The Rise of TikTok: The Evolution of a Social Media Platform During COVID-19
- First Online: 11 March 2021

Cite this chapter

- Jana Feldkamp 6
Part of the book series: SpringerBriefs in Information Systems ((BRIEFSINORMAT))
10k Accesses
18 Citations
In the global efforts to fight the pandemic, social distancing guidelines were enforced. Ways to virtually interact and communicate with each other had to be found in order to fulfill social needs. One of these ways were social media platforms as for example TikTok, which download rate increased significantly in the last year. This chapter investigates the rise of TikTok during the global pandemic by reviewing the existing literature from research and practice. As a result, I identified key success factors that supported the rise of TikTok as well as diversification possibilities for the post-pandemic evolution of TikTok. Therefore, the chapter explores the digital transformation of an ecosystem, deriving conceptual knowledge.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Aerzteblatt. (2020). COVID-19: Die Hashtags der Krise . Retrieved June 25, 2020, from https://www.aerzteblatt.de/nachrichten/111302/COVID-19-Die-Hashtags-der-Krise
Carr, C., & Hayes, R. (2015). Social media: Defining, developing, and divining. Atlantic Journal of Communication, 23 (1), 46–65. https://doi.org/10.1080/15456870.2015.972282 .
Article Google Scholar
Clement, J. (2020a). Leading Android apps worldwide 2020, by downloads . Retrieved July 1, 2020, from https://www.statista.com/statistics/693944/leading-android-apps-worldwide-by downloads/
Clement, J. (2020b). Leading iPhone apps worldwide 2020, by downloads . Retrieved July 1, 2020, from https://www.statista.com/statistics/695791/top-iphone-apps-worldwide-by-number-of downloads/
Cullinan, E. (2020). Why we lack motivation to work during a global pandemic . Retrieved July 1, 2020, from https://www.welcometothejungle.com/en/articles/lack-motivation-during-corona-crisis
Daugherty, T., Eastin, M., & Bright, L. (2008). Exploring consumer motivations for creating user-generated content. Journal of Interactive Advertising, 8 (2), 16–25. https://doi.org/10.1080/15252019.2008.10722139 .
Docherty, K. (2020). 12 TikTok challenges to inspire your next campaign . Retrieved July 1, 2020, from https://later.com/blog/tiktok-challenges/
Hallikainen, P. (2015). Why people use social media platforms: Exploring the motivations and consequences of use. In L. Mola, F. Pennarola, & S. Za (Eds.), From information to smart society . Lecture Notes in Information Systems and Organisation (Vol. 5). Cham: Springer.
Google Scholar
Haoran. (2020). TikTok: Using AI to take over the world . Retrieved July 1, 2020, from https://digital.hbs.edu/platform-digit/submission/tik-tok-using-ai-to-take-over-the world/
Hutchinson, A. (2020a, May 28). TikTok announces #LearnOnTikTok initiative to encourage education during lockdowns . Retrieved July 7, 2020, from https://www.socialmediatoday.com/news/tiktok-announces-learnontiktok-initiative-to-encourage-education-during-lo/578805/
Hutchinson, A. (2020b, June 18). How TikTok’s algorithm works – as explained by TikTok . Retrieved July 1, 2020, from https://www.socialmediatoday.com/news/how-tiktoks-algorithm-works-as-explained-by-tiktok/580153/
InfluencerMarketingHub. (2020a, January 2). How much do TikTok Ads cost? Retrieved July 1, 2020, from https://influencermarketinghub.com/how-much-do-tiktok-ads-cost/ )
InfluencerMarketingHub. (2020b, May 26). What is TikTok? What you need to know about the new Musical.ly . Retrieved from https://influencermarketinghub.com/what-is-tiktok/
InfluencerMarketingHub. (2020c, July 12). TikTok-Marketing für Anfänger – Ein Marketing-Handbuch für Werbung auf TikTok . Retrieved July 1, 2020, from https://influencermarketinghub.com/de/tiktok-marketing-anfaenger/
Iqbal, O. (2020a). TikTok makes moves into education market . Retrieved July 10, 2020, from https://www.bbc.com/news/technology-53079625
Iqbal W. (2020b). TikTok revenue and usage statistics . Retrieved July 10, 2020, from https://www.businessofapps.com/data/tik-tok-statistics/
Johnson, J. (2020a). Online media use changes during the coronavirus pandemic in Europe 2020 . Retrieved July 1, 2020, from https://www.statista.com/statistics/1110864/online-media-use-during-the-coronavirus-pandemic-europe/
Johnson, T. (2020b). The rise of TikTok during COVID-19 . Retrieved June 25, 2020, from https://tinuiti.com/blog/marketing-news-covid-19/tiktok-covid-19/
Joseph, S. (2020). ‘A shift towards maturity’: Why TikTok is investing $15m in short-form educational content in Europe . Retrieved July 10, 2020, from https://digiday.com/media/a-shift-towards-maturity-why-tiktok-is-investing-15m-in-short-form-educational-content-in-europe/
Kaplan, A., & Haenlein, M. (2010). Users of the world, unite! The challenges and opportunities of social media. Business Horizons, 53 (1), 59–68. https://doi.org/10.1016/j.bushor.2009.09.003 .
Kavanagh, D. (2019). Is time against TikTok? Retrieved from https://blog.globalwebindex.com/chart-of-the-week/time-against-tiktok/
Krause, R. (2020, May 18). TikTok raises profile in digital ads, hires Disney streaming boss as CEO . Investor’s Business Daily . Retrieved from https://search.proquest.com/docview/2404160634?accountid=10218
Lewanczik, N. (2020). TikTok: Neue features und API Öffnung liefern mehr Optionen für TikToker und Advertiser . Retrieved July 7, 2020, from https://onlinemarketing.de/news/tiktok-neue-features-api-oeffnung-optionen-tiktoker
LLC. (2020, April 25). Tik tok’s challenge that binds families during coronavirus quarantine. CE Noticias Financieras . Retrieved July 1, 2020, from https://search.proquest.com/docview/2394770938?accountid=10218
Maslow, A. H. (1943). A theory of human motivation. Psychological Review, 50 , 370–396. Retrieved from http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.318.2317&rep=rep1&type=pdf
Mohsin, M. (2020). 10 TikTok statistics that you need to know in 2020 [Infographics] . Retrieved July 7, 2020, from https://www.oberlo.com/blog/tiktok-statistics
Newsroom TikTok. (2020). TikTok small gestures launches with brand partners to give back . Retrieved July 7, 2020, from https://newsroom.tiktok.com/de-de/tiktok-small-gestures-launches with-brand-partners-to-give-back
Nikolinakou, A., & Phua, J. (2019). Do human values matter for promoting brands on social media? How social media users’ values influence valuable brand-related activities such as sharing, content creation, and reviews. Journal of Consumer Behaviour, 19 (1), 13–23. https://doi.org/10.1002/cb.1790 .
Novak, T. (2020). The rise of TikTok and understanding its parent company, ByteDance . Retrieved July 1, 2020, from https://turner.substack.com/p/the-rise-of-tiktok-and-understanding
Obar, J. A., & Wildman, S. (2015). Social media definition and the governance challenge: An introduction to the special issue. Telecommunications Policy, 39 (9), 745–750.
Paul, K. (2020a). It’s corona time’: TikTok helpy teens cope with the coronavirus pandemic . Retrieved June 25, 2020, from https://www.theguardian.com/world/2020/mar/12/coronavirus-outbreak-tik-tok-memes
Paul, M. (2020b). How to use TikTok challenges for business . Retrieved July 7, 2020, from https://www.socialmediaexaminer.com/how-to-use-tiktok-challenges-for-business/
Pham, S. (2020). TikTok ban undercuts ByteDance in one of the world’s biggest digital markets . Retrieved July 13, 2020, from https://edition.cnn.com/2020/06/30/tech/tiktok-india-ban-intl-hnk/index.html
Porter, J. (2020). Facebook’s TikTok clone Lasso will shut down this month . Retrieved July 13, 2020, from https://www.theverge.com/2020/7/2/21311077/facebook-lasso-shutting-down-tiktok short-form-video-hobbi
Sbai, A. (2020). Hashtag Challenges als Trend: TikTok auf dem Vormarsch . Retrieved July 11, 2020, from https://onlinemarketing.de/news/hashtag-challenges-tiktok-vormarsch
Schwär, H. (2020). TikTok bricht sämtliche Download-Rekorde – dank Langeweile in der Isolation . Retrieved July 5, 2020, from https://www.gruenderszene.de/media/tiktok-download-rekord-corona?interstitial
Shao, G. (2009). Understanding the appeal of user-generated media: A uses and gratification perspective. Internet Research, 19 (1), 7–25. https://doi.org/10.1108/10662240910927795 .
Singh, M. (2020). TikTok goes down in India, its biggest overseas market . Retrieved July 13, 2020, from https://techcrunch.com/2020/06/30/tiktok-goes-down-in-india-its-biggest-overseas-market
Sloane, G., & Rittenhouse, L. (2019). First look at TikTok’s game plan: Leaked pitch deck reveals how the app is luring brands. Spoiler alert: There will be gummy bears. Advertising Age, 90 (20), 6. Retrieved from https://search.proquest.com/docview/2306286732?rfr_id=info%3Axri%2Fsid%3Aprimo
SmartInsights. (2020). TikTok – Launches ‘Small Gestures’ on its social media platform . Retrieved July 15, 2020, from https://www.smartinsights.com/social-media-marketing/social-media-strategy/tiktok small-gestures-virtual-gift-giving-social-media-platform/
Sprinklr. (2020). Retrieved July 15, 2020, from https://www.sprinklr.com/de/
Sturm, B., & Sunyaev, A. (2019). Design principles for systematic search systems: A holistic synthesis of a rigorous multicycle design science research journey. Business & Information Systems Engineering, 61 (1), 91–111.
TikTok. (2020). Retrieved from https://www.tiktok.com
Verto Analytics. (2019, November 12). Most popular mobile social networking apps in the United States as of September 2019, by average session duration (in minutes) [Graph]. Statista . Retrieved July 15, 2020, from https://www.statista.com/statistics/579411/top-us-socialnetworking-apps-ranked-by-session-length/
Werder, K., Helms, R.W., & Jansen, S. (2014). Social media for success: A strategic framework. In Pacific Asia conference on information systems 2014 , AISeL, Chengdu, PRC, Paper 92.
Xu, L., Yan, X., & Zhang, Z. (2019). Research on the causes of the “TikTok” app becoming popular and the existing problems. Journal of Advanced Management Science, 7 (2). Retrieved from http://www.joams.com/uploadfile/2019/0613/20190613034911476.pdf
Zheng, T., Foschi, L., Haynie, M., Lyster, L., Pittard. B., Dirkx, D., Low, B., Friedman, K., & Kelly, S., (2020). The role of social media during the coronavirus pandemic . Retrieved July 10, 2020, from https://www.pmg.com/blog/the-role-of-social-media-during-the-coronavirus pandemic/?cn-reloaded=1
Download references
Author information
Authors and affiliations.
University of Cologne, Cologne, Germany
Jana Feldkamp
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Jana Feldkamp .
Editor information
Editors and affiliations.
Christian Hovestadt
Janek Richter
Karl Werder
Rights and permissions
Reprints and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Feldkamp, J. (2021). The Rise of TikTok: The Evolution of a Social Media Platform During COVID-19. In: Hovestadt, C., Recker, J., Richter, J., Werder, K. (eds) Digital Responses to Covid-19. SpringerBriefs in Information Systems. Springer, Cham. https://doi.org/10.1007/978-3-030-66611-8_6
Download citation
DOI : https://doi.org/10.1007/978-3-030-66611-8_6
Published : 11 March 2021
Publisher Name : Springer, Cham
Print ISBN : 978-3-030-66610-1
Online ISBN : 978-3-030-66611-8
eBook Packages : Business and Management Business and Management (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

- Publishing Policies
- For Organizers/Editors
- For Authors
- For Peer Reviewers
TikTok Addiction Behaviour Among Users: A Conceptual Model and Research Propositions

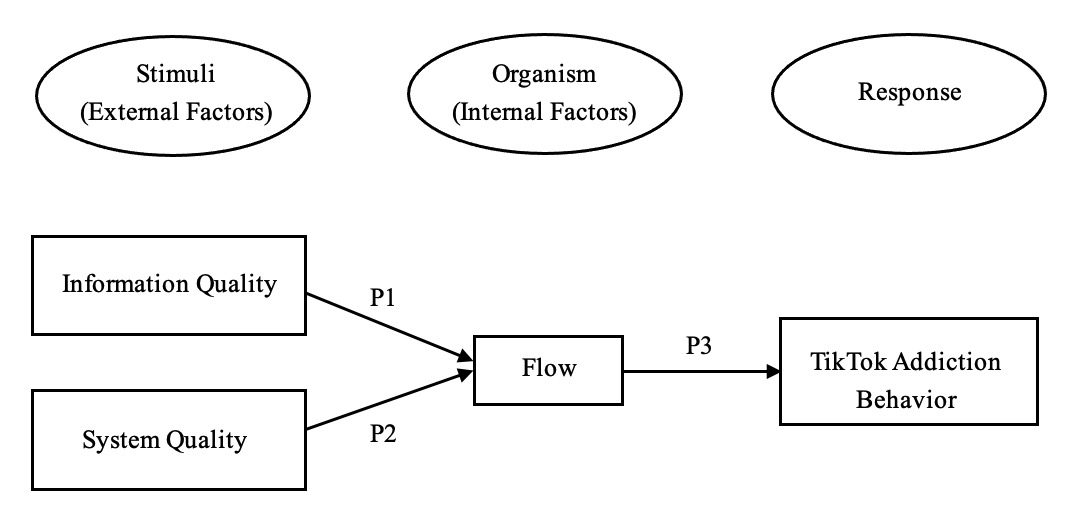
Social media addiction has become a serious problem and deserve urgent attention. TikTok, one of the emerging social media platforms, has gained popularity among social media users and scholars anticipate that the phenomenon of TikTok addiction is expanding especially among adolescents. Despite this alarming concern, less research attention has been paid to the dark side of TikTok compulsive behaviour. The present article aims to propose a conceptual model to depict the external and internal factors determining addiction behaviour among young users of TikTok. We propose a causal-chain framework originated from the Stimuli-Organism-Response (SOR) paradigm to delineate the role of information quality and system quality (i.e.: the external factors as the stimuli), and flow experience (i.e.: the internal factors as organism) in explaining TikTok addiction behaviour (as the response). By adopting SOR framework and employing the flow theory as a guide, this study develops a conceptual model of TikTok addiction behaviour. The model posits that users experience with the system leads to TikTok addiction behaviour. This article contributes to our understanding of TikTok addiction among adolescence and suggests possible solutions to curb this prevailing social problem in society. Theoretical and managerial implications are subsequently discussed in light of the conclusion.
Keywords: TikTok , information system , flow , addiction behaviour
Introduction
With the development of technology, short-form video media has gradually become a new favourite of people, which has dramatically changed the way people communicate and interact ( Ngai et al., 2015 ). TikTok, known as Douyin in China, has 1.5 billion active users so far, and downloaded more than 1 billion times around the world, and is already ahead of competitors like Netflix, YouTube, Snapchat and Facebook ( Omar & Dequan, 2020 ; Weimann & Masri, 2020 ).
TikTok is also the most popular social media platform among millennials in China ( Jung & Zhou, 2019 ). The characteristics of younger group users is short attention span and easily to get immersed in the content they like. According to the features and preferences of this age group, designers build a special algorithm (Feed for You) to customize video content for each user ( Figliola, 2020 ).
When adolescent user exposed with more and more matched content, they will extend the using time, and immersed in TikTok. According to statistics, active TikTok users open the app 8 times per day on average, about 22% of TikTok users use the app for more than an hour a day ( Iqbal, 2020 ). During the COVID-19 outbreak globally, Chinese government has implemented the lockdown. people stay at home without going outside, the average time spent per day by TikTok users rose to 122.3 minutes, that's almost double the 68.8 minutes recorded in 2019, and the number of daily active users increased by 19.4% during the period ( Iqbal, 2020 ) and most of them were active between 9 p.m. and 12 a.m., when about 26.3 percent of its users are online ( Mou, 2020 ).
Problem Statement
But excessive immersion leads to users' attachment and addiction to social media ( Cao et al., 2020 ; Weimann & Masri, 2020 ), it then caused depression, anxiety, insomnia, poor eyesight, academic problem, low work performance, etc. ( Beyens et al., 2016 ; Enez Darcin et al., 2016 ; Fu et al., 2020 ; Weinstein & Lejoyeux, 2010 ). These adverse outcomes are well-known indicators of addiction ( Gao et al., 2017 ).
Thus, similar to Facebook addiction, short-form video app addiction may be another sub-category of Internet addiction ( Zhang et al., 2019 ). Some scholars believe that the phenomenon of TikTok addiction is expanding ( Zhang et al., 2019 ).
The existing literature on social media use behaviour, while very commendable, most of the researches only considered single factors such as the technology characteristic ( Rahi et al., 2020 ), website design quality ( Ma et al., 2019 ), perceived usefulness and perceived ease of use ( Ifinedo, 2018 ), IS quality ( Idemudia et al., 2018 ), satisfaction and attitude ( Zhang et al., 2016 ), the user personality ( Omar & Dequan, 2020 ), cognitive factors ( Liao et al., 2009 ), etc.,. In addition, when explaining social media use behaviour, they over-rely on use and gratification theory (U&G), theory of planed behaviour (TPB), technology continuance theory (TCT) and expectation conformation theory (ECM) models and other models. Further research needs to combine both media factors (external factors) and user factors (internal factors) to comprehensively investigate user behaviour.
Research Questions
This research is guided by the following research questions:
RQ1: How do the external factors (information quality and system quality) affect internal factors (flow experience)?
RQ2: Do internal factors (flow experience) have a significant effect on the TikTok addiction behaviour?
RQ3: Do internal factors (flow experience) mediate the effect between external factors and TikTok addiction behaviour?
Purpose of Statement
The current conceptual paper aims to develop theoretical framework by proposing the relationship between information quality, system quality, flow, and addictive behaviour. More importantly, to support theoretical framework, two theories were employed including SOR and flow theory. Because So far, there is no comprehensive effort to integrate the factors that induce users to use social media into a single model. This requires further research to develop a wholistic cause and chain framework to help gain more explanatory power and illuminate social media use behaviour.
Literature Review and propositions development
Current research on the short-form video app TikTok has focused on user adoption ( Omar & Dequan, 2020 ), and the business and social value created (such as job opportunity) ( Hu, 2020 ; Xu et al., 2019 ). Recently, scholars have gradually begun to use SOR to explain user behaviour through the combination of internal and external factors, but most studies focus on its negative consequences, like depression, anxiety, insomnia, poor vision, academic problems, low job performance ( Cao & Sun, 2018 ; Fu et al., 2020 ; Luqman et al., 2017, 2020; Moqbel, 2020 ; Whelan et al., 2020 ).
Despite SOR contributes the body of literature on addiction behaviour, the researchers believe that it still ignores the formation of addictive behaviour. To explore the factors of TikTok addictive behaviour in the emerging short-form video medium, SOR model was adopted in this study, and IS model and flow theory were integrated into SOR to develop a comprehensive theoretical framework and expand our understanding of adolescent TikTok addictive behaviour. Drawing on these theories, the conceptual framework of this paper will be reviewed and propositions.
The SOR model, also known as the environmental psychological model, was developed by Mehrabian and Russell ( 1974 ). In the SOR framework, it is assumed that environmental cues would stimulate individual’s emotional and cognitive state, which leads to certain behavioural ( Lee et al., 2018 ; Mehrabian & Russell, 1974 ).
As a meta-theory to explain human behaviour process, SOR is used to predict the cognitive judgment and subsequent behaviour or intention of network users. The model has been successfully used to explain consumer behaviours, social media applications, virtual experiences, gamification studies ( Cho et al., 2019 ; Kamboj et al., 2018 ; Sun et al., 2018 ; Triantoro et al., 2019 ; Xu et al., 2019 ). It can explain the internal psychological change and interruption response of individuals when they face the environmental stimulus produced by media. For example, both technological environments and virtual psychological experiences have significant effects on the behaviour of social network users ( Luqman et al., 2017 ). Short-form video applications have a lot in common with social media and SNS. However, as an emerging platform, the current research is still in the initial stage, and we could borrow the theoretical framework from social media research.
Stimuli: External factors: IS mode
In the SOR framework, a stimulus refers to "the environment that an individual encounter ( Mehrabian & Russell, 1974 ). In previous studies, the technical aspects of virtual space have been treated as environmental stimuli ( Animesh et al., 2011 ; Zhang et al., 2015 ). A study in the field of information systems (IS) used this framework to explain how information technology attributes relate to the user's internal state and subsequent adoption behaviour ( Benlian, 2015 ). Application quality is divided into information quality and system quality ( Almahamid et al., 2016 ), this site quality structure is a major factor in assessing site users' expectations and perceptions of site quality ( DeLone & McLean, 2003 ; Liang & Chen, 2009 ).
Information Quality
Information quality refers to the accuracy, completeness, and freshness of website content, which IS the user's evaluation of IS's performance in providing information based on their experience in using the system ( McKinney et al., 2002 ). It reflects the relevance, timeliness and adequacy of the information provided by the platform ( Kim et al., 2003 ). This assessment is based on the content of the IS website and needs to be personalized, complete, relevant, and easy to use and provide security aspects to encourage online use ( DeLone & McLean, 2003 ). Recently, the IS success model has been used to understand mobile user behaviour. For example, Gao and Bai ( 2014 ) used the IS model to explain the continuous intention of users of mobile social network services and found that information quality was positively correlated with user experience of using mobile social network services.
System Quality
System quality refers to the degree to which a website functions, such as accessibility, reliability, and response time ( DeLone & McLean, 2003 ). It represents the technical capability of a website to provide users with simple and quick access to information while ensuring reliability and security ( Teo et al., 2008 ). A well-designed system is necessary to reap organizational benefits, such as reduced costs, improved process efficiency, and increased revenue. Conversely, a poorly designed system may be disruptive to the organization, leading to increased product costs and organizational inefficiency ( Ghasemaghaei & Hassanein, 2015 ; Gorla et al., 2010 ).
Organism: Flow as international factors
The next element of the SOR framework is the organism component, consisting of cognitive and affective mediating states, expressed in the process of regulating the relationship between stimuli and individual responses ( Chen & Chang, 2008 ; Mehrabian & Russell, 1974 ). According to Gao and Bai ( 2014 ), the Organism is a customer's cognitive judgment of the online consumer experience, presented as a stream experience. In this study, we also consider flow as organism component.
Flow theory
SOR model provides a theoretical basis for the mediating effect of flow experience. Studies using SOR framework have shown that consumer internal states (organisms) can play a mediating role between timulus and consumer response behaviour ( Gao & Bai, 2014 ; Ha & Lennon, 2010 ). Computer-mediated communication is a typical situation in which users can experience a psychological state of flow ( Lee et al., 2018 ).
The flow theory was first proposed by Csikszentmihalyi ( 1975 ). It refers to a state of deep immersion in a pleasingly optimal psychological experience ( Novak et al., 2000 ), which is a key driver of persistence ( Chang, 2013 ; Khang et al., 2013 ). Individuals experiencing flow may become so completely lost in the activities they are doing that they lose awareness of time and their surroundings ( Csikszentmihalyi, 1975 ).
Since the short-form video application is an experience product, the user's value mainly comes from their experience during the use process, they can feel great fun. Therefore, based on the SOR model, combined with previous mediation effect on internal cognitive status of research, we have reason to believe that flow in the information system quality and the intermediary role between user reaction, affect the user's internal mental process, which affect their behavioural responses, the flow theory is applied to study the short-form video application addictive behaviour of users.
Response: TikTok addiction behaviour
The response component in the SOR framework refers to the result, final action or reaction, including psychological reaction such as attitude or behaviour, which can be divided into approach behaviour and avoidance behaviour ( Mehrabian & Russell, 1974 ). Approaching behaviour is a positive response and avoiding behaviour is a negative response.
More recently, as algorithmic technology has been upgraded, users have been given more matched content, and using these features has led to varying degrees of immersion, which in turn has induced addictive behaviour. In social media, users are exposed to various technical features or functions, such as user-provided experience, technical stress, exhaustion, and user profiles, which all affect users' participation in social media. As mentioned above, behaviour is closely related to the psychological experience of using social networks ( Zhang et al., 2016 ). TikTok is an emerging short-form video app that offers customized content to users based on their preferences. These fun features and personalized content have addictive entertainment value for very young users. Then, we use addictive behaviour as response to immersive experiences associated with the use of smartphone-based short-form video media.
Proposition development
Information system quality to flow experience.
According to the previous research ( Zhou et al., 2010 ), information quality has a significant impact on users' flow experience, which in turn determines users' loyalty. There are many factors that affect flow, Jung et al. ( 2009 ) point out that content quality affects the flow experience of mobile TV users. Zhou ( 2014 ) confirmed the impact of system quality and information quality on user flow experience of mobile Internet sites as well.
TikTok has its unique way of improving the user experience compared to other social media. For example, offer a variety of special effects filters, fun stickers, and video editing tools to help users spice up their videos. TikTok also offers customized content to users based on their preferences. These fun features and personalized content have addictive entertainment value for very young users. Therefore, this study believes that in order to enable users to have flow experience in TikTok, the positive cognition of the two attributes (information quality and system quality) provided by the platform makes users to immerse themselves in the use process and thus to have flow experience. Therefore, it is very easy for users, especially teenagers who lack self-control, to become addicted to short-form video apps. From this we derive the proposition:
Preposition 1: Information quality has a positive influence on user flow experience.
Preposition 2: System quality has a positive influence on user flow experience.

Flow experience to TikTok addiction
Recent research provides some empirical support that flow can have negative outcomes. For example, Chou and Ting ( 2003 ) found that flow significantly affects online game addiction. Previous studies have shown that smartphone users may experience flow while playing games on their devices ( Joo, 2016 ) and browsing the Internet ( Kim & Han, 2014 ). When people want to have a positive experience of flow, they are also easily addicted to media platforms ( Salehan & Negahban, 2013 ). In this study, we propose that flow may influence the addictive use of short-form video apps in a similar way. We predict that flow may be an important stage prior to users' addictive behaviour ( Khang et al., 2013 ). Therefore, we believe that people who experience flow during the use of short-form video apps are more likely to engage in addictive behaviour. We now raise the proposition:
Preposition 3: Flow experience has a positive influence on TikTok addiction behavioural.
The rest of this paper describes the theoretical background of SOR model, IS theory, flow theory and addictive behaviour in detail. Then, the conceptual framework and three propositions are used to study the influence of the combination of internal and external factors on addictive behaviour.
Research Methods
This paper is a conceptual work that outlines some research prepositions to understand TikTok addition behaviour. This proposed conceptual model should be tested empirically. To statistically validate our conceptual model, users’ perception of information and system qualities as well as their experience with flow and addiction behaviour need to be gauged. Hence, a survey research is the most suitable method to gauge users’ perceptions and behaviours. This is consistent with past research which also used survey method to examine TikTok usage behaviour ( Omar & Dequan, 2020 ). It involves identifying sampling technique, measurement, and data analysis.
With regards to sampling technique, adolescents or young people is the targeted sample. According to Mou ( 2020 ), the largest age group of TikTok users is 6-17 years old, accounting for 31.59%, followed by 18-24 years old (30.14), 25-30 years old (20.85%), 31-35 years old (8.66%), and over 35 years old (8.76). Hence, individuals between the ages of 14 and 18 who have used TikTok in the past year could be an appropriate sample for study. Researchers can adopt non-probability sampling such as virtual snowballing sampling or network sampling to reach out to the TikTok users online.
As for the measurement of constructs, the items can be adopted from past research. Measures for information quality and system quality can be drawn from Kim et al. ( 2003 ) and Zhang et al. ( 2016 ). Meanwhile, the measurement of flow experience can be taken from Zaman et al. ( 2010 ) and Zhang et al. ( 2014 ). Similarly, the TikTok addiction behaviour’s measurement is found in Khang et al. ( 2013 ); Kim et al. ( 2003 ). Table, 1 presents the various constructs in the current framework and strategies for their measurement.
In terms of data analysis, partial least squares (PLS-SEM) analysis is the most option to test the proposed model. This is because PLS-SE< is suitable for the identification of complex critical structural models ( Hair et al., 2019 ). As suggested by Hair et al., ( 2019 ), the study model should be tested in two steps. Firstly, the measurement model should be evaluated to establish the validity and reliability of the questionnaire. Then, in the second step, the structural model should be tested using the bootstrapping technique in order to test the proposed research prepositions.
This study has conceptualized the addictive behaviour of users of short-form video applications, in a word, it is a negative behavioural result of users' flow experience under the influence of external factors of the information system. In this context, this paper proposes a conceptual model that provides theoretical and practical benefits from the perspective of SOR model and flow theory.
Theoretical implications
Theoretically, this study will contribute to the media literature by confirming the SOR model in the context of TikTok addictive behaviour. It will provide strong evidence that internal factors (flow experience) and external factors (IS quality) can lead to adolescents' addiction to TikTok. This study advances the understanding of adolescent addiction behaviour in TikTok through IS quality and flow factors by applying the modified SOR model ( Belk, 1975 ). Previous literature conducted on social media were heavily rely on theory of planed behaviour (TPB), technology continuance theory (TCT) and expectation conformation theory (ECM) models. These studies analyse the causes of addiction from the perspective of the individual, ignoring external environmental stimuli. Therefore, this study overcomes the defects mentioned before. Based on previous literature, we combine the internal factors (flow) with external factors (information quality and system quality) to revaluate the relationship between information system, flow, and addiction behaviour.
Practical implications
This research also has practical contributions. Social media addiction can have many negative effects on young users and the society, so it is necessary for scholars and practitioners to solve this problem. As for TikTok adolescents’ users, excessive immersion on media platform can actively trigger addictive behaviours, which can lead many problems such as depression and anxiety. Therefore, This could raise legal liability and ethical issues for TikTok operator ( Gong et al., 2020 ; Zheng & Lee, 2016 ). Adolescents are at a critical stage of development, media operators should cultivate user with healthy social media use habits, instead of inducing them to become addicted. Therefore, when facing addiction issue, the operators should help users to get rid of it. For example, adolescent mode can be set to limit the content provided to adolescents and control the duration of their use (excessive use of the reminder or disconnection system), this method has been proven to be an effective way to control addictive behaviours ( Chen et al., 2017 ).
Limitations and future research
Although this article presents diverse theoretical and practical implications, limitations are still existing for future research. First, the conceptual framework and propositions must be tested. Due to the current epidemic, the work and life of TikTok users are in an abnormal state. The life at home leads to the prolonged use of smartphone, which may exaggerate the effect of addiction. Therefore, the proposed theoretical model can be used as a reference for subsequent empirical research. Second, the formation of addiction is a complex problem, only adopt quantitative methods may lead to research bias. Future studies could combine qualitative and quantitative method to gain depth of understanding of short-form video application addiction behaviour.
Almahamid, S. M., Tweiqat, A. F., & Almanaseer, M. S. (2016). University website quality characteristics and success: Lecturers’ perspective. International Journal of Business Information Systems, 22(1), 41–61. DOI:
Animesh, A., Pinsonneault, A., Yang, S. B., & Oh, W. (2011). An odyssey into virtual worlds: Exploring the impacts of technological and spatial environments on intention to purchase virtual products. MIS Quarterly: Management Information Systems, 35(3), 789–810. DOI:
Belk, R. W. (1975). Situational Variables and Consumer Behavior. Journal of Consumer Research, 2(3), 157. DOI:
Benlian, A. (2015). Web personalization cues and their differential effects on user assessments of website value. Journal of Management Information Systems, 32(1), 225–260. DOI:
Beyens, I., Frison, E., & Eggermont, S. (2016). “I don’t want to miss a thing”: Adolescents’ fear of missing out and its relationship to adolescents’ social needs, Facebook use, and Facebook related stress. Computers in Human Behavior, 64, 1–8. DOI:
Cao, X., Gong, M., Yu, L., & Dai, B. (2020). Exploring the mechanism of social media addiction: an empirical study from WeChat users. Internet Research, 30(4), 1305–1328. DOI:
Cao, X., & Sun, J. (2018). Exploring the effect of overload on the discontinuous intention of social media users: An S-O-R perspective. In Computers in Human Behavior (Vol. 81, pp. 10–18). DOI:
Chang, C. C. (2013). Examining users′ intention to continue using social network games: A flow experience perspective. Telematics and Informatics, 30(4), 311-321.
Chen, C., Zhang, K. Z. K., Gong, X., Zhao, S. J., Lee, M. K. O., & Liang, L. (2017). Understanding compulsive smartphone use: An empirical test of a flow-based model. International Journal of Information Management, 37(5), 438–454. DOI:
Chen, S. W., & Chang, H. H. (2008). The impact of online store environment cues on purchase intention: Trust and perceived risk as a mediator. Online Information Review, 32(6), 818–841.
Cho, W. C., Lee, K. Y., & Yang, S. B. (2019). What makes you feel attached to smartwatches? The stimulus–organism–response (S–O–R) perspectives. Information Technology and People, 32(2), 319–343. DOI:
Chou, T. J., & Ting, C. C. (2003). The Role of Flow Experience in Cyber-Game Addiction. Cyberpsychology and Behavior, 6(6), 663–675. DOI:
Csikszentmihalyi, M. (1975). Play and intrinsic rewards. Journal of Humanistic Psychology, 15, 41–63.
DeLone, W. H., & McLean, E. R. (2003). The DeLone and McLean model of information systems success: a ten-year update. Journal of management information systems, 19(4), 9-30.
Enez Darcin, A., Kose, S., Noyan, C. O., Nurmedov, S., Yılmaz, O., & Dilbaz, N. (2016). Smartphone addiction and its relationship with social anxiety and loneliness. Behaviour and Information Technology, 35(7), 520–525. DOI:
Figliola, P. (2020). TikTok: Technology Overview and Issues (CRS Report Number: R46543).
Fu, S., Chen, X., & Zheng, H. (2020). Exploring an adverse impact of smartphone overuse on academic performance via health issues: a stimulus-organism-response perspective. In Behaviour and Information Technology. DOI:
Gao, L., & Bai, X. (2014). An empirical study on continuance intention of mobile social networking services: integrating the IS success model, network externalities and flow theory. 26(2), 168–189.
Gao, W., Liu, Z., & Li, J. (2017). How does social presence influence SNS addiction? A belongingness theory perspective. Computers in Human Behavior, 77, 347–355. DOI:
Ghasemaghaei, M., & Hassanein, K. (2015). Online information quality and consumer satisfaction: The moderating roles of contextual factors - A meta-analysis. Information and Management, 52(8), 965–981. DOI:
Gong, M., Yu, L., & Luqman, A. (2020). Understanding the formation mechanism of mobile social networking site addiction: evidence from WeChat users. Behaviour and Information Technology, 39(11), 1176–1191. DOI:
Gorla, N., Somers, T. M., & Wong, B. (2010). Organizational impact of system quality, information quality, and service quality. Journal of Strategic Information Systems, 19(3), 207–228. DOI:
Ha, Y., & Lennon, S. J. (2010). Online visual merchandising (VMD) cues and consumer pleasure and arousal: Purchasing versus browsing situation. Psychology and Marketing, 27(2), 141–165. DOI:
Hair, J. F., Risher, J. J., Sarstedt, M., & Ringle, C. M. (2019). When to use and how to report the results of PLS-SEM. European Business Review, 31(1), 2–24. DOI:
Hu, Y. (2020). Research on the commercial value of Tiktok in China. Academic Journal of Business & Management, 2(7), 57–64. DOI:
Idemudia, E. C., Raisinghani, M. S., & Samuel-Ojo, O. (2018). The contributing factors of continuance usage of social media: An empirical analysis. Information Systems Frontiers, 20(6), 1267–1280. DOI:
Ifinedo, P. (2018). Determinants of students’ continuance intention to use blogs to learn: an empirical investigation. Behaviour and Information Technology, 37(4), 381–392. DOI:
Iqbal, M. (2020). TikTok revenue and usage statistics. In Business of Apps. https://www.businessofapps.com/data/tik-tok-statistics/
Joo, J. (2016). Exploring Korean Collegians’ Smartphone Game Behavior: Focusing on Conciseness, Perceived Ease of Use, Perceived Enjoyment, Flow, and Intent to Use. Journal of Digital Convergence, 14(1), 379–386. DOI:
Jung, H., & Zhou, Q. (2019). Learning and Sharing Creative Skills with Short Videos: A Case Study of User Behavior in TikTok and Bilibili. International Association of Societies of Design Research Conference, 10, 25–50. https://www.researchgate.net/publication/335335984
Jung, Y., Perez-Mira, B., & Wiley-Patton, S. (2009). Consumer adoption of mobile TV: Examining psychological flow and media content. Computers in Human Behavior, 25(1), 123–129. DOI:
Kamboj, S., Sarmah, B., Gupta, S., & Dwivedi, Y. (2018). Examining branding co-creation in brand communities on social media: Applying the paradigm of Stimulus-Organism-Response. International Journal of Information Management, 39, 169–185. DOI:
Khang, H., Kim, J. K., & Kim, Y. (2013). Self-traits and motivations as antecedents of digital media flow and addiction: The Internet, mobile phones, and video games. Computers in Human Behavior, 29(6), 2416–2424. DOI:
Kim, H. W., Xu, Y., Koh, J., Kim, J., Lee, J., & Choi, D. (2003). A Comparison of Online Trust Building Factors between Potential Customers and Repeat Customers. Journal of the Association for Information Systems, 5(6), 392–420.
Kim, Y. J., & Han, J. (2014). Why smartphone advertising attracts customers: A model of Web advertising, flow, and personalization. Computers in human behavior, 33, 256-269.
Lee, C. H., Chiang, H. S., & Hsiao, K. L. (2018). What drives stickiness in location-based AR games? An examination of flow and satisfaction. Telematics and Informatics, 35(7), 1958-1970. DOI:
Liang, C. J., & Chen, H. J. (2009). A study of the impacts of website quality on customer relationship performance. Total Quality Management and Business Excellence, 20(9), 971–988. DOI:
Liao, C., Palvia, P., & Chen, J. L. (2009). Information technology adoption behavior life cycle: Toward a Technology Continuance Theory (TCT). International Journal of Information Management, 29(4), 309–320. DOI:
Luqman, A., Cao, X., Ali, A., Masood, A., & Yu, L. (2017). Empirical investigation of Facebook discontinues usage intentions based on SOR paradigm. Computers in Human Behavior, 70, 544–555. DOI:
Luqman, A., Masood, A., Weng, Q., Ali, A., & Rasheed, M. I. (2020). Linking Excessive SNS Use, Technological Friction, Strain, and Discontinuance: The Moderating Role of Guilt. Information Systems Management, 37(2), 94–112. DOI:
Ma, Y., Ruangkanjanases, A., & Chen, S. C. (2019). Investigating the impact of critical factors on continuance intention towards cross-border shopping websites. Sustainability (Switzerland), 11(21). DOI:
McKinney, V., Yoon, K., & Zahedi, F. (2002). The measurement of Web-customer satisfaction: An expectation and disconfirmation approach. Information Systems Research, 13(3), 296–315. DOI:
Mehrabian, A., & Russell, J. A. (1974). An Approach to Environmental Psychology. 266.
Moqbel, M. (2020). Understanding the Relationship between Smartphone Addiction and Well-Being: The Mediation of Mindfulnessand Moderation of Hedonic Apps. Proceedings of the 53rd Hawaii International Conference on System Sciences, 3, 6083–6092. DOI:
Mou, J. B. (2020). Study on Social Media Marketing Campaign Strategy-TikTok and Instagram. MIT Sloan School of Management, 3(8), 1–41.
Ngai, E. W. T., Tao, S. S. C., & Moon, K. K. L. (2015). Social media research: Theories, constructs, and conceptual frameworks. International Journal of Information Management, 35(1), 33–44. DOI:
Novak, T. P., Hoffman, D. L., & Yung, Y. F. (2000). Measuring the customer experience in online environments: A structural modeling approach. Marketing Science, 19(1), 22–42. DOI:
Omar, B., & Dequan, W. (2020). Watch, share or create: The influence of personality traits and user motivation on TikTok mobile video usage. International Journal of Interactive Mobile Technologies, 14(4), 121–137. DOI:
Rahi, S., Khan, M. M., & Alghizzawi, M. (2020). Extension of technology continuance theory (TCT) with task technology fit (TTF) in the context of Internet banking user continuance intention. International Journal of Quality and Reliability Management. DOI:
Salehan, M., & Negahban, A. (2013). Social networking on smartphones: When mobile phones become addictive. Computers in Human Behavior, 29(6), 2632–2639. DOI:
Sun, W., Cai, Z., Li, Y., Liu, F., Fang, S., & Wang, G. (2018). Data processing and text mining technologies on electronic medical records: A review. Journal of Healthcare Engineering, 2018. DOI:
Teo, T. S. H., Srivastava, S. C., & Jiang, L. (2008). Trust and electronic government success: An empirical study. Journal of Management Information Systems, 25(3), 99–132. DOI:
Triantoro, T., Gopal, R., Benbunan-Fich, R., & Lang, G. (2019). Would you like to play? A comparison of a gamified survey with a traditional online survey method. International Journal of Information Management, 49, 242–252. DOI:
Weimann, G., & Masri, N. (2020). Research Note: Spreading Hate on TikTok. In Studies in Conflict and Terrorism. DOI:
Weinstein, A., & Lejoyeux, M. (2010). Internet addiction or excessive internet use. American Journal of Drug and Alcohol Abuse, 36(5), 277–283. DOI:
Whelan, E., Islam, A. K. M. N., & Brooks, S. (2020). Applying the SOBC paradigm to explain how social media overload affects academic performance. Computers and Education, 143(August 2019), 103692. DOI:
Xu, L., Yan, X., & Zhang, Z. (2019). Research on the Causes of the “Tik Tok” App Becoming Popular and the Existing Problems. Journal of Advanced Management Science, 7(2), 59–63. DOI:
Zaman, M., Anandarajan, M., & Dai, Q. (2010). Experiencing flow with instant messaging and its facilitating role on creative behaviors. Computers in Human Behavior, 26(5), 1009–1018. DOI:
Zhang, H., Lu, Y., Gupta, S., & Zhao, L. (2014). What motivates customers to participate in social commerce? the impact of technological environments and virtual customer experiences. Information and Management, 51(8), 1017–1030. DOI:
Zhang, H., Lu, Y., Wang, B., & Wu, S. (2015). The impacts of technological environments and co-creation experiences on customer participation. Information and Management, 52(4), 468–482. DOI:
Zhang, K., Min, Q., Liu, Z., & Liu, Z. (2016). Understanding microblog continuance usage intention: an integrated model. Aslib Journal of Information Management, 68(6), 772–792. DOI:
Zhang, X., Wu, Y., & Liu, S. (2019). Exploring short-form video application addiction: Socio-technical and attachment perspectives. Telematics and Informatics, 42(April), 101243. DOI:
Zheng, X., & Lee, M. K. O. (2016). Excessive use of mobile social networking sites: Negative consequences on individuals. Computers in Human Behavior, 65, 65–76. DOI:
Zhou, T. (2014). Understanding continuance usage intention of mobile internet sites. Universal Access in the Information Society, 13(3), 329–337. DOI:
Zhou, T., Li, H., & Liu, Y. (2010). The effect of flow experience on mobile SNS users’ loyalty. Industrial Management and Data Systems, 110(6), 930–946. DOI:
Copyright information

About this article
Publication date.
31 January 2022
Article Doi
https://doi.org/10.15405/epsbs.2022.01.02.19
978-1-80296-122-5
European Publisher
Print ISBN (optional)
Edition number.
1st Edition
Communication, Media, Disruptive Era, Digital Era, Media Technology
Cite this article as:
Yao, Q., & Omar, B. (2022). TikTok Addiction Behaviour Among Users: A Conceptual Model and Research Propositions. In J. A. Wahab, H. Mustafa, & N. Ismail (Eds.), Rethinking Communication and Media Studies in the Disruptive Era, vol 123. European Proceedings of Social and Behavioural Sciences (pp. 231-243). European Publisher. https://doi.org/10.15405/epsbs.2022.01.02.19
We care about your privacy
We use cookies or similar technologies to access personal data, including page visits and your IP address. We use this information about you, your devices and your online interactions with us to provide, analyse and improve our services. This may include personalising content or advertising for you. You can find out more in our privacy policy and cookie policy and manage the choices available to you at any time by going to ‘Privacy settings’ at the bottom of any page.
Manage My Preferences
You have control over your personal data. For more detailed information about your personal data, please see our Privacy Policy and Cookie Policy .
These cookies are essential in order to enable you to move around the site and use its features, such as accessing secure areas of the site. Without these cookies, services you have asked for cannot be provided.
Third-party advertising and social media cookies are used to (1) deliver advertisements more relevant to you and your interests; (2) limit the number of times you see an advertisement; (3) help measure the effectiveness of the advertising campaign; and (4) understand people’s behavior after they view an advertisement. They remember that you have visited a site and quite often they will be linked to site functionality provided by the other organization. This may impact the content and messages you see on other websites you visit.
Advertisement
Read TikTok’s legal challenge
- Share full article
A PDF version of this document with embedded text is available at the link below:
Download the original document (pdf)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 1 of 70 IN THE UNITED STATES COURT OF APPEALS FOR THE DISTRICT OF COLUMBIA CIRCUIT TIKTOK INC., and BYTEDANCE LTD., V. ) Petitioners, No. 24-1113 MERRICK B. GARLAND, in his official capacity as Attorney General of the United States, (Page 1 of Total) Respondent. PETITION FOR REVIEW OF CONSTITUTIONALITY OF THE PROTECTING AMERICANS FROM FOREIGN ADVERSARY CONTROLLED APPLICATIONS ACT
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 2 of 70 2. That law 1. Congress has taken the unprecedented step of expressly singling out and banning TikTok: a vibrant online forum for protected speech and expression used by 170 million Americans to create, share, and view videos over the Internet. For the first time in history, Congress has enacted a law that subjects a single, named speech platform to a permanent, nationwide ban, and bars every American from participating in a unique online community with more than 1 billion people worldwide. the Protecting Americans From Foreign Adversary Controlled Applications Act (the "Act") is unconstitutional. Banning Tik Tok is so obviously unconstitutional, in fact, that even the Act's sponsors recognized that reality, and therefore have tried mightily to depict the law not as a ban at all, but merely a regulation of TikTok's ownership. According to its sponsors, the Act responds to TikTok's ultimate ownership by ByteDance Ltd., a company with Chinese subsidiaries whose employees support various Byte Dance businesses, including TikTok. They claim that the Act is not a ban because it offers Byte Dance a choice: divest TikTok's U.S. business or be shut down.1 ― - 1 References to "TikTok Inc." are to the specific U.S. corporate entity that is a Petitioner in this lawsuit and publishes the TikTok platform in the 1 (Page 2 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 3 of 70 3. But in reality, there is no choice. The "qualified divestiture" demanded by the Act to allow TikTok to continue operating in the United States is simply not possible: not commercially, not technologically, not legally. And certainly not on the 270-day timeline required by the Act. Petitioners have repeatedly explained this to the U.S. government, and sponsors of the Act were aware that divestment is not possible. There is no question: the Act will force a shutdown of TikTok by January 19, 2025, silencing the 170 million Americans who use the platform to communicate in ways that cannot be replicated elsewhere. 4. Of course, even if a "qualified divestiture" were feasible, the Act would still be an extraordinary and unconstitutional assertion of power. If upheld, it would allow the government to decide that a company may no longer own and publish the innovative and unique speech United States. References to "TikTok" are to the online platform, which includes both the Tik Tok mobile application and web browser experience. References to “ByteDance Ltd." are to the specific Cayman Islands- incorporated holding company that is identified in the Act and is a Petitioner in this lawsuit. References to "ByteDance" are to the ByteDance group, inclusive of ByteDance Ltd. and relevant operating subsidiaries. TikTok Inc. and ByteDance. Ltd. are together referred to as "Petitioners." (Page 3 of Total) 21
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 4 of 70 platform it created. If Congress can do this, it can circumvent the First. Amendment by invoking national security and ordering the publisher of any individual newspaper or website to sell to avoid being shut down. And for Tik Tok, any such divestiture would disconnect Americans from the rest of the global community on a platform devoted to shared content an outcome fundamentally at odds with the Constitution's commitment to both free speech and individual liberty. 5. There are good reasons why Congress has never before enacted a law like this. Consistent with the First Amendment's guarantee of freedom of expression, the United States has long championed a free and open Internet - and the Supreme Court has repeatedly recognized that speech "conveyed over the Internet” fully qualifies for “the First Amendment's protections." 303 Creative LLC v. Elenis, 600 U.S. 570, 587 (2023). And consistent with the fundamental principles of fairness and equal treatment rooted in the Bill of Attainder Clause and the Fifth Amendment, Congress has never before crafted a two-tiered speech regime with one set of rules for one named platform, and another set of rules for everyone else. (Page 4 of Total) 3
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 5 of 70 6. In dramatic contrast with past enactments that sought to regulate constitutionally protected activity, Congress enacted these extreme measures without a single legislative finding. The Act does not articulate any threat posed by Tik Tok nor explain why TikTok should be excluded from evaluation under the standards Congress concurrently imposed on every other platform. Even the statements by individual Members of Congress and a congressional committee report merely indicate concern about the hypothetical possibility that TikTok could be misused in the future, without citing specific evidence - even though the platform has operated prominently in the United States since it was first launched in 2017. Those speculative concerns fall far short of what is required when First Amendment rights are at stake. 7. Nor is there any indication that Congress considered any number of less restrictive alternatives, such as those that Petitioners developed with the Executive Branch after government agencies began evaluating the security of U.S. user data and the risk of foreign government influence over the platform's content as far back as 2019. While such concerns were never substantiated, Petitioners nevertheless (Page 5 of Total) 4
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 6 of 70 worked with the government for four years on a voluntary basis to develop a framework to address the government's concerns. 8. As part of this engagement, Petitioners have voluntarily invested more than $2 billion to build a system of technological and governance protections sometimes referred to as "Project Texas" - to help safeguard U.S. user data and the integrity of the U.S. TikTok platform against foreign government influence. Petitioners have also made extraordinary, additional commitments in a 90-page draft National Security Agreement developed through negotiations with the Committee on Foreign Investment in the United States ("CFIUS”), including agreeing to a “shut-down option” that would give the government the authority to suspend TikTok in the United States if Petitioners violate certain obligations under the agreement. 9. Congress tossed this tailored agreement aside, in favor of the politically expedient and punitive approach of targeting for disfavor one publisher and speaker (TikTok Inc.), one speech forum (TikTok), and that forum's ultimate owner (ByteDance Ltd.). Through the Act's two-tiered. structure, Congress consciously eschewed responsible industry-wide. regulation and betrayed its punitive and discriminatory purpose. 5 (Page 6 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 7 of 70 Congress provided every other company however serious a threat to - national security it might pose - paths to avoiding a ban, excluding only Tik Tok Inc. and ByteDance Ltd. Indeed, for any other company's application to be banned, Congress mandated notice and a "public report" describing "the specific national security" concern, accompanied by supporting classified evidence. For Petitioners only, however, there is no statement of reasons and no supporting evidence, with any discussion of the justifications for a ban occurring only behind closed doors. 10. Congress must abide by the dictates of the Constitution even when it claims to be protecting against national security risks: “against [those] dangers ... as against others, the principle of the right to free speech is always the same." Abrams v. United States, 250 U.S. 616, 628 (1919) (Holmes, J., dissenting). Congress failed to do so here, and the Act should be enjoined. 11. Jurisdictional Statement Pursuant to Sections 3(a) and 3(b) of the Act, H.R. 815, div. H, 118th Cong., Pub. L. No. 118-50 (April 24, 2024), this Court has original (Page 7 of Total) 6
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 8 of 70 and exclusive jurisdiction over this challenge to the constitutionality of the Act. 2 A. 12. Background and Nature of Proceedings TikTok Is a Speech Platform Used by 170 Million Americans. Tik Tok is an online video entertainment platform designed to provide a creative and entertaining forum for users to express themselves and make connections with others over the Internet. More than 170 million Americans use TikTok every month, to learn about and share information on a range of topics from entertainment, to religion, to - politics. Content creators use the TikTok platform to express their opinions, discuss their political views, support their preferred political candidates, and speak out on today's many pressing issues, all to a global audience of more than 1 billion users. Many creators also use the 2 A copy of the Act is attached to this Petition as Exhibit A. Because this Petition does not involve a challenge to any agency action, it is not governed by Federal Rule of Appellate Procedure 15(a). Petitioners intend to file a separate motion regarding the procedures governing this original proceeding. Petitioners summarize the pertinent facts and claims below to facilitate this Court's review consistent with the practice of a case-initiating pleading in a court of original jurisdiction, but reserve their rights to present additional facts and arguments in due course. 7 (Page 8 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 9 of 70 platform to post product reviews, business reviews, and travel information and reviews. 13. In the United States, the TikTok platform is provided by Tik Tok Inc., a California-incorporated company that has its principal place of business in Culver City, California and offices in New York, San Jose, Chicago, and Miami, among other locations. TikTok Inc. has thousands of employees in the United States. Like many platforms owned by companies that operate globally, the global TikTok platform is supported not only by those employees, but also by employees of other ByteDance subsidiaries around the globe, including in Singapore, the United Kingdom, Brazil, Germany, South Africa, Australia, and China. Many of the global TikTok platform's functions are spread across different corporate entities and countries, and the global TikTok business is led by a leadership team based in Singapore and the United States. Like other U.S. companies, TikTok Inc. is governed by U.S. law. 14. Tik Tok Inc.'s ultimate parent company is ByteDance Ltd., a Cayman Islands-incorporated equity holding company. Byte Dance was founded in 2012 by Chinese entrepreneurs. Over time, the company sought funding to fuel growth, as is common in the technology sector, 8 (Page 9 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 10 of 70 which resulted in the issuance of additional equity and the dilution of existing shares. Today, approximately 58 percent of ByteDance Ltd. is owned by global institutional investors (such as BlackRock, General Atlantic, and Susquehanna International Group), 21 percent is owned by the company's founder (a Chinese national who lives in Singapore), and 21 percent is owned by employees including approximately 7,000 Americans. 15. ByteDance launched TikTok in May 2017 in over 150 countries, including the United States.³ Since its launch, TikTok has become one of the world's most popular applications, with over 1 billion users worldwide. As of January 2024, more than 170 million Americans use TikTok on a monthly basis. 16. Users primarily view content on TikTok through its "For You" page, which presents a collection of videos curated by TikTok's proprietary recommendation engine. The recommendation engine customizes each user's content feed based on how the user interacts with 3 Tik Tok was later relaunched in August 2018 following a transaction involving the company Musical.ly. See generally Petition for Review, Tik Tok Inc. v. CFIUS, No. 20-1444 (D.C. Cir. Nov. 10, 2020). 9 (Page 10 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 11 of 70 the content that the user watches. TikTok's popularity is based in large part on the effectiveness of the recommendation engine. The source code for TikTok's recommendation engine was originally developed by ByteDance engineers based in China, and the engine is customized for operations in TikTok's various global markets, including in the United States. TikTok is not offered in mainland China. 17. Aside from TikTok, ByteDance has developed and operates more than a dozen other online platforms and software applications for use in U.S. and international markets, including for content-sharing, video and music editing, e-commerce, gaming, and enterprise productivity. B. 18. The Government Previously Made Unlawful Attempts to Ban TikTok. Petitioners' efforts to address the U.S. government's asserted concerns regarding the TikTok platform date back to 2019. At that time, Petitioners began engaging with CFIUS, which had initiated a review of ByteDance Ltd.'s 2017 acquisition of Musical.ly, another Internet-based video-sharing platform. (Page 11 of Total) 10
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 12 of 70 19. Petitioners were in the early stages of engaging with CFIUS on a voluntary basis to address the government's concerns, when on August 6, 2020, President Trump abruptly issued an executive order purporting to ban TikTok under the International Emergency Economic Powers Act ("IEEPA”), 50 U.S.C. §§ 1701-08. See 85 Fed. Reg. 48,637 (the "Ban Order"). Two separate district courts preliminarily enjoined the Ban Order, concluding (among other things) that it exceeded the President's IEEPA authority. TikTok Inc. v. Trump, 490 F. Supp. 3d 73, 83 (D.D.C. 2020); TikTok Inc. v. Trump, 507 F. Supp. 3d 92, 112 (D.D.C. 2020); Marland v. Trump, 498 F. Supp. 3d 624, 641 (E.D. Pa. 2020). 20. Specifically, as these courts correctly recognized, the President's IEEPA authority "to deal with any unusual and extraordinary threat" to the nation “does not include the authority to regulate or prohibit, directly or indirectly ... [any] personal communication” or the importation or exportation “of any information or informational materials.” 50 U.S.C. § 1702(b)(1), (3). These restrictions on the President's IEEPA authority-which Congress expanded through multiple amendments to the statute were designed “to prevent the statute from running afoul of the First Amendment.” United States v. 11 (Page 12 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 13 of 70 Amirnazmi, 645 F.3d 564, 585 (3d Cir. 2011) (quotation marks omitted); see also Kalantari v. NITV, Inc., 352 F.3d 1202, 1205 (9th Cir. 2003) (IEEPA's limitations necessary “to prevent the executive branch from restricting the international flow of materials protected by the First. Amendment"); Marland, 498 F. Supp. 3d at 629 (same). 21. Looking to the foundational First Amendment principles codified in IEEPA's text and legislative history, these courts concluded that President Trump's efforts to ban TikTok violated the statute and raised "serious" constitutional questions (which were unnecessary to decide under the doctrine of constitutional avoidance). Tik Tok Inc., 507 F. Supp. 3d at 112 n.6; TikTok Inc., 490 F. Supp. 3d at 83 n.3. The courts granted the government's motions to voluntarily dismiss its appeals after President Biden withdrew the Ban Order. See Tik Tok Inc. v. Biden, No. 20-5302, 2021 WL 3713550 (D.C. Cir. July 20, 2021); Tik Tok Inc. v. Biden, No. 20-5381, 2021 WL 3082803 (D.C. Cir. July 14, 2021); Marland v. Trump, No. 20-3322, 2021 WL 5346749 (3d Cir. July 14, 2021). 22. Separately, acting on a CFIUS referral, President Trump on August 14, 2020 issued an order under Section 721 of the Defense Production Act, 50 U.S.C. § 4565, purporting to direct ByteDance to 12 (Page 13 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 14 of 70 divest from TikTok's U.S. business and U.S. user data. 85 Fed. Reg. 51,297 (the "Divestment Order"). On November 10, 2020, Petitioners petitioned this Court for review of the Divestment Order and underlying CFIUS actions, arguing, among other things, that the government lacked jurisdiction under the statute. See Petition for Review, TikTok Inc. v. CFIUS, No. 20-1444 (D.C. Cir. Nov. 10, 2020). That petition was held in abeyance in February 2021 on the parties' joint motion to allow the parties to negotiate a resolution. The government has filed status reports every 60 days since then, most recently on April 22, 2024. Those status reports have consistently reported that “[t]he parties continue to be involved in ongoing negotiations” and “[a] beyance continues to be appropriate.” See, e.g., Status Report, Tik Tok Inc. v. CFIUS, No. 20-1444 (D.C. Cir. Apr. 22, 2024). 23. Between January 2021 and August 2022, Petitioners and CFIUS engaged in an intensive, fact-based process to develop a National Security Agreement that would resolve the U.S. government's concerns about whether Chinese authorities might be able to access U.S. user data or manipulate content on TikTok, as well as resolve the pending CFIUS During that time, Petitioners and government officials dispute. 13 (Page 14 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 15 of 70 communicated regularly, often several times a week - including several - in-person meetings about the government's concerns and potential solutions. The result was an approximately 90-page draft National Security Agreement with detailed annexes embodying a comprehensive solution addressing the government's national security concerns. Notably, the draft National Security Agreement provided that all protected U.S. user data (as defined in the agreement) would be stored in the cloud environment of a U.S.-government-approved partner, Oracle Corporation, which would also review and vet the TikTok source code. 24. From Petitioners' perspective, all indications were that they were nearing a final agreement. After August 2022, however, CFIUS without explanation stopped engaging with Petitioners in meaningful discussions about the National Security Agreement. Petitioners repeatedly asked why discussions had ended and how they might be restarted, but they did not receive a substantive response. In March 2023, without providing any justification for why the draft National Security Agreement was inadequate, CFIUS insisted that Byte Dance would be required to divest the U.S. TikTok business. (Page 15 of Total) 14
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 16 of 70 25. Since March 2023, Petitioners have explained to CFIUS, in multiple written communications and in-person meetings, that a divestiture of the U.S. TikTok business from the rest of the integrated global Tik Tok platform and business of the sort now required by the Act is not feasible. CFIUS has never articulated any basis for disagreeing with that assessment, offering instead only a conclusory assertion that the reason ByteDance was not divesting was because it was simply unwilling to do so. The Act nonetheless incorporates precisely such an infeasible divestiture standard. C. 26. A Divestiture that Severs TikTok's U.S. Operations From the Rest of the Globally Integrated TikTok Business Is Not Commercially, Technologically, or Legally Feasible. The Act purports to allow Petitioners to avoid a ban by executing a "qualified divestiture." Sec. 2(c). But that alternative is illusory because, as Petitioners have repeatedly explained to CFIUS, the divestiture of the TikTok U.S. business and its severance from the globally integrated platform of which it is an integral part is not commercially, technologically, or legally feasible. (Page 16 of Total) 15
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 17 of 70 - 27. First, a standalone U.S. TikTok platform would not be commercially viable. TikTok and its competitors are globally integrated platforms where content created in one country is available to users in other countries. Indeed, a substantial part of TikTok's appeal is the richness of the international content available on the platform from global sporting events like the Olympics to international K-pop stars from South Korea, as well as videos created by U.S. creators and enjoyed by audiences worldwide. A divestment of the U.S. TikTok platform, without any operational relationship with the remainder of the global platform, would preclude the interoperability necessary to make international content seamlessly available in the U.S. market and vice versa. As a result, the U.S. TikTok platform would become an “island” where Americans would have an experience detached from the rest of the global platform and its over 1 billion users. Such a limited pool of content, in turn, would dramatically undermine the value and viability of the U.S. TikTok business.4 4 The contemplated qualified divestiture would also undercut the important role currently played by American voices in the global conversation ongoing on TikTok. 16 (Page 17 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 18 of 70 28. Second, precipitously moving all TikTok source code development from ByteDance to a new Tik Tok owner would be impossible as a technological matter. The platform consists of millions of lines of software code that have been painstakingly developed by thousands of engineers over multiple years. Although much of this code is basic infrastructure for running the global TikTok platform and has nothing at all to do with TikTok's recommendation algorithm, the statute requires that all of this code be wrested from Petitioners, so that there is no “operational relationship" between ByteDance and the new U.S. platform. Specifically, to comply with the law's divestiture requirement, that code base would have to be moved to a large, alternative team of engineers a team that does not exist and would have no understanding of the complex code necessary to run the platform. It would take years for an entirely new set of engineers to gain sufficient familiarity with the source code to perform the ongoing, necessary maintenance and development activities for the platform. Moreover, to keep the platform functioning, these engineers would need access to ByteDance software tools, which the Act prohibits. Such a fundamental rearchitecting is not - (Page 18 of Total) 17
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 19 of 70 remotely feasible on anything approaching the 270-day timeframe contemplated by the Act. 29. Third, the Chinese government has made clear that it would not permit a divestment of the recommendation engine that is a key to the success of TikTok in the United States. Like the United States,5 China regulates the export of certain technologies originating there. China's export control rules cover “information processing technologies” such as "personal interactive data algorithms.”6 China's official news agency has reported that under these rules, any sale of recommendation algorithms developed by engineers employed by ByteDance subsidiaries in China, including for TikTok, would require a government license. 5 For example, the U.S. Department of Commerce has issued restrictions on the export to China of advanced chips that can be used to train artificial intelligence models. E.g., Implementation of Additional Export Controls: Certain Advanced Computing Items; Supercomputer and Semiconductor End Use; Updates and Corrections, 88 Fed. Reg. 73458 (Oct. 25, 2023) (to be codified at 15 C.F.R. § 732.2 et seq.). 6 See Karen M. Sutter, Cong. Rsch. Serv., IN11524, China Issues New Export Control Law and Related Policies 2 (2020). 7 Paul Mozur, Raymond Zhong & David McCabe, Tik Tok Deal Is Complicated by New Rules From China Over Tech Exports, N.Y. Times (Aug. 29, 2020), https://perma.cc/L6RB-CTT9. 18 (Page 19 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 20 of 70 China also enacted an additional export control law that "gives the Chinese government new policy tools and justifications to deny and impose terms on foreign commercial transactions."8 China adopted these enhanced export control restrictions between August and October 2020, shortly after President Trump's August 6, 2020 and August 14, 2020 executive orders targeting TikTok. By doing so, the Chinese government clearly signaled that it would assert its export control powers with respect to any attempt to sever TikTok's operations from ByteDance, and that any severance would leave TikTok without access to the recommendation engine that has created a unique style and community that cannot be replicated on any other platform today. D. 30. The Act Bans TikTok and Other Byte Dance Applications. On April 24, 2024, the President signed the Protecting Americans from Foreign Adversary Controlled Applications Act. 31. The Act prohibits, on pain of draconian penalties, “online mobile application store[s]" and "internet hosting services" from servicing "foreign adversary controlled application[s]" within the United States. 8 Sutter, supra n.6. 19 (Page 20 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 21 of 70 See Sec. 2(a), 2(d)(1)(A). This includes the "distribution, maintenance, or updating" of a covered application through an online marketplace. Sec. 2(a)(1). 32. Section 2(g) (3) creates two classes of "foreign adversary controlled applications" covered by the Act. 33. The first class singles out only one corporate group: "Byte Dance[] Ltd.,” “TikTok,” their “subsidiar[ies] or successor[s]" that are "controlled by a foreign adversary," or any entity "owned or controlled" by the aforementioned.9 The Act deems any application. operated by these entities a “foreign adversary controlled application," without any finding about why any particular application much less - - every application operated by these entities should be so designated. See Sec. 2(g)(3)(A). 9 “TikTok” is a platform, not a legal entity. Petitioners assume that Congress intended this provision to be a reference to TikTok Inc., and further reserve their rights to amend this Petition to include additional Tik Tok entities to the extent the government takes the position that other entities are covered by this reference. In any event, TikTok Inc. is covered as an entity “owned or controlled" by ByteDance Ltd. 20 (Page 21 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 22 of 70 34. The second class creates a discretionary process by which the President can designate other companies whose applications will also effectively be banned. Under these provisions, the President may designate an application as a "foreign adversary controlled application" if several qualifications are met: a. Covered Company. The website or application is operated directly or indirectly by a "covered company" - i.e., a company that operates a website or application that permits users to share content and has at least 1 million monthly active users. See Sec. 2(g)(2)(A). b. Controlled by a Foreign Adversary. The "covered company" operating the website or application must also be "controlled by a foreign adversary," meaning it is "headquartered in, has its principal place of business in, or is organized under the laws" of a "foreign adversary country," which currently includes China, North Korea, Russia, and Iran. Sec. 2(g)(1)(A), (g)(4); see also 10 U.S.C. § 4872(d)(2). A company may also be "controlled by a foreign adversary" if persons domiciled in any of the 21 (Page 22 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 23 of 70 (Page 23 of Total) specified countries (i.e., China, Iran, Russia, or North Korea) directly or indirectly own at least 20 percent of the company. Sec. 2(g)(1)(B). c. Not Exempt under Sec. 2(g)(2)(B). But Congress specifically exempted from the term “covered company" any "entity that operates" a website or application "whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews." An entity that operates a single website or application of this nature thus cannot be a “covered company,” even if it is "controlled by a foreign adversary," poses a significant national security risk, and separately operates an application whose primary purpose is anything other than allowing users to post reviews. Sec. 2(g)(2)(B). d. Presidential Determination, Notice and Report, and Judicial Review. Finally, the President must determine that such a company presents “a significant threat to the national security of the United States." Sec. 2(g)(3)(B)(ii). Before making such a determination, the President must 22
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 24 of 70 issue public notice proposing the determination and then provide a public report to Congress describing "the specific national security concern involved," supplemented by a classified annex, and also explain "what assets would need to be divested to execute a qualified divestiture." Id. These presidential determinations are then subject to judicial review. Sec. 3(a). 35. Section 2(c) exempts a "foreign adversary controlled application[]" from the Act's prohibitions if the company that operates the application executes a “qualified divestiture." Sec. 2(c). The President must determine that such divestiture would (1) "result in the relevant covered company no longer being controlled by a foreign adversary," and (2) “preclude[] the establishment or maintenance of any operational relationship" between the application's U.S. operations and any formerly affiliated entities that are controlled by a foreign adversary, including "any cooperation with respect to the operation of a content. recommendation algorithm." Sec. 2(c), (g) (6). As noted above, the Act's broad definition of "controlled by a foreign adversary" includes, among other things, any entity organized under the laws of a "foreign adversary 23 (Page 24 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 25 of 70 country," or any entity in which a foreign person domiciled in a foreign adversary country holds at least a 20 percent ownership stake. Sec. 2(g)(1), (3)(B)(i), (4). 36. The prohibition on providing Internet hosting and mobile application store services to TikTok and other ByteDance applications. takes effect 270 days after enactment. Sec. 2(a)(2)(A). The President may extend this deadline, but only for 90 days maximum, and only if the President certifies to Congress that a path to executing a qualified divestiture has been identified, evidence of significant progress toward executing that qualified divestiture has been produced, and the relevant binding legal agreements to enable execution of the qualified divestiture are in place. 37. "Before the date on which [this] prohibition" takes effect, Petitioners are required to provide, upon request by any U.S. user of any of their applications, “all the available data related to the account of such user with respect to such application." Sec. 2(b).10 10 Because Section 2(b)'s data portability requirement applies "[b]efore" the prohibition under Section 2(a) takes effect, it cannot be "given effect" without Section 2(a) for purposes of Section 2(e)(1) of the Act, which provides that "[i]f any provision of this section or the application of this 24 (Page 25 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 26 of 70 38. Because the Act lacks any legislative findings or a statement of purpose, Petitioners and the more than 170 million American monthly users of TikTok are left to scrutinize statements from individual Members of Congress and other sources to try to discern any purported justification for this extraordinary intrusion on free speech rights. Based on these sources, it appears at least some Members of Congress sought to address "two threats" that could emerge from foreign ownership of communications platforms. 11 39. First, they may have sought to protect U.S. users' “data security."12 According to the House Committee Report for an earlier version of the Act, mobile applications, including those that are not section to any person or circumstance is held invalid, the invalidity shall not affect the other provisions or applications of this section that can be given effect without the invalid provision or application." Because Section 2(a) violates the Constitution for the reasons set forth herein, Section 2(b) is accordingly "not operative in the absence of the unconstitutional provision.” Barr v. Am. Ass'n of Pol. Consultants, Inc., 140 S. Ct. 2335, 2352 n.9 (2020). 11 Jane Coaston, What the Tik Tok Bill Is Really About, According to a Leading Republican, N.Y. Times (Apr. 1, 2024), https://perma.cc/BL32- 786X (quoting the Act's original sponsor, Rep. Mike Gallagher). 12 Id. (Page 26 of Total) 25
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 27 of 70 controlled by foreign adversaries, can “collect vast amounts of data on Americans."13 The House Committee Report expressed a concern that such data could be used by a foreign adversary to "conduct espionage campaigns," such as by tracking specific individuals. 14 40. Second, others in Congress appear to have been motivated by a "greater concern": an alleged "propaganda threat." 15 One proponent of the Act stated that communications applications could be used to "push misinformation, disinformation, and propaganda on the American public."16 Another supporter claimed in the House Select Committee press release accompanying the bill's introduction that “[TikTok] is ... poisoning the minds of our youth every day on a massive scale."17 13 H.R. Comm. on Energy & Com., Protecting Americans from Foreign Adversary Controlled Applications Act, H.R. Rep. No. 118-417 at 2 (2024) (hereinafter the "House Committee Report"). 14 Id. 15 Coaston, supra n.11 (quoting Rep. Gallagher). 16 House Committee Report at 2. 17 Press Release, U.S. House Select Comm. on Strategic Competition Between the U.S. and the Chinese Communist Party, Gallagher, Bipartisan Coalition Introduce Legislation to Protect Americans From Foreign Adversary Controlled Applications, Including TikTok (Mar. 5, 2024), https://perma.cc/KC5T-6AX3. (Page 27 of Total) 26
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 28 of 70 E. Congress Disregarded Alternatives to Banning TikTok, Such as the National Security Measures Petitioners Negotiated with the Executive Branch. 41. Petitioners have demonstrated a commitment to addressing both of those concerns without the need to resort to the drastic, unconstitutional step of shuttering one of the most widely used forums for speech in the United States. The 90-page draft National Security Agreement that Petitioners developed with Petitioners developed with CFIUS would, if implemented, provide U.S. TikTok users with protections more robust than those employed by any other widely used online platform in the industry. 42. The draft National Security Agreement contains several means of ensuring data security without banning TikTok. All protected U.S. user data (as defined in the National Security Agreement) would be safeguarded in the United States under a special corporate structure: TikTok U.S. Data Security (a new subsidiary of Tik Tok Inc.). A special board, with Security Directors whose appointment would be subject to the U.S. government's approval, would oversee TikTok U.S. Data Security, and in turn exclude ByteDance and all of its other subsidiaries and affiliates from such responsibilities. Further separation between the 27 (Page 28 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 29 of 70 U.S. TikTok business and Byte Dance subsidiaries and affiliates, including TikTok in the rest of the world, would be achieved by appointing a U.S.-government-approved Security Director to the board of Tik Tok Inc. Protected U.S. user data would be stored in the cloud environment of a U.S.-government-approved partner, Oracle Corporation, with access to such data managed by TikTok U.S. Data Security. 43. The draft Agreement would also protect against the concern about content manipulation and propaganda. Multiple layers of protection address concerns related to content available on the TikTok platform, including ensuring that all content moderation - both human and algorithmic ➖ would be subject to third-party verification and monitoring. The concern about content manipulation would also be addressed by securing all software code through Oracle Corporation, a U.S. trusted technology provider. The Tik Tok U.S. platform and application would be deployed through the Oracle cloud infrastructure and subject to source code review and vetting by Oracle with another U.S.-government-approved third party responsible for conducting security inspections. As part of this process, Oracle and third parties 28 (Page 29 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 30 of 70 approved by CFIUS would conduct independent inspections of the Tik Tok recommendation engine. 44. The draft Agreement also includes strict penalties for noncompliance, including a "shut-down option," giving the government the authority to suspend TikTok in the United States in response to specified acts of noncompliance. The Agreement also provides significant monetary penalties and other remedies for noncompliance. 45. Although the government has apparently abandoned the draft National Security Agreement, Petitioners have not. TikTok Inc. has begun the process of voluntarily implementing the National Security Agreement's provisions to the extent it can do so without the U.S. government's cooperation, including by incorporating and staffing the TikTok U.S. Data Security entity, and by partnering with Oracle Corporation on the migration of the U.S. platform and protected U.S. user data to Oracle's cloud environment. 46. To date, Petitioners have spent more than $2 billion to implement these measures and resolve the very concerns publicly expressed by congressional supporters of the Act all without the overbroad and unconstitutional method of an outright ban. 29 (Page 30 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 31 of 70 Grounds On Which Relief Is Sought Petitioners seek review of the constitutionality of the Act on grounds that include, without limitation, the following. Ground 1: Violation of the First Amendment 47. The First Amendment to the U.S. Constitution provides that "Congress shall make no law. . . abridging the freedom of speech." U.S. Const., amend. I. 48. By banning all online platforms and software applications offered by "TikTok" and all ByteDance subsidiaries, Congress has made a law curtailing massive amounts of protected speech. Unlike broadcast television and radio stations, which require government licenses to operate because they use the public airwaves, the government cannot, consistent with the First Amendment, dictate the ownership of newspapers, websites, online platforms, and other privately created. speech forums. 49. Indeed, in the past, Congress has recognized the importance of protecting First Amendment rights, even when regulating in the interest of national security. For example, Congress repeatedly amended IEEPA which grants the President broad authority to address national 30 (Page 31 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 32 of 70 emergencies that pose "unusual and extraordinary threat[s]" to the country to expand protections for constitutionally protected materials. 50 U.S.C. §§ 1701-02. Accordingly, under IEEPA, the President does not have the authority to even indirectly regulate "personal communication" or the importation or exportation "of any information or informational materials,” id. § 1702(b)(1), (3) limitations that are necessary "to prevent the statute from running afoul of the First Amendment," Amirnazmi, 645 F.3d at 585. Yet Congress has attempted to sidestep these statutory protections aimed at protecting Americans' constitutional rights, preferring instead to simply enact a new statute that tries to avoid the constitutional limitations on the government's existing statutory Those statutory protections were evidently seen as an impediment to Congress's goal of banning TikTok, so the Act dispensed authority. with them. 50. The Act's alternative to a ban a so-called “qualified - - divestiture" is illusory to the point of being no alternative at all. As explained above, divesting TikTok Inc.'s U.S. business and completely severing it from the globally integrated platform of which it is a part is not commercially, technologically, or legally feasible. 31 (Page 32 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 33 of 70 51. The Act will therefore have the effect of shutting down TikTok in the United States, a popular forum for free speech and expression used by over 170 million Americans each month. And the Act will do so based not on any proof of a compelling interest, but on speculative and analytically flawed concerns about data security and content manipulation concerns that, even if grounded in fact, could be - addressed through far less restrictive and more narrowly tailored means. 52. Petitioners' protected speech rights. The Act burdens Tik Tok Inc.'s First Amendment rights in addition to the free speech - rights of millions of people throughout the United States in two ways. - 53. First, Petitioner TikTok Inc. has a First Amendment interest in its editorial and publishing activities on TikTok. See Hurley v. Irish- Am. Gay, Lesbian & Bisexual Grp. of Bos., 515 U.S. 557, 570 (1995). TikTok “is more than a passive receptacle or conduit for news, comment, and advertising" of others; TikTok Inc.'s "choice of material" to recommend or forbid “constitute[s] the exercise of editorial control and judgment" that is protected by the First Amendment. Miami Herald Pub. Co. v. Tornillo, 418 U.S. 241, 258 (1974); see also Alario v. Knudsen, (Page 33 of Total) 32
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 34 of 70 - F. Supp. 3d, 2023 WL 8270811, at *6 (D. Mont. Nov. 30, 2023) (recognizing Tik Tok Inc.'s First Amendment editorial rights). 54. As the government itself has acknowledged, “[w]hen [social media] platforms decide which third-party content to present and how to present it, they engage in expressive activity protected by the First Amendment because they are creating expressive compilations of speech." Br. for United States as Amicus Curiae at 12-13, Moody v. NetChoice LLC, No. 22-277 (U.S.), 2023 WL 8600432; see also id. at 18- 19, 25-26. 55. Second, Tik Tok Inc. is among the speakers whose expression the Act prohibits. TikTok Inc. uses the TikTok platform to create and share its own content about issues and current events, including, for example, its support for small businesses, Earth Day, and literacy and education. 18 When TikTok Inc. does so, it is engaging in core speech protected by the First Amendment. See Sorrell v. IMS Health Inc., 564 18 Tik Tok (@tiktok), TikTok, https://www.tiktok.com/t/ZTL9QsTYs/ (last visited May 6, 2024); TikTok (@tiktok), TikTok, https://www.tiktok.com/t/ZTL9QbSHv/ (last visited May 6, 2024); TikTok (@tiktok), TikTok, https://www.tiktok.com/t/ZTL9QXE7R/ (last visited May 6, 2024). (Page 34 of Total) 33
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 35 of 70 U.S. 552, 570 (2011); NetChoice, LLC v. Att'y Gen., Fla., 34 F.4th 1196, 1210 (11th Cir. 2022), cert. granted, 144 S. Ct. 478 (2023). The Act precludes TikTok Inc. from expressing itself over that platform. 56. Even if the U.S. TikTok platform could be divested, which it cannot for the reasons explained above, TikTok Inc.'s protected speech rights would still be burdened. Because the Act appears to conclusively determine that any application operated by "TikTok" - a term that — Congress presumably meant to include Tik Tok Inc. is a foreign adversary controlled application, Sec. 2(g)(3)(A), the President appears to lack the power to determine that a TikTok Inc.-owned application is "no longer being controlled by a foreign adversary" and has no “operational relationship" with “formerly affiliated entities that are controlled by a foreign adversary," Sec. 2(g)(6)(A) & (B). The Act therefore appears to conclusively eliminate TikTok Inc.'s ability to speak through its editorial and publishing activities and through its own. account on the TikTok platform. 57. For similar reasons, the Act burdens the First Amendment rights of other ByteDance subsidiaries to reach their U.S. user audiences, (Page 35 of Total) 34
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 36 of 70 since those companies are likewise prohibited from speaking and engaging in editorial activities on other ByteDance applications. 58. The Act is subject to strict scrutiny. The Act's restrictions on Petitioners' First Amendment rights are subject to strict scrutiny for three independent reasons. 59. First, the Act represents a content- and viewpoint-based restriction on protected speech. The Act discriminates on a content basis because it exempts platforms "whose primary purpose" is to host specific types of content: "product reviews, business reviews, or travel information and reviews.” Sec. 2(g)(2)(B). The Act thus “distinguish[es] favored speech" - i.e., speech concerning travel information and business reviews "from disfavored speech" ―i.e., all other types of - speech, including particularly valuable speech like religious and political content. Turner Broad. Sys., Inc. v. FCC, 512 U.S. 622, 643 (1994). 60. The Act also discriminates on a viewpoint basis because it appears to have been enacted at least in part because of concerns over the viewpoints expressed in videos posted on TikTok by users of the platform. For example, the House Committee Report asserted, without supporting evidence, that Tik Tok "can be used by [foreign adversaries] to 35 (Page 36 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 37 of 70 push misinformation, disinformation, and propaganda on the American public" 19 a concern that in any event could be raised about any platform for user-generated content. See infra ¶¶82, 87. Similarly, Rep. Raja Krishnamoorthi, who co-sponsored the Act, expressed the unsubstantiated concern that “the platform continued to show dramatic differences in content relative to other social media platforms."20 61. Second, the Act discriminates between types of speakers. As explained above, TikTok Inc. is a protected First Amendment speaker with respect to the TikTok platform. The Act facially discriminates between Tik Tok Inc. and other speakers depending on the "primary purpose” of the platforms they operate. Any application offered by Petitioners is automatically deemed a “foreign adversary controlled application,” without any exclusions or exceptions. Sec. 2(g)(3)(A). By contrast, any other company's application can be deemed a "foreign adversary controlled application” only if the company does not operate a 19 House Committee Report at 2. 20 Sapna Maheshwari, David McCabe & Annie Karni, House Passes Bill to Force Tik Tok Sale From Chinese Owner or Ban the App, N.Y. Times (Mar. 13, 2024), https://perma.cc/Z7UE-WYH6. (Page 37 of Total) 36
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 38 of 70 website or application "whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews." Sec. 2(g)(2)(B). The Act thus favors speakers that do offer such websites or applications over speakers that do not. 62. Moreover, the Act singles out TikTok Inc. and other subsidiaries of ByteDance for unique disfavor in other ways. Whereas other companies with ownership in a country deemed a "foreign adversary" become subject to the Act's restrictions only upon a presidential determination that the company poses "a significant threat to the national security of the United States,” Sec. 2(g)(3)(B), ByteDance Ltd. and its subsidiaries are automatically subject to the Act's draconian restrictions by fiat, Sec. 2(g)(3)(A). The standard and process that the Act specifies for every other company likely fall short of what is required. by the First Amendment and other applicable constitutional protections, but TikTok Inc. and ByteDance have been singled out for a dramatically different, even more clearly unconstitutional regime with no public notice, no process for a presidential determination that there is a significant national security threat, no justification of that determination by a public report and submission of classified evidence to Congress, and 37 - (Page 38 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 39 of 70 no judicial review for statutory and constitutional sufficiency based on the reasons set forth in the presidential determination. The Act also draws a speaker-based distinction insofar as it specifically names Byte Dance Ltd. and TikTok, and also exempts applications with fewer than 1 million monthly users (except if those applications are operated by ByteDance Ltd. or TikTok). Sec. 2(g)(2)(A)(ii), (3)(A). 63. A statutory restriction targeting specific classes of speakers is subject to strict scrutiny. See United States v. Playboy Ent. Grp., Inc., 529 U.S. 803, 812 (2000) ("Laws designed or intended to suppress or restrict the expression of certain speakers contradict basic First Amendment principles."). And that is especially true when, as here, the Act singles out Petitioners by name for uniquely disfavored treatment and congressional statements indicate that the Act targets Petitioners in part because of concerns about the content on TikTok. Because the Act "target[s]" both "speakers and their messages for disfavored treatment,” strict scrutiny review is required. Sorrell, 564 U.S. at 565; see also Turner, 512 U.S. at 658-60. 64. Third, the Act is subject to strict scrutiny as an unlawful prior restraint. The Supreme Court has "consistently" recognized in a "long 38 (Page 39 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 40 of 70 line" of cases that government actions that “deny use of a forum in advance of actual expression" or forbid “the use of public places [for plaintiffs] to say what they wanted to say" are prior restraints. Se. Promotions, Ltd. v. Conrad, 420 U.S. 546, 552-53 (1975). “[P]rior restraints on speech and publication are the most serious and the least. tolerable infringement on First Amendment rights." Nebraska Press Ass'n v. Stuart, 427 U.S. 539, 559 (1976). The Act suppresses speech in advance of its actual expression by prohibiting all U.S. TikTok users including Petitioner Tik Tok Inc. - from communicating on the platform. See Backpage.com, LLC v. Dart, 807 F.3d 229 (7th Cir. 2015) (defendant's conduct restricting the operator of classified advertising website was a prior restraint); Org. for a Better Austin v. Keefe, 402 U.S. 415, 418–19 (1971) (ban on distributing leaflets a prior restraint); U.S. WeChat Users All. v. Trump, 488 F. Supp. 3d 912, 926 (N.D. Cal. 2020) (ban on communications application a prior restraint). The same is true of other Byte Dance subsidiaries and their platforms. Such restrictions “bear[] a heavy presumption against [their] constitutional validity." Se. Promotions, 420 U.S. at 558. (Page 40 of Total) 39
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 41 of 70 65. The Act fails strict scrutiny because it does not further a compelling interest. Strict scrutiny “requires the Government to prove that the restriction [1] furthers a compelling interest and [2] is narrowly tailored to achieve that interest." Reed v. Town of Gilbert, 576 U.S. 155, 171 (2015) (numerical alterations added). "If a less restrictive alternative would serve the Government's purpose, the legislature must use that alternative." Playboy, 529 U.S. at 813. The Act fails on both counts. 66. The Act does not further a compelling interest. To be sure, national security is a compelling interest, but the government must show that the Act furthers that interest. To do so, the government "must do more than simply posit the existence of the disease sought to be cured." Turner, 512 U.S. at 664 (plurality op.). Rather, it “must demonstrate that the recited harms are real, not merely conjectural, and that the regulation will in fact alleviate these harms in a direct and material way." Id. 67. Congress itself has offered nothing to suggest that the TikTok platform poses the types of risks to data security or the spread of foreign propaganda that could conceivably justify the Act. The Act is devoid of 40 (Page 41 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 42 of 70 any legislative findings, much less a demonstration of specific harms that Tik Tok supposedly poses in either respect, even though the platform was first launched in 2017. 68. The statements of congressional committees and individual Members of Congress during the hasty, closed-door legislative process preceding the Act's enactment confirm that there is at most speculation, not "evidence,” as the First Amendment requires. Instead of setting out evidence that TikTok is actually compromising Americans' data security by sharing it with the Chinese government or spreading pro-China propaganda, the House Committee Report for an earlier version of the Act relies repeatedly on speculation that Tik Tok could do those things. See, e.g., House Committee Report at 6 (TikTok could “potentially [be] allowing the CCP 'to track the locations of Federal employees and contractors") (emphasis added) (quoting Exec. Order 13,942, 85 Fed. Reg. 48637, 48637 (Aug. 6, 2020)); id. at 8 (discussing "the possibility that the [CCP] could use [TikTok] to control data collection on millions of users") (emphasis added); id. ("Tik Tok has sophisticated capabilities that create the risk that [it] can ……. suppre[ss] statements and news that the PRC deems negative") (emphasis added). Speculative risk of harm is simply 41 (Page 42 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 43 of 70 not enough when First Amendment values are at stake. These risks are even more speculative given the other ways that the Chinese government could advance these asserted interests using a variety of intelligence tools and commercial methods. See infra 85–87. 69. The conjectural nature of these concerns are further underscored by President Biden's decision to continue to maintain a Tik Tok account for his presidential campaign even after signing the Act into law. 21 Congressional supporters of the Act have also maintained campaign accounts on TikTok. 22 This continued use of TikTok by President Biden and Members of Congress undermines the claim that the platform poses an actual threat to Americans. 70. Further, even if the government could show that TikTok or another ByteDance-owned application "push[es] misinformation, disinformation, and propaganda on the American public," House 21 Monica Alba, Sahil Kapur & Scott Wong, Biden Campaign Plans to Keep Using Tik Tok Through the Election, NBC News (Apr. 24, 2024), https://perma.cc/QPQ5-RVAD. 22 Tom Norton, These US Lawmakers Voted for Tik Tok Ban But Use It Themselves, Newsweek (Apr. 17, 2024), https://perma.cc/AQ5F-N8XQ. At least one Member created a TikTok account after the Act was enacted. See https://perma.cc/L3GT-7529. (Page 43 of Total) 42
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 44 of 70 Committee Report at 2, the government would still lack a compelling interest in preventing Americans from hearing disfavored speech. generated by TikTok users and shared on the platform just because the government considers it to be foreign "propaganda." See Lamont v. Postmaster Gen. of U.S., 381 U.S. 301, 305 (1965). 71. The Act also offers no support for the idea that other applications operated by subsidiaries of ByteDance Ltd. pose national security risks. Indeed, the legislative record contains no meaningful discussion of any ByteDance-owned application other than TikTok― let alone evidence “proving” that those other applications pose such risks. Reed, 576 U.S. at 171. 72. - The Act also provides neither support nor explanation for subjecting Petitioners to statutory disqualification by legislative fiat while providing every other platform, and users of other platforms, with a process that includes a statutory standard for disqualification, notice, a reasoned decision supported by evidence, and judicial review based on those specified reasons. Only Petitioners are subjected to a regime that has no notice and no reasoned decision supported by evidence - opening the door to, among other things, post-hoc arguments that may not have 43 (Page 44 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 45 of 70 been the basis for the government action. The Supreme Court recently explained that the requirement of a "reasoned explanation" is "meant to ensure that [the government] offer[s] genuine justifications for important decisions, reasons that can be scrutinized by courts and the interested public. Accepting contrived reasons would defeat the purpose of the enterprise." Dep't of Com. v. New York, 139 S. Ct. 2551, 2576 (2019). Depriving Petitioners of those protections imposes a dramatically heavier burden on the free speech rights of Petitioners and TikTok users that is wholly unjustified and certainly not supported by a compelling interest. The Act also fails strict scrutiny because it is not narrowly tailored. "Even where questions of allegedly urgent national security. . . are concerned," the government must show that "the evil that would result from the [restricted speech] is both great and certain and cannot be mitigated by less intrusive measures.” CBS, Inc. v. Davis, 510 U.S. 1315, 1317 (1994). To satisfy narrow tailoring, the Act must represent the least restrictive means to further the government's asserted data security and propaganda interests, Sable Commc'ns of Cal., Inc. v. FCC, 492 U.S. 115, 126 (1989), and be neither over- nor under- 73. (Page 45 of Total) 44
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 46 of 70 inclusive, Ark. Writers' Project, Inc. v. Ragland, 481 U.S. 221, 232 (1987). The Act fails in each of these respects. 74. The Act opts for a wholesale prohibition on Petitioners offering online applications in lieu of a multitude of less restrictive measures it could have taken instead. As discussed above, Petitioners have been involved in negotiations with CFIUS since 2019 over a package of measures that would resolve the government's concerns about data security and purported propaganda related to TikTok. The terms of that negotiated package are far less restrictive than an outright ban. The negotiations have resulted in the draft National Security Agreement, which Tik Tok Inc. is already in the process of voluntarily implementing to the extent it can do so without government action. That initiative includes a multi-billion-dollar effort to create a new TikTok U.S. subsidiary devoted to protecting U.S. user data and have U.S.-based Oracle Corporation store protected U.S. TikTok user data in the United States, run the TikTok recommendation system for U.S. users, and inspect TikTok's source code for security vulnerabilities. 75. If executed by the government, the National Security Agreement would also give CFIUS a "shut-down option" to suspend 45 (Page 46 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 47 of 70 Tik Tok in the United States in response to specified acts of noncompliance. The government has never meaningfully explained why the National Security Agreement (a far less restrictive alternative to an outright, total ban) is insufficient to address its stated concerns about data security and propaganda. 76. Even if the government's dissatisfaction with the draft. National Security Agreement were valid (despite the government never explaining why the agreement that the government itself negotiated is unsatisfactory), the CFIUS process in in which Petitioners have participated in good faith is geared toward finding any number of other less restrictive alternatives to an outright, total ban. The CFIUS member agencies could return to working with Petitioners to craft a solution that is tailored to meet the government's concerns and that is commercially, technologically, and legally feasible. Yet the government has not explained why the CFIUS process is not a viable alternative. 77. There are also a wide range of other less restrictive measures that Congress could have enacted. While many of these measures are themselves unjustified as applied to Petitioners, they nevertheless. illustrate that the Act does not select the least restrictive means to 46 (Page 47 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 48 of 70 further the national security goals that appear to have motivated it. For example, Congress could have addressed some members' stated concern about Tik Tok allegedly "track[ing] the locations of Federal employees and contractors" 23 by expanding the existing ban on government-owned devices to cover personal devices of federal employees and contractors. Or Congress could have enacted legislation to regulate TikTok's access to measures the Department of certain features on users' devices Homeland Security identified in 2020 as potential mitigations to "reduce the national security risks associated with" TikTok.24 78. Of course, Congress could also have decided not to single out a single speech platform (TikTok) and company (ByteDance Ltd.), and instead pursued any number of industry-wide regulations aimed at addressing the industry-wide issues of data security and content integrity. Congress could have enacted a data protection law governing transfers of Americans' sensitive data to foreign countries, similar to the 23 House Committee Report at 6. 24 Cybersecurity and Infrastructure Agency, Critical Infrastructure Security and Resilience Note, Appendix B: Department of Homeland Security Tik Tok and WeChat Risk Assessment 4 (Sept. 2, 2020). 47 (Page 48 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 49 of 70 strategy President Biden is currently pursuing through executive - the order. 25 Indeed, Congress did enact such a data-transfer law similarly named "Protecting Americans' Data from Foreign Adversaries Act of 2024" as the very next division of the legislation that contains the Act. Yet it chose to prohibit only “data broker[s]” from “mak[ing] available personally identifiable sensitive data of a United States. individual to any foreign adversary country or ... any entity that is controlled by a foreign adversary." H.R. 815, div. I, § 2(a), 118th Cong., Pub. L. No. 118-50 (Apr. 24, 2024). 79. There are also models for industry-wide regulation that Congress could have followed from other jurisdictions. For example, the European Union's Digital Services Act requires certain platforms to make disclosures about their content-moderation policies and to provide regulators and researchers with access to their data so those researchers can assess if the platforms are systemically promoting or suppressing 25 See Exec. Order 14, 117, 89 Fed. Reg. 15421 (Mar. 1, 2024). 48 (Page 49 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 50 of 70 content with particular viewpoints. 26 Congress pursued none of these alternatives. 80. Congress did not even provide Petitioners with the process and fact-finding protections that the Act extends to all other companies -protections which themselves likely fall short of what the Constitution mandates. Other companies receive prior notice, followed by a presidential determination of (and public report on) the national security threat posed by the targeted application, and the submission to Congress. of classified evidence supporting that determination, Sec. 2(g)(3)(B), which then is subject to judicial review based on the actual reasons for the decision, not post hoc rationalizations. 81. Because Congress failed to try any of these less restrictive measures, or at a minimum to explain why these alternatives would not address the government's apparent concerns, the Act is not narrowly tailored. 82. The Act independently fails strict scrutiny because it is both under- and over-inclusive. The Act is under-inclusive because it 26 EU Reg. 2022/2065 arts. 15, 40(4), 42(2). 49 (Page 50 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 51 of 70 ignores the many ways in which other companies. - both foreign and domestic can pose the same risks to data security and promotion of misinformation supposedly posed by Petitioners. The government "cannot claim" that banning some types of foreign owned applications is "necessary" to prevent espionage and propaganda “while at the same time" allowing other types of platforms and applications that may "create the same problem.” Reed, 576 U.S. at 172. Put differently, the Act's “[u]nderinclusiveness raises serious doubts about whether the government is in fact pursuing the interest it invokes, rather than disfavoring a particular speaker or viewpoint.” Brown v. Ent. Merchants Ass'n, 564 U.S. 786, 802 (2011). 83. Most glaringly, the Act applies only to Petitioners and certain other platforms that allow users to generate and view "text, images, videos, real-time communications, or similar content.” Sec. 2(g)(2)(A). The Act's coverage is thus triggered not by whether an application. collects users' data, but whether it shows them “content." Accordingly, there is no necessary relationship between the Act's scope and Congress's apparent concern with risks to Americans' data security, which could (Page 51 of Total) 50
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 52 of 70 equally be posed by personal finance, navigation, fitness, or many other types of applications. 84. The Act also singles out Petitioners by exempting all other companies that operate any website or application "whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews." Sec. 2(g)(2)(B). But the Act does not explain why such applications, when (i) “foreign adversary controlled” under the Act's broad definition; and (ii) determined by the President to be a significant national security threat, could not likewise be used to collect data from Americans such as Americans' location information - or to spread misinformation. Nor does the Act explain why an entire company presents no threat simply because it operates a single website or application the “primary purpose” of which is posting “product reviews, business reviews, or travel information and reviews." Sec. 2(g)(2)(B). The Act's differential treatment of this favored category of websites and applications also disregards the fact that there is voluminous content on Tik Tok containing product reviews, business reviews, and travel information and reviews. Yet TikTok and all ByteDance applications are ineligible for this exclusion. 51 (Page 52 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 53 of 70 85. More broadly, the Act ignores the reality that much of the data collected by Tik Tok is no different in kind from the data routinely collected by other applications and sources in today's online world, including by American companies like Google, Snap, and Meta. The Act also ignores that foreign countries, including China, can obtain such information on Americans in other ways such as through open-source research and hacking operations. 86. Likewise, the House Committee Report on an earlier version of the Act speculates that allowing source code development in China "potentially exposes U.S. users to malicious code, backdoor vulnerabilities, surreptitious surveillance, and other problematic activities tied to source code development."27 But those supposed risks arise for each of the many American companies that employ individuals in China to develop code. The Act, however, does not seek to regulate, much less prohibit, all online applications offered by companies that have offices in China or that otherwise employ Chinese nationals as software developers. 28 27 House Committee Report at 5. 28 See, e.g., Karen Freifeld & Jonathan Stempel, Former Google Engineer 52 (Page 53 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 54 of 70 87. Nor does the Act seek to cut off numerous other ways that Americans could be exposed to foreign propaganda. For instance, the Act leaves foreign nationals (and even adversarial governments themselves) free to operate cable television networks in the United States, spread propaganda through accounts on other online platforms that enable the sharing of user-generated content, or distribute copies of state-run newspapers physically or over the Internet (including by software applications) in the United States. 29 Indicted for Stealing AI Secrets to Aid Chinese Companies, Reuters (Mar. 6, 2024), https://perma.cc/6LYE-64J6. 29 The U.S. government has recognized that foreign government. propaganda is an industry-wide challenge for online platforms. See, e.g., Nat'l Intel. Council, Declassified Intelligence Community Assessment, Foreign Threats to the 2020 US Federal Elections (Mar. 10, 2021), https://perma.cc/VD3Y-VXSB. YouTube, for example, added disclaimers to certain channels that were reportedly being used to spread disinformation on behalf of the Russian government. Paresh Dave & Christopher Bing, Russian Disinformation on YouTube Draws Ads, Lacks Warning Labels - Researchers, Reuters (June 7, 2019), https://perma.cc/2BEJ-VKGW. Like others in the industry, TikTok publishes transparency reports on attempts by users to use the platform for government propaganda purposes. See TikTok, Countering Influence Operations (last visited May 6, 2024), https://perma.cc/AB39-S8FJ. 53 (Page 54 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 55 of 70 88. The Act is also over-inclusive because it applies to other Byte Dance Ltd.-owned applications that Congress has not shown and could not possibly prove pose the risks the Act apparently seeks to address. - 89. At a minimum, the Act fails intermediate scrutiny. Even if strict scrutiny did not apply, the Act would still fail intermediate scrutiny as a time, place, and manner restriction: the Act prohibits speech activity on TikTok at all times, in all places, and in all manners anywhere across the United States. To pass intermediate scrutiny, a law must be "narrowly tailored to serve a significant governmental interest.” McCullen v. Coakley, 573 U.S. 464, 486 (2014). This means that it must not "burden substantially more speech than is necessary to further the government's legitimate interests," Turner, 512 U.S. at 661-62, and "leave open ample alternative channels for communication of the information," Clark v. Cmty. for Creative Non-Violence, 468 U.S. 288, 293 (1984). 90. For many of the same reasons the Act cannot satisfy strict scrutiny, it also cannot satisfy intermediate scrutiny: (Page 55 of Total) 54
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 56 of 70 91. As discussed supra ¶¶67-69, the government has failed to establish that its apparent data security and propaganda concerns with Tik Tok are non-speculative. And as discussed supra ¶¶ 73-81, the Act. burdens substantially more speech than necessary because there are many less restrictive alternatives Congress could have adopted to address any legitimate concerns. The Act also fails intermediate scrutiny because it “effectively prevents” TikTok Inc. “from reaching [its] intended audience" and thus "fails to leave open ample alternative means of communication." Edwards v. City of Coeur d'Alene, 262 F.3d 856, 866 (9th Cir. 2001). 92. Regardless of the level of scrutiny, the Act violates the First Amendment for two additional reasons. 93. The Act forecloses an entire medium of expression. First, by banning TikTok in the United States, the Act "foreclose[s] an entire medium of expression." City of Ladue v. Gilleo, 512 U.S. 43, 56 (1994). A "long line of Supreme Court cases indicates that such laws are almost never reasonable." Anderson v. City of Hermosa Beach, 621 F.3d 1051, 1064-65 (9th Cir. 2010). (Page 56 of Total) 55
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 57 of 70 94. The Act is constitutionally overbroad. Second, the Act is facially overbroad. A law is "overbroad if a substantial number of its. applications are unconstitutional, judged in relation to the statute's plainly legitimate sweep." United States v. Stevens, 559 U.S. 460, 473 (2010) (citation omitted). Here, for example, the government has never contended that all or even most of the content on TikTok (or any other Byte Dance-owned application) represents misinformation, or propaganda. Yet the Act shuts down all speech on ByteDance-owned applications at all times, in all places, and in all manners. That is textbook overbreadth. See, e.g., Bd. of Airport Comm'rs v. Jews for Jesus, Inc., 482 U.S. 569, 574–75 (1987). disinformation, Ground 2: Unconstitutional Bill of Attainder 95. The Act is an unconstitutional bill of attainder. Article I of the U.S. Constitution prohibits Congress from passing any bill of attainder. U.S. Const. art. I § 9, cl. 3 ("No Bill of Attainder or ex post facto Law shall be passed."). A bill of attainder is "legislative punishment, of any form or severity, of specifically designated persons or groups." United States v. Brown, 381 U.S. 437, 447 (1965). The protection against bills of attainder is “an implementation of 56 (Page 57 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 58 of 70 the separation of powers, a general safeguard against legislative exercise of the judicial function, or more simply trial by legislature." Id. at 442. - 97. By singling out Petitioners for legislative punishment, the Act is an unconstitutional bill of attainder. 98. The Act inflicts "pains and penalties" that historically have been associated with bills of attainder. See Nixon v. Adm'r of Gen. Servs., 433 U.S. 425, 474 (1977). Historically, common "pains and penalties" included "punitive confiscation of property by the sovereign” and “a legislative enactment barring designated individuals or groups from participation in specified employments or vocations," among others. Id. As described above, the Act confiscates Petitioners' U.S. businesses by forcing ByteDance to shutter them within 270 days or sell on terms that are not commercially, technologically, or legally feasible. See supra ¶¶26-29. For the same reason, the Act bars Petitioners from operating in their chosen line of business. 99. "[V]iewed in terms of the type and severity of burdens imposed" on Petitioners, the Act's treatment of Petitioners cannot "reasonably ... be said to further nonpunitive legislative purposes." Nixon, 433 U.S. at 475–76. The Act transforms Petitioners into a “vilified 57 (Page 58 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 59 of 70 class" by explicitly prohibiting their current and future operations in the United States, without qualification or limitation, but does not extend the same treatment to other similarly situated companies. Foretich v. United States, 351 F.3d 1198, 1224 (D.C. Cir. 2003). 100. Moreover, in light of the less restrictive alternatives discussed above, there is no justification for automatically barring Petitioners' current and future operations in the United States (or those of its subsidiaries or successors) in perpetuity without providing them a meaningful opportunity to take corrective action. See Kaspersky Lab, Inc. v. U.S. Dep't of Homeland Sec., 909 F.3d 446, 456 (D.C. Cir. 2018). Indeed, the Act imposes this punishment uniquely on Petitioners without the process, and presidential determination of a significant national security threat, that Congress has afforded to everyone else. Expressly singling out Petitioners for these punitive burdens while at the same time adopting a statutory standard and decision-making process applicable to every other entity makes clear that Petitioners are subjected to a prohibited legislatively imposed punishment. 101. Moreover, while Petitioners can avoid the Act's prohibitions only via a wholesale divestment, all other companies 58 even those with (Page 59 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 60 of 70 Chinese ownership and determined by the President to present a "significant threat" to U.S. national security ― can avoid prohibition simply by operating a website or an application "whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews." Sec. 2(g)(2)(b). 102. Indeed, any other "adversary-controlled" company that operates an application exactly like TikTok, but also operates a website the primary purpose of which is to post product reviews, is left untouched, leaving a ready path for any company but those affiliated with Petitioners to circumvent the Act's prohibitions altogether. For all practical purposes, then, the Act applies to just one corporate group is a "Tik Tok bill," as congressional leaders have described it.30 - it 103. For all of these reasons, the Act constitutes an unconstitutional bill of attainder. 30 Rachel Dobkin, Mike Johnson's Letter Sparks New Flood of Republican Backlash, Newsweek (Apr. 17, 2024), https://perma.cc/Z5HD-7UVU (quoting letter from Speaker Johnson referencing the “TikTok_bill”); Senator Chuck Schumer, Majority Leader, to Colleagues (Apr. 5, 2024), https://perma.cc/J7Q4-9PGJ (referencing “TikTok legislation”). 59 (Page 60 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 61 of 70 Ground 3: Violation of Equal Protection 104. The Act also violates Petitioners' rights under the equal protection component of the Fifth Amendment's Due Process Clause because it singles Petitioners out for adverse treatment without any reason for doing so. 105. First, the Act deems any application offered by Petitioners to be a “foreign adversary controlled application" without notice or a presidential determination. Sec. 2(g)(3)(A). By contrast, applications offered by other companies "controlled by a foreign adversary" are deemed to be "foreign adversary controlled applications" only after notice. and a presidential determination that those companies present "significant threat[s]" to U.S. national security, a determination that must be supported by evidence submitted to Congress. Sec. 2(g)(2)(B); see supra 34(d). 106. That distinction imposes a dramatically heavier burden on Petitioners' free speech rights without any justification. The Act precludes the government from burdening the speech rights of any speakers other than Petitioners unless and until the President issues a public report on the specific national security concerns animating the 60 (Page 61 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 62 of 70 President's decision, provides support for that decision, and describes the assets requiring divestiture. Those protections ensure that the President must, at the very least, provide a detailed national security justification for his or her actions before burdening other speakers' speech a justification that then will provide the basis for judicial review. The Act imposes none of those requirements as a precondition for burdening Petitioners' speech it levies that burden by unexplained legislative fiat. — 107. Second, the Act denies Petitioners the exemption available to any other company that is purportedly “controlled by a foreign adversary." As noted, any application Petitioners offer is ipso facto deemed a "foreign adversary controlled application." By contrast, other companies "controlled by a foreign adversary" are exempt from the Act's definition of a "covered company," and thus from the Act's requirements, so long as they offer at least one application with the "primary purpose" of “allow[ing] users to post product reviews, business reviews, or travel information and reviews." Sec. 2(g)(2)(B). 108. There is no conceivable reason for treating Petitioners differently than all other similarly situated companies. Even if Congress 61 (Page 62 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 63 of 70 had valid interests in protecting U.S. users' data and controlling what content may be disseminated through global platforms that would be advanced through the Act, there is no reason why those concerns would support a ban on Petitioners' platforms without corresponding bans on other platforms. Nor is there any rational reason why Congress would ban Petitioners' platforms while allowing any other company "controlled by a foreign adversary" - regardless of the national security threat posed by that company to sidestep the Act's reach by simply offering an - application that “allows users to post product reviews, business reviews, or travel information and reviews," but changing nothing else about the company's operations, ownership structure, or other applications. 109. By treating Petitioners differently from others similarly situated, the Act denies Petitioners the equal protection of the law. Ground 4: Unconstitutional Taking 110. The Act effects an unlawful taking of private property without just compensation, in violation of the Fifth Amendment's Takings Clause. 111. The Takings Clause provides that “private property” shall not be "taken for public use, without just compensation." U.S. Const. amend. V, cl. 5. The Act does just that by shutting down ByteDance's 62 (Page 63 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 64 of 70 U.S. businesses or, to the extent any qualified divestiture alternative is even feasible (it is not), compelling ByteDance to sell those businesses. under fire-sale circumstances that guarantee inadequate compensation. 112. Petitioners have substantial property interests in, and associated with, their and their affiliates' U.S. operations. These include not only ByteDance Ltd.'s interest in TikTok Inc. and other U.S. businesses, but also the platforms and applications themselves. See Kimball Laundry Co. v. United States, 338 U.S. 1, 11–13 (1949) (Takings Clause also protects losses to going-concern value of business). 113. If the Act's prohibitions take effect, they will deprive Petitioners of property protected by the Takings Clause. Absent a qualified divestiture, the Act will shutter Petitioners' businesses in the United States. And even if a qualified divestiture were feasible (it is not), any sale could be, at best, completed only at an enormous discount to the U.S. businesses' current market value, given the forced sale conditions. See BFP v. Resol. Tr. Corp., 511 U.S. 531, 537 (1994) (“[M]arket value, as it is commonly understood, has no applicability in the forced-sale context; indeed, it is the very antithesis of forced-sale value."). (Page 64 of Total) 63
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 65 of 70 114. Because the Act compels ByteDance "to relinquish specific, identifiable property" or forfeit "all economically beneficial uses," the Act effects a per se taking. Horne v. Dep't of Agric., 576 U.S. 350, 364-65 (2015); Lucas v. S.C. Coastal Council, 505 U.S. 1003, 1019 (1992). 115. Alternatively, the Act inflicts a regulatory taking. Even when a law does not compel the physical invasion of property or deprive the property of all economically viable use, it still effects a taking "if [it] goes too far." Penn. Coal Co. v. Mahon, 260 U.S. 393, 415 (1922). In determining when a law "goes too far," courts have typically looked to "several factors" identified in Penn Central Transportation Co. v. City of New York, 438 U.S. 104, 124 (1978), namely, (a) “[t]he economic impact of the regulation”; (b) “the extent to which the regulation has interfered with reasonable investment-backed expectations"; and (c) "the character of the governmental action." The Act inflicts a regulatory taking under each of these three factors. 116. The Act does not compensate Petitioners (let alone provide just compensation) for the dispossession of their U.S. businesses. See United States v. Miller, 317 U.S. 369, 373 (1943). Prospective injunctive (Page 65 of Total) 64
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 66 of 70 relief is accordingly warranted. See, e.g., Youngstown Sheet & Tube Co. v. Sawyer, 343 U.S. 579, 585 (1952). Requested Relief relief: Petitioners respectfully request that this Court grant the following A. Issue a declaratory judgment that the Act violates the U.S. Constitution; B. Issue an order enjoining the Attorney General from enforcing the Act; C. Enter judgment in favor of Petitioners; and D. Grant any further relief that may be appropriate. (Page 66 of Total) 65
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 67 of 70 DATED: May 7, 2024 Andrew J. Pincus Avi M. Kupfer MAYER BROWN LLP 1999 K Street, NW Washington, DC 20006 Telephone: 202-263-3220 Email: [email protected] [email protected] Respectfully submitted, /s/ Alexander A. Berengaut Alexander A. Berengaut David M. Zionts Megan A. Crowley COVINGTON & BURLING LLP One CityCenter 850 Tenth Street, NW Washington, DC 20001 Telephone: (202) 662-6000 Email: [email protected] [email protected] [email protected] John E. Hall Anders Linderot COVINGTON & BURLING LLP The New York Times Building 620 Eighth Avenue New York, New York 10018 Telephone: (212) 841-1000 Email: [email protected] [email protected] Counsel for Petitioners (Page 67 of Total) 66
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 68 of 70 IN THE UNITED STATES COURT OF APPEALS FOR THE DISTRICT OF COLUMBIA CIRCUIT TIKTOK INC., and BYTEDANCE LTD., V. ) Petitioners, No. 24-1113 MERRICK B. GARLAND, in his official capacity as Attorney General of the United States, Respondent. CORPORATE DISCLOSURE STATEMENT Petitioners state as follows: ByteDance Ltd. is a privately held corporation incorporated in the Cayman Islands. ByteDance Ltd. subsidiaries provide a suite of more than a dozen products and services that allow people to connect with, create, and consume content on the Internet. ByteDance Ltd. has no (Page 68 of Total) 1
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 69 of 70 parent company, and no publicly traded company owns 10% or more of Byte Dance Ltd.'s stock. Tik Tok Inc. is a California-incorporated company that provides the TikTok platform in the United States. TikTok Inc. is a wholly owned subsidiary of TikTok LLC, which is a wholly owned subsidiary of TikTok Ltd. TikTok Ltd. is a wholly owned subsidiary of ByteDance Ltd. TikTok Inc. has no other parent company, and no publicly held corporation owns 10% or more of its stock. (Page 69 of Total) 2 /s/Alexander A. Berengaut Alexander A. Berengaut Counsel for Petitioners
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 70 of 70 CERTIFICATE OF SERVICE I hereby certify that on this 7th day of May, I caused copies of the foregoing Petition for Review and Corporate Disclosure Statement to be served upon the following recipients. By certified mail, postage prepaid: Merrick B. Garland Attorney General of the United States U.S. Department of Justice 950 Pennsylvania Avenue, NW Washington, DC 20530 By hand delivery: Matthew M. Graves United States Attorney 601 D Street, NW Washington, DC 20579 /s/ Alexander A. Berengaut Alexander A. Berengaut Counsel for Petitioners (Page 70 of Total)
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 1 of 7 (Page 71 of Total) EXHIBIT A
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 2 of 7 (Page 72 of Total) H. R. 815-61 Fusion Development Strategy programs of the People's Republic of China, including the following: (1) A brief summary of each such identified field and its relevance to the military power and national security of the People's Republic of China. (2) The implications for the national security of the United States as a result of the leadership or dominance by the People's Republic of China in each such identified field and associated supply chains. (3) The identification of at least 10 entities domiciled in, controlled by, or directed by the People's Republic of China (including any subsidiaries of such entity), involved in each such identified field, and an assessment of, with respect to each such entity, the following: (A) Whether the entity has procured components from any known United States suppliers. (B) Whether any United States technology imported by the entity is controlled under United States regulations. (C) Whether United States capital is invested in the entity, either through known direct investment or passive investment flows. (D) Whether the entity has any connection to the Peo- ple's Liberation Army, the Military-Civil Fusion program of the People's Republic of China, or any other state-spon- sored initiatives of the People's Republic of China to sup- port the development of national champions. (c) APPROPRIATE CONGRESSIONAL COMMITTEES DEFINED.-In this section, the term "appropriate congressional committees" means- (1) the Committee on Foreign Affairs of the House of Rep- resentatives; (2) the Committee on Armed Services of the House of Representatives; (3) the Committee on Foreign Relations of the Senate; and (4) the Committee on Armed Services of the Senate. DIVISION H-PROTECTING AMERICANS FROM FOREIGN ADVERSARY CON- TROLLED APPLICATIONS ACT SEC. 1. SHORT TITLE. This division may be cited as the "Protecting Americans from Foreign Adversary Controlled Applications Act”. SEC. 2. PROHIBITION OF FOREIGN APPLICATIONS. ADVERSARY CONTROLLED (a) IN GENERAL.— (1) PROHIBITION OF FOREIGN ADVERSARY CONTROLLED APPLICATIONS.-It shall be unlawful for an entity to distribute, maintain, or update (or enable the distribution, maintenance, or updating of) a foreign adversary controlled application by carrying out, within the land or maritime borders of the United States, any of the following:
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 3 of 7 (Page 73 of Total) H. R. 815-62 (A) Providing services to distribute, maintain, or update such foreign adversary controlled application (including any source code of such application) by means of a marketplace (including an online mobile application store) through which users within the land or maritime borders of the United States may access, maintain, or update such application. (B) Providing internet hosting services to enable the distribution, maintenance, or updating of such foreign adversary controlled application for users within the land or maritime borders of the United States. (2) APPLICABILITY.-Subject to paragraph (3), this sub- section shall apply― (A) in the case of an application that satisfies the definition of a foreign adversary controlled application pursuant to subsection (g)(3)(A), beginning on the date that is 270 days after the date of the enactment of this division; and (B) in the case of an application that satisfies the definition of a foreign adversary controlled application pursuant to subsection (g)(3)(B), beginning on the date that is 270 days after the date of the relevant determination of the President under such subsection. (3) EXTENSION. With respect to a foreign adversary con- trolled application, the President may grant a 1-time extension of not more than 90 days with respect to the date on which this subsection would otherwise apply to such application pursuant to paragraph (2), if the President certifies to Congress that- (A) a path to executing a qualified divestiture has been identified with respect to such application; (B) evidence of significant progress toward executing such qualified divestiture has been produced with respect to such application; and (C) there are in place the relevant binding legal agree- ments to enable execution of such qualified divestiture during the period of such extension. (b) DATA AND INFORMATION PORTABILITY TO ALTERNATIVE APPLICATIONS.-Before the date on which a prohibition under sub- section (a) applies to a foreign adversary controlled application, the entity that owns or controls such application shall provide, upon request by a user of such application within the land or maritime borders of United States, to such user all the available data related to the account of such user with respect to such application. Such data shall be provided in a machine readable format and shall include any data maintained by such application with respect to the account of such user, including content (including posts, photos, and videos) and all other account information. (c) EXEMPTIONS.— (1) EXEMPTIONS FOR QUALIFIED DIVESTITURES.-Subsection (a)— (A) does not apply to a foreign adversary controlled application with respect to which a qualified divestiture is executed before the date on which a prohibition under subsection (a) would begin to apply to such application; and
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 4 of 7 (Page 74 of Total) H. R. 815-63 (B) shall cease to apply in the case of a foreign adversary controlled application with respect to which a qualified divestiture is executed after the date on which a prohibition under subsection (a) applies to such applica- tion. (2) EXEMPTIONS FOR CERTAIN NECESSARY SERVICES.-Sub- sections (a) and (b) do not apply to services provided with respect to a foreign adversary controlled application that are necessary for an entity to attain compliance with such sub- sections. (d) ENFORCEMENT.— (1) CIVIL PENALTIES.― (A) FOREIGN ADVERSARY CONTROLLED APPLICATION VIO- LATIONS. An entity that violates subsection (a) shall be subject to pay a civil penalty in an amount not to exceed the amount that results from multiplying $5,000 by the number of users within the land or maritime borders of the United States determined to have accessed, maintained, or updated a foreign adversary controlled application as a result of such violation. (B) DATA AND INFORMATION VIOLATIONS.-An entity that violates subsection (b) shall be subject to pay a civil penalty in an amount not to exceed the amount that results from multiplying $500 by the number of users within the land or maritime borders of the United States affected by such violation. (2) ACTIONS BY ATTORNEY GENERAL.-The Attorney Gen- eral- (A) shall conduct investigations related to potential violations of subsection (a) or (b), and, if such an investiga- tion results in a determination that a violation has occurred, the Attorney General shall pursue enforcement under paragraph (1); and (B) may bring an action in an appropriate district court of the United States for appropriate relief, including civil penalties under paragraph (1) or declaratory and injunctive relief. (e) SEVERABILITY.― (1) IN GENERAL.-If any provision of this section or the application of this section to any person or circumstance is held invalid, the invalidity shall not affect the other provisions or applications of this section that can be given effect without the invalid provision or application. (2) SUBSEQUENT DETERMINATIONS.-If the application of any provision of this section is held invalid with respect to a foreign adversary controlled application that satisfies the definition of such term pursuant to subsection (g)(3)(A), such invalidity shall not affect or preclude the application of the same provision of this section to such foreign adversary con- trolled application by means of a subsequent determination pursuant to subsection (g)(3)(B). (f) RULE OF CONSTRUCTION.-Nothing in this division may be construed― (1) to authorize the Attorney General to pursue enforce- ment, under this section, other than enforcement of subsection (a) or (b);
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 5 of 7 (Page 75 of Total) H. R. 815-64 (2) to authorize the Attorney General to pursue enforce- ment, under this section, against an individual user of a foreign adversary controlled application; or (3) except as expressly provided herein, to alter or affect any other authority provided by or established under another provision of Federal law. (g) DEFINITIONS.-In this section: (1) CONTROLLED BY A FOREIGN ADVERSARY.-The term "con- trolled by a foreign adversary" means, with respect to a covered company or other entity, that such company or other entity is- (A) a foreign person that is domiciled in, is headquartered in, has its principal place of business in, or is organized under the laws of a foreign adversary country; (B) an entity with respect to which a foreign person or combination of foreign persons described in subpara- graph (A) directly or indirectly own at least a 20 percent stake; or (C) a person subject to the direction or control of a foreign person or entity described in subparagraph (A) or (B). (2) COVERED COMPANY.— (A) IN GENERAL.—The term "covered company" means an entity that operates, directly or indirectly (including through a parent company, subsidiary, or affiliate), a website, desktop application, mobile application, or aug- mented or immersive technology application that— (i) permits a user to create an account or profile to generate, share, and view text, images, videos, real- time communications, or similar content; (ii) has more than 1,000,000 monthly active users with respect to at least 2 of the 3 months preceding the date on which a relevant determination of the President is made pursuant to paragraph (3)(B); (iii) enables 1 or more users to generate or dis- tribute content that can be viewed by other users of the website, desktop application, mobile application, or augmented or immersive technology application; and (iv) enables 1 or more users to view content gen- erated by other users of the website, desktop applica- tion, mobile application, or augmented or immersive technology application. (B) EXCLUSION.—The term “covered company” does not include an entity that operates a website, desktop applica- tion, mobile application, or augmented or immersive tech- nology application whose primary purpose is to allow users to post product reviews, business reviews, or travel information and reviews. a (3) FOREIGN ADVERSARY CONTROLLED APPLICATION.―The term "foreign adversary controlled application" means website, desktop application, mobile application, or augmented or immersive technology application that is operated, directly or indirectly (including through a parent company, subsidiary, or affiliate), by— (A) any of (i) ByteDance, Ltd.;
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 6 of 7 (Page 76 of Total) (ii) TikTok; H. R. 815-65 (iii) a subsidiary of or a successor to an entity identified in clause (i) or (ii) that is controlled by a foreign adversary; or (iv) an entity owned or controlled, directly or indirectly, by an entity identified in clause (i), (ii), or (iii); or (B) a covered company that- (i) is controlled by a foreign adversary; and (ii) that is determined by the President to present a significant threat to the national security of the United States following the issuance of (I) a public notice proposing such determina- tion; and (II) a public report to Congress, submitted not less than 30 days before such determination, describing the specific national security concern involved and containing a classified annex and a description of what assets would need to be divested to execute a qualified divestiture. (4) FOREIGN ADVERSARY COUNTRY.-The term “foreign adversary country" means a country specified in section 4872(d)(2) of title 10, United States Code. (5) INTERNET HOSTING SERVICE.―The term "internet hosting service" means a service through which storage and computing resources are provided to an individual or organiza- tion for the accommodation and maintenance of 1 or more websites or online services, and which may include file hosting, domain name server hosting, cloud hosting, and virtual private server hosting. (6) QUALIFIED DIVESTITURE.—The term "qualified divesti- ture" means a divestiture or similar transaction that- (A) the President determines, through an interagency process, would result in the relevant foreign adversary controlled application no longer being controlled by a for- eign adversary; and (B) the President determines, through an interagency process, precludes the establishment or maintenance of any operational relationship between the United States operations of the relevant foreign adversary controlled application and any formerly affiliated entities that are controlled by a foreign adversary, including any cooperation with respect to the operation of a content recommendation algorithm or an agreement with respect to data sharing. (7) SOURCE CODE.-The term "source code" means the com- bination of text and other characters comprising the content, both viewable and nonviewable, of a software application, including any publishing language, programming language, pro- tocol, or functional content, as well as any successor languages or protocols. (8) UNITED STATES.-The term "United States" includes the territories of the United States. SEC. 3. JUDICIAL REVIEW. (a) RIGHT OF ACTION.-A petition for review challenging this division or any action, finding, or determination under this division
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 7 of 7 (Page 77 of Total) H. R. 815-66 may be filed only in the United States Court of Appeals for the District of Columbia Circuit. (b) EXCLUSIVE JURISDICTION.-The United States Court of Appeals for the District of Columbia Circuit shall have exclusive jurisdiction over any challenge to this division or any action, finding, or determination under this division. (c) STATUTE OF LIMITATIONS.-A challenge may only be brought― (1) in the case of a challenge to this division, not later than 165 days after the date of the enactment of this division; and (2) in the case of a challenge to any action, finding, or determination under this division, not later than 90 days after the date of such action, finding, or determination. DIVISION I-PROTECTING AMERICANS' DATA FROM FOREIGN ADVERSARIES ACT OF 2024 SEC. 1. SHORT TITLE. This division may be cited as the "Protecting Americans' Data from Foreign Adversaries Act of 2024". SEC. 2. PROHIBITION ON TRANSFER OF PERSONALLY IDENTIFIABLE SENSITIVE DATA OF UNITED STATES INDIVIDUALS TO FOR- EIGN ADVERSARIES. (a) PROHIBITION.-It shall be unlawful for a data broker to sell, license, rent, trade, transfer, release, disclose, provide access to, or otherwise make available personally identifiable sensitive data of a United States individual to- (1) any foreign adversary country; or (2) any entity that is controlled by a foreign adversary. (b) ENFORCEMENT BY FEDERAL TRADE COMMISSION.― (1) UNFAIR OR DECEPTIVE ACTS OR PRACTICES.-A violation of this section shall be treated as a violation of a rule defining an unfair or a deceptive act or practice under section 18(a)(1)(B) of the Federal Trade Commission Act (15 U.S.C. 57a(a)(1)(B)). (2) POWERS OF COMMISSION.― (A) IN GENERAL.-The Commission shall enforce this section in the same manner, by the same means, and with the same jurisdiction, powers, and duties as though all applicable terms and provisions of the Federal Trade Commission Act (15 U.S.Č. 41 et seq.) were incorporated into and made a part of this section. (B) PRIVILEGES AND IMMUNITIES.-Any person who vio- lates this section shall be subject to the penalties and entitled to the privileges and immunities provided in the Federal Trade Commission Act. (3) AUTHORITY PRESERVED.-Nothing in this section may be construed to limit the authority of the Commission under any other provision of law. (c) DEFINITIONS.-In this section: (1) COMMISSION.-The term "Commission" means the Fed- eral Trade Commission.
Vanderbilt Law School Students Craft Guide on Public Grocery Stores
May 7, 2024, 1:20 PM
This spring, four Vanderbilt Law Students authored Public Grocery Stores: A Guide for Policymakers . Using case studies from stores around the country, the paper sheds light on the benefits and drawbacks of public grocery store models, offering guidance and a model bill for policymakers and leaders considering their use in urban or rural communities. The guide is the first published paper to come out of the Political Economy and Regulation Policy Lab, a new course offered at Vanderbilt Law School, and was published by the Vanderbilt Policy Accelerator for Political Economy and Regulation (VPA).
Authors Taylor Lawing ‘24 , Yesenia Jimenez ‘24 , Jon McNeal ‘25, and Raghav Gupta ’24 researched and drafted the paper during the fall of 2023 under the guidance of VPA Director Ganesh Sitaraman , who holds the New York Alumni Chancellor’s Chair in Law “Our prompt was to research public grocery stores across the country,” said Lawing. “There were not many of these stores, but those in operation provided the foundation for our research. We used that research to determine if the implementation of a public grocery store was a viable approach to combat food deserts and food insecurity in urban and rural communities.”
The paper was partly inspired by the Illinois Grocery Initiative Act, passed in summer 2023, which will invest $20 million to help maintain and establish grocery stores in “food deserts,” areas with limited access to fresh foods. “We found that there was a lot of room for creativity in how these bills are applied,” said Gupta. “The Illinois bill is written very broadly. It’s not only about having to open supermarkets in these places, but also about how we can best serve the community.”
Through the semester-long course, the students researched their respective sections of the paper; Sitaraman offered guidance and feedback each week. “It was a really great opportunity to experience a different style of law school class, where the outside research impacted in-class discussions each week, with a focus on policy implications rather than caselaw,” Lawing noted. Their research included interviews with operators of public grocery stores in Boston, MA; Baldwin, FL; and Winston-Salem, NC; along with associated individuals and organizations. “One thing I noticed in our case studies was that oftentimes grocers can feel like they’re the only ones doing something,” said Jimenez, “but our paper also shows that there’s a network of people doing this kind of work, who are passionate about addressing food access and food insecurity.”
The paper, published by the Vanderbilt Policy Accelerator (VPA) in March, begins with introduction to the significance and causes of Food Deserts, followed by an overview of solutions. It continues with a series of case studies detailing different public options – Publicly-Owned, Non-Profit, Public-Private Partnership, and Cooperative stores – and a guide for building stores. The Appendices offer a checklist for launching a store and a model bill for policymakers.
“I think a lot of folks come to law school with a desire to effect some positive change in the world,” said McNeil. “But the reality is, in that both law school and law as a practice, those opportunities might not come as readily as people might think. I think it was really cool to work on a project that would directly have a positive impact on many people.”
Jimenez noted the difference between the clinic experience and the Policy Lab – “they build two very different skill sets. Something I was looking for in the lab was how to address situations that don’t necessarily have a solution in the courtroom, and food deserts was one of them.”
“I think a lot of people, when they think of experiential education in law school, think of clinical work. I found the policy lab was another great way to teach my brain something new,” Gupta said.
“I’m proud of the way the students embraced this opportunity to conduct in-depth research and develop proposals with immediate, real world applications,” said VPA Director Sitaraman. “Their work is impressive and important, and I look forward to seeing how they carry forward the skills and insights they’ve developed into their future endeavors.”
VPA is part of Discovery Vanderbilt , a groundbreaking initiative to bolster innovative research and education at Vanderbilt. VPA focuses on cutting-edge topics in political economy and regulation to swiftly bring research, education, and policy proposals from infancy to maturity at a pace that aligns with the urgency of today’s challenges.
Explore Story Topics
- Vanderbilt Law News
- Home Page Feature
- newsroom sidebar
- research news side
- Student News
Keep Reading

Elodie Currier ’23 Takes First Place in 2023 Brown Award for Excellence in Legal Writing

What do Lawyers, Judges, and Policymakers Need to Know about Brain Science?

Why Rescheduling Marijuana Won’t Save the Marijuana Industry

IMAGES
COMMENTS
Research perspectives on TikT ok and its legacy apps: introduction. Zeng, Jing ; Abidin, Chrystal ; Schäfer, Mike S. Abstract: TikTok, a short-video app featuring video content between 15 and 60 ...
Introduction. TikTok is a social ... In light of user characteristics of the TikTok platform, this research is highly relevant because TikTok users are often adolescents and therefore from a group ...
This research paper is aimed at shedding light on the use of the mobile application Tiktok, it concluded that the use of the application, has had a very little negative impact on the main target ...
As of November 2020, 800 million monthly users have been reported 1, and 738 million first-time installs in 2019 have been estimated 2. TikTok use is allowed for those 13 years or older, but direct messaging between users is allowed only for those 16 or older (in order to protect young users from grooming) 3. In China, the main users of TikTok ...
TikTok allows users to consume and create short videos between 15-60 s in length; using various filters, music and lip-syncing templates. TikTok's unique selling point is that the content presented to an individual is algorithm-driven, and tailored to their indicated preferences and previously liked content (Anderson, 2020).It is particularly popular with the traditionally hard-to-reach 13 ...
Since its release in 2016, the video-sharing platform TikTok has enjoyed a meteoric rise in popularity: as of February 2021, it has been downloaded over 2.6 billion times worldwide (with 315 million of these downloads occurring in the first quarter of 2020), and has approximately one billion monthly active users (TikTok Statistics, 2021).Originally released by the Chinese company ByteDance ...
Introduction. Social media is ubiquitous in adolescents' lives. ... By the time of the final writing of this paper in May 2022, the global views for #anxiety had reached 13.9 billion. ... Fourth, we suggest that further research into TikTok as an alternative to specific apps for the self-management of anxiety may be warranted from an ...
In this paper I discuss the affordances and popularity of the short-video app TikTok from an audience studies point of view. I do so by drawing on findings from ethnographic fieldwork with young adult TikTok users based in the United Kingdom that was conducted in 2020 and 2021.
Introduction. #stayathome was a ... Since there is limited research on TikTok and the impact of COVID-19, there are several points future research can investigate: ... PRC, Paper 92. Google Scholar Xu, L., Yan, X., & Zhang, Z. (2019). Research on the causes of the "TikTok" app becoming popular and the existing problems. Journal of Advanced ...
TikTok is the fastest growing social network in the post-pandemic era. It was the most downloaded application globally in 2020 and 2021, achieving 1506 million downloads in these years, much more than Instagram, with 1048 million downloads (Forbes, 2020, 2021).Fig. 1 depicts these statistics. In 2020, 36.0% of US marketers employed TikTok for influencer marketing; in 2021, this percentage ...
This Special Section is among the first collections of articles in the growing field of studies on TikTok and its legacy apps that provides a glimpse of the nascent framings, approaches, methodologies, and applications of TikTok studies in the field of social media scholarship. TikTok, a short-video app featuring video content between 15 and 60 seconds long, has in the last few years become ...
Introduction . Launched in 2017, the video-sharing social network TikTok, quickly became one of the most ... The first potential direction in TikTok research is social network analysis or SNA in ...
This paper extends the existing research on the use of social media for knowledge mobilization and collaborative knowledge exchange, focusing explicitly on TikTok. It is among the first academic papers to draw attention to this fast-growing social media platform and its potential use as a digital knowledge mobilization tool.
Introduction. TikTok is a short-video application that became a popular communication tool for creating videos up to 10 min (increased from 3 min in March 2022) after its merger with 'Musical.ly' in August 2018. ... this paper aims to understand how teachers engage in micro-celebrification on TikTok through short, creative videos featuring ...
This research paper will start from introducing background information of TikTok and relevant theoretical framework, to explaining the research questions of the study and the methodologies adopted. Then, research findings will be displayed in an order of TikTok environment of expected use, to TikTok technical walkthrough, to interview findings.
Abstract. This Special Issue of "TikTok and Social Movements" emerges from an attempt to map out the landscape of social movements happening on TikTok, drawing from the online symposium "TikTok and Social Movements" hosted in September 2021 by the TikTok Cultures Research Network, a research portal for interdisciplinary scholarship on ...
Introduction TikTok is one of the most popular apps on social media. This app is the world‟s prominent destination for creating short-form ... In this paper, a primary research has been conducted through content analysis of parent‟s comments and feedback on TikTok and its effect on children. The idea was to look
Introduction. The term "side" of TikTok has emerged as a colloquial way to describe communities on the short-form video app. ... Our reasons were twofold: One, because extant TikTok research notes the app is "content-centric, rather than network-centric" (Kaye et al., 2022, p. 19), there would be creation practices, platform vernaculars ...
Introduction. With the development of technology, ... Current research on the short-form video app TikTok has focused on user adoption (Omar & Dequan, ... Research Methods. This paper is a conceptual work that outlines some research prepositions to understand TikTok addition behaviour. This proposed conceptual model should be tested empirically.
However, my research experience also underscores how the platform, particularly the algorithm of TikTok, regulated my self-portrayal, thereby highlighting the intricate nature of ethnographic spaces. Through the critical presentation of a vignette below, I centre my attention on the impact of TikTok in facilitating outreach to a more diverse ...
TikTok is a social network launched in the Chinese marke t. in 2016 (as Douyin) and internationally in 2017 (as TikTok). In 2018, it was the mos t downloaded mobile app in the United. States, and ...
USCA Case #24-1113 Document #2053212 Filed: 05/07/2024 Page 2 of 70 2. That law 1. Congress has taken the unprecedented step of expressly singling out and banning TikTok: a vibrant online forum ...
Video de TikTok de heal.me (@heal.meapp): «"Stay with me now" 🤣 👇 👀 A quote from a research paper published by Pubmed-National Library of Medicine: "Our prescription drugs are the third leading cause of death after heart disease and cancer in the United States and Europe. Around half of those who die have taken their drugs correctly". ⛅️ When we're doing well and ...
TikTok has one of the most advanced algorithm systems and is the most addictive as compared to other social media platforms. While research on social media addiction is abundant, we know much less about how the TikTok information system environment affects users' internal states of enjoyment, concentration, and time distortion (which scholars define as the flow experience), which in turn ...
The paper, published by the Vanderbilt Policy Accelerator (VPA) in March, begins with introduction to the significance and causes of Food Deserts, followed by an overview of solutions. It continues with a series of case studies detailing different public options - Publicly-Owned, Non-Profit, Public-Private Partnership, and Cooperative stores ...
Abstract. Recommendation algorithms are reshaping the ecology of digital video-sharing platforms and users' media usage behaviors. TikTok's recommender system is widely considered to be an ...