Vancouver Security Management
Create or edit vulnerability response assignment rules, table of contents.
- Understanding Security Operations
- Get entitlement for a Security Operations product or application
- Activate a ServiceNow Store application
- Install a Security Operations integration
- Update an application previously downloaded from the ServiceNow Store
- Upgrade your instance to the next family release
- Opt-in for benchmark scores
- Set targets
- Configure Knowbe4 integration
- Configure Microsoft Defender for Office 365 integration
- Domain separation and Security Incident Response
- Download and install the Security Analyst Workspace
- Components installed with Security Incident Response
- Other additional Security Incident Response setup tasks
- Setup Assistant reference
- Set up primary and secondary filters for Security Analyst Workspace
- Security Analyst Workspace properties
- Landing page filter configuration
- Enable UI Actions
- Form UI actions
- Related List UI Actions
- Form configuration system properties
- Enable playbooks for analyst selection
- Troubleshooting Security Incident Response
- CISO dashboard
- Security Incident Management Premium dashboard
- Security Incident Management dashboard
- Security Incident Explorer dashboard
- Security Operations Efficiency dashboard
- SIR Workspace plugins and roles
- SIR workspace features
- SIR Workspace interface overview
- View upcoming tasks
- Working with quick links
- Personalize a list
- Assign Security Incidents
- Assign Response Tasks
- Report Phish Email
- Add or modify quick filters
- Export Security Incidents or Response Tasks
- Set up view of SIR Records
- Creating View for associated info tables
- Adding an entry point list
- Mapping View of the Associate Info to the entry point list
- Configure each associated list from the view to handle run time data rendering
- SIR Workspace Related Records
- Security Incident Overview section
- Security Incident Details section
- Explore Investigation Canvas
- Unified experience capabilities and modal screens
- Select implementations
- Example 2: Common Inputs: Sighting Search
- Example 3: Add specific runtime details inputs to an implementation: Run Additional Actions
- Create a Response Task
- Security Incident Response Other Records
- Security Incident Response Post Incident Review
- Security Incident Playbook
- Prerequisites for the Playbooks
- Rebuilding existing playbooks on PAD
- Create an Activity Action
- Submit to CSF X Sandbox
- Sample Playbooks for SIR Workspace
- Propose as Major Security Incident
- Promote to Major Security Incident
- Link to Major Security Incident
- Working with Form UI actions
- Security Incident Closure workflow
- View Security Analyst Overview dashboard
- View Security Incident Explorer dashboard
- View Security Incident Management dashboard
- View Security Operations Efficiency dashboard
- View Security Incident Response Premium KPIs dashboard
- View Context Sensitive Analytics - SI dashboard
- View CISO dashboard
- View CISO Reporting Overview dashboard
- View Security Incident Manager Overview dashboard
- Create a security incident from the Security Incident list
- Create a security incident from the Security Incident Catalog
- Create a security incident from an Event Management alert
- Data imported into security alerts
- Create security incidents from User Reported Phishing emails
- Create a change, incident, or problem from a security incident
- Create a Customer Service case from a security incident
- Add a security incident to a security case
- Create response tasks
- Predictive Intelligence for User Reported Phishing
- Required components and plugins
- Final verdict generation for User Reported Phishing
- Troubleshooting Predictive Intelligence for User Reported Phishing
- Configure Predictive Intelligence for User Reported Phishing
- Assigning security analysts
- Create an inbound request
- Show IoC information for a security incident
- Create a security incident observable
- Manage file observables
- Edit a security incident observable list
- Add multiple security incident observables
- Automatic security incident observable log data enrichment
- Publish observables to a third-party watchlist
- Submit an IoC Lookup request from a security incident
- Submit an IoC Lookup request from the Security Incident Catalog
- Submit a vulnerability scan request from a security incident
- Submit a vulnerability scan request from the Security Incident Response catalog
- Perform on-demand orchestration from the Security Incident form
- Perform on-demand orchestration from the Security Incident list
- Register new Security Operations applications for on-demand orchestration
- Add related problems, changes, and incidents to a security incident
- Invoke a process dump for an enriched process in Windows
- Parent and child security incident relationships
- View affected items for a security incident
- View related items for a security incident
- View enrichment data for a security incident
- View response task information for a security incident
- View related events and alerts in security incidents
- View security incident to customer service case mapping
- View a Security Incident Response runbook
- Identify all configuration items affected by a security incident
- Calculate the severity of a security incident
- Search for and delete phishing emails
- Create a security incident knowledge article
- Escalate a security incident
- Assign post incident review roles
- Manage Post Incident Review Report
- Assessment trigger conditions examples
- Create post incident review questionnaire categories
- Compose post incident review questions
- Create PIR assignment rules
- Add closure information to a security incident
- Restrict access to security incidents
- Resolve security threats with the playbook
- Sightings searches on user-reported phishing and malware attacks
- Activate a Security Incident Response flow
- Add parallel activities
- Using the Manual Phishing playbook
- Workspace Playbook summary
- Create processes for Automated Phishing in PAD
- Using the Automated Phishing playbook
- Create processes for Manual Malware in PAD
- Using the Manual Malware playbook
- Create processes Automated Malware in PAD
- Using the Automated Malware playbook
- Create processes for Failed Login Manual in PAD
- Using the Failed Login Manual playbook
- View automated phishing response playbook flow action designer
- View the automated phishing response playbook subflow designer
- Run the automated malware playbook flow
- Playbook for Failed Login Manual
- Playbook for Child Security Incident Automation
- Use the Office 365 Malicious File Detected playbook
- Use the Repeat Detection playbook
- Use the Spoofed Emails (using the same Display name) playbook
- Use the Endpoint Detection playbook
- Use the Possible Password Spray playbook
- Use the T1003 - Detect Credential Dumping Tools playbook
- Use the Email Domain Spoofing Detection playbook
- Use the Typo Squatted Domain playbook
- Use the Credential Sniffing playbook
- Use the T1070 - Windows Events Logs Cleared playbook
- Use the OSquery of External Address in the /etc/hosts file playbook
- Use the User Deleting Bash History playbook
- Use the Successful VPN Attempts from the Service Accounts playbook
- Use the Attempted Access to Deactivated Accounts playbook
- Use the T1003 - Defense Evasion - Mimikatz DCShadow playbook
- Use the T1003 - Credential Dumping - Mimikatz DCsync playbook
- Use the Okta User Login Failures from Multiple IPs playbook
- Use the ModSec Brute force by IP Burst playbook
- Security Incident Response playbook actions
- Access Security Incident Response Explorer
- Add map to Security Incident Response overview
- Modify security incident map
- Add treemaps to the Security Incident Response overview
- Create or update a treemap category
- Create or update a treemap indicator
- Add vulnerability significance charts to an overview
- Major Security Incident Management
- Get started with MSIM
- Checklist for Major Security Incident Management setup
- Major Security Incident Management roles
- Set up Microsoft SharePoint Document Library
- Configure REST Connection for MS SharePoint
- Configure Graph Connection for MS SharePoint
- Attach a Java Key Store certificate for MS Teams
- Configure the JWT signing key for MS Teams
- Configure the JWT provider for MS Teams
- Establish a connection using certificates
- Establish a connection using client secret
- Activate MS Teams chat connector for MS Teams Graph Spoke user
- Start a conference call
- Add participants to a conference call
- Mute participants in a conference call
- View conference call details
- Use the MSIM Conference Call Microsoft Teams integration
- Use the MSIM Conference Call Zoom integration
- Use the Conference Calls Cisco Webex integration
- Get Started with File Explorer
- Configure File Explorer Repository Drive
- Configure Folder and File Action Settings
- Create Folder Templates
- File Explorer Activity Stream in Workspace
- File Explorer troubleshooting
- Get started with Microsoft Teams
- Activate MS Teams as a chat provider
- Create a chat channel template
- View Chat Message Activity
- MS Teams Chat Connector Troubleshooting for MSIM
- Major Security Incident Management administration
- Major Security Incident Management workspace
- Propose as a Major Security Incident
- Promote to a Major Security Incident
- Using MSI List view in the MSIM workspace
- View Major Security Incident trend charts
- View Major Security Incident impact metrics
- Restrict access to certain major security incidents
- Link additional records to Major Security Incident
- Unlink records from Major Security Incident
- Manage tasks using the Visual Task Board
- Manage tasks using the List view
- Track collaboration activity via MSIM workspace
- Create and distribute MSIM Status Reports
- Add Branding to your Report Templates
- Use Visualizations in Report Templates
- Use Reports Lists in Report Templates
- Use Template Scripts in your Report Templates
- Preview the Report Template
- Create a Report Section Template
- Create a Report Subsection Template
- Create a Free Form Type Element
- Create a Visualization Type Element
- Create a List Type Element
- Create a Custom Type Element
- Add system properties
- Configure Linked Records in Major Security Incident Management
- Configure Rollup Records in Major Security Incident Management
- Configure List Layout in Major Security Incident Management
- Step 1. Create linked record configuration for a Security Case
- Step 2. Create a view for modal window for a Security Case
- Step 3. Create UI actions for the Source Table for a Security Case
- Step 4. Create a view for a new Linked Record Tab for a Security Case
- Step 5. Add Access Control Lists (ACLs) for Major Security Incident Management workspace users
- Step 6. Create business rules for a Security Case
- Step 7. Create rollup record configurations
- Perform on demand atomic rollup
- Set up the ArcSight ESM Query Viewer
- Install and configure the ServiceNow application for the ArcSight ESM Event Ingestion integration
- Create and name the profile for ArcSight ESM event ingestion integration
- Select correlation events for ArcSight ESM event ingestion integration
- Create mappings for ArcSight ESM event ingestion integration
- Preview the security incident for the ArcSight ESM event ingestion Integration
- Create a schedule for ArcSight ESM event ingestion ingestion
- Additional options: Automate correlated event updates and closure based on SIR incident status
- ArcSight ESM Integration Settings for event ingestion integration
- Troubleshooting ArcSight ESM event ingestion integration
- Copy ArcSight ESM profile for event ingestion integration
- Use the script editor to format correlation event values for ArcSight ESM integration
- Flow Designer usage with ArcSight ESM event ingestion integration
- Get started with the Carbon Black - Incident Enrichment integration
- Get started with the Carbon Black integration
- Check Point Anti-bot - Email Parser integration
- Create an API account for the Check Point NGTP integration
- Set up the Check Point NGTP integration
- Activate the Check Point NGTP integration
- Create a block list for the Check Point NGTP integration
- Activate a block list for the Check Point NGTP integration
- Configure a block list as a Custom Intelligence Feed on the Check Point NGTP integration
- Submit block list entries from a security incident for the Check Point NGTP integration
- Submit block list entries directly from the Block List Entry Table
- Approve block list entries for the Check Point NGTP integration
- Block list entry exceptions for the Check Point NGTP integration
- Edit the security tag name for the Check Point NGTP integration
- Uninstall the Check Point NGTP integration
- Get started with the CrowdStrike Falcon Host integration
- Collect CrowdStrike Falcon Host Configurations activity
- Publish to Watchlist activity
- Getting started with the CrowdStrike Falcon Insight integration
- Create CrowdStrike API client and generate keys
- Install and configure CrowdStrike Falcon Insight
- Create an approval group
- Create a capability profile for the CrowdStrike Falcon Insight integration
- Configure profiles and security incidents for the CrowdStrike Falcon Insight integration
- How trigger conditions work with a configuration item for a profile
- Verify CrowdStrike Falcon Insight profile trigger conditions
- Trigger a CrowdStrike Falcon Insight profile manually from a security incident
- Create and configure a profile for the sighting search
- Configure and trigger additional actions in CrowdStrike Falcon Insight
- Using CrowdStrike Falcon Insight integration in Analyst Workspace
- Get started with the CrowdStrike Falcon X Sandbox integration
- Set up Sandbox submission configurations
- Manually submit files or URLs to Sandbox
- Automate CrowdStrike Falcon Sandbox submissions using Flow Designer
- Monitor the submission results in the sandbox
- Tag security incidents with the Sandbox submission status
- Review the sandbox global settings
- Get started with the Elasticsearch - Incident Enrichment integration
- Set up your NowPlatform instance for FireEye integration
- Configuring Timestamp Settings for Triage Acquisition
- FireEye Default Settings
- Create a new capability profile for the FireEye Endpoint integration
- Understand how trigger conditions work with a configuration item
- Verify the Trigger Condition Filters
- Trigger a FireEye capability profile from Related Links
- Trigger a FireEye Capability profile from Configuration Item related list
- FireEye Get File Capability
- FireEye Additional Actions on Endpoint
- Create and configure a profile for sightings search with the FireEye Integration
- Invoke Sighting Search from a Security Incident
- Activate the Security Operations Have I been pwned? integration
- Update your X.509 certificate
- Threat Lookup - Have I been pwned? workflow
- HPE Security ArcSight ESM - Email Parser integration
- Get started with the HPE ArcSight Logger - Incident Enrichment integration
- Install and configure Hybrid Analysis
- Verify expected results for Hybrid Analysis
- (Optional) Manually attach an observable for Hybrid Analysis
- Install and configure the ServiceNow application for the IBM QRadar offense ingestion integration
- Create profiles for ingesting IBM QRadar offenses
- Select IBM QRadar rules
- Ingesting the sample IBM QRadar offenses
- Mapping IBM QRadar offense fields to security incident response fields
- Preview the security incident for the IBM QRadar integration
- Define schedule for the IBM QRadar integration
- Automate offense updates and closure based on SIR incident status
- IBM QRadar integration configuration settings
- Optional: Copy a IBM QRadar profile
- Domain separation and IBM QRadar Offense Ingestion
- Security Incident Response form after offense ingestion
- Flow Designer and Integration Hub usage with IBM QRadar offense ingestion integration
- Troubleshooting IBM QRadar offense ingestion integration
- Get started with the IBM QRadar - Incident Enrichment integration
- Set up the REST API for LogRhythm
- Install the plugin and configure LogRhythm
- Map LogRhythm alarm fields to security incident fields
- Filter alarms for LogRhythm
- Previewing the security incident with mapped LogRhythm alarm values
- Schedule and retrieve LogRhythm alarms
- Additional options for LogRhythm alarms
- Use the script editor to format LogRhythm values
- Copy an alarm profile for LogRhythm
- Disable automated alarm closure for LogRhythm
- View LogRhythm drilldown events
- Verify connectivity for LogRhythm
- Script execution and system log for LogRhythm
- Integration architecture for McAfee ePO
- Checklist for the McAfee ePO integration
- Set up your Now Platform® instance for the McAfee ePO integration
- Set up your McAfee ePO console to integrate with Security Incident Response (SIR)
- Install the application and configure a server for the McAfee ePO integration
- Edit security tags in the Now Platform for the McAfee ePO integration
- Create a capability profile for the McAfee ePO integration
- Defining triggering conditions with a Configuration item (CI) field for a McAfee ePO profile
- Configure profiles and security incidents for system enrichment queries for the McAfee ePO integration
- Trigger McAfee ePO profile manually from a security incident
- Trigger additional actions in McAfee ePO integration
- Using McAfee ePO integration in Analyst Workspace
- Configure McAfee ESM - Email Parser integration
- Get started with the McAfee ESM - Incident Enrichment integration
- Get started with Microsoft Azure Sentinel integration
- Register and configure the Microsoft Azure portal
- Install and configure the Microsoft Azure Sentinel integration
- Create a profile for Microsoft Azure Sentinel
- Map the Microsoft Azure Sentinel incident fields
- Defining filter and aggregation criteria
- Schedule the Microsoft Azure Sentinel incident retrieval
- Automate the incident updates and closures by the SIR incident status
- Copy a Microsoft Azure Sentinel profile
- SIR form after an incident ingestion
- Review the Microsoft Azure Sentinel integration settings
- Domain separation and the Microsoft Azure Sentinel integration
- Comparing Microsoft Azure Sentinel and Microsoft Graph Security API integrations with SIR
- Register and configure the Microsoft Defender for Endpoint in the Microsoft Azure portal
- Get started with the Microsoft Defender for Endpoint integration
- Microsoft Defender for Endpoint Default Settings
- Map the Microsoft Defender for Endpoint indicator types
- Create a capability profile for the Microsoft Defender for Endpoint integration
- Trigger conditions in a configuration item
- Trigger the Microsoft Defender for Endpoint capabilities from Related Links
- Trigger the Microsoft Defender for Endpoint from Configuration Item related list
- Configure Isolate Host capability in Microsoft Defender for Endpoint
- Configure Remove Host Isolation capability in Microsoft Defender for Endpoint
- Configure Run Antivirus Scan capability in Microsoft Defender for Endpoint
- Configure Restrict App Execution capability in Microsoft Defender for Endpoint
- Configure Remove App Restriction capability in Microsoft Defender for Endpoint
- Configure Get Related Machines from Defender Capability in Microsoft Defender for Endpoint
- Configure Stop and Quarantine File capability in Microsoft Defender for Endpoint
- Perform a manual sighting search in Microsoft Defender for Endpoint
- Perform an automatic observable enrichment in Microsoft Defender for Endpoint
- Perform a manual observable enrichment in Microsoft Defender for Endpoint
- Update indicators in Microsoft Defender for Endpoint
- Domain separation in Microsoft Defender for Endpoint integration
- Rate limit configuration in Microsoft Defender for Endpoint integration
- Set up your Microsoft Azure account for the ServiceNow Microsoft Exchange Online integration
- Set up Exchange Online Integration with Security Incident Response
- Set up your Now Platform® instance for the Microsoft Exchange Online integration
- Install the Microsoft Exchange Online application for the ServiceNow Microsoft Exchange Online integration
- Configure the Microsoft Exchange Online integration with your Now Platform instance
- Define email search criteria and request a search on the Microsoft Exchange Online service
- Request delete approval for emails on Microsoft Exchange online service
- Approve delete email requests for the Microsoft Exchange Online integration
- Integration architecture and external systems connection for the Microsoft Exchange Online integration
- Recover deleted emails on the Microsoft Exchange Online service
- Edit security tags in the Now Platform for the Microsoft Exchange Online integration
- Checklist for the Microsoft Exchange Online integration
- Troubleshooting Microsoft Exchange Online integration
- Get started with the Microsoft Exchange On-Premises integration
- Microsoft Exchange - Perform Email Search and Deletion workflow
- Configure the Microsoft Azure portal
- Install and configure the Servicenow application for Microsoft Graph Security API alert ingestion integration
- Identify the source for the profile
- Ingest sample Microsoft Graph Security API alerts
- Mapping alerts to security incident response fields
- Preview the security incident for the Microsoft Graph Security API integration
- Define schedule for Microsoft Graph Security API integration
- Automate alert updates and closure based on SIR incident status
- Microsoft Graph Security API integration configuration settings
- Security Incident Response form after alert ingestion
- Optional: Copy a Microsoft Graph Security API profile
- Domain separation and Microsoft Graph Security API alert ingestion
- Flow Designer and Integration Hub usage in Microsoft Graph Security API integration
- Troubleshooting Microsoft Graph Security API integration
- Activate and configure Palo Alto Networks - AutoFocus integration
- Get AutoFocus Session Info Enrichment workflow
- Set up SSH credentials to the MID Server
- Activate and configure the Palo Alto Networks Firewall Integration
- Security Operations Integration Palo Alto Networks Firewall Launcher workflow
- Security Operations Palo Alto Networks - Check and Block Value workflow
- Get Log Data workflow
- Activate Security Operations Palo Alto Networks - WildFire
- Get WildFire Data Enrichment workflow
- Create a certificate profile for the Palo Alto Networks Next-Generation Firewall
- Set up and install Palo Alto Networks Next-Generation Firewall
- Create the API account role for Palo Alto Networks Next-Generation Firewall
- Supported External Dynamic Lists for Palo Alto Networks Next-Generation Firewall
- Create an EDL for Palo Alto Networks Next-Generation Firewall
- Configure an EDL in Palo Alto Networks Next-Generation Firewall
- Activate an EDL for Palo Alto Networks Next-Generation Firewall with a change request
- Submit EDL entries from a security incident record for Palo Alto Networks Next-Generation Firewall
- Submit EDL entries from the blocklist for Palo Alto Networks Next-Generation Firewall
- Approve EDL entries for Palo Alto Networks Next-Generation Firewall
- EDL entry exceptions for Palo Alto Networks Next-Generation Firewall
- (Optional) Edit the security tag name for Palo Alto Networks Next-Generation Firewall
- Uninstall Palo Alto Networks Next-Generation Firewall
- Install and configure PhishTank
- Verify expected results for PhishTank
- (Optional) Manually attach an observable for PhishTank
- Install and configure Reverse Whois
- (Optional) Install and configure Whois
- Initiate the lookup for Reverse Whois
- Verify expected results for Reverse Whois
- (Optional) Run enrichment lookup and verify expected results for Whois
- Supported observables for RISKIQ and RISKIQ WHOISIQ
- Install and configure RISKIQ and WHOISIQ
- RISKIQ SSL certificate lookups that return an exact match
- RISKIQ SSL certificate lookups that return multiple certificates or no certificates
- Verify expected results for WHOISIQ URL lookups
- Create an observable for manual WHOISIQ lookups
- Verify expected results for manual WHOISIQ lookups
- Install and configure Shodan
- Verify expected results for Shodan
- (Optional) Manually attach an observable for Shodan
- Install and configure the ServiceNow application for the Secureworks CTP ticket ingestion integration
- Identify the source of the profile
- Ingesting the sample Secureworks tickets
- Mapping Secureworks ticket fields to security incident response fields
- Preview the mapped values in the security incident
- Define schedule for the Secureworks CTP Ticket ingestion
- Automate ticket updates and closure based on SIR incident status
- Optional: Copy a Secureworks CTP profile
- Security Incident Response form changes after ticket ingestion
- Secureworks CTP Master Ticket Closure Notice
- Secureworks CTP integration configuration settings
- Getting started with Security Incident Response integration with Zscaler
- Configure access to Zscaler Internet Access APIs
- Install and configure Security Incident Response integration with Zscaler
- Add Zscaler Internet Access URL category lists
- Submit observables from a security incident record to a URL category list
- Approve observables to URL category lists
- Submit the security incident to the Zscaler URL category list
- Run a threat lookup by using the Zscaler global threat library
- Submit to Zscaler Sandbox analysis
- Set up email alerts for Patient 0 events
- Download the ServiceNow Security Operations application
- Install the ServiceNow Security Operations add-on for Splunk
- Configure Application Registry on the ServiceNow instance
- Manual search commands
- Splunk event actions
- Single-record Splunk alerts
- Create a multi-record, custom field Splunk alert
- Multi-record, custom field Splunk alert examples
- Splunk error reporting
- Set up your Now Platform® instance for the Splunk Enterprise Event Ingestion integration
- Configure Splunk Enterprise Event Ingestion settings
- Select scheduled alerts for the Splunk Enterprise Event Ingestion integration
- Mapping alerts and events for the Splunk Enterprise Event Ingestion integration
- Map alerts for the Splunk Enterprise Event Ingestion integration
- Preview the security incident for the Splunk Enterprise Event Ingestion integration
- Schedule and retrieve alerts for the Splunk Enterprise Event Ingestion integration
- Copy Splunk Enterprise Event Ingestion profiles from one instance to another using export/import functionality
- Copy an event profile for the Splunk Enterprise Event Ingestion integration
- Set up your Splunk environment for manual event ingestion for the Splunk Enterprise event ingestion integration
- Save searches in your Splunk Enterprise console for the Splunk Enterprise Event Ingestion integration
- Use the script editor to format alert values for the Splunk Enterprise Event Ingestion integration
- Checklist for the Splunk Enterprise Event Ingestion integration
- Key terms used in this integration
- Set up your Now Platform® instance for the Splunk Enterprise Security integration
- Configure Splunk Enterprise Security settings
- Authentication errors
- Create and name an event profile for the Splunk Enterprise Security event ingestion integration
- Copy an event profile for the Splunk Enterprise Security Event Ingestion integration
- Use the script editor to format alert values for the Splunk Enterprise Security Event Ingestion integration
- Copy Splunk Enterprise Security profiles from one instance to another using export/import functionality
- Checklist for the Splunk Enterprise Security Notable Event Ingestion integration
- Get started with the Splunk Search integration for Security Operations
- Activate and configure the Security Operations Tanium integration
- Configure for MID Server access
- Tanium - Get File Details workflow
- Tanium - Get Running Processes workflow
- Set up checklist for the Security Incident Response Mobile app
- Log in to the Security Incident Response Mobile app
- View, edit, and assign open security incidents with the Security Incident Response Mobile app
- View, edit, and reassign security incidents assigned to you with the Security Incident Response Mobile app
- View, edit and assign unassigned security incidents with the Security Incident Response Mobile app
- View, edit, and assign high priority incidents with the Security Incident Response Mobile app
- View, edit, and assign security incidents with a risk score greater than 60 with the Security Incident Response Mobile app
- Search for security incidents with the Security Incident Response Mobile app
- View, edit, and assign open response tasks with the Security Incident Response Mobile app
- View, edit, and reassign your response tasks with the Security Incident Response Mobile app
- Filter records with the Security Incident Response Mobile app
- Set up Security Incident Response Orchestration
- Create IoC Lookup Request activity
- Security Incident Response - Get Network Statistics workflow
- Security Operations System Command Integration - Get Running Processes workflow
- Get Configuration Item FQDN activity
- Determine Shell Script by OS activity
- Get Running Services - WMI Enrichment
- Create Enrichment Data records activity
- Execute procdump activity
- Security Incident - Evaluate response task outcome workflow
- Security Incident Confidential Data Exposure workflow template
- Security Incident Denial of Service workflow template
- Security Incident Lost Equipment workflow template
- Security Incident Malicious Software workflow template
- Security Incident Phishing workflow template
- Security Incident Policy Violation workflow template
- Security Incident Reconnaissance workflow template
- Security Incident Rogue Server or Service workflow template
- Security Incident Spam workflow template
- Security Incident Unauthorized Access workflow template
- Security Incident Web/BBS Defacement workflow template
- Install the supported applications for Security Posture Control
- Service Graph Connectors for Security Posture Control
- Activate a policy for a use case in Security Posture Control
- Create, clone, and activate a policy for Security Posture Control
- Create and activate a custom insight for Security Posture Control
- Configuring and viewing your findings for Security Posture Control
- Create an asset search in Security Posture Control
- Security Posture Control use case: Detecting assets with missing endpoint protection
- Security Posture Control use case: Detecting assets missed by vulnerability assessment tools
- Security Posture Control use case: Detecting unmanaged assets
- Security Posture Control use case: Detecting assets missing an endpoint management solution
- Security Posture Control use case: Detecting assets with vulnerabilities and security tool coverage gaps
- Security Posture Control use case: Detecting internet exposure of cloud assets and high-risk combinations
- Installation of Vulnerability Response and supported applications
- Vulnerability Response personas and granular roles
- Vulnerability Response assignment rules overview
- Vulnerability Response remediation tasks and task rules overview
- Vulnerability Response remediation target rules
- Vulnerability classification groups and rules
- Machine Learning solutions for Vulnerability Response
- Unclassed hardware
- Unmatched CIs
- Updating CI class for unmatched cloud assets
- CI changes for discovered items
- Re-evaluating discovered items
- Vulnerable item age calculation and display
- Removing assignments from vulnerable items and remediation tasks
- Vulnerability Response calculators and vulnerability calculator rules
- Vulnerability Response vulnerable item detections from third-party integrations
- Understanding the Microsoft Security Response Center Solution Integration
- Understanding the Red Hat Solution Integration
- Rapid7 solution management
- Preparing the Common Vulnerability Reporting Framework (CVRF) solution integration
- Patch orchestration with Vulnerability Response
- Exception Management overview
- Exception rules overview
- False Positive overview
- Watchdog for Vulnerability Response
- Change management for Vulnerability Response
- Software exposure assessment using Software Asset Management (SAM)
- Vulnerability Crisis Management
- Domain separation and Vulnerability Response
- Service Mapping in Vulnerability Response
- Components installed with Vulnerability Response
- Manage persona and granular roles for Vulnerability Response
- Importing data with the NVD and CWE integrations and managing third-party libraries
- Install the Solution Management for Vulnerability Response application
- Install and configure the Performance Analytics for Vulnerability Response [PA] application
- Create a Vulnerability Response assignment rule using ML
- Create a Vulnerability Response assignment rule for service support
- Create or edit Vulnerability Response remediation task rules
- Define fields and weights for the risk rule for Vulnerability Response Risk Calculators
- Vulnerability Response Rollup Calculators
- Create or edit Vulnerability Response remediation target rules
- Configure installed solution integrations for Vulnerability Solution Management using Setup Assistant
- Configure the MS TVM Vulnerability Integration using Setup Assistant
- Configure the Qualys Vulnerability Integration using Setup Assistant
- Configure the Tenable Vulnerability Integration using Setup Assistant
- Import Common Vulnerability Reporting Framework data through file import
- Configure Connection and Credential aliases
- Configure a Common Vulnerability Reporting Framework vendor other than Cisco
- Import Common Vulnerability Reporting Framework data from advisories
- Import Common Vulnerability Reporting Framework (CVRF) data through CVRF URL
- Troubleshooting Common Vulnerability Reporting Framework data import
- Run the Automated Test Framework (ATF) test suite for Vulnerability Response
- Configure Vulnerability Assignment Recommendations for Vulnerability Response
- Create and train a solution definition for Vulnerability Response
- Disable the default vulnerability calculator if not used
- Create, enable, or, modify Vulnerability Response auto delete rules
- Add vulnerability significance charts to the Vulnerability Response homepage
- Define Vulnerability Response email templates
- Create or edit remediation target notifications
- Configure Exposure Assessment
- Add an exception approver
- Create configurations for an approval rule
- Create approval levels for Exception Management
- Exception management workflow versus flow designer
- Add a false positive approver
- Configure questionnaire for risk reduction
- View Vulnerability Response SLAs for remediation tasks
- Configure watchdog
- Create and support multiple domains in the background jobs framework
- Ignore CI classes
- Filter decommissioned CIs
- Auto-promote CIs
- Adding proof to Rapid7 vulnerable item keys
- Delete all your vulnerable item records and related data in Vulnerability Response
- Filtering within Vulnerability Response
- Create a Vulnerability Response severity map
- Define service classifications for Vulnerability Response reporting and related lists
- Audit selected fields in the vulnerable items table
- Define background job configurations in Vulnerability Response
- Advanced parallel processing for background jobs in Vulnerability Response
- Preparing for the NVD integrations
- Configure and run the scheduled job for updating CWE records
- Install the Vulnerability Response Integration with the NIST National Vulnerability Database
- Perform a manual NVD integration import
- View the (National Vulnerability Database) NVD integration import run status
- Add CVEs to third-party entries
- View Vulnerability Response vulnerability libraries
- Preparing for the CISA integration
- Install the ServiceNow® Vulnerability Response Integration with CISA application
- Configure and run a scheduled job to update CVE records with EPSS data
- Add EPSS Score condition in Risk calculator Business Rule
- Preparing for the Microsoft Threat and Vulnerability Management Vulnerability Integration
- Set up Microsoft Azure for the MS TVM integration
- Install and configure the Vulnerability Response Integration with the MS TVM application using Setup Assistant
- Data retrieval settings for the Microsoft Threat and Vulnerability Management Integration
- Data transformation for the Microsoft Threat and Vulnerability Management Vulnerability Integration
- Verify the Microsoft Threat and Vulnerability Management integration import run status
- Integrations and dependencies of the Vulnerability Response Patch Orchestration integration with HCL BigFix
- Prepare for the Vulnerability Response Patch Orchestration integration with HCL BigFix
- Install the Vulnerability Response Patch Orchestration with HCL BigFix application
- Configure the Vulnerability Response patch orchestration integration with HCL BigFix
- Viewing patch data for the Vulnerability Response patch orchestration integration with HCL BigFix
- Schedule patches with the Vulnerability Response patch orchestration integration HCL BigFix
- REST messages for the Vulnerability Response patch orchestration integration with HCL BigFix
- Data transformation for the patch orchestration integration with HCL BigFix
- Example workflow for the Vulnerability Response patch orchestration integration with HCL BigFix
- Integrations and dependencies of the Vulnerability Response Patch Orchestration with the Microsoft SCCM application
- Prepare for the Vulnerability Response patch orchestration integration with Microsoft SCCM
- Install the Vulnerability Response Patch Orchestration with Microsoft SCCM application
- Configure the Vulnerability Response Patch Orchestration with Microsoft SCCM integration
- Viewing patch data and patch data rollup for the Vulnerability Response Patch Orchestration integration with Microsoft SCCM
- Schedule patches with the Microsoft SCCM integration with Vulnerability Response
- REST messages for the Vulnerability Response Patch Orchestration with Microsoft SCCM
- Data transformation for the Patch Orchestration with Microsoft SCCM Integration
- Example workflow for the Vulnerability Response Patch Orchestration integration with Microsoft SCCM
- Preparing for the Qualys Vulnerability Integration
- Activate the Qualys scanners
- Components installed with the Qualys Vulnerability Integration
- Update configuration items with the network partition identifier for the Qualys Vulnerability Integration
- Optional Qualys modifications
- Advanced Qualys configurations and modifications
- Import additional metadata from Qualys
- Qualys metadata values for vulnerabilities
- Set additional filter parameters for Qualys imports
- Resolving Qualys Vulnerability Integration issues
- Qualys integration run status chart
- Dynamic Search List Import
- Static Search List Import
- Asset Group Import
- Appliance Import
- Qualys REST messages
- Set up for the Rapid7 data warehouse Integration
- Set up for the Rapid7 InsightVM Integration
- Configure the Rapid7 Vulnerability Integration
- Prepend SITE to your Rapid7 InsightVM site tags
- Deduplicate Rapid7 Vulnerability Integration data warehouse records
- View the Rapid7 Vulnerability Integration import runs status dashboard
- Initiate rescan for the Rapid7 Vulnerability Integration
- Set additional filter parameters for Rapid7 InsightVM imports
- Preparing for the Shodan Exploit Integration
- Set Shodan Exploit Integration import time
- Perform a manual Shodan exploit import
- View the Shodan Exploit Integration import run status
- Tenable.io integrations with the Vulnerability Response and Configuration Compliance applications
- Tenable.sc integrations with the Vulnerability Response application
- Preparing for the Tenable Vulnerability Integration
- Install the Vulnerability Response Integration with Tenable application using Setup Assistant
- Data retrieval settings for the Tenable Vulnerability Integration
- Data transformation for the Tenable Vulnerability Integration
- Set additional filter parameters for Tenable.io imports
- Integration run status chart for the Tenable Vulnerability Integration
- Initiate rescan for the Tenable.sc integration
- Initiate rescan for the Tenable.io integration
- Update configuration items with the network partition identifier for the Tenable Vulnerability Integration
- Import modifications for the Tenable Vulnerability Integration
- Preparing for the Jira Vulnerability Response integration
- Install the Vulnerability Response Integration with Jira
- Create agile issue manually using list action
- Create agile issue manually using form action
- Configure scheduler to create issues automatically
- Configure scheduler to update issues automatically
- Configure scheduler to synchronize the Jira status to ServiceNow® automatically
- Single call integrations
- Multiple call integrations
- Attachments as retrieveData() return values
- Use the data source attachment report processor strategy
- About custom report processor scripts
- Integration factory script fields
- Manually run a vulnerability integration
- Ingest vulnerabilities manually
- Verify manual integration run
- Configure auto-close manual detections
- Verify upload status
- Template for manual ingestion of vulnerabilities
- Patch orchestration with the Vulnerability Response Workspaces
- Vulnerability Response Workspaces and updates to remediation tasks and remediation task rules
- Configure the Vulnerability Response Workspaces
- Home page overview
- Related items list and visualizations in a watch topic (v15 to v17.1)
- Related items list and visualizations in a watch topic (v18.0 and later)
- Life cycles of remediation efforts, remediation tasks, and records in the Vulnerability Response Workspaces
- Lists overview
- Understanding compensating controls for risk reduction
- Unified Vulnerability Response Dashboard
- Create filters to visualize the summary of active records
- Create a watch topic in the Vulnerability Manager Workspace
- Edit or delete a watch topic
- Deactivate or activate a watch topic
- Create a remediation effort in the Vulnerability Manager Workspace
- Create a remediation task on-demand in the Vulnerability Manager Workspace
- Create a recurring remediation effort in the Vulnerability Response Workspaces
- Transfer records to remediation efforts in the Vulnerability Response Workspaces
- Associate compensating controls with CVEs or TPEs for risk reduction requests
- Disable or enable risk reduction for a CVE or TPE
- Edit host vulnerable items in bulk in the Vulnerability Manager Workspace
- Request exceptions for remediation tasks and records from the Vulnerability Manager Workspace
- Request an extension for a deferred vulnerable item in the Vulnerability Manager workspace
- Rescan records and remediation tasks in the Vulnerability Manager Workspace
- Dashboards overview
- Create a customised list of records
- Approve or reject requests in the Vulnerability Manager Workspace
- Set up email notifications in the Vulnerability Response Workspaces
- Create Watch Topic form fields
- Create change request form fields
- GRC request exception form fields
- Generate remediation digest fields
- Impact of the compensating controls on risk score and expiration date
- View a workflow example in the IT Remediation Workspace
- Use the email digest in the Vulnerability Response Workspaces
- Use records in the IT Remediation Workspace
- Use remediation task records in the IT Remediation Workspace
- Use the List view in the IT Remediation Workspace
- Assign a remediation task to yourself in the IT Remediation Workspace
- View configuration items with vulnerabilities in the IT Remediation Workspace
- Request a False Positive in the IT Remediation Workspace
- Create a change request in the IT Remediation Workspace
- Split a remediation task in the IT Remediation Workspace
- Request an exception in the IT Remediation Workspace
- Request an exception using GRC: Policy and Compliance Management in the IT Remediation Workspace
- Request risk reduction in the IT Remediation Workspace
- Rescan Qualys vulnerable items from the Vulnerability Response workspaces
- Rescan Rapid7 vulnerable items from the Vulnerability Response workspaces
- Rescan Tenable.io and Tenable.sc vulnerable items from the Vulnerability Response workspaces
- Request exception form fields for policy exceptions
- Add CVEs to assess exposure
- Create VIs for CVEs for exposure assessment
- Activate or deactivate CVEs for exposure assessment
- Export impacted CIs for exposure assessment
- View vulnerable software details
- Confidence score reference tables for exposure assessment
- Add software for exposure assessment
- Create VIs for software for exposure assessment
- Activate or deactivate software for exposure assessment
- Export impacted CIs for software in the Vulnerability Assessment workspace
- Create a vulnerability assessment record
- Modify the vulnerability assessment record
- Assessment tab
- Overview tab
- Assign a priority and exposure level to the vulnerability assessment record
- Add affected CIs to the assessment record
- Create vulnerable items for the affected CI or affected software component
- Link the vulnerability assessment record to major security incident in Major Security Incident Management
- Verify successful completion of Vulnerability Response integration imports
- Verify Vulnerability Response vulnerable item detection data on integration run (VINTRUN) records
- Patch data and state rollup for patch orchestration in Vulnerability Response
- View patches without solutions in Vulnerability Response
- Viewing patch orchestration data on the Vulnerability Response dashboards
- View a solution
- Manually exclude solutions from third-party records or vice versa
- Edit vulnerable items in bulk in Vulnerability Response
- View ungrouped Vulnerability Response vulnerable items
- Manually add a vulnerable item to a remediation task
- Remove assignments from vulnerable items for you or your groups
- Approve or reject an unassign request in Vulnerability Response
- Working with retired configuration items
- Automatically close vulnerable items related to retired CIs
- Automatically close stale detections in Vulnerability Response
- Add users to the Vulnerability Response group
- Request an extension for a deferred vulnerable item
- Identify and escalate security issues in third-party software
- Identify and escalate security issues using NVD
- Identify and escalate security issues using CWE
- View the remediation target status of a Vulnerability Response vulnerable item
- Reclassify unclassed hardware
- View and reclassify unmatched configuration items
- Reapply CI lookup rules on selected discovered items
- Steps to help prevent duplicate or orphaned records after running Vulnerability Response CI lookup rules
- De-duplicating existing configuration items
- Request an extension for a deferred remediation task
- Close a remediation task
- Automatically resolve duplicate vulnerabilities
- Create and edit a classification rule
- Apply a rule to an existing vulnerability
- Deactivate or delete a classification rule
- Create a change request from a remediation task
- Associate a remediation task to an existing change request
- Split a remediation task
- State synchronization between change requests and remediation tasks
- Assess your exposure to vulnerable software
- Request assignment group recommendations for a vulnerable item
- Request assignment group recommendations for multiple vulnerable items
- Request assignment group recommendations for a remediation task
- Request an exception for a vulnerable item
- Request an exception for a remediation task
- Request a bulk exception
- Request a bulk exception using GRC: Policy and Compliance Management
- Approve an exception request in Vulnerability Response
- Create an exception rule
- Approve an exception rule request
- Activating an exception rule
- Request an extension for an exception rule
- Reopen an exception rule
- Update an approved exception rule
- Delete an exception rule
- Bulk edit for false positive
- Approve a false positive
- Using the default Vulnerability Response dashboards
- View Performance Analytics for Vulnerability Response [PA] reports in real-time
- View the Performance Analytics indicators for Vulnerability Response [PA]
- Configure the Scan Coverage reports
- Configure the PA indicators for the CISO Dashboard
- Modifying the threshold values
- Implementation checklist for the Vulnerability Response application
- Detections, remediation tasks, and vulnerable item states
- Remediation tasks and vulnerable item states
- Remediation task state for Vulnerable Items (VIs) in multiple groups
- Additional settings for domain separation
- Discovered Items form fields
- Vulnerability Response vulnerability form fields
- Remediation task form fields
- Vulnerability Response vulnerable item form fields
- Questionnaire Configuration form fields
- Solution form fields
- Approval workflow configurations for unassign request
- Vulnerability Response remediation task rule examples
- Risk score calculation example for Vulnerability Response
- Error handling for detections
- Set up checklist for the Vulnerability Response Mobile app
- Log in to the Vulnerability Response Mobile app
- View, assign, and edit remediation tasks with the Vulnerability Response Mobile app
- View, reassign, and edit remediation tasks assigned to you with the Vulnerability Response Mobile app
- Search for remediation tasks with the Vulnerability Response Mobile app
- Filter records with the Vulnerability Response Mobile app
- Scan vulnerability workflow
- Scan vulnerability item workflow
- Variables for Create Scan Record for Vulnerabilities activity
- Exploring Application Vulnerability Response
- Verify that the scheduled job for updating CWE records is running
- Verify that the scheduled job for updating NVD records is running
- Activate Application Vulnerability Response Integrations
- Configure Exception Management for Application Vulnerability Response
- Configure approval rules for Exception Management
- Deferring remediation in Application Vulnerability Response
- Add an exception approver for Application Vulnerability Response
- Request an exception for an application vulnerable item
- Request an exception for application vulnerabilities using GRC: Policy and Compliance Management
- Request an exception for an application remediation task
- Request an extension for an exception rule in Application Vulnerability Response
- Approve an exception request in Application Vulnerability Response
- Define policy reason mapping
- Request an extension for a deferred remediation task in Application Vulnerability Response
- Request an extension for a deferred application vulnerable item in Application Vulnerability Response
- Create, delete, and cancel an exception rule for Application Vulnerability Response
- Create, edit, and delete Application Vulnerability Response remediation task rules
- Create an application remediation task manually in Application Vulnerability Response
- Configure sprints for penetration testing
- Configure assessment types for penetration testing
- Preparing for the Fortify Vulnerability Integration
- Install the ServiceNow® Vulnerability Response Integration with Fortify
- Configure the Fortify Vulnerability Integration
- View the Fortify Vulnerability Integration import run status
- Perform a manual Fortify application vulnerability import
- Import data using the Fortify Vulnerability Integration
- Include Closed Fortify on Demand application vulnerable items
- Create the required records for OAuth authentication for the GitHub Application Vulnerability Integration
- Install the ServiceNow® GitHub Application Vulnerability Integration
- View the GitHub Application Vulnerability Integration import run status
- View GitHub Application Vulnerability Integration import sets
- Prepare for the Invicti Vulnerability Integration
- Install the ServiceNow® Vulnerability Response Integration with Invicti
- Configure the Invicti Vulnerability Integration
- Viewing the Invicti Vulnerability Integration import run status and records
- Invicti Vulnerability Integration state mapping
- Preparing for the Veracode Vulnerability Integration
- Install the ServiceNow® Vulnerability Response Integration with Veracode
- View the Veracode Application Vulnerability Integration import run status
- View Veracode scan summaries
- Data transformation for the Veracode Vulnerability Integration
- Veracode Vulnerability Integration modifications and activities
- Application Vulnerability fields
- Prevent duplicate or orphaned records after running Application Vulnerability Response CI lookup rules
- Reapplying CI Lookup rules in Application Vulnerability Response
- Create or edit Application Vulnerability Response assignment rules
- Define fields and weights for the risk rule
- Create an application vulnerability calculator
- Filtering within Application Vulnerability Management
- Create or edit application remediation target rules
- View the remediation target status of an application vulnerable item
- Create a penetration test assessment request from existing requests (v19.0)
- Replicate a penetration test request in closed state
- Create penetration test findings based on assessment requests (prior to v19.0)
- Create an application vulnerability entry
- Application Vulnerability Management (PA) dashboard
- My Application Vulnerabilities dashboard
- Application Vulnerability Response user groups and roles
- Several types of components are
- Application Vulnerable Item (AVI) states
- Scanned application fields
- Application Vulnerable Item fields
- Penetration testing states
- Managing state mapping for deferrals and false positives in Application Vulnerability Response
- Application Vulnerability Response references
- Exception rule example for Application Vulnerability Response
- Application Vulnerability Response remediation task rule examples
- Application Vulnerability Response product view
- Exploring Container Vulnerability Response
- Install Vulnerability Response and Configuration Compliance for Containers
- Configure Exception Management for Container Vulnerability Response
- Run the Automated Test Framework (ATF) test suite for Container Vulnerability Response
- Preparing for the Vulnerability Response Integration with Palo Alto Networks Prisma Cloud Compute
- Install the Vulnerability Response Integration with Palo Alto Networks Prisma Cloud Compute
- Configure the Vulnerability Response Integration with Palo Alto Networks Prisma Cloud Compute application
- Container Vulnerability Response calculator rules
- Container Vulnerability Response assignment rules
- Container Vulnerability Response remediation target rules
- Request an exception for a container vulnerable item
- Request an exception for a container remediation task
- Request an exception for container vulnerabilities using GRC: Policy and Compliance Management
- Define a policy reason mapping
- Approve an exception request in Container Vulnerability Response
- Defer a container vulnerable item in Container Vulnerability Response
- Request an extension for a deferred container vulnerable item
- Create an exception rule in Container Vulnerability Response
- Activating an exception rule in Container Vulnerability Response
- Reopen an exception rule in Container Vulnerability Response
- Update an approved exception rule in Container Vulnerability Response
- Delete an exception rule in Container Vulnerability Response
- Request an extension for a deferred remediation task in Container Vulnerability Response
- Request an extension for an exception rule in Container Vulnerability Response
- Mark as a false positive in Container Vulnerability Response
- IT Operations Management and pattern discovery
- Container Vulnerability Response dashboard
- Components installed with Container Vulnerability Response
- Container Vulnerability Response glossary
- Configuration Compliance discovery
- Configuration Compliance correlation
- CI changes for discovered items for Configuration Compliance
- Reconcile unmatched discovered items for Configuration Compliance
- Reapply CI lookup rules on selected discovered items for Configuration Compliance
- The Tenable Vulnerability Integration with Configuration Compliance
- Deduplicating existing configuration items for Configuration Compliance
- Creating CIs for Configuration Compliance using the Identification and Reconciliation Engine
- Removing assignments from Configuration Compliance test result groups
- Configuration Compliance test result groups and group rules overview
- Configuring calculator groups and calculators for Configuration Compliance
- Configuration Compliance Exception Management overview
- Configuration Compliance change management
- Install Configuration Compliance
- Components installed with Configuration Compliance
- Create or edit Configuration Compliance assignment rules
- Configuration Compliance remediation target rules
- Configuration Compliance calculator groups
- Create or edit risk rollup calculators for Configuration Compliance
- Create, edit, and reapply risk calculators for Configuration Compliance
- Examples for Configuration Compliance risk score calculation
- Create or edit Configuration Compliance test result group rules
- Specify the duration of an exception requested for a test result group
- Configure Exception Management for Configuration Compliance
- Add an exception approver for Configuration Compliance
- Create a Configuration Compliance criticality map
- Create email notifications
- Install and configure Microsoft Defender for Cloud Integration for Security Operations
- Configuration Compliance imported data for Microsoft Defender for Cloud Integration
- Preparing for installing the Vulnerability Response Integration with Palo Alto Prisma Cloud
- Install and configure the Vulnerability Response Integration with Palo Alto Prisma Cloud application
- Configure the Vulnerability Response Integration with Palo Alto Prisma Cloud application
- Verify the Vulnerability Response Integration with Palo Alto Prisma Cloud import run status
- Data mapping
- Prisma Cloud REST Messages
- Components installed with the Qualys Integration for Security Operations
- Update configuration items with the network partition identifier for the Qualys Integration
- Attachments not appearing after import
- Modify transform maps
- Check XML attachment property size
- Data retrieval limitations
- Qualys Knowledge Base Integration is failing
- Manually create a Configuration Compliance test result group
- Manually create a Configuration Compliance test result group from the Test Results list
- Create a change request in Configuration Compliance
- Associate a test result group to an existing change request
- Split a test result group
- Remove assignments from test result groups for you or your groups
- Approve an unassign request in Configuration Compliance
- Working with retired configuration items in Configuration Compliance
- Automatically close test results related to retired CIs
- Use Auto-Close Stale Test Results in Configuration Compliance
- Close a test result group
- Request an exception for a test result group in Configuration Compliance
- Request an extension for a test result group
- Request an extension for an exception rule in Configuration Compliance
- Request an exception for test result groups using GRC: Policy and Compliance Management
- Approve an exception request in Configuration Compliance
- Define policy reason mappings
- Configuration Compliance reporting
- Activate Performance Analytics for Configuration Compliance
- Viewing the Performance Analytics for Configuration Compliance dashboard
- View Configuration Compliance policies
- View Configuration Compliance authoritative sources
- View Configuration Compliance technologies
- View Configuration Compliance tests
- View Configuration Compliance test results
- View a test result group
- State synchronization between change requests and test result groups
- Domain separation and Configuration Compliance
- Test Results fields
- Configuration Compliance criticality maps
- Configuration Compliance states
- Modify Qualys PC Results start date
- CI lookup rules for Microsoft Defender for Cloud Integration for Security Operations and Palo Alto Prisma Cloud
- Run multiple aggregations simultaneously
- Configure the number of aggregations that can run simultaneously
- Create a report using an aggregation
- Domain separation and Threat Intelligence
- Set up Threat Intelligence
- Define an attack mode/method
- Add an IoC to an attack mode/method
- Add a related attack mode method
- Add associated task to an attack mode/method
- View an IoC
- Add a related observable to an IoC
- Add a related attack mode/method to an IoC
- Identify associated indicator types
- Identify indicator sources
- Add associated tasks to an IoC
- Define an observable
- Add a related IoC to an observable
- Add associated tasks to an observable
- Add a related observable
- Load more IoC data
- Identify observable sources
- Perform lookups on observables
- Perform threat enrichment on observables
- Define an attack pattern
- Define a campaign
- Define a course of action
- Define identities
- Define infrastructure
- Define an intrusion set
- Define Location
- Define Malware
- Define malware analysis
- Define observed data
- Define threat actors
- Define threat groupings
- Define marking definitions
- Define threat notes
- Define threat opinions
- Define threat reports
- Define indicator sightings
- Define object sightings
- Define tools
- Define vulnerabilities
- Define object-object relationships
- Define object-indicator relationships
- Define object-observable relationships
- STIX Visualizer
- Get started with MITRE-ATT&CK framework
- Understand the MITRE to STIX data model
- Domain separation and MITRE-ATT&CK
- Set up the MITRE-ATT&CK™ framework
- Manage matrices
- Manage techniques
- Manage mitigations
- Manage groups
- Manage malware
- Manage tools
- Manage MITRE relationships
- Manage CVE and technique mapping
- Extend the MITRE-ATT&CK data
- Define the data source and detection tool mapping
- Define the data source and data component mapping
- MITRE-ATT&CK Scoring definition
- Map your technique detection coverage to a technique
- Technique mitigation coverage definitions
- Overall technique mitigation coverage calculator
- Create and map detection rules
- Auto-extract technique rules for importing MITRE-ATT&CK information
- Review threat group and MITRE-ATT&CK techniques mapping
- Threat group to technique heatmap definition
- Review the MITRE-ATT&CK system properties
- Associate MITRE-ATT&CK™ information with security incidents
- Associate MITRE-ATT&CK information with observables
- Associate MITRE-ATT&CK information with security case
- Rollup MITRE-ATT&CK information using Threat Lookup results
- Rollup MITRE-ATT&CK information from detection rules
- Rollup MITRE-ATT&CK information from child security incidents
- Perform link analysis and threat hunting using MITRE-ATT&CK specific filters
- MITRE-ATT&CK heat map and navigator
- Using the MITRE-ATT&CK dashboard
- Using Threat Lookup Finding Calculators
- CrowdStrike Falcon Intelligence integration overview
- Threat Lookup - CrowdStrike Falcon Intelligence workflow
- MISP user roles and permissions
- Install and configure the MISP integration for Security Operations
- Review the MISP integration settings
- Configure MISP sighting searches
- Configure how an automatic event is created
- MISP event data
- Associated MISP events
- MISP user information
- Domain separation and MISP
- Troubleshooting MISP integration
- Sighting searches in MISP
- Observable enrichment in MISP
- Managing events in MISP
- Roll up MITRE-ATT&CK information using MISP enrichment results
- OPSWAT Metadefender integration overview
- Threat Lookup - OPSWAT Metadefender workflow
- Activate and configure the VirusTotal integration
- Threat Lookup - VirusTotal workflow
- Activate and configure the Security Operations Whois integration
- Enrich Observable WhoIs workflow
- Set up Threat Intelligence Orchestration
- Threat Intelligence Orchestration workflows and activities
- Add artifacts to a case
- Create a case from IoCs or observables
- Add IoCs and observables to an existing case
- Create an observable from a case
- Run a sightings search on observables in a case
- Create a case from security incidents
- Add security incidents to an existing case
- Create a case from CIs
- Add CIs to existing cases
- Create a case from affected users
- Add affected users to existing cases
- View related details for a security incident artifact
- View related details for a configuration item artifact
- View related details for an IoC artifact
- View related details for an affected user artifact
- View related details for an observable artifact
- Exclude security artifacts from a case
- Return excluded security artifacts to a case
- Annotate security artifacts
- Search for security artifacts
- Create and define filter groups in Security Operations
- Create duplication rules in Security Operations
- Create Security Operations email properties
- Create email parsers in Security Operations
- Edit email records in Security Operations
- View and reprocess unmatched Security Operations emails
- Map tables to tables with Security Operations field mapping
- Create Security Operations field value transforms
- Create a Security Operations enrichment data map
- Create a Security Operations user-defined escalation group
- Create domain-separated property overrides
- Create an operating system group
- Create security tag rules
- Import security tag rules
- Create security annotations for CIs
- Create security annotations for observables
- Create security annotations for users
- View security annotations reports
- View components installed with Security Support Common
- Search Security Operations
- Types of ServiceNow integrations provided
- Activate and configure third-party integrations
- Create an integration
- Tips for writing integrations
- Replace an untrusted or expired third-party SSL certificate
- Integrations Capabilities framework 2.0
- REST APIs for third-party integration with Security Operations
- Run Block Request
- Filter Allowlisted Observables activity
- Execution Tracking Begin (Mail Search) activity
- Get Supported Security Capabilities activity
- Capability Execution Tracking - No Impls activity
- Execution Tracking - Begin activity
- Capability - Determine CIs activity
- Execution Tracking - Begin (CIs) activity
- Get Network Statistics via netstat activity
- Capability Execution Tracking - Failure activity
- Get IP from CI activity
- Collect Carbon Black Configurations activity
- Check MID Server Status
- Get Sensor ID activity
- Create Session activity
- Check Session Status activity
- Create Command Process activity
- Check Command Status and Get Process activity
- Map Processes Data activity
- Capability Execution Tracking - Complete activity
- Close Session activity
- Tanium: Build Get Processes Request activity
- Tanium: Execute Request activity
- Tanium: Get Question ID from Response activity
- Tanium: Build Check if Done Request activity
- Tanium: Determine if done from Response activity
- Tanium: Build Get Result Data Request activity
- Tanium: Get Result Data from Response activity
- Get Running Processes via PowerShell activity
- Execute Shell Script activity
- Combine results activity
- Run Isolate Host
- Set Network Isolation Enabled activity
- Update Sensor activity
- Determine Observables activity
- Run a Sightings Search
- Sightings Search - Determine Observables activity
- Get Observable Sightings Queries activity
- Collect ArcSight Configurations activity
- ArcSight Event Query activity
- Persistent Observable Sightings activity
- Elasticsearch Event QueryActivity activity
- Collect McAfee Configurations activity
- McAfee ESM Event Query activity
- Collect QRadar Configurations activity
- QRadar Event QueryActivity activity
- Collect Splunk Configurations activity
- Splunk Event Query activity
- Share Sightings Search results
- Share observables from a security incident
- View Sightings Search Details
- Change the order of workflow execution
- Create Security Operations workflow triggers
- Update security incident with lookup results workflow
- Create Compliance Search Activity
- Get running processes via WMI activity
- Check Compliance Search Status Activity
- Update Task Worknotes activity
- Roll up lookup info to security incident activity
- Write content to record as attachment activity
- DLP Incident Response overview
- Get started with DLP Incident Response
- Install and configure the DLP Incident Response application
- Domain separation and DLP Incident Response
- DLP default configuration settings
- Configure end user lookup rules
- Create an assignment rule for your Data Loss Prevention Incident Response incidents
- Configure incident consolidation rules to consolidate your DLP incidents
- Add multiple users to access DLP incidents
- Configure Approval Rules
- Configure DLP UI user instructions
- Create and manage email templates for your DLP incidents
- Create and manage assessments for DLP incidents
- Configure response option for your DLP incidents
- Configure the age chart for your DLP incidents
- Configure how end-user actions are delegated
- Configure repeat offender identification rules
- Create custom states for your DLP incidents
- Create custom fields for your DLP incidents
- Configure advanced settings for Data Loss Prevention Incident Response
- Monitor Microsoft DLP Integration Run process
- Set up field level restrictions for your DLP incidents
- Set up record level restrictions for your DLP incidents
- Archive DLP related records
- Report or respond to DLP incidents
- Working with my approvals module
- Data Loss Prevention Incident Response Analyst Workspace
- Data Loss Prevention Incident Response Dashboard
- Inbound Integration for Data Loss Prevention Incident Response
- Getting started with Symantec DLP integration for Data Loss Prevention
- Install and configure the Symantec DLP integration for Data Loss Prevention
- Define filters to apply for the Incident creation
- Schedule the Symantec DLP Incident Retrieval
- Mapping Symantec DLP incident statuses with ServiceNow incident Status
- Severity mapping between Symantec DLP incidents with ServiceNow incidents
- Configure the Symantec DLP integration settings
- Domain Separation in the Symantec DLP integration
- Getting started with Proofpoint integration for Data Loss Prevention
- Configure the Webhook on the Proofpoint DLP tenant for alert notifications to ServiceNow
- Map Proofpoint DLP incidents status with ServiceNow incident status
- Configure Proofpoint DLP integration settings
- Domain Separation in Proofpoint DLP integration
- Getting started with Netskope DLP integration for Data Loss Prevention
- Install and configure the Netskope DLP integration for Data Loss Prevention
- Define Filters to apply for the Incident creation
- Schedule the Netskope Data Loss Prevention Alerts Retrieval
- Configure Netskope DLP integration settings
- Notifications for users on credential expiration
- Domain Separation in Netskope DLP integration
- Getting started with Microsoft DLP IR integration for data loss prevention
- Install and configure the Microsoft DLP integration
- Configure the match content for the incident
- Schedule the DLP IR Microsoft incident retrieval
- Configure Microsoft DLP IR integration settings
- Request release email from quarantine
- Download files for DLP incidents of type Exchange Online, OneDrive, and SharePoint
- Domain separation in Microsoft DLP integration
- Exploring Software Bill of Materials
- Install the supported applications for Software Bill of Materials
- Uploading Software Bill of Materials files using a REST API
- Upload Software Bill of Materials files manually
- Reviewing the Home page in the Software Bill of Materials Workspace
- Reviewing the Components module in the Software Bill of Materials Workspace
- Creating rules for application vulnerable items in the Software Bill of Materials Workspace
- Viewing upload status for Software Bill of Materials files
- Checking a Software Bill of Materials entity for vulnerabilities
- Create an application vulnerable item rule in the Software Bill of Materials Workspace
- Updated Aug 3, 2023
- 3 minutes to read
- Vulnerability Response
After you complete your initial assessment of assignment rules using Setup Assistant, you can create rules to automatically assign vulnerable items based on filter conditions. These rules assign vulnerable items as they are imported or manually created.
Before you begin
Persona and granular roles are available to help you manage what users and groups can see and do in the Vulnerability Response application. For an initial assignment of the persona roles in Setup Assistant, see Assign the Vulnerability Response persona roles using Setup Assistant . For more information about managing granular roles, see Manage persona and granular roles for Vulnerability Response .
About this task
The base system ships with one vulnerability assignment rule, Assign to CI support group , which assigns vulnerable items to the same assignment group as the CI support group. This rule can be modified using filter conditions or you can create a new rule. With assignment rules, you define the condition(s) of assignment and the order of execution. Once a VI matches a rule condition, the assignment lookup stops.
- Navigate to All > Vulnerability Response > Administration > Assignment Rules .
- Open the Assign to CI support group rule or click New .
The reapply feature requires a baseline application of the rules. Once your rules are created, if you haven't already done so, activate the Reapply all vulnerability assignment rules scheduled job to execute, at your convenience. It applies all the rules to all Open VIs except those manually assigned. Depending on how many active VIs you have in your environment, remember to set the Run field appropriately following the initial run to prevent performance impacts.
If you haven't run this scheduled job, when you try to use the Apply Changes button on the Assignment Rules form, you will have to do it then. Reapplying assignment rules does not regroup the vulnerable items.
Announcing the Global SNUG Board of Directors. Learn more here

ServiceNow Community servicenow community
- English (US)
- English (UK)
- Portuguese (Brazilian)
- ServiceNow Community
- Security Operations
- SecOps forum
- Success with Vulnerability Response: Deep-dive int...
- Subscribe to RSS Feed
- Mark Question as New
- Mark Question as Read
- Float this Question for Current User
- Printer Friendly Page
Success with Vulnerability Response: Deep-dive into Classification Rules and Assignment Rules
- Mark as New
- Report Inappropriate Content
02-23-2023 09:46 AM - edited 01-19-2024 12:17 PM
- Best Practices
- Vulnerability Response
- 3,034 Views
- All forum topics
- Previous Question
- Next Question
03-20-2023 04:54 PM - edited 03-20-2023 04:57 PM
04-11-2023 11:41 AM
- Tenable Integration Plugin with ServiceNow - Additional Fields (Specifically 'Patch Published Date') in SecOps forum 3 weeks ago
- "Success with VR" webinar series in SecOps articles 02-07-2024
- Vulnerability Response roles support - allowing group managers to see VULs assigned to their groups in SecOps VR forum (Read Only) 01-30-2024
- My Experiences and approach Implementing Vulnerability Response in SecOps VR forum (Read Only) 01-25-2024
- Assignment Recommendations in SecOps VR forum (Read Only) 12-18-2023

- ServiceNow Consulting Services
- ServiceNow IT Workflows
- ServiceNow Customer Workflows
- ServiceNow Employee Workflows
- Hyperautomation
- ServiceNow Implementation Services
- ServiceNow Integration Services
- ServiceNow Managed Services
- ServiceNow for Manufacturing Industry
- Digital Transformation In Banking
- Digital Transformation In Insurance
- Digital Transformation in Wealth & Asset Management
- Digital Transformation in Life Sciences
- Digital Transformation in Hospitals
- Digital Transformation for Payers
- Data Migration Utility
- 360 Degree Business Assessment
- ServiceNow Dx Support
- Service Automate
- Rome Release
- Case Studies
- News Events
- Infographic
- Thought Leadership
Handling Assignment Rules in ServiceNow
In ServiceNow, if one is looking for automatic assignments then he can rely on the instance’s ability to assign the tasks automatically to different users and groups depending on the specified conditions. In order to achieve this, ServiceNow has the following modules:
- Assignment Lookup Rules
- Assignment Rules
Assignment Lookup Rules:
This module appears under the ‘System Policy application’ menu. This table is basically generated out of the box as its definition is provided in the ‘Data Lookup Definition’ table in the instance, specifically for field assignments in the incident table. Assignment lookup rules mainly provide the functionality of changing any field value and not just the assignment fields.

Assignment Rules:
This module appears under the ‘System Policy application’ menu. It helps to automatically assign the tasks to a particular user or a particular group using the assigned_to and assignment_group fields respectively, depending on the specified set of conditions. One can define these assignment rules readily for their desired table.
Following are the steps for defining the assignment rule:
- Navigate to System Policy -> Assignment -> New
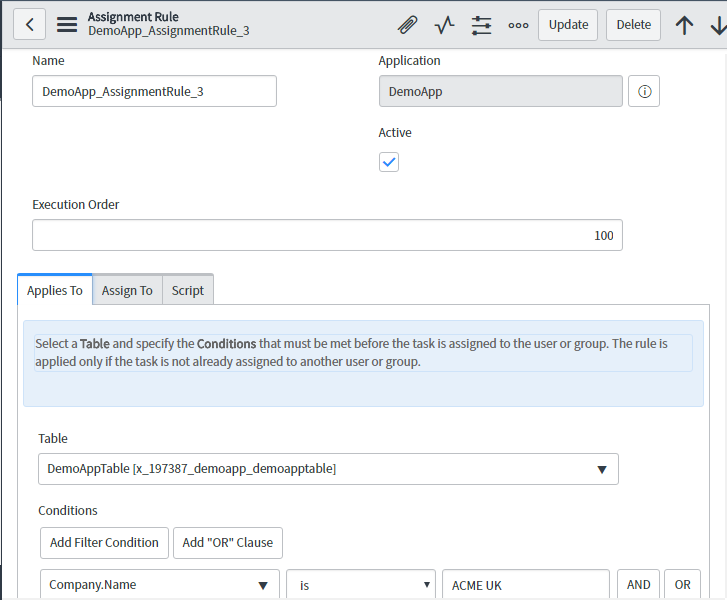
- From the above figure, one can see that the dot-walking can also be done in the condition builder field. Just select the ‘Show Related Fields’ option in the condition and then select the appropriate attribute.
- Further, in the ‘Assign To’ tab, select the appropriate user and group to whom the task is to be assigned.
If two assignment rules conflict, then the assignment rule with the lowest execution order runs first. The lower the execution order, the higher is the precedence.
Distinguishing Factors between the Data Lookup Rules and Assignment Rules:
Precedence among the assignment rule and business rule:.
In certain circumstances, the business rules gain precedence over the assignment rules.
The business rules and assignments rules run in the following order:
- All the ‘before record insert’ business rules having order less than 1000.
- First and foremost, assignment rule with lowest execution order and matching condition.
- All the ‘before record insert’ business rules having order more than 1000.
- All the ‘after record insert’ business rules.
We are pretty sure that this blog must have given an overview of dealing with Assignment Rules in ServiceNow.
Any comments\suggestions are most welcome. We have posted further blogs as well on other topics and will frequently come back with something innovative.
Share This Story, Choose Your Platform!

IMAGES
VIDEO
COMMENTS
The scheduled job [Reapply all vulnerability assignment rules] is inactive by default. When activated, it applies all the rules to all open VIs except those manually assigned. ... Vulnerability Assignment Recommendations uses ServiceNow Predictive Intelligence and machine learning to recommend assignment groups for vulnerable items (VIs) and ...
Vulnerability Response assignment rules overview - Product Documentation: Utah - Now Support Portal.
It works with application vulnerability scanners and the Common Weakness Enumeration (CWE) to assesses DAST and SAST results to identify vulnerable applications and coordinate fixes with developer teams. It offers Focus resources on the most critical risks Automate prioritization and assignment with configurable risk score calculators and rules.
Community Ask questions, give advice, and connect with fellow ServiceNow professionals. Developer Build, test, and deploy applications. Documentation Find detailed information about ServiceNow products, apps, features, and releases. Impact Accelerate ROI and amplify your expertise.
Loading... Loading...
The ServiceNow solution. ServiceNow® Security Operations is a security orchestration, automation, and response (SOAR) engine built on the Now Platform. Designed to help security and IT teams respond faster and more efficiently to incidents and vulnerabilities, Security Operations uses intelligent workflows, automation, and a deep connection ...
Tips and trick for Vulnerability Assignment Rules
Loading... Loading...
Grow your skills and RiseUp with ServiceNow. Enhance security response, prioritize vulnerabilities, and gain real-time visibility with ServiceNow Vulnerability Response. Streamline coordination and remediation across security and IT teams.
Grow your skills and RiseUp with ServiceNow. Rise up and join the digital revolution. Help fill the need for people with ServiceNow expertise. Mitigate application security risks with ServiceNow Application Vulnerability Response. Centralize vulnerability management and coordinate fixes with ease.
ServiceNow This two-day course covers Vulnerability Response essentials such as why customers need Vulnerability Response, what Vulnerability Response is, and how to properly implement Vulnerability Response. Participants will learn the common technical aspects of a Vulnerability Response implementation as well as experience various processes to effectively manage a Vulnerability Response ...
Success with Vulnerability Response: Deep-dive into Classification Rules and Assignment Rules. Elizabeth Skogq. ServiceNow Employee. Options. 02-23-202309:46 AM - last edited on 04-13-202309:34 AM by Eric Feron. Our "Success with Vulnerability Response" series of recommended practices deep-dive webinars continues. After the great feedback ...
To showcase how Dengene introduced an Intelligent and efficient Vulnerability Assignment and Grouping for ServiceNow Vulnerability Response application.
This includes defining classification rules, assignment rules, and integrating with third-party tools. User Training: Training users on how to utilize the module effectively is essential. ServiceNow provides comprehensive documentation and training resources to support users in maximizing the benefits of ServiceNow VR.
The vulnerability response assignment rules table (sn_vul_assignment_rule) does not load due to transaction timeout.
One can define these assignment rules readily for their desired table. Following are the steps for defining the assignment rule: Navigate to System Policy -> Assignment -> New. Fill in the appropriate details. The below figure is for reference: From the above figure, one can see that the dot-walking can also be done in the condition builder field.
ServiceNow Vulnerability Response application. Select this check-box to map the vulnerability (detection) state in the Vulnerable Items table, that is, AVIT table (sn_vul_app_vulnerable_item) as per the Triage map maintained ... to let the customer add remediation rules, assignment rules etc for AVR. Customers can enable the inactive ...
The Snyk Code integration means ServiceNow customers can harness the many benefits of AI-assisted coding with full confidence that their code is secure. Solving application security challenges at Knowledge '24. Snyk and ServiceNow ties extend beyond the partnership with ServiceNow Ventures, which invested $25 million in Snyk in 2023.