Get-AzPolicyAssignment
In this Azure PowerShell article, we will discuss the syntax and usage of the Get-AzPolicyAssignment PowerShell cmdlet and along with that, we will also discuss the use of the Get-AzPolicyAssignment PowerShell command with an example.
Table of Contents

Get-AzPolicyAssignment – Video Tutorial
Get-AzPolicyAssignment is a very good Azure PowerShell command to retrieve the policy assignments.
Below is the syntax of the Get-AzPolicyAssignment PowerShell command.
Now, let’s discuss a few examples of how to use the Get-AzPolicyAssignment PowerShell command with a few examples.
Below PowerShell command can help you to retrieve the lists of policy assignments.
After running the above command, I got the below output.
You can see the same output here as below

Check out a video tutorial on this command.
In this Azure article, we discussed, the syntax and usage of the Get-AzPolicyAssignment PowerShell cmdlet and along with certain examples of how to use this command.

I am Rajkishore, and I have over 14 years of experience in Microsoft Azure and AWS, with good experience in Azure Functions, Storage, Virtual Machine, Logic Apps, PowerShell Commands, CLI Commands, Machine Learning, AI, Azure Cognitive Services, DevOps, etc. Not only that, I do have good real-time experience in designing and developing cloud-native data integrations on Azure or AWS, etc. I hope you will learn from these practical Azure tutorials. Read more .
How to Get All Azure Policy Assignments of a Specific Category?
- 2-minute read
I’ve been in quite a pickle recently: I needed to find out how many and what Azure Policy definitions from Guest Configuration category are currently assigned to my subscription, so that I could understand if any of those policies are applicable to Azure Arc-enabled servers that are residing in the same subscription. Why?
Well, because Guest Configuration is a billed functionality, when it comes to Azure Arc. In this case it’s good to get an overview if any policies related to the billed functionality are enabled in order to further evaluate if you want to use this functionality or not (and therefore disable it to avoid undesired billing). You may also have different use cases for why you would want to retrieve the same information from Azure Policy🧐
After some time investigating I discovered that it’s quite a challenging to retrieve this kind of information in Azure portal: you can see the category of every single Azure Policy definition in the list of all definitions, but you can’t use policy category as a filter on assignments or compliance page. There’s no single-line solution in Azure CLI either.
That’s when I got lazy once again and leaned back to my dear friend PowerShell to achieve this😅 Following PowerShell script retrieves all policy definition assignments coming both from regular policy assignments and policy initiative assignments. If any of the assigned policies belong to the requested category, like Guest Configuration in my case, information about those policies will be provided as output upon script execution.
You can find the PowerShell script in my GitHub repo: Get-Policy-Assignments-In-Category.ps1
The output will look something like the screenshot below:
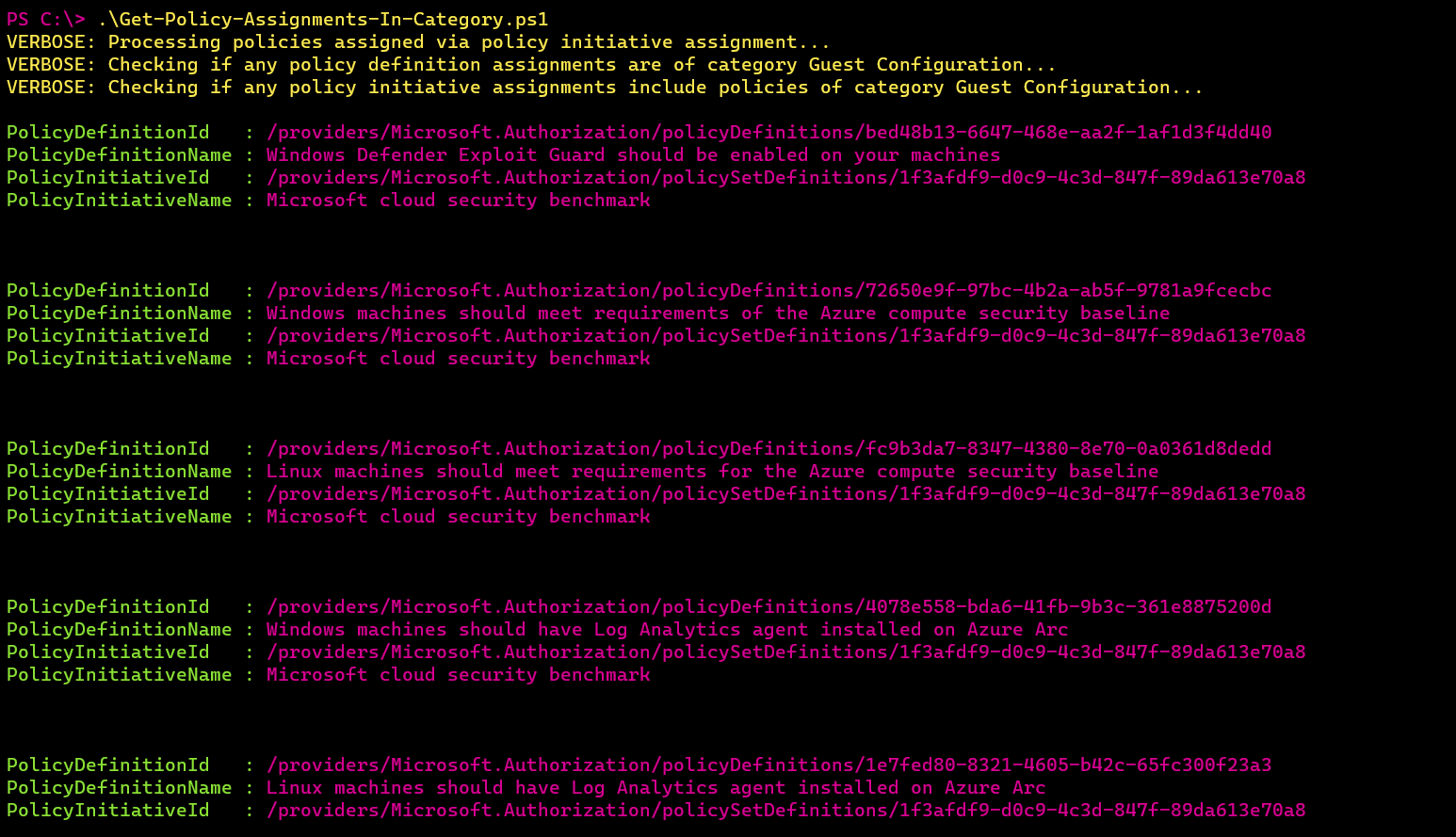
Already tested it out? Let me know how it went!🤗
That’s it from me this time, thanks for checking in!💖
If this article was helpful, I’d love to hear about it! You can reach out to me on LinkedIn, X, GitHub or by using the contact form on this page.😺
Stay secure, stay safe.
Till we connect again!😻

DEV Community
Posted on Oct 31, 2022
Bicep and Azure Policy: Manage Policy and Initiative Assignment
This is the third post about Azure Policy. This time, the post will focus on policy assignments with Azure Bicep and PowerShell. Policy assignment enforces a policy and a policy set at a given scope, management group, or subscription. This is where policies are applied to target resources.
A policy Assignment object has several properties:
- A name (limited to 24 characters at the management group scope, 64 characters for other scopes)
- A location, the Azure to store the operation metadata
- A display name, limited to 128 characters
- An identity object
- A description
- The enforcement mode, either default (enforced) or DonotEnforce
- A non-compliance object. The message will be displayed when resources are not compliant with the policy.
- A not scope array, to not apply the assignment at some management group or subscriptions
- A parameters object, to apply parameters for the policy for the assignment
- The Policy definition ID, resource ID of the policy definition, or the policy set
In Bicep language
The deployment of this bicep file could be done by the New-AzManagementGroupDeployment cmdlet. But like custom policy definitions and policy sets, you will certainly be asked to not assign only one policy. How can you manage several policy assignments in one place? This is the same problem we had with deploying policies. But even if a policy assignment can be seen as a JSON document, the amount of information needed to assign a policy is limited. Instead of using one JSON file per assignment, we can create a single JSON document with all assignments, but we need to take care of the scope.
the bicep file:
This Bicep file will deploy a policy assignment. As the deployment will be made via PowerShell, we need to convert the value of the parameters and the nonComplianceMessage properties from string to JSON with the JSON function in Bicep.
All the parameters needed for the deployment are stored in a JSON document.
There is one policy to assign but two assignments in the JSON document. It’s to illustrate the power of parameters in the assignment process. You can assign the same policy, multiple times, even at the same scope, as long as the name changes and the parameters are different.
Each object in the JSON document will serve to deploy the assignment via a PowerShell script.
The script read the content of the JSON document and for each object, it extracts the variable needed to deploy the bicep file. But there is a difficulty, the bicep nonComplianceMessages require a JSON array, but most of the time there will be only one message or no message at all (multiple messages are only used for policy set). And if there is only one message (or none) you will not end up with a JSON array, but a simple JSON object, so a modification is needed.
To deploy, simply run the deployAssignment.ps1 from its folder. You can add the "location" parameter to adjust the azure region for your needs.
You can find the related PwSh/Bicep code here
Top comments (0)
Templates let you quickly answer FAQs or store snippets for re-use.
Are you sure you want to hide this comment? It will become hidden in your post, but will still be visible via the comment's permalink .
Hide child comments as well
For further actions, you may consider blocking this person and/or reporting abuse

PROM- Architecture
anhphan - Apr 22

From $r$ to $Q^*$: Your Language Model is Secretly a Q-Function
Mike Young - Apr 21
Lossless Acceleration of Large Language Model via Adaptive N-gram Parallel Decoding

Creating a Stunning Responsive WordPress Landing Page with Elementor: A Step-by-Step Guide
sajjad hussain - Apr 22

We're a place where coders share, stay up-to-date and grow their careers.
John Folberth
Resources and posts for those figuring out DevOps in Azure
- Professional
Testing Azure Policy via PowerShell

Azure Policy is a powerful tool that can be used as effective guardrails to safeguard an environment. In addition it can be leverage to auto remediate anything required a developer may forget about. For some examples on Azure Policy check out my posts “ Creating and Deploying Azure Policy via Terraform ” or “Dynamically Adding Terraform Policy Assignments…Reusing Infrastructure as code “. Specifically, this post is related to “ Terraform, Azure Policy, and Datas OH MY! “
Problem Statement
In a nutshell this policy ensures Azure Resource Groups require a delete-by tag and this delete-by tag must be within a certain date range. The follow up to this is a PowerShell script hooked up to an Azure Automation account which will delete resource groups who have past expiration. The dilemma is how can we seed test data to validate the script when Azure Policy will deny it? We could just delete the policy assignment do our testing and re assign it; however, that is a manual process and leaves open the room for error that the policy is never assigned. So that leaves us with the problem statement: How to seed test data that violates a policy?
Requirements
To run this the following Az Modules will need to be installed:
- Az.Resources
Breaking down this problem we can outline the steps we should take:
Remove the Policy Assignment
- Create the Resources that would violate the policy
- Re add the Policy Assignment
To do this successfully we should read in the existing policy assignment and store that information in our script so we reapply the policy with the same information that was originally available.
Store Policy Assignment Information
To store the policy assignment information, we will use the Get-AzPolicyAssignment PowerShell module:
The $PolicyParameterObject is a hashtable of parameters the Policy Assignment expects.
Can see we look up the Policy Assignment by name and store that as well as the Policy Definition ID as this will be used later.
Removing the Policy Assignment is quite easily actually. We just use the Remove-AzPolicyAssignment command.
Create the Resources that Violate the Policy
For this specific example the resources being created will be Resource Groups who have a delete-by tag value which is in the past. To accomplish this and provide a more realistic scenario the Get-Random command will be used.
The random number will be different for each resource group being created and will be used with the .addDays() function to subtract days from the $dateRan which is the starting point.
Re Add the Policy Assignment
Lastly, we need to re add the policy assignment to ensure this doesn’t drift.
This is being done with the New-AzPolicyAssignmnt function and passing in the assignment parameters as a hash table and the necessary information which was scraped from the original Policy Assignment that was saved off.
Sometimes when testing automation or the cleaning up of resources automatically it is important to create an automated way to seed test data. This will help improve consistency and help minimize the potential for human error.
Source Code
Leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- DevOps Lifecycle
- DevOps Roadmap
- Docker Tutorial
- Kubernetes Tutorials
- Amazon Web Services [AWS] Tutorial
- AZURE Tutorials
- GCP Tutorials
- Docker Cheat sheet
- Kubernetes cheat sheet
- AWS interview questions
- Docker Interview Questions
- Ansible Interview Questions
- Jenkins Interview Questions
- Microsoft Azure Tutorial
Introduction
- Introduction to Microsoft Azure | A cloud computing service
- Microsoft Azure - High-Level Overview of Architecture Center
- How Microsoft Azure Works?
- Microsoft Azure - Using the Azure Quickstart Centre
- Microsoft Azure - Getting Free Trial with Azure Quickstart Center
- Microsoft Azure - Storage Accounts
- Microsoft Azure - Storage in Azure Cloud Shell
- Microsoft Azure - Mounting Azure Storage in a Container App
- Microsoft Azure - Concept of Blob Versioning in Azure Storage
- Microsoft Azure - Using Blob Versioning
- Microsoft Azure - Automatically Manage Azure Blobs Lifecycles
- Microsoft Azure - Add Storage Blob Owner Role Assignment For Azure AD User
- Microsoft Azure- Disk Storage in Microsoft Azure
- How to Setup a Azure Storage Account For Data Archive?
- Microsoft Azure - Hosting a Static Website with Azure Storage
- Microsoft Azure - Azure Managed Disk State Details using PowerShell
- Microsoft Azure - Mount Azure Storage in Container App In App Service
- Microsoft Azure - Delete Orphaned Disks using PowerShell Script
- What Are Azure Data Security Features?
- Microsoft Azure - Virtual Network
- Microsoft Azure - Find Orphaned Network Interface Cards(NICs)
- What is Microsoft Azure Network Watcher?
- Microsoft Azure - Finding the Right Load Balancing Service
- Microsoft Azure - Application Security with Azure Active Directory
- Microsoft Azure - Find and Delete Orphaned Public IP addresses in Azure Portal
- Microsoft Azure - Protecting Hybrid Cloud Workloads using Azure Defender
Compute Virtual Machines
- What are Azure Virtual Machines?
- Microsoft Azure - Introduction to Azure VM Extension
- Microsoft Azure - Simpler Management of Virtual Machine
- Microsoft Azure - Managing Multiple Virtual Machines
- Create Free Windows Virtual Machine in Azure
- Microsoft Azure - Pre-built Azure VMs
- Microsoft Azure - Archive Azure VM to Azure Storage Account
- How to Reset a Azure VM Password?
- Microsoft Azure - Improvements in Linux Virtual Machine
- Microsoft Azure - Connecting Linux VM using SSH
- Microsoft Azure - Connecting Windows VM using RDP
- Microsoft Azure - Azure VM Disk Space in Percentage using Azure KQL
- Microsoft Azure - Creating an OS Disk Snapshot of a Azure VM
- Microsoft Azure - Reduce Cost Using Virtual Machine
- Microsoft Azure - Resize a Azure Virtual Machine for Windows or Linux Servers
- Microsoft Azure - Resizing Virtual Machine Using PowerShell Script
- Microsoft Azure - Configuring Backup For Azure App Services
- Microsoft Azure - Getting Started With Azure Backup For Protecting an IaaS VM
- Defense in Depth Strategy in Microsoft Azure
- Microsoft Azure - Enable IIS Logs for Monitoring
- Microsoft Azure - Using Azure Monitor Workbooks
- Microsoft Azure - Enable Azure Monitor VM Insights Agent For Azure VM
- Microsoft Azure - Introduction to Spot Virtual Machines
- Azure Virtual Machine for Machine Learning
- Microsoft Azure - Tracking Memory Utilization of Azure VM using KQL Log Query
- Microsoft Azure - Track CPU Utilization of a Azure Virtual Machines using KQL Log Query
- Microsoft Azure - Heartbeat KQL Log Monitoring Query
- Microsoft Azure - Firewall Network Flow Logs with TimeGenerated using KQL
- Microsoft Azure - Setting up a Auto Shutdown For Azure Virtual Machine
- Microsoft Azure - Get CPU Utilization Data of a Azure VM in Azure Portal
- Microsoft Azure - CPU and Memory Utilization of Azure VMs in a Single Table Chart
- Microsoft Azure - Retrieve Azure Virtual Machine Admin User Name
- Microsoft Azure - Enable Boot Diagnostics For a VM in Azure
- Microsoft Azure - Disable Boot Diagnostics For a VM in Azure
- Microsoft Azure - Setup Auto Startup and Shutdown of an Azure VM
- 7 Tips to Reduce Cost with Azure Virtual Machines
- Microsoft Azure - Assigning Tags to a Azure VM
- Microsoft Azure - Check Virtual Machine Creation Date and Time
- Microsoft Azure - VMs Patch Update Summary by Installation Status
- Microsoft Azure - Graph Query to Get Properties of Azure VM Resource
- Microsoft Azure - Check for Apache Log4J Vulnerability in Azure VMs
- Microsoft Azure - Get Azure VM Properties using Azure PowerShell
- Microsoft Azure - Manage Azure VMs using Azure PowerShell Commands
- Microsoft Azure - Check Status of Azure VM using Azure PowerShell
- Microsoft Azure - Azure CLI Commands to Manage Azure VMs
- Microsoft Azure - KQL Query to Get the VM Computer Properties
- Microsoft Azure - Create SHH Key to Manage Azure Linux VMs
- Microsoft Azure - VM CPU Utilisation Across Subscriptions with Range
- Microsoft Azure - Common Virtual Machine Issues
- Microsoft Azure - Manage Virtual Machine via Azure Mobile App
- Microsoft Azure - Increase Processors & Memory Size of Windows Virtual Machine
- Microsoft Azure - Troubleshoot Azure VM Inbound and Outbound Connections
- Microsoft Azure - Deletion of Snapshots using PowerShell Script
- Microsoft Azure - Connect to a Storage Account using Private Link
- Microsoft Azure - Accessing Virtual Machines using Bastion
- Microsoft Azure - Getting VMComputer Records Properties
Compute Functions
- Microsoft Azure - Monitoring Azure Functions
- Microsoft Azure - Creating Azure Functions From VS Code
- Microsoft Azure - Debugging Azure Functions using VS Code
- Microsoft Azure - Deploy Azure Functions using VS Code
- Microsoft Azure - Renaming an Azure Functions
- Microsoft Azure - Simple way to Create a Function App
- Microsoft Azure - New Features in Azure Functions
- Microsoft Azure - Using VS Code for Azure Function Projects
- Microsoft Azure - Custom Handlers for Azure Functions
Compute Monitoring
- Microsoft Azure - Enable Windows Performance Counters in Azure for Monitoring
- Microsoft Azure - Enable Linux Performance Counters in Azure for Monitoring
- Microsoft Azure - Enable Windows Event Logs in Azure for Monitoring
- Microsoft Azure - Enable Linux System Logs in Azure for Monitoring
Azure Services
- Microsoft Azure - Introduction to Quickstart Center
- Microsoft Azure- Add Extensions in Azure App Service
- Microsoft Azure - Working with App Service Domains
- Microsoft Azure - Create Web Apps in Azure
- Microsoft Azure - Creating an App Service Plan
- Microsoft Azure - Creating a Logic App of Consumption Type
- Microsoft Azure - Azure App Service Managed Certificates
- Microsoft Azure - Deploy a Static Web App
- Microsoft Azure - Removing Unused Services From Azure
- What is Microsoft Azure Functions?
- Microsoft Azure - RDP to Azure Virtual Machines using Azure Bastion
- Microsoft Azure - Getting started with Azure Static Web Apps
- Microsoft Azure - Cloning Web Apps using Azure App Services
- Microsoft Azure - Enable Local Cache on Azure App
- Microsoft Azure - Exploring the Azure Mobile App Home Screen
- Microsoft Azure - Container Registration for App Deployment
- Microsoft Azure - Roll Back Versions of Azure Logic Apps
- Microsoft Azure - Modifying API Connections With Logic Apps
- Microsoft Azure - Azure Media Service
- Microsoft Azure - Using Github Action in Azure App Service
- Microsoft Azure - Using JSON with Azure Logic Apps
- Microsoft Azure - Configuring Log Analytics Data Retention
- Microsoft Azure - Creating JSON Snippet For Policy Initiative Creation using CSV File
- Microsoft Azure - Working with Files in Azure App Service
- Microsoft Azure - Using Power Apps in VS Code
- Microsoft Azure - Preventing Changes to Resources in Azure App Services
- Microsoft Azure- Writing Queries and Creating Dashboards using Azure Resource Graph
- Microsoft Azure - Enabling Resource Providers for Azure Subscription
- Microsoft Azure - Find Orphaned Disks
- Microsoft Azure - Handling Orphaned NSGs
- Microsoft Azure - Configuring an Alert Rule with Azure Monitor
- Microsoft Azure - Count of Azure Resources using Resource Graph Query
- Microsoft Azure - Create Alert For Conditional Access Policy Changes
- Microsoft Azure - Create Pie Charts For Orphaned Resources using KQL
- Microsoft Azure - Patch Management Update Summary Status
- Microsoft Azure - Check Resource Owner in Azure using KQL
- Microsoft Azure - Check Enabled and Disabled Diagnostics for Azure Resources
- Microsoft Azure - Azure Firewall Flow Logs From Select Source IP
- Microsoft Azure - Resource Tagging and Best Practices
- Microsoft Azure - Using the Azure Activity Log
- Microsoft Azure - Scaling Inventory Resources
- Microsoft Azure - Moving Resources Among Groups
Cognitive Services
- Build a Text Translator Web App using Flask and Azure Cognitive Services
- Microsoft Azure - Introduction to Metric Advisor
- Microsoft Azure - Cognitive Service Text Analytics in Web App Containers
- Microsoft Azure - Opinion Mining with Azure Cognitive Services
- Microsoft Azure - Customizing Charts on Azure Dashboard
- Microsoft Azure - Customizing Azure Dashboard Tiles
- Microsoft Azure - Auto Refreshing Dashboards
- Microsoft Azure - Pinning to Portal Dashboard
- Microsoft Azure - Database Availability and Consistency For Azure SQL
- Microsoft Azure SQL Database
- Microsoft Azure - Security in Azure SQL
- Microsoft Azure - Identifying & Accessing Management for Azure SQL
- Microsoft Azure - Security Capabilities and Tasks of Azure SQL
- Microsoft Azure - Configure Azure SQL with Azure CLI
- Microsoft Azure - Configure Auditing for Azure SQL Database
- Microsoft Azure - Azure SQL Managed Instance Deployment Options
- Microsoft Azure - Azure SQL Managed Instance
- Microsoft Azure - PaaS vs. IaaS in Azure SQL
- Microsoft Azure - Management Interfaces for Azure SQL
- Microsoft Azure - Opportunities in the Cloud with Azure SQL
- Microsoft Azure - Create Azure SQL Database
- Microsoft Azure - Introduction to Azure Database For MySQL
- Microsoft SQL Server Active Directory Authentication on Linux Machine
- Introduction to Azure Cosmos DB
- Microsoft Azure - Notebooks in Cosmos DB
- Microsoft Azure - Using C# in CosmoDB
- Microsoft Azure - Choosing a Partition Key in Cosmos DB
- Microsoft Azure - Introduction to Azure Data Factory
- Microsoft Azure - Migrating From MySQL to Cloud
- Microsoft Azure - Advanced Threat Protection for Azure SQL Database
- Microsoft Azure - Using Flexible Server in Azure Database for PostrgeSQL
- Microsoft Azure - Accelerating Cloud Migration & Datacenter Discovery
- Azure DevOps: An Introduction, Services, Projects, Benefits, Drawbacks
- Microsoft Azure - Availability Zones For Kubernetes Cluster
- Microsoft Azure - Zone Redundancy and SLA of Azure SQL
- Microsoft Azure - Create Project in Azure Devops using Basic Process
- Microsoft Azure – Create Project in Azure Devops using Agile Process
- Microsoft Azure - Starting & Stopping a Azure Kubernetes Service Cluster
- Microsoft Azure - Introduction to Azure Kung Fu Toolkit
- Microsoft Azure - Introduction to Kubernetes Diagnostics
- How to Create Backlog and Sprint in Agile Process?
- Microsoft Azure - Running an App inside a Docker Container Image
- How to Push a Container Image to a Docker Repository?
- Microsoft Azure - Manage and Export Azure Policies with GitHub Integration
- Microsoft Azure Arc Enabled Kubernetes
- Microsoft Azure - Introduction to Azure Arc
- Microsoft Azure - Deploying Web Applications Using GitHub Actions
- Microsoft Azure - Messaging with Azure Web PubSub
- Microsoft Azure - Testing in Production Sites Feature using PowerShell
- Microsoft Azure - Build and Deploy App with Azure SDK For Java
Machine Learning and IoT
- Microsoft Azure - Introduction to Azure Sentinel
- Machine Learning with Microsoft Azure ML Studio Without Code
- What is the Best Azure IoT Service for You?
- Microsoft Azure - Key IoT Products
- Microsoft Azure - Using Azure Form Recognizer
Miscellaneous
- Microsoft Azure - Productivity Tips For Azure portal
- Microsoft Azure - Get Azure Policies Definitions and Policy Initiatives Definitions
- Microsoft Azure - Create a Custom Policy Initiative in Azure
- Technical Overview of Microsoft Mesh
- Microsoft Azure - Working with Azure Health Bot
- Microsoft Azure - Introduction to Azure Digital Twins
- Microsoft Azure - Working with Themes in Azure
- Microsoft Azure - Understanding Azure KeyBoard Shortcuts
- Microsoft Azure - Using Table Parameter in Azure CLI
- Microsoft Azure - Add Azure Cloud Shell to VS Code
- Microsoft Azure - Accessing Cloud Shell from Microsoft Docs
- Microsoft Azure - Azure App Servers Routing using PowerShell
- Microsoft Azure - Introduction to SMART
- Microsoft Azure - Lift & Shift Approach for Infrastructure Migration
- Microsoft Azure - Configure Diagnostic Settings For Azure Subscription
- Microsoft Azure - Checking your Access on Azure Subscription
- Microsoft Azure - Enabling Logs for Troubleshooting the Azure Firewall Rules
- Microsoft Azure - Rebooting an Application Gateway
- Microsoft Azure - PAL Tagging in Azure
- Microsoft Azure - Using Cost Management in Azure Portal
- Microsoft Azure - View Delegated Roles in Azure Lighthouse
- Microsoft Azure - Using the Global Search
- Microsoft Azure - Quick Copy & Paste on Portal
- Microsoft Azure - Alerts as Notifications on Phone
- Microsoft Azure - Developing ARM Templates using Azure Bicep
Microsoft Azure – Get Azure Policies Definitions and Policy Initiatives Definitions
In this article, we will be using some Azure PowerShell Commands either in Azure Cloud Shell or in Azure PowerShell ISE in Admin mode to get the details and properties about the Azure Policies. Let’s get started.
1. Use the Get-AzPolicyStateSummary PowerShell command to get the details of the azure policy compliance status of Non-Compliant Resources and Non-Compliant Policies.

2. Use the Get-AzPolicySetDefinition PowerShell command to get Azure Policy Initiative Definitions
The command returns the properties of all the Azure Policy Initiative Definitions.

3. Use (Get-AzPolicySetDefinition).count PowerShell command to get the count of Azure Policy Initiative Definitions.
The command returns the count of the total number of Azure Policy Initiative Definitions.

4. Use Get-AzPolicyDefinition PowerShell command to get the Azure Policy Definitions list and properties.
The command returns the properties of all the Azure Policy Definitions.

5. Use (Get-AzPolicyDefinition).count PowerShell command to get the count of Azure Policy Definitions.
The command returns the count of the total number of Azure Policy Definitions.

Please Login to comment...
Similar reads.

- Cloud-Computing
- Geeks-Premier-League-2022
- Geeks Premier League
- Microsoft Azure
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Subscribe for Practical 365 updates
Please turn off your ad blocker and refresh the page to subscribe.
You may withdraw your consent at any time. Please visit our Privacy Statement for additional information
Blog / Teams
Creating a complete teams policy assignment report.

Table of Contents
Group-Based Policy Assignments Not Covered in the Previous Version
In November 2021, I wrote an article explaining how to generate an HTML report about the Teams policies assigned to user accounts . Life was simpler then and group-based policy assignments were relatively new. Showing its age, the ill-fated and never-successful Teams advanced communications license was the requirement required to build and assign custom policy packages to user accounts. Now Teams Premium is the necessary license to support custom policy packages. However, organizations can assign the standard policy packages with the base Teams license.
This explanation is a long-winded way of saying that the report I wrote about in November 2021 only reports direct policy assignments. Any policies assigned to users through group membership are blissfully ignored, a fact highlighted in a LinkedIn discussion that invoked my name.
This is a good example of the risk inherent in sample code: technical developments can render the example less valuable over time. It’s irritating for readers to find that an example that seems to meet their needs doesn’t work. I can assure you that it’s equally irksome for those who create example code when they discover that time and technology erodes the value of their efforts.
Coping with Three Types of Teams Policy Assignments
Something had to be done. Group-based management of objects like policies and licenses is an efficient way to ensure that user accounts with the same role receive a consistent configuration. Fixing the report script would also address other obvious flaws, like using the Exchange Online PowerShell module to get the organization name. I fired up Visual Studio Code and spent a couple of hours on a Saturday afternoon to figure out the best way of reporting the three kinds of policy assignments that exist in Teams:
- Default : No other type of policy assignment exists for an account, so user activity is governed by the default policy.
- Direct : An administrator assigns a specific policy to an account
- Group : A user inherits a policy from a policy package assigned to their account.
Figure 1 shows some of the policies assigned to a Teams user. We can see that 24 different policies are available and that two of the five visible policies are direct assignments while the other three are default assignments.
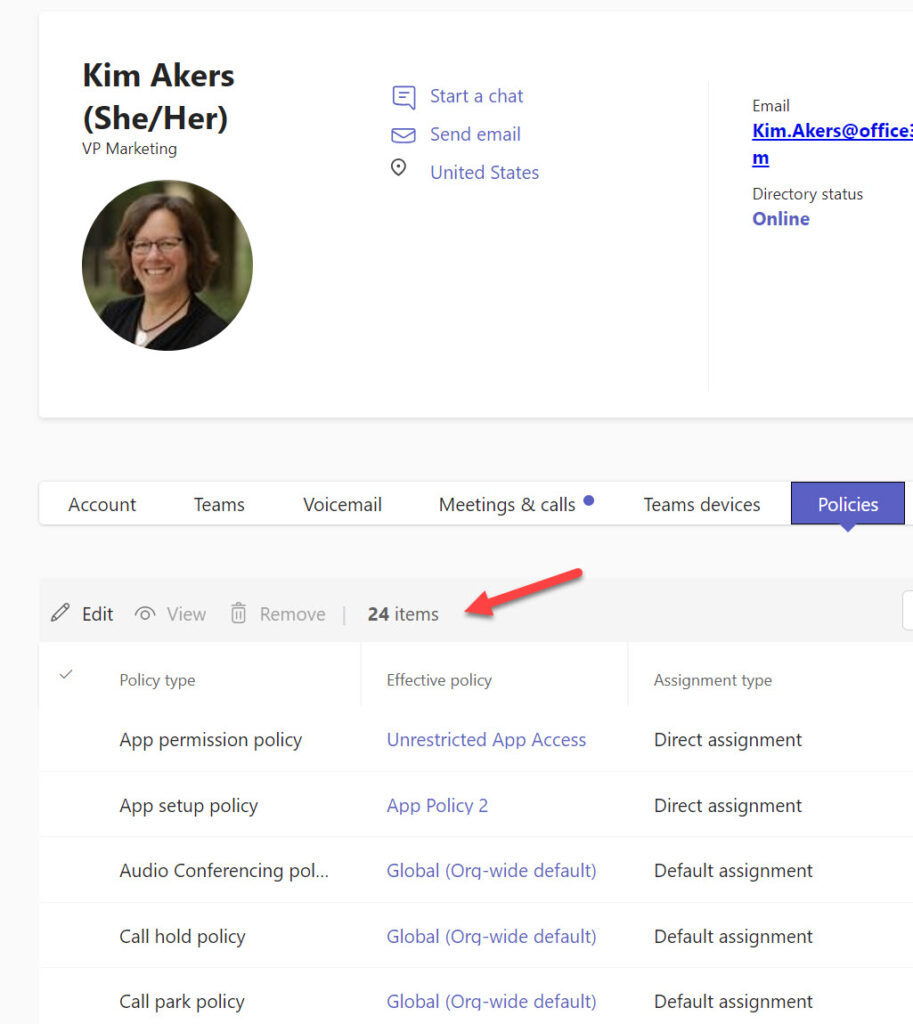
Reporting Teams Policy Assignments
The Get-CsOnlineUser cmdlet retrieves policy assignments along with a lot of other information about Teams users. The information returned by the cmdlet is sufficient to deal with default and direct policy assignments. If the property for a policy is blank, it means that the default policy is used. If the name of a policy is in the property, it is a direct assignment. In the extract shown below, there are three direct assignments and five instances where the default policy is used:
Interestingly, the Get-CsOnlineUser cmdlet returns 44 Teams policies. Some of the policies that don’t show up in the Teams admin center are disused. Others might be used in the future.
The script described in the original article reported default and direct assignments, so generating the report is simply a matter of running down through each policy to check if a direct assignment exists and if not, report it as a default assignment. A different approach is needed to deal with group-based assignments. Take this code section that reports the meeting policy for a user:
First, the script sets the variable that stores the name of the assigned policy to a default value. Next, it checks if the Get-CsOnlineUser cmdlet returned a policy name. If so, the meeting policy is a direct assignment, and the script doesn’t need to be probed further. The next step runs the Get-CsUserPolicyAssignment cmdlet to check if any assignments exist. The cmdlet returns details of group and direct assignments. A Switch command checks the first (most recent) assignment and updates the variable storing the name of the assigned policy with the policy and a prefix. The direct assignment check might be unnecessary because Get-CsOnlineUser returns this information, but I included it just in case.
If it’s a group assignment, the script calls a function to run the Get-MgGroup cmdlet (from the Microsoft Graph PowerShell SDK) to return the display name of the group used for the assignment. When processing policy assignments for all users, it’s likely that the same groups will be met many times. It would be wasteful to call Get-MgGroup each time, so the function uses a hash table to hold details of the groups it has already processed and only calls Get-MgGroup if the group hasn’t been seen before.
Figure 1 shows an example of the report output.
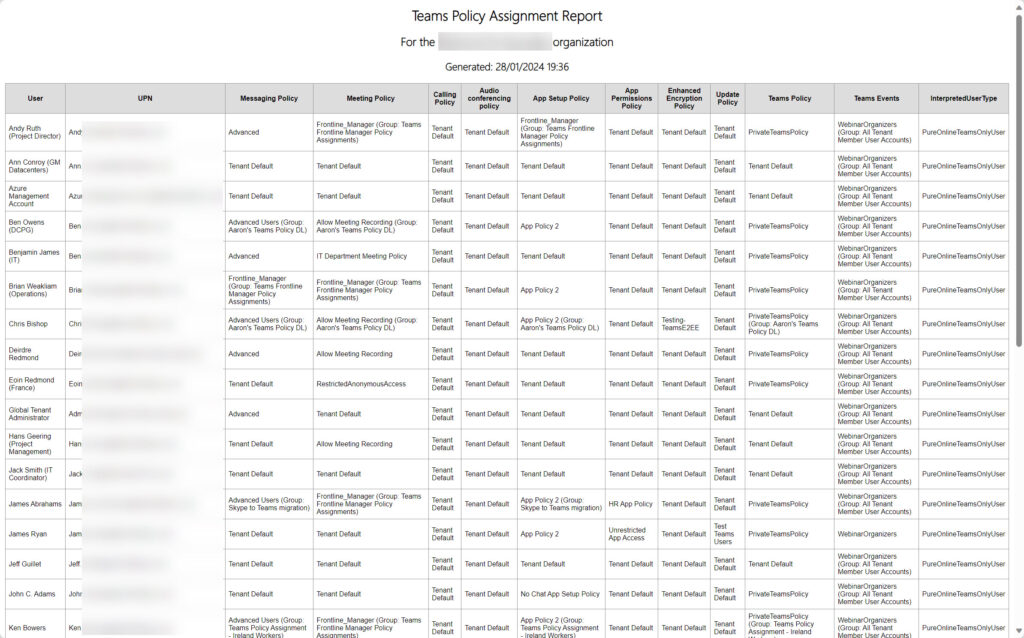
The folks who reported the problem have tested the updated script ( available from GitHub ) and say that it works. At least, it addresses the issue that they had and provides a better overview of the policy assignments for Teams users within a tenant. No doubt the code can be improved, but it’s PowerShell so that’s easily done.
Effort Required to Get the Right Results
The downside is that the amended script takes longer to run because of all the extra processing. The upside is that the report generated by the script is accurate because it includes group-based policy assignments. This goes to prove (once again) that achieving the right result takes effort. In this case, the effort filled a couple of hours on a wet Saturday and delivered a practical solution to a problem. That’s always nice.
Preparing for a Transition from Active Directory to Azure AD

About the Author

Tony Redmond
Leave a reply cancel reply, latest articles.

Practical Protection: Breaches, Exposure, and You
In this edition of Practical Protection, Paul Robichaux dives into 5 steps you can take to protect yourself, and potentially your organization, from future breaches.

Deploy Cloud-Based Windows LAPS to Windows Endpoints
Microsoft recently released a revamped version of LAPS that can store the local admin password in Entra ID to work with cloud-managed endpoints. In this blog, we dive into deploying LAPS and how to use it to further enhance the security of Windows endpoints.
PowerShell Serialization Payload Signing in Exchange Server
In this article, Jaap Wesselius discusses PowerShell serialization, what PowerShell serialization payload signing is, why this is important, and how to manage it.
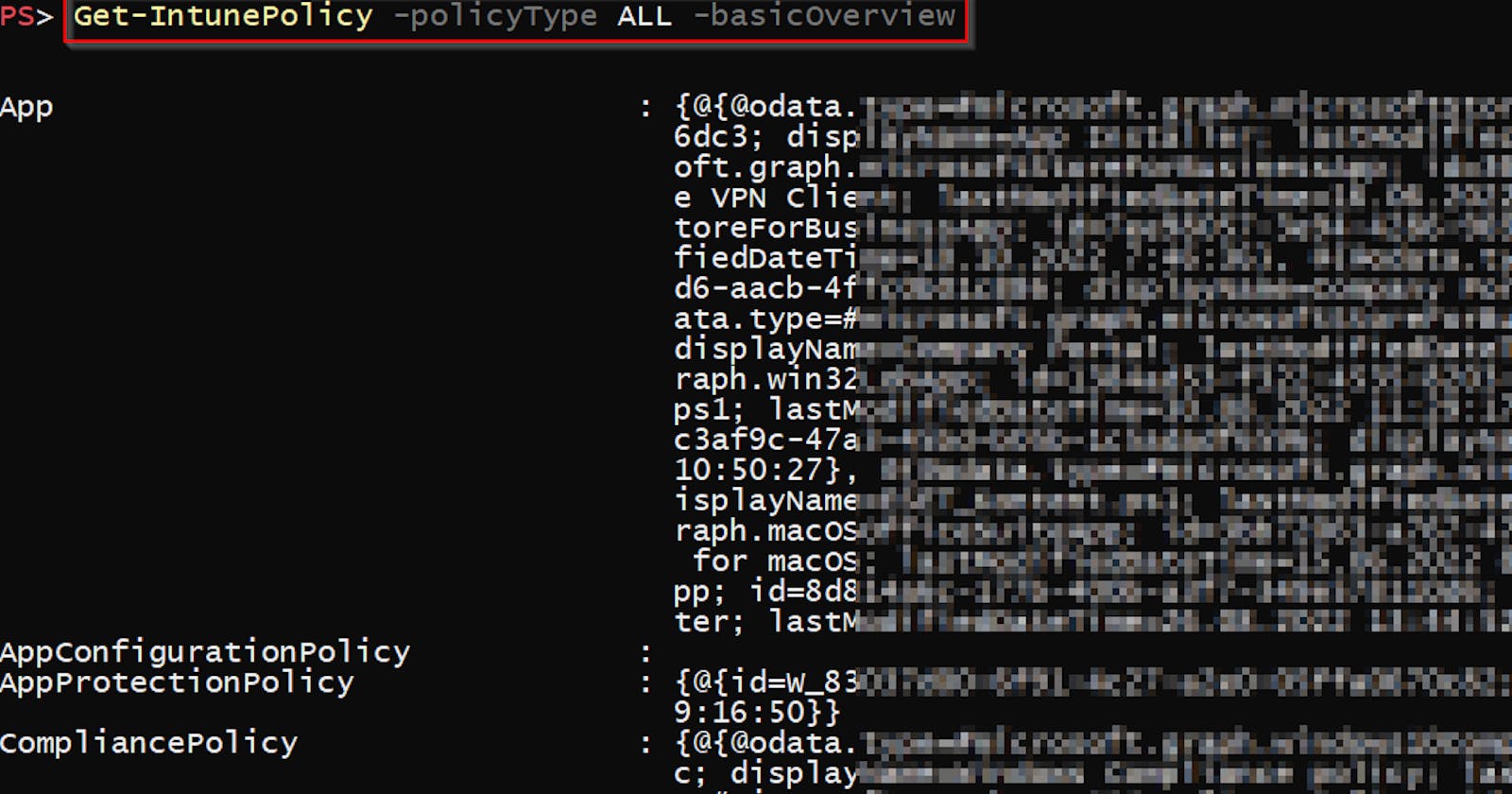

Get all Intune policies using PowerShell and Graph API

Table of contents
How to use the get-intunepolicy function, what kind of policies this function returns, how did i find the correct graph api urls.
For my new PowerShell function Search-IntuneAccountPolicyAssignment (for searching Intune policies assigned to selected account ) I was in need to have a list of all these policies so I can search through them. For this reason, I have created a function Get-IntunePolicy and integrated it into my module IntuneStuff .
To get assignable Intune policies, use the function Get-IntunePolicy from my module IntuneStuff like this 👇 🙂
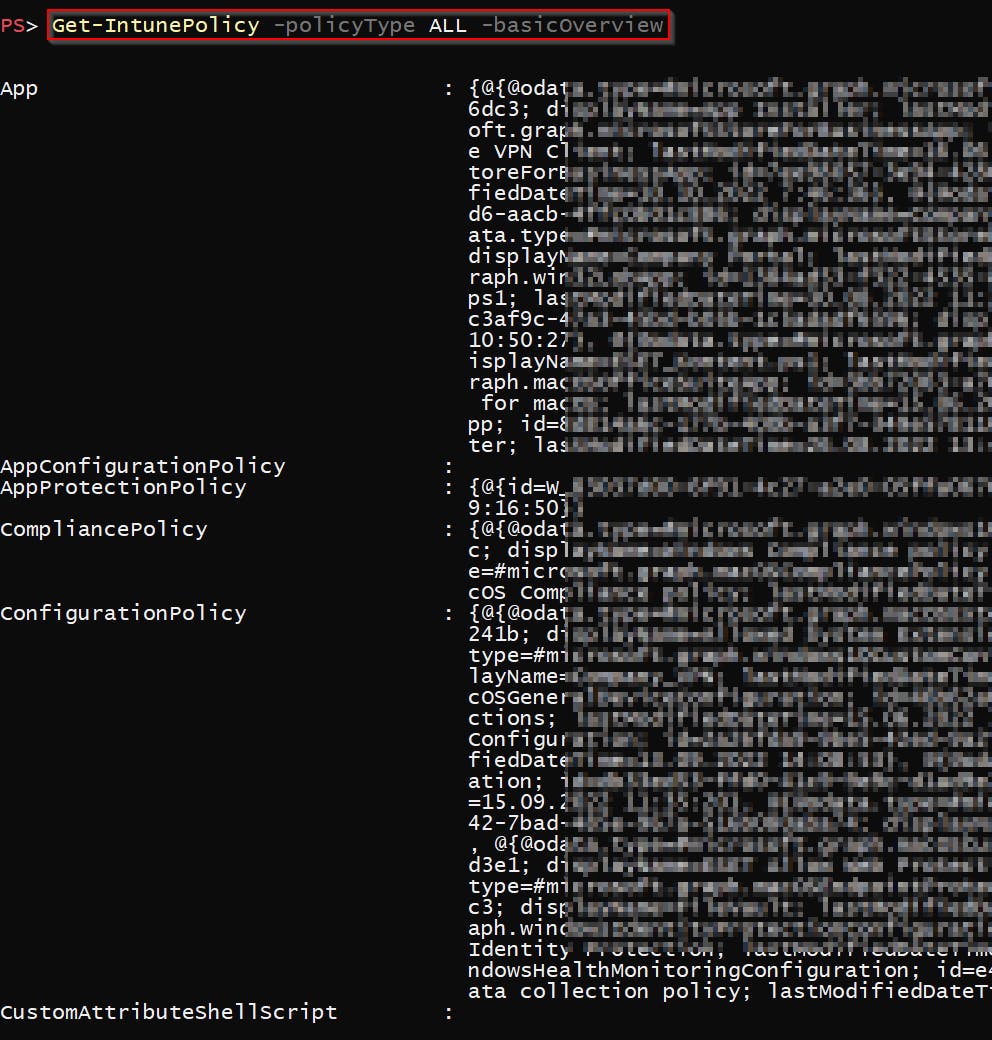
What policies does this function return? As I said, all assignable Intune policies . Right now the list consists of:
- App Configuration policies
- App Protection policies
- Compliance policies
- Administrative Templates
- Settings Catalog
- MacOS Custom Attribute Shell Scripts
- Device Enrollment Configurations
- Device Management PowerShell scripts
- Device Management Shell scripts
- Account Protection policies
- Antivirus policies
- Attack Surface Reduction policies
- Defender policies
- Disk Encryption policies
- Endpoint Detection and Response policies
- Firewall policies
- Security baselines
- iOS App Provisioning profiles
- iOS Update Configurations
- Policy Sets
- Remediation Scripts
- S Mode Supplemental policies
- Windows Autopilot Deployment profiles
- Windows Feature Update profiles
- Windows Quality Update profiles
- Windows Update Rings
So hopefully I haven't forgotten anything.
I hope you will find this function useful. And if you find any bug, please let me know in comments or on my twitter @AndrewZtrhgf .
Did you find this article valuable?
Support Ondrej Sebela by becoming a sponsor. Any amount is appreciated!

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Set-Az Policy Assignment
Modifies a policy assignment.
Description
The Set-AzPolicyAssignment cmdlet modifies a policy assignment. Specify an assignment by ID or by name and scope.
Example 1: Update the display name
The first command gets a resource group named ResourceGroup11 by using the Get-AzResourceGroup cmdlet. The command stores that object in the $ResourceGroup variable. The second command gets the policy assignment named PolicyAssignment by using the Get-AzPolicyAssignment cmdlet. The command stores that object in the $PolicyAssignment variable. The final command updates the display name on the policy assignment on the resource group identified by the ResourceId property of $ResourceGroup.
Example 2: Add a system assigned managed identity to the policy assignment
The first command gets the policy assignment named PolicyAssignment from the current subscription by using the Get-AzPolicyAssignment cmdlet. The command stores that object in the $PolicyAssignment variable. The final command assigns a system assigned managed identity to the policy assignment.
Example 3: Add a user assigned managed identity to the policy assignment
The first command gets the policy assignment named PolicyAssignment from the current subscription by using the Get-AzPolicyAssignment cmdlet. The command stores that object in the $PolicyAssignment variable. The second command gets the user assigned managed identity named UserAssignedIdentity1 by using the Get-AzUserAssignedIdentity cmdlet and stores it in the $UserAssignedIdentity variable. The final command assigns the user assigned managed identity identified by the Id property of $UserAssignedIdentity to the policy assignment.
Example 4: Update policy assignment parameters with new policy parameter object
The first and second commands create an object containing all Azure regions whose names start with "france" or "uk". The second command stores that object in the $AllowedLocations variable. The third command gets the policy assignment named 'PolicyAssignment' The command stores that object in the $PolicyAssignment variable. The final command updates the parameter values on the policy assignment named PolicyAssignment.
Example 5: Update policy assignment parameters with policy parameter file
Create a file called AllowedLocations.json in the local working directory with the following content.
The command updates the policy assignment named 'PolicyAssignment' using the policy parameter file AllowedLocations.json from the local working directory.
Example 6: Update an enforcementMode
The first command gets a resource group named ResourceGroup11 by using the Get-AzResourceGroup cmdlet. The command stores that object in the $ResourceGroup variable. The second command gets the policy assignment named PolicyAssignment by using the Get-AzPolicyAssignment cmdlet. The command stores that object in the $PolicyAssignment variable. The final command updates the enforcementMode property on the policy assignment on the resource group identified by the ResourceId property of $ResourceGroup.
Example 7: Update non-compliance messages
The first command gets the policy assignment named VirtualMachinePolicy by using the Get-AzPolicyAssignment cmdlet and stores it in the $PolicyAssignment variable. The final command updates the non-compliance messages on the policy assignment with a new message that will be displayed if a resource is denied by the policy.
-ApiVersion
Specifies the version of the resource provider API to use. If you do not specify a version, this cmdlet uses the latest available version.
-AssignIdentity
Generate and assign a system assigned managed identity for this policy assignment. The identity will be used when executing deployments for 'deployIfNotExists' and 'modify' policies. Location is required when assigning an identity.
-DefaultProfile
The credentials, account, tenant, and subscription used for communication with azure
-Description
The description for policy assignment
-DisplayName
Specifies a new display name for the policy assignment.
-EnforcementMode
The enforcement mode for policy assignment. Currently, valid values are Default, DoNotEnforce.
Specifies the fully qualified resource ID for the policy assignment that this cmdlet modifies.
-IdentityId
Specifies the Id of the user assigned managed identity to assign to this policy assignment. This value is required if the value 'UserAssigned' is passed to the -IdentityType parameter.
-IdentityType
Specifies the type of managed identity to assign to this policy assignment. If the 'SystemAssigned' value is provided, a system assigned managed identity is generated and assigned to this policy assignment. If the 'UserAssigned' value is provided, the user assigned identity passed via its Id to the -IdentityId parameter is assigned to this policy assignment. The identity will be used when executing deployments for 'deployIfNotExists' and 'modify' policies. Location is required when assigning an identity. Permissions must be granted to the identity using New-AzRoleAssignment after the system assigned identity is created. The IdentityType parameter will be given precedence if both the AssignIdentity and the IdentityType parameter are used.
-InputObject
The policy assignment object to update that was output from another cmdlet.
The location of the policy assignment's resource identity. This is required when the -IdentityType value is provided.
The updated metadata for the policy assignment. This can either be a path to a file name containing the metadata, or the metadata as a string.
Specifies the name of the policy assignment that this cmdlet modifies.
-NonComplianceMessage
The non-compliance messages that describe why a resource is non-compliant with the policy.
The policy assignment not scopes.
-PolicyParameter
The new policy parameters file path or string for the policy assignment.
-PolicyParameterObject
The new policy parameters object for the policy assignment.
Indicates that this cmdlet considers pre-release API versions when it automatically determines which version to use.
Specifies the scope at which the policy is applied.
Nullable<T> [ [ Microsoft.Azure.Commands.ResourceManager.Cmdlets.Entities.Policy.PolicyAssignmentEnforcementMode, Microsoft.Azure.PowerShell.Cmdlets.ResourceManager, Version=3.5.0.0, Culture=neutral, PublicKeyToken=null ] ]
PsPolicyAssignment
PsNonComplianceMessage [ ]
Related Links
- Get-AzPolicyAssignment
- New-AzPolicyAssignment
- Remove-AzPolicyAssignment
Azure PowerShell
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Microsoft 365 Scripts
Microsoft 365 scripts repository.
m365scripts.com
Group Policy Assignments Using Microsoft Teams PowerShell
Unmanaged devices, external file-sharing, and email integration impose a big question mark on the security posture of Microsoft Teams. In order to secure and manage Microsoft Teams, policies are used under various sections like messaging, meetings, calling, conferencing, and many more. Usually, these Teams policies for users, groups, and batches are managed in the Microsoft Teams admin center or using the Teams PowerShell Module (TPM). But now Microsoft extends the managing capability of additional Office 365 group policies using the Teams PowerShell Module as per MC557818 .
According to this latest update, group policy assignments for Microsoft 365 groups, distribution lists, mail-enabled security groups, and security groups support additional policies in the Teams PowerShell Module. Apart from action control, policy assignments also set way for security controls like restricting anonymous access in meetings.
Let us see how to assign group policies using Microsoft Teams PowerShell Module and their functionalities under this blog.
What are Group Policy Assignments?
As the name suggests, assigning a policy to a particular group of users is known as a group policy assignment. The groups can be managed in Microsoft 365 admin center whereas group policies can be managed under the single roof of the Teams PowerShell Module.
Policy assignments are applied only to the direct members of a group and not to the nested group. That too, they are applied according to the precedence rules. And at the time of addition or deletion of users from a group, the policy assignments are updated which is also applicable when a policy is unassigned. Before jumping into group policy assignments, let us look through the precedence rules and ranking of policies.
What are Microsoft Teams Policy Precedence Rules?
Policy precedence determines the user’s effective policy when a user is assigned two or more of the same policy types. The precedence rules of policies are listed below for deeper insights into how an assigned policy will be deployed according to these rules.
- If a user is directly assigned a policy, the same type of policy can’t be inherited from the group. Therefore, the directly assigned policy takes precedence over the same policy type defined by the group.
- Also, if a user doesn’t contain a directly assigned policy, the user inherits the highest-ranking policy from the same type of policies applied by two or more groups.
- Finally, if the user is not assigned a policy directly or by group, then the global (organization-wide) policy takes precedence .
The user policy is updated under the following circumstances.
- Especially when a user is added or removed from the policy assigned group.
- And when a group policy is unassigned.
- At last, if a directly assigned policy is removed from a user.
What is Group Policy Assignment Rank in Teams?
As an admin, you are asked to define the rank of policy while assigning the policy. Primarily this ranking weighs the priority of the same type of policies assigned from two or more groups for a common user. Finally, the highest-ranking group policy is assigned as the effective policy to the end user after weighing the priority. Because a policy type can be assigned to a maximum number of 64 groups in Office 365.
NOTE: If the rank value is undefined, then the lowest ranking is given to the policy assignment.
How to Assign Policy to a Group in Teams Admin Center?
Follow the below steps to configure group policies in the Teams admin center where it majorly supports Teams calling policy, Teams call park policy, Teams policy, Teams live events policy, Teams meeting policy, and Teams messaging policy.
- Navigate using the path below.
Microsoft Teams admin center 🡢 Messaging Policies (Select the desired policy type page) 🡢 Group policy assignment 🡢 Add group 🡢 Assign policy to group
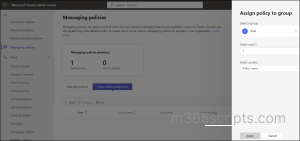
2. Then, select a group to which you want to assign a policy. 3. Set the ranking value for the group policy assignment through the select rank option. 4. After that, select a policy from the available policy types in the drop-down list and click Apply .
Unfortunately, all policy types can’t be managed under the Microsoft Teams admin center since it supports only certain policy types. Without a second thought, PowerShell is the go-to solution! Yes, managing policies using PowerShell is easy and efficient as it is the primary automation tool that ensures the deployment of objects in multiple tenants. Also, it is a place where error handling and logging are more flexible compared to the native admin center. Thus, let us deeply look through the next section of the blog to manage group policy assignments using Microsoft Teams PowerShell.
Manage Group Policy Assignments Using Teams PowerShell Module
As per the new update, Teams PowerShell Module now helps to manage group policies of Microsoft 365 groups, mail-enabled security groups, distribution lists, and security groups including Teams-related policies. Thus, create & manage groups in Microsoft 365 admin center and manage their policies in Teams PowerShell. Before getting started with PowerShell cmdlets, make sure to connect to the Teams PowerShell Module .
Assign Policy to Group Using Teams PowerShell Module
Get group policy assignments using ms teams powershell, remove policy assignment from a group using tpm, modify group policy assignment using teams powershell module.
By defining group policies, you can control user-specific actions like allowing them to schedule meetings, edit sent messages, etc. You can assign the available policies or create and assign custom policies depending on your requirements. Execute the following cmdlet after replacing the unique group identifier, policy type, policy name, and expected rank to assign a new policy for a group.
This “New-CsGroupPolicyAssignment” cmdlet is basically used to create new policy assignments for security groups and distribution lists. In which the group ID, policy type, policy name, and rank must be mentioned as mandatory parameters. Here with the rank value as one, the ‘AllOn’ policy under TeamsMeetingPolicy type is created for the given group.
The rank of the policy must be defined to determine the precedence. The recommended group membership size is 50,000 users per group while assigning a group policy. Also, it takes 24 hours or more to propagate the policy to all members of the larger groups.
Knowing all the available policy assignments allows you to understand the working conditions and their precedence levels better. Using this you can remove unnecessary policies, alter the desired ranking for policies and efficiently manage teams & groups around your Office environment.
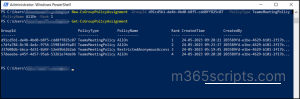
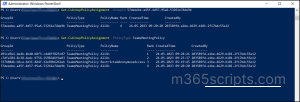
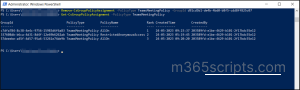
The “Get-CsGroupPolicyAssignment” cmdlet primarily returns all the group policy assignments with some optional parameters to filter the results.
- Primarily, list all the policy-assigned groups by running the following command.
2. However, you can also retrieve all the policies assigned to a particular group using the below cmdlet.
Here the cmdlet is mentioned with group ID so that retrieving only the policy assignments of that particular group.
3.Also, you can list the groups based on their policy type by executing the below command.
In this case, the policy type is mentioned as TeamsMeetingPolicy. Hence this cmdlet returns only the groups assigned with this policy.
Remove the unnecessary policies found in your organization that are interrupting the ranking and slowing down the work progress. Most importantly, the removal of policies will update the ranking value of the same type policies where the policies in the list will be ranked consecutively after the removal.
Run the following cmdlet to remove a specific group policy assignment in Microsoft 365 environment.
The ” Remove-CsGroupPolicyAssignment” cmdlet removes the given policy type in mentioned group ID.
Directly altering the policy assignment ranking value is not possible in the Teams admin center. The policy assignments should be removed and newly assigned again with a new rank value to change the ranking. To take away this hassle, PowerShell lends you a hand with a simple and reusable cmdlet which is described below.
The “Set-CsGroupPolicyAssignment” cmdlet can be used to make the following alterations in group policy assignments based on the given attributes.
- Change policy assignment ranking.
- Change the policy under the existing policy type.
- Change policy assignment ranking value and policy of a given policy type.
In this example, the policy is changed to ‘SupportCallPark’ policy, and the rank value is assigned to 3.
NOTE: The “Set-CsGroupPolicyAssignment” cmdlet is currently not released for use. So, for now, you need to remove policies and add new policies to change the policy or ranking. But you can easily alter the policy settings once after the availability of this cmdlet.
New Group Policy Assignment Support in Teams PowerShell Module
Microsoft rolls out group policy assignment support for additional policies in Teams PowerShell Module as a new update. So that admins can manage their groups in the M365 admin center and group policies in Teams PowerShell with a breeze. This feature will allow you to configure custom policies to groups for all Microsoft commercial licenses. With this update, dependency on global or direct policy assignments through manual methods is eliminated. In addition to the core policies such as meeting policies, calling policies, and messaging policies, the following policies are now expected to be available in Teams PowerShell by late May 2023 .
- Application Access Policy
- Call Hold Policy
- Carrier Emergency Call Routing Policy
- Cortana Policy
- Dial Out Policy
- Education Assignments App Policy
- Emergency Calling Policy
- Enhanced Encryption Policy
- Events Policy
- External Access Policy
- Feedback Policy
- Files Policy
- IPPhone Policy
- Media Logging Policy
- Meeting Branding Policy
- Meeting Template Permission Policy
- Mobility Policy
- Notification And Feeds Policy
- Room Video Tele Conferencing Policy
- Synthetic Automated Call Policy
- Teams Branch Survivability Policy
- Template Permission Policy
- Video Interop Service Policy
- Voice Routing Policy
- Voicemail Policy
In conclusion, ultimately manage all group policies including Teams using PowerShell cmdlets. Take charge of the user-specific actions and security controls through this group policy assignment. Not only policies, you can also manage your Teams using PowerShell for effective administration. Rather than performing numerous repetitive tasks in the Teams admin center, automate them with just a few cmdlets in PowerShell.
I hope that this blog provides you with deeper insights into group policy assignments using Teams PowerShell. For any clarifications feel free to reach us through comments.
Related Posts:


IMAGES
VIDEO
COMMENTS
The Get-AzPolicyAssignment cmdlet gets all policy assignments or particular assignments. Identify a policy assignment to get by name and scope or by ID. Examples Example 1: Get all policy assignments Get-AzPolicyAssignment. This command gets all the policy assignments. Example 2: Get a specific policy assignment
This cmdlets returns the effective policies for a user, based on either direct policy assignment or inheritance from a group policy assignment. For a given policy type, if an effective policy is not returned, this indicates that the effective policy for the user is either the tenant global default policy (if set) or the system global default policy. This cmdlet does not currently support ...
Policy assignment. Policy assignments are used to declare where the policy definitions are applied. You can create a policy assignment by linking an existing policy definition and specifying the target scope. In this way, the same policy definition object can be reused with another policy assignment. Policy scope
For this PowerShell command, you can use it to get all the policy assignments, no matter which policy and which resource like this: Get-AzPolicyAssignment And you also can use it to get a special policy assignment for a special resource like this: Get-AzPolicyAssignment -Scope resourceId -PolicyDefinitionId policyDefinitionId See the examples ...
In this article. The first step in understanding compliance in Azure is to identify the status of your resources. In this quickstart, you create a policy assignment to identify non-compliant resources using Azure PowerShell. The policy is assigned to a resource group and audits virtual machines that don't use managed disks.
Get-AzPolicyAssignment [-Name <String>] [-Scope <String>] Now, let's discuss a few examples of how to use the Get-AzPolicyAssignment PowerShell command with a few examples. Example. Below PowerShell command can help you to retrieve the lists of policy assignments. Get-AzPolicyAssignment. After running the above command, I got the below output.
If any of the assigned policies belong to the requested category, like Guest Configuration in my case, information about those policies will be provided as output upon script execution. You can find the PowerShell script in my GitHub repo: Get-Policy-Assignments-In-Category.ps1. The output will look something like the screenshot below:
This time, the post will focus on policy assignments with Azure Bicep and PowerShell. Policy assignment enforces a policy and a policy set at a given scope, management group, or subscription. This is where policies are applied to target resources. A policy Assignment object has several properties: A non-compliance object.
Within the Azure Portal, search for Policy. Click on Remediation on the left-hand side. Click on a policy that is of the type of deployIfNotExists an d has non-compliant resources. Filter the resources to be re-mediated on the New remediation task page to limit what the task applies to. Click on Remediate to start the task itself.
To do this successfully we should read in the existing policy assignment and store that information in our script so we reapply the policy with the same information that was originally available. Store Policy Assignment Information. To store the policy assignment information, we will use the Get-AzPolicyAssignment PowerShell module:
This cmdlets returns the status of all batch policy assignment operations for the last 30 days. If an operation ID is specified, the detailed status for that operation is returned including the status for each user in the batch.
==>>A special thanks to Timmy Andersson for the PowerShell script!!<<== Dear Microsoft Intune Friends, In Microsoft Intune, it is possible to ... @TomWechsler Has the mobileapps functionality changed as I don't get the assignments back when I try it. I've even tried the Graph command directly in Graph explorer and I don't get them ...
Output: 4. Use Get-AzPolicyDefinition PowerShell command to get the Azure Policy Definitions list and properties. Get-AzPolicyDefinition. The command returns the properties of all the Azure Policy Definitions. Output: 5. Use (Get-AzPolicyDefinition).count PowerShell command to get the count of Azure Policy Definitions.
Connect to the Exchange Online manage m ent PowerShell module. This is an optional connection that I use to fetch the tenant name for the report using the Get-OrganizationConfig cmdlet. You could also use the Get-AzureADTenantDetail cmdlet from the Azure AD module. For each user, extract the policy assignments and update a PowerShell list object.
For more information about assignment policies, see Understanding management role assignment policies. You need to be assigned permissions before you can run this cmdlet. Although this topic lists all parameters for the cmdlet, you may not have access to some parameters if they're not included in the permissions assigned to you. To find the permissions required to run any cmdlet or parameter ...
If it's a group assignment, the script calls a function to run the Get-MgGroup cmdlet (from the Microsoft Graph PowerShell SDK) to return the display name of the group used for the assignment. When processing policy assignments for all users, it's likely that the same groups will be met many times.
But I want to assign a policy set, how can I assign a policy set using Powershell? azure; powershell; azure-policy; Share. Follow edited Sep 27, 2022 at 8:59. Maytham Fahmi. 32.5k 16 16 gold badges 123 123 silver badges 146 146 bronze badges. asked May 21, 2019 at 20:44.
To get assignable Intune policies, use the function Get-IntunePolicy from my module IntuneStuff like this 👇 🙂. Install-Module IntuneStuff -Force. Import-Module IntuneStuff -Force. # connect to Graph API. Connect-MSGraph. # get all Intune policies. Get-IntunePolicy -verbose. # get just Apps and Compliance Intune policies. Get-IntunePolicy ...
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function.
The Set-AzPolicyAssignment cmdlet modifies a policy assignment. Specify an assignment by ID or by name and scope.
Microsoft Teams admin center 🡢 Messaging Policies (Select the desired policy type page) 🡢 Group policy assignment 🡢 Add group 🡢 Assign policy to group. 2. Then, select a group to which you want to assign a policy. 3. Set the ranking value for the group policy assignment through the select rank option. 4.