- Golfing the complexity with subtraction
- Shortest battleship game, to find number of battleships
- Advice on designing an inconsistent magic system
- Customized equation referencing
- When in Rome... – a deconstruction sudoku
- What major advances in theoretical and computational chemistry have been made in recent decades?
- In OOP, what counts as a "getter"
- Meaning of gold border around Steam achievement
- Using WiFi and Ethernet for same LAN at the same time, resolver issue
- Official draw rules in the game of American checkers
- Efficient C Tokenizer/Lexer in C++
- Java interpreter

- NIST 800-53
- Common Controls Hub
The Back up files and directories user right must only be assigned to the Administrators group.

IMAGES
VIDEO
COMMENTS
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. ... Restrict the Back up files and directories user right to members of the IT team who must back up organizational data as part of their daily job responsibilities. If you use software that backs up data under specific ...
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any groups or accounts other than the following are granted the "Back up files and directories" user right, this is a finding: Administrators. Fix Text (F-69781r1_fix)
User rights assignments are settings applied to the local device. They allow users to perform various system tasks, such as local logon, remote logon, accessing the server from network, shutting down the server, and so on. ... Back up files and directories: Administrators. This is a sensitive privilege that allows a user to bypass NTFS ...
AKA: SeBackupPrivilege, Back up files and directories. Default assignment: Administrators and Backup Operators This right allows you access any persistent object (file, folder, registry key, et al) on the computer using the Win32 backup APIs. This is equivalent, from a security perspective, to giving the user the Read permission group to all ...
Much of what makes the Backup Operators group special is that, by default, it is granted a handful of privileges:. SeBackupPrivilege, "back up files and directories"; SeRestorePrivilege, "restore files and directories"; SeShutdownPrivilege, "shut down the system"; SeBatchLogonRight, "log on as a batch job"; Privileges can be assigned using the User Rights Assignment section of the Local ...
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
Accounts with the "Back up files and directories" user right can circumvent file and directory permissions and could allow access to sensitive data." ... Configure the policy value for Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment >> "Back up files and directories" to only include ...
Back up files and directories. Determines which users can bypass file and directory, registry, and other persistent object permissions for the purposes of backing up the system. Administrators and Backup Operators. Bypass traverse checking. Determines which users can traverse directory trees even though the user may not have permissions on the ...
From the left pane, expand Computer Configuration and go to Policies | Windows Settings | Security Settings | Local Policies | User Rights Assignments. 5. From the right pane, right-click Log on as a batch Job --> Properties. 6. Click Add user or Group. 7. For the Add user or Group window, click Browse.
Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups other than the following are granted the "Back up files and directories" user right, this is a finding: - Administrators For server core installations, run the following command:
Back up files and directories; Log on as a batch job; ... In the Local Security Policy editor, expand Local Policies, and click on User Rights Assignment. There you will see what groups/users are granted which rights. The local User Rights Assignment settings can be overriden by domain group policy. If you create a domain group policy that ...
Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any groups or accounts other than the following are granted the "Restore files and directories" user right, this is a finding: Administrators. Fix Text (F-69867r1_fix)
Under Security Settings, select Local Policies -> User Rights Assignment: Select Back up files and directories and Restore files and directories: Make sure the policy is set to the Administrators group. In case the policy is not set to the Administrators group: Double-click on the policy. Click on Add User or a Group:
This policy setting allows users to circumvent file and directory permissions to back up the system. This user right is enabled only when an application (such as NTBACKUP) attempts to access a file or directory through the NTFS file system backup application programming interface (API). Otherwise, the assigned file and directory permissions ...
Directions: Local policy: On the local machine Press the Windows logo key + R to open the RUN dialogue. Type gpedit.msc in the text box, and then click OK or press ENTER. Browse to "\Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment" and add the user to each policy listed above.
Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups other than the following are granted the "Back up files and directories" user right, this is a finding. - Administrators.