
Windows 10 Top Contributors: neilpzz - Ramesh Srinivasan ✅
October 14, 2024

Windows 10 Top Contributors:
neilpzz - Ramesh Srinivasan ✅
- Search the community and support articles
- Search Community member
Ask a new question
Locked local policy -- need to unlock
I went to make changes in the local computer policy, specifically >windows settings> security settings>local policies>user rights assignment. It appears that security settings>local policies>user rights assignment are locked as are the local policies (little padlock on the file) I am the administrator of the computer -- the only user -- how do I unlock these folders so I can make changes. This is a personal computer. Any help would be appreciated.
Report abuse
Reported content has been submitted
Replies (13)
* Please try a lower page number.
* Please enter only numbers.
- Independent Advisor
1 person found this reply helpful
Was this reply helpful? Yes No
Sorry this didn't help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
Thanks for your feedback.
Hi, Geoffrey. I'll be happy to assist you today. Sorry to know you're experiencing this policy issue. What we need to do first is perform the following procedure in order to reset security policies: Please open CMD as administrator then paste the following commands then reboot the computer: SECEDIT /configure /cfg %windir%\inf\defltbase.inf /db defltbase.sdb /verbose RD /S /Q "%WinDir%\System32\GroupPolicyUsers" RD /S /Q "%WinDir%\System32\GroupPolicy" RD /S /Q %localappdata%\GroupPolicy\DataStore Please let me know if you need any further assistance.
thanks -- the first three commands worked -- the fourth and final one gave me a not found error. Rebooted anyway and still locked.
2 people found this reply helpful
the exact error is " The system cannot find the path specified."
Thanks for your feedback, Geoffrey. Please open a normal CMD session, then type the following command to generate a policy result file containing policies currently applied to your user and computer: gpresult /h desktop\result.html Next upload the file to OneDrive or another file share service and share the file publicly. Paste the link here, please.
Getting invalid pointer error with a blank html file generated.
Have the same issue -- blank file created in the target folder
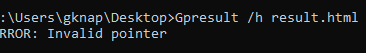
The change does not hold. Once I close the policy app the change disappears and reboot, tried it a couple of different ways. But same result.
Question Info
- Norsk Bokmål
- Ελληνικά
- Русский
- עברית
- العربية
- ไทย
- 한국어
- 中文(简体)
- 中文(繁體)
- 日本語
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Allow log on locally - security policy setting
- 1 contributor
- Windows 11
- Windows 10
Describes the best practices, location, values, policy management, and security considerations for the Allow log on locally security policy setting.
This policy setting determines which users can start an interactive session on the device. Users must have this user right to log on over a Remote Desktop Services session that is running on a Windows-based member device or domain controller.
Note: Users who do not have this right are still able to start a remote interactive session on the device if they have the Allow logon through Remote Desktop Services right.
Constant: SeInteractiveLogonRight
Possible values
- User-defined list of accounts
- Not Defined
By default, the members of the following groups have this right on workstations and servers:
- Administrators
- Backup Operators
By default, the members of the following groups have this right on domain controllers:
- Account Operators
- Enterprise Domain Controllers
- Print Operators
- Server Operators
Best practices
- Restrict this user right to legitimate users who must log on to the console of the device.
- If you selectively remove default groups, you can limit the abilities of users who are assigned to specific administrative roles in your organization.
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignment
Default values
The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy's property page.
Policy management
Restarting the device is not required to implement this change.
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Modifying this setting might affect compatibility with clients, services, and applications. Use caution when removing service accounts that are used by components and by programs on member devices and on domain controllers in the domain from the default domain controller's policy. Also use caution when removing users or security groups that log on to the console of member devices in the domain, or removing service accounts that are defined in the local Security Accounts Manager (SAM) database of member devices or of workgroup devices. If you want to grant a user account the ability to log on locally to a domain controller, you must make that user a member of a group that already has the Allowed logon locally system right or grant the right to that user account. The domain controllers in the domain share the Default Domain Controllers Group Policy Object (GPO). When you grant an account the Allow logon locally right, you are allowing that account to log on locally to all domain controllers in the domain. If the Users group is listed in the Allow log on locally setting for a GPO, all domain users can log on locally. The Users built-in group contains Domain Users as a member.
Group Policy
Group Policy settings are applied through GPOs in the following order, which will overwrite settings on the local computer at the next Group Policy update:
- Local policy settings
- Site policy settings
- Domain policy settings
- OU policy settings
Security considerations
This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Vulnerability
Any account with the Allow log on locally user right can log on to the console of the device. If you do not restrict this user right to legitimate users who must log on to the console of the computer, unauthorized users could download and run malicious software to elevate their privileges.
Countermeasure
For domain controllers, assign the Allow log on locally user right only to the Administrators group. For other server roles, you may choose to add Backup Operators in addition to Administrators. For end-user computers, you should also assign this right to the Users group. Alternatively, you can assign groups such as Account Operators, Server Operators, and Guests to the Deny log on locally user right.
Potential impact
If you remove these default groups, you could limit the abilities of users who are assigned to specific administrative roles in your environment. If you have installed optional components such as ASP.NET or IIS, you may need to assign the Allow log on locally user right to additional accounts that are required by those components. IIS requires that this user right be assigned to the IUSR_ <ComputerName> account. You should confirm that delegated activities are not adversely affected by any changes that you make to the Allow log on locally user rights assignments.
Related topics
- User Rights Assignment
Additional resources
Local Security Policy in Windows 10 and Windows 11 Explained
By Victor Ashiedu
Published October 18, 2019
On this page...
Have you heard about the Local Security Policy in Windows 10 and Windows 11, but you do not know what it does? Learn all there is to know about this Windows feature.
The Windows Operating System offers some features you can use to enhance the security of your PC. If you use your computer in an office and the computer belongs to a Windows network (called “domain”), your IT administrator can apply some of these security features from the server.
In a domain network, the IT administrator will apply these policies using what we call “Group Policy”.
However, if your computer does not belong to a domain, you can apply some of these security features using the Local Security Policy . The Local Security Policy is a set of information you can use to enhance the security of a local Windows computer.
Windows offers the Local Security Policy in two main categories – Account Policies and Local Policies . The Account Policies allow you to set Password policies like enforce password history.
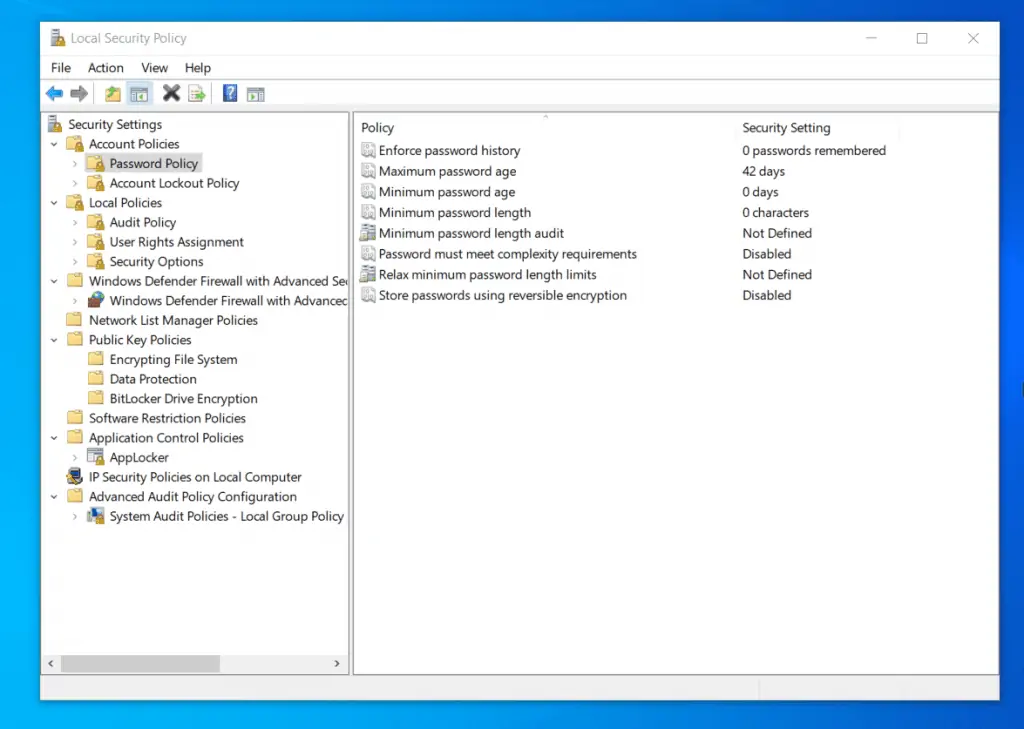
In addition to that, under account policies, you can also set Account Lockout Policies. For example, you can set a policy that determines how many minutes an account stays locked (if locked out) before automatically becoming unlocked.
On the contrary, under the Local Policy section of the Local Security Policy, you can set Audit Policy, User Rights Assignments, and Security Options policies.
In the subsequent sections of this guide, I will break down how these security policies work, their features and advantages, and their limitations.
How Local Security Policy Works
When a Windows 10 or Windows 11 local administrator sets Local Security Policies, the policies apply to all users that log in to the computer.
For example, a local administrator may modify the Local Security Policy, “Allow Log on locally” to allow only administrators to log on to the computer.
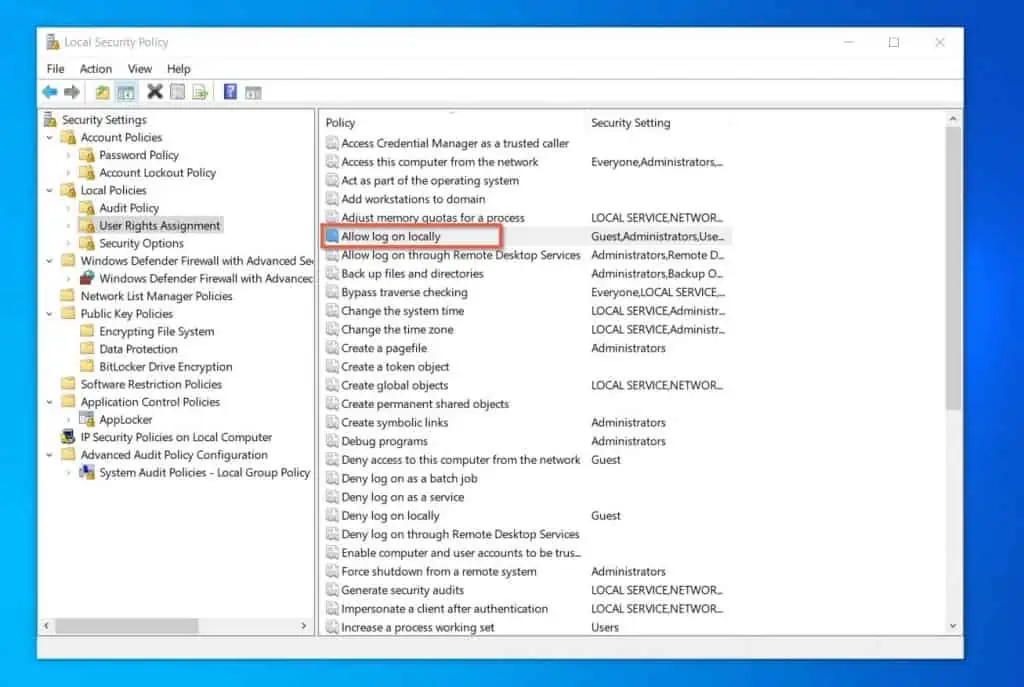
This policy will be enforced on the local computer. So, when a non-administrator tries to log in to the computer, the computer will deny the user access.
This policy will remain enforced as long as the computer does not belong to a Windows domain network. If, however, the computer belongs to a Windows domain network, policies (called “Group Policy”) applied by the network administrator will override any Local Security Policy applied by the local administrator.
If this happens, a non-administrator user can log on to the Windows 10 or Windows 11 computer. That is if the Group Policy applied by the network administrator allows non-administrators to log in to computers on the Windows domain network.
Essentially, Local Security Policies applied on the computer from the computer’s Local Security Policy snap-in only apply to the local computer.
Features of Local Security Policy
So far, I have discussed an overview of the Local Security Policy. In addition to that, I have also discussed how this Windows security feature works.
In this section, you’ll learn the main features of the Local Security Policy in Windows 10 and Windows 11.
Policies Created from the Local Computer Applies Only to the Computer
Unlike policies applied by a Windows domain network administrator, if a Windows local administrator applies a policy, it is only enforced on the local computer.
On the contrary, if a network domain administrator applies a security policy via Group Policy, the policy applies to all computers and/or users that meet the criteria.
Group Policies Applied by the Network Domain Administrator Takes Precedence Over Local Policies
As I hinted in the “how it works” section, if an administrator creates a policy that conflicts with a local policy, the domain policy takes precedence. The implication of this is that the network administrator has more control over Windows computers than local administrators.
So, for domain-joined computers, Local Group Policies apply before Group Policies. So, when the computer applies the Group Policies, they override the local policies.
Windows 10 and Windows 11 Home Editions do not Have the Local Security Policy Snap-in
This is a very important feature to mention as many Windows 10 Home users complain that they cannot find the Local Security Policy snap-in. If you own a Windows 10 Home edition, your license does not include this option.
To determine your Windows 10 edition, search winver and open the app. Then, check your Windows edition – see the screenshot below.
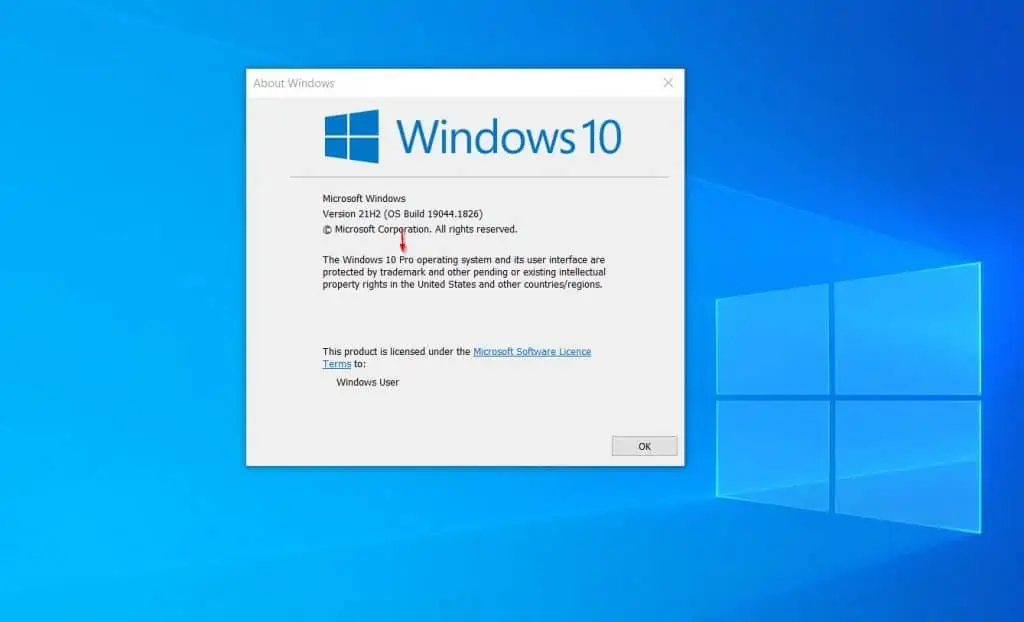
If your Windows 10 or Windows 11 shows “Home” where mine displays “Pro” in the screenshot above, you’ll NOT be able to open the Local Security Policy.
So, you need to upgrade your Windows “Home” to “Pro” in this situation.

The Local Security Policy Snap-in has Nine Nodes
The LSP snap-in has 9 nodes that offer you different policies you can apply to the local computer. However, most of the policies you may need to apply to a local computer are located in the Account Policies and Local Policies nodes.
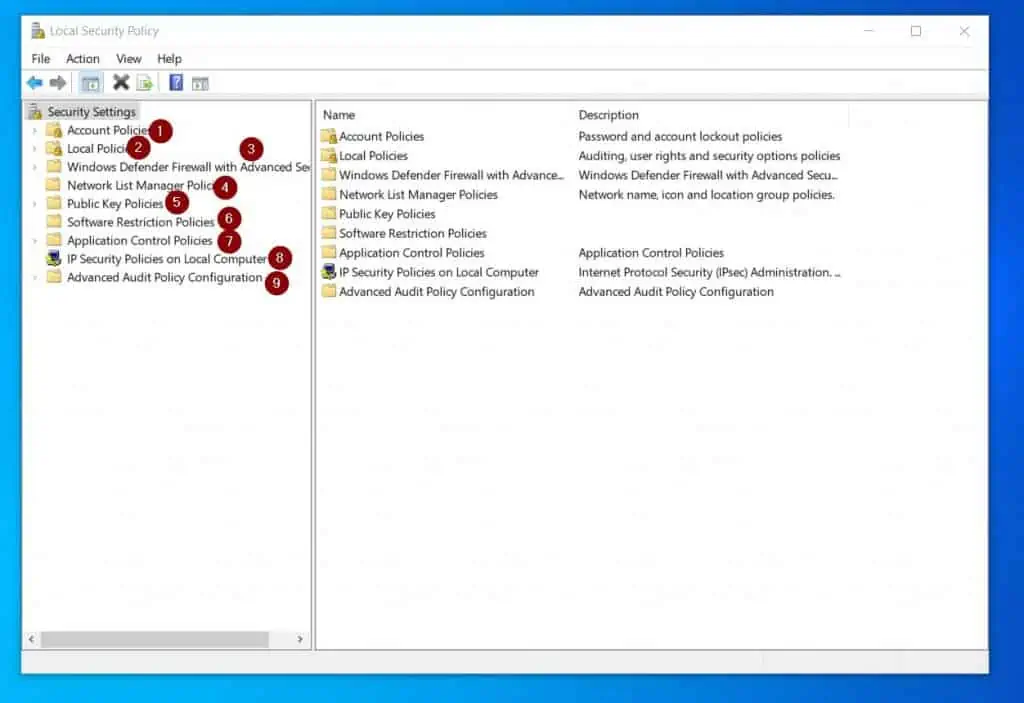
Moreover, within each node, there are sub-nodes that contain the policies you can enable and apply. As an example, the Account Policies node has two sub-nodes – Password Policy and Account Lockout Policy.
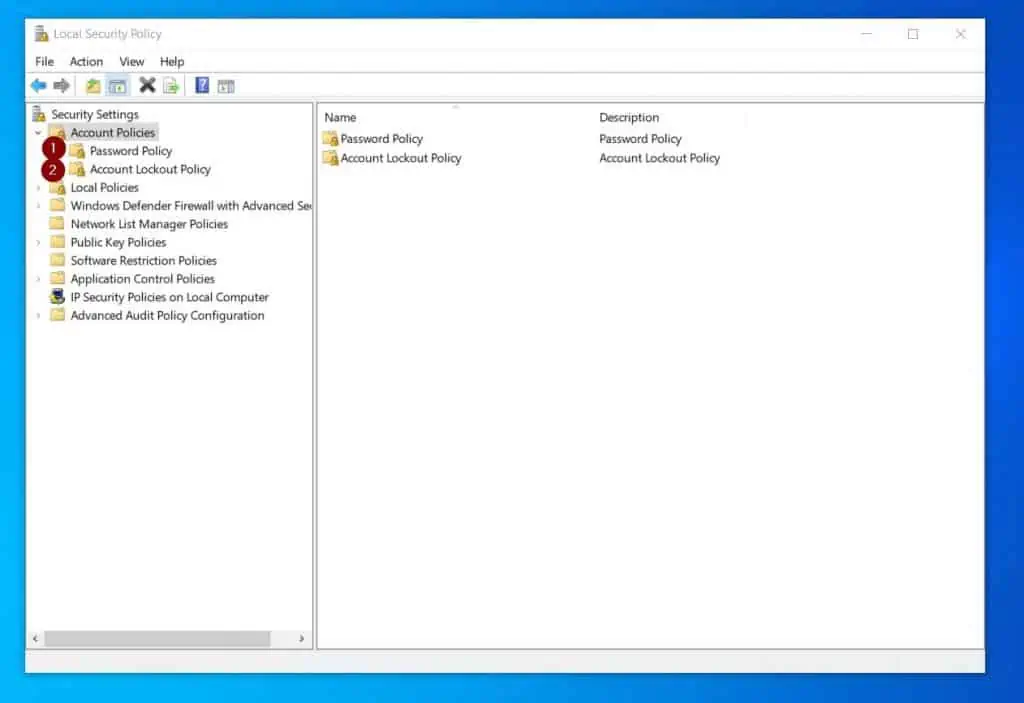
To display the policies available in a sub-node, click on it. For example, click the sub-node to display the policies in the Password Policy sub-node.
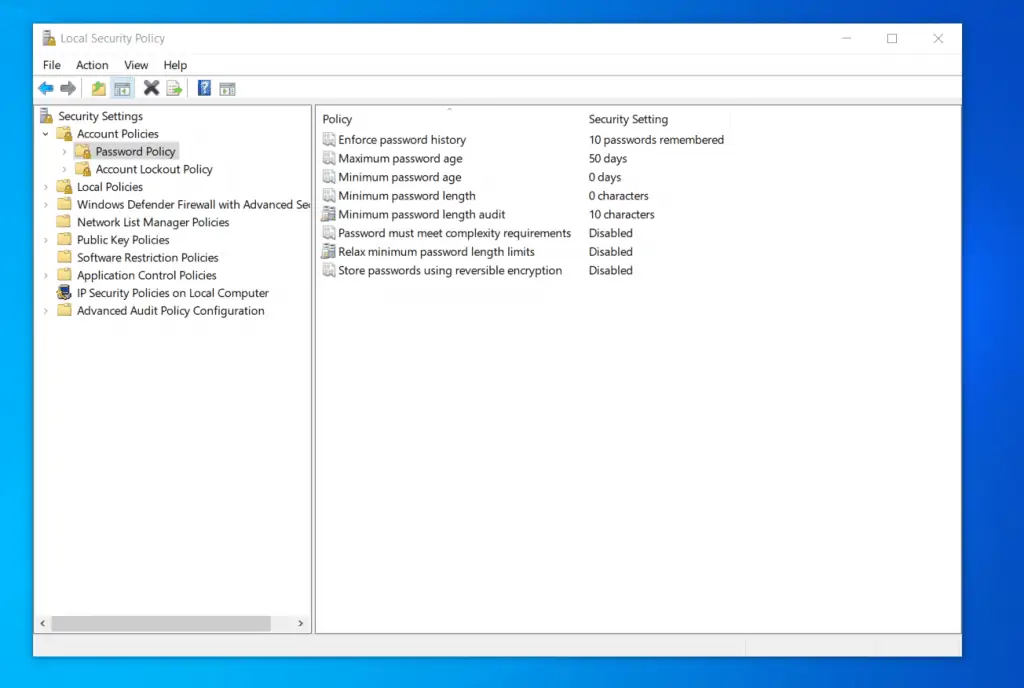
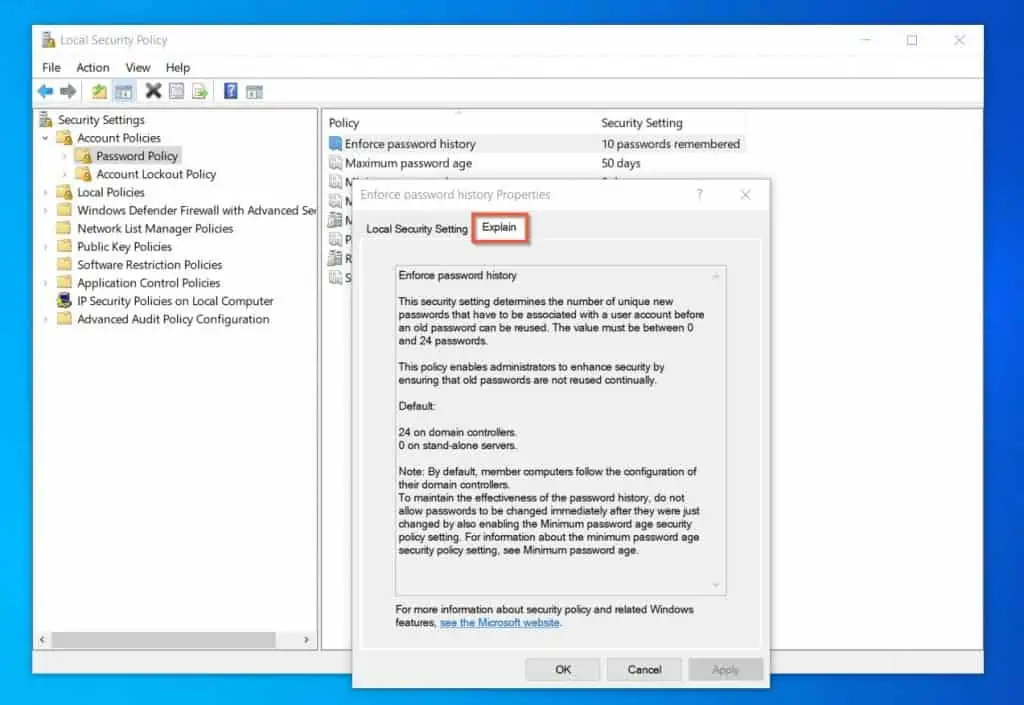
Finally, to configure a policy, double-click it. For example, if I want to configure the “Enforce password history”, double-click the policy. Then, configure the policy and click OK.
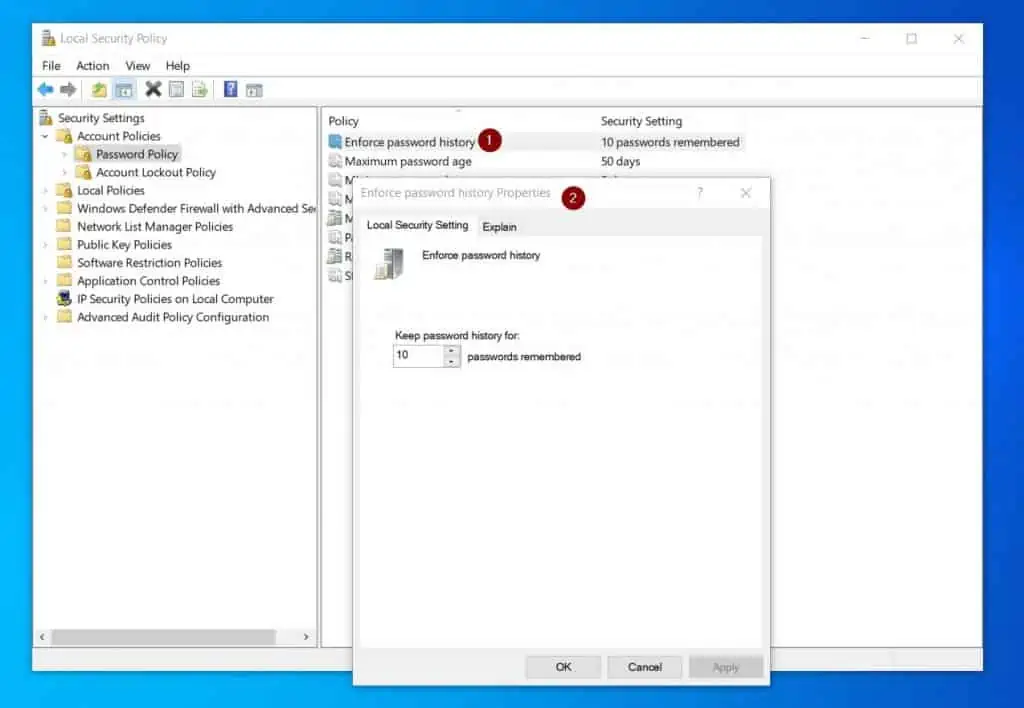
However, if you need additional help with the policy, click the “Explain” tab.
Pros of the Local Security Policy
Local security policies have helpful information that explains what the policy does and how to configure it.
If you want to enable a policy in the LSP snap-in but you do not know what it does, you can click the “Explain” tab to get more information. To learn how to do this, see the last sub-section in the features section of this guide.
Local Security Policies Help Local Administrators Tighten Security on Computers Used by Multiple People
If you manage a small office with computers available to multiple users, you can use the Local Security Policies to enhance the security of the computers.
It Offers Ease of Configuration
Setting up local policies with the LSP snap-in is relatively easy. In addition to ease of configuration, the policies apply immediately without requiring you to restart the computer.
Offers Audit and Advanced Audit Policies that Allows Tracking of Events
If you want to track potential security breaches by users that log in to a local computer, you can use the audit policies provided by the Local Security snap-in. After enabling these policies, you can track the events in the Windows events log. Then, take the necessary actions to tighten the local computer’s security further.
Limitations of the Local Security Policy
Domain group policies override the local security policies.
If a Windows 10 or Windows 11 computer is joined to a domain, all policies applied by the network administrator override all policies applied via the Local Security Policy. This is a major limitation for the local administrator because this means that the local administrator loses control over the security of the PC. However, for the network administrator, this is a benefit as this gives the administrator the ability to manage the security of multiple computers.
Local Security Policies Apply to Local Computers
As I mentioned in the features section of this guide, when you set a policy in the Local Security Policy snap-in, the policy applies to the local computer. So, if your computers are not in a Windows domain network, you have to set the policies individually on each computer. This is time-consuming and an inefficient way to secure your multiple computers. Therefore, if you run a small office with up to 20 computers, I strongly recommend that you consider joining your computers to the Microsoft Azure Domain
How to Open Local Security Policy
You can open the Local Security Policy in 5 different ways. This section covers the 5 methods.
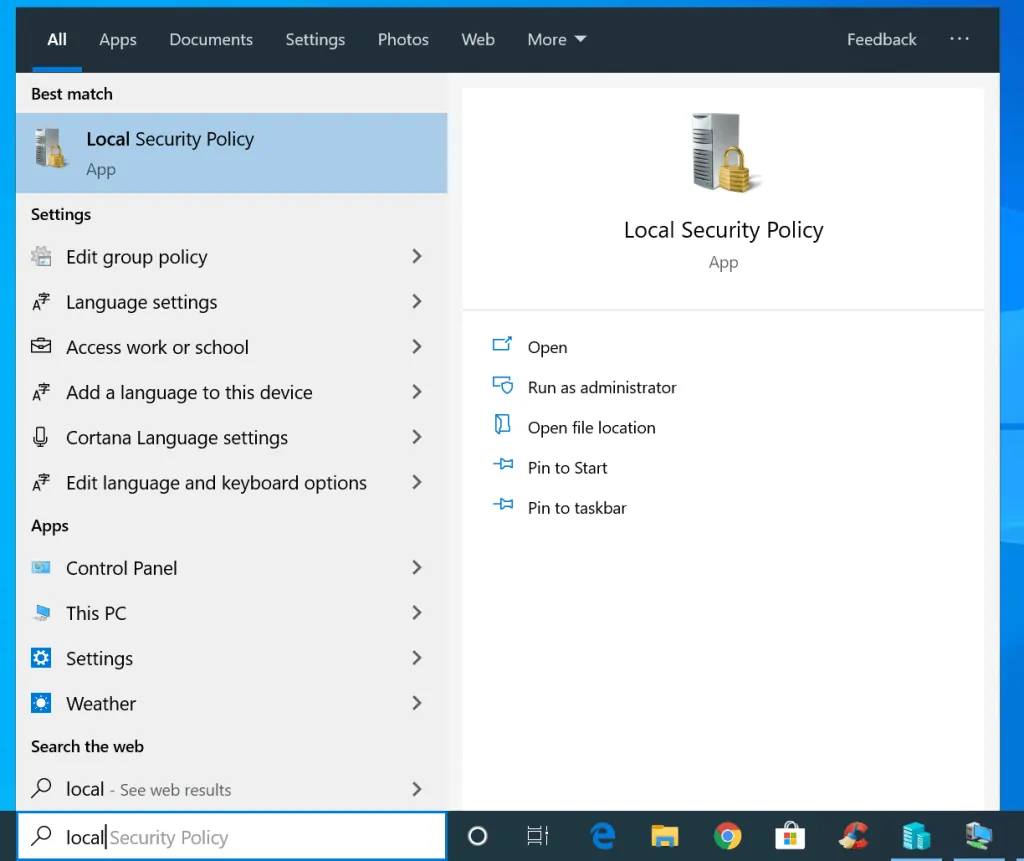
Option 1: Open Local Security Policy from Search
The quickest method to open the local security policy in Windows 10 or Windows 1 is to use search.
Here are the detailed steps.
- Type local in the Windows search bar. Then click Local Security Policy .
- It will open…
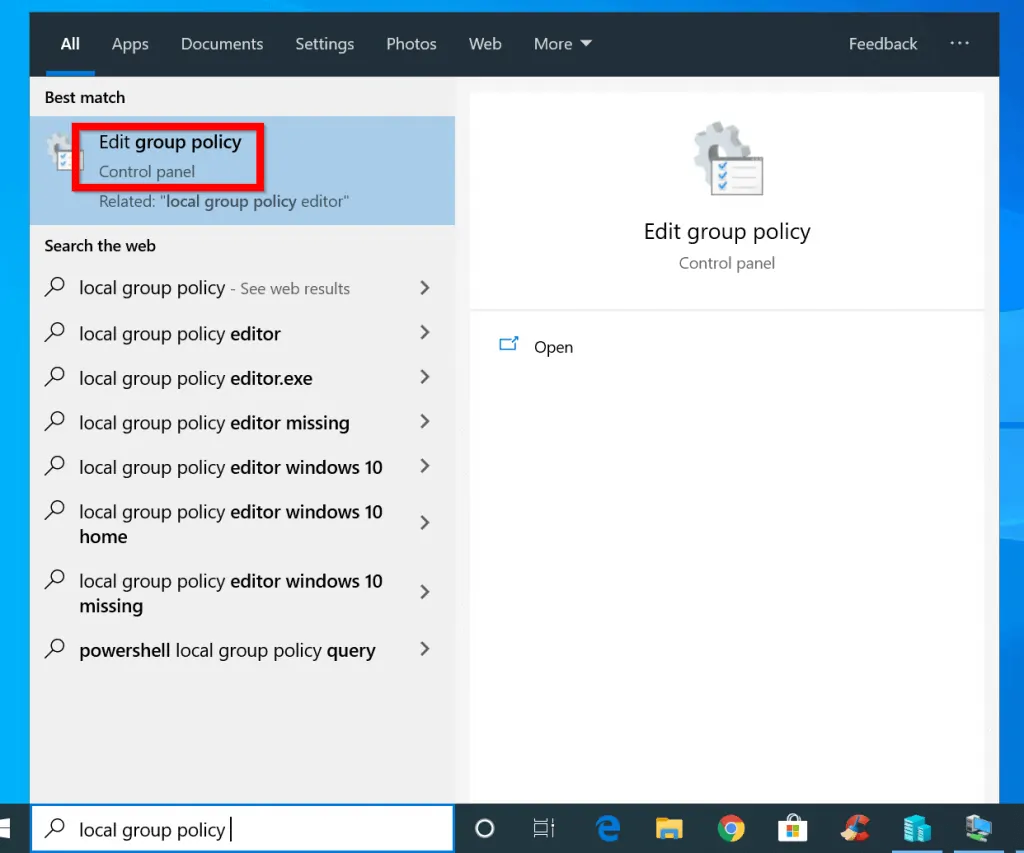
Option 2: Access Local Security Policy from Local Group Policy
You can also access the local security policy from the local group policy editor.
The detailed steps…
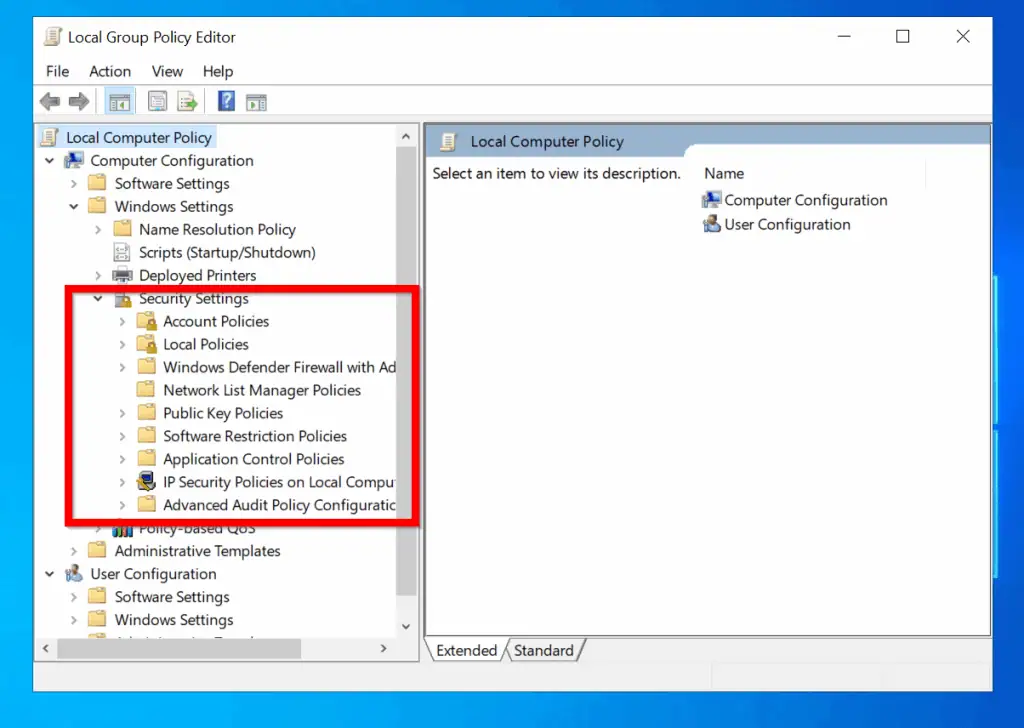
- Type local group policy in the search bar. Then select Edit group policy .
- At Local Group Policy Editor , expand Windows Settings on the Computer Configuration section. Then expand Security Settings . You can configure your Local Security Policies from the highlighted section of the image below..
Option 3: Access Local Security Policy from the Run Command
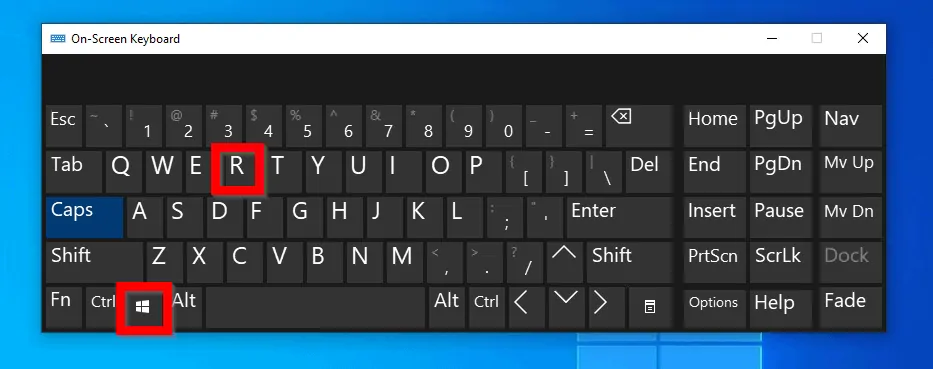
Another easy way to access local security policy is via Run Command. Here are the detailed steps:
- Click the Windows logo and R keys to open the Run command box.
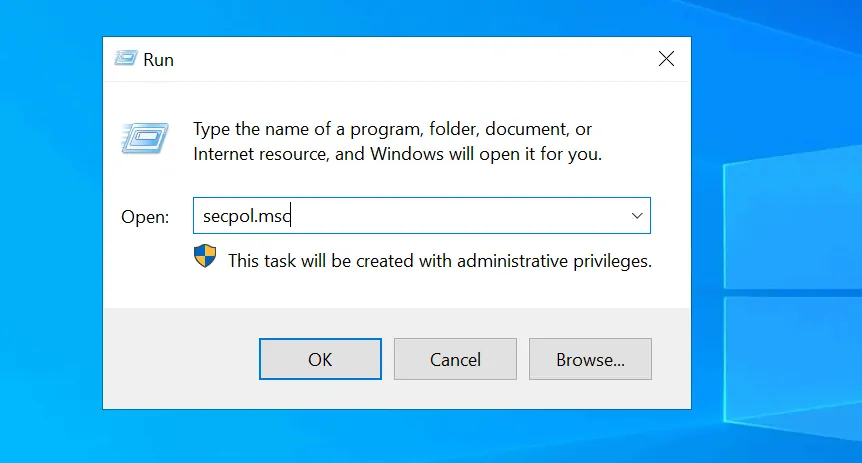
- Then, at the Run command, type secpol.msc and click OK.
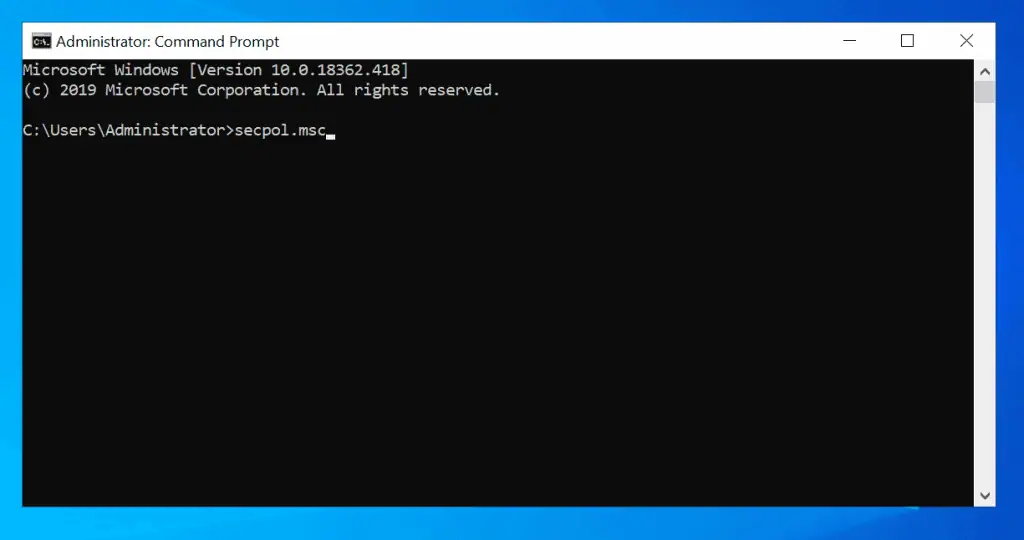
Option 4: Access Local Security Policy from the Command Prompt
This method is very similar to the Run command method. Here are the steps:
- Type command prompt in the search bar. Then click Command Prompt in the search results.

- At the command prompt, type the command below. Then press enter the command below and press the enter key on your keyboard.
Option 5: Open Local Security Policy from the Control Panel
You can also access security policy from Administrative Tools via Control Panel . The steps are detailed below:
- Type Control Panel into Windows 10 search. Then click Control Panel from the search results.
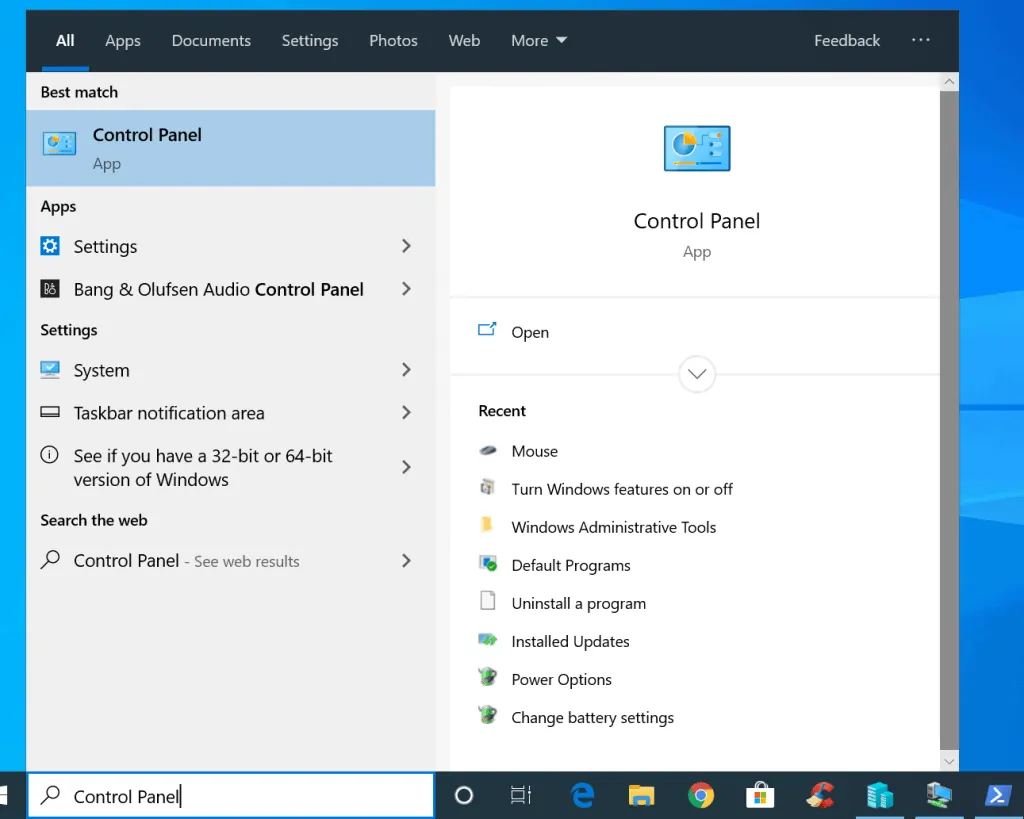
- When Control Panel opens, click the View by drop-down. Then select Large icons .
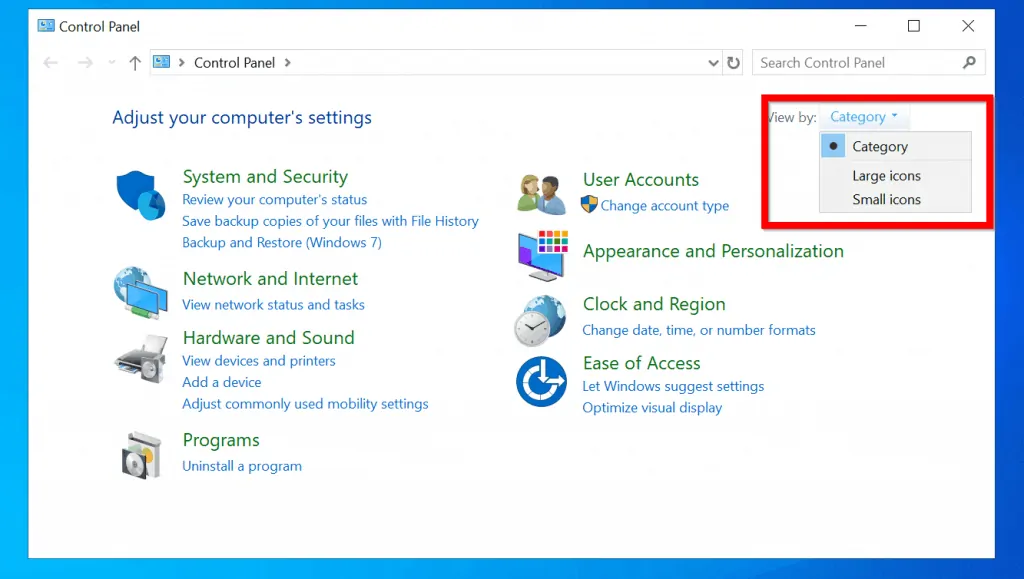
- At the modified Control Panel view, click Administrative Tools . It will open in a new Window.
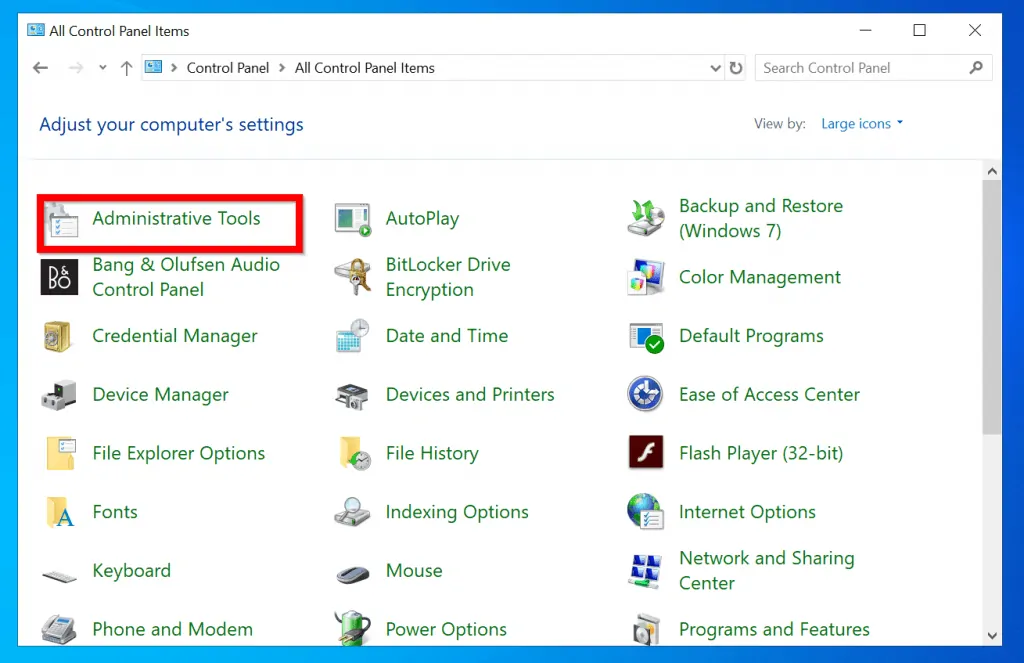
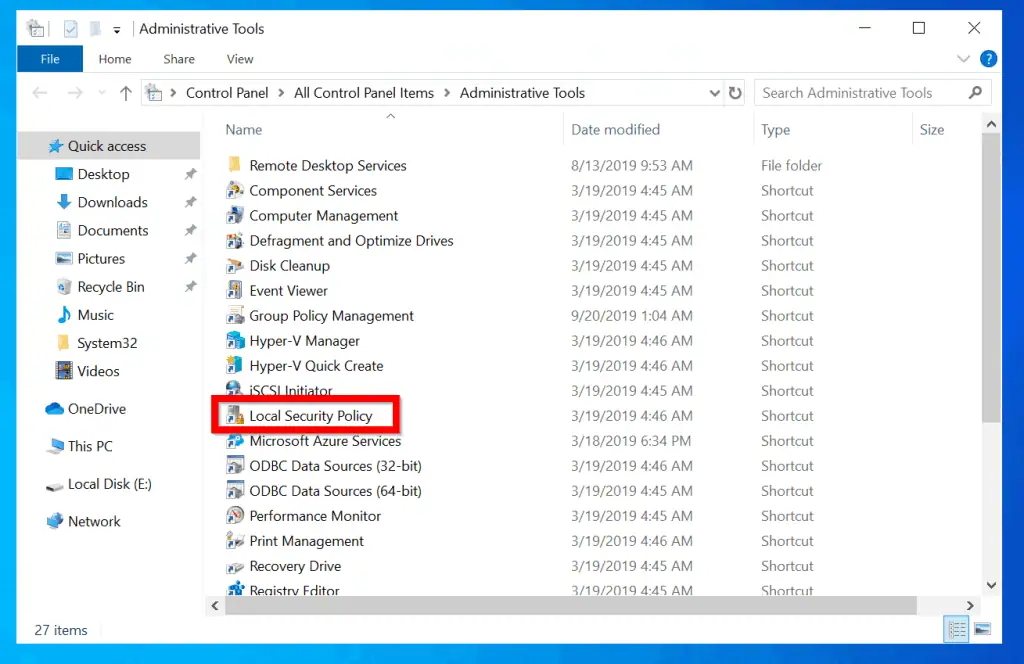
- Finally, to open the local security policy in Windows 10, click Local Security Policy .
Frequently Asked Questions
Yes. Windows 10 and Windows 11 have the Local Security Policy. However, the Home edition of Windows Operating Systems does not have this security snap-in
The reason your Windows 10 or Windows 11 computer does not have the Local Security Policy is likely that you’re running the Home edition of these operating systems.
The Local Security Policy snap-in contains policies that allow you to tighten the security and access of your Windows computer.
The easiest way to open the Local Security Policy is to search for it. You can search Local Security Policy in Windows 10 or Windows 11.
The primary difference between Local Security Policy (LSP) and Group Policy is that LSP is created on a local computer, and the policies apply to the local computer. On the contrary, Group Policy is created on a Domain Controller, and the policies apply to all domain-joined computers that meet the GPO criteria. Another difference is that Group Policies take precedence over Local Security Policies. So, if you create a local policy and a network administrator creates Group Policies, the network policies will be applied, and the local policies will be ignored.
The Local Security Policy is a set of policies local Windows PC administrators can use to strengthen the security of the local computer.
Local administrators can create these policies using the Local Security Policy snap-in. These policies are applied to the local computer and to all users who sign in to the local computer.
However, if the computer belongs to a Windows domain, policies (Group Policies) that network administrators apply override local policies.
I hope I have been able to explain this Windows feature and made it easy for you to understand. If I did a good job, click on “Yes” beside the “Was this page helpful” question below.
You may also express your thoughts and opinions by using the “Leave a Comment” form at the bottom of this page.
Finally, you may read more Windows articles via one of these links – Windows 11 How-To Guides , Windows 10 How-To Guides – Over 500 Guides
- Was this page helpful?
- Yes (14) No (8)
About the Author
Victor Ashiedu
Related Articles

Windows 11 Editions Explained: Which is the Best for You?

Disk in Task Manager Explained: What it Means and How it Works

Windows 10 vs Windows 11: Which is the Better Windows?
Get in Touch
We're committed to writing accurate content that informs and educates. To learn more, read our Content Writing Policy , Content Review Policy , Anti-plagiarism Policy , and About Us .
However, if this content does not meet your expectations, kindly reach out to us through one of the following means:
- Respond to "Was this page helpful?" above
- Leave a comment with the "Leave a Comment" form below
- Email us at [email protected] or via the Contact Us page.
1 thought on “Local Security Policy in Windows 10 and Windows 11 Explained”
Nice one! I like what you are doing bro. Leye-CWG
Leave a comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.

Windows 11 Is Here! Release Date, Features, Download, and More
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Allow logon locally option grayed out
We have a Domain Controller running on windows2012R2.
All local computers are on Windows10.
When i try to login to one of the client computer with Domain User Credentials i get an error

What could be the issue?
I tried to add users to " Allow log on locally " Policy on Local computer with Local admin login but im unable to add users or groups
Is there any work around?
please suggest.
- group-policy
- Probably UAC; use "Run as administrator" to launch the policy editor. Anyway, there already is "Everyone" listed... you can't really add much more. – Massimo Commented Apr 4, 2016 at 19:17
- i tried running with administrator even , no Luck. . if this is not the solution, what could be the issue "The sign in method . . . . " :/ – Uday Sriramadas Commented Apr 4, 2016 at 19:22
- 1 Seems like a user/computer GPO setting more than a local computer. Might want to check the GPO settings on the server more than on the local computer. – Naryna Commented Apr 4, 2016 at 19:22
- May be , Do you have any idea which GPO may cause this thing? #Brandyn – Uday Sriramadas Commented Apr 4, 2016 at 19:26
- You can use gpresult to find what GPOs are applied to the computer. – Massimo Commented Apr 4, 2016 at 19:28
You need to manage this element via Group Policy Management. Czerw11 did a good write up of the process of using Group Policy Management to update this on your domain controllers via the Default Domain Controller Policy, you can extend this to your client policy as well.
https://czerwsup.wordpress.com/2014/11/05/allow-log-on-locally-add-new-user-greyed-out-fix-via-domain-controller-policy-settings/
Summary Steps:
- Admin Tools
- Group Policy Management
- Navigate through your domain to Default Domain Policy in your case (not Default Domain Controllers Policy as in the example)
To improve this answer, the best practice is to not edit the Default Domain Controllers Policy, but to create a GPO with these policies changes and assign it to the narrowest OU you need to affect the servers. If you edit the Default Policies you remove all of the default permissions.
- Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies
- User Rights Assignment
- Double Click on Allow Log On Locally and add your users
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged group-policy login windows-10 ..
- The Overflow Blog
- Tragedy of the (data) commons
- How can you get your kids into coding? We asked an 8-year-old.
- Featured on Meta
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
Hot Network Questions
- Is syntactic simplicity (or elegance) more important than ontological simplicity?
- Are moral statements closed under negation?
- How Do Maneuver and Weapon Mastery Work Together?
- Why is the Vulgar Latin syncope of unstressed syllables not visible in the Croatian word "Sotona" (<Latin "Satanas")? Why isn't it *Sotna?
- Why don't we shake lulav and esrog for Ana Hashem Hatzlicha Na?
- Monkeys, spores and bouncy mushrooms
- I've never been an olympiad-winning excellent student; is there a chance for me in academia?
- Maximally Entangled Non-Bell Forms in Two Qubits
- What can happen if a damaged CV boot isn't repaired, allowed to operate until failure?
- What do these two symmetrical hooks on this captain's helmet do?
- Why did Jesus use spit in his miracles?
- Should I follow my processor manual or system motherboard specified max RAM?
- ESTA re entry to USA
- Is there any reason not to use a 7805? Assuming I need a linear reg and I've got the headroom
- Some に vs. で exceptions (?) for places
- Does a British Italian dual national need to carry both passports when traveling from Italy to the UK?
- Could pragmatism be a useful heuristic for "theory choice" between competing religious worldviews (or none at all)?
- KOH - Early Full Disk Encryption
- What aircraft has the propeller with the highest blade count?
- how to make start of 'align*' material line up with start of preceding line of text?
- What does はむりと mean?
- Removing an effect from a filter in Inkscape
- Is it impossible to launch a rocket from Venus’ surface to space?
- Simultaneous clang, hesitation and drop when I peddle with any weight

IMAGES
VIDEO
COMMENTS
How to Change User Rights Assignment Security Policy Settings in Windows 10. User Rights Assignment policies govern the methods by which a user can log on to a system. User rights are applied at the local device level, and they allow users to perform tasks on a device or in a domain.
You can configure the user rights assignment settings in the following location within the Group Policy Management Console (GPMC) under Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment, or on the local device by using the Local Group Policy Editor (gpedit.msc).
I went to make changes in the local computer policy, specifically >windows settings> security settings>local policies>user rights assignment.
Select Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. When you find the policy setting in the details pane, double-click the security policy that you want to modify.
User Rights Assignment. Describes the best practices, location, values, policy management, and security considerations for the Allow log on locally security policy setting.
User rights permissions control access to computer and domain resources, and they can override permissions that have been set on specific objects. User rights are managed in Group Policy under the User Rights Assignment item.
On the contrary, under the Local Policy section of the Local Security Policy, you can set Audit Policy, User Rights Assignments, and Security Options policies. In the subsequent sections of this guide, I will break down how these security policies work, their features and advantages, and their limitations. How Local Security Policy Works.
As you can see in the Group Policy Settings Reference Guide (see your 1st link; in particular, Windows10andWindowsServer2016PolicySettings.xlsx document), most of security settings (e.g. User Rights, Password Policy, Audit Policy etc.) are not registry keys.
There are several ways to configure security policy settings. The most common are: Group policy objects (GPO) – Used in Active Directory domains to configure and regularly reapply security settings to multiple computers. Local security policy (secpol.msc) – Used to configure a single (local) computer.
If you edit the Default Policies you remove all of the default permissions. Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies; User Rights Assignment; Double Click on Allow Log On Locally and add your users