Set and Check User Rights Assignment via Powershell
You can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts..
Posted by : blakedrumm on Jan 5, 2022
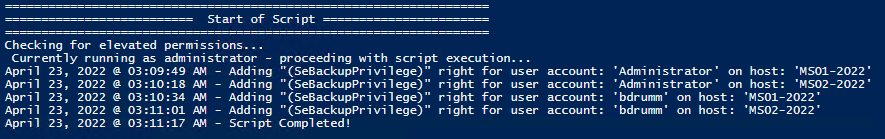

Local Computer
Remote computer, output types.
This post was last updated on August 29th, 2022
I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights.
Set User Rights
How to get it.
All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Here are a few examples:
Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Check User Rights
In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
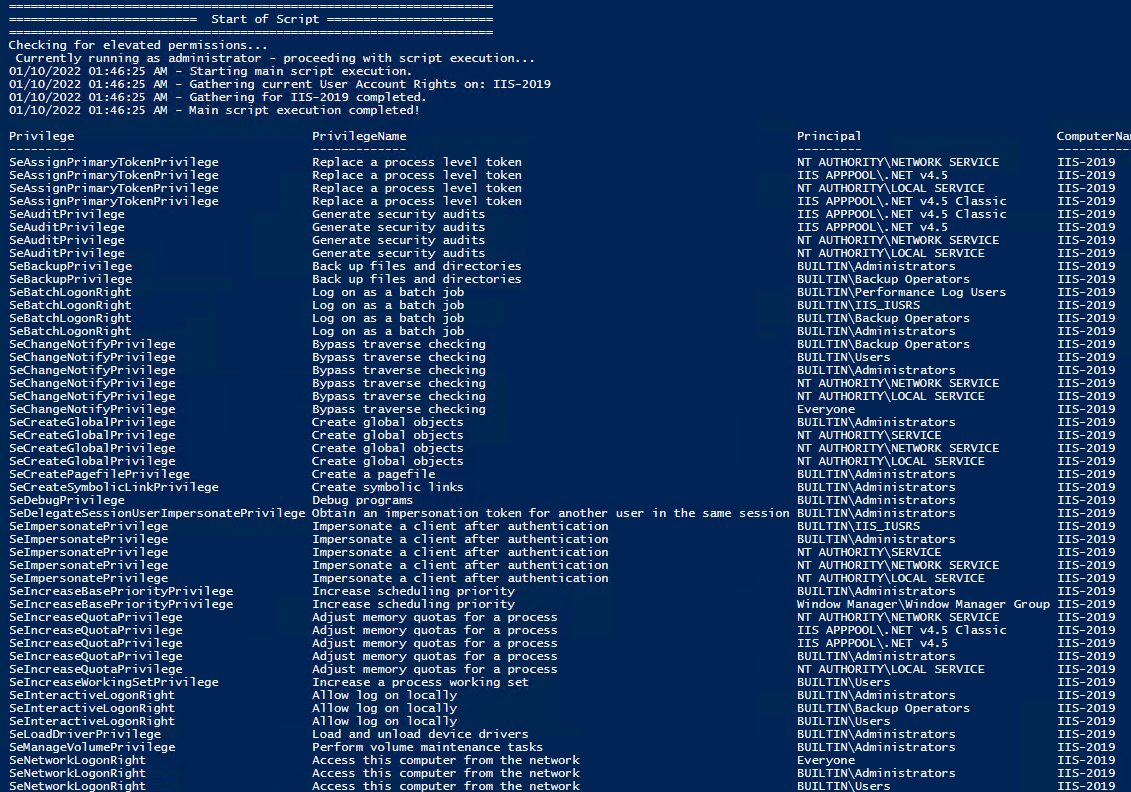
Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Get Local User Account Rights and output to text in console:
Get Remote SQL Server User Account Rights:
Get Local Machine and SQL Server User Account Rights:
Output Local User Rights on Local Machine as CSV in ‘C:\Temp’:
Output to Text in ‘C:\Temp’:
PassThru object to allow manipulation / filtering:
I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs.
Email : [email protected]
Website : https://blakedrumm.com
My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
- operationsManager
- troubleshooting
- certificates
ECS.LocalGPO
Functions/get-ecslocalgpouserrightassignment.ps1.

- PowerShell Forum Directory
- Publications
Managing Privileges using PoshPrivilege
A recent project of mine has been to write a module to manage privileges on a local system. What I came up is a module called PoshPrivilege that allows you to not only look at what user rights are available on a local or remote system, but also provide the ability to Add, Remove, Enable and Disable the privileges as well.
If you are running PowerShell V5, you can download this module from the PowerShell Gallery:
Otherwise, check out my GitHub page where I am maintaining this project:
https://github.com/proxb/PoshPrivilege
I won’t spend time talking about how I wrote this module and my reasons behind it. What I will say is that instead of writing out C# code and then using Add-Type to compile it, I went with the Reflection approach of building out everything from the pinvoke signatures for methods to the Structs and even the Enums.
Let’s get started by looking at what is available in this module. The first function that is available is Get-Privilege and it comes with a few parameters. This function’s purpose is to let you view what privileges are currently available on the system (local or remote) as well as what is currently applied to your current process token.

A quick run through of using this function with various parameters:

If this one looks familiar, then it is probably likely that you have used the following command:

I opted for boolean values instead to determine the state for easier filtering if needed.
Up next are the Enable/Disable-Privilege functions. These work to Enable or Disable the privileges that are currently available on your local system to your process token. This means that if something like SeDebugPrivilege isn’t available on your system (such as being removed via Group Policy), then you cannot use Enable-Privilege to add your process token to this privilege. As in the previous image where we can see what is enabled and disabled, these are the only privileges that are available for me to work with.
To show this point, I am going to enable both SeSecurityPrivilege and SeDebugPrivilege so you can see that while the first privilege will show as Enabled, the other will not appear as it has not been made available.

As you can see from the picture, SeSecurityPrivilege has been enabled as expected, but SeDebugPrivilege is nowhere to be found. If we want SeDebugPrivilege, we will need to go about this another way which will be shown shortly.
Disabling a privilege can be done using Disable-Privilege as shown in the example below.

Now that I have covered Enabling and Disabling of the privileges and their limitations, I will move onto the Add/Remove-Privilege functions which allow you to add a privilege for a user or group or remove them on a local system. Note that this only works up until it gets reverted if set by group policy. This will also note show up if you look at the privileges available on your current process token (you will log off and log back in to see it).
Remember that I do not have SeDebugPrivilege available to use? Well, now we can add it to my own account using Add-Privilege.

We can see it is now available, but as I mentioned before, it doesn’t show up in my current process. A logoff and login now shows that it is not only available, but already enabled.

With this now enabled, we could disable it as well if needed using Disable-Privilege. I added my account for show, but we can also add groups this was as well.
As with Adding a privilege, we can remove privileges as well using Remove-Privilege.

As with Add-Privilege, you will need to log off and log back in to see the change take effect on your account.
Again, you can install this module using Install-Module if running PowerShell V5 and this project is out on GitHub to download (and contribute to as well). Enjoy!
Share this:
4 responses to managing privileges using poshprivilege.
I downloaded the scripts from Github, but getting compile errors.
Specifically the errors are around the WInOS Structures listed below:
Unable to find type [LUID]: make sure that the assembly containing this type is loaded. Unable to find type [LSA_UNICODE_STRING]: make sure that the assembly containing this type is loaded. Unable to find type [LARGE_INTEGER]: make sure that the assembly containing this type is loaded. Unable to find type [LUID_AND_ATTRIBUTES]: make sure that the assembly containing this type is loaded. Unable to find type [TokPriv1Luid]: make sure that the assembly containing this type is loaded.
Unable to find type [TOKEN_INFORMATION_CLASS]: make sure that the assembly containing this type is loaded.
Unable to find type [ProcessAccessFlags]: make sure that the assembly containing this type is loaded.
BTW, I have posted the full error log @ https://docs.google.com/document/d/18boeWSbvlLwpoIAMTJAp0ooNaLxe6kniYrJr_q3ZNMQ/edit?usp=sharing
Just a question, how can I grant the SESecurityPrivilege to the Set-Acl process ? If I do a whoami /priv I can see my useraccount (PS –> run as administrator) I can see the privilege is enabled, but when I try to run the script I have I get the following error :
Set-Acl : The process does not possess the ‘SeSecurityPrivilege’ privilege which is required for this operation. At C:\Scripts\SESOG\ImportACLSEv2.ps1:16 char:16 + $acl | Set-Acl $path + ~~~~~~~~~~~~~ + CategoryInfo : PermissionDenied: (P:\Common:String) [Set-Acl], PrivilegeNotHeldException + FullyQualifiedErrorId : System.Security.AccessControl.PrivilegeNotHeldException,Microsoft.PowerShell.Commands.SetAclCommand
The script looks like this : $par = Import-Csv -Path “c:\scripts\sesog\ImportMainCC.csv” -Delimiter “;”
foreach ( $i in $par ) { $path= $i.Path $IdentityReference= $i.IdentityReference $AccessControlType=$i.AccessControlType $InheritanceFlags= $i.InheritanceFlags $PropagationFlags=$i.PropagationFlags $FileSystemRights=$i.FileSystemRights echo $path $IdentityReference $acl = Get-Acl $path $permission = $IdentityReference, $FileSystemRights, $InheritanceFlags, $PropagationFlags, $AccessControlType $accessRule = new-object System.Security.AccessControl.FileSystemAccessRule $permission $acl.SetAccessRule($accessRule) $acl | Set-Acl $path }
In the import csv a path is set and exported export rights from the original location (I am doing a fileserver migration) but on each of the folders mentioned the inherentance flag has been removed.
Pingback: PowerShell Magazine » The case of potentially broken PackageManagement for Windows 10 Insiders
You are a lifesaver! I have been fretting over how to manage service account rights on remote servers – each OU has a corresponding AD security group and GPO, and doing this manually is both time-consuming and fraught with error. I can’t wait to try this out. First PoshWSUS, then this …you rock.
Leave a comment Cancel reply
Translate this blog.
- Search for:
Recent Posts
- Dealing with Runspacepool Variable Scope Creep in PowerShell
- 2018 PowerShell Resolutions
- Quick Hits: Getting the Local Computer Name
- Recent Articles on MCPMag
- Quick Hits: Finding all Hyperlinks in an Excel Workbook
- Querying UDP Ports with PowerShell
- Changing Ownership of File or Folder Using PowerShell
- Fix Duplicate WSUS ClientIDs Using PowerShell
- Locating Mount Points Using PowerShell
- Using PowerShell Parameter Validation to Make Your Day Easier
- PowerShell and Excel: Adding Some Formatting To Your Report
- Starting,Stopping and Restarting Remote Services with PowerShell
- Sharing Variables and Live Objects Between PowerShell Runspaces
- Use PowerCLI to Report Storage Paths in your ESXi Environment
- Quick Hits: Finding Exception Types with PowerShell
- background jobs
- Internet Explorer
- performance
- powerscripting
- Regular Expressions
- scripting games 2012
- scripting games 2013
- scripting guy
- winter scriting games 2014
Email Subscription
Enter your email address to subscribe to this blog and receive notifications of new posts by email.
Email Address:
Sign me up!
- 5,542,082 Visitors Since August 5, 2010
- Entries feed
- Comments feed
- WordPress.com

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar

Managing User Rights in Powershell
Managing User Rights Assignments in Powershell
Windows User Rights, also known as Windows Privileges, are traditionally managed via GPO or in the simplest of cases via the server’s Local Security Policy. These assignments control special permissions that are often needed by IIS applications or other application hosting on Windows Servers.
So how can we manage these assignments in Powershell? There’s no obvious solution provided in Powershell, but there are several options are available. None of which are a pure Powershell solution, but some are close.
- Wrap the ntrights.exe process in Powershell. This is relatively simple, but the downside is having an external dependency on the ntrights.exe file.
- Embed a wrapper class to the LSA API in your script. This is a pretty good solution but certainly bloats your script.
- Load and Reference the Carbon DLL (If you haven’t already checked out this Powershell library, you should it is very powerful and regularly updated. I choose this approach because it keeps the script clean and compact, it returns an array of strings for easy interrogation. It does require a dependency on carbon.dll, but this library provides a ton of functionality beyond just this.
I like the 3rd option, its very clean, and I like working with the Carbon library.
Now lets take this script to the next level and wrap it into a DSC Script implementation. We can use this same logic in a DSC configuration to make sure our desired User Rights Assignments are kept in place.
What else can we do? We could also create a Custom DSC Resource to have a cleaner DSC Configuration.
Related Posts

Local Administrator Audit Script

Powershell Log Archival Script
My new stories.


Set Allow Log On Locally User Rights via Powershell, C# and CMD
Description:.
In this article, I am going to explain about how to set or configure Allow Log on Locally User rights/permission/privilege using Local Security Policy , Powershell , C# and Command Line tool.
Configure Allow log on locally user rights via Local Security Policy GUI
- Grant Allow log on locally user rights via Powershell
- Set Allow log on locally user rights via Command Line
- Set Allow log on locally user permission using C#
Follow the below steps to set Allow log on locally user rights via Local Security Policy
1. Open the Run window by pressing ‘ Windows’ + ‘ R’ keys. 2. Type the command secpol.msc in the text box and click OK.

3. Now the Local Security Policy window will be open, in that window navigate to the node User Rights Assignment ( Security Settings -> Local Polices ->User Rights Assignment ). In right side pane, search and select the policy Allow log on locally .

4. Double-click on the policy Allow log on locally , in the opened window click the button Add User or Group, select the user account you want to set Allow log on locally rights and click OK, and click Apply button to finish.

Set or Grant Allow log on locally user rights via Powershell
We can set the Allow log on locally user rights using Powershell by importing the third party DLL ( Carbon ). Before you run the below script you need to the download latest Carbon files from here Download Carbon DLL .
Steps to follow to set Allow log on locally user rights via Powershell :
1. Download latest Carbon files from here Download Carbon DLL . 2. If you have downloaded the files, extract the zip file and you could see the Carbon DLL inside bin folder (In my case: C:UsersAdministratorDownloadsCarbonbinCarbon.dll ). 3. Copy the below Powershell script commands and place it notepad or textfile. 4. Now you can replace your Carbon DLL path in following script for the variable $CarbonDllPath 5. You can also replace the user identity that you are going to set log on locally user rights in the variable $Identity 6. Now run as Powershell window with Admin Privilege ( Run as Administrator ) 7. Copy the edited Powershell script and Run it in Powershell to configure Allow log on locally user rights.
Powershell output :

Other web site links for Carbon DLL: https://bitbucket.org/splatteredbits/carbon/downloads http://pshdo.com/ http://get-carbon.org/help/Grant-Privilege.html
Set Allow log on locally user right via Command Line tool
You can use the NTRights.exe utility to grant or deny user rights to users and groups from a command line or a batch file. The NTRights.exe utility is included in the Windows NT Server 4.0 Resource Kit Supplement 3. Use the below command to set log on locally user right using cmd.
Refer: http://support.microsoft.com/kb/266280
Set Log on Locally user right
Revoke Log on Locally user right

Set or Grant Allo Log on locally right/permission to user using C#
You can use the below function GrantLogonLocallyRights to set log on locally rights to user using C# code. This function uses the class LsaWrapper.
LsaWrapper class file
Share this:
Related posts.
- Change local system user account password using Powershell
- Remove user from local Administrator group using PowerShell
- Unlock AD User Account using Powershell script
- Check if AD user exists with PowerShell
- Set Office 365 user password via Powershell
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to add a user group in the "Shut down the system" group policy in Windows Server by CMD or PowerShell
I've read some documentation on Microsoft and other sites. Some of them suggest GPRegistryValue for registry-based policies and other recommended third-party software.
The full path of the key is: "Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment"
But in my case I cannot use other packages except CMD or PowerShell (UI not available).
- group-policy
- windows-server
- superuser.com/questions/1254253/… and blakedrumm.com/blog/set-and-check-user-rights-assignment might help you for a starting point to play with. – Vomit IT - Chunky Mess Style Nov 25, 2022 at 21:25
- This is just local security policy settings. What did you search for as this is a common task? powershell 'Local User Rights Management' – postanote Nov 25, 2022 at 21:37
Windows provides the secedit.exe tool for this and or custom code, as per the link provided in my comment to you.
Also, did you check the mspowershellgallery.com site for modules that assist with local user security policy?
Update as per '@Vomit IT - Chunky Mess Style', suggestion.
The more succinct/elegant option.
FYI --- Update for '@Vomit IT - Chunky Mess Style'. Using the PS_LSA.Wrapper
- 1 @VomitIT-ChunkyMessStyle... update provided. – postanote Nov 25, 2022 at 21:43
- Oh yeah, now you're talking!!! I saw github examples of that Indented.SecurityPolicy you suggested listed there. I like it! – Vomit IT - Chunky Mess Style Nov 25, 2022 at 21:55
- 1 Yeppers, I've got a bunch of these I've collected, refactored, and written over the years in different engagements. Even one using the underlying OS PS_LSA Windows library. – postanote Nov 25, 2022 at 22:06
- Thanks for helping me.The module of 'SecurityPolicy' is available, but when I try to find its modules "Get-Command -Module 'SecurityPolicy'" nothing is listed. Thus, I can't execute 'Add-UserRightsAssignment'. – Daniel Teodoro Nov 29, 2022 at 13:38
- If you did this Get-Command -Module 'SecurityPolicy' , and you see nothing? If so, that means it's not installed/in your PSModulePath. Did you install the module as I show in my suggested answer? If not, then you need to. Then you use Get-Module -ListAvailable to validate it's on your system. – postanote Nov 30, 2022 at 6:37
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged powershell group-policy windows-server ..
- The Overflow Blog
- Can software startups that need $$$ avoid venture capital?
- How to prevent your new chatbot from giving away company secrets
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
Hot Network Questions
- Physical reality of physics properties
- Do we really see the back of a cube when cube moves in relativistic speed?
- Using Anchor 26 and lower with Ubuntu 22 or newer
- What's the one digit you can fill in this partially hidden Sudoku?
- Italicizing a Lettrine on an Ad Hoc Basis
- Safe to remove wall separation between two closets?
- What exactly is a Morita invariant property for rings?
- How can I help a PhD student who's dead-set on keeping methodologically wrong results?
- How do real-world proof assistants bind variables and check equality?
- Examples of finitely presented subgroups of GL(n, Z) with unsolvable decision problems
- A Crossworm Puzzle
- Approximating the length of a circular arc using geometrical construction. How does it work?
- small slanted blackboard math
- Did uncompressed public keys use the `04` prefix before compressed public keys were used?
- How to start using git in a project that is already underway?
- Technique for Riding a Hybrid Bike on Trails and Switching to Knobbed Tires?
- Obvious wrongness of Aristotle
- Why does Heep refer to Copperfield sometimes as mister and sometimes as master?
- Possibly NSFW? What is an 既成事実?
- The relation between voices in piano pieces
- Is Maldives banning Israelis a form of 'collective punishment' and therefore illegal?
- According to Christian proponents of Intelligent Design, is Satan blinding the minds of the advocates of naturalistic abiogenesis and evolution?
- Is it ever more appropriate to use "incessant" over "constant"?
- The end of risk-neutral valuation
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Set-Local User
Modifies a local user account.
Description
The Set-LocalUser cmdlet modifies a local user account. This cmdlet can reset the password of a local user account.
The Microsoft.PowerShell.LocalAccounts module is not available in 32-bit PowerShell on a 64-bit system.
Example 1: Change a description of a user account
This command changes the description of a user account named Admin07.
Example 2: Change the password on an account
The first command prompts you for a password by using the Read-Host cmdlet. The command stores the password as a secure string in the $Password variable.
The second command gets a user account named User02 by using Get-LocalUser . The command stores the account in the $UserAccount variable.
The third command sets the new password on the user account stored in $UserAccount .
-AccountExpires
Specifies when the user account expires. To obtain a DateTime object, use the Get-Date cmdlet.
If you do not want the account to expire, specify the AccountNeverExpires parameter.
-AccountNeverExpires
Indicates that the account does not expire.
Prompts you for confirmation before running the cmdlet.
-Description
Specifies a comment for the user account. The maximum length is 48 characters.
Specifies the full name for the user account. The full name differs from the user name of the user account.
-InputObject
Specifies the user account that this cmdlet changes. To obtain a user account, use the Get-LocalUser cmdlet.
Specifies the name of the user account that this cmdlet changes.
Specifies a password for the user account. If the user account is connected to a Microsoft account, do not set a password.
You can use Read-Host -AsSecureString , Get-Credential , or ConvertTo-SecureString to create a SecureString object for the password.
If you omit the Password and NoPassword parameters, Set-LocalUser prompts you for the user's password.
-PasswordNeverExpires
Indicates whether the password expires.
Specifies the security ID (SID) of the user account that this cmdlet changes.
-UserMayChangePassword
Indicates that the user can change the password on the user account.
Shows what would happen if the cmdlet runs. The cmdlet is not run.
System.Management.Automation.SecurityAccountsManager.LocalUser
You can pipe a local user to this cmdlet.
You can pipe a string to this cmdlet.
SecurityIdentifier
You can pipe a SID to this cmdlet.
This cmdlet returns no output.
Windows PowerShell includes the following aliases for Set-LocalUser :
The PrincipalSource property is a property on LocalUser , LocalGroup , and LocalPrincipal objects that describes the source of the object. The possible sources are as follows:
- Active Directory
- Microsoft Entra group
- Microsoft Account
PrincipalSource is supported only by Windows 10, Windows Server 2016, and later versions of the Windows operating system. For earlier versions, the property is blank.
Related Links
- Disable-LocalUser
- Enable-LocalUser
- Get-LocalUser
- New-LocalUser
- Remove-LocalUser
- Rename-LocalUser
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

COMMENTS
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
I want to edit security settings of user rights assignment of local security policy using powershell or cmd. Eg: policy = "change the system time". default_security_settings = "local service,Administrators". i want to remove everything except Administrators. i have tried ntrights command, but seems like not working Any command will be appreciated.
9. You can use AccessChk in accomplish this task. Accesschk "domain\user" -a * will list all the permissions of a given domain user. You can call this program within a PowerShell script, concatenate the results into a text file, then filter out just the permissions you want to know about. Share.
They include account policies, local policies, user rights assignment, the Windows firewall, software restrictions, and so on. There are several ways to configure security policy settings. The most common are: Group policy objects (GPO) - Used in Active Directory domains to configure and regularly reapply security settings to multiple computers.
To view the local groups on a computer, run the command. Get-LocalGroup. To view the members of a specific group, use the Get-LocalGroupMember cmdlet. For example, to figure out who is a member of the local Administrators group, run the command Get-LocalGroupMember Administrators. You can create a new local user using the New-LocalUser cmdlet.
Get-ECSLocalGPOUserRightAssignment will retrieve Local Group Policy Object (GPO) user right assignments. This function is useful if you're looking to audit or backup your current user right assignments to a CSV. This function utilizes the Windows builtin SecEdit.exe to export the user rights list, and then this function. parses the exported file.
The Get-LocalUser cmdlet gets local user accounts. This cmdlet gets default built-in user accounts, local user accounts that you created, and local accounts that you connected to Microsoft accounts. Note. The Microsoft.PowerShell.LocalAccounts module is not available in 32-bit PowerShell on a 64-bit system.
This function's purpose is to let you view what privileges are currently available on the system (local or remote) as well as what is currently applied to your current process token. A quick run through of using this function with various parameters: Get-Privilege. Get-Privilege -Privilege SeAuditPrivilege, SeServiceLogonRight | Format-List.
1. 0. Managing User Rights Assignments in Powershell. Windows User Rights, also known as Windows Privileges, are traditionally managed via GPO or in the simplest of cases via the server's Local Security Policy. These assignments control special permissions that are often needed by IIS applications or other application hosting on Windows Servers.
undefined. User Rights Assignment is one of those meat and potatoes features of the operating system that we all have a cursory understanding of but rarely think about in depth. User rights include logon rights and permissions. Logon rights control who is authorized to log on to a device and how they can log on.
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
User rights govern the methods by which a user can log on to a system. User rights are applied at the local device level, and they allow users to perform tasks on a device or in a domain. User rights include logon rights and permissions. Logon rights control who is authorized to log on to a device and how they can log on. User rights ...
How to Set Logon User Rights with the Ntrights.exe in windows 10(64 bit) [duplicate] Ask Question Asked 7 years, 10 months ago. Modified 9 months ago. ... Set and Check User Rights Assignment via Powershell You can add, remove, and check User Rights Assignment (remotely / locally) with the following Powershell scripts. ...
This cmdlet is available in on-premises Exchange and in the cloud-based service. Some parameters and settings may be exclusive to one environment or the other. Use the Get-RoleAssignmentPolicy cmdlet to view existing management role assignment policies in your organization. For information about the parameter sets in the Syntax section below ...
Configure Allow log on locally user rights via Local Security Policy GUI. Follow the below steps to set Allow log on locally user rights via Local Security Policy. 1. Open the Run window by pressing ' Windows' + ' R' keys. 2. Type the command secpol.msc in the text box and click OK. 3. Now the Local Security Policy window will be open ...
Manual steps: Open Group Policy Management. Navigate to the following path in the Group Policy Object. Select Policy. Right click & Edit: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Add/remove the necessary users. Windows. Active Directory.
The full path of the key is: "Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment" But in my case I cannot use other packages except CMD or PowerShell (UI not available). Thanks. powershell; group-policy; windows-server; ... powershell 'Local User Rights Management' - postanote. Nov 25, 2022 at 21:37.
The Microsoft Graph and PowerShell modules provide excellent ways of provisioning items into the Microsoft 365 tenant. The main advantage for admins is to make repeatable and configurable scripts for a smoother and quicker user onboarding process. To learn more about working with Microsoft Graph, see official documentation here.
You can pipe a local user to this cmdlet. String. You can pipe a string to this cmdlet. SecurityIdentifier. You can pipe a SID to this cmdlet. Outputs. None. This cmdlet returns no output. Notes. Windows PowerShell includes the following aliases for Set-LocalUser: slu
Open Group Policy Management. Navigate to the following path in the Group Policy Object. Select Policy. Right click & Edit: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Add/remove the necessary users. Click on image for details. Tried Set-GPPermission but didn't work it adds user in delegation ...