

Terror attacks and kidnappings spread in Nigeria: why Lagos could be a target
Senior Lecturer, Department of Urban and Regional Planning, Olabisi Onabanjo University
Disclosure statement
Adewumi I. Badiora does not work for, consult, own shares in or receive funding from any company or organization that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.
View all partners
Crimes that were previously associated with Nigeria’s northern region – like kidnapping for ransom and terrorism – appear to be spreading to the south-west region, including Lagos. Adewumi Badiora, an urban and community safety researcher , outlines urgent steps that must be taken to keep banditry and insecurity out of Lagos.
What is the current state of banditry and terror attacks in Nigeria?
Banditry has existed for years in Nigeria. State security officers call it a complex, violent crime involving terrorism, jihad insurgencies, armed robbery, murder, kidnapping, rape and the illegal possession of firearms. It has gained a base in the country’s north-eastern, north-western and some north-central states.
According to the Armed Conflict Location and Event Data Project , activities by bandit gangs increased by 731% between 2018 and 2022, and there were around 13,485 banditry-related deaths between January 2010 and May 2023.
How do we know Lagos could be a target and why?
In July 2022, the Nigeria Security and Civil Defence Corps placed all its state commands on alert following intelligence reports that elements of the Boko Haram terrorists as well as those of Islamic State West Africa Province had heightened plots to attack Nigeria’s commercial capital, Lagos.
Several other threats have been issued since then but none seems to have been fully carried out.
Crimes like kidnappings have become increasingly common in the Nigerian south-west, however, including Lagos. Recent research by the polling service NOIPolls put south-west as the epicentre of kidnapping after north-central.
Large attacks in the country’s south-west were relatively rare until double massacres in Owo, Ondo state, in 2022. These attacks have been traced to bandits .
In January 2024, gunmen on the Lagos-Ibadan corridor abducted political figures. The same month, gunmen killed two traditional rulers in Ekiti state. In May, seven travellers were abducted and another one killed by bandits on the Sagamu-Ijebu-Ode expressway.
These are some of the signs that insecurity is being experienced within the Lagos region.
In my recent research , I identified that Lagos could become a target for banditry and terrorism for several reasons. I surveyed a total of 288 residents of Lagos to find out their concerns for safety and implications for individual and city-level security planning.
First, Lagos has a vulnerable population. Terrorist groups aim to harm innocent people to gain political attention or military objectives. Any attack on a part of Lagos (like a church, mosque, market or bus stop) is likely to cause mass deaths of innocent people.
Second, Lagos has strategic political and economic importance in Nigeria and Africa. A bandit attack would undermine this and make an impact on the nation’s economy, politics and governance.
Like Abuja, Lagos is heavily protected. A bandit attack that penetrated the city’s security would have propaganda value.
There is widespread youth unemployment and inequality in Lagos, and different ethnic groups coexist. This creates tension which could enable bandit groups to mix with residents, particularly disadvantaged youth in the slum settlements.
In my research , 37% of my respondents said their families or community members had experienced shooting or kidnapping in Lagos. For most of my respondents, this happened during clashes among different violent groups. Respondents also mentioned cases of kidnapping and other violent crime.
These residents of Lagos appeared afraid. My research respondents (78%) were very concerned about their safety. Almost all (90%) had been forced to make changes in their daily lives. Some were considering moving away. Women and girls were the worst affected. Some communities had taken greater safety precautions.
What are the implications of this threat?
My research findings show that if this trend of spreading insecurity continues, farmers may become more frightened to go to farm, causing food insecurity.
The livelihoods of people who work and trade in the informal sector and formal businesses could be undermined by banditry.
Enterprises may begin to close or relocate, and this would add to the youth unemployment crisis.
Lagos is the foremost commercial hub of Nigeria, offering manufacturing and a huge, accessible market within the African economic zone. The embryonic banditry around the city borders poses a severe risk to this regional economic growth.
What urban design security planning must be done to make Lagos secure?
Based on the results of my study, I outline some of the things that could turn the tide of banditry and insecurity in Lagos:
ensure perpetrators and their sponsors are caught and face the law
beef up security and check-points on all roads and in public places and forests in the south-west
address underlying socio-economic drivers and enablers of insecurity
push for state policing or reinvigorate the Amotekun security approaches with training and equipment (Amotekun is a paramilitary security network)
enable local communities to fight banditry, as opposed to top-down strategies.
Further planning of Lagos should prevent excessive sprawl and vulnerable development at border communities. At present, Lagos has over 157 vulnerable communities deserving of urgent planning attention. These areas have been identified as tactical shelters for criminals.
Bandits sometimes use motorcycles to attack soft targets. Urban design that uses physical barriers should be considered. Small bends, bumps or turns in roads could limit the speed at which motorcycle attacks can be launched.
Improved policing and smart monitoring systems, such as smart CCTV and advanced street lighting, would help.
Cooperation from Lagos residents concerning intelligence gathering is vital. Residents should be more vigilant and report security issues to the police as soon as possible.
The approach should allow community members to take ownership of and actively participate in addressing banditry issues and challenges facing them.
- Urban planning
- Nigeria kidnapping
- rural banditry
- Islamic State West Africa Province (ISWAP)
Want to write?
Write an article and join a growing community of more than 192,200 academics and researchers from 5,074 institutions.
Register now
- Tools and Resources
- Customer Services
- Food and the Humanities
- Food History and Anthropology
- Food Politics and Policy
- Food Science
- Food Globalization and Industrialization
- Conflict Studies
- Development
- Environment
- Foreign Policy
- Human Rights
- International Law
- Organization
- International Relations Theory
- Political Communication
- Political Economy
- Political Geography
- Political Sociology
- Politics and Sexuality and Gender
- Qualitative Political Methodology
- Quantitative Political Methodology
- Security Studies
- Share Facebook LinkedIn Twitter
Article contents
Transnational organized crime and terrorism.
- Katharine Petrich Katharine Petrich Rockefeller College of Public Affairs and Policy, University at Albany, SUNY
- https://doi.org/10.1093/acrefore/9780190846626.013.705
- Published online: 19 October 2022
A significant, policy-relevant relationship exists between terrorist groups and transnational organized crime. However, definitional challenges, disciplinary boundaries, and legal logistics all contribute to the mischaracterization of the relationship, leading to piecemeal responses and uneven academic attention. International studies research tends to focus on one or the other, with an emphasis on terrorist group dynamics and choices. Two enduring rationales for separating the study of terrorism from that of transnational organized crime exist: the “greed versus grievance” debate, which argues that organizations pursue either private (financial) goals or public (social or organizational change) goals and the “methods not motives” argument, which suggests groups may overlap in their tactics but diverge in their strategic goals. Terrorist violence by criminal groups is largely held separate from the “transnational crime and terrorism” literature, often categorized instead as “criminal governance” rather than terrorism studies. The reality is much more nuanced: both group types pursue a variety of objectives and engage with a spectrum of actors which may or may not share their aspirations. Members are diverse in their priorities, a fact that is often lost when analysis collapses the rank and file with leadership into a monolithic bloc. Additionally, globalization has increased opportunities for groups to pursue different activities in different theaters. In areas where terrorist groups are contesting for political control and seeking to present themselves as viable alternative governance actors, they may be less likely to work openly with illicit actors, but in areas (or countries) where they have little governance ambition, criminal networks may be important public partners.
These groups intersect in a spectrum of ways, from engaging in temporary ad hoc relationships designed to achieve a specific goal, to fully incorporating the opposite type’s motive into organizational priorities. Political ambitions largely center on power and control, but illicit activities are wide ranging, with the most prominent involving firearms, drugs, and people. Further, there are several important enabling factors that foster these relationships, including corruption, illicit financial flows, fragile states, and lootable resources. When these enabling factors are present, diversification and relationship building are more likely, increasing organizational resilience and making demobilization less likely. These factors, particularly corruption, also increase the chances of organized crime entering the political system.
Looking ahead, both policymakers and academics should consider transnational organized crime and terrorism more holistically. Work that engages with only one element will fall short in assessing the dynamics of irregular conflict, leading to incomplete analysis and weak policy recommendations. Observers should cultivate the flexibility to think in terms of networks and variety across geographic contexts—the way that a terrorist group behaves in one area or with one type of criminal group does not necessarily predict its behavior globally.
- transnational organized crime
- irregular conflict
- illicit economies
- trafficking
- black market
- law enforcement
You do not currently have access to this article
Please login to access the full content.
Access to the full content requires a subscription
Printed from Oxford Research Encyclopedias, International Studies. Under the terms of the licence agreement, an individual user may print out a single article for personal use (for details see Privacy Policy and Legal Notice).
date: 25 October 2024
- Cookie Policy
- Privacy Policy
- Legal Notice
- Accessibility
- [66.249.64.20|162.248.224.4]
- 162.248.224.4
Character limit 500 /500
Woman accused of kidnapping her son from DSS
WATERTOWN, New York (WWNY) - A Watertown woman is accused of kidnapping her son from Jefferson County’s Department of Social Services Wednesday morning and fleeing the scene in a stolen vehicle.
Watertown city court papers show that 28-year-old Renee Rink allegedly grabbed the juvenile from DSS around 9 a.m. and ran outside into the parking lot, where she twisted away from DSS personnel who were trying to stop her from taking her son.
That move, court papers say, injured the child, who had to be hospitalized.
Rink’s actions violated a stay-away order of protection.
Rink is also accused of attempting to flee by stealing a vehicle. She allegedly jumped on the hood of a 2023 Ford Bronco, then onto the roof, then back onto the hood, where she kicked out the windshield. She jumped into the driver’s seat when the driver left the vehicle to call 911.
Bystanders pulled her from the vehicle and restrained her until police arrived.
She was charged with second-degree kidnapping, first-degree criminal contempt, endangering the welfare of a child, second-degree robbery, and third-degree criminal mischief.
Rink was arraigned in Watertown city court, where she was committed to jail on $50,000 bail.
Copyright 2024 WWNY. All rights reserved.

‘Unimaginable tragedy:’ 44 shelter dogs killed in fire

Potsdam man accused of possessing child porn

Settlement reached in transgender Watertown woman’s case against police, jail

3 accused of possessing $34K worth of cocaine, fentanyl in St. Lawrence County

Firefighters make quick work of early morning fire

Firefighters battle wildfire near Potsdam

A dam bad deal: Drastic tax increase in the town of Lewis
Latest news.
Gunshots in Watertown? Don’t be alarmed, police say

Crash closes part of State Route 342

Jefferson Co. Public Health offers lead testing to residents

'Unimaginable tragedy:' 44 shelter dogs killed in fire

Carthage school district concerned about drivers passing stopped buses

Testimony continues in Adam Smith double murder trial

Doha Declaration
Education for justice.
- Agenda Day 1
- Agenda Day 2
- Agenda Day 3
- Agenda Day 4
- Registration
- Breakout Sessions for Primary and Secondary Level
- Breakout Sessions for Tertiary Level
- E4J Youth Competition
- India - Lockdown Learners
- Chuka, Break the Silence
- The Online Zoo
- I would like a community where ...
- Staying safe online
- Let's be respectful online
- We can all be heroes
- Respect for all
- We all have rights
- A mosaic of differences
- The right thing to do
- Solving ethical dilemmas
- UNODC-UNESCO Guide for Policymakers
- UNODC-UNESCO Handbooks for Teachers
- Justice Accelerators
- Introduction
- Organized Crime
- Trafficking in Persons & Smuggling of Migrants
- Crime Prevention & Criminal Justice Reform
- Crime Prevention, Criminal Justice & SDGs
- UN Congress on Crime Prevention & Criminal Justice
- Commission on Crime Prevention & Criminal Justice
- Conference of the Parties to UNTOC
- Conference of the States Parties to UNCAC
- Rules for Simulating Crime Prevention & Criminal Justice Bodies
- Crime Prevention & Criminal Justice
- Engage with Us
- Contact Us about MUN
- Conferences Supporting E4J
- Cyberstrike
- Play for Integrity
- Running out of Time
- Zorbs Reloaded
- Developing a Rationale for Using the Video
- Previewing the Anti-Corruption Video
- Viewing the Video with a Purpose
- Post-viewing Activities
- Previewing the Firearms Video
- Rationale for Using the Video
- Previewing the Human Trafficking Video
- Previewing the Organized Crime Video
- Previewing the Video
- Criminal Justice & Crime Prevention
- Corruption & Integrity
- Human Trafficking & Migrant Smuggling
- Firearms Trafficking
- Terrorism & Violent Extremism
- Introduction & Learning Outcomes
- Corruption - Baseline Definition
- Effects of Corruption
- Deeper Meanings of Corruption
- Measuring Corruption
- Possible Class Structure
- Core Reading
- Advanced Reading
- Student Assessment
- Additional Teaching Tools
- Guidelines for Stand-Alone Course
- Appendix: How Corruption Affects the SDGs
- What is Governance?
- What is Good Governance?
- Corruption and Bad Governance
- Governance Reforms and Anti-Corruption
- Guidelines for Stand-alone Course
- Corruption and Democracy
- Corruption and Authoritarian Systems
- Hybrid Systems and Syndromes of Corruption
- The Deep Democratization Approach
- Political Parties and Political Finance
- Political Institution-building as a Means to Counter Corruption
- Manifestations and Consequences of Public Sector Corruption
- Causes of Public Sector Corruption
- Theories that Explain Corruption
- Corruption in Public Procurement
- Corruption in State-Owned Enterprises
- Responses to Public Sector Corruption
- Preventing Public Sector Corruption
- Forms & Manifestations of Private Sector Corruption
- Consequences of Private Sector Corruption
- Causes of Private Sector Corruption
- Responses to Private Sector Corruption
- Preventing Private Sector Corruption
- Collective Action & Public-Private Partnerships against Corruption
- Transparency as a Precondition
- Detection Mechanisms - Auditing and Reporting
- Whistle-blowing Systems and Protections
- Investigation of Corruption
- Introduction and Learning Outcomes
- Brief background on the human rights system
- Overview of the corruption-human rights nexus
- Impact of corruption on specific human rights
- Approaches to assessing the corruption-human rights nexus
- Human-rights based approach
- Defining sex, gender and gender mainstreaming
- Gender differences in corruption
- Theories explaining the gender–corruption nexus
- Gendered impacts of corruption
- Anti-corruption and gender mainstreaming
- Manifestations of corruption in education
- Costs of corruption in education
- Causes of corruption in education
- Fighting corruption in education
- Core terms and concepts
- The role of citizens in fighting corruption
- The role, risks and challenges of CSOs fighting corruption
- The role of the media in fighting corruption
- Access to information: a condition for citizen participation
- ICT as a tool for citizen participation in anti-corruption efforts
- Government obligations to ensure citizen participation in anti-corruption efforts
- Teaching Guide
- Brief History of Terrorism
- 19th Century Terrorism
- League of Nations & Terrorism
- United Nations & Terrorism
- Terrorist Victimization
- Exercises & Case Studies
- Radicalization & Violent Extremism
- Preventing & Countering Violent Extremism
- Drivers of Violent Extremism
- International Approaches to PVE &CVE
- Regional & Multilateral Approaches
- Defining Rule of Law
- UN Global Counter-Terrorism Strategy
- International Cooperation & UN CT Strategy
- Legal Sources & UN CT Strategy
- Regional & National Approaches
- International Legal Frameworks
- International Human Rights Law
- International Humanitarian Law
- International Refugee Law
- Current Challenges to International Legal Framework
- Defining Terrorism
- Criminal Justice Responses
- Treaty-based Crimes of Terrorism
- Core International Crimes
- International Courts and Tribunals
- African Region
- Inter-American Region
- Asian Region
- European Region
- Middle East & Gulf Regions
- Core Principles of IHL
- Categorization of Armed Conflict
- Classification of Persons
- IHL, Terrorism & Counter-Terrorism
- Relationship between IHL & intern. human rights law
- Limitations Permitted by Human Rights Law
- Derogation during Public Emergency
- Examples of States of Emergency & Derogations
- International Human Rights Instruments
- Regional Human Rights Instruments
- Extra-territorial Application of Right to Life
- Arbitrary Deprivation of Life
- Death Penalty
- Enforced Disappearances
- Armed Conflict Context
- International Covenant on Civil and Political Rights
- Convention against Torture et al.
- International Legal Framework
- Key Contemporary Issues
- Investigative Phase
- Trial & Sentencing Phase
- Armed Conflict
- Case Studies
- Special Investigative Techniques
- Surveillance & Interception of Communications
- Privacy & Intelligence Gathering in Armed Conflict
- Accountability & Oversight of Intelligence Gathering
- Principle of Non-Discrimination
- Freedom of Religion
- Freedom of Expression
- Freedom of Assembly
- Freedom of Association
- Fundamental Freedoms
- Definition of 'Victim'
- Effects of Terrorism
- Access to Justice
- Recognition of the Victim
- Human Rights Instruments
- Criminal Justice Mechanisms
- Instruments for Victims of Terrorism
- National Approaches
- Key Challenges in Securing Reparation
- Topic 1. Contemporary issues relating to conditions conducive both to the spread of terrorism and the rule of law
- Topic 2. Contemporary issues relating to the right to life
- Topic 3. Contemporary issues relating to foreign terrorist fighters
- Topic 4. Contemporary issues relating to non-discrimination and fundamental freedoms
Module 16: Linkages between Organized Crime and Terrorism
- Thematic Areas
- Content Breakdown
- Module Adaptation & Design Guidelines
- Teaching Methods
- Acknowledgements
- 1. Introducing United Nations Standards & Norms on CPCJ vis-à-vis International Law
- 2. Scope of United Nations Standards & Norms on CPCJ
- 3. United Nations Standards & Norms on CPCJ in Operation
- 1. Definition of Crime Prevention
- 2. Key Crime Prevention Typologies
- 2. (cont.) Tonry & Farrington’s Typology
- 3. Crime Problem-Solving Approaches
- 4. What Works
- United Nations Entities
- Regional Crime Prevention Councils/Institutions
- Key Clearinghouses
- Systematic Reviews
- 1. Introduction to International Standards & Norms
- 2. Identifying the Need for Legal Aid
- 3. Key Components of the Right of Access to Legal Aid
- 4. Access to Legal Aid for Those with Specific Needs
- 5. Models for Governing, Administering and Funding Legal Aid
- 6. Models for Delivering Legal Aid Services
- 7. Roles and Responsibilities of Legal Aid Providers
- 8. Quality Assurance and Legal Aid Services
- 1. Context for Use of Force by Law Enforcement Officials
- 2. Legal Framework
- 3. General Principles of Use of Force in Law Enforcement
- 4. Use of Firearms
- 5. Use of “Less-Lethal” Weapons
- 6. Protection of Especially Vulnerable Groups
- 7. Use of Force during Assemblies
- 1. Policing in democracies & need for accountability, integrity, oversight
- 2. Key mechanisms & actors in police accountability, oversight
- 3. Crosscutting & contemporary issues in police accountability
- 1. Introducing Aims of Punishment, Imprisonment & Prison Reform
- 2. Current Trends, Challenges & Human Rights
- 3. Towards Humane Prisons & Alternative Sanctions
- 1. Aims and Significance of Alternatives to Imprisonment
- 2. Justifying Punishment in the Community
- 3. Pretrial Alternatives
- 4. Post Trial Alternatives
- 5. Evaluating Alternatives
- 1. Concept, Values and Origin of Restorative Justice
- 2. Overview of Restorative Justice Processes
- 3. How Cost Effective is Restorative Justice?
- 4. Issues in Implementing Restorative Justice
- 1. Gender-Based Discrimination & Women in Conflict with the Law
- 2. Vulnerabilities of Girls in Conflict with the Law
- 3. Discrimination and Violence against LGBTI Individuals
- 4. Gender Diversity in Criminal Justice Workforce
- 1. Ending Violence against Women
- 2. Human Rights Approaches to Violence against Women
- 3. Who Has Rights in this Situation?
- 4. What about the Men?
- 5. Local, Regional & Global Solutions to Violence against Women & Girls
- 1. Understanding the Concept of Victims of Crime
- 2. Impact of Crime, including Trauma
- 3. Right of Victims to Adequate Response to their Needs
- 4. Collecting Victim Data
- 5. Victims and their Participation in Criminal Justice Process
- 6. Victim Services: Institutional and Non-Governmental Organizations
- 7. Outlook on Current Developments Regarding Victims
- 8. Victims of Crime and International Law
- 1. The Many Forms of Violence against Children
- 2. The Impact of Violence on Children
- 3. States' Obligations to Prevent VAC and Protect Child Victims
- 4. Improving the Prevention of Violence against Children
- 5. Improving the Criminal Justice Response to VAC
- 6. Addressing Violence against Children within the Justice System
- 1. The Role of the Justice System
- 2. Convention on the Rights of the Child & International Legal Framework on Children's Rights
- 3. Justice for Children
- 4. Justice for Children in Conflict with the Law
- 5. Realizing Justice for Children
- 1a. Judicial Independence as Fundamental Value of Rule of Law & of Constitutionalism
- 1b. Main Factors Aimed at Securing Judicial Independence
- 2a. Public Prosecutors as ‘Gate Keepers’ of Criminal Justice
- 2b. Institutional and Functional Role of Prosecutors
- 2c. Other Factors Affecting the Role of Prosecutors
- Basics of Computing
- Global Connectivity and Technology Usage Trends
- Cybercrime in Brief
- Cybercrime Trends
- Cybercrime Prevention
- Offences against computer data and systems
- Computer-related offences
- Content-related offences
- The Role of Cybercrime Law
- Harmonization of Laws
- International and Regional Instruments
- International Human Rights and Cybercrime Law
- Digital Evidence
- Digital Forensics
- Standards and Best Practices for Digital Forensics
- Reporting Cybercrime
- Who Conducts Cybercrime Investigations?
- Obstacles to Cybercrime Investigations
- Knowledge Management
- Legal and Ethical Obligations
- Handling of Digital Evidence
- Digital Evidence Admissibility
- Sovereignty and Jurisdiction
- Formal International Cooperation Mechanisms
- Informal International Cooperation Mechanisms
- Data Retention, Preservation and Access
- Challenges Relating to Extraterritorial Evidence
- National Capacity and International Cooperation
- Internet Governance
- Cybersecurity Strategies: Basic Features
- National Cybersecurity Strategies
- International Cooperation on Cybersecurity Matters
- Cybersecurity Posture
- Assets, Vulnerabilities and Threats
- Vulnerability Disclosure
- Cybersecurity Measures and Usability
- Situational Crime Prevention
- Incident Detection, Response, Recovery & Preparedness
- Privacy: What it is and Why it is Important
- Privacy and Security
- Cybercrime that Compromises Privacy
- Data Protection Legislation
- Data Breach Notification Laws
- Enforcement of Privacy and Data Protection Laws
- Intellectual Property: What it is
- Types of Intellectual Property
- Causes for Cyber-Enabled Copyright & Trademark Offences
- Protection & Prevention Efforts
- Online Child Sexual Exploitation and Abuse
- Cyberstalking and Cyberharassment
- Cyberbullying
- Gender-Based Interpersonal Cybercrime
- Interpersonal Cybercrime Prevention
- Cyber Organized Crime: What is it?
- Conceptualizing Organized Crime & Defining Actors Involved
- Criminal Groups Engaging in Cyber Organized Crime
- Cyber Organized Crime Activities
- Preventing & Countering Cyber Organized Crime
- Cyberespionage
- Cyberterrorism
- Cyberwarfare
- Information Warfare, Disinformation & Electoral Fraud
- Responses to Cyberinterventions
- Framing the Issue of Firearms
- Direct Impact of Firearms
- Indirect Impacts of Firearms on States or Communities
- International and National Responses
- Typology and Classification of Firearms
- Common Firearms Types
- 'Other' Types of Firearms
- Parts and Components
- History of the Legitimate Arms Market
- Need for a Legitimate Market
- Key Actors in the Legitimate Market
- Authorized & Unauthorized Arms Transfers
- Illegal Firearms in Social, Cultural & Political Context
- Supply, Demand & Criminal Motivations
- Larger Scale Firearms Trafficking Activities
- Smaller Scale Trafficking Activities
- Sources of Illicit Firearms
- Consequences of Illicit Markets
- International Public Law & Transnational Law
- International Instruments with Global Outreach
- Commonalities, Differences & Complementarity between Global Instruments
- Tools to Support Implementation of Global Instruments
- Other United Nations Processes
- The Sustainable Development Goals
- Multilateral & Regional Instruments
- Scope of National Firearms Regulations
- National Firearms Strategies & Action Plans
- Harmonization of National Legislation with International Firearms Instruments
- Assistance for Development of National Firearms Legislation
- Firearms Trafficking as a Cross-Cutting Element
- Organized Crime and Organized Criminal Groups
- Criminal Gangs
- Terrorist Groups
- Interconnections between Organized Criminal Groups & Terrorist Groups
- Gangs - Organized Crime & Terrorism: An Evolving Continuum
- International Response
- International and National Legal Framework
- Firearms Related Offences
- Role of Law Enforcement
- Firearms as Evidence
- Use of Special Investigative Techniques
- International Cooperation and Information Exchange
- Prosecution and Adjudication of Firearms Trafficking
- Teaching Methods & Principles
- Ethical Learning Environments
- Overview of Modules
- Module Adaption & Design Guidelines
- Table of Exercises
- Basic Terms
- Forms of Gender Discrimination
- Ethics of Care
- Case Studies for Professional Ethics
- Case Studies for Role Morality
- Additional Exercises
- Defining Organized Crime
- Definition in Convention
- Similarities & Differences
- Activities, Organization, Composition
- Thinking Critically Through Fiction
- Excerpts of Legislation
- Research & Independent Study Questions
- Legal Definitions of Organized Crimes
- Criminal Association
- Definitions in the Organized Crime Convention
- Criminal Organizations and Enterprise Laws
- Enabling Offence: Obstruction of Justice
- Drug Trafficking
- Wildlife & Forest Crime
- Counterfeit Products Trafficking
- Falsified Medical Products
- Trafficking in Cultural Property
- Trafficking in Persons
- Case Studies & Exercises
- Extortion Racketeering
- Loansharking
- Links to Corruption
- Bribery versus Extortion
- Money-Laundering
- Liability of Legal Persons
- How much Organized Crime is there?
- Alternative Ways for Measuring
- Measuring Product Markets
- Risk Assessment
- Key Concepts of Risk Assessment
- Risk Assessment of Organized Crime Groups
- Risk Assessment of Product Markets
- Risk Assessment in Practice
- Positivism: Environmental Influences
- Classical: Pain-Pleasure Decisions
- Structural Factors
- Ethical Perspective
- Crime Causes & Facilitating Factors
- Models and Structure
- Hierarchical Model
- Local, Cultural Model
- Enterprise or Business Model
- Groups vs Activities
- Networked Structure
- Jurisdiction
- Investigators of Organized Crime
- Controlled Deliveries
- Physical & Electronic Surveillance
- Undercover Operations
- Financial Analysis
- Use of Informants
- Rights of Victims & Witnesses
- Role of Prosecutors
- Adversarial vs Inquisitorial Legal Systems
- Mitigating Punishment
- Granting Immunity from Prosecution
- Witness Protection
- Aggravating & Mitigating Factors
- Sentencing Options
- Alternatives to Imprisonment
- Death Penalty & Organized Crime
- Backgrounds of Convicted Offenders
- Confiscation
- Confiscation in Practice
- Mutual Legal Assistance (MLA)
- Extradition
- Transfer of Criminal Proceedings
- Transfer of Sentenced Persons
- Module 12: Prevention of Organized Crime
- Adoption of Organized Crime Convention
- Historical Context
- Features of the Convention
- Related international instruments
- Conference of the Parties
- Roles of Participants
- Structure and Flow
- Recommended Topics
- Background Materials
- What is Sex / Gender / Intersectionality?
- Knowledge about Gender in Organized Crime
- Gender and Organized Crime
- Gender and Different Types of Organized Crime
- Definitions and Terminology
- Organized crime and Terrorism - International Legal Framework
- International Terrorism-related Conventions
- UNSC Resolutions on Terrorism
- Organized Crime Convention and its Protocols
- Theoretical Frameworks on Linkages between Organized Crime and Terrorism
- Typologies of Criminal Behaviour Associated with Terrorism
- Terrorism and Drug Trafficking
- Terrorism and Trafficking in Weapons
- Terrorism, Crime and Trafficking in Cultural Property
- Trafficking in Persons and Terrorism
- Intellectual Property Crime and Terrorism
- Kidnapping for Ransom and Terrorism
- Exploitation of Natural Resources and Terrorism
- Review and Assessment Questions
- Research and Independent Study Questions
- Criminalization of Smuggling of Migrants
- UNTOC & the Protocol against Smuggling of Migrants
- Offences under the Protocol
- Financial & Other Material Benefits
- Aggravating Circumstances
- Criminal Liability
- Non-Criminalization of Smuggled Migrants
- Scope of the Protocol
- Humanitarian Exemption
- Migrant Smuggling v. Irregular Migration
- Migrant Smuggling vis-a-vis Other Crime Types
- Other Resources
- Assistance and Protection in the Protocol
- International Human Rights and Refugee Law
- Vulnerable groups
- Positive and Negative Obligations of the State
- Identification of Smuggled Migrants
- Participation in Legal Proceedings
- Role of Non-Governmental Organizations
- Smuggled Migrants & Other Categories of Migrants
- Short-, Mid- and Long-Term Measures
- Criminal Justice Reponse: Scope
- Investigative & Prosecutorial Approaches
- Different Relevant Actors & Their Roles
- Testimonial Evidence
- Financial Investigations
- Non-Governmental Organizations
- ‘Outside the Box’ Methodologies
- Intra- and Inter-Agency Coordination
- Admissibility of Evidence
- International Cooperation
- Exchange of Information
- Non-Criminal Law Relevant to Smuggling of Migrants
- Administrative Approach
- Complementary Activities & Role of Non-criminal Justice Actors
- Macro-Perspective in Addressing Smuggling of Migrants
- Human Security
- International Aid and Cooperation
- Migration & Migrant Smuggling
- Mixed Migration Flows
- Social Politics of Migrant Smuggling
- Vulnerability
- Profile of Smugglers
- Role of Organized Criminal Groups
- Humanitarianism, Security and Migrant Smuggling
- Crime of Trafficking in Persons
- The Issue of Consent
- The Purpose of Exploitation
- The abuse of a position of vulnerability
- Indicators of Trafficking in Persons
- Distinction between Trafficking in Persons and Other Crimes
- Misconceptions Regarding Trafficking in Persons
- Root Causes
- Supply Side Prevention Strategies
- Demand Side Prevention Strategies
- Role of the Media
- Safe Migration Channels
- Crime Prevention Strategies
- Monitoring, Evaluating & Reporting on Effectiveness of Prevention
- Trafficked Persons as Victims
- Protection under the Protocol against Trafficking in Persons
- Broader International Framework
- State Responsibility for Trafficking in Persons
- Identification of Victims
- Principle of Non-Criminalization of Victims
- Criminal Justice Duties Imposed on States
- Role of the Criminal Justice System
- Current Low Levels of Prosecutions and Convictions
- Challenges to an Effective Criminal Justice Response
- Rights of Victims to Justice and Protection
- Potential Strategies to “Turn the Tide”
- State Cooperation with Civil Society
- Civil Society Actors
- The Private Sector
- Comparing SOM and TIP
- Differences and Commonalities
- Vulnerability and Continuum between SOM & TIP
- Labour Exploitation
- Forced Marriage
- Other Examples
- Children on the Move
- Protecting Smuggled and Trafficked Children
- Protection in Practice
- Children Alleged as Having Committed Smuggling or Trafficking Offences
- Basic Terms - Gender and Gender Stereotypes
- International Legal Frameworks and Definitions of TIP and SOM
- Global Overview on TIP and SOM
- Gender and Migration
- Key Debates in the Scholarship on TIP and SOM
- Gender and TIP and SOM Offenders
- Responses to TIP and SOM
- Use of Technology to Facilitate TIP and SOM
- Technology Facilitating Trafficking in Persons
- Technology in Smuggling of Migrants
- Using Technology to Prevent and Combat TIP and SOM
- Privacy and Data Concerns
- Emerging Trends
- Demand and Consumption
- Supply and Demand
- Implications of Wildlife Trafficking
- Legal and Illegal Markets
- Perpetrators and their Networks
- Locations and Activities relating to Wildlife Trafficking
- Environmental Protection & Conservation
- CITES & the International Trade in Endangered Species
- Organized Crime & Corruption
- Animal Welfare
- Criminal Justice Actors and Agencies
- Criminalization of Wildlife Trafficking
- Challenges for Law Enforcement
- Investigation Measures and Detection Methods
- Prosecution and Judiciary
- Wild Flora as the Target of Illegal Trafficking
- Purposes for which Wild Flora is Illegally Targeted
- How is it Done and Who is Involved?
- Consequences of Harms to Wild Flora
- Terminology
- Background: Communities and conservation: A history of disenfranchisement
- Incentives for communities to get involved in illegal wildlife trafficking: the cost of conservation
- Incentives to participate in illegal wildlife, logging and fishing economies
- International and regional responses that fight wildlife trafficking while supporting IPLCs
- Mechanisms for incentivizing community conservation and reducing wildlife trafficking
- Critiques of community engagement
- Other challenges posed by wildlife trafficking that affect local populations
- Global Podcast Series
- Apr. 2021: Call for Expressions of Interest: Online training for academics from francophone Africa
- Feb. 2021: Series of Seminars for Universities of Central Asia
- Dec. 2020: UNODC and TISS Conference on Access to Justice to End Violence
- Nov. 2020: Expert Workshop for University Lecturers and Trainers from the Commonwealth of Independent States
- Oct. 2020: E4J Webinar Series: Youth Empowerment through Education for Justice
- Interview: How to use E4J's tool in teaching on TIP and SOM
- E4J-Open University Online Training-of-Trainers Course
- Teaching Integrity and Ethics Modules: Survey Results
- Grants Programmes
- E4J MUN Resource Guide
- Library of Resources
- {{item.name}} ({{item.items.length}}) items
- Add new list
E4J University Module Series: Organized Crime / Counter-Terrorism
Introduction and learning outcomes.
- Definitions and terminology
- Organized crime and terrorism: International legal framework
- Terrorism international framework: International terrorism-related conventions
- Terrorism international framework: General UNSC resolutions on terrorism
- Organized crime international framework: The Organized Crime Convention and its Protocols
- Theoretical frameworks on the linkages between organized crime and terrorism
- Typologies of criminal behaviour associated with terrorism
- Terrorism and drug trafficking
- Terrorism and trafficking in weapons
- Links between terrorism, crime and trafficking in cultural property / antiquities
- Trafficking in persons and terrorism
- Intellectual property crime and terrorism
Kidnapping for ransom and terrorism
- Exploitation of natural resources and terrorism
Case studies
Possible class structure, core reading, advanced reading, student assessment.
- Research and independent study questions
- Review and assessment questions
Additional teaching tools
Published March 2019
Regional Perspective: Eastern and Southern Africa - added in April 2020
This module is a resource for lecturers
Kidnapping-for-ransom, or hostage-taking, is defined in the International Convention against the Taking of Hostages :
Any person who seizes or detains and threatens to kill, to injure or to continue to detain another person in order to compel a third party, namely, a State, an international intergovernmental organization, a natural or juridical person, or a group of persons, to do or abstain from doing any act as an explicit or implicit condition for the release of hostages (article 1).
From 1970-2010, kidnapping incidents represented a small portion of all terrorist attacks (6.9%), however, through 2016 the percentage of kidnappings has jumped significantly to 15.8% of all terrorist attacks (Global Terrorism Database, 2018). In 2017, the total number of terrorist attacks (8,584 worldwide) decreased by 23 percent and the number of casualties due to terrorist attacks decreased by 27 percent, compared to 2016. The number of kidnapping victims and hostages recorded in this year were more than 8,900, which signifies a 43 percent decline from 2016 and a notable shift from previous years, which saw sharp increases in this figure. Globally, bombings and explosions accounted for 47 per cent of attacks in that year. Armed assault was the next most common form of attack in accounting for 22 per cent, followed by facility/infrastructure attacks (12 per cent), hostage taking (10 per cent) and assassinations (8 per cent).
Nasser Al-Wuhayshi, former leader of Yemen-based Al-Qaida in the Arabian Peninsula, called kidnapping "an easy spoil... a profitable trade and a precious treasure" (Rhode, 2014). Oumar Ould Hamaha, commander of the Mali-based Al-Qaida in the Islamic Maghreb (AQIM), noted in a newspaper interview: "lots of Western countries are paying enormous sums to the jihadists. The source of our financing is the Western countries. They are paying for jihad" (Nossiter, 2012).
Between 2008 and 2014, Al-Qaida and its direct affiliates made at least $125 million in revenue from kidnappings, $66 million of which was collected in 2013 (Callimachi, 2014). It is estimated that Al-Qaida in the Islamic Maghreb received $75 million in ransom payments between 2010 and 2014 (UNSC (b), 2014). Abu Sayyaf Group has participated in kidnappings where around $1.5 million in ransoms were collected by 2014, with approximately half that amount collected in 2012 and 2013. Boko Haram has also been known to raise funds thought mass kidnapping of foreigners and civilians for ransom. According to reports, Boko Haram has a specialized kidnapping task force that sets out to abduct politicians, business people, foreigners, rulers and civil servants with the intention of later trading them back for large sums of money or for the return of other Boko Haram militants (Institute for Economics and Peace, 2017).
Next: Exploitation of natural resources and terrorism
Back to top, supported by the state of qatar, 60 years crime congress.
- Subject List
- Take a Tour
- For Authors
- Subscriber Services
- Publications
- African American Studies
- African Studies
- American Literature
- Anthropology
- Architecture Planning and Preservation
- Art History
- Atlantic History
- Biblical Studies
- British and Irish Literature
- Childhood Studies
- Chinese Studies
- Cinema and Media Studies
- Communication
Criminology
- Environmental Science
- Evolutionary Biology
- International Law
- International Relations
- Islamic Studies
- Jewish Studies
- Latin American Studies
- Latino Studies
- Linguistics
- Literary and Critical Theory
- Medieval Studies
- Military History
- Political Science
- Public Health
- Renaissance and Reformation
- Social Work
- Urban Studies
- Victorian Literature
- Browse All Subjects

How to Subscribe
- Free Trials
In This Article Expand or collapse the "in this article" section Kidnapping
Introduction, general overviews.
- Child Kidnapping
- Terrorism and Kidnapping
- As a Business
- Societal Impact
- Secondary Economics of Kidnapping
- Responses to Kidnapping
- In the Media
- Government Relations, Politics, and Responsibility
Related Articles Expand or collapse the "related articles" section about
About related articles close popup.
Lorem Ipsum Sit Dolor Amet
Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Aliquam ligula odio, euismod ut aliquam et, vestibulum nec risus. Nulla viverra, arcu et iaculis consequat, justo diam ornare tellus, semper ultrices tellus nunc eu tellus.
- Commercial Sexual Exploitation of Children
- Crime, (In)Security, and Islam
- Cross-National Crime
- Human Rights
- Human Trafficking
Other Subject Areas
Forthcoming articles expand or collapse the "forthcoming articles" section.
- Education Programs in Prison
- Juvenile Justice Professionals' Perceptions of Youth
- Find more forthcoming articles...
- Export Citations
- Share This Facebook LinkedIn Twitter
Kidnapping by Rob T. Guerette , Andrea Headley LAST REVIEWED: 25 February 2016 LAST MODIFIED: 25 February 2016 DOI: 10.1093/obo/9780195396607-0195
Kidnappings refer to the taking or abduction of an individual against his or her will, usually followed by some duration of captivity. Kidnappings can be undertaken for several reasons, but the most common are for a demand of ransom payment, as a political terrorist event, or the abduction of a child, often following a child custody dispute. Kidnapping as a behavior has been documented long throughout history and was common practice among nomadic groups, who would steal brides from neighboring tribes. Studies of kidnappings have examined the topic from a variety of perspectives, including tracing the historical development of kidnapping epidemics in specific regions of the world, identification of the various typologies of kidnappings, and efforts to understand kidnappings from the offender’s perspective. Some literature has focused solely on a specific variety of kidnapping, such as child and parental kidnapping, terrorism-based kidnappings, and so-called corporate kidnappings. Other research has looked at the impact that kidnapping has on victims, families, and society at large. In focusing on the societal impact, a considerable portion of research has explored the economic benefits of kidnappings both for offenders and for secondary economic markets. Finally, research has examined approaches to the prevention of kidnappings, as well as common responses, particularly the role of media and government in kidnapping incidents. Perhaps the biggest limitation found in existing kidnapping research is the absence of empirical studies, which stems from the difficulty in obtaining systematically collected and representative data samples. Most existing empirical studies have been devoted to identifying the most problematic kidnapping countries around the world, while a handful have begun to examine patterns and trends in an effort to further theoretical foundations within the topical area.
Several scholars have characterized the nature or historical progression of kidnapping epidemics that have occurred generally and in various parts of the world, while others have traced the development of specific varieties of kidnappings, such as political or corporate. Khan and Sajid 2010 examines the circumstance of kidnapping in the North West Frontier Province of Pakistan and the limitation of existing governmental responses, while Mohamed 2008 inspects kidnapping for ransom in Southeast Asia. Ochoa 2012 highlights trends in kidnapping in Mexico City, Mexico and Wilson 1994 discusses the historical kidnappings of free blacks in the United States from 1780 to 1865. Newton 2002 gives a more general overview of kidnapping throughout history. Detotto, et al. 2014 examines duration of kidnapping events in Sardinia over time. Auerbach 1998 provides narratives that highlight the evolution and nature of ransom and politically based kidnappings. Johnson, et al. 2003 discusses the increase of corporate kidnappings in developing countries.
Auerbach, Ann H. 1998. Ransom: The untold story of international kidnapping . New York: Henry Holt.
This book employs a narrative case-study approach in combination with scientific studies to understand kidnapping worldwide. Specifically, the book looks at the growth of kidnapping for ransom and political purposes by exposing kidnapping negotiation processes.
Detotto, Claudio, Bryan C. McCannon, and Marco Vannini. 2014. Understanding ransom kidnappings and their duration. B. E. Journal of Economic Analysis & Policy 14.3: 849–871.
This paper analyzes the determinants of the length of kidnapping incidents by assessing ransom kidnappings that have occurred in Sardinia over time. A theoretical model is developed that particularly focuses on characteristics of the crime and the victim. Available online for purchase.
Johnson, Brian R., Doug McKenzie, and Greg L. Warchol. 2003. Corporate kidnapping: An exploratory study. Journal of Security Administration 26.2: 13–31.
This study examines corporate kidnapping’s beginning and rise in developing countries while offering explanations for the increase. Additionally, this paper documents the inadequacies of reporting mechanisms, which distort official numbers for recording kidnapping incidents.
Khan, Naushad Ali, and Imran A. Sajid. 2010. Kidnapping in the North West Frontier Province (NWFP) . Pakistan Journal of Criminology 2:175–187.
This study identifies reasons for kidnapping occurrences while highlighting the frequency and overarching trends in kidnapping in the North West Frontier Province. This paper also attempts to understand the deficiencies in legal responses to kidnapping in this locale.
Mohamed, Mohd K. N. 2008. Kidnap for ransom in South East Asia: The case for a regional recording standard. Asian Criminology 3.1: 61–73.
DOI: 10.1007/s11417-007-9040-1
This article advocates the need for a systematic counting method in order to understand the extent and range of kidnapping incidents. Additionally, the paper outlines some of the shortcomings of current agency statistics (e.g., variations in legal definitions, categorizing mechanisms, and counting strategies utilized). Available online for purchase.
Newton, Mike. 2002. The encyclopedia of kidnappings . New York: Checkmark.
This reference guide serves as a survey of kidnappings throughout history in order to identify kidnappers, victims, and the characteristics pertinent to the specific incident.
Ochoa, R. 2012. Not just rich: New tendencies in kidnapping in Mexico City. Global Crime 13.1: 1–21.
DOI: 10.1080/17440572.2011.632499
This paper focuses on the transformation and evolution of kidnappings in Mexico City, particularly paying attention to who is being kidnapped. The article utilizes qualitative analyses in order to provide an explanation for changes over time. Available online for purchase.
Wilson, Carol. 1994. Freedom at risk: The kidnapping of free Blacks in America, 1780–1865 . Lexington: Univ. Press of Kentucky.
The author utilizes archival records in order to highlight the depth and breadth of kidnapping free Blacks, particularly as it pertained to the reinforcement of the slave trade. Additionally, the author discusses the feelings and responses to such kidnappings by Black individuals.
back to top
Users without a subscription are not able to see the full content on this page. Please subscribe or login .
Oxford Bibliographies Online is available by subscription and perpetual access to institutions. For more information or to contact an Oxford Sales Representative click here .
- About Criminology »
- Meet the Editorial Board »
- Active Offender Research
- Adler, Freda
- Adversarial System of Justice
- Adverse Childhood Experiences
- Aging Prison Population, The
- Airport and Airline Security
- Alcohol and Drug Prohibition
- Alcohol Use, Policy and Crime
- Alt-Right Gangs and White Power Youth Groups
- Animals, Crimes Against
- Back-End Sentencing and Parole Revocation
- Bail and Pretrial Detention
- Batterer Intervention Programs
- Bentham, Jeremy
- Big Data and Communities and Crime
- Biosocial Criminology
- Black's Theory of Law and Social Control
- Blumstein, Alfred
- Boot Camps and Shock Incarceration Programs
- Burglary, Residential
- Bystander Intervention
- Capital Punishment
- Chambliss, William
- Chicago School of Criminology, The
- Child Maltreatment
- Chinese Triad Society
- Civil Protection Orders
- Collateral Consequences of Felony Conviction and Imprisonm...
- Collective Efficacy
- Commercial and Bank Robbery
- Communicating Scientific Findings in the Courtroom
- Community Change and Crime
- Community Corrections
- Community Disadvantage and Crime
- Community-Based Justice Systems
- Community-Based Substance Use Prevention
- Comparative Criminal Justice Systems
- CompStat Models of Police Performance Management
- Confessions, False and Coerced
- Conservation Criminology
- Consumer Fraud
- Contextual Analysis of Crime
- Control Balance Theory
- Convict Criminology
- Co-Offending and the Role of Accomplices
- Corporate Crime
- Costs of Crime and Justice
- Courts, Drug
- Courts, Juvenile
- Courts, Mental Health
- Courts, Problem-Solving
- Crime and Justice in Latin America
- Crime, Campus
- Crime Control Policy
- Crime Control, Politics of
- Crime Prevention, Delinquency and
- Crime Prevention, Situational
- Crime Prevention, Voluntary Organizations and
- Crime Trends
- Crime Victims' Rights Movement
- Criminal Career Research
- Criminal Decision Making, Emotions in
- Criminal Justice Data Sources
- Criminal Justice Ethics
- Criminal Justice Fines and Fees
- Criminal Justice Reform, Politics of
- Criminal Justice System, Discretion in the
- Criminal Records
- Criminal Retaliation
- Criminal Talk
- Criminology and Political Science
- Criminology of Genocide, The
- Critical Criminology
- Cross-Sectional Research Designs in Criminology and Crimin...
- Cultural Criminology
- Cultural Theories
- Cybercrime Investigations and Prosecutions
- Cycle of Violence
- Deadly Force
- Defense Counsel
- Defining "Success" in Corrections and Reentry
- Developmental and Life-Course Criminology
- Digital Piracy
- Driving and Traffic Offenses
- Drug Control
- Drug Trafficking, International
- Drugs and Crime
- Elder Abuse
- Electronically Monitored Home Confinement
- Employee Theft
- Environmental Crime and Justice
- Experimental Criminology
- Family Violence
- Fear of Crime and Perceived Risk
- Felon Disenfranchisement
- Feminist Theories
- Feminist Victimization Theories
- Fencing and Stolen Goods Markets
- Firearms and Violence
- Forensic Science
- For-Profit Private Prisons and the Criminal Justice–Indust...
- Gangs, Peers, and Co-offending
- Gender and Crime
- Gendered Crime Pathways
- General Opportunity Victimization Theories
- Genetics, Environment, and Crime
- Green Criminology
- Halfway Houses
- Harm Reduction and Risky Behaviors
- Hate Crime Legislation
- Healthcare Fraud
- Hirschi, Travis
- History of Crime in the United Kingdom
- History of Criminology
- Homelessness and Crime
- Homicide Victimization
- Honor Cultures and Violence
- Hot Spots Policing
- Identity Theft
- Immigration, Crime, and Justice
- Incarceration, Mass
- Incarceration, Public Health Effects of
- Income Tax Evasion
- Indigenous Criminology
- Institutional Anomie Theory
- Integrated Theory
- Intermediate Sanctions
- Interpersonal Violence, Historical Patterns of
- Interrogation
- Intimate Partner Violence, Criminological Perspectives on
- Intimate Partner Violence, Police Responses to
- Investigation, Criminal
- Juvenile Delinquency
- Juvenile Justice System, The
- Juvenile Waivers
- Kornhauser, Ruth Rosner
- Labeling Theory
- Labor Markets and Crime
- Land Use and Crime
- Lead and Crime
- LGBTQ Intimate Partner Violence
- LGBTQ People in Prison
- Life Without Parole Sentencing
- Local Institutions and Neighborhood Crime
- Lombroso, Cesare
- Longitudinal Research in Criminology
- Mandatory Minimum Sentencing
- Mapping and Spatial Analysis of Crime, The
- Mass Media, Crime, and Justice
- Measuring Crime
- Mediation and Dispute Resolution Programs
- Mental Health and Crime
- Merton, Robert K.
- Meta-analysis in Criminology
- Middle-Class Crime and Criminality
- Migrant Detention and Incarceration
- Mixed Methods Research in Criminology
- Money Laundering
- Motor Vehicle Theft
- Multi-Level Marketing Scams
- Murder, Serial
- Narrative Criminology
- National Deviancy Symposia, The
- Nature Versus Nurture
- Neighborhood Disorder
- Neutralization Theory
- New Penology, The
- Offender Decision-Making and Motivation
- Offense Specialization/Expertise
- Organized Crime
- Outlaw Motorcycle Clubs
- Panel Methods in Criminology
- Peacemaking Criminology
- Peer Networks and Delinquency
- Perceptions of Youth, Juvenile Justice Professionals'
- Performance Measurement and Accountability Systems
- Personality and Trait Theories of Crime
- Persons with a Mental Illness, Police Encounters with
- Phenomenological Theories of Crime
- Plea Bargaining
- Police Administration
- Police Cooperation, International
- Police Discretion
- Police Effectiveness
- Police History
- Police Militarization
- Police Misconduct
- Police, Race and the
- Police Use of Force
- Police, Violence against the
- Policing and Law Enforcement
- Policing, Body-Worn Cameras and
- Policing, Broken Windows
- Policing, Community and Problem-Oriented
- Policing Cybercrime
- Policing, Evidence-Based
- Policing, Intelligence-Led
- Policing, Privatization of
- Policing, Proactive
- Policing, School
- Policing, Stop-and-Frisk
- Policing, Third Party
- Polyvictimization
- Positivist Criminology
- Pretrial Detention, Alternatives to
- Pretrial Diversion
- Prison Administration
- Prison Classification
- Prison, Disciplinary Segregation in
- Prison Education Exchange Programs
- Prison Gangs and Subculture
- Prison History
- Prison Labor
- Prison Visitation
- Prisoner Reentry
- Prisons and Jails
- Prisons, HIV in
- Private Security
- Probation Revocation
- Procedural Justice
- Property Crime
- Prosecution and Courts
- Prostitution
- Psychiatry, Psychology, and Crime: Historical and Current ...
- Psychology and Crime
- Public Criminology
- Public Opinion, Crime and Justice
- Public Order Crimes
- Public Social Control and Neighborhood Crime
- Punishment Justification and Goals
- Qualitative Methods in Criminology
- Queer Criminology
- Race and Sentencing Research Advancements
- Race, Ethnicity, Crime, and Justice
- Racial Threat Hypothesis
- Racial Profiling
- Rape and Sexual Assault
- Rape, Fear of
- Rational Choice Theories
- Rehabilitation
- Religion and Crime
- Restorative Justice
- Risk Assessment
- Routine Activity Theories
- School Bullying
- School Crime and Violence
- School Safety, Security, and Discipline
- Search Warrants
- Seasonality and Crime
- Self-Control, The General Theory:
- Self-Report Crime Surveys
- Sentencing Enhancements
- Sentencing, Evidence-Based
- Sentencing Guidelines
- Sentencing Policy
- Sex Offender Policies and Legislation
- Sex Trafficking
- Sexual Revictimization
- Situational Action Theory
- Snitching and Use of Criminal Informants
- Social and Intellectual Context of Criminology, The
- Social Construction of Crime, The
- Social Control of Tobacco Use
- Social Control Theory
- Social Disorganization
- Social Ecology of Crime
- Social Learning Theory
- Social Networks
- Social Threat and Social Control
- Solitary Confinement
- South Africa, Crime and Justice in
- Sport Mega-Events Security
- Stalking and Harassment
- State Crime
- State Dependence and Population Heterogeneity in Theories ...
- Strain Theories
- Street Code
- Street Robbery
- Substance Use and Abuse
- Surveillance, Public and Private
- Sutherland, Edwin H.
- Technology and the Criminal Justice System
- Technology, Criminal Use of
- Terrorism and Hate Crime
- Terrorism, Criminological Explanations for
- Testimony, Eyewitness
- Therapeutic Jurisprudence
- Trajectory Methods in Criminology
- Transnational Crime
- Truth-In-Sentencing
- Urban Politics and Crime
- US War on Terrorism, Legal Perspectives on the
- Victim Impact Statements
- Victimization, Adolescent
- Victimization, Biosocial Theories of
- Victimization Patterns and Trends
- Victimization, Repeat
- Victimization, Vicarious and Related Forms of Secondary Tr...
- Victimless Crime
- Victim-Offender Overlap, The
- Violence Against Women
- Violence, Youth
- Violent Crime
- White-Collar Crime
- White-Collar Crime, The Global Financial Crisis and
- White-Collar Crime, Women and
- Wilson, James Q.
- Wolfgang, Marvin
- Women, Girls, and Reentry
- Wrongful Conviction
- Privacy Policy
- Cookie Policy
- Legal Notice
- Accessibility
Powered by:
- [66.249.64.20|162.248.224.4]
- 162.248.224.4
- The Inventory

Kidnapping for ransom has become Nigeria’s latest security problem

Frequent acts of violent crime have grown to form a major threat to Nigeria’s national security . These include instances of militancy, insurgency and banditry. Banditry includes cattle rustling, armed robbery and kidnapping for ransom.
Kidnapping has remained the most virulent form of banditry in Nigeria. It has become the most pervasive and intractable violent crime in the country.
Kidnapping can be targeted at individuals or at groups. School children have been kidnapped in groups in various parts of Nigeria. Usually, the prime targets of kidnapping for ransom are those considered to be wealthy enough to pay a fee in exchange for being freed.
Kidnapping is the unlawful detention of a person through the use of force, threats, fraud or enticement. The purpose is an illicit gain, economic or material, in exchange for liberation. It may also be used to pressure someone into doing something—or not doing something.
Nigeria has one of the world’s highest rates of kidnap-for-ransom cases. Other countries high up on the list included Venezuela, Mexico, Yemen, Syria, the Philippines, Iraq, Afghanistan and Somalia.
Thousands of Nigerians have been kidnapped for ransom and other purposes over the years . Kidnapping has prevailed in spite of measures put in place by the government. The Nigerian police’s anti-kidnapping squad, introduced in the 2000s, has endeavored to stem the menace. But this been to no avail, mainly due to a lack of manpower and poor logistics.
In my view these efforts have also failed because of weak sanctioning and deterrence mechanisms. Kidnapping thrives in an environment that condones crime; where criminal opportunism and impunity prevail over and above deterrence.
This obviously calls for an urgent review of Nigeria’s current anti-kidnapping approach to make it more effective.
Opportunistic and organized bandits
Even prior to the advent of colonialism there were recorded cases of kidnap for rape, ritual or for other purposes in various parts of Nigeria. But kidnapping today is done primarily for ransom – either money or its material equivalent to be paid for someone’s release. The underlying logic of the kidnapping enterprise is that the victim is worth a ransom value and they or their proxy have the capacity to pay.
Each victim has a so-called “kidnap ransom value” which makes them an attractive target. This value is determined by a number of factors. These include the victim’s socio-economic or political status, family or corporate premium on the victim, the type of kidnappers involved, as well as the dynamics of ransom negotiation.
The kidnapping business in Nigeria has been mostly perpetrated by criminal gangs and violent groups pursuing political agendas . Bandits have often taken to kidnapping for ransom to make money. The escapades of the famous kidnap kingpin, Evans, speak volumes of this pattern of kidnapping. Evans was a multimillionaire kidnapper who was arrested in Lagos a few years ago. He is currently is detention awaiting trial.
Organized violent groups such as militants and insurgents have also been involved in kidnap for ransom in Nigeria. Current trends have been linked back to the example set by Niger Delta militants who resorted to solo and group abductions as a means of generating funds both for private use and for the cause of a particular group.
Similarly, Boko Haram insurgents have used the proceeds of kidnapping to keep their insurgency afloat. The insurgents engage in single or group kidnapping as a means of generating money to fund their activities. Huge sums are often paid as ransom by the victims’ families and associates to secure their release.
In addition to militants and insurgents, organized local and transnational criminal syndicates have been involved. This is happening to apocalyptic proportions in North West Nigeria where rural bandits engage regularly in kidnapping in the states of Zamfara, Kaduna, Katsina, Kebbi and Sokoto.
Kidnapping has led to the loss of tens of thousands of lives and huge sums of money in Nigeria. Many of the victims of the crime have been killed in the course of their abduction, custody or release. Many more have been injured. This is in addition to huge amounts of money lost to ransom takers.
For the victims and their families and friends, the consequences are even more frightful.
Nigeria should never have got here. Kidnappers persist because the benefits of their crimes exceed the costs. So the obvious solution is to raise the costs by imposing harsher, surer penalties. The present penalty for kidnapping ranges from one to 20 years in prison, with the possibility of life imprisonment for extreme cases involving, for instance, murder.
Stricter measures, such as life imprisonment or the death penalty, may not be completely out of place in dealing with the kidnapping menace. After all, the crime of kidnapping is a maximum threat that requires an equally maximum deterrence.
Chukwuma Al Okoli , Lecturer/Resident Researcher Department of Political Science, Federal University Lafia
This article is republished from The Conversation under a Creative Commons license. Read the original article .
Sign up to the Quartz Africa Weekly Brief here for news and analysis on African business, tech and innovation in your inbox
📬 Sign up for the Daily Brief
Our free, fast, and fun briefing on the global economy, delivered every weekday morning.
Growing Nexus of Terrorism and Organized Crime: An Introduction
- Living reference work entry
- First Online: 12 August 2022
- Cite this living reference work entry

- Christina Schori Liang 2
72 Accesses
Terrorism has become an enduring global threat, due to an unprecedented growth in interactivity between and among a range of armed violent non-state actors, including organized criminal groups. This is due to a crisis of state fragility, as state institutions weaken and some states even face the prospect of collapse. In this absence of governance, corruption becomes rampant, in some cases allowing terrorist and criminal groups to replace state functions, further undermining the state. In this vicious cycle, these groups are beginning to cooperate on multiple levels and are sometimes even becoming hybrid organizations. This chapter will attempt to shed light on some of the key issues that have led to the nexus of crime and terror, and it will offer some innovative and strategic ideas on how best to move forward in meeting these current and future challenges.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Institutional subscriptions
Similar content being viewed by others

The Nexus Between Terrorist Organizations and Organized Crime

The Challenges of Defining Terrorism for Counter-Terrorism Policy
Agence France-Press (2015) Islamic State ‘Mafias’ made $11 million per month in Iraq Province
Google Scholar
Basra R, Neumann PR (2017) Crime as Jihad: developments in the crime-Terror Nexus in Europe. Combating Terrorism Center (CTC) Sentinel 10(9):1–5, November 20
Basra R, Neumann PR, Brunner C (2016) Criminal pasts, terrorist futures: European Jihadists and the New Crime-Terror Nexus. ICSR. Perspect Terrorism 10(6):25–40
Bruce J (2015) How prison breaks help ISIS. The Arab Weekly, 17 July. Accessed from http://www.thearabweekly.com/Opinion/1167/How-prison-breaks-helped-ISIS
Canadian Security Intelligence Service Commentary No.13 (1991) Terrorism and the rule of law: dangerous comprise
Chulov M (2014) ISIS: the inside story. The Guardian, 11 December. Accessed from https://www.theguardian.com/world/2014/dec/11/-sp-isis-the-inside-storys
Clarke CP (2015) Terrorism Inc.: The financing of terrorism, insurgency, and irregular warfare. Praeger, London
Clarke C (2018) Lessons from the Islamic State in Iraq and Syria and other emerging threats, testimony, financial services committee, subcommittee on terrorism and illicit finance, September 7, 2018. An overview of current trends in terrorism and illicit finance, 7 September 2018
CNBC, How ISIS managed to acquire $2B in assets, 14 June, 2014
Counter-Terrorism Office Tells Security Council, Security Council 8116th Meeting. https://www.un.org/press/en/2017/sc13097.doc.htm
EUROPOL (2016) Changes in modus operandi of Islamic State Terrorist Attacks. EUROPOL Public Information, January 18. Accessed from https://www.europol.europa.eu/content/changes-modus-operandi-islamic-state-terrorist-attacks
Felbab-Brown V, Trinkunas H, Hamid S (2017) Militants, criminals and warlords: the challenge of local governance in an age of disorder. The Brookings Institution Press, Washington, DC
Freedom House (2021) Freedom in the world 2021, report (2021) Freedom House. Accessed from https://freedomhouse.org/report/freedom-world/2021/democracy-under-siege
Global Initiative (2018) World Atlas of illicit flows. Accessed from https://globalinitiative.net/wp-content/uploads/2018/09/Atlas-Illicit-Flows-FINAL-WEB-VERSION-copia-compressed.pdf
Goodwin B (2021) Pandora papers: how journalists mined terabytes of offshore data to expose the world’s elites. Computer Weekly, 2 December. Accessed from https://www.computerweekly.com/news/252510313/Pandora-Papers-How-journalists-mined-terabytes-of-offshore-data-to-expose-the-worlds-elites
Hubbard B, Saad H (2021) On Syrias Ruins, a drug empire flourishes. New York Times, 5 December. Accessed from https://www.nytimes.com/2021/12/05/world/middleeast/syria-drugs-captagon-assad.html
Hutchinson S, O’Malley P (2007) A Crime-Terror Nexus? Thinking of some of the links between terrorism and criminality. Stud Conflict Terrorism 30(12):1095–1107
Article Google Scholar
Jongman A (2011) World directory of extremist, terrorist and other organisations associated with Guerrilla warfare, political violence, protest, organised crime and cyber-crime. In: Schmid AP (ed) The Routledge handbook of terrorism research. Routledge, London/New York
Krassén P, Lallerstedt K (2015) How leading companies are affected by counterfeiting and IP Infringement: a study of the NASDAQ OMX 30 Stockholm Index. Black Market Watch and Svenskt Näringsliv, Geneva/Stockholm. May 2015. Accessed from http://www.svensktnaringsliv.se/migration_catalog/Rapporter_och_opinionsmaterial/Rapporter/omx30_english_webbpdf_617515.html/BINARY/OMX30_English_webb.pdf
Liang CS (2015) Cyber Jihad: understanding and countering Islamic State Propaganda. GCSP Policy Paper 2(4):6. Accessed from https://www.gcsp.ch/publications/cyber-jihad
Ligeti K, Lasalle M (2018) The organised crime-terrorism nexus: how to address the issue of ISIS benefitting from lucrative criminal activities? University of Luxembourg Law working paper no. 2018-009
Makarenko T (2004) The crime-terror continuum: tracing the interplay between transnational organised crime and terrorism. Global Crime 6(1):129–145
Matfess H, Miklaucic M (eds) (2016) Beyond convergence: world without order. Center for Complex Operations, Institute for National Security Studies, National Defense University, Washington, DC. Accessed from https://cco.ndu.edu/Portals/96/Documents/books/Beyond%20Convergence/BEYOND%20CONVERGENCE%20%20World%20Without%20Order%20.pdf?ver=2016-10-25-125406-170
Nellemann C, Henriksen R, Kreilhuber A, Stewart D, Kotsovou M, Raxter P, Mrema E, Barrat S (eds) (2016) The rise of environmental crime: a growing threat to natural resources, peace, development and security: a UNEP-INTERPOL rapid response assessment UNEP and RHIPTO
Office of the High Commissioner for Human Rights (OHCHR) (2016) Press Release, UN Commission of Inquiry on Syria: ISIS is committing genocide against the Yazidis. Accessed from https://www.ohchr.org/en/press-releases/2016/06/uncommission-inquiry-syria-isis-committing-genocide-against-yazidis
Oftedal E (2015) The financing of Jihadi Terrorist cells in Europe, Oslo, Norwegian Defence Research Establishment, 6 January
Peritz A (2019) The coming ISIS jailbreak. Foreign Affairs. Accessed from https://www.foreignaffairs.com/articles/middle-east/2019-10-23/coming-isis-jailbreak
Phillips M, Kamen E (2014) Entering the Black Hole: the Taliban, terrorism and organised crime. Contemp Voices St Andrews J Int Relat 5(3)
Poushter J, Manevich D (2017) Globally, people point to ISIS and climate change as leading security threats. Pew Research Center, August 1. Accessed from https://www.pewresearch.org/global/2017/08/01/globally-people-point-to-isis-and-climate-change-as-leading-security-threats/
Reuter C (2015) The terror strategist: secret files reveal the structure of the Islamic State. Der Spiegel Online, April 18. Accessed from http://www.spiegel.de/international/world/islamic-state-files-show-structure-ofislamist-terror-group-a-1029274-druck.html
Rhipto (2015) INREP briefing document (Lillehammer: Rhipto-Norwegian Centre for Global Analysis), September 2015
Romaniecki L (1974) Soviet Union and international terrorism. Soviet Stud 26(3):417–440
Rumiyah, Issue 11, Al Hayat Media Center, 2017, pp 44–52
Shaw M (2016) “We pay, you pay”: protection economies, financial flows and violence. In: Matfess H, Miklaucic M (eds) Beyond convergence: world without order. Center for Complex Operations, Institute for National Strategic Studies, National Defense University, Washington, DC. Accessed from https://cco.ndu.edu/Portals/96/Documents/books/Beyond%20Convergence/BEYOND%20CONVERGENCE%20%20World%20Without%20Order%20.pdf?ver=2016-10-25-125406-170
Singer PW, Brooking E (2015) Terror on Twitter: how ISIS is taking war to social media –and social media is fighting back. Popular Science, December 11
UNCTED (2017) Greater cooperation needed to tackle danger posed by returning foreign fighters, H10e2a7d of 1028
UNICRI (2020) Stop the virus of disinformation: the malicious use of social media by terrorist, violent extremists and criminal groups during the COVID-19 pandemic. UNICRI Report, November
United Nations (2017) Greater cooperation needed to tackle danger posed by returning foreign fighters, Head of Counter-Terrorism Office Tells Security Council, Security Council 8116th Meeting, 28 November 2017. https://www.un.org/press/en/2017/sc13097.doc.htm
UNODC (2019) Linkages between organized crime and terrorism. United National Office on Drugs and Crime, Vienna
UNODC (2021) Drug situation in Afghanistan 2021: latest findings and emerging threats. United Nations Office on Drugs and Crime (UNODC). https://www.unodc.org/documents/data-and-analysis/Afghanistan/Afghanistan_brief_Nov_2021.pdf . Assessed Jan 2022
UNSC 2482 (2019) Accessed from https://undocs.org/S/RES/2482(2019)
Woodiwiss M (2001) Organized crime and American power. University of Toronto Press, Toronto
Book Google Scholar
Download references
Author information
Authors and affiliations.
Geneva Centre for Security Policy, Geneva, Switzerland
Christina Schori Liang
You can also search for this author in PubMed Google Scholar
Editor information
Editors and affiliations.
College of Public Health, University of South Florida, Tampa, FL, USA
Anthony J. Masys
Section Editor information
Rights and permissions.
Reprints and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this entry
Cite this entry.
Liang, C.S. (2022). Growing Nexus of Terrorism and Organized Crime: An Introduction. In: Masys, A.J. (eds) Handbook of Security Science. Springer, Cham. https://doi.org/10.1007/978-3-319-51761-2_65-1
Download citation
DOI : https://doi.org/10.1007/978-3-319-51761-2_65-1
Received : 23 February 2022
Accepted : 04 March 2022
Published : 12 August 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-51761-2
Online ISBN : 978-3-319-51761-2
eBook Packages : Springer Reference Physics and Astronomy Reference Module Physical and Materials Science Reference Module Chemistry, Materials and Physics
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Israel-Gaza War
- War in Ukraine
- US & Canada
- UK Politics
- N. Ireland Politics
- Scotland Politics
- Wales Politics
- Latin America
- Middle East
- In Pictures
- BBC InDepth
- US Election
- Election polls
- Kamala Harris
- Donald Trump
- Executive Lounge
- Technology of Business
- Women at the Helm
- Future of Business
- Science & Health
- Artificial Intelligence
- AI v the Mind
- Film & TV
- Art & Design
- Entertainment News
- Arts in Motion
- Destinations
- Australia and Pacific
- Caribbean & Bermuda
- Central America
- North America
- South America
- World’s Table
- Culture & Experiences
- The SpeciaList
- Natural Wonders
- Weather & Science
- Climate Solutions
- Sustainable Business
- Green Living
Nigeria's security crises - five different threats

Nigeria is faced with an unprecedented wave of different but overlapping security crises - from kidnapping to extremist insurgencies - almost every corner of the country has been hit by violence and crime.
Audu Bulama Bukarti, a senior analyst on Sahel security at the Tony Blair Institute, says the scale of the insecurity threatens the very fabric of Nigerian society: "With every attack, human lives are lost or permanently damaged and faith in democracy and the country is diminishing."
When President Muhammadu Buhari was elected in 2015, he promised to protect citizens from terrorists and criminals. But there are less than two years left of his final term in office and the country is more unstable than it's been in decades.
Some have linked the recent surge of insecurity to the staggering poverty across the country. Youth unemployment currently stands at 32.5% and the country is in the middle of one of the worst economic downturns in 27 years.
Here are Nigeria's five biggest security threats:
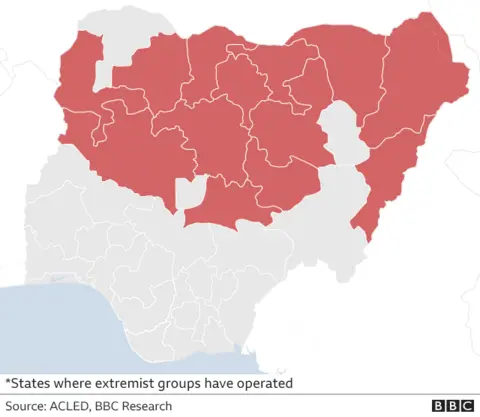
Despite claiming during his first year in office that Islamist militant group Boko Haram had been "technically" defeated, President Buhari now admits that his government is failing to stop the insurgency, which began in the north-east.
Indeed, Boko Haram is expanding into new areas and taking advantage of Nigeria's poverty and other security challenges to fuel its extremist ideologies. According to the UN, by the end of 2020, conflict with the group had led to the deaths of almost 350,000 people and forced millions from their homes.
Boko Haram launches deadly raids, in some cases hoisting its flag and imposing extremist rule on local people. It levies taxes on farms and the sale of agricultural products. The once booming international fish market in the Chad Basin is now completely controlled by the group.

The challenge is made harder by Nigeria's ungoverned spaces - areas that are remote and largely ignored, where groups can torment rural communities without fear of reprisal.
In recent years, a splinter faction allied to the Islamic State group, called the Islamic State's West Africa Province, has surpassed Boko Haram in size and capacity. It now ranks among IS's most active affiliates in the region.
Both groups have so far resisted the government's military operations.
- ANALYSIS: Why Nigeria has failed to defeat Boko Haram
Clashes between herders and farmers
There have been violent disputes between nomadic animal herders and farmers in Nigeria for many years.
But disagreements over the use of land and water, as well as grazing routes, have been exacerbated by climate change and the spread of the Sahara Desert, as herders move further south looking for pasture. Thousands have been killed in clashes over limited resources.
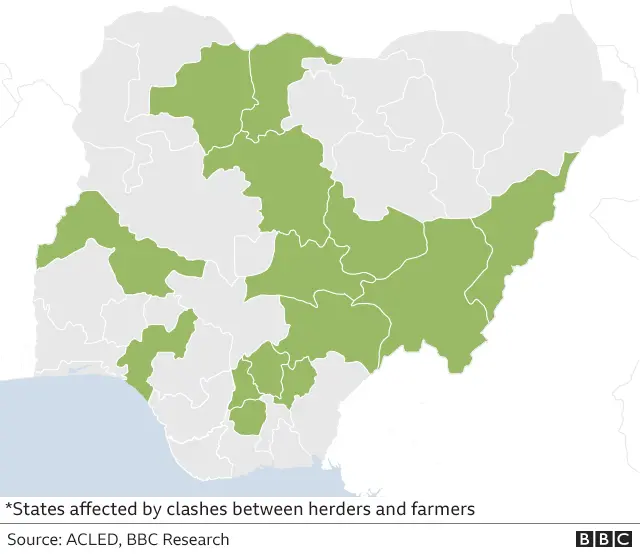
Benue State, in the centre of the country, has recorded the deadliest attacks. Recently, seven people were killed when gunmen opened fire on a camp for those fleeing the conflict. Some have also blamed herders for kidnapping people and demanding a ransom.

The tension has led to some state governors banning grazing on open land, and thus creating friction with the central government.
In 2019, federal authorities launched a 10-year National Livestock Transformation Plan to curtail the movement of cattle and boost livestock production in an attempt to stop the conflict. But critics say a lack of political leadership, expertise and funding, plus delays are derailing the project.
- Could ranches solve Nigeria's deadly herder-farmer conflict?
Banditry and kidnapping
One of the scariest threats for families in Nigeria is the frequent kidnapping of schoolchildren from their classrooms and boarding houses.
More than 1,000 students have been abducted from their schools since December 2020, many only released after thousands of dollars are paid as ransom.
Some of the kidnappers are commonly referred to as "bandits" in Nigeria. These criminals raid villages, kidnap civilians and burn down houses.
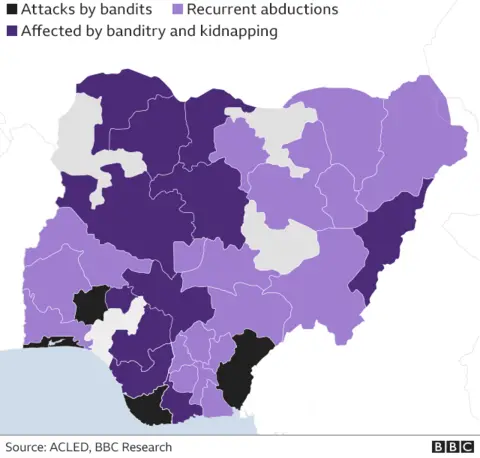
Attacks by bandits have forced thousands of people to flee their homes and seek shelter in other parts of the country.
The north-west is the epicentre of these attacks. In Zamfara state alone, over 3,000 people have been killed since 2012 and the attacks are still going on. Hundreds of schools were closed following abductions at schools in Zamfara and Niger state, where children as young as three years old were seized.
By every indication, Nigeria's lucrative kidnapping industry is thriving - expanding into previously safe areas - and seemingly beyond the control of the country's army. It poses a real threat to trade and education, as well as the country's farming communities.

More on Nigeria's kidnapping crisis:
- Why schoolchildren are being abducted in Nigeria
- Why a $30m scheme failed to stop school abductions
- WATCH: Where kidnappers millions for a child's life
Separatist insurgency
A separatist group called the Indigenous People of Biafra (Ipob) has been clashing with Nigeria's security agencies. Ipob wants a group of states in the south-east, mainly made up of people from the Igbo ethnic group, to break away and form the independent nation of Biafra.

The group was founded in 2014 by Nnamdi Kanu, who was recently arrested and is set to face trial on terrorism and treason charges. His arrest has been a major blow to the movement.
The idea of Biafra is not new. In 1967, regional leaders declared an independent state, which led to a brutal civil war and the death of up to a million people.
Supporters of Nnamdi Kanu's movement have been accused of launching deadly attacks on government offices, prisons and the homes of politicians and community leaders.
President Buhari has vowed to crush Ipob. Last month he tweeted that "those misbehaving today" would be dealt with in "the language they will understand".
The post was removed by Twitter for violating its rules after Mr Buhari faced a backlash online. The incident led to the suspension of Twitter in Nigeria.
- ANALYSIS: What Kanu's arrest means for Ipob
Oil militants

In the oil-producing south, security challenges are nothing new.
It is Nigeria's biggest foreign export earner, and militants in the Niger Delta have long agitated for a greater share of the profit. They argue the majority of the oil comes from their region and the environmental damage caused by its extraction has devastated communities and made it impossible for them to fish or farm.
For years, militants pressured the government by kidnapping oil workers and launching attacks on security personnel and oil infrastructure, like pipelines.
To address this, ex-president Umaru Musa Yar'Adua launched a presidential amnesty programme in 2009, which saw the formal end of the Niger Delta militants.
But armed cult groups still pose a security challenge in the region and industry officials have been warning that militancy is once again picking up.
Who are Boko Haram?
Is africa the new jihadist battleground, how islamic state has expanded into central africa, fewer boots: radical rethink in fighting insurgencies, #bringbackourgirls explained two years on.

An official website of the United States government
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- The Attorney General
- Organizational Chart
- Budget & Performance
- Privacy Program
- Press Releases
- Photo Galleries
- Guidance Documents
- Publications
- Information for Victims in Large Cases
- Justice Manual
- Business and Contracts
- Why Justice ?
- DOJ Vacancies
- Legal Careers at DOJ
Five Defendants Involved in String of Violent Crimes, Drug and Gun Offenses, And Money Laundering Have Been Sentenced
Louisville, KY – A fifth defendant was sentenced this week to 30 years in federal prison for his role in numerous felony offenses, including kidnapping, robbery, drug trafficking, and money laundering. Several other defendants were previously sentenced on the charges.
U.S. Attorney Michael A. Bennett of the Western District of Kentucky, Special Agent in Charge Michael E. Stansbury of the FBI Louisville Field Office, Chief Paul Humphrey of the Louisville Metro Police Department, Sheriff Walt Sholar of the Bullitt County Sheriff’s Office, and Sheriff John E. Aubrey of the Jefferson County Sheriff’s Office made the announcement.
According to court documents, Dayton Peterson , 24, of Louisville, was sentenced on October 22, 2024, to 30 years in prison, followed by 5 years of supervised release, for kidnapping, impersonator making arrest or search, robbery, using or carrying a firearm during and in relation to a crime of violence, conspiracy to possess with intent to distribute cocaine and heroin, possession with intent to distribute cocaine and heroin, possession of a firearm in furtherance of a drug trafficking crime, and engaging in monetary transactions derived from a specified unlawful activity.
Joshua Lohden , 26, of Louisville was sentenced on July 24, 2024, to 22 years in prison, followed by 5 years of supervised release, for kidnapping, impersonator making arrest or search, possession of a firearm in furtherance of a drug trafficking crime, and robbery.
David Langdon , 39, of Louisville was sentenced on September 11, 2024, to 11 years and 5 months in prison, followed by 5 years of supervised release, for kidnapping, impersonator making arrest or search, robbery, possession with intent to distribute methamphetamine, cocaine, and fentanyl, possession of a firearm by a convicted felon, and possession of a firearm in furtherance of a drug trafficking crime. On or about August 23, 2022, Langdon was prohibited from possessing a firearm because he had previously been convicted of the following felony offenses.
On October 14, 2015, in Jefferson County Circuit Court, Langdon was convicted of possession of a handgun by a convicted felon, trafficking in a controlled substance in the first degree, and possession of a controlled substance in the first degree.
On October 15, 2015, in Jefferson County Circuit Court, Langdon was convicted of trafficking in a controlled substance in the first degree greater than 2 grams of heroin.
J. Louis Nance , 34, of Louisville was sentenced on July 24, 2024, to 6 years in prison, followed by 5 years of supervised release, for kidnapping and impersonator making arrest or search.
Samantha Trummer , 30, of Louisville was sentenced on July 22, 2024, to 4 years of probation for engaging in monetary transactions derived from a specified unlawful activity.
John Lohden is awaiting sentencing.
Defendants Dayton Peterson , John Lohden , and Samantha Trummer were found guilty after a 10-day jury trial in March of 2024. The remaining defendants pleaded guilty prior to trial.
There is no parole in the federal system.
The FBI, LMPD, Jefferson County Sheriff’s Office, and Bullitt County Sheriff’s Office investigated the case, with assistance from the ATF, IRS, DEA, and Kentucky State Police.
Assistant U.S. Attorneys Alicia P. Gomez and Frank E. Dahl III are prosecuting the case, with assistance from paralegal Adela Alic.
This case is part of Project Safe Neighborhoods (PSN), a program bringing together all levels of law enforcement and the communities they serve to reduce violent crime and gun violence, and to make our neighborhoods safer for everyone. On May 26, 2021, the Department launched a violent crime reduction strategy strengthening PSN based on these core principles: fostering trust and legitimacy in our communities, supporting community-based organizations that help prevent violence from occurring in the first place, setting focused and strategic enforcement priorities, and measuring the results.
Related Content

IMAGES
VIDEO
COMMENTS
State security officers call it a complex, violent crime involving terrorism, jihad insurgencies, armed robbery, murder, kidnapping, rape and the illegal possession of firearms.
What Is Terrorism? Terrorism has a long history, appearing in nearly every asymmetric conflict. One of the earliest accounts of terrorism centers on nonstate actor resistance to the Roman Empire in the Judea Province in the 1st century ce (Chaliand & Blin, 2016).Groups of all religions, national origins, political aims, and ideological creeds have used violence or the threat of violence ...
A Watertown woman is accused of kidnapping her son from Jefferson County's Department of Social Services and fleeing the scene in a stolen vehicle. ... court papers say, injured the child, who ...
2006, shows that the main causes of kidnapping are 'politicians, poverty, terrorism, lack of stif fer punishment by government, negligence on the part of the well -to-do in families and quick ...
This module is a resource for lecturers Kidnapping for ransom and terrorism Key facts. Kidnapping-for-ransom, or hostage-taking, is defined in the International Convention against the Taking of Hostages:. Any person who seizes or detains and threatens to kill, to injure or to continue to detain another person in order to compel a third party, namely, a State, an international intergovernmental ...
Kidnapping is derived from "kid"= "child" and "nap"="snatch", and was first recorded in 1673. 4. It was originally used as a term for the practice of stealing children for use as servants or laborers in the American colonies. Kidnapping is the crime of taking away of a person by force,
Kidnapping has become an attractive criminal enterprise owing to its low risk and high financial yield for in the hands of its perpetrators, who have turned it into a multi-million-naira enterprises.
Ochoa 2012 highlights trends in kidnapping in Mexico City, Mexico and Wilson 1994 discusses the historical kidnappings of free blacks in the United States from 1780 to 1865. Newton 2002 gives a more general overview of kidnapping throughout history. Detotto, et al. 2014 examines duration of kidnapping events in Sardinia over time.
Kidnapping in Nigeria. Kidnapping is not a new problem in Nigeria, and it is one of the country's biggest challenges. The country faces many problems, including unemployment, corruption, and low education rates—but it is kidnapping, thanks to high-profile incidents perpetrated by the Islamic militant group Boko Haram, that has drawn the world's attention.
An abduction becomes a kidnapping once demands are made by the hostage-takers. In this guide, the term 'abduction' is used broadly to refer to the forcible capture of individuals and is used as an umbrella term to refer to situations where no demands have been made as well as kidnappings (where demands have been made). Introduction Introduction
The Model Penal Code also includes acts of terrorism and interference with government and political duties in the definition of kidnapping (Model Penal Code, No. 212.1). Following case law in Nigeria, the Supreme Court laid out the elements required for establishing a crime of kidnapping in the case of Okashetu v.
The most recent case, and example of group kidnapping operation is the kidnapped of 110 schoolgirls from Dapchi in Yobe State, Nigeria, in 2018, by the dreaded Boko Haram terrorist group (see, Okolie-Osemene & Okolie-Osemene, Citation 2019). Unlike the single kidnapping where there may be element of deception, in the case of group kidnapping ...
The study's findings show a moderate relationship between kidnapping for ransom and victims' psycho-spiritual well-being, with Pearson's correlation coefficient of two variables of r=.377 ...
Governments continue to be concerned about kidnapping as a source of terrorist finance. A host of international commitments, underpinned by UN Security Council Resolutions and domestic laws, forbids the commercial resolution of terrorist-related kidnappings and prevents governments from making concessions to terrorists.
The 2020 report of the Global Terrorism Index ranks Nigeria third among 163 countries on the scale of key global security trends and patterns of terrorism. This paper examines the impact of terrorism, banditry and kidnapping on human security in Nigeria. The paper posits that Nigeria continues to experience increasing insecurity and violence through frequent attacks by terrorist, bandits and ...
Incidences of insecurity arising from incessant cases of kidnapping, banditry, insurgences, and the attendant consequences such as ransom demand and taking, severe injuries, destructions, and killings of victims in Nigeria appear to have taken a worrisome dimension that even none victims and keen observers are now apprehensive. This paper examined the phenomena of kidnaping, banditry, security ...
Kidnapping has prevailed in spite of measures put in place by the government. The Nigerian police's anti-kidnapping squad, introduced in the 2000s, has endeavored to stem the menace.
Kidnapping is a worldwide and historic phenomenon, with various populations at risk (e.g. infants, children, women, migrants, young adults in honor communities, LGBTQ, actively deployed troops in ...
State weakness has helped violent non-state actors worldwide, especially terrorists and criminals who continue to threaten statehood. When the United Nations bolstered its fight against terrorism in 2001 by adopting resolution 1373 in the immediate aftermath of the 9/11 terrorist attacks on US soil, al-Qa'ida numbered around 300 mujahedeen in Afghanistan with the support of the Taliban.
Nigeria is faced with an unprecedented wave of different but overlapping security crises - from kidnapping to extremist insurgencies - almost every corner of the country has been hit by violence ...
According to court documents, Dayton Peterson, 24, of Louisville, was sentenced on October 22, 2024, to 30 years in prison, followed by 5 years of supervised release, for kidnapping, impersonator making arrest or search, robbery, using or carrying a firearm during and in relation to a crime of violence, conspiracy to possess with intent to ...