MIT Technology Review
- Newsletters

Preparing for AI-enabled cyberattacks
Artificial intelligence in the hands of cybercriminals poses an existential threat to organizations—IT security teams need “defensive AI” to fight back.
- MIT Technology Review Insights archive page
In association with Darktrace
Cyberattacks continue to grow in prevalence and sophistication. With the ability to disrupt business operations, wipe out critical data, and cause reputational damage, they pose an existential threat to businesses, critical services, and infrastructure. Today’s new wave of attacks is outsmarting and outpacing humans, and even starting to incorporate artificial intelligence (AI). What’s known as “offensive AI” will enable cybercriminals to direct targeted attacks at unprecedented speed and scale while flying under the radar of traditional, rule-based detection tools.
Some of the world’s largest and most trusted organizations have already fallen victim to damaging cyberattacks, undermining their ability to safeguard critical data. With offensive AI on the horizon, organizations need to adopt new defenses to fight back: the battle of algorithms has begun.
Download the full report
MIT Technology Review Insights, in association with AI cybersecurity company Darktrace, surveyed more than 300 C-level executives, directors, and managers worldwide to understand how they’re addressing the cyberthreats they’re up against—and how to use AI to help fight against them.
As it is, 60% of respondents report that human-driven responses to cyberattacks are failing to keep up with automated attacks, and as organizations gear up for a greater challenge, more sophisticated technologies are critical. In fact, an overwhelming majority of respondents—96%—report they’ve already begun to guard against AI-powered attacks, with some enabling AI defenses.
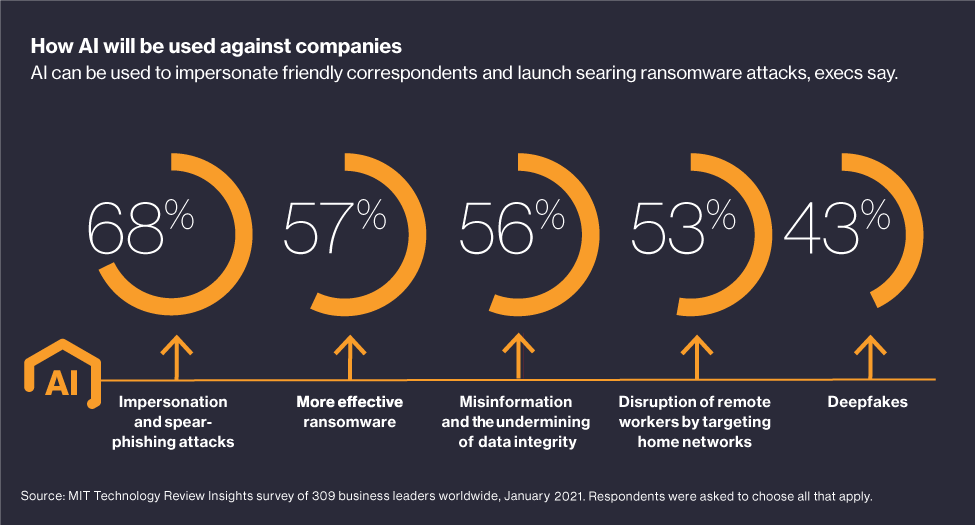
Offensive AI cyberattacks are daunting, and the technology is fast and smart. Consider deepfakes, one type of weaponized AI tool, which are fabricated images or videos depicting scenes or people that were never present, or even existed.
In January 2020, the FBI warned that deepfake technology had already reached the point where artificial personas could be created that could pass biometric tests. At the rate that AI neural networks are evolving, an FBI official said at the time, national security could be undermined by high-definition, fake videos created to mimic public figures so that they appear to be saying whatever words the video creators put in their manipulated mouths.
This is just one example of the technology being used for nefarious purposes. AI could, at some point, conduct cyberattacks autonomously, disguising their operations and blending in with regular activity. The technology is out there for anyone to use, including threat actors.
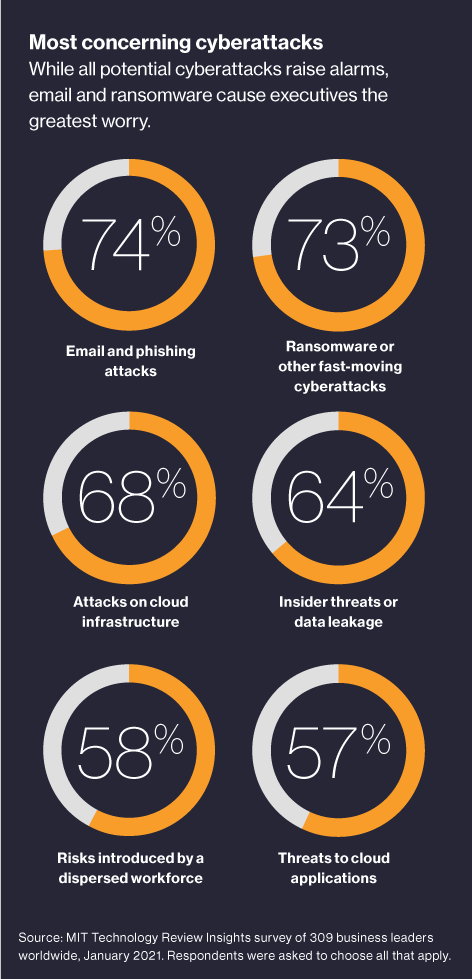
Offensive AI risks and developments in the cyberthreat landscape are redefining enterprise security, as humans already struggle to keep pace with advanced attacks. In particular, survey respondents reported that email and phishing attacks cause them the most angst, with nearly three quarters reporting that email threats are the most worrisome. That breaks down to 40% of respondents who report finding email and phishing attacks “very concerning,” while 34% call them “somewhat concerning.” It’s not surprising, as 94% of detected malware is still delivered by email. The traditional methods of stopping email-delivered threats rely on historical indicators—namely, previously seen attacks—as well as the ability of the recipient to spot the signs, both of which can be bypassed by sophisticated phishing incursions.
When offensive AI is thrown into the mix, “fake email” will be almost indistinguishable from genuine communications from trusted contacts.
How attackers exploit the headlines
The coronavirus pandemic presented a lucrative opportunity for cybercriminals. Email attackers in particular followed a long-established pattern: take advantage of the headlines of the day—along with the fear, uncertainty, greed, and curiosity they incite—to lure victims in what has become known as “fearware” attacks. With employees working remotely, without the security protocols of the office in place, organizations saw successful phishing attempts skyrocket. Max Heinemeyer, director of threat hunting for Darktrace, notes that when the pandemic hit, his team saw an immediate evolution of phishing emails. “We saw a lot of emails saying things like, ‘Click here to see which people in your area are infected,’” he says. When offices and universities started reopening last year, new scams emerged in lockstep, with emails offering “cheap or free covid-19 cleaning programs and tests,” says Heinemeyer.
There has also been an increase in ransomware, which has coincided with the surge in remote and hybrid work environments. “The bad guys know that now that everybody relies on remote work. If you get hit now, and you can’t provide remote access to your employee anymore, it’s game over,” he says. “Whereas maybe a year ago, people could still come into work, could work offline more, but it hurts much more now. And we see that the criminals have started to exploit that.”
What’s the common theme? Change, rapid change, and—in the case of the global shift to working from home—complexity. And that illustrates the problem with traditional cybersecurity, which relies on traditional, signature-based approaches: static defenses aren’t very good at adapting to change. Those approaches extrapolate from yesterday’s attacks to determine what tomorrow’s will look like. “How could you anticipate tomorrow’s phishing wave? It just doesn’t work,” Heinemeyer says.
Download the full report .
It’s time to retire the term “user”
The proliferation of AI means we need a new word.
- Taylor Majewski archive page
Modernizing data with strategic purpose
Data strategies and modernization initiatives misaligned with the overall business strategy—or too narrowly focused on AI—leave substantial business value on the table.
How ASML took over the chipmaking chessboard
MIT Technology Review sat down with outgoing CTO Martin van den Brink to talk about the company’s rise to dominance and the life and death of Moore’s Law.
- Mat Honan archive page
- James O'Donnell archive page
Why it’s so hard for China’s chip industry to become self-sufficient
Chip companies from the US and China are developing new materials to reduce reliance on a Japanese monopoly. It won’t be easy.
- Zeyi Yang archive page
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.
Doha Declaration
Education for justice.
- Agenda Day 1
- Agenda Day 2
- Agenda Day 3
- Agenda Day 4
- Registration
- Breakout Sessions for Primary and Secondary Level
- Breakout Sessions for Tertiary Level
- E4J Youth Competition
- India - Lockdown Learners
- Chuka, Break the Silence
- The Online Zoo
- I would like a community where ...
- Staying safe online
- Let's be respectful online
- We can all be heroes
- Respect for all
- We all have rights
- A mosaic of differences
- The right thing to do
- Solving ethical dilemmas
- UNODC-UNESCO Guide for Policymakers
- UNODC-UNESCO Handbooks for Teachers
- Justice Accelerators
Introduction
- Organized Crime
- Trafficking in Persons & Smuggling of Migrants
- Crime Prevention & Criminal Justice Reform
- Crime Prevention, Criminal Justice & SDGs
- UN Congress on Crime Prevention & Criminal Justice
- Commission on Crime Prevention & Criminal Justice
- Conference of the Parties to UNTOC
- Conference of the States Parties to UNCAC
- Rules for Simulating Crime Prevention & Criminal Justice Bodies
- Crime Prevention & Criminal Justice
- Engage with Us
- Contact Us about MUN
- Conferences Supporting E4J
- Cyberstrike
- Play for Integrity
- Running out of Time
- Zorbs Reloaded
- Developing a Rationale for Using the Video
- Previewing the Anti-Corruption Video
- Viewing the Video with a Purpose
- Post-viewing Activities
- Previewing the Firearms Video
- Rationale for Using the Video
- Previewing the Human Trafficking Video
- Previewing the Organized Crime Video
- Previewing the Video
- Criminal Justice & Crime Prevention
- Corruption & Integrity
- Human Trafficking & Migrant Smuggling
- Firearms Trafficking
- Terrorism & Violent Extremism
- Introduction & Learning Outcomes
- Corruption - Baseline Definition
- Effects of Corruption
- Deeper Meanings of Corruption
- Measuring Corruption
- Possible Class Structure
- Core Reading
- Advanced Reading
- Student Assessment
- Additional Teaching Tools
- Guidelines for Stand-Alone Course
- Appendix: How Corruption Affects the SDGs
- What is Governance?
- What is Good Governance?
- Corruption and Bad Governance
- Governance Reforms and Anti-Corruption
- Guidelines for Stand-alone Course
- Corruption and Democracy
- Corruption and Authoritarian Systems
- Hybrid Systems and Syndromes of Corruption
- The Deep Democratization Approach
- Political Parties and Political Finance
- Political Institution-building as a Means to Counter Corruption
- Manifestations and Consequences of Public Sector Corruption
- Causes of Public Sector Corruption
- Theories that Explain Corruption
- Corruption in Public Procurement
- Corruption in State-Owned Enterprises
- Responses to Public Sector Corruption
- Preventing Public Sector Corruption
- Forms & Manifestations of Private Sector Corruption
- Consequences of Private Sector Corruption
- Causes of Private Sector Corruption
- Responses to Private Sector Corruption
- Preventing Private Sector Corruption
- Collective Action & Public-Private Partnerships against Corruption
- Transparency as a Precondition
- Detection Mechanisms - Auditing and Reporting
- Whistle-blowing Systems and Protections
- Investigation of Corruption
- Introduction and Learning Outcomes
- Brief background on the human rights system
- Overview of the corruption-human rights nexus
- Impact of corruption on specific human rights
- Approaches to assessing the corruption-human rights nexus
- Human-rights based approach
- Defining sex, gender and gender mainstreaming
- Gender differences in corruption
- Theories explaining the gender–corruption nexus
- Gendered impacts of corruption
- Anti-corruption and gender mainstreaming
- Manifestations of corruption in education
- Costs of corruption in education
- Causes of corruption in education
- Fighting corruption in education
- Core terms and concepts
- The role of citizens in fighting corruption
- The role, risks and challenges of CSOs fighting corruption
- The role of the media in fighting corruption
- Access to information: a condition for citizen participation
- ICT as a tool for citizen participation in anti-corruption efforts
- Government obligations to ensure citizen participation in anti-corruption efforts
- Teaching Guide
- Brief History of Terrorism
- 19th Century Terrorism
- League of Nations & Terrorism
- United Nations & Terrorism
- Terrorist Victimization
- Exercises & Case Studies
- Radicalization & Violent Extremism
- Preventing & Countering Violent Extremism
- Drivers of Violent Extremism
- International Approaches to PVE &CVE
- Regional & Multilateral Approaches
- Defining Rule of Law
- UN Global Counter-Terrorism Strategy
- International Cooperation & UN CT Strategy
- Legal Sources & UN CT Strategy
- Regional & National Approaches
- International Legal Frameworks
- International Human Rights Law
- International Humanitarian Law
- International Refugee Law
- Current Challenges to International Legal Framework
- Defining Terrorism
- Criminal Justice Responses
- Treaty-based Crimes of Terrorism
- Core International Crimes
- International Courts and Tribunals
- African Region
- Inter-American Region
- Asian Region
- European Region
- Middle East & Gulf Regions
- Core Principles of IHL
- Categorization of Armed Conflict
- Classification of Persons
- IHL, Terrorism & Counter-Terrorism
- Relationship between IHL & intern. human rights law
- Limitations Permitted by Human Rights Law
- Derogation during Public Emergency
- Examples of States of Emergency & Derogations
- International Human Rights Instruments
- Regional Human Rights Instruments
- Extra-territorial Application of Right to Life
- Arbitrary Deprivation of Life
- Death Penalty
- Enforced Disappearances
- Armed Conflict Context
- International Covenant on Civil and Political Rights
- Convention against Torture et al.
- International Legal Framework
- Key Contemporary Issues
- Investigative Phase
- Trial & Sentencing Phase
- Armed Conflict
- Case Studies
- Special Investigative Techniques
- Surveillance & Interception of Communications
- Privacy & Intelligence Gathering in Armed Conflict
- Accountability & Oversight of Intelligence Gathering
- Principle of Non-Discrimination
- Freedom of Religion
- Freedom of Expression
- Freedom of Assembly
- Freedom of Association
- Fundamental Freedoms
- Definition of 'Victim'
- Effects of Terrorism
- Access to Justice
- Recognition of the Victim
- Human Rights Instruments
- Criminal Justice Mechanisms
- Instruments for Victims of Terrorism
- National Approaches
- Key Challenges in Securing Reparation
- Topic 1. Contemporary issues relating to conditions conducive both to the spread of terrorism and the rule of law
- Topic 2. Contemporary issues relating to the right to life
- Topic 3. Contemporary issues relating to foreign terrorist fighters
- Topic 4. Contemporary issues relating to non-discrimination and fundamental freedoms
- Module 16: Linkages between Organized Crime and Terrorism
- Thematic Areas
- Content Breakdown
- Module Adaptation & Design Guidelines
- Teaching Methods
- Acknowledgements
- 1. Introducing United Nations Standards & Norms on CPCJ vis-à-vis International Law
- 2. Scope of United Nations Standards & Norms on CPCJ
- 3. United Nations Standards & Norms on CPCJ in Operation
- 1. Definition of Crime Prevention
- 2. Key Crime Prevention Typologies
- 2. (cont.) Tonry & Farrington’s Typology
- 3. Crime Problem-Solving Approaches
- 4. What Works
- United Nations Entities
- Regional Crime Prevention Councils/Institutions
- Key Clearinghouses
- Systematic Reviews
- 1. Introduction to International Standards & Norms
- 2. Identifying the Need for Legal Aid
- 3. Key Components of the Right of Access to Legal Aid
- 4. Access to Legal Aid for Those with Specific Needs
- 5. Models for Governing, Administering and Funding Legal Aid
- 6. Models for Delivering Legal Aid Services
- 7. Roles and Responsibilities of Legal Aid Providers
- 8. Quality Assurance and Legal Aid Services
- 1. Context for Use of Force by Law Enforcement Officials
- 2. Legal Framework
- 3. General Principles of Use of Force in Law Enforcement
- 4. Use of Firearms
- 5. Use of “Less-Lethal” Weapons
- 6. Protection of Especially Vulnerable Groups
- 7. Use of Force during Assemblies
- 1. Policing in democracies & need for accountability, integrity, oversight
- 2. Key mechanisms & actors in police accountability, oversight
- 3. Crosscutting & contemporary issues in police accountability
- 1. Introducing Aims of Punishment, Imprisonment & Prison Reform
- 2. Current Trends, Challenges & Human Rights
- 3. Towards Humane Prisons & Alternative Sanctions
- 1. Aims and Significance of Alternatives to Imprisonment
- 2. Justifying Punishment in the Community
- 3. Pretrial Alternatives
- 4. Post Trial Alternatives
- 5. Evaluating Alternatives
- 1. Concept, Values and Origin of Restorative Justice
- 2. Overview of Restorative Justice Processes
- 3. How Cost Effective is Restorative Justice?
- 4. Issues in Implementing Restorative Justice
- 1. Gender-Based Discrimination & Women in Conflict with the Law
- 2. Vulnerabilities of Girls in Conflict with the Law
- 3. Discrimination and Violence against LGBTI Individuals
- 4. Gender Diversity in Criminal Justice Workforce
- 1. Ending Violence against Women
- 2. Human Rights Approaches to Violence against Women
- 3. Who Has Rights in this Situation?
- 4. What about the Men?
- 5. Local, Regional & Global Solutions to Violence against Women & Girls
- 1. Understanding the Concept of Victims of Crime
- 2. Impact of Crime, including Trauma
- 3. Right of Victims to Adequate Response to their Needs
- 4. Collecting Victim Data
- 5. Victims and their Participation in Criminal Justice Process
- 6. Victim Services: Institutional and Non-Governmental Organizations
- 7. Outlook on Current Developments Regarding Victims
- 8. Victims of Crime and International Law
- 1. The Many Forms of Violence against Children
- 2. The Impact of Violence on Children
- 3. States' Obligations to Prevent VAC and Protect Child Victims
- 4. Improving the Prevention of Violence against Children
- 5. Improving the Criminal Justice Response to VAC
- 6. Addressing Violence against Children within the Justice System
- 1. The Role of the Justice System
- 2. Convention on the Rights of the Child & International Legal Framework on Children's Rights
- 3. Justice for Children
- 4. Justice for Children in Conflict with the Law
- 5. Realizing Justice for Children
- 1a. Judicial Independence as Fundamental Value of Rule of Law & of Constitutionalism
- 1b. Main Factors Aimed at Securing Judicial Independence
- 2a. Public Prosecutors as ‘Gate Keepers’ of Criminal Justice
- 2b. Institutional and Functional Role of Prosecutors
- 2c. Other Factors Affecting the Role of Prosecutors
- Basics of Computing
- Global Connectivity and Technology Usage Trends
- Cybercrime in Brief
- Cybercrime Trends
- Cybercrime Prevention
- Offences against computer data and systems
- Computer-related offences
- Content-related offences
- The Role of Cybercrime Law
- Harmonization of Laws
- International and Regional Instruments
- International Human Rights and Cybercrime Law
- Digital Evidence
- Digital Forensics
- Standards and Best Practices for Digital Forensics
- Reporting Cybercrime
- Who Conducts Cybercrime Investigations?
- Obstacles to Cybercrime Investigations
- Knowledge Management
- Legal and Ethical Obligations
- Handling of Digital Evidence
- Digital Evidence Admissibility
- Sovereignty and Jurisdiction
- Formal International Cooperation Mechanisms
- Informal International Cooperation Mechanisms
- Data Retention, Preservation and Access
- Challenges Relating to Extraterritorial Evidence
- National Capacity and International Cooperation
- Internet Governance
- Cybersecurity Strategies: Basic Features
- National Cybersecurity Strategies
- International Cooperation on Cybersecurity Matters
- Cybersecurity Posture
- Assets, Vulnerabilities and Threats
- Vulnerability Disclosure
- Cybersecurity Measures and Usability
- Situational Crime Prevention
- Incident Detection, Response, Recovery & Preparedness
- Privacy: What it is and Why it is Important
- Privacy and Security
- Cybercrime that Compromises Privacy
- Data Protection Legislation
- Data Breach Notification Laws
- Enforcement of Privacy and Data Protection Laws
- Intellectual Property: What it is
- Types of Intellectual Property
- Causes for Cyber-Enabled Copyright & Trademark Offences
- Protection & Prevention Efforts
- Online Child Sexual Exploitation and Abuse
- Cyberstalking and Cyberharassment
- Cyberbullying
- Gender-Based Interpersonal Cybercrime
- Interpersonal Cybercrime Prevention
- Cyber Organized Crime: What is it?
- Conceptualizing Organized Crime & Defining Actors Involved
- Criminal Groups Engaging in Cyber Organized Crime
- Cyber Organized Crime Activities
- Preventing & Countering Cyber Organized Crime
- Cyberespionage
- Cyberterrorism
- Cyberwarfare
- Information Warfare, Disinformation & Electoral Fraud
- Responses to Cyberinterventions
- Framing the Issue of Firearms
- Direct Impact of Firearms
- Indirect Impacts of Firearms on States or Communities
- International and National Responses
- Typology and Classification of Firearms
- Common Firearms Types
- 'Other' Types of Firearms
- Parts and Components
- History of the Legitimate Arms Market
- Need for a Legitimate Market
- Key Actors in the Legitimate Market
- Authorized & Unauthorized Arms Transfers
- Illegal Firearms in Social, Cultural & Political Context
- Supply, Demand & Criminal Motivations
- Larger Scale Firearms Trafficking Activities
- Smaller Scale Trafficking Activities
- Sources of Illicit Firearms
- Consequences of Illicit Markets
- International Public Law & Transnational Law
- International Instruments with Global Outreach
- Commonalities, Differences & Complementarity between Global Instruments
- Tools to Support Implementation of Global Instruments
- Other United Nations Processes
- The Sustainable Development Goals
- Multilateral & Regional Instruments
- Scope of National Firearms Regulations
- National Firearms Strategies & Action Plans
- Harmonization of National Legislation with International Firearms Instruments
- Assistance for Development of National Firearms Legislation
- Firearms Trafficking as a Cross-Cutting Element
- Organized Crime and Organized Criminal Groups
- Criminal Gangs
- Terrorist Groups
- Interconnections between Organized Criminal Groups & Terrorist Groups
- Gangs - Organized Crime & Terrorism: An Evolving Continuum
- International Response
- International and National Legal Framework
- Firearms Related Offences
- Role of Law Enforcement
- Firearms as Evidence
- Use of Special Investigative Techniques
- International Cooperation and Information Exchange
- Prosecution and Adjudication of Firearms Trafficking
- Teaching Methods & Principles
- Ethical Learning Environments
- Overview of Modules
- Module Adaption & Design Guidelines
- Table of Exercises
- Basic Terms
- Forms of Gender Discrimination
- Ethics of Care
- Case Studies for Professional Ethics
- Case Studies for Role Morality
- Additional Exercises
- Defining Organized Crime
- Definition in Convention
- Similarities & Differences
- Activities, Organization, Composition
- Thinking Critically Through Fiction
- Excerpts of Legislation
- Research & Independent Study Questions
- Legal Definitions of Organized Crimes
- Criminal Association
- Definitions in the Organized Crime Convention
- Criminal Organizations and Enterprise Laws
- Enabling Offence: Obstruction of Justice
- Drug Trafficking
- Wildlife & Forest Crime
- Counterfeit Products Trafficking
- Falsified Medical Products
- Trafficking in Cultural Property
- Trafficking in Persons
- Case Studies & Exercises
- Extortion Racketeering
- Loansharking
- Links to Corruption
- Bribery versus Extortion
- Money-Laundering
- Liability of Legal Persons
- How much Organized Crime is there?
- Alternative Ways for Measuring
- Measuring Product Markets
- Risk Assessment
- Key Concepts of Risk Assessment
- Risk Assessment of Organized Crime Groups
- Risk Assessment of Product Markets
- Risk Assessment in Practice
- Positivism: Environmental Influences
- Classical: Pain-Pleasure Decisions
- Structural Factors
- Ethical Perspective
- Crime Causes & Facilitating Factors
- Models and Structure
- Hierarchical Model
- Local, Cultural Model
- Enterprise or Business Model
- Groups vs Activities
- Networked Structure
- Jurisdiction
- Investigators of Organized Crime
- Controlled Deliveries
- Physical & Electronic Surveillance
- Undercover Operations
- Financial Analysis
- Use of Informants
- Rights of Victims & Witnesses
- Role of Prosecutors
- Adversarial vs Inquisitorial Legal Systems
- Mitigating Punishment
- Granting Immunity from Prosecution
- Witness Protection
- Aggravating & Mitigating Factors
- Sentencing Options
- Alternatives to Imprisonment
- Death Penalty & Organized Crime
- Backgrounds of Convicted Offenders
- Confiscation
- Confiscation in Practice
- Mutual Legal Assistance (MLA)
- Extradition
- Transfer of Criminal Proceedings
- Transfer of Sentenced Persons
- Module 12: Prevention of Organized Crime
- Adoption of Organized Crime Convention
- Historical Context
- Features of the Convention
- Related international instruments
- Conference of the Parties
- Roles of Participants
- Structure and Flow
- Recommended Topics
- Background Materials
- What is Sex / Gender / Intersectionality?
- Knowledge about Gender in Organized Crime
- Gender and Organized Crime
- Gender and Different Types of Organized Crime
- Definitions and Terminology
- Organized crime and Terrorism - International Legal Framework
- International Terrorism-related Conventions
- UNSC Resolutions on Terrorism
- Organized Crime Convention and its Protocols
- Theoretical Frameworks on Linkages between Organized Crime and Terrorism
- Typologies of Criminal Behaviour Associated with Terrorism
- Terrorism and Drug Trafficking
- Terrorism and Trafficking in Weapons
- Terrorism, Crime and Trafficking in Cultural Property
- Trafficking in Persons and Terrorism
- Intellectual Property Crime and Terrorism
- Kidnapping for Ransom and Terrorism
- Exploitation of Natural Resources and Terrorism
- Review and Assessment Questions
- Research and Independent Study Questions
- Criminalization of Smuggling of Migrants
- UNTOC & the Protocol against Smuggling of Migrants
- Offences under the Protocol
- Financial & Other Material Benefits
- Aggravating Circumstances
- Criminal Liability
- Non-Criminalization of Smuggled Migrants
- Scope of the Protocol
- Humanitarian Exemption
- Migrant Smuggling v. Irregular Migration
- Migrant Smuggling vis-a-vis Other Crime Types
- Other Resources
- Assistance and Protection in the Protocol
- International Human Rights and Refugee Law
- Vulnerable groups
- Positive and Negative Obligations of the State
- Identification of Smuggled Migrants
- Participation in Legal Proceedings
- Role of Non-Governmental Organizations
- Smuggled Migrants & Other Categories of Migrants
- Short-, Mid- and Long-Term Measures
- Criminal Justice Reponse: Scope
- Investigative & Prosecutorial Approaches
- Different Relevant Actors & Their Roles
- Testimonial Evidence
- Financial Investigations
- Non-Governmental Organizations
- ‘Outside the Box’ Methodologies
- Intra- and Inter-Agency Coordination
- Admissibility of Evidence
- International Cooperation
- Exchange of Information
- Non-Criminal Law Relevant to Smuggling of Migrants
- Administrative Approach
- Complementary Activities & Role of Non-criminal Justice Actors
- Macro-Perspective in Addressing Smuggling of Migrants
- Human Security
- International Aid and Cooperation
- Migration & Migrant Smuggling
- Mixed Migration Flows
- Social Politics of Migrant Smuggling
- Vulnerability
- Profile of Smugglers
- Role of Organized Criminal Groups
- Humanitarianism, Security and Migrant Smuggling
- Crime of Trafficking in Persons
- The Issue of Consent
- The Purpose of Exploitation
- The abuse of a position of vulnerability
- Indicators of Trafficking in Persons
- Distinction between Trafficking in Persons and Other Crimes
- Misconceptions Regarding Trafficking in Persons
- Root Causes
- Supply Side Prevention Strategies
- Demand Side Prevention Strategies
- Role of the Media
- Safe Migration Channels
- Crime Prevention Strategies
- Monitoring, Evaluating & Reporting on Effectiveness of Prevention
- Trafficked Persons as Victims
- Protection under the Protocol against Trafficking in Persons
- Broader International Framework
- State Responsibility for Trafficking in Persons
- Identification of Victims
- Principle of Non-Criminalization of Victims
- Criminal Justice Duties Imposed on States
- Role of the Criminal Justice System
- Current Low Levels of Prosecutions and Convictions
- Challenges to an Effective Criminal Justice Response
- Rights of Victims to Justice and Protection
- Potential Strategies to “Turn the Tide”
- State Cooperation with Civil Society
- Civil Society Actors
- The Private Sector
- Comparing SOM and TIP
- Differences and Commonalities
- Vulnerability and Continuum between SOM & TIP
- Labour Exploitation
- Forced Marriage
- Other Examples
- Children on the Move
- Protecting Smuggled and Trafficked Children
- Protection in Practice
- Children Alleged as Having Committed Smuggling or Trafficking Offences
- Basic Terms - Gender and Gender Stereotypes
- International Legal Frameworks and Definitions of TIP and SOM
- Global Overview on TIP and SOM
- Gender and Migration
- Key Debates in the Scholarship on TIP and SOM
- Gender and TIP and SOM Offenders
- Responses to TIP and SOM
- Use of Technology to Facilitate TIP and SOM
- Technology Facilitating Trafficking in Persons
- Technology in Smuggling of Migrants
- Using Technology to Prevent and Combat TIP and SOM
- Privacy and Data Concerns
- Emerging Trends
- Demand and Consumption
- Supply and Demand
- Implications of Wildlife Trafficking
- Legal and Illegal Markets
- Perpetrators and their Networks
- Locations and Activities relating to Wildlife Trafficking
- Environmental Protection & Conservation
- CITES & the International Trade in Endangered Species
- Organized Crime & Corruption
- Animal Welfare
- Criminal Justice Actors and Agencies
- Criminalization of Wildlife Trafficking
- Challenges for Law Enforcement
- Investigation Measures and Detection Methods
- Prosecution and Judiciary
- Wild Flora as the Target of Illegal Trafficking
- Purposes for which Wild Flora is Illegally Targeted
- How is it Done and Who is Involved?
- Consequences of Harms to Wild Flora
- Terminology
- Background: Communities and conservation: A history of disenfranchisement
- Incentives for communities to get involved in illegal wildlife trafficking: the cost of conservation
- Incentives to participate in illegal wildlife, logging and fishing economies
- International and regional responses that fight wildlife trafficking while supporting IPLCs
- Mechanisms for incentivizing community conservation and reducing wildlife trafficking
- Critiques of community engagement
- Other challenges posed by wildlife trafficking that affect local populations
- Global Podcast Series
- Apr. 2021: Call for Expressions of Interest: Online training for academics from francophone Africa
- Feb. 2021: Series of Seminars for Universities of Central Asia
- Dec. 2020: UNODC and TISS Conference on Access to Justice to End Violence
- Nov. 2020: Expert Workshop for University Lecturers and Trainers from the Commonwealth of Independent States
- Oct. 2020: E4J Webinar Series: Youth Empowerment through Education for Justice
- Interview: How to use E4J's tool in teaching on TIP and SOM
- E4J-Open University Online Training-of-Trainers Course
- Teaching Integrity and Ethics Modules: Survey Results
- Grants Programmes
- E4J MUN Resource Guide
- Library of Resources
Module 1: Introduction to Cybercrime
- {{item.name}} ({{item.items.length}}) items
- Add new list
E4J University Module Series: Cybercrime
Introduction and learning outcomes.
- Basics of computing
- Global connectivity and technology usage trends
- Cybercrime in brief
- Cybercrime trends
- Cybercrime prevention
Possible class structure
Core reading, advanced reading, student assessment, additional teaching tools.
- First published in May 2019, updated in February 2020
This module is a resource for lecturers
Information and communication technology (ICT) has transformed the way in which individuals conduct business, purchase goods and services, send and receive money, communicate, share information, interact with people, and form and cultivate relationships with others. This transformation, as well as the world's ever-increasing use of and dependency on ICT, creates vulnerabilities to criminals and other malicious actors targeting ICT and/or using ICT to commit crime.
This Module provides an introduction to key concepts relating to cybercrime, what cybercrime is, Internet, technology and cybercrime trends, and the technical, legal, ethical, and operational challenges related to cybercrime and cybercrime prevention. The reading material selected for this Module provides an overview of key concepts, basic terms, and definitions, and a general introduction to cybercrime, its challenges, and prevention.
Learning outcomes
- Define and describe basic concepts relating to computing
- Describe and assess global connectivity and technology usage trends
- Define cybercrime and discuss why cybercrime is scientifically studied
- Discuss and analyse cybercrime trends
- Identify, examine, and analyse the technical, legal, ethical, and operational challenges relating to the investigation and prevention of cybercrime
Next: Key issues
Back to top, supported by the state of qatar, 60 years crime congress.
- Search Menu
- Browse content in Arts and Humanities
- Browse content in Archaeology
- Anglo-Saxon and Medieval Archaeology
- Archaeological Methodology and Techniques
- Archaeology by Region
- Archaeology of Religion
- Archaeology of Trade and Exchange
- Biblical Archaeology
- Contemporary and Public Archaeology
- Environmental Archaeology
- Historical Archaeology
- History and Theory of Archaeology
- Industrial Archaeology
- Landscape Archaeology
- Mortuary Archaeology
- Prehistoric Archaeology
- Underwater Archaeology
- Urban Archaeology
- Zooarchaeology
- Browse content in Architecture
- Architectural Structure and Design
- History of Architecture
- Residential and Domestic Buildings
- Theory of Architecture
- Browse content in Art
- Art Subjects and Themes
- History of Art
- Industrial and Commercial Art
- Theory of Art
- Biographical Studies
- Byzantine Studies
- Browse content in Classical Studies
- Classical History
- Classical Philosophy
- Classical Mythology
- Classical Literature
- Classical Reception
- Classical Art and Architecture
- Classical Oratory and Rhetoric
- Greek and Roman Epigraphy
- Greek and Roman Law
- Greek and Roman Papyrology
- Greek and Roman Archaeology
- Late Antiquity
- Religion in the Ancient World
- Digital Humanities
- Browse content in History
- Colonialism and Imperialism
- Diplomatic History
- Environmental History
- Genealogy, Heraldry, Names, and Honours
- Genocide and Ethnic Cleansing
- Historical Geography
- History by Period
- History of Emotions
- History of Agriculture
- History of Education
- History of Gender and Sexuality
- Industrial History
- Intellectual History
- International History
- Labour History
- Legal and Constitutional History
- Local and Family History
- Maritime History
- Military History
- National Liberation and Post-Colonialism
- Oral History
- Political History
- Public History
- Regional and National History
- Revolutions and Rebellions
- Slavery and Abolition of Slavery
- Social and Cultural History
- Theory, Methods, and Historiography
- Urban History
- World History
- Browse content in Language Teaching and Learning
- Language Learning (Specific Skills)
- Language Teaching Theory and Methods
- Browse content in Linguistics
- Applied Linguistics
- Cognitive Linguistics
- Computational Linguistics
- Forensic Linguistics
- Grammar, Syntax and Morphology
- Historical and Diachronic Linguistics
- History of English
- Language Acquisition
- Language Evolution
- Language Reference
- Language Variation
- Language Families
- Lexicography
- Linguistic Anthropology
- Linguistic Theories
- Linguistic Typology
- Phonetics and Phonology
- Psycholinguistics
- Sociolinguistics
- Translation and Interpretation
- Writing Systems
- Browse content in Literature
- Bibliography
- Children's Literature Studies
- Literary Studies (Asian)
- Literary Studies (European)
- Literary Studies (Eco-criticism)
- Literary Studies (Romanticism)
- Literary Studies (American)
- Literary Studies (Modernism)
- Literary Studies - World
- Literary Studies (1500 to 1800)
- Literary Studies (19th Century)
- Literary Studies (20th Century onwards)
- Literary Studies (African American Literature)
- Literary Studies (British and Irish)
- Literary Studies (Early and Medieval)
- Literary Studies (Fiction, Novelists, and Prose Writers)
- Literary Studies (Gender Studies)
- Literary Studies (Graphic Novels)
- Literary Studies (History of the Book)
- Literary Studies (Plays and Playwrights)
- Literary Studies (Poetry and Poets)
- Literary Studies (Postcolonial Literature)
- Literary Studies (Queer Studies)
- Literary Studies (Science Fiction)
- Literary Studies (Travel Literature)
- Literary Studies (War Literature)
- Literary Studies (Women's Writing)
- Literary Theory and Cultural Studies
- Mythology and Folklore
- Shakespeare Studies and Criticism
- Browse content in Media Studies
- Browse content in Music
- Applied Music
- Dance and Music
- Ethics in Music
- Ethnomusicology
- Gender and Sexuality in Music
- Medicine and Music
- Music Cultures
- Music and Religion
- Music and Media
- Music and Culture
- Music Education and Pedagogy
- Music Theory and Analysis
- Musical Scores, Lyrics, and Libretti
- Musical Structures, Styles, and Techniques
- Musicology and Music History
- Performance Practice and Studies
- Race and Ethnicity in Music
- Sound Studies
- Browse content in Performing Arts
- Browse content in Philosophy
- Aesthetics and Philosophy of Art
- Epistemology
- Feminist Philosophy
- History of Western Philosophy
- Metaphysics
- Moral Philosophy
- Non-Western Philosophy
- Philosophy of Science
- Philosophy of Language
- Philosophy of Mind
- Philosophy of Perception
- Philosophy of Action
- Philosophy of Law
- Philosophy of Religion
- Philosophy of Mathematics and Logic
- Practical Ethics
- Social and Political Philosophy
- Browse content in Religion
- Biblical Studies
- Christianity
- East Asian Religions
- History of Religion
- Judaism and Jewish Studies
- Qumran Studies
- Religion and Education
- Religion and Health
- Religion and Politics
- Religion and Science
- Religion and Law
- Religion and Art, Literature, and Music
- Religious Studies
- Browse content in Society and Culture
- Cookery, Food, and Drink
- Cultural Studies
- Customs and Traditions
- Ethical Issues and Debates
- Hobbies, Games, Arts and Crafts
- Lifestyle, Home, and Garden
- Natural world, Country Life, and Pets
- Popular Beliefs and Controversial Knowledge
- Sports and Outdoor Recreation
- Technology and Society
- Travel and Holiday
- Visual Culture
- Browse content in Law
- Arbitration
- Browse content in Company and Commercial Law
- Commercial Law
- Company Law
- Browse content in Comparative Law
- Systems of Law
- Competition Law
- Browse content in Constitutional and Administrative Law
- Government Powers
- Judicial Review
- Local Government Law
- Military and Defence Law
- Parliamentary and Legislative Practice
- Construction Law
- Contract Law
- Browse content in Criminal Law
- Criminal Procedure
- Criminal Evidence Law
- Sentencing and Punishment
- Employment and Labour Law
- Environment and Energy Law
- Browse content in Financial Law
- Banking Law
- Insolvency Law
- History of Law
- Human Rights and Immigration
- Intellectual Property Law
- Browse content in International Law
- Private International Law and Conflict of Laws
- Public International Law
- IT and Communications Law
- Jurisprudence and Philosophy of Law
- Law and Politics
- Law and Society
- Browse content in Legal System and Practice
- Courts and Procedure
- Legal Skills and Practice
- Primary Sources of Law
- Regulation of Legal Profession
- Medical and Healthcare Law
- Browse content in Policing
- Criminal Investigation and Detection
- Police and Security Services
- Police Procedure and Law
- Police Regional Planning
- Browse content in Property Law
- Personal Property Law
- Study and Revision
- Terrorism and National Security Law
- Browse content in Trusts Law
- Wills and Probate or Succession
- Browse content in Medicine and Health
- Browse content in Allied Health Professions
- Arts Therapies
- Clinical Science
- Dietetics and Nutrition
- Occupational Therapy
- Operating Department Practice
- Physiotherapy
- Radiography
- Speech and Language Therapy
- Browse content in Anaesthetics
- General Anaesthesia
- Neuroanaesthesia
- Browse content in Clinical Medicine
- Acute Medicine
- Cardiovascular Medicine
- Clinical Genetics
- Clinical Pharmacology and Therapeutics
- Dermatology
- Endocrinology and Diabetes
- Gastroenterology
- Genito-urinary Medicine
- Geriatric Medicine
- Infectious Diseases
- Medical Toxicology
- Medical Oncology
- Pain Medicine
- Palliative Medicine
- Rehabilitation Medicine
- Respiratory Medicine and Pulmonology
- Rheumatology
- Sleep Medicine
- Sports and Exercise Medicine
- Clinical Neuroscience
- Community Medical Services
- Critical Care
- Emergency Medicine
- Forensic Medicine
- Haematology
- History of Medicine
- Browse content in Medical Dentistry
- Oral and Maxillofacial Surgery
- Paediatric Dentistry
- Restorative Dentistry and Orthodontics
- Surgical Dentistry
- Browse content in Medical Skills
- Clinical Skills
- Communication Skills
- Nursing Skills
- Surgical Skills
- Medical Ethics
- Medical Statistics and Methodology
- Browse content in Neurology
- Clinical Neurophysiology
- Neuropathology
- Nursing Studies
- Browse content in Obstetrics and Gynaecology
- Gynaecology
- Occupational Medicine
- Ophthalmology
- Otolaryngology (ENT)
- Browse content in Paediatrics
- Neonatology
- Browse content in Pathology
- Chemical Pathology
- Clinical Cytogenetics and Molecular Genetics
- Histopathology
- Medical Microbiology and Virology
- Patient Education and Information
- Browse content in Pharmacology
- Psychopharmacology
- Browse content in Popular Health
- Caring for Others
- Complementary and Alternative Medicine
- Self-help and Personal Development
- Browse content in Preclinical Medicine
- Cell Biology
- Molecular Biology and Genetics
- Reproduction, Growth and Development
- Primary Care
- Professional Development in Medicine
- Browse content in Psychiatry
- Addiction Medicine
- Child and Adolescent Psychiatry
- Forensic Psychiatry
- Learning Disabilities
- Old Age Psychiatry
- Psychotherapy
- Browse content in Public Health and Epidemiology
- Epidemiology
- Public Health
- Browse content in Radiology
- Clinical Radiology
- Interventional Radiology
- Nuclear Medicine
- Radiation Oncology
- Reproductive Medicine
- Browse content in Surgery
- Cardiothoracic Surgery
- Gastro-intestinal and Colorectal Surgery
- General Surgery
- Neurosurgery
- Paediatric Surgery
- Peri-operative Care
- Plastic and Reconstructive Surgery
- Surgical Oncology
- Transplant Surgery
- Trauma and Orthopaedic Surgery
- Vascular Surgery
- Browse content in Science and Mathematics
- Browse content in Biological Sciences
- Aquatic Biology
- Biochemistry
- Bioinformatics and Computational Biology
- Developmental Biology
- Ecology and Conservation
- Evolutionary Biology
- Genetics and Genomics
- Microbiology
- Molecular and Cell Biology
- Natural History
- Plant Sciences and Forestry
- Research Methods in Life Sciences
- Structural Biology
- Systems Biology
- Zoology and Animal Sciences
- Browse content in Chemistry
- Analytical Chemistry
- Computational Chemistry
- Crystallography
- Environmental Chemistry
- Industrial Chemistry
- Inorganic Chemistry
- Materials Chemistry
- Medicinal Chemistry
- Mineralogy and Gems
- Organic Chemistry
- Physical Chemistry
- Polymer Chemistry
- Study and Communication Skills in Chemistry
- Theoretical Chemistry
- Browse content in Computer Science
- Artificial Intelligence
- Computer Architecture and Logic Design
- Game Studies
- Human-Computer Interaction
- Mathematical Theory of Computation
- Programming Languages
- Software Engineering
- Systems Analysis and Design
- Virtual Reality
- Browse content in Computing
- Business Applications
- Computer Security
- Computer Games
- Computer Networking and Communications
- Digital Lifestyle
- Graphical and Digital Media Applications
- Operating Systems
- Browse content in Earth Sciences and Geography
- Atmospheric Sciences
- Environmental Geography
- Geology and the Lithosphere
- Maps and Map-making
- Meteorology and Climatology
- Oceanography and Hydrology
- Palaeontology
- Physical Geography and Topography
- Regional Geography
- Soil Science
- Urban Geography
- Browse content in Engineering and Technology
- Agriculture and Farming
- Biological Engineering
- Civil Engineering, Surveying, and Building
- Electronics and Communications Engineering
- Energy Technology
- Engineering (General)
- Environmental Science, Engineering, and Technology
- History of Engineering and Technology
- Mechanical Engineering and Materials
- Technology of Industrial Chemistry
- Transport Technology and Trades
- Browse content in Environmental Science
- Applied Ecology (Environmental Science)
- Conservation of the Environment (Environmental Science)
- Environmental Sustainability
- Environmentalist Thought and Ideology (Environmental Science)
- Management of Land and Natural Resources (Environmental Science)
- Natural Disasters (Environmental Science)
- Nuclear Issues (Environmental Science)
- Pollution and Threats to the Environment (Environmental Science)
- Social Impact of Environmental Issues (Environmental Science)
- History of Science and Technology
- Browse content in Materials Science
- Ceramics and Glasses
- Composite Materials
- Metals, Alloying, and Corrosion
- Nanotechnology
- Browse content in Mathematics
- Applied Mathematics
- Biomathematics and Statistics
- History of Mathematics
- Mathematical Education
- Mathematical Finance
- Mathematical Analysis
- Numerical and Computational Mathematics
- Probability and Statistics
- Pure Mathematics
- Browse content in Neuroscience
- Cognition and Behavioural Neuroscience
- Development of the Nervous System
- Disorders of the Nervous System
- History of Neuroscience
- Invertebrate Neurobiology
- Molecular and Cellular Systems
- Neuroendocrinology and Autonomic Nervous System
- Neuroscientific Techniques
- Sensory and Motor Systems
- Browse content in Physics
- Astronomy and Astrophysics
- Atomic, Molecular, and Optical Physics
- Biological and Medical Physics
- Classical Mechanics
- Computational Physics
- Condensed Matter Physics
- Electromagnetism, Optics, and Acoustics
- History of Physics
- Mathematical and Statistical Physics
- Measurement Science
- Nuclear Physics
- Particles and Fields
- Plasma Physics
- Quantum Physics
- Relativity and Gravitation
- Semiconductor and Mesoscopic Physics
- Browse content in Psychology
- Affective Sciences
- Clinical Psychology
- Cognitive Psychology
- Cognitive Neuroscience
- Criminal and Forensic Psychology
- Developmental Psychology
- Educational Psychology
- Evolutionary Psychology
- Health Psychology
- History and Systems in Psychology
- Music Psychology
- Neuropsychology
- Organizational Psychology
- Psychological Assessment and Testing
- Psychology of Human-Technology Interaction
- Psychology Professional Development and Training
- Research Methods in Psychology
- Social Psychology
- Browse content in Social Sciences
- Browse content in Anthropology
- Anthropology of Religion
- Human Evolution
- Medical Anthropology
- Physical Anthropology
- Regional Anthropology
- Social and Cultural Anthropology
- Theory and Practice of Anthropology
- Browse content in Business and Management
- Business Strategy
- Business Ethics
- Business History
- Business and Government
- Business and Technology
- Business and the Environment
- Comparative Management
- Corporate Governance
- Corporate Social Responsibility
- Entrepreneurship
- Health Management
- Human Resource Management
- Industrial and Employment Relations
- Industry Studies
- Information and Communication Technologies
- International Business
- Knowledge Management
- Management and Management Techniques
- Operations Management
- Organizational Theory and Behaviour
- Pensions and Pension Management
- Public and Nonprofit Management
- Strategic Management
- Supply Chain Management
- Browse content in Criminology and Criminal Justice
- Criminal Justice
- Criminology
- Forms of Crime
- International and Comparative Criminology
- Youth Violence and Juvenile Justice
- Development Studies
- Browse content in Economics
- Agricultural, Environmental, and Natural Resource Economics
- Asian Economics
- Behavioural Finance
- Behavioural Economics and Neuroeconomics
- Econometrics and Mathematical Economics
- Economic Systems
- Economic History
- Economic Methodology
- Economic Development and Growth
- Financial Markets
- Financial Institutions and Services
- General Economics and Teaching
- Health, Education, and Welfare
- History of Economic Thought
- International Economics
- Labour and Demographic Economics
- Law and Economics
- Macroeconomics and Monetary Economics
- Microeconomics
- Public Economics
- Urban, Rural, and Regional Economics
- Welfare Economics
- Browse content in Education
- Adult Education and Continuous Learning
- Care and Counselling of Students
- Early Childhood and Elementary Education
- Educational Equipment and Technology
- Educational Strategies and Policy
- Higher and Further Education
- Organization and Management of Education
- Philosophy and Theory of Education
- Schools Studies
- Secondary Education
- Teaching of a Specific Subject
- Teaching of Specific Groups and Special Educational Needs
- Teaching Skills and Techniques
- Browse content in Environment
- Applied Ecology (Social Science)
- Climate Change
- Conservation of the Environment (Social Science)
- Environmentalist Thought and Ideology (Social Science)
- Natural Disasters (Environment)
- Social Impact of Environmental Issues (Social Science)
- Browse content in Human Geography
- Cultural Geography
- Economic Geography
- Political Geography
- Browse content in Interdisciplinary Studies
- Communication Studies
- Museums, Libraries, and Information Sciences
- Browse content in Politics
- African Politics
- Asian Politics
- Chinese Politics
- Comparative Politics
- Conflict Politics
- Elections and Electoral Studies
- Environmental Politics
- European Union
- Foreign Policy
- Gender and Politics
- Human Rights and Politics
- Indian Politics
- International Relations
- International Organization (Politics)
- International Political Economy
- Irish Politics
- Latin American Politics
- Middle Eastern Politics
- Political Methodology
- Political Communication
- Political Philosophy
- Political Sociology
- Political Behaviour
- Political Economy
- Political Institutions
- Political Theory
- Politics and Law
- Public Administration
- Public Policy
- Quantitative Political Methodology
- Regional Political Studies
- Russian Politics
- Security Studies
- State and Local Government
- UK Politics
- US Politics
- Browse content in Regional and Area Studies
- African Studies
- Asian Studies
- East Asian Studies
- Japanese Studies
- Latin American Studies
- Middle Eastern Studies
- Native American Studies
- Scottish Studies
- Browse content in Research and Information
- Research Methods
- Browse content in Social Work
- Addictions and Substance Misuse
- Adoption and Fostering
- Care of the Elderly
- Child and Adolescent Social Work
- Couple and Family Social Work
- Developmental and Physical Disabilities Social Work
- Direct Practice and Clinical Social Work
- Emergency Services
- Human Behaviour and the Social Environment
- International and Global Issues in Social Work
- Mental and Behavioural Health
- Social Justice and Human Rights
- Social Policy and Advocacy
- Social Work and Crime and Justice
- Social Work Macro Practice
- Social Work Practice Settings
- Social Work Research and Evidence-based Practice
- Welfare and Benefit Systems
- Browse content in Sociology
- Childhood Studies
- Community Development
- Comparative and Historical Sociology
- Economic Sociology
- Gender and Sexuality
- Gerontology and Ageing
- Health, Illness, and Medicine
- Marriage and the Family
- Migration Studies
- Occupations, Professions, and Work
- Organizations
- Population and Demography
- Race and Ethnicity
- Social Theory
- Social Movements and Social Change
- Social Research and Statistics
- Social Stratification, Inequality, and Mobility
- Sociology of Religion
- Sociology of Education
- Sport and Leisure
- Urban and Rural Studies
- Browse content in Warfare and Defence
- Defence Strategy, Planning, and Research
- Land Forces and Warfare
- Military Administration
- Military Life and Institutions
- Naval Forces and Warfare
- Other Warfare and Defence Issues
- Peace Studies and Conflict Resolution
- Weapons and Equipment

- < Previous chapter
- Next chapter >
33 Cybercrime and You: How Criminals Attack and the Human Factors That They Seek to Exploit
Jason R. C. Nurse, School of Computing, University of Kent, UK
- Published: 09 October 2018
- Cite Icon Cite
- Permissions Icon Permissions
Cybercrime is a significant challenge to society, but it can be particularly harmful to the individuals who become victims. This chapter engages in a comprehensive and topical analysis of the cybercrimes that target individuals. It also examines the motivation of criminals that perpetrate such attacks and the key human factors and psychological aspects that help to make cybercriminals successful. Key areas assessed include social engineering (e.g., phishing, romance scams, catfishing), online harassment (e.g., cyberbullying, trolling, revenge porn, hate crimes), identity-related crimes (e.g., identity theft, doxing), hacking (e.g., malware, cryptojacking, account hacking), and denial-of-service crimes. As a part of its contribution, the chapter introduces a summary taxonomy of cybercrimes against individuals and a case for why they will continue to occur if concerted interdisciplinary efforts are not pursued.
Introduction
The internet and its significance to us as individuals.
Technology drives modern day society. It has influenced everything from governments and market economies, to global trade, travel, and communications. Digital technologies have further revolutionized our world, and since the advent of the Internet and the World Wide Web, society has become more efficient and advanced (Graham & Dutton, 2014 ). There are many benefits of the online world and to such large scales of connectivity. For individual Internet users, instantaneous communication translates into a platform for online purchases (on sites such as Amazon and eBay), online banking and financial management, interaction with friends and family members using messaging apps (e.g., WhatsApp and LINE), and the sharing of information (personal, opinion, or fact) on websites, blogs, and wikis. As the world has progressed technologically, these and many other services (such as Netflix, Uber, and Google services) have been made available to individuals with the aim of streamlining every aspect of our lives.
In a 2017 study of 30 economies including the United Kingdom (UK), United States of America (US), and Australia, it was the citizens of the Philippines that spent the most time online—at eight hours fifty-nine minutes, on average, per day—across PC and mobile devices (We Are Social, 2017 ). Brazil was second with eight hours fifty-five minutes, followed by Thailand at eight hours forty-nine minutes online. Developed countries such as the US, UK, and Australia posted usage values of between six hours twenty-one minutes and five hours eighteen minutes. This highlights a substantial usage gap compared to some developing states. A key driver of this increased Internet usage is social media, and particularly individuals’ use of platforms such as Facebook, Facebook Messenger, WhatsApp, YouTube, and instant messaging service QQ (We Are Social, 2017 ). Evidence supporting this reality has also been found in other studies, where social networks are more frequently used by Internet users in the emerging world (Poushter, 2016 ); this type of use is key to understanding the impact of social media in online crime, as will be outlined further later in this chapter.
The Prevalence of Cybercrime
To critically reflect on today’s world, while the Internet has various positive uses, it is increasingly being used as a tool to facilitate possibly the most significant challenge facing individuals’ use of the Internet: cybercrime. Cybercrime has been defined in several ways but can essentially be regarded as any crime (traditional or new) that can be conducted or enabled through, or using, digital technologies. Such technologies include personal computers (PCs), laptops, mobile phones, and smart devices (e.g., Internet-connected cameras, voice assistants), but the scope is quickly expanding to encompass smart systems and infrastructures (e.g., homes, offices, and buildings driven by the Internet of Things or IoT).
The importance of cybercrime can be seen in its ever-rising prevalence. In the UK, for example, a key finding of an early Crime Survey of England and Wales by the Office for National Statistics (ONS) was that there were 3.8 million reported instances of cybercrime in the twelve months to June 2016 (Scott, 2016 ). This is generally noteworthy, but even more so, given that the total number of crimes recorded in the other components of the survey (e.g., burglary, theft, violent crimes, but excluding fraud) tallied 6.5 million. The number of cybercrimes, therefore, amounts to more than half of the total crimes. Similar trends can also be found in the 2018 ONS report, with cybercrime and fraud accounting for almost half of crimes (techUK, 2018 ). This reality becomes more concerning given that these statistics are only based on the reported crimes, and moreover, that such cybercrimes are almost certainly set to increase in the future. Studies from the US also further evidence the extent of cybercrime and identity theft. Research from the 2018 Identity Fraud Study found that $16.8 billion was stolen from 16.7 million US consumers in 2017, which represents an 8% increase in the number of victims from a year earlier (Weber, 2018 ).
Types of Cybercrime
At its core, there are arguably three types of cybercrime: crimes in the device, crimes using the device, and crimes against the device (Wall, 2007 ). Crimes in the device relates to situations in which the content on the device may be illegal or otherwise prohibited. Examples include trading and distribution of content that promotes hate crimes or incites violence. The next category, crimes using the device, encompasses crimes where digital systems are used to engage and often, to deceive, victims. An example of this is a criminal pretending to be a legitimate person (or entity) and tricking an individual into releasing their personal details (e.g., account credentials) or transferring funds to other accounts. Wall’s final category, crimes against the device, pertains to incidents that compromise the device or system in some way. These crimes directly target the fundamental principles of cybersecurity, i.e., the confidentiality, integrity, and availability (regularly referred to as the CIA triad) of systems and data. This typology provides some general insight into the many crimes prevalent online today.
This chapter aims to build on the introduction to cybercrime and security issues online and focus in detail on cybercrimes conducted against individuals. It focuses on many of the crimes being conducted today and offers a topical discourse on how criminals craft these attacks, their motivations, and the key human factors and psychological aspects that make cybercriminals successful. Areas covered include social engineering (e.g., phishing, romance scams, catfishing), online harassment (e.g., cyberbullying, trolling, revenge porn, 1 and hate crimes), identity-related crimes (e.g., identity theft and doxxing), hacking (e.g., malware and account hacking), and denial-of-service (DoS) crimes.
Cybercrimes against Individuals: A Focus on the Core Crimes
The cybercrime landscape is enormous, and so are the varieties of ways in which cybercriminals can seek to attack individuals. This section introduces a taxonomy summarizing the most significant types of online crimes against individuals. These types of cybercrime are defined based on a comprehensive and systematic review of online crimes, case studies, and articles in academic, industry, and government circles. This includes instances and cases of cybercrime across the world (e.g., BBC News, 2016b ; Sidek & Rubbi-Clarke, 2017 ), taxonomies of cybercrime and cyberattacks that have been developed in research (e.g., Gordon & Ford, 2006 ; Wall, 2007 ; Wall, 2005/2015 ), industry reports on prevalent crimes (e.g., CheckPoint, 2017 ; PwC, 2016 ), and governmental publications in the space (e.g., NCA, 2017 ).
The intention is to connect the identified types of cybercrime to real-world situations, but also to maintain a flexible structure as new types of cybercrimes may well emerge. Moreover, the chapter is inclusive in its approach and defines types that are relatable and easily communicated—which has benefits for engagement, especially for those not involved in cybersecurity nor with a technical background or expertise. It is important to note here that many of the types identified here can be seen across prior works. For example, Wall’s work ( 2005/2015 ) examines crimes against the individual, crimes against the machine, and crimes in the machine, and Gordon and Ford ( 2006 ) use some of these types as exemplars of their Type 1 and Type 2 cybercrimes. This taxonomy’s value is therefore not in identifying new types of cybercrime, but instead in providing a new perspective on the topic which centers in on the types of cybercrime most prevalent today. The taxonomy is presented in Figure 1 .
Main types of cybercrimes against individuals.
The first type of cybercrime is Social Engineering and Trickery , which involves applying deceitful methods to coerce individuals into behaving certain ways or performing some task. Next, Online Harassment is similar to its offline counterpart and describes instances where persons online are annoyed/abused and tormented by others. Identity-related crimes are those in which an individual’s identity is stolen or misused by others for a nefarious or illegitimate purpose (e.g., fraud). Hacking , one of the most well publicized cybercrimes both in the news and the entertainment industry (e.g., Mr. Robot , Live Free or Die Hard , The Matrix , Swordfish ), is the action of compromising computing systems. While traditionally not regarded as a significant personal crime, Denial of Service is one of the most used by online criminals, and its popularity is attributed to its simplicity—i.e., it primarily involves blocking legitimate access to information, files, websites, or services—and effectiveness. Finally, (Denial of) Information accommodates the new trend of ransomware which is similar in that it denies individuals access to their own information. The next sections analyze the taxonomy and each of its types of crimes in detail.
Social Engineering and Online Trickery
Trickery, deceit, and scams are examples of some of the oldest means used by adversaries to achieve their goals. In Greek mythology, their army used deceit in the form of a Trojan horse; presented to the Trojans as a gift (or more specifically, an offering to Athena, goddess of war), it was instead a means for the Greek army to enter and destroy the city of Troy. Additionally, in The Art of War , fifth-century bce Chinese military strategist Sun Tzu declares, “Hence, when able to attack, we must seem unable; when using our forces, we must seem inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near” (Tzu/Giles, 2009 ). According to this well-known text on war, the intention is to deceive and, ideally, to misdirect, while discretely progressing towards and obtaining the goal—in Tzu’s case, winning against the enemy in battle.
Cybercriminals, potentially informed by history itself, have been applying such techniques for decades in Social Engineering , i.e., a specific class of cybercrime that uses deception or trickery to manipulate individuals into performing some unauthorized or illegitimate task. It seeks to exploit human psychology and is possibly the most effective means of conducting a crime against an individual.
In one example, a social engineer breaks into an individual’s cell-phone provider account in under two minutes. 2 This was achieved by phoning the cell-phone provider’s help desk, pretending to be the customer’s wife (impersonation is typically a core component of this crime), and using an audio recording of a crying baby (under the guise of it being her baby) to elicit sympathy from the help desk employee. Here, the social engineer used some basic information (i.e., knowing the customer’s name), sympathy, and the fact that a help desk is primarily supposed to provide assistance, to manipulate the help desk to grant her unauthorized access to a client account. There are numerous other similar types of attacks, and entire books (e.g., Hadnagy, 2010 ; Mann, 2008 , 2013 ) and training courses on the topic (e.g., at the well-known hacking conference, BlackHat).
Phishing and Its Variants
Phishing is a specific type of social engineering crime that occurs using electronic communications, such as an email or a website. In it, criminals send an email, or create a website, that appears to be from a legitimate entity with the intention of conning individuals into divulging some sensitive information or performing a particular action. Today there are many different variants of phishing, including spear-phishing, vishing, smishing (or SMSishing), and whaling.
Spear-phishing is a targeted phishing attack on an individual that has been customized based on other key and pertinent information, such as their date of birth, current bank, Internet service provider, or email address. This additional information is used to enhance the appearance of legitimacy and thereby increase the effectiveness of the con. Spear-phishing is held to be the reason for several well-known crimes including “Celebgate,” where private photographs of actresses Jennifer Lawrence, Kate Upton, and Scarlett Johansson were stolen and later exposed online. The terms vishing and smishing represent phishing attacks that occur over the phone (i.e., voice), and via text messages (especially SMS, but including WhatsApp, etc.) respectively. These often overlap with traditional phone scams but may also be used in combination with email phishing attempts. Whaling is very similar to spear-phishing but targets high-profile individuals (the notion being that a whale is a “big phish”) such as company executives, with the goal of a higher payoff for criminals if the attack is successful.
The success of phishing attacks over the last decade has been phenomenal. To take the UK as an example, the City of London Police’s National Fraud Intelligence Bureau (NFIB) and the Get Safe Online security awareness campaign estimated that in 2015 alone, phishing scams cost victims £174 million. Moreover, Symantec ( 2017 ) estimates that spear-phishing emails as a category in themselves have drained $3 billion from businesses over the last three years. These estimates are likely to increase, as are the various ways in which criminals have targeted individuals.
In one phishing scam, criminals monitored a lady in the process of purchasing a home, and after disguising themselves as her solicitor they requested that she transfer £50,000 into their account (iTV News, 2015 ). This can be considered as a spear-phishing attack given the amount of information the criminals had on her and her activities, and how they used that information to achieve their goal (similar to the process of reconnaissance). There have also been emails sent to university students where criminals have posed as employees of the university’s finance department. They pretend to offer educational grants that can only be redeemed after students provide personal and banking details (BBC News, 2016a ). While emails are prominent tools, fake websites also are a popular avenue for phishing crimes. A 2017 study discovered hundreds of fake websites posing as banks, including HSBC, Standard Chartered, Barclays, and Natwest, that targeted the public (McGoogan, 2017 ). These websites looked identical to official sites and used similar domain names, such as hsbc-direct.com , barclaya.net , and lloydstsbs.com (note the additional letter or slight re-organization of bank name in these addresses).
A key observation about these attacks and those above is that criminals have sought to exploit many human psychological traits. These include a willingness to trust others and to be kind, the impact of anxiety and stress on decision making, personal needs and wants, and in some regards, the naivety in decision making. In the home purchase case, criminals firstly targeted the stressful process of purchasing a home, and then secondly, waited for a specific moment in time where they could impersonate the solicitor to request transfer of funds. While not privy to the email sent, the tone of the email must have emphasized the importance of transferring the funds immediately to secure the purchase. Fear of losing the prospective property, the overall anxiety of house buying, and trust in the (supposed) solicitor are undoubtedly factors that would have led to the transfer of funds. Mann ( 2008 ) mentions similar tricks as core to social engineering, and Iuga, Nurse, and Erola ( 2016 ) mention these tricks as increasing the susceptibility of individuals to phishing attacks.
In the case of the university students, criminals targeted a prime need of students during their time at university, i.e., financial support to fund their degrees and themselves. By using university logos and other information, they were able to pose as a legitimate entity and thereby not arouse the suspicion of students. This impersonation also occurs within the fake website example. Criminals prey on naïve decision-making abilities, or more specifically, the heuristics (or quick “rules of thumb”) that individuals apply to make decisions. Here, they are presenting emails and sites as we expect they should appear, thus deceiving us into accepting them and acting without detailed consideration. This process has previously been described via the psychological heuristic of representativeness by psychologists Tversky and Kahneman during the 1970s. The heuristic posits that humans often make decisions based on how representative an event is grounded on the evidence, rather than what may be probabilistically true (Kahneman & Tversky, 1973 ). Therefore, because the website or email appears to possess all of the key evidence (a logo, familiar names, etc.), its legitimacy is more likely to be accepted. This is only one example of the ways in which psychology overlaps with cybersecurity; many others can be found in Nurse, Creese, Goldsmith, and Lamberts. ( 2011a ).
Online Scams—Tech Support, Romance, and Catfishing
In addition to phishing, online scams are also worth mentioning. Scams also involve trickery and deceit and typically have financial gain as the prime motive. One prominent example of the now common series of “tech support” scams is that of a global con uncovered in 2017. There, criminals purchased pop-up browser advertisements which appeared on victim’s computer screens and locked their browsers (US DoJ, 2017 ). These pop-ups inaccurately informed individuals that their computers were compromised and that they should call the “tech support” company for assistance. Reports indicate that over 40,000 people across the globe were victimized and defrauded out of more than $25 million USD (US DoJ, 2017 ). These criminals were using a series of fear tactics to deceive individuals, many of whom were elderly and potentially more vulnerable.
Romance scams are also rampant on the Internet via online dating websites. Here, criminals seek to engage in faked and extensive relationships, again, usually for financial gain. Their technique involves preying on vulnerable individuals seeking romance and love and exploiting them under the guise of a relationship. Research has studied these scams from a variety of perspectives, including understanding their prevalence (e.g., Whitty & Buchanan, 2012 ) and their impact on victims (e.g., Whitty & Buchanan, 2016 ). A noteworthy finding for our work on cybercrimes and individuals is that while financial losses may be incurred by victims, it is often the loss of the relationship that was more upsetting and psychologically traumatic. Catfishing is another variant of the common romance scam where fake, online identities and potentially, even social groupings are created to lure individuals into romantic relationships. Similar to traditional scams, the goal may be for financial gain, but notoriety may also be considered as a motive, e.g., American football player Manti Te’o (Schulman, 2014 ). Te’o was famously tricked into believing that he was in a relationship with Stanford University student Lennay Kekua, who, in reality, did not exist: Te’o was the victim of a year-long girlfriend hoax.
It is also important to consider the reasons behind why people continuously fall for online scams in the face of the large amounts of publicity to educate and warn individuals. Although fear, trickery, and the targeting of vulnerable individuals all play large parts, other research has extended consideration of these issues. Button, Nicholls, Kerr, and Owen ( 2014 ) have also identified core motivational factors that include the diversity of scams and frauds (i.e., criminals may find areas where individuals may be less wary of being defrauded), small amounts of money sought by criminals (if small amounts of money are lost, this may worry individuals less), authority and legitimacy displayed by scammers (this touches on the previous point of trickery and impersonation), as well as visceral appeals (i.e., criminals devising scams that appeal to human needs/feelings such as finance, love, sex, and sorrow). These cut across the various scams covered here and provide some insight into the diverse ways criminals use trickery and social engineering to achieve their nefarious goals, and thus why scams continue to be successful.
The Challenge of Online Harassment
Online harassment can broadly be regarded as the targeting of individuals with negative terms or actions. Emphasizing the significance of this crime, a 2016 Data & Society Research Institute study found that 47% of US Internet users have personally experienced online harassment or abuse, and 72% of these users have seen someone harassing someone else online. In terms of types of individuals that have been targeted, the research found that men and women are equally likely to face harassment online, but the latter have experienced a wider diversity of abuse. The individuals that are more likely to experience or witness abuse online include young users, black users, or those that identify as lesbian, gay, and bisexual (LGB). These findings broadly demonstrate an upwards progression from 2014 research by Marie Duggan at the Pew Research Center that also focused specifically on understanding online harassment.
In the UK, statistics collated by the National Society for the Prevention of Cruelty to Children (NSPCC) indicate a similarly worrying situation, especially considering children and online abuse. They note that one in three children have been victims of bullying online and almost one in four young people have come across racist or hate messages online (NSPCC, n.d. ). According to the NSPCC, such harassment has led to over 11,000 counseling sessions with young people who talked to ChildLine (a UK help and advice hotline) about online issues between 2015 and 2016.
Cyberbullying
Cyberbullying is one of the various types of online harassment, and one of many that are online manifestations of offline malevolent actions. It affects children, teenagers, and adults alike. It, like bullying, essentially involves repeated aggression (direct or indirect) levied by a group or individual against a victim that is (often) unable to easily defend him/herself. This aggression however, now occurs through modern technological devices such as the Internet or smartphones (Slonje & Smith, 2008 ). There are countless examples of this crime to be found in the media and, tragically, a number of resulting instances of suicide among youth (e.g., BBC News, 2016b ; Turner, 2017 ). A 2016 BBC report referred to one victim and noted that “His confidence and self-esteem had been eroded over a long period of time by the bullying behavior he experienced in secondary education. People who had never even met [ … ] were abusing him over social media and he found that he was unable to make and keep friends” (BBC News, 2016b ). This example captures the essence of cyberbullying, and also highlights the use of current platforms such as social media as one of its core conduits.
Research also contributes significantly to understanding the problem of cyberbullying. For instance, Whittaker and Kowalski ( 2015 ) found that texting and social media are two of the most common venues for cyberbullying in college-age students. More interesting however, is the finding that there may be an overlap in roles between “bully” and “victim” and that despite the significant emotional impact of cyberbullying, many victims do not seek support (Price & Dalgleish, 2010 ). These factors are important because they suggest a continuation of cyberbullying due to related behavior, and the lack of treatment (which potentially leads to exacerbation). A key factor to point out here, as compared to social engineering, is that perpetrators are usually not conventional criminals. Instead, they tend to be individuals who do not recognize the full extent of the psychologically detrimental impact of their actions. This is especially the case with young people, where there may be a lack of awareness of others’ feelings compounded by the inherent immaturity present in this age group. Cyberbullying is, however, also prevalent in adults (e.g., in social media and the workplace (Privitera & Campbell, 2009 )) even though the expectation exists for adults to be better informed and more cognitively aware of their actions than are young people.
Internet Trolling and Cyberstalking
Internet trolling and cyberstalking are two other forms of online harassment that both share a few similarities with cyberbullying. Trolling is the action of posting inflammatory messages deliberately with the intention of being disruptive, starting arguments, and upsetting individuals. Bishop ( 2014 ) identifies twelve types of “trollers” split into four groups: Haters (inflame situations for no benefit to others); Lolcows (provoke others to gain attention); Bzzzters (chat regardless of accuracy or value of contribution); and Eyeballs (wait for the opportune moment to post provocative messages). The motives for such actions have been empirically studied and relate to boredom, attention-seeking and revenge, fun and entertainment, and damage to the community and other people (Shachaf & Hara, 2010 ). This research provides useful insight into the types of actions that are core to trolling, and the motives of individuals who engage in it.
Real-world examples of trolls can be found in media reports and include people who have used online means such as social media to falsely brand others as pedophiles and witches, and also threatened to harm them (The Guardian, 2014 ; The Telegraph, 2015 ). As a result of such online malfeasance, the UK is an example of a country that now has stringent laws regarding this behavior (notably the Malicious Communications Act) 3 and has already sentenced several trolls to jail.
Cyberstalking is the use of electronic means (e.g., Internet, email) by criminals to repeatedly harass, threaten, prey on, or otherwise track an individual. Factors that tend to differentiate cyberstalking from other forms of online harassment include prolonged monitoring (or “keeping tabs”) of victims and making victims feel afraid and unsafe. A more interesting distinction to consider, nonetheless, is what separates cyberstalking from offline stalking—which could assist in the understanding of its prevalence. Goodno ( 2007 ) defines five peculiarities exclusive to cyberstalking: cyberstalkers use electronic means to instantly harass victims and have opportunities for wide dissemination; they can be physically/geographically far away from their victims; criminals operate under a cloak of (perceived) anonymity online; they can easily impersonate their victims to aggravate situations; and finally, these cybercriminals often encourage third parties in their harassment. These differences are so significant that they have led to cyberstalking overtaking offline physical harassment in the UK as a crime (McVeigh, 2011 ).
While cyberstalking does affect a cross-section of society, research has shown that some groups and types of individuals are more likely to be targets. In one study for instance, LGB Internet users were found to be almost four times as likely to report experiencing continuous contact which made them feel unsafe (Data & Society Research Institute, 2016). Women are also often targeted, e.g., for one female author, it had a serious impact on her personal and professional life (Gough, 2016 ), and is one of many examples that illustrate how social media, in particular, can be used to support stalking. Here, the stalker continuously monitored the individual, tracked her movements, gathered personal data (e.g., her address), and contacted her son’s school and newly met friends with malicious messages, e.g., from the stalker to a friend via Facebook—“ One of the people around you is author [author’s name]. She seems like a nice person at first-but actually she is a toxic person under a silver tongued mask. [Author’s name] is a secretly sadistic narcissistic person who tries to get others to commit suicide. STAY AWAY FROM HER … She is a wolf in sheeps’ clothing and has no conscience ” (Gough, 2016 ). This example demonstrates one of the ways in which stalkers can use the Internet to abuse and control their victims, i.e., through targeting friends and family; this is in addition to the more direct forms of harassment (e.g., attempts at ongoing messages or persistent threats).
The challenge here is that the Internet and social media have become so embedded in the modern lifestyle that these technologies and individuals’ tendency to overshare provides cyberstalkers and other criminals with copious amounts of personal information they need (Nurse, 2015 ). Additionally, Cavezza and McEwan ( 2014 ) found that, compared to offline stalkers, cyberstalkers may be more likely to be ex-intimate partners. These results are interesting because they provide further insight into the types of people who perform such actions as well as those who are often impacted.
Revenge Porn and Sextortion
Revenge porn and sextortion are two of the newest (in broad terms) forms of online harassment. Within the former, individuals, especially ex-partners, post sexual images of victims online without their permission. Criminals use these photo leaks to embarrass, humiliate, and demean victims. Sextortion is the gathering of sexual images or video (potentially via entrapment), and its use to blackmail individuals for further sexual footage or other favors. Reports indicate the significance of these crimes in cyberspace, with Facebook having to disable more than 14,000 accounts related to this form of crime in a single month alone (Hopkins & Solon, 2017 ). Examples of these crimes can typically be found in two main scenarios.
The first scenario involves disgruntled ex-partners using private photos, likely shared during a previous sexual relationship, to humiliate their victims—this may occur especially if relationships did not end amicably. This has also become known as revenge porn, or more accurately, non-consensual sharing of private sexual images. Secondly, there are an increasing number of cybercriminal gangs using the guise of attractive young women to trick individuals into sexually explicit actions online (e.g., via webcams or Skype sessions). These actions are recorded and later used to blackmail victims—typically using threats of sharing photos with family and friends unless money is paid (Sawer, 2016 ).
Cybercriminals have also combined sextortion with phishing and hacked passwords to boost impact. The latest trend has been in emailing individuals claiming to have compromising video of them watching pornography, and recorded via their webcam; the email includes one of the individual’s passwords (attained most likely from a prior organizational data breach) to suggest legitimacy. Individuals are asked to pay a certain amount (e.g., via Bitcoin) or risk the video being sent to friends, family and coworkers. A poignant example, taken from the EFF, is as follows: “ Hi, victim. I write you because I put a malware on the web page with porn which you have visited. My virus grabbed all your personal info and turned on your camera which captured the process. … Just after that the soft saved your contact list. I will delete the compromising video and info if you pay me 999 USD in bitcoin. … I give you 30 hours after you open my message for making the transaction ” (Quintin, 2018 ).
Similar to the other crimes mentioned, revenge porn and sextortion can have devastating impacts on victims. In possibly one of the largest studies on the topic, Henry, Powell, and Flynn ( 2017 ) found that 80% of people who experienced sextortion reported heightened levels of psychological distress, such that it was also consistent with moderate to severe depression and/or anxiety disorder. Furthermore, victims often felt highly fearful for their safety after the ordeal. This response is well-justified as there have been other reports of serious threats (e.g., abuse and threats of rape) to victims of revenge porn (Raven, 2014 ), and other reports of suicide due to its prolonged effects (BBC News, 2017a ). It is worth mentioning that most research up until this point has focused on the legal and criminal aspects of revenge porn and combatting it. Simultaneously, there has been a surge in new laws (e.g., the UK Criminal Justice and Courts Act 2015, the Protecting Canadians from Online Crime Act) and subsequent prosecutions for criminals involved in these types of acts (CPS, 2015 ).
Hate Crimes
Hate crimes (and hate speech) are another form of offline harassment that have made the transition to online. These are crimes that arise due to prejudice based on race, sexual orientation, gender, religion, ethnicity, or disability (McDevitt, Levin, & Bennett., 2002 ). In many ways, these crimes overlap with those mentioned, and also extend them in terms of the threats levied. Jacks and Adler ( 2015 ) build on earlier work (e.g., McDevitt et al., 2002 ) to examine the types of users that are engaged in online hate crimes (or with hate materials). They identify four main types: Browsers (viewers of hate material); Commentators (viewers and those who engage with and post comments); Activists (those who add overt hate material and seek to promote their views and engage with others); and Leaders (individuals who use the Internet to support, organize, and promote their extremist ideologies). As to be expected, Leaders are typically the smallest group, but as Jacks and Adler ( 2015 ) note, they tend to be high repeat offenders.
Social media also plays a central role in hate speech and crimes, particularly those that occur after significant events. For instance, after the Woolwich attack on an off-duty soldier in London in May 2013, there were hundreds of hate messages posted on social media, especially Twitter, targeting Muslims (Awan, 2014 ). These perpetrators were using the platform of social media, and its wide reach, to openly attack people due to their faith. This issue of hate on social media has become so widespread that London’s Met Police have set up an Online Hate Crime Hub unit to address it, and there have been demands for fines on Facebook, Twitter, and YouTube for failing to act swiftly against such content (Fiveash, 2017 ). It is arguably only via such concerted efforts that progress will be made in tackling the issue of online hate, but also that of online harassment more broadly.
Identity-Related Cybercrimes
Identity theft and identity fraud are traditional crimes that have flourished due to online systems and the open nature of the Internet. While the theft of identities by criminals is enabled due the amount of information on individuals online, fraud becomes possible when that information is used for monetary gain (e.g., impersonating the individual to purchase an item). In the UK alone, there were just short of 173,000 incidents of identity fraud in 2016, which represents 53.3% of all reported fraud, and more importantly, 88% of this occurred online (BBC News, 2017b ). The US market has also witnessed significant rises in identity-related fraud, with a 40% increase in 2016 in “card not present” (i.e., mainly online) fraud (Javelin Strategy & Research, 2017 ) and in 2017, this type of fraud being 81% more likely than point-of-sale fraud (Weber, 2018 ). These reports also act to highlight some of the main activities by cybercriminals engaging in identity theft and fraud, e.g., making online purchases, signing up for credit accounts (e.g., credit cards or loans), signing up to paid websites. Depending on the amount of data possessed by these criminals, there are even concerns that they could apply for passports in a victim’s name. Other examples of crimes such as unlawful identity delegation and exchange have also been documented in research (Koops, Leenes, Meints, van der Meulen, & Jaquet-Chiffelle, 2009 ).
Identity theft works by criminals gathering information on individuals and using that as the basis through which to steal their identities. Today, there are two information-gathering techniques preferred by cybercriminals: the monitoring of individuals on social media as they post and interact online, and the gathering and use of personal data from previous online security breaches. The first of these techniques exploits a factor previously mentioned that pertains to phishing, i.e., the nature to overshare, but also the poor management of security and privacy online. A noteworthy study by fraud prevention organization Cifas found that Twitter, Facebook, and LinkedIn are now prime “hunting grounds” used by identity thieves (Samee, 2016 ); these networks contain an abundance of personal details, from birth dates and family member details to addresses, school histories, and job titles.
Previous research has considered this issue of oversharing and modeled how social media data could be used to place individuals at great risk, both online and offline (Creese, Goldsmith, Nurse, & Phillips, 2012 ; Nurse, 2015 ). There are also greater impacts on security and privacy as this data is combined with that from IoT devices such as fitness trackers and smart watches (Aktypi, Nurse, & Goldsmith, 2017 ). Most recently, people using Strava to track their exercise patterns inadvertently exposed details of military bases when posting their results to the app; such types of exposure can increase the risk to individuals, businesses, and governments (Hern, 2018 ; Nurse, 2018 ). In addition to focusing on these risks, other relevant psychological research has sought to understand why individuals tend to disclose more online. This has led to the identification of six factors which explain such behavior and create what has been deemed the “online disinhibition effect”: dissociative anonymity (separation of online actions from offline identities); invisibility (opportunity to be physically invisible and unseen); asynchron-icity (lack of immediate and real-time reactions); solipsistic introjection (or, merging of minds with other online individuals); dissociative imagination (impression of the online world as make believe and not connected to reality); and minimization of status and authority (based on the perspective that everyone online is equal) (Suler, 2004 ). These factors, including their interactions, are widely considered to impact online behavior, and thus may also potentially be linked to exposure to risks (such as identity theft and fraud).
The second information gathering technique used by cybercriminals is that of previous online data breaches. Over the last ten years, a significant number of companies have been victims of cyberattacks and subsequently have leaked customer data online. A few well-known enterprises include Yahoo!, Uber, Target, Sony, Anthem (health insurer), JP Morgan Chase, Ashley Madison, and eHarmony, and the data exposed spans biographic information, medical records, email addresses, family members, social security numbers, card details, and passwords. These customer details have often been available openly on public websites (e.g., pastebin.com ), or for sale online. Pastebin.com provides an interesting case study given that although it has positive uses, hackers have become increasingly attached to it to publicly share/expose sensitive details (in addition to the above, this includes compromised social media accounts, access credentials to companies, etc.) online. Likely reasons for this preference include the site’s lack of requirement for users to register, its lack of proactive moderation of posts, and its ability to handle large text-based files.
The Dark Web is particularly relevant here as it is one of the most well-known places where identity data and banking details can be found and traded by cybercriminals. Because the Web exists on an encrypted network it can only be accessed by tools such as Tor (The Onion Router), and thus offers some level of anonymity. According to the Underground Hacker Marketplace report, credit cards can be purchased for as little as $7 USD, identity packages (including social security number, driver’s license, and matching utility bill) for $90 USD, and a dossier of credentials and data (dubbed a Fullz, and containing names, addresses, banking information, and physical counterfeit cards) for $140–$250 USD (Dell SecureWorks, 2016 ). Such cybercrime marketplaces and ecosystems place individuals at a continued risk of identity theft and fraud, especially considering that much of an individual’s most valued identity data (e.g., name, email, social security number, bank accounts) is not easily changed.
Although it is not as significant (at least from a monetary standpoint) as identity theft or fraud, the newer crime of online doxxing (or doxing) is worth a mention here. This attack involves inspecting and researching personal information (e.g., home addresses, emails and phone numbers, preferences) about an individual and then posting that information publicly online. The criminal’s intention is generally to infringe on the privacy of that person for malicious reasons such as harassment, or to conduct some form of vigilante justice for an actual or perceived wrong.
Hacking: The Dark Art
Hacking is one of the most traditional forms of cybercrime and involves activities that result in the compromise of computing systems and/or digital information. By compromise, this chapter refers specifically to the detrimental impact of these actions on the confidentiality and integrity of systems and data. As such, hacking can refer to corporate or personal data (e.g., a person’s photo album) being exposed, or accessed by, unintended parties; the unauthorized modification or deletion of that data (with or without the knowledge of the individual); or computer systems being disrupted from functioning as intended.
Malware (Viruses, Worms, Trojans, Spyware, and Cryptojacking)
There is a plethora of crimes that can be labeled as hacking. The most topical threat in this domain however, is arguably that of malware. Malicious software (or malware) describes applications developed and used by criminals to compromise the confidentiality or integrity of systems and information. The cost of managing malware alone for UK organizations in a 2016 study totaled £7.5 billion (Warwick, 2016 ). This has been matched by an even more drastic increase in the amount of malware applications and variants deployed by criminals. For instance, in 2017, Symantec ( 2017 ) reported a threefold increase in new malware families online, while in 2018 there was a 88% increase in new malware variants (Symantec, 2018 ). The most popular types of malware that impact individuals are viruses, worms, Trojan horses, and spyware.
Viruses are programs that replicate when executed and spread to other files and systems. They are known for attaching themselves to other programs. The Melissa virus is one of the most famous viruses in history. It was implemented as a Microsoft Word macro virus that once opened by an unwitting individual, automatically distributed itself via email to the first 50 people in that individual’s Outlook address book, with the message “ Here is that document you asked for … don’t show anyone else ;-).” As these emails were opened and the document was accessed, the virus would spread even further, infecting more computers, and generating thousands of unsolicited emails. A unique characteristic of Melissa (and many of the viruses it has since inspired) was that its success and the continued spread of the virus exploited human psychology. Specifically, it targeted individuals’ friendships, i.e., sending to contacts thereby hijacking existing trust relationships, and also used trickery by referencing a document that was supposedly requested and allegedly secretive.
Worms are similar to viruses but they are standalone and do not need to be attached to a file. The prime purpose of worms is to self-replicate especially to other computers on the network (e.g., a home, university, or public network). As a result of its purpose, worms tend to vastly consume system resources (e.g., a computer’s CPU and memory, and a network’s bandwidth) thus slowing down computers and network speeds. Examples of recorded computer worms include Blaster, which would also cause the user’s computer to shut down or restart repeatedly, ILOVEYOU, and the Daprosy worm.
Trojan horses, as the name suggests, are programs that appear legitimate but have another core purpose, which commonly is acting as a back door into computers or systems (most notably, Remote-Access Trojans (RATs)). These malware variants can allow cybercriminals to circumvent security mechanisms to gain unauthorized access into systems. This access may be used to steal files, monitor individuals, or to employ the computer as a proxy for a larger attack. For example, personal information and files (e.g., photo albums, information on finances, private diaries, saved passwords) may be accessed and leaked online, or criminals may remotely turn on web cameras to spy on and take photos of individuals (e.g., Blue, 2016 ; Korolov, 2016 ). The latter of which could lead to sextortion. Furthermore, computers could be used as a platform to launch cyberattacks against other systems. This is similar to the recent case of the DoS attack on DNS provider, Dyn, where IoT devices from within homes and organizations across the world aided in disrupting access to hundreds of popular websites (Krebs, 2016 ).
Another type of malware targeting individuals online is spyware, which, as the name suggests, spies on and collects information about users, which could span from gathering specific information (e.g., passwords, banking information, search habits, computer-usage information) to storing all of the individual’s behavior on the computer or system. The primary goal of spyware is to extract useful information about users that can then be used by the cybercriminal for a financial gain. There are numerous instances of such malware found on computers and smartphones (e.g., CheckPoint, 2017 ; Lecher, 2016 ).
While many of the other malware types have been known for some time, a more recent entry in the malware domain is that of cryptojacking typically through coin mining malware. Cryptojacking is the process of using an individual’s computing device (PC, laptop, etc.) without their knowledge to ‘mine’ cryptocurrencies such as Bitcoin. Mining is a computationally expensive problem, and therefore, cybercriminals have sought to use any resources they can find—including hijacking the processing power of unsuspecting user devices—and pool these together to form a remotely linked system for efficient mining. This hijacking typically works by the hacker secretly including mining scripts (pieces of programming code) within webpages or browser extensions which automatically execute when a user visits a website. In early 2018, several government websites in the UK, US, and Australia were compromised by cryptojacking malware (Osborne, 2018 ), which meant visitors to those sites unwittingly may have participated in mining. Numerous other companies, networks and online sites have also been compromised by this threat, including Tesla, GitHub, a Starbucks Wi-Fi network, and a series of pirate video streaming websites. More worryingly, the problem of cryptojacking is likely to become significantly worse in the future as current reports note that attacks in the UK alone have surged 1200% (Martin, 2018 ) and over the course of 2017, there was a 34000% increase in coin mining attacks (Symantec, 2018 )—the motivation for attackers being new currency or simply, more money.
Having reflected on the several types of malware present, it is also worthwhile to consider the ways in which individuals’ technology become infected, and thus what makes such crimes/attacks truly successful. Focusing on viruses and worms first, these are unique as they self-replicate and automatically spread to other systems with little user contact. The computers and users that are initially infected are therefore the key to the prevalence of this computer attack. Trojans horses, spyware, and their variants (e.g., adware and scareware) offer a different challenge to cybercriminals as to how they disseminate their attacks. There is a range of techniques developed to threaten individuals.
Phishing (and spear-phishing) attacks are the most common vector through which criminals transmit malware (Symantec, 2017 ). These exploit the trust of humans through impersonation and social engineering. Another infection vector is the bundling of malware with legitimate software downloads; this regularly occurs with spyware and third-party browsers or applications such as peer-to-peer file sharing platforms like Kazaa (Moshchuk, Bragin, Gribble, & Levy, 2006 ). Here, cybercriminals recognize the importance of certain applications and seek to exploit that by pairing installations. In many cases the pairing of additional software may not be known by users, although in some cases it may be and users may still choose to download it. From a psychological perspective, this may occur for multiple reasons. For instance, users may be focused only on their end goal (e.g., watching a film or listening to music) and ignore anything that distracts from that goal, or they may not want to pay for services and so prefer to watch a film online for free. There is also the reality that users often misunderstand the level of risk they are facing and overestimate the capability of protection measures such as anti-virus software (Nurse et al., 2011a ). This results in overly risky decisions, and ultimately may lead to the successfulness of a hack.
Watering hole attacks and drive-by downloads are also highly preferred techniques, and these demonstrate how simple it is to compromise individuals. These attacks only require individuals to visit an infected webpage or misclick in a browser window, and the malware will be downloaded automatically for later installation. Watering hole attacks are particularly interesting because they involve the cybercriminal monitoring the types of sites an individual or certain group tends to visit, and then compromising (one or more of) those sites to allow for the injection of malware (in essence, “poisoning the watering hole”). They then wait until the intended targets visit those sites again and thus become infected. This exemplifies one of the many tailored attacks levied by cybercriminals to target individuals. It also demonstrates the research in which cybercriminals often engage and the extent to which they may be willing to monitor human behavior to increase successfulness of their crime. A crucial point worth noting here is that the sites targeted could be regular websites, and there is not necessarily an act, or fault, of the user that makes this attack possible other than visiting the site.
Account and Password Hacking
Beyond malware, the hacking of online accounts (e.g., Facebook, Gmail, Government portals, paid services) and user passwords is a significant challenge faced by individuals. This is due to a variety of techniques being applied by cybercriminals, many of which are now even automated. One popular approach to hacking an individual’s account is through the stealing of their username and password credentials. Criminals typically achieve this via shoulder surfing (i.e., looking over someone’s shoulder while they are entering their password), and cybercriminals also focus on installing malware on the victim’s computer that logs all keys typed (also known as a keylogger) or applying social engineering techniques.
A real-world example of such attacks was the case of a student who installed keyloggers on university computers to steal staff passwords, and then used their accounts to increase his test scores (Vaas, 2015 ). Keyloggers are particularly dangerous as they can record all keystrokes, from passwords to credit card numbers. It is worth noting, however, that new approaches to stealing passwords are continuously being discovered, as evidenced with PINs deciphered through video recording and tracking the motion/tilt of smartphones (Mehrnezhad, Toreini, Shahandashti, & Hao, 2016 ; Nurse, Erola, Agrafiotis, Goldsmith, & Creese, 2015 ). The IoT could pose a real challenge here given the amount of personal information that may be leaked via the usage of smart devices—be they wearables (smart watches, fitness trackers), voice assistants (e.g., Amazon Alexa, Google Home, or Apple HomePod), or smart appliances (e.g., smart TVs, fridges, and ovens). Research has already demonstrated the somewhat irrational behavior of individuals when using the IoT, considering their beliefs regarding privacy versus their inaction to behave privately (i.e., the privacy paradox) (Williams, Nurse, & Creese, 2016 , 2017 ).
Password guessing is another way in which cybercriminals can gain illegitimate access to individuals’ accounts. Informed guessing is the most successful technique and is where criminals use prior information to guess account credentials or infer details that would allow them to reset user accounts. Such information can be readily gathered from social media profiles (e.g., hobbies, pets, sports teams, mother’s maiden name, family member names, and dates of birth), which is why it is important for individuals to be wary of what they share online. Another avenue used by cybercriminals is that of previously breached passwords. Given the number of data breaches that have occurred over the last few years as discussed earlier and the tendency of individuals to reuse passwords across sites, criminals have the perfect platform to amass sensitive user data and existing credentials. Research has investigated this reality and demonstrated the various ways in which hackers can reuse and guess passwords with some degree of success using this prior knowledge (Das, Bonneau, Caesar, Borisov, & Wang, 2014 ). Sites such as haveibeenpwned.com have since become popular as they allow users to check whether or not their account has been compromised in a breach.
Dictionary attacks, i.e., where words from the dictionary are used to form potential passwords, are also a common password hacking technique. Here, cybercriminals look to exploit poorly created passwords based on dictionary words. One unique aspect of these attacks is that they can be automated using hacking tools such as John the Ripper, Cain and Abel, and L0phtCrack. The availability of these tools, and the fact that they require little expertise yet combine several different password crackers into one packaged application, provides cybercriminals with a significant advantage. That is, that up-skilling and increasing the scale of attacks is much easier than before and thus less of a barrier to conducting crime.
To exacerbate this issue, there are many common, weak passwords in use by individuals. A study of 10 million passwords sourced from data breaches that occurred in 2016 (Guccione, 2017 ) highlighted several key points: firstly, the top five common passwords used by individuals were 123456, 123456789, qwerty, 12345678, and 111111; secondly, 17% of users had the password “123456.”; thirdly, the list of most frequently used passwords has demonstrated little change over the last few years; and finally, nearly half of the top 15 passwords are six characters or shorter. Fortune Magazine recently reported that many of these same issues occurred again in 2017 (Korosec, 2017 ). One inference that might be made from these findings is that users prefer to maintain simple and memorable passwords. This is hardly a surprise as security is often known to crumble when placed in conflict with usability (Nurse, Creese, Goldsmith, & Lamberts, 2011b ), and after all, humans favor consistency and are known to be creatures of habit. For hackers, however, such weak and common passwords are ideal, and can be guessed extremely quickly, thus placing users at risk of account takeovers.
Denial-of-Service (DoS) and Ransomware
A DoS attack involves cybercriminals blocking individuals from accessing legitimate websites and services. This is normally achieved by bombarding the websites/services with an enormous number of fabricated requests (e.g., page visits), which causes legitimate requests to be dropped or the organization’s websites/services to crash under the load. This crime is somewhat unique as compared to the others above because it depicts another way that individuals may be impacted by cybercrime, i.e., via attacks on organizations and services that they use. Interestingly, there would be little obvious signs of this to a user other than the website being unavailable. Of course, the unavailability of a website does not necessarily mean a DoS attack has occurred; there are many other reasons that may be behind this, including human errors (BBC News, 2016c ).
On Christmas Eve of 2015 a DoS cyberattack inundated BBC services with a substantial number of web requests which eventually forced many offline (Korolov, 2016 ). While this attack was not unique (and, indeed there have been larger Distributed-DoS (DDoS) attacks, e.g., GitHub (Kottler, 2018 ) or Dyn in 2016 (Krebs, 2016 ), there is one very worrying observation about it: the cybercriminals that claimed responsibility, a group named New World Hacking, stated that the attack was only a test and that they had not planned to take the BBC down for multiple hours. This demonstrates the power of cybercriminals today and suggests that, on occasion, they themselves are not fully aware of their capabilities. A compelling reason for this heightened and unknown capability might be the ease at which criminals can procure or rent hacking and botnet 4 services on the Dark Web (Dell SecureWorks, 2016 ). Often, these services are rented without a proper understanding of their full impact.
In addition to DoS attacks, cybercriminals have also employed other forms of crime to block legitimate access requests by individuals. A popular trend today is using ransomware, which is a form of malware that encrypts individual’s information and only allows subsequent access if ransom is paid (typically via the cryptocurrency, Bitcoin). Individuals might become infected by phishing attacks or using infected devices (e.g., pen-drives). According to Symantec ( 2017 ), the growth of ransomware has been phenomenal, especially its use as a profit center for criminals. On average, they note that criminals demand $1,077 USD per victim in each ransomware attack. There are many potential reasons for the growth in this crime, but arguably the most prominent is that criminals have fully recognized that an individual’s data, whether it be personal photos and videos, financial spreadsheets, or files, is their most valuable possession. As a result, these attacks are crafted to target that data.
The increasing prevalence of this crime is motivated by its high success rates. For example, 64% of people in the US whose technology was infected were found to be willing to pay the necessary amount to regain access to their data (Symantec, 2017 ). Similarly, at an organizational level one infected hospital paid $17,000 USD to have its files unencrypted (Wong & Solon, 2017 ). Psychologically, it is a simple decision of cost versus benefit for individuals and organizations: the cost of paying the ransom is significantly less than the benefit of having access to files, therefore the payment is made. For individuals, this might mean regaining access to precious videos of their child’s first steps or photos of a graduation or a selfie with a celebrity. For a hospital, access to the electronic health records database is required to be able to properly treat patients and thereby, to conduct business. Again, therefore, criminals have found a key weakness in these parties and are crafting crimes to carefully exploit them.
To further support their plight, cybercriminals are also making efforts to ensure that the paying of ransoms is as seamless and “painless” as possible. There have been anecdotes of cybercriminals providing ransom payment FAQs, helpdesks, and even offering discounts to individuals who cannot pay the full demands. This demonstrates a level of sophistication by criminals where crime is becoming an industry (see Nurse and Bada , this volume), capable of even offering “customer services”. At the same time, there is an increasing amount of ransomware attacks, e.g., the WannaCry attack in 2017, which affected nearly 100 countries and critical services such as the UK’s National Health Service (NHS) (Guardian, 2017 ). These attacks seem to increase due to the combination of reasons and raise a number of interesting questions for us as a society. For example, as these attacks continue to grow, will society simply accept them (and for instance, just pay the ransom)? Will the occasional (e.g., yearly) breach of our data simply be viewed as part of being online? And broadly, will we become desensitized (even further) to online risk? These present interesting avenues for future research in the field.
Summarizing Key Human Factors, and Future Research
While the advantages that accompany Internet use and digital technologies are plentiful, there is an abundance of challenges and concerns facing the new, high-tech world. Cybercrime is one of the most prevalent and has the ability to impact people psychologically, financially, and even physically. This chapter reflected on many of the crimes that cybercriminals engage in today and the reasons why these are often quite successful, from social engineering and online harassment to hacking and ransomware attacks. A salient point is that cybercriminals are ready, willing, and have a strong history in exploiting many human psychological needs and weaknesses. Such facets include our innate desire to trust and help each other (e.g., in the case of the mother with the crying baby), the human need for love and affection (e.g., romance scams), the host of biases that affect decision-making on security (Nurse et al., 2011a ), and a perfect knowledge of what people consider most important, i.e., the willingness to pay for the return of something valuable (e.g., instances of ransomware). Table 1 summarizes the main types of crimes and the respective human and psychological factors that may be exploited by cybercriminals to lead to their success.
As the sophistication of cybercriminals has increased, so too must the approaches to prevent, detect, and deter their behaviors. Cyberpsychology research has made significant inroads to the analysis of this problem through the study of criminal behavior and the psychological and social impact on victims. The field of Cybersecurity features a range of new models, systems, and tools that aim to prevent and detect attacks against individuals—these utilize a variety of the latest techniques in machine learning and anomaly detection to boost accuracy and efficiency. Criminology is also a key area, and there are now several laws across the world seeking to deter online crimes and prosecute those who perpetrate them. However, if approaches towards preventing cybercrime are to be truly effective at protecting individuals, a more concerted, cross-disciplinary program is mandatory. It is only in this way that the insight from each field can be properly synthesized and combined to address the issue of online crime.
Aktypi, A. , Nurse, J. R. C. , & Goldsmith, M. (2017). Unwinding Ariadne’s identity thread: Privacy risks with fitness trackers and online social networks. In Proceedings of the Multimedia Privacy and Security Workshop at the 24th ACM Conference on Computer and Communications Security (CCS) (pp. 1–11). 30 October to 3 November, Dallas, Texas. New York: ACM. doi: 10.1145/3137616.3137617 10.1145/3137616.3137617
Awan, I. ( 2014 ). Islamophobia and Twitter: A typology of online hate against Muslims on social media. Policy & Internet 6(2), 133–150. doi: 10.1002/1944-2866.POI364 10.1002/1944-2866.POI364
Google Scholar
Aycock, J. ( 2006 ). Computer viruses and malware . New York: Springer Science & Business Media.
Google Preview
BBC News. (2016a). Students warned of new “phishing” scam . Retrieved from http://www.bbc.co.uk/news/education-37408373
BBC News. (2016b). Felix Alexander death: Worcester mum’s open letter against cyberbullying . Retrieved from http://www.bbc.co.uk/news/uk-england-hereford-worcester-37574528
BBC News. (2016c). Web host 123-reg deletes sites in clean-up error . Retrieved from http://www.bbc.co.uk/news/technology-36072240
BBC News. (2017a). Italy’s Tiziana: Tragedy of a woman destroyed by viral sex videos . Retrieved from http://www.bbc.co.uk/news/world-europe-38848528
BBC News. (2017b). Identity fraud reached record levels in 2016 . Retrieved from http://www.bbc.co.uk/news/uk-39268542
Bishop, J. ( 2014 ). Dealing with Internet trolling in political online communities: Towards the “This Is Why We Can’t Have Nice Things” scale. International Journal of E-Politics (IJEP) 5(4), 1–20. doi: 10.4018/ijep.2014100101 10.4018/ijep.2014100101
Blue, V. (2016, 23 September). The FBI recommends you cover your laptop’s webcam, for good reason. [blog post]. Engadget . Retrieved from https://www.engadget.com/2016/09/23/the-fbi-recommends-you-cover-your-laptops-webcam-good-reasons/
Button, M. , Nicholls, C. M. , Kerr, J. , & Owen, R. ( 2014 ). Online frauds: Learning from victims why they fall for these scams. Australian & New Zealand Journal of Criminology 47(3), 391–408. doi: 10.1177/0004865814521224 10.1177/0004865814521224
Cavezza, C. , & McEwan, T. E. ( 2014 ). Cyberstalking versus off-line stalking in a forensic sample. Psychology, Crime & Law 20(10), 955–970. doi: 10.1080/1068316X.2014.893334 10.1080/1068316X.2014.893334
Check Point Software Technologies Ltd. (2017). Preinstalled malware targeting mobile users. [blog post]. Retrieved from http://blog.checkpoint.com/2017/03/10/preinstalled-malware-targeting-mobile-users/
Creese, S. , Goldsmith, M. , Nurse, J. R. C. , & Phillips, E. (2012). A data-reachability model for elucidating privacy and security risks related to the use of online social networks. Proceedings of the 11th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom) (pp. 1124–1131). 25–27 June, Liverpool, UK. Red Hook, NY: Curran Associates. doi: 10.1109/TrustCom.2012.22 10.1109/TrustCom.2012.22
Crown Prosecution Service (CPS). (2015, 7 August). Prosecutors being advised to learn from revenge porn cases across the country to help them tackle this “humiliating” crime. [blog post]. CPS News Brief . Retrieved from http://blog.cps.gov.uk/2015/08/prosecutors-being-advised-to-learn-from-revenge-porn-cases-across-the-country-to-help-them-tackle-th.html
Das, A. , Bonneau, J. , Caesar, M. , Borisov, N. , & Wang, X. (2014). The tangled web of password reuse. In Proceedings of the Network and Distributed System Security Symposium (pp. 23–26), 23–26 February, San Diego, CA. Reston, VA: Internet Society.
Dell SecureWorks. (2016). 2016 Underground Hacker Marketplace Report . Retrieved from https://www.secureworks.com/resources/rp-2016-underground-hacker-marketplace-report
Duggan, M. (2014). Online Harassment . Washington, DC: Pew Research Center. Retrieved from http://www.pewinternet.org/2014/10/22/online-harassment/
Fiveash, K. (2017). Online hate crime: MPs demand fines for Facebook, Twitter, YouTube. Ars Technica . Retrieved from https://arstechnica.co.uk/tech-policy/2017/05/online-hate-crime-fines-facebook-twitter-youtube/
Hadnagy, C. ( 2010 ). Social engineering: The art of human hacking . Indianapolis: John Wiley & Sons.
Henry, N. , Powell, A. , & Flynn, A. ( 2017 ). Not Just “Revenge Pornography”: Australians’ Experiences of Image-Based Abuse . A Summary Report. Melbourne: RMIT University. Retrieved from https://www.rmit.edu.au/content/dam/rmit/documents/college-of-design-and-social-context/schools/global-urban-and-social-studies/revenge_porn_report_2017.pdf
Goodno, N. H. ( 2007 ). Cyberstalking, a new crime: Evaluating the effectiveness of current state and federal laws. Missouri Law Review 72(7). Retrieved from http://scholarship.law.missouri.edu/mlr/vol72/iss1/7
Gordon, S. , & Ford, R. ( 2006 ). On the definition and classification of cybercrime. Journal in Computer Virology 2(1), 13–20. doi: 10.1007/s11416-006-0015-z 10.1007/s11416-006-0015-z
Gough, L. (2016, 7 September). What it’s like to be cyberstalked: When you can’t escape the untraceable threat. The Guardian . Retrieved from https://www.theguardian.com/society/2016/sep/07/cyberstalking-online-stalking-email-threats-laurie-gough
Graham, M. , & Dutton, W. H. (Eds.). ( 2014 ). Society and the Internet: How networks of information and communication are changing our lives . Oxford: OUP.
Guccione, D. (2017, January 13). What the most common passwords of 2016 list reveals (Research Study). [blog post]. Retrieved from https://blog.keepersecurity.com/2017/01/13/most-common-passwords-of-2016-research-study/
Hern, A. (2018, 28 January). Fitness tracking app Strava gives away location of secret US army bases. The Guardian . Retrieved from https://www.theguardian.com/world/2018/jan/28/fitness-tracking-app-gives-away-location-of-secret-us-army-bases
Hopkins, N. , & Solon, O. (2017, 22 May). Facebook flooded with “sextortion” and revenge porn, files reveal. The Guardian . Retrieved from https://www.theguardian.com/news/2017/may/22/facebook-flooded-with-sextortion-and-revenge-porn-files-reveal
ITV News. (2015). Scammed out of £50,000 over email . Retrieved from http://www.itv.com/goodmorningbritain/news/scammed-out-of-50000-over-email
Iuga, C. , Nurse, J. R. C. , & Erola, A. ( 2016 ). Baiting the hook: Factors impacting susceptibility to phishing attacks. Human-centric Computing and Information Sciences Journal 6(1), 1–20. doi: 10.1186/s13673-016-0065-2 10.1186/s13673-016-0065-2
Jacks, W. , & Adler, J. R. ( 2015 ). A proposed typology of online hate crime. Open Access Journal of Forensic Psychology 7, 64–89.
Javelin Strategy & Research. (2017). Identity Fraud Hits Record High with 15.4 Million U.S. Victims in 2016, Up 16 % According to New Javelin Strategy & Research Study . Retrieved from https://www.javelinstrategy.com/press-release/identity-fraud-hits-record-high-154-million-us-victims-2016-16-percent-according-new
Kahneman, D. , & Tversky, A. ( 1973 ). On the psychology of prediction. Psychological Review 80(4), 237. doi: 10.1037/h0034747 10.1037/h0034747
Kochekova, K. (2016, April 28). Hackers broadcast live footage from hacked webcams on YouTube and trolls are loving it . Retrieved from https://blog.kaspersky.com/2ch-webcam-hack/11961/
Koops, B. J. , Leenes, R. , Meints, M. , van der Meulen, N. , & Jaquet-Chiffelle, D. O. ( 2009 ). A typology of identity-related crime: Conceptual, technical, and legal issues. Information, Communication & Society 12(1), 1–24. doi: 10.1080/13691180802158516 10.1080/13691180802158516
Korolov, M. (2016, 8 January). DDoS attack on BBC may have been biggest in history. CSO . Retrieved from http://www.csoonline.com/article/3020292/cyber-attacks-espionage/ddos-attack-on-bbc-may-have-been-biggest-in-history.html
Korosec, K. (2017, 19 December). The 25 Most Common Passwords of 2017 Include “Star Wars”. Fortune . Retrieved from http://fortune.com/2017/12/19/the-25-most-used-hackable-passwords-2017-star-wars-freedom/
Kottler, S. (2018, 1 March). February 28th DDoS Incident Report. GitHub . Retrieved from https://githubengineering.com/ddos-incident-report/
Krebs, B. (2016). DDoS on Dyn Impacts Twitter, Spotify, Reddit. [blog post]. Krebs on Security. Retrieved from https://krebsonsecurity.com/2016/10/ddos-on-dyn-impacts-twitter-spotify-reddit/
Lecher, C. (2016, 15 November). Budget Android phones are secretly sending users’ text messages to China. The Verge . Retrieved from https://www.theverge.com/2016/11/15/13636072/budget-android-phones-blu-china-text-messages
Lenhar, A. , Ybarra, M. , Zickurh, K. , & Price-Feeney, M. ( 2016 ). Online Harassment, Digital Abuse, and Cyberstalking in America . New York: Data & Society Research Institute. Retrieved from https://www.datasociety.net/pubs/oh/Online_Harassment_2016.pdf
Mann, I. ( 2008 ). Hacking the human: Social engineering techniques and security countermeasures . Aldershot: Gower Publishing, Ltd.
Mann, I. ( 2013 ). Hacking the human II: The adventures of a social engineer . Whitley Bay: Consilience Media.
Martin, A. J. (2018). “Cryptojacking” attacks surge 1,200% in UK . Retrieved from https://news.sky.com/story/cryptojacking-attacks-surge-1200-in-uk-11269594
McDevitt, J. , Levin, J. , & Bennett, S. ( 2002 ). Hate crime offenders: An expanded typology. Journal of Social Issues 58(2), 303–317. doi: 10.1111/1540-4560.00262 10.1111/1540-4560.00262
McGoogan, C. (2017). Warning over fake bank websites targeting British savers. The Telegraph . Retrieved from http://www.telegraph.co.uk/technology/2017/05/02/warning-fake-bank-websites-targeting-british-savers/
McVeigh, K. (2011, April 8). Cyberstalking “now more common” than face-to-face stalking The Guardian . Retrieved from https://www.theguardian.com/uk/2011/apr/08/cyberstalking-study-victims-men
Mehrnezhad, M. , Toreini, E. , Shahandashti, S. F. , & Hao, F. ( 2016 ). Stealing PINs via mobile sensors: Actual risk versus user perception. International Journal of Information Security 17 (3), 1–23. doi: 10.1007/s10207-017-0369-x 10.1007/s10207-017-0369-x
Moshchuk, A. , Bragin, T. , Gribble, S. D. , & Levy, H. M. (2006). A Crawler-based study of spyware in the web. In 13th Annual Proceedings of the Network and Distributed System Security Symposium (NDSS) . San Diego, CA.
National Crime Agency (NCA). (London, 2017). Pathways into cybercrime . Retrieved from http://www.nationalcrimeagency.gov.uk/publications/791-pathways-into-cyber-crime/file
Nurse, J. R. C. ( 2015 ). Exploring the risks to identity security and privacy in cyberspace. XRDS: Crossroads, The ACM Magazine 21(3), 42–47. doi: 10.1145/2730912 10.1145/2730912
Nurse, J. R. C. (2018). Strava storm: Why everyone should check their smart gear security settings before going for a jog. The Conversation . Retrieved from https://theconversation.com/strava-storm-why-everyone-should-check-their-smart-gear-security-settings-before-going-for-a-jog-90880
Nurse, J. R. C. , Creese, S. , Goldsmith, M. , & Lamberts, K. (2011a). Trustworthy and effective communication of cybersecurity risks: A review. Proceedings of the International Workshop on Socio-Technical Aspects in Security and Trust (STAST) (pp. 60–68). 8 September, Milan, Italy. Red Hook, NY: Curran Associates. doi: 10.1109/STAST.2011.6059257 10.1109/STAST.2011.6059257
Nurse, J. R. C. , Creese, S. , Goldsmith, M. , & Lamberts, K. (2011b). Guidelines for Usable Cybersecurity: Past and Present. Proceedings of the Third International Workshop on Cyberspace Safety and Security (CSS) (pp. 21–26). 8 September, Milan, Italy. Red Hook, NY: Curran Associates. doi: 10.1109/CSS.2011.6058566 10.1109/CSS.2011.6058566
Nurse, J. R. C. , Erola, A. , Agrafiotis, I. , Goldsmith, M. , & Creese, S. (2015). Smart insiders: Exploring the threat from insiders using the Internet-of-Things. In Proceedings of the International Workshop on Secure Internet of Things (SIoT) (pp. 5–14). 21–25 September, Vienna, Austria. Los Alamitos, CA: IEEE Computer Society. doi: 10.1109/SIOT.2015.10 10.1109/SIOT.2015.10
Osborne, C. (2018, 12 February). UK government websites, ICO hijacked by cryptocurrency mining malware . Retrieved from http://www.zdnet.com/article/uk-government-websites-ico-hijacked-by-cryptocurrency-mining-malware
Peter Nunn jailed for abusive tweets to MP Stella Creasy. (2014, 29 September). [press release]. The Guardian . Retrieved from https://www.theguardian.com/uk-news/2014/sep/29/peter-nunn-jailed-abusive-tweets-mp-stella-creasy
Poushter, J. (2016). Smartphone Ownership and Internet Usage Continues to Climb in Emerging Economies . Washington, DC: Pew Research Center. Retrieved from http://www.pewglobal.org/files/2016/02/pew_research_center_global_technology_report_final_february_22__2016.pdf
Price, M. , & Dalgleish, J. ( 2010 ). Cyberbullying: Experiences, impacts and coping strategies as described by Australian young people. Youth Studies Australia 29(2), 51.
Privitera, C. , & Campbell, M. A. ( 2009 ). Cyberbullying: The new face of workplace bullying? Cyberpsychology & Behavior 12(4), 395–400. doi: 10.1089/cpb.2009.0025
PwC. (2016). The Global State of Information Security ® Survey 2017 . Retrieved from https://www.pwc.com/gx/en/issues/cyber-security/information-security-survey.html
Quintin, C. (2018). Sextortion Scam: What to Do If You Get the Latest Phishing Spam Demanding Bitcoin. Electronic Frontier Foundation (EFF) . Retrieved from https://www.eff.org/deeplinks/2018/07/sextortion-scam-what-do-if-you-get-latest-phishing-spam-demanding-bitcoin
Raven, D. (2014, 27 August). “Revenge porn ruined my life”: Woman received rape threats after nude leaked pictures online. The Mirror . Retrieved from http://www.mirror.co.uk/news/uk-news/revenge-porn-ruined-life-woman-4113969
Samee, S. (2016, 4 July). Criminals Target UK Youth as Identity Fraud Rises . [blog post] Retrieved from https://www.cifas.org.uk/newsroom/criminals-target-uk-youth-as-identity-fraud-rises
Sawer, P. (2016, 30 November). Huge rise in “sextortion” by crime gangs using social media to entrap victims . The Telegraph . Retrieved from http://www.telegraph.co.uk/news/2016/11/30/huge-rise-sextortion-crime-gangs-using-social-media-entrap-victims/
Schulman, N. ( 2014 ). In real life: Love, lies & identity in the digital age . London: Hachette UK.
Scott, P. (2016). How much of a problem is cyber-crime in the UK? The Telegraph . Retrieved from http://www.telegraph.co.uk/news/2016/11/01/how-much-of-a-problem-is-cyber-crime-in-the-uk/
Shachaf, P. , & Hara, N. ( 2010 ). Beyond vandalism: Wikipedia trolls. Journal of Information Science 36(3), 357–370. doi: 10.1177/0165551510365390 10.1177/0165551510365390
Sidek, F. , & Rubbi-Clarke, J. (2017, 11 January). The Top Cyber Security Risks in Asia-Pacific in 2017. Forbes . Retrieved from https://www.forbes.com/sites/riskmap/2017/01/11/the-top-cyber-security-risks-in-asia-pacific-in-2017/
Slonje, R. , & Smith, P. K. ( 2008 ). Cyberbullying: Another main type of bullying? Scandinavian Journal of Psychology 49(2), 147–154. doi: 10.1111/j.1467–9450.2007.00611.x 10.1111/j.1467–9450.2007.00611.x
Suler, J. ( 2004 ). The online disinhibition effect. Cyberpsychology & Behavior 7(3), 321–326. doi: 10.1089/1094931041291295 10.1089/1094931041291295
Symantec. (2017). 2017 Internet Security Threat Report . Retrieved from https://www.symantec.com/content/dam/symantec/docs/reports/istr-22-2017-en.pdf
Symantec. (2018). 2018 Internet Security Threat Report . Retrieved from https://www.symantec.com/content/dam/symantec/docs/reports/istr-23-2018-en.pdf
techUK. (2018). ONS Crime Stats: Fraud & Cyber Crime Still Dominate . Retrieved from http://www.techuk.org/insights/news/item/13518-ons-crime-stats-fraud-cyber-crime-still-dominate
The National Society for the Prevention of Cruelty to Children (NSPCC). (n.d.). Online abuse: Facts and statistics . Retrieved from https://www.nspcc.org.uk/preventing-abuse/child-abuse-and-neglect/online-abuse/facts-statistics/
The Telegraph. (2015, 10 February). Prolific internet troll who branded victims paedophiles spared jail . [Agency press release]. Retrieved from http://www.telegraph.co.uk/news/uknews/crime/11404512/Prolific-internet-troll-who-branded-victims-paedophiles-spared-jail.html
Turner, C. (2017, 18 May). Exclusive: Sayat.me app, that allows cyberbullying, at centre of police investigation into teenager’s suicide . The Telegraph . Retrieved from http://www.telegraph.co.uk/education/2017/05/18/exclusive-sayatme-app-allows-cyberbullying-centre-police-investigation/
Tzu, S. ( 2009 ). The Art of War ( L. Giles , Trans.). Pax Librorum.
US Department of Justice (DoJ). (2017, May 12). Seven Charged in International “Tech Support Scam.” Retrieved from https://www.justice.gov/usao-sdil/pr/seven-charged-international-tech-support-scam
Vaas, L. (2015, April 27). Student jailed for using keylogger to up his exam marks . Retrieved from https://nakedsecurity.sophos.com/2015/04/27/student-jailed-for-using-keylogger-to-up-his-exam-marks/
Wall, D. S. ( 2007 ). Policing cybercrimes: Situating the public police in networks of security within cyberspace. Police Practice and Research 8(2), 183–205. doi: 10.1080/15614260701377729 10.1080/15614260701377729
Wall, D. S. ( 2005 /15). The Internet as a conduit for criminal activity. In A. Pattavina (Ed.), Information Technology and the Criminal Justice System (pp. 77–98). Thousand Oaks, CA: Sage.
Warwick, A. (2016, 14 July). Cyber attacks cost UK business more than £34bn a year, study shows. Computer Weekly . Retrieved from http://www.computerweekly.com/news/450300330/Cyber-attacks-cost-UK-business-more-than-34bn-a-year-study-shows
We Are Social. (2017). Digital in 2017 Global Overview: A collection of Internet, Social Media and Mobile Data from around the world . Retrieved from https://wearesocial.com/blog/2017/01/digital-in-2017-global-overview
Weber, J. (2018). Identity Fraud Hits All Time High With 16.7 Million U.S. Victims in 2017, According to New Javelin Strategy & Research Study [press release]. Retrieved from https://www.javelinstrategy.com/press-release/identity-fraud-hits-all-time-high-167-million-us-victims-2017-according-new-javelin
Whittaker, E. , & Kowalski, R. M. ( 2015 ). Cyberbullying via social media. Journal of School Violence 14(1), 11–29. doi: 10.1080/15388220.2014.949377 10.1080/15388220.2014.949377
Whitty, M. T. , & Buchanan, T. ( 2012 ). The online romance scam: A serious cybercrime. Cyberpsychology, Behavior and Social Networking 15(3), 181–183. doi: 10.1089/cyber.2011.0352 10.1089/cyber.2011.0352
Whitty, M. T. , & Buchanan, T. ( 2016 ). The online dating romance scam: The psychological impact on victims–both financial and non-financial. Criminology & Criminal Justice 16(2), 176–194. doi: 10.1177/1748895815603773 10.1177/1748895815603773
Williams, M. , Nurse, J. R. C. , & Creese, S. (2016). The perfect storm: The privacy paradox and the Internet-of-Things. Proceedings of the 11th International Conference on Availability, Reliability and Security (ARES) (pp. 644–652). IEEE. doi: 10.1109/ARES.2016.25 10.1109/ARES.2016.25
Williams, M. , Nurse, J. R. C. , & Creese, S. (2017). Privacy is the boring bit: User perceptions and behaviour in the Internet-of-Things. Proceedings of the 15th International Conference on Privacy, Security and Trust (PST) . 28–30 August, Calgary, Alberta, Canada. doi: 10.1109/PST.2017.00029
Wong, J. C. , & Solon, O. (2017, 12 May). Massive ransomware cyber-attack hits nearly 100 countries around the world. The Guardian . Retrieved from https://www.theguardian.com/technology/2017/may/12/global-cyber-attack-ransomware-nsa-uk-nhs
Or possibly, more appropriately termed, the distribution of sexual images of individuals without their consent.
This is how hackers hack you using simple social engineering. See https://www.youtube.com/watch?v=lc7scxvKQOo
http://www.legislation.gov.uk/ukpga/1988/27/introduction
A botnet is a series of Internet-connected computing devices that are infected with malware which allows them to be remotely controlled. These devices are not normally aware they are a part of the botnet.
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Advertisement
Cybercrime and Artificial Intelligence. An overview of the work of international organizations on criminal justice and the international applicable instruments
- Open access
- Published: 22 February 2022
- Volume 23 , pages 109–126, ( 2022 )
Cite this article
You have full access to this open access article

- Cristos Velasco 1 , 2 , 3
15k Accesses
8 Citations
6 Altmetric
Explore all metrics
The purpose of this paper is to assess whether current international instruments to counter cybercrime may apply in the context of Artificial Intelligence (AI) technologies and to provide a short analysis of the ongoing policy initiatives of international organizations that would have a relevant impact in the law-making process in the field of cybercrime in the near future. This paper discusses the implications that AI policy making would bring to the administration of the criminal justice system to specifically counter cybercrimes. Current trends and uses of AI systems and applications to commit harmful and illegal conduct are analysed including deep fakes. The paper finalizes with a conclusion that offers an alternative to create effective policy responses to counter cybercrime committed through AI systems.
Similar content being viewed by others

Artificial Intelligence Crime: An Interdisciplinary Analysis of Foreseeable Threats and Solutions

Cyber Threats and National Security: The Use and Abuse of Artificial Intelligence

Avoid common mistakes on your manuscript.
1 Introduction
Undoubtedly, AI has brought enormous benefits and advantages to humanity in the last decade and this trend will likely continue in coming years since AI is gradually becoming part of the digital services that we use in our daily lives. Many governments around the world are considering the deployment of AI systems and applications to help them achieve their activities and more concretely to facilitate the identification and prediction of crime. Footnote 1 Further, national security and intelligence agencies have also realized the potential of AI technologies to support and achieve national and public security objectives.
There are significant developments of AI technologies like the use of facial recognition in the criminal justice realm, the use of drones, lethal autonomous weapons and self-driving vehicles that when not properly configured or managed without proper oversight mechanisms in place have the potential to be used for disruptive purposes and harm individual’s rights and freedoms.
Currently, there is an ongoing discussion in international policy and legislative circles on the revision and improvement of the liability framework and threshold concerning AI systems and technologies, Footnote 2 although due to the complexity of the topic and the different legal approaches around the world concerning civil liability, there will probably not be a consensus on a harmonized and uniformed response, at least not in the near future.
Further, AI and machine learning have the potential and offer the possibility to detect and respond to cyberattacks targeted to critical infrastructure sectors including water, energy and electricity supplies, as well as the correct management of cybersecurity solutions to help reduce and mitigate security risks. Footnote 3 However, many complex challenges remain particularly for small and medium enterprises which continue to rely on limited budgets to improve their cybersecurity capabilities.
Due to the COVID-19 pandemic, a large part of the world’s connected population was confined. This situation made companies and individuals more dependent on the use of systems, technologies and applications based on AI to conduct their activities, including remote work, distance learning, online payments or simply having access to more entertainment options like streaming and video on demand services. Unfortunately, this situation also led organized criminal groups to reconsider and re-organized their criminal activities in order to specifically target a number of stakeholders, including international organizations, Footnote 4 research and health sector entities, Footnote 5 supply chain companies Footnote 6 and individuals. We have witnessed that organized criminal groups have largely improve their CasS (crime as a service) capabilities and turn their activities into higher financial profits with very small possibilities of being traced by law enforcement and brought to justice.
Through the use of AI technologies, cybercriminals have not only found a novel vehicle to leverage their unlawful activities, but particularly new opportunities to design and conduct attacks against governments, enterprises and individuals. Although, there is no sufficient evidence that criminal groups have a strong technical expertise in the management and manipulation of AI and machine learning systems for criminal purposes, it is true that said groups have realized its enormous potential for criminal and disruptive purposes. Footnote 7 Further, organized criminal groups currently recruit and bring technical skilled hackers into their files to manipulate, exploit and abuse computer systems and to perpetrate attacks and conduct criminal activities 24/7 from practically anywhere in the world. Footnote 8
2 Current cybercrime trends
Current trends and statistics show that cybercriminals are relying more on the use of IoT to write and distribute malware and target ransomware attacks which are largely enhanced through AI technologies. Footnote 9 This trend will likely continue as it is expected that more than 2.5 million devices will be fully connected online in the next 5 years including industrial devices and critical infrastructure operators which will make companies and consumers more vulnerable to cyberattacks. Footnote 10
Furthermore, the discussion on bias and discrimination Footnote 11 are also relevant debated aspects on AI policy in many international and policy making circles. Footnote 12 The widespread use of technologies based on facial recognition systems, Footnote 13 deserves further attention in the international policy arena because even when facial recognition may be very appealing for some governments to enhance aspects of public security and safety to prioritize national security activities, including terrorist activities, this technology may as well raises relevant and polemic issues concerning the protection of fundamental rights, including privacy and data protection under existing international treaties and conventions, topics that are currently being discussed in relevant international fora including the Council of Europe, the European Commission, the European Parliament Footnote 14 and the OECD.
There is an ongoing global trend to promote misinformation with the support of AI technologies known as ‘bots’. Footnote 15 Bots are mainly used to spread fake news and content throughout the internet and social networks and have the chilling effect of disinforming and misleading the population, particularly younger generations who cannot easily differentiate between legitimate sources of information and fake news. Further, the use of ‘bots’ have the potential to erode trust and question the credibility of the media and destabilize democratic and government institutions.
Although AI holds the prospect to enhance the analysis of big amounts of data to avoid the spread of misinformation in social networks, Footnote 16 humans still face the challenge to check and verify the credibility of the sources, an activity which is usually conducted by content moderators of technology companies and media outlets without specific links to government spheres, a situation that has led relevant policy making institutions like the European Commission to implement comprehensive and broad sets of action to tackle the spread and impact of online misinformation. Footnote 17
Another trend and technology widely used across many industries are deep fakes. Footnote 18
The abuse and misuse of deepfakes has become a major concern in national politics Footnote 19 and among law enforcement circles. Footnote 20 Deepfakes have been used to impersonate politicians, Footnote 21 celebrities and CEO’s of companies which may be used in combination with social engineering techniques and system automatization to perpetrate fraudulent criminal activities and cyberattacks. The use of deep fake technologies for malicious purposes is expanding rapidly and is currently being exploited by cybercriminals on a global scale. For example, in 2019, cybercriminals used AI voice generating software to impersonate the voice of a Chief Executive of an energy company based in the United Kingdom and were able to obtain $243,000 and distribute the transfers of the funds to bank accounts located in Mexico and other countries. Footnote 22
Another relevant case occurred in January 2020 where criminals used deep voice technology to simulate the voice of the director of a transnational company. Through various calls with the branch manager of a bank based in the United Arab Emirates, criminals were able to steal $35 million that were deposited into several bank accounts, making the branch manager of the bank believe that the funds will be used for the acquisition of another company. Footnote 23
The spoofing of voices and videos through deep fakes raise relevant and complex legal challenges for the investigation and prosecution of these crimes. First and foremost, many law enforcement authorities around the world do not yet have full capabilities and trained experts to secure evidence across borders, and often times the lack of legal frameworks particularly procedural measures in criminal law to order the preservation of digital evidence and investigate cybercrime represents another major obstacle. Second, since most of these attacks are usually orchestrated by well organized criminal groups located in different jurisdictions, there is the clear need for international cooperation, and in particular a close collaboration with global services providers to secure subscriber and traffic data, as well as to conduct more expedited investigations and law enforcement actions with other countries through the deployment of joint investigation teams in order to be able to trace and locate the suspects and follow the final destination of illicit funds. Footnote 24 Cross-border cybercrime investigations are complex, lengthy, and do not always necessarily result in convictions of the perpetrators.
Further, cyberattacks based on AI systems is a growing trend identified by the European Cybercrime Centre (EC3) of EUROPOL in its Internet Crime Threat Assessment Report 2020 . According to the EC3, the risks concerning the use of AI for criminal purposes need to be well understood in order to protect society against malicious actors. According to the EC3, “through AI, criminals may facilitate and improve their attacks by maximizing their opportunities for profit in a shorter period of time and create more innovative criminal business models, while reducing the possibility of being traced and identified by criminal justice authorities”. Footnote 25
Further, the EC3 of EUROPOL recommends the development of further knowledge regarding the potential use of AI by criminals with a view to better anticipating possible malicious and criminal activities facilitated by AI, as well as to prevent, respond to, or mitigate the effects of such attacks in a more proactive manner and in close cooperation with industry and academia. Footnote 26
3 Strategic partnerships
Due to the complexities that the misuse and abuse of AI systems for criminal purposes entail for law enforcement agencies, key stakeholders are trying to promote the development of strategic partnerships between law enforcement, international organizations and the private sector to counter more effectively against the misuse and abuse of AI technologies for criminal purposes. For example, in November 2020, Trend Micro Research, the EC3 of EUROPOL and the Centre for Artificial Intelligence and Robotics of the UN Interregional Crime and Justice Research Institute (UNICRI) published the report: Malicious Uses and Abuses of Artificial Intelligence . Footnote 27 This report contains an in-depth technical analysis of present and future malicious uses and abuses of AI and related technologies that drew from the outcomes of a workshop organized by EUROPOL, Trend Micro and UNICRI in March 2020. The report highlights relevant technical findings and contains examples of AI capabilities divided into “malicious AI uses” and “malicious AI abuses”. The report also sets forth future scenarios in areas like AI supported ransomware, AI detection systems, and developed a case study on deepfakes highlighting the development of major policies to counter it, as well as recommendations and considerations for further and future research. Footnote 28
Strategic initiatives and more partnerships like the one mentioned above are further needed in the field of AI and cybercrime to ensure that relevant stakeholders particularly law enforcement authorities and the judiciary understand the complexities and dimensions of AI systems and start developing cooperation partnerships that may help to identify and locate perpetrators that misuse and abuse AI systems with the support of the private sector. The task is complex and needs to be achieved with the support of the technical and business community, otherwise isolated investigative and law enforcement efforts against criminals making use of AI systems will not likely succeed.
AI policy has been at the core of the discussions only in recent years. At the regional level, the European Commission has recently published a regulation proposal known as the Digital Services Act Footnote 29 though this proposal has just recently been opened for consultation and it will take a few years until it is finally approved.
On April 21, 20021, the European Commission published its awaited Regulation proposal for Artificial Intelligence Systems . Footnote 30 The proposal contains broad and strict rules and obligations before AI services can be put into the European market based on the assessment of different levels of risks. The regulation proposal of the European Commission also contains express prohibitions of AI practices that may contravene EU values and violate fundamental rights of citizens, and it establishes the European Artificial Intelligence Board (EIAB) as the official body that will supervise the application and enforcement of the regulation across the EU. Footnote 31
The prospect of developing a new international convention that will regulate relevant aspects concerning the impact and development of AI systems and the intersection with the protection of fundamental rights has been proposed by the Ad-Hoc Committee on Artificial Intelligence of the Council of Europe, better known as ‘CAHAI’. The work of CAHAI will be analysed in section 5.1 of this paper.
4 International instruments to counter cybercrime
At the international level, there are a number of international and regional instruments that are used to investigate “cyber dependent crime”, “cyber enabled crime” and “computer supported crime”. Footnote 32 This paper will only focus on the analysis of three major instruments of the Council of Europe which are applicable to criminal conduct and activities concerning the use of computer and information systems, the exploitation and abuse of children and violence against women committed through information and computer systems:
The Convention on Cybercrime better known as the ‘the Budapest Convention’ ;
The Convention on Protection of Children against Sexual Exploitation and Sexual Abuse, better known as ‘the Lanzarote Convention’ ; and
The Convention on preventing and combating violence against women and domestic violence better known as the ‘the Istanbul Convention’ .
4.1 The Budapest Convention
The Council of Europe’s Budapest Convention on Cybercrime is the only international treaty that criminalizes conducts and typologies committed through computer and information systems. This instrument contains substantive and procedural provisions for the investigation, execution and adjudication of crimes committed through computer systems and information technologies. Footnote 33 The Budapest Convention is mainly used as a vehicle for international cooperation to investigate and prosecute cybercrime among the now 66 State Parties, which includes many countries outside Europe. Footnote 34
The Cybercrime Convention Committee (T-CY) which is formed by State Parties, country observers invited to accede to the Budapest Convention and ad-hoc participants is the entity responsible inter alia for conducting assessments of the implementation of the provisions of the Budapest Convention, as well as the adoption of opinions and recommendations regarding the interpretation and implementation of its main provisions. Footnote 35
During the 2021 Octopus Conference on Cooperation against Cybercrime in November 2021 that marked the 20th anniversary of the Budapest Convention, the organizers announced that the Committee of Ministers of the Council of Europe approved the adoption of the Second Additional Protocol to the Budapest Convention on enhanced cooperation and the disclosure of electronic evidence as originally adopted by 24 the Plenary Session of the T-CY Committee in May 2021. The text of the Second Additional Protocol will be officially opened for signature among State parties to the Budapest Convention in the summer of 2022. Footnote 36
The Second Additional Protocol to the Budapest Convention on enhanced cooperation and the disclosure of electronic evidence regulates inter alia how the information and electronic evidence - including subscriber information, traffic data and content data - may be ordered and preserved in criminal investigations among State Parties to the Budapest Convention. It provides a legal basis for disclosure of information concerning the registration of domain names from domain name registries and registrars and other key aspects concerning cross-border investigations including mutual legal assistance procedures, direct cooperation with service providers, disclosure of data in emergency situations, protection of safeguards for transborder access to data and joint investigation teams. Footnote 37
Although, the T-CY Committee has not yet fully explored how the Budapest Convention and its first additional protocol on xenophobia and racism may be applicable in the context of technologies and systems based on AI, it is worth mentioning that the Budapest Convention was drafted with broad consideration of the principle of technological neutrality precisely because the original drafters of this instrument anticipated how the threat landscape for cybercrime would likely evolve and change in the future. Footnote 38
The Budapest Convention contains only a minimum of definitions; however, this instrument criminalizes a number of conducts and typifies many offenses concerning computer and content related crimes that may as well be applicable to crimes committed through the use of AI systems.
During the 2018 Octopus Conference on Cooperation against Cybercrime, the Directorate General of Human Rights and Rule of Law of the Council of Europe convened a panel on AI and Cybercrime Footnote 39 where representatives of the CoE presented its early activities and findings on AI policy. Footnote 40 Although the panel presentations were more descriptive concerning the technical terminology used in the field AI at that time, some speakers highlighted and discussed some of the challenges that AI poses to law enforcement authorities like for instance the criminalization of video and document forgery and how authorities could advance the challenge to obtain and preserve electronic evidence in court. Footnote 41
The 2021 Octopus Conference on Cooperation against Cybercrime held fully online from 16-18 November 2021 due to the COVID-19 situation, held a panel on “Artificial Intelligence, cybercrime and electronic evidence”. Footnote 42 This panel discussed complex questions concerning criminal liability and trustworthiness of evidence of AI systems in auditing and driving automation and assistance; and other relevant aspects concerning harms and threats of misinformation and disinformation developed by AI systems and effective responses, countermeasures and technical solutions from the private sector.
AI and cybercrime are relevant aspects that need further analysis and detailed discussions among the TC-Y and State Parties to the Budapest Convention, particularly since there has been an increase of cases concerning the misuse of AI technologies by cybercriminals and as vehicles to launch cyberattacks and commit criminal offenses against individuals in the cyberspace. Questions such as who will bear the responsibility for a conduct committed through the use of algorithms and machine learning and the liability threshold among State Parties need further discussion and clarification since the regulation of criminal liability differs significantly among the legal systems of many countries, as well as to explore the development of strategic partnerships in other regions of the world to counter attacks based on AI systems.
4.2 The Lanzarote Convention
The Council of Europe Lanzarote Convention is an international treaty that contains substantive legal measures for the protection of children from sexual violence including sexual exploitation and abuse of children online. Footnote 43 This convention harmonizes minimum legal conducts at the domestic level to combat crimes against children and provide measures for international cooperation to counter the sexual exploitation of children. The Lanzarote Convention requires the current 48 State Parties to offer a holistic response to sexual violence against children through the “4Ps approach”: Prevention, Protection, Prosecution and Promotion of national and international cooperation. Footnote 44 The monitoring and implementation body of the Lanzarote Convention is conducted by the Committee of the Parties, also known as the ‘Lanzarote Committee’ . This committee is formed by State Parties and it is primarily responsible for monitoring how State Parties put legislation, policies and countermeasures into practice, including organizing capacity building activities to exchange information and best practices concerning the implementation of the Lanzarote Convention across State Parties. Footnote 45
Like, the TC-Y, the ‘Lanzarote Committee’ has not yet fully explored how the substantive and procedural criminal law provisions of the Lanzarote Convention may apply in the context of the use of AI systems for criminal related purposes, a situation that needs to be further discussed among State Parties in order to not only share and diffuse knowledge on current trends among State Parties of that treaty, but to also help identify illicit conducts and abuse and exploitation of children through AI systems, as well as an analysis of positive uses of AI technologies for the prevention of crimes concerning the protection of children online.

4.3 The Istanbul Convention
The Istanbul Convention is another treaty of the Council of Europe the main purpose of which is to protect women against all forms of violence and to counter and eliminate all forms of violence against women including aspects of domestic violence. Footnote 46 The Istanbul Convention consists of four main pillars: (i) prevention, (ii) protection of victims, (iii) prosecution of offenders, and (iv) implementation of comprehensive and coordinated policies to combat violence against women at all levels of government. The Istanbul Convention establishes an independent group of experts known as the GREVIO (Group of Experts on Action against Violence against Women and Domestic Violence). The GREVIO is responsible for monitoring the effective implementation of the provisions of the Istanbul Convention by the now 34 States Parties. Footnote 47
The Istanbul Convention does not specifically contain specific provisions in the context of violence committed through the use of information technologies, however the GREVIO is currently analysing approaches to extend the application of the commission of illegal conducts through the use of computer and information systems within the national legal framework of State Parties. Footnote 48 The GREVIO adopted during its twenty-fifth meeting on 20 October 2021, a General Recommendation on the Digital Dimension of Violence against Women . Footnote 49 The Recommendation addresses inter alia the application of the general provisions of the Istanbul Convention in relation to conducts and crime typologies committed against women in cyberspace and proposes specific actions to take, based on the four pillars of the Istanbul Convention: prevention, protection, prosecution and coordinated policies.
As part of promoting the scope of the adopted General Recommendation, the GREVIO held a conference in Strasbourg in November 24, 2021 that featured a keynote address of the Commissioner of Human Rights of the Council of Europe and presentations of the President of the GREVIO and the Chair of the Committee of the Parties to the Istanbul Convention followed by a panel discussion with representatives of EU member states, internet industry and civil society. Footnote 50 Among the relevant points made during the panel discussions were how the recommendation may help to advance legal and policy developments, attention of victims of current forms of cyberviolence, further international cooperation and to contribute to the general understanding of the scope of the provisions of the Istanbul Convention and other key instruments of the Council of Europe including the Budapest Convention and the Lanzarote Convention in relation to digital violence against women. Footnote 51
The Cybercrime Convention Committee (T-CY) issued a comprehensive report titled Mapping Study on Cyberviolence with recommendations adopted by the TC-Y on 9 July, 2018. Footnote 52
The mapping study developed a working definition on “cyberviolence” Footnote 53 and described how the different forms of cyberviolence may be classified and criminalized under the Budapest-, Lanzarote- and Istanbul Conventions. According to the mapping study “not all forms of violence are equally severe and not all of them necessarily require a criminal law solution but could be addressed with a combination of preventive, educational, protective and other measures” . The main conclusions of the Cybercrime Convention Committee (T-CY) in the Mapping Study on Cyberviolence were:
the Budapest Convention and its additional Protocol on Racism and Xenophobia covers and address some types of cyberviolence;
the procedural powers and the provisions on international cooperation of the Budapest Convention will help to support the investigation of cyberviolence and the secure and preservation of digital evidence; and
the Budapest, the Istanbul and Lanzarote conventions complement each other and should promote synergies. These synergies may include raising further awareness and capacity building activities among Parties to said treaties; encourage parties to the Lanzarote and Istanbul Conventions to introduce the procedural powers contained in the Budapest Convention ( Arts. 16-21 ) into domestic law and consider becoming parties to the Budapest Convention to facilitate international cooperation on electronic evidence in relation to crimes related to cyberviolence; encourage parties to the Budapest Convention to implement the provisions on psychological violence, stalking and sexual harassment of the Istanbul Convention, as well as the provisions on sexual exploitation and abuse of children online of the Lanzarote Convention, among others . Footnote 54
Cyberviolence and crimes concerning the abuse and exploitation of children online require strategic cooperation of different stakeholders. Other key institutions at the regional level like the European Commission have also explored paths on how AI systems may help to identify, categorise and remove child sexual abuse images and to minimise the exposure of human investigators to distressing images and the importance of the role of internet hotlines in facilitation the reporting process. Footnote 55
5 Ongoing work of international organizations
5.1 council of europe cahai.
The Ad-Hoc Committee on Artificial Intelligence of the Council of Europe (CAHAI) Footnote 56 was established by the Committee of Ministers during its 1353rd meeting on 11 September 2019. Footnote 57 The specific task of CAHAI is “to complete the feasibility study and produce the potential elements on the basis of broad multi-stakeholder consultations, of a legal framework for the development, design and application of artificial intelligence, based on the Council of Europe’s standards on human rights, democracy and the rule of law.”
The work of CAHAI is relevant because it sets forth a multi-stakeholder group where global experts may provide their views on the development of policies on AI, to forward meaningful proposals to ensure the application of international treaties and technical standards on AI and submit proposals for the creation of a future legal instrument that will regulate AI while ensuring the protection of fundamental rights, rule of law and democracy principles contained in relevant instruments of the Council of Europe, like Convention 108+, the Budapest, Lanzarote and Istanbul Conventions, among others. Footnote 58
The work of CAHAI will impact the 47 members states and country observers of the Council of Europe, particularly state institutions including national parliamentarians and policy makers who are responsible for the implementation of international treaties into their national legal frameworks. Therefore, the inclusion and participation of relevant stakeholders from different nations will play a decisive role in the future implementation of a global treaty on AI in the coming years.
5.2 European Parliament
The European Parliament (EP) is perhaps the most proactive legislative and policy making institution worldwide. The European Parliament has a Centre for Artificial Intelligence known as (C4AI) that was established in December 2019. Footnote 59 The EP has Committees that analyse the impact of policy related aspects of AI in many different areas including cybersecurity, defence, predictive policing and criminal justice. The most active committee is the Special Committee on Artificial Intelligence in a Digital Age (AIDA Committee) Footnote 60 that has organized many hearings and workshops with different experts and stakeholders on AI from different regions of the world to hear views and opinions on the Regulation proposal for Artificial Intelligence Systems . Footnote 61
According to the President of the AIDA Committee, “the use of AI in law enforcement is a political decision and not a technical one, our duty is to apply the political worldview to determine what are the allowed uses of AI and under which conditions” . Footnote 62
As a result of the existing dangers and risks posed by the use of AI systems across Europe, the European Parliament adopted a resolution on 6 October 2021 that calls for a permanent ban on AI systems which allow for the use of automated recognition of individuals by law enforcement in public spaces. Further, the resolution calls for a moratorium on the deployment of facial recognition systems for law enforcement purposes and a ban on predictive policing based on behavioural data and social scoring in order to ensure the protection of fundamental rights of European citizens. Footnote 63
The Committee on Civil Liberties, Justice and Home Affairs of the European Parliament has also conducted relevant work on AI and criminal justice. On February 20, 2020, said committee conducted a public hearing on “Artificial Intelligence in Criminal Law and its use by the Police and Judicial Authorities” where relevant opinions and recommendations of experts and international organizations were discussed and presented. Footnote 64
Further, the AIDA Committee of the European Parliament held a two-day public hearing with the AFET Committee on March 1 st and 4 th 2021. The first hearing was on “AI Diplomacy and Governance in a Global Setting: Toward Regulatory Convergence”, and the second hearing on “AI, Cybersecurity and Defence”. Footnote 65 Many relevant aspects of AI policy were mentioned during the hearings, including the support of a transatlantic dialogue and cooperation on AI, the development of ethical frameworks and standards, the development of a shared system of norms, respect of fundamental rights, diplomacy and capacity building among others. Although, there was mention on the importance of AI for cybersecurity in the defence realm and how AI might be helpful to mitigate cyberattacks and protect critical infrastructure, there was no specific mention on how the current international treaties on cybercrime and national legal frameworks may coexist with a future treaty on AI to counter cybercrime more effectively.
The dialogue and engagement of the different committees of the European Parliament on AI policy is key for the future implementation of policies in the criminal justice area concerning the use and deployment of AI systems and applications. The European Parliament should continue to promote further dialogues and activities with other international organizations like the Council of Europe and the OECD, as well as with national parliamentarians around the world to help them understand the dimensions and implications of creating regulations and policies on AI to specifically counter cybercrime.
5.3 The UN Interregional Crime and Justice Research Institute (UNICRI) Centre for Artificial Intelligence and Robotics
The Centre for Artificial Intelligence and Robotics of the United Nations Interregional Crime and Justice Research Institute (UNICRI), a research arm of the United Nations is very active in the organization of workshops and information and reports to demystify the world of robotics and AI and to facilitate an in-depth understanding of the crimes and threats conducted through AI systems among law enforcement officers, policy makers, practitioners, academia and civil society. UNICRI and INTERPOL drafted the report “ Artificial Intelligence and Robotics for Law Enforcement” Footnote 66 in 2019 that draws upon the discussions of a workshop held in Singapore in July 2018. Among the main findings of UNICRI and INTERPOL’s report are:
“AI and Robotics are new concepts for law enforcement and there are expertise gaps that should be filled to avoid law enforcement falling behind.” “Some countries have explored further than others and a variety of AI techniques are materializing according to different law enforcement authorities. There is, however, a need for greater international coordination on this issue.”
The mandate of the Centre for Artificial Intelligence and Robotics of UNICRI is quite broad. It covers policy related aspects of AI in the field of criminal justice including areas such as cybersecurity, autonomous weapons, self-driving vehicles and autonomous patrol systems. UNCRI organizes every year the Global Meeting on Artificial Intelligence for Law Enforcement , an event that discusses relevant developments on AI with experts and stakeholders from different sectors and countries to enhance and improve the capabilities for law enforcement authorities and the criminal justice system in the use and deployment of AI technologies. Footnote 67
The Centre for Artificial Intelligence and Robotics of UNICRI is currently working with a group of experts from INTERPOL, the European Commission and other relevant institutions and stakeholders in the development of a Toolkit for Responsible AI Innovation in Law Enforcement . The toolkit will provide and facilitate practical guidance for law enforcement agencies around the world on the use of AI in a trustworthy, lawful and responsible manner. The toolkit addresses practical insights, use cases, principles, recommendations, best practices and resources which will help to support law enforcement agencies around the world to use AI technologies and applications. Footnote 68
6 Conclusion
The use of AI systems across different sectors is an ongoing trend, and this includes authorities of the criminal justice system which have realized the benefits and advantages of using this technology. National law enforcement authorities involved in the investigation of cybercrime are not yet fully prepared to deal with the technical and legal dimensions of AI when used for disruptive or malicious purposes. Further, there is no yet sufficient evidence to justify whether law enforcement authorities around the world are well equipped and trained to gather cross-border evidence to conduct national investigations where an AI system was involved in the commission or perpetration of an illicit conduct.
Second, the coordination and cooperation with service providers and companies that manage and operate AI systems and services is crucial to help determine its abuse and misuse by perpetrators. However, these tasks bring a number of technical and legal challenges, since most AI systems rely on an internet connection to function where oftentimes subscriber and traffic data is needed to conduct an investigation. Therefore, global service providers will also have an important role to play in the possible identification and location of cybercriminals, a situation that needs well-coordinated efforts, measures and responses based on international treaties and national laws between law enforcement authorities and private sector entities. The need for further strategic partnerships to counter cybercrime is more important than ever.
The future work of international organizations like UNICRI, the Council of Europe through CAHAI and the T-CY Committee of the Budapest Convention will be very relevant for policy makers and law enforcement authorities for the correct guidance in the implementation of future national policies on AI. The CAHAI may fill up the missing discussions in international fora concerning AI to specifically counter cybercrime based on the current standards of the Council of Europe like the Budapest Convention, the Lanzarote Convention and the Istanbul Convention, as well as the emerging practices of members states to specifically counter cyber enable crimes.
The creation of national taskforces on cybercrime (composed of law enforcement authorities, representatives of the judiciary, AI technology developers and global service providers) may serve as a relevant vehicle to coordinate and tackle illicit conducts concerning the misuse and abuse of AI technologies. These taskforces may be articulated in the context of the national strategies on AI and should be linked to the tasks of the criminal justice authorities to specifically counter cybercrime.
Burgess, Matt, “Police built an AI to predict violent crime. It was seriously flawed”, WIRED, August 6, 2020, available at: https://www.wired.co.uk/article/police-violence-prediction-ndas .
European Commission, “Liability for Artificial Intelligence and other emerging digital technologies”, Report from the Experts Group on Liability and New Technologies-New Technologies Formation, European Union 2019, available at: https://digital-strategy.ec.europa.eu/en/policies/european-approach-artificial-intelligence . See also: European Parliament Research Service (EPRS), “The European added value of a common EU approach to liability rules and insurance for connected and autonomous vehicles” Study published by the European Added Value Unit, February 2018, available at: https://www.europarl.europa.eu/RegData/etudes/STUD/2018/615635/EPRS_STU(2018)615635_EN.pdf .
MIT Technology Review, “Transforming the Energy Industry with AI”, January 21, 2021, available at: https://www.technologyreview.com/2021/01/21/1016460/transforming-the-energy-industry-with-ai/ .
World Health Organization (WHO), “WHO reports fivefold increase in cyberattacks, urges vigilance”, April 23, 2020, available at: https://www.who.int/news/item/23-04-2020-who-reports-fivefold-increase-in-cyber-attacks-urges-vigilance .
The New York Times, “Cyber Attack Suspected in German Woman’s Death”, September 18, 2020, available at: https://www.nytimes.com/2020/09/18/world/europe/cyber-attack-germany-ransomeware-death.html .
Supply Chain, “Lessons Learned from the Vaccine Supply Chain Attack”, January 16, 2021, available at: https://www.supplychaindigital.com/supply-chain-risk-management/lessons-learned-vaccine-supply-chain-attack .
Prakarsh and Riya Khanna, “Artificial Intelligence and Cybercrime- A curate’s Egg”, Medium, June 14, 2020, available at: https://medium.com/the-%C3%B3pinion/artificial-intelligence-and-cybercrime-a-curates-egg-2dbaee833be1 .
INTSIGHTS, “The Dark Side of Latin America: Cryptocurrency, Cartels, Carding and the Rise of Cybercrime”, p.6, available at: https://wow.intsights.com/rs/071-ZWD-900/images/Dark%20Side%20of%20Latin%20America.pdf . See also, “The Next, El Chapo is Coming for your Smartphone”, June 26, 2020, available at: https://www.ozy.com/the-new-and-the-next/the-next-el-chapo-might-strike-your-smartphone-and-bank/273903/ .
Malwarebytes Lab, “When Artificial Intelligence goes awry: separating science fiction from fact”, without publication date, available at: https://resources.malwarebytes.com/files/2019/06/Labs-Report-AI-gone-awry.pdf .
SIEMENS Energy, “Managed Detection and Response Service”, 2020, available at: https://assets.siemens-energy.com/siemens/assets/api/uuid:a95b9cd3-9f4d-4a54-8c43-77fbdb6f418f/mdr-white-paper-double-sided-200930.pdf .
POLITICO, “Automated racism: How tech can entrench bias”, March 2, 2021, available at: https://www.politico.eu/article/automated-racism-how-tech-can-entrench-bias/ .
For a discussion on discrimination caused by algorithmic decision making on AI, see ZUIDERVEEN BORGESIUS, Frederik, “Discrimination, Artificial Intelligence and Algorithmic decision making”. Paper published by the Directorate General of Democracy of the Council of Europe, 2018, available at: https://rm.coe.int/discrimination-artificial-intelligence-and-algorithmic-decision-making/1680925d73 .
See the Special Report on Facial Recognition of the Center for AI and Digital Policy (CAIDP) that contains a summary of key references on this topic contained in the 2020 Report on Artificial Intelligence and Democratic Values / The AI Social Contract Index 2020 prepared by CAIDP, December 2020, available at: https://caidp.dukakis.org/aisci-2020/ .
In October 2021, the European Parliament adopted a resolution to ban the use facial recognition technologies in public spaces by law enforcement authorities to ensure the protection of fundamental rights. See European Parliament, “Use of Artificial Intelligence by the police: MEPs oppose mass surveillance”. LIBE Plenary Session press release, October 6, 2021, available at: https://www.europarl.europa.eu/news/en/press-room/20210930IPR13925/use-of-artificial-intelligence-by-the-police-meps-oppose-mass-surveillance .
BBC, “What are ‘bots’ and how can they spread fake news, available at: https://www.bbc.co.uk/bitesize/articles/zjhg47h .
FORBES, “Fake News is Rampant, Here is How Artificial Intelligence Can Help” , January 21, 2021, available at: https://www.forbes.com/sites/bernardmarr/2021/01/25/fake-news-is-rampant-here-is-how-artificial-intelligence-can-help/?sh=17a6616e48e4 .
European Commission, “Tackling online disinformation”, 18 January 2021, available at: https://ec.europa.eu/digital-single-market/en/tackling-online-disinformation . For a general review of policy implications in the UK concerning the use of AI and content moderation, see Cambridge Consultants, “Use of AI in Online Content Moderation” . 2019 Report produced on behalf of OFCOM, available at: https://www.ofcom.org.uk/__data/assets/pdf_file/0028/157249/cambridge-consultants-ai-content-moderation.pdf .
Deepfakes are based on AI deep learning algorithms, an area of machine learning that applies neural net simulation to massive data sets to create fakes videos of real people. Deepfakes are trained algorithms that allows the recognition of data patterns, as well as human facial movement and expressions and can match voices that can imitate the real voice and gestures of an individual. See: European Parliamentary Research Service, “What if deepfakes made us doubt everything we see and hear (Science and Technology podcast], available at: https://epthinktank.eu/2021/09/08/what-if-deepfakes-made-us-doubt-everything-we-see-and-hear/ . Like, many technologies, deepfakes can be used as a tool for criminal related purposes such as fraud, extortion, psychological violence and discrimination against women and minors, see: MIT Technology Review, “A deepfake bot is being used to “undress” underage girls”, October 20, 2020, available at: https://bit.ly/3qj1qWx .
For specific information regarding the work of the US government to counter the use of deepfakes, see CNN, “ Inside the Pentagon’s race against deepfake videos” , available at: https://bit.ly/38aEqCS https://edition.cnn.com/interactive/2019/01/business/pentagons-race-against-deepfakes/ .
EURACTIV, “EU police recommend new online ‘screening tech’ to catch deepfakes”, November 20, 2020, available at: https://www.euractiv.com/section/digital/news/eu-police-recommend-new-online-screening-tech-to-catch-deepfakes/ .
The Verge, “Watch Jordan Peele use AI to make Barack Obama deliver a PSA about fake news”, April 17, 2018, available at: https://www.theverge.com/tldr/2018/4/17/17247334/ai-fake-news-video-barack-obama-jordan-peele-buzzfeed .
Wall Street Journal, “Fraudsters Use AI to Mimic CEO’s Voice in Unusual Cybercrime Case”, August 30, 2019, available at: https://www.wsj.com/articles/fraudsters-use-ai-to-mimic-ceos-voice-in-unusual-cybercrime-case-11567157402 .
GIZMODO, “Bank Robbers in the Middle East Reportedly ‘Cloned’ Someone’s Voice to Assist with $35 Million Heist”, October 14, 2021, available at: https://gizmodo.com/bank-robbers-in-the-middle-east-reportedly-cloned-someo-1847863805 .
The EC3 of Europol has developed good capacities and practice with other countries in the deployment of joint investigation teams to counter organized crime, including cybercrime. See the section on Join Investigation Team of Europol at: https://www.europol.europa.eu/activities-services/joint-investigation-teams .
INTERPOL (EC3), “Internet Crime Assessment Report 2020” (IOCTA 2020 Report), p. 18, available at: https://www.europol.europa.eu/activities-services/main-reports/internet-organised-crime-threat-assessment-iocta-2020 . The Internet Crime Assessment Report 2021 (IOCTA 2021 Report) was published on 11 November 2021. The report of this year does not actually make any novel references to misuse and abuse of AI systems for criminal purposes, available at: https://www.europol.europa.eu/activities-services/main-reports/internet-organised-crime-threat-assessment-iocta-2021 .
IOCTA 2020 Report, Op. cit . note 25, p. 18.
Trend Micro Research, EUROPOL EC3 and UN Interregional Crime and Justice Research Institute (UNICRI), Malicious Uses and Abuses of Artificial Intelligence , 19 November 2020, available at: https://www.europol.europa.eu/publications-documents/malicious-uses-and-abuses-of-artificial-intelligence .
This report was also presented in a workshop on cybercrime, e-evidence and artificial intelligence during the 2021 Octopus Conference on Cooperation against Cybercrime organized by the Council of Europe on November 17, 2021 where the representatives of each organization highlighted the main aspects and features of the report, including current trends and concrete examples of misuse of AI technologies. The presentation is available at: https://rm.coe.int/edoc-1193149-v1-coe-ai-ppt/1680a4892f . The Digital Services Act establishes new rules and requirements for intermediary service providers which includes hosting providers and online platforms. This regulation covers inter alia rules on liability for online intermediary service platforms, establishes internal complaint handling systems and implement measures against online legal content. The Digital Services Act is currently a draft proposal under discussion between the European Parliament and the Council of the EU and it may take some years until it is finally approved, available at: https://digital-strategy.ec.europa.eu/en/policies/digital-services-act-package .
See Proposal for a Regulation of the European Parliament and the Council laying down harmonized rules on Artificial Intelligence (Artificial Intelligence Act) and Amending Certain Union Legislative Acts, Brussels 21.4.2021, available at: https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:52021PC0206&from=EN .
See: European Commission, “Europe fit for the Digital Age: Commission proposes new rules and actions for excellence and trust in Artificial Intelligence”, Brussels, April 21, 2021, available at: https://ec.europa.eu/commission/presscorner/detail/en/ip_21_1682 . See also the website of the European Commission that explains the approach of the EC on AI and the relevant milestones in this area, available at: https://digital-strategy.ec.europa.eu/en/policies/european-approach-artificial-intelligence .
Among those instruments are: (i) The United Convention against Organized Crime and its Protocols ( Palermo Convention ); (ii) The Council of Europe Convention on Cybercrime ( Budapest Convention ) and its Additional Protocol concerning the criminalisation of acts of a racist and xenophobic nature committed through computer systems; (iii) The Council of Europe Convention on Protection of Children against Sexual Exploitation and Sexual Abuse ( Lanzarote Convention ); (iv) The African Union Convention on Cyber Security and Personal Data Protection ( Malabo Convention ); (v) Directive 2013/40/UE on attacks against information systems; (vi) Directive 2011/92/UE on combating the sexual abuse and exploitation of children and child pornography, among others.
The Budapest Convention requires that Party States amend their substantive and procedural criminal legislation to make it consistent with the substantive and procedural criminal law provisions of that treaty. Considering that cybercrime has a transnational dimension, the Budapest Convention also requires that countries implement international cooperation measures either to supplement or complement the existing ones, particularly when a country does not have mutual assistance and cooperation treaties in criminal matters in place, as well as to equip investigative and law enforcement authorities with the necessary tools and procedural mechanisms to conduct cybercrime investigations including measures concerning: (i) expedited preservation of stored computer data, (ii) disclosure of preserved traffic data, (iii) mutual assistance measures regarding access to stored computer data, (iv) trans-border access to stored computer data, (v) mutual assistance regarding real-time collection of traffic data, (vi) mutual assistance regarding the interception of content data, and the (vii) creation of a network or point of contact 24/7 to centralize investigations and procedures related to requests for data and mutual assistance concerning cybercrime investigations with other 27/7 points of contact.
See the Budapest Convention Chart of Signatures and Ratifications at: https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/185/signatures?p_auth=yUQgCmNc .
Cybercrime Convention Committee, “T-CY Rules of Procedure. As revised by T-CY on 16 October 2020”, Strasbourg, 16 October 2020, available at: https://rm.coe.int/t-cy-rules-of-procedure/1680a00f34 .
Council of Europe, “Second Additional Protocol to the Budapest Convention adopted by the Committee of Ministers of the Council of Europe”, Strasbourg, 17 November 2021, available at: https://www.coe.int/en/web/cybercrime/-/second-additional-protocol-to-the-cybercrime-convention-adopted-by-the-committee-of-ministers-of-the-council-of-europe .
See the text of the Explanatory Report of the Second Additional Protocol to the Budapest Convention drafted by Cybercrime Convention Committee (T-CY) at: https://search.coe.int/cm/pages/result_details.aspx?objectid=0900001680a48e4b .
See the Explanatory Report to the Convention on Cybercrime at: https://rm.coe.int/CoERMPublicCommonSearchServices/DisplayDCTMContent?documentId=09000016800cce5b .
The Conference program of the 2018 Octopus conference on cooperation against cybercrime is available at: https://rm.coe.int/3021-90-octo18-prog/16808c2b04 .
See: Activities of the Council of Europe on Artificial Intelligence (AI), 9 May, 2018, available at: https://rm.coe.int/cdmsi-2018-misc8-list-ai-projects-9may2018/16808b4eac .
See the presentations of this panel at the Plenary Closing session of the 2018 Octopus Conference, available at: https://www.coe.int/en/web/cybercrime/resources-octopus-2018 .
The presentation and materials of this panel are available at: https://www.coe.int/en/web/cybercrime/workshop-cybercrime-e-evidence-and-artificial-intelligence .
The Lanzarote Convention entered in force on 1 July 2010, available at: https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/201/signatures . Among the conducts that the Lanzarote Convention requires Sates parties to criminalize are: (i) Child sexual abuse; (ii) sexual exploitation through prostitution; (iii) child sexual abuse material; (iv) exploitation of a child in sexual performances; (v) corruption of children, and (vi) solicitation of children for sexual purposes.
See the Booklet of the Lanzarote Convention, available at: https://rm.coe.int/lanzarote-convention-a-global-tool-to-protect-children-from-sexual-vio/16809fed1d .
The Rules of procedure, adopted documents, activity reports and the Meetings of the ‘Lanzarote Committee’ are available at: https://www.coe.int/en/web/children/lanzarote-committee#{%2212441908%22:[] .
The Istanbul Convention entered into force on 1 August 2014 and it has been ratified by 34 countries. See the chart of signatures and ratifications at: https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/210/signatures?p_auth=OwhAGtPd .
The Rules of procedure and adopted documents of the GREVIO are available at: https://www.coe.int/en/web/istanbul-convention/grevio .
See the presentations of the webinar, “Cyberviolence against Women” organized by the CyberEast Project of the Council of Europe, 12 November, 2020, available at: https://www.coe.int/en/web/cybercrime/cyberviolence-against-women .
The Text of the GREVIO General Recommendation No. 1 on the digital dimension of violence against women adopted on 20 October 2021 is available at: https://rm.coe.int/grevio-rec-no-on-digital-violence-against-women/1680a49147 .
Council of Europe, “Launch Event: Combating violence against women in a digital age-utilizing the Istanbul Convention”, 24 November 2021, available at: https://www.coe.int/en/web/istanbul-convention/launching-event-of-grevio-s-first-general-recommendation-on-the-digital-dimension-of-violence-against-women .
Council of Europe Media Release, “New Council of Europe Recommendation tackles the ‘digital dimension” of violence against women and girls”, Strasbourg, 24 November, 2021, available at: https://search.coe.int/directorate_of_communications/Pages/result_details.aspx?ObjectId=0900001680a4a67b .
Council of Europe Cybercrime Convention Committee (TC-Y), “Mapping Study on Cybercrime” with recommendations adopted by the TC-Y on 9 July 2018, available at: https://rm.coe.int/t-cy-2017-10-cbg-study-provisional/16808c4914 .
The definition is an adaptation of the definition of violence against women contained in Art. 3 of the Istanbul Convention to the cyber context as follows: “ Cyberviolence is the use of computer systems to cause, facilitate, or threaten violence against individuals that results in, or is likely to result in, physical, sexual, psychological or economic harm or suffering and may include the exploitation of the individual’s circumstances, characteristics or vulnerabilities” .
“Mapping Study on Cybercrime”, Op. cit . note 52, pp. 42-43.
European Commission, “Exploring potential of AI in fight against child online abuse”, Event report 11 June 2020, available at: https://ec.europa.eu/digital-single-market/en/news/exploring-potential-ai-fight-against-child-online-abuse .
CAHAI’s composition consist of three main groups composed of up to 20 experts appointed by Members States, as well as observers and participants. The mandate of the Policy Development Group (CAHAI-PDG) is the development of the feasibility study of a legal framework on artificial intelligence applications, building upon the mapping work already undertaken by the CAHAI and to prepare key findings and proposals on policy and other measures, to ensure that international standards and international legal instruments in this area are up-to-date and effective and prepare proposals for a specific legal instrument regulating artificial intelligence. The Consultation and Outreach Group (CAHAI-COG) is responsible for taking stock of the analysis undertaken by the Secretariat of responses to online consultations and analysis of ongoing developments and reports which are directly relevant for CAHAI’s working groups’ tasks. The Legal Frameworks Group (CAHAI-LFG) is responsible for the preparation of key findings and proposals on possible elements and provisions of a legal framework with a view to draft legal instruments, for consideration and approval by the CAHAI, taking into account the scope of existing legal instruments applicable to artificial intelligence and policy options set out in the feasibility study approved by the CAHAI. Further info on the composition of CAHAI working groups, the plenary meetings and the documents issued by the three working groups is available at: https://www.coe.int/en/web/artificial-intelligence/cahai .
The terms of reference of CAHAI are available at: https://search.coe.int/cm/Pages/result_details.aspx?ObjectId=09000016809737a1 .
The Final Virtual Plenary Meeting of CAHAI from 30.11.2021 to 02.12.2021 will facilitate meaningful discussions towards the adoption of a document outlining the possible elements of a legal framework on AI, which may include binding and non-binding standards based on the Council of Europe’s standards on human rights, democracy and rule of law. See Council of Europe, “The CAHAI to hold its final meeting”, Strasbourg, 24 November 2021, available at: https://www.coe.int/en/web/artificial-intelligence/-/cahai-to-hold-its-final-meeting .
European Parliament, “STOA Centre for Artificial Intelligence (C4AI)”. The C4AI produces studies, organises public events and acts as a platform for dialogue and information exchange and coordinate its efforts and influence global AI standard-setting, available at: https://www.europarl.europa.eu/stoa/en/centre-for-AI .
The AIDA Committee website is available at: https://www.europarl.europa.eu/committees/en/aida/home/highlights .
See supra note 30.
See Dragos Tudorache Plenary Speech on Artificial Intelligence of 4 October 2021, available at: https://www.youtube.com/watch?v=V9y5gt39AD0 .
European Parliament News, “Use of artificial intelligence by the police: MEPs oppose mass surveillance”. Press release of the Plenary Session, October 6, 2021, available at: https://www.europarl.europa.eu/news/en/press-room/20210930IPR13925/use-of-artificial-intelligence-by-the-police-meps-oppose-mass-surveillance and Eurocadres, “European Parliament adopts resolution on the use of AI in law enforcement”, October 6, 2021, available at: https://www.eurocadres.eu/news/european-parliament-adopts-resolution-on-the-use-of-ai-in-law-enforcement/ .
European Parliament. “MEPs to look into Artificial Intelligence in criminal law on Thursday”, February 18, 2020, available at: https://www.europarl.europa.eu/news/en/press-room/20200217IPR72718/meps-to-look-into-artificial-intelligence-in-criminal-law-on-thursday .
European Parliament, Special Committee on Artificial Intelligence in a Digital Age (AIDA), “Joint hearing on the external policy dimension of AI”, March 1 st and 4 th 2021, available at: https://www.europarl.europa.eu/meetdocs/2014_2019/plmrep/COMMITTEES/AIDA/DV/2021/03-01/Final_Programme_externalpolicydimensionofAI_V26FEB_EN.pdf .
UNICRI and INTERPOL, “ Artificial Intelligence and Robotics for Law Enforcement” , 2019, available at: https://issuu.com/unicri/docs/artificial_intelligence_robotics_la/4?ff .
UNCRI, “2 nd INTERPOL, UNICRI Global Meeting on Artificial Intelligence for Law Enforcement”, Singapore, July 3, 2019, available at: http://www.unicri.it/news/article/ai_unicri_interpol_law_enforcement .
UNICRI, “The European Commission provides support to UNICRI for the Development of the Toolkit for Responsible AI Innovation in Law Enforcement”, The Hague, Monday November 1, 2021, available at: http://www.unicri.it/index.php/News/EC-UNICRI-agreement-toolkit-responsible-AI .
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and affiliations.
Center for AI and Digital Policy (CAIDP), Washington (DC), USA
Cristos Velasco
DHBW Cooperative State University in Mannheim and Stuttgart, Stuttgart, Germany
Mexico City, Mexico
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Cristos Velasco .
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
C. Velasco is Research Fellow and Outreach Committee Board Member of the Center for AI and Digital Policy (CAIDP), also Law Lecturer on “Information Technology Law” and “International Business Law & International Organizations” at the DHBW Cooperative State University in Mannheim and Stuttgart.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Velasco, C. Cybercrime and Artificial Intelligence. An overview of the work of international organizations on criminal justice and the international applicable instruments. ERA Forum 23 , 109–126 (2022). https://doi.org/10.1007/s12027-022-00702-z
Download citation
Accepted : 24 January 2022
Published : 22 February 2022
Issue Date : May 2022
DOI : https://doi.org/10.1007/s12027-022-00702-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Budapest Convention
- Criminal justice
- Istanbul Convention
- Law enforcement
- Lanzarote Convention
- Find a journal
- Publish with us
- Track your research
- Home Products
- Small Business 1-49 employees
- Medium Business 50-999 employees
- Enterprise 1000+ employees
What is cybercrime? How to protect yourself

What is cybercrime?
Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most cybercrime is committed by cybercriminals or hackers who want to make money. However, occasionally cybercrime aims to damage computers or networks for reasons other than profit. These could be political or personal.
Cybercrime can be carried out by individuals or organizations. Some cybercriminals are organized, use advanced techniques and are highly technically skilled. Others are novice hackers.
What are the types of cybercrime?
Types of cybercrime include:
- Email and internet fraud.
- Identity fraud (where personal information is stolen and used).
- Theft of financial or card payment data.
- Theft and sale of corporate data.
- Cyberextortion (demanding money to prevent a threatened attack).
- Ransomware attacks (a type of cyberextortion).
- Cryptojacking (where hackers mine cryptocurrency using resources they do not own).
- Cyberespionage (where hackers access government or company data).
- Interfering with systems in a way that compromises a network.
- Infringing copyright.
- Illegal gambling.
- Selling illegal items online.
- Soliciting, producing, or possessing child pornography.
Cybercrime involves one or both of the following:
- Criminal activity targeting computers using viruses and other types of malware .
- Criminal activity using computers to commit other crimes.
Cybercriminals that target computers may infect them with malware to damage devices or stop them working. They may also use malware to delete or steal data. Or cybercriminals may stop users from using a website or network or prevent a business providing a software service to its customers, which is called a Denial-of-Service (DoS) attack.
Cybercrime that uses computers to commit other crimes may involve using computers or networks to spread malware, illegal information or illegal images.
Cybercriminals are often doing both at once. They may target computers with viruses first and then use them to spread malware to other machines or throughout a network. Some jurisdictions recognize a third category of cybercrime which is where a computer is used as an accessory to crime. An example of this is using a computer to store stolen data.

Examples of cybercrime
Here are some famous examples of different types of cybercrime attack used by cybercriminals:
1. Malware attacks
A malware attack is where a computer system or network is infected with a computer virus or other type of malware. A computer compromised by malware could be used by cybercriminals for several purposes. These include stealing confidential data, using the computer to carry out other criminal acts, or causing damage to data.
A famous example of a malware attack was the WannaCry ransomware attack, a global cybercrime committed in May 2017. WannaCry is a type of ransomware, malware used to extort money by holding the victim’s data or device to ransom. The ransomware targeted a vulnerability in computers running Microsoft Windows.
When the WannaCry ransomware attack hit, 230,000 computers were affected across 150 countries. Users were locked out of their files and sent a message demanding that they pay a Bitcoin ransom to regain access.
Worldwide, the WannaCry cybercrime is estimated to have caused $4 billion in financial losses. To this day, the attack stands out for its sheer size and impact.
2. Phishing
A phishing campaign is when spam emails, or other forms of communication, are sent with the intention of tricking recipients into doing something that undermines their security. Phishing campaign messages may contain infected attachments or links to malicious sites, or they may ask the receiver to respond with confidential information.
A famous example of a phishing scam took place during the World Cup in 2018. According to our report, 2018 Fraud World Cup , the World Cup phishing scam involved emails that were sent to football fans. These spam emails tried to entice fans with fake free trips to Moscow, where the World Cup was being hosted. People who opened and clicked on the links contained in these emails had their personal data stolen.
Another type of phishing campaign is known as spear-phishing . These are targeted phishing campaigns which try to trick specific individuals into jeopardizing the security of the organization they work for.
Unlike mass phishing campaigns, which are very general in style, spear-phishing messages are typically crafted to look like messages from a trusted source. For example, they are made to look like they have come from the CEO or the IT manager. They may not contain any visual clues that they are fake.
3. Distributed DoS attacks
Distributed DoS attacks (DDoS) are a type of cybercrime attack that cybercriminals use to bring down a system or network. Sometimes connected IoT (Internet of Things) devices are used to launch DDoS attacks.
A DDoS attack overwhelms a system by using one of the standard communication protocols it uses to spam the system with connection requests. Cybercriminals who are carrying out cyberextortion may use the threat of a DDoS attack to demand money. Alternatively, a DDoS may be used as a distraction tactic while another type of cybercrime takes place.
A famous example of this type of attack is the 2017 DDoS attack on the UK National Lottery website . This brought the lottery’s website and mobile app offline, preventing UK citizens from playing. The reason behind the attack remains unknown, however, it is suspected that the attack was an attempt to blackmail the National Lottery.

Impact of cybercrime
Generally, cybercrime is on the rise. According to Accenture’s State of Cybersecurity Resilience 2021 report , security attacks increased 31% from 2020 to 2021. The number of attacks per company increased from 206 to 270 year on year. Attacks on companies affect individuals too since many of them store sensitive data and personal information from customers.
A single attack – whether it’s a data breach, malware, ransomware or DDoS attack - costs companies of all sizes an average of $200,000, and many affected companies go out of business within six months of the attack, according to insurance company Hiscox .
Javelin Strategy & Research published an Identity Fraud Study in 2021 which found that identity fraud losses for the year totalled $56 billion.
For both individuals and companies, the impact of cybercrime can be profound – primarily financial damage, but also loss of trust and reputational damage.
How to report a cybercrime
File a report with the Internet Crime Complaint Center (IC3) as soon as possible. Visit ic3.gov for more information.
Contact Action Fraud as soon as possible – find out more on their website here.
Europol has a useful website here which collates the relevant cybercrime reporting links for each EU member state.
You can find information about how to report cybercrime in the UAE on this official website here .
The Australian Cyber Security Centre has information about how to report a cybercrime here.
- How to protect yourself against cybercrime
Given its prevalence, you may be wondering how to stop cybercrime? Here are some sensible tips to protect your computer and your personal data from cybercrime:
1. Keep software and operating system updated
Keeping your software and operating system up to date ensures that you benefit from the latest security patches to protect your computer.
2. Use anti-virus software and keep it updated
Using anti-virus or a comprehensive internet security solution like Kaspersky Premium is a smart way to protect your system from attacks. Anti-virus software allows you to scan, detect and remove threats before they become a problem. Having this protection in place helps to protect your computer and your data from cybercrime, giving you piece of mind. Keep your antivirus updated to receive the best level of protection.
3. Use strong passwords
Be sure to use strong passwords that people will not guess and do not record them anywhere. Or use a reputable password manager to generate strong passwords randomly to make this easier.
4. Never open attachments in spam emails
A classic way that computers get infected by malware attacks and other forms of cybercrime is via email attachments in spam emails. Never open an attachment from a sender you do not know.
5. Do not click on links in spam emails or untrusted websites
Another way people become victims of cybercrime is by clicking on links in spam emails or other messages, or unfamiliar websites. Avoid doing this to stay safe online.
6. Do not give out personal information unless secure
Never give out personal data over the phone or via email unless you are completely sure the line or email is secure. Make certain that you are speaking to the person you think you are.
7. Contact companies directly about suspicious requests
If you are asked for personal information or data from a company who has called you, hang up. Call them back using the number on their official website to ensure you are speaking to them and not a cybercriminal. Ideally, use a different phone because cybercriminals can hold the line open. When you think you’ve re-dialed, they can pretend to be from the bank or other organization that you think you are speaking to.
8. Be mindful of which website URLs you visit
Keep an eye on the URLs you are clicking on. Do they look legitimate? Avoid clicking on links with unfamiliar or URLs that look like spam. If your internet security product includes functionality to secure online transactions, ensure it is enabled before carrying out financial transactions online.
9. Keep an eye on your bank statements
Spotting that you have become a victim of cybercrime quickly is important. Keep an eye on your bank statements and query any unfamiliar transactions with the bank. The bank can investigate whether they are fraudulent.
A good antivirus will protect you from the threat of cybercrime. Learn more about Kaspersky Premium.
Further reading:
- How to protect your data online by using a password manager
- What to do if you’ve been a victim of a phishing attack
- Ransomware protection: how to keep your data safe in 2024
Related videos:
Featured Articles

Black Friday Scams: How to Shop Safely Online

What is a dark web scan?

The Biggest Crypto Exchange Hacks: How to Make Sure You Protect Your Crypto Against Hacks

What Can Hackers Do With Your Email Address?

What is SIM Swapping?
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information .
The Journal of the NPS Center for Homeland Defense and Security
21st Century Crime: How Malicious Artificial Intelligence Will Impact Homeland Security
By Kevin Peters

Kevin Peters' thesis
– Executive Summary –
Artificial intelligence (AI) has the potential to dramatically transform how society interacts with information technology, particularly how personal information will interconnect with the hardware and software systems people use on a daily basis. The combination of developing AI systems and a digitally connected society could transform our culture in a manner not seen since the Industrial Revolution. Experts in the field of AI disagree on the pace at which the technology will develop; however, cognitive computing and machine learning are likely to affect homeland security in the coming years. Criminals, motivated by profit, are likely to adapt future AI software systems to their operations, further complicating present-day cybercrime investigations. If the homeland security enterprise is going to be prepared for the potential malicious usage of AI technology, it must begin to examine how criminal elements may use the technology and what should be done today to ensure it is ready for tomorrow’s threat.
This thesis examines how transnational criminal organizations and cybercriminals may leverage developing AI technology to conduct more sophisticated criminal activities and what steps the homeland security enterprise should take to prepare. A byproduct of ongoing research is that criminals may create malevolent AI. Cybercriminals, motivated by profit, may attempt to develop proxy AI systems that mask their involvement, avoid risk, and direct attribution and responsibility. The malicious use of AI could threaten digital security, and machines could become as proficient at hacking and social engineering as human cybercriminals. The ability to detect cybersecurity attacks from malicious AI is predicated on an examination of these technologies and their application to existing criminal patterns and activities. Criminals have long demonstrated that they are early adopters of new technologies, and they will almost certainly incorporate AI into their criminal enterprises.
This thesis applied a red-teaming approach—using a future scenario methodology—to project how cybercriminals may use AI systems and what should be done now to protect the United States from the malicious use of AI. The analysis first considered current fields of AI research, likely timelines for technological developments, and AI’s perceived impact on daily life in the United States over the next ten years. Next, the analysis examined how present-day cybercrime threats—such as remote-controlled aerial systems, the ability to create fake video files, spear phishing attacks, and social media profiling—could be enhanced by future AI systems. The final step in the analysis was to examine these scenarios and build countermeasures that homeland security officials in the United States could employ to mitigate the potential risks of malicious AI. The criminal use of AI will likely affect multiple echelons of government, and a strategic review analyzes the policy framework required to confront the threats identified in the AI scenarios. Best practices from foreign partners were examined to find strategies and methodologies that could be applied within the United States. A tactical review analyzed how law enforcement agencies could respond to the attacks in the AI scenarios and what existing law enforcement operations could be adapted to prepare for malicious AI.
The progression of AI is uncertain, and the scenarios highlight the ways that cybercriminals could leverage even relatively minor technological developments. Education and awareness of emerging technologies should form the basis of how cybercrime is examined. The thesis recommends that the homeland security enterprise expand outreach programs and partner with private industry and academia that are developing AI systems in order to understand the dual-use implications of emerging AI technology. Public security officials also have much to offer the AI research community; perspectives from law enforcement, emergency response, policymakers, and intelligence officials will be vital to assisting in the development of safe and ethical AI systems. Federal agencies with cybercrime enforcement authority should develop strategies that align with existing national cyber and AI strategies and can form the framework for confronting the potential challenge of future AI-enabled cybercrime.
This research concludes that the potential threats posed by cybercriminals’ use of AI are not a challenge that can be mitigated by any one agency. Rather, a coalition of willing partners across multiple echelons of government, private industry, and academia will need to work together to combat future cybercrime. International partnerships with law enforcement agencies and associations that support anti-crime operations will also be critical in tracking, investigating, and prosecuting future cybercrime. This thesis begins the discussion of how to confront the challenge of future AI-enabled cybercrime and seeks to expand awareness of how to combat dual-use emerging technologies.
Find all CHDS Theses
Homeland Security Digital Library's Thesis Repository
More Articles

Beyond the Border: The Impact of Flawed Migration Strategies in South and Central America on U.S. Immigration
Do the dutch know much a comparative analysis of gender and use of force in law enforcement in the netherlands and the united states, all hands on deck: a preparedness analysis of municipal fire department mutual aid during fires aboard u.s. navy vessels, legitimation of the police: a practitioner’s framework, leave a comment cancel reply.
Your email address will not be published. Required fields are marked *


Profiling the Cybercriminal
This is a summary of a presentation given by Dr Maria Bada , former research fellow at the Global Cyber Security Capacity Centre, and Dr Jason R. C. Nurse , former researcher at Cyber Security Oxford , during the International Crime and Intelligence Analysis Conference in February 2016 . The purpose of the presentation was to reflect on the current research and practice in the field of cybercrime, to present different methods of profiling cybercriminals and case scenarios, and to outline a future research agenda.
The Challenge
The challenge for research on cybercrime (or crime perpetrated using online technological means) is that it, at one hand, comprises any crime that involves a computer and a network . On the other hand, it relates to any crime committed on the Internet using the computer either as a tool or as target . The difference of those perspectives is that in the first case, the crime does not require a high level of technical expertise and aims to attack an individual in the real world in a subtle manner and /or on the psychological level. When using the computer as a target, crimes are often committed by groups of collaborating individuals. This requires a high level technical knowledge and skills, as well as coordination of those individuals, which makes this kind of crime often very sophisticated.
The Research
Current research focuses on the impact of an attack and its economic (and financial) harm, less on the cybercriminal itself . The existing stereotype of the uncertain, geeky hacker, is no longer accurate and attackers now are often cautious and stealthy. Practitioners cope with the situation in different ways: Governments attempt to respond with laws, corporations with policies and procedures, suppliers with terms and conditions, users with peer pressure, and technologists with code. The challenge for them as well for researchers is to factor in an understanding of criminal behaviour that has been amplified and facilitated by technology (Europol, 2011).
The Cybercriminal Profile
The key step in profiling a cybercriminal is identifying specific common characteristics that need to be investigated: Personal traits and characteristics comprise innate aspects such as openness, conscientiousness, extroversion, agreeableness, and neuroticism. Also, personal traits and characteristics are shaped by life experiences and events thus leading to machiavellianism, narcissism, psychopathy, sensation seeking maturity, aggressiveness, social-skill problems, superficiality, (lack of) self-esteem and personal integrity. The motivating factors for cybercriminals reach from hacktivism, monetary gain, espionage/ sabotage, and political/ religious belief, to curiosity/boredom, emotion/ sexual impulses, intolerance, thrill-seeking, enhancing self-worth, and the intent to control/manipulate others. Besides that, Rogers Mitchell (2006) has identified types of cybercriminals distinguished by their skill levels and motivations, such as novice, cyber-punks, internals (insider threat), coders, information warriors/cyber-terrorists, old guard hackers, and professional cybercriminals.
In practice, forensic psychologists use inductive or deductive profiling to make an educated guess of the characteristics of criminals. Inductive criminal profiles are developed by studying statistical data involving known behavioural patterns and demographic characteristics shared by criminals. Deductive profiling uses a range of data, e.g. including forensic evidence, crime scene evidence, victimology, and offender characteristics. A model example for a deductive cybercriminal profile (Nykodym et al., 2005) take information regarding the victim, the motive, the offender, and any forensic evidence.
Another way for profiling cybercriminals is the framework for understanding insider threat (Nurse et al., 2014) by the University of Oxford. It takes precipitating event (e.g. demotion) to look at a variety of actor characteristics and how those shape the character and the aim of an attack (see fig. 1)

The Case Scenarios
Using the existing literature and information available online presentation focused on analysing the profiles of cybercriminals based on two case scenarios:
Traits / Social characteristics:
- M. Mitchell worked with DuPont for ~24 years , and was DuPont engineer and Kevlar marketing executive
- Mitchell had been a model citizen with no criminal record
- Became disgruntled and eventually fired for poor performance
Technical skills:
- During his tenure, he copied numerous DuPont computer files containing sensitive and proprietary information to his home computer
- Mitchell entered into lucrative consulting agreement s with Kolon Industries, a DuPont competitor, and supplied them with the data (via email), resulting in millions of dollars in losses to DuPont
Using Mitchell and others to template the insider cybercriminal that targets Intellectual Property (IP) Theft

So, how can law enforcement benefit from these approaches?
By understanding the cybercriminal profile law enforcement can develop strategies to combat criminal behaviour manifested online and inform investigative methods. For future research this means to work further on the development and modelling of cybercriminal profiles and gathering more case and cybercriminal data to link types of cybercriminal profiles to types of cyber attacks (i.e. identify the patterns).
Presentation.
Literature:
Nurse, J.R.C., Buckley, O., Legg, P.A., Goldsmith, M., Creese, S., Wright, G.R. and Whitty, M., 2014. Understanding insider threat: A framework for characterising attacks. In Security and Privacy Workshops (SPW), 2014 IEEE (pp. 214-228). IEEE. https://www.cpni.gov.uk/documents/publications/2014/2014-04-16-understanding_insider_threat_framework.pdf
Nykodym, N., Taylor, R. and Vilela, J. (2005) 'Criminal profiling and insider cyber crime', Computer Law & Security Report, 21 (5), pp. 408-414.
Rogers, M. K. (2006) 'A two-dimensional circumplex approach to the development of a hacker taxonomy', Digital Investigation, 3 (2), pp. 97-102.
www.tradesecretsnoncompetelaw.com/2010/03/articles/trade-secrets-and-confidential-information/former-dupont-employee-sentenced-to-18-months-for-trade-secret-misappropriation
www.richmond.com/news/article_27284dfe-d106-58b4-91f7-1812756b15cb.html
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

presentation on cyber crimes-slides

Related Papers
Faruk Ahmmed
Nadia Khadam
Ramandeep Kaur
IRJET Journal
Amnah Rashid
Prasad Pednekar
Bhartiya Shodh
Crime, in whatever forms it is, directly or indirectly, always affects the society. In today’s world, there is immense increase in the use of Internet in every field of the society and due to this increase in usage of Internet, a number of new crimes have evolved. Such crimes where use of computers coupled with the use of Internet is involved are broadly termed as Cyber Crimes.
Pauline Reich
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Best Practice & Research Clinical Gastroenterology
Boris Pasche
Constantin G. Daniliuc
Bernadith Borja
Anadolu Kliniği Tıp Bilimleri Dergisi
Harun Cansız
Amedeo Manfrin
Ciência & Saúde Coletiva
JOSE SAMPAIO
Robert Murison
Tierra nuestra
Tomas Barriga
Asian Journal of Pharmaceutical and Clinical Research
gouramma patil
Antonino Fiore
Bulletin of the American Physical Society
Oleg Vasilyev
Dianna Roberts
The lancet. Psychiatry
John R Geddes
Logos Universality Mentality Education Novelty: Social Sciences
Olivia Pisica
Industria Textila
Laurențiu Alexandru
Lecture Notes in Computer Science
Syarif Udin
Oxford Guide to Papuan languages
Alexandra Aikhenvald
Claude Duchon
Revista Latinoamericana De Ciencias Sociales Ninez Y Juventud
Cristian Vega soto
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Artificial intelligence is being used in healthcare for everything from answering patient questions to assisting with surgeries and developing new pharmaceuticals.
According to Statista , the artificial intelligence (AI) healthcare market, which is valued at $11 billion in 2021, is projected to be worth $187 billion in 2030. That massive increase means we will likely continue to see considerable changes in how medical providers, hospitals, pharmaceutical and biotechnology companies, and others in the healthcare industry operate.
Better machine learning (ML) algorithms, more access to data, cheaper hardware, and the availability of 5G have contributed to the increasing application of AI in the healthcare industry, accelerating the pace of change. AI and ML technologies can sift through enormous volumes of health data—from health records and clinical studies to genetic information—and analyze it much faster than humans.
Healthcare organizations are using AI to improve the efficiency of all kinds of processes, from back-office tasks to patient care. The following are some examples of how AI might be used to benefit staff and patients:
- Administrative workflow: Healthcare workers spend a lot of time doing paperwork and other administrative tasks. AI and automation can help perform many of those mundane tasks, freeing up employee time for other activities and giving them more face-to-face time with patients. For example, generative AI can help clinicians with note-taking and content summarization that can help keep medical records as thoroughly as possible. AI might also help with accurate coding and sharing of information between departments and billing.
- Virtual nursing assistants: One study found that 64% of patients are comfortable with the use of AI for around-the-clock access to answers that support nurses provide. AI virtual nurse assistants—which are AI-powered chatbots, apps, or other interfaces—can be used to help answer questions about medications, forward reports to doctors or surgeons and help patients schedule a visit with a physician. These sorts of routine tasks can help take work off the hands of clinical staff, who can then spend more time directly on patient care, where human judgment and interaction matter most.
- Dosage error reduction: AI can be used to help identify errors in how a patient self-administers medication. One example comes from a study in Nature Medicine , which found that up to 70% of patients don’t take insulin as prescribed. An AI-powered tool that sits in the patient’s background (much like a wifi router) might be used to flag errors in how the patient administers an insulin pen or inhaler.
- Less invasive surgeries: AI-enabled robots might be used to work around sensitive organs and tissues to help reduce blood loss, infection risk and post-surgery pain.
- Fraud prevention: Fraud in the healthcare industry is enormous, at $380 billion/year, and raises the cost of consumers’ medical premiums and out-of-pocket expenses. Implementing AI can help recognize unusual or suspicious patterns in insurance claims, such as billing for costly services or procedures that are not performed, unbundling (which is billing for the individual steps of a procedure as though they were separate procedures), and performing unnecessary tests to take advantage of insurance payments.
A recent study found that 83% of patients report poor communication as the worst part of their experience, demonstrating a strong need for clearer communication between patients and providers. AI technologies like natural language processing (NLP), predictive analytics, and speech recognition might help healthcare providers have more effective communication with patients. AI might, for instance, deliver more specific information about a patient’s treatment options, allowing the healthcare provider to have more meaningful conversations with the patient for shared decision-making.
According to Harvard’s School of Public Health , although it’s early days for this use, using AI to make diagnoses may reduce treatment costs by up to 50% and improve health outcomes by 40%.
One use case example is out of the University of Hawaii , where a research team found that deploying deep learning AI technology can improve breast cancer risk prediction. More research is needed, but the lead researcher pointed out that an AI algorithm can be trained on a much larger set of images than a radiologist—as many as a million or more radiology images. Also, that algorithm can be replicated at no cost except for hardware.
An MIT group developed an ML algorithm to determine when a human expert is needed. In some instances, such as identifying cardiomegaly in chest X-rays, they found that a hybrid human-AI model produced the best results.
Another published study found that AI recognized skin cancer better than experienced doctors. US, German and French researchers used deep learning on more than 100,000 images to identify skin cancer. Comparing the results of AI to those of 58 international dermatologists, they found AI did better.
As health and fitness monitors become more popular and more people use apps that track and analyze details about their health. They can share these real-time data sets with their doctors to monitor health issues and provide alerts in case of problems.
AI solutions—such as big data applications, machine learning algorithms and deep learning algorithms—might also be used to help humans analyze large data sets to help clinical and other decision-making. AI might also be used to help detect and track infectious diseases, such as COVID-19, tuberculosis, and malaria.
One benefit the use of AI brings to health systems is making gathering and sharing information easier. AI can help providers keep track of patient data more efficiently.
One example is diabetes. According to the Centers for Disease Control and Prevention , 10% of the US population has diabetes. Patients can now use wearable and other monitoring devices that provide feedback about their glucose levels to themselves and their medical team. AI can help providers gather that information, store, and analyze it, and provide data-driven insights from vast numbers of people. Using this information can help healthcare professionals determine how to better treat and manage diseases.
Organizations are also starting to use AI to help improve drug safety. The company SELTA SQUARE, for example, is innovating the pharmacovigilance (PV) process , a legally mandated discipline for detecting and reporting adverse effects from drugs, then assessing, understanding, and preventing those effects. PV demands significant effort and diligence from pharma producers because it’s performed from the clinical trials phase all the way through the drug’s lifetime availability. Selta Square uses a combination of AI and automation to make the PV process faster and more accurate, which helps make medicines safer for people worldwide.
Sometimes, AI might reduce the need to test potential drug compounds physically, which is an enormous cost-savings. High-fidelity molecular simulations can run on computers without incurring the high costs of traditional discovery methods.
AI also has the potential to help humans predict toxicity, bioactivity, and other characteristics of molecules or create previously unknown drug molecules from scratch.
As AI becomes more important in healthcare delivery and more AI medical applications are developed, ethical, and regulatory governance must be established. Issues that raise concern include the possibility of bias, lack of transparency, privacy concerns regarding data used for training AI models, and safety and liability issues.
“AI governance is necessary, especially for clinical applications of the technology,” said Laura Craft, VP Analyst at Gartner . “However, because new AI techniques are largely new territory for most [health delivery organizations], there is a lack of common rules, processes, and guidelines for eager entrepreneurs to follow as they design their pilots.”
The World Health Organization (WHO) spent 18 months deliberating with leading experts in ethics, digital technology, law, and human rights and various Ministries of Health members to produce a report that is called Ethics & Governance of Artificial Intelligence for Health . This report identifies ethical challenges to using AI in healthcare, identifies risks, and outlines six consensus principles to ensure AI works for the public’s benefit:
- Protecting autonomy
- Promoting human safety and well-being
- Ensuring transparency
- Fostering accountability
- Ensuring equity
- Promoting tools that are responsive and sustainable
The WHO report also provides recommendations that ensure governing AI for healthcare both maximizes the technology’s promise and holds healthcare workers accountable and responsive to the communities and people they work with.
AI provides opportunities to help reduce human error, assist medical professionals and staff, and provide patient services 24/7. As AI tools continue to develop, there is potential to use AI even more in reading medical images, X-rays and scans, diagnosing medical problems and creating treatment plans.
AI applications continue to help streamline various tasks, from answering phones to analyzing population health trends (and likely, applications yet to be considered). For instance, future AI tools may automate or augment more of the work of clinicians and staff members. That will free up humans to spend more time on more effective and compassionate face-to-face professional care.
When patients need help, they don’t want to (or can’t) wait on hold. Healthcare facilities’ resources are finite, so help isn’t always available instantaneously or 24/7—and even slight delays can create frustration and feelings of isolation or cause certain conditions to worsen.
IBM® watsonx Assistant™ AI healthcare chatbots can help providers do two things: keep their time focused where it needs to be and empower patients who call in to get quick answers to simple questions.
IBM watsonx Assistant is built on deep learning, machine learning and natural language processing (NLP) models to understand questions, search for the best answers and complete transactions by using conversational AI.
Get email updates about AI advancements, strategies, how-tos, expert perspective and more.
See IBM watsonx Assistant in action and request a demo
Get our newsletters and topic updates that deliver the latest thought leadership and insights on emerging trends.

IMAGES
VIDEO
COMMENTS
Cyber crime and security ppt - Download as a PDF or view online for free. Submit Search. Upload. Cyber crime and security ppt • Download as PPTX, PDF • 842 likes • 616,295 views. Lipsita Behera Follow. Technology. Report. Share. Report. Share. 1 of 22. Download now. Recommended. Cyber security presentation.
4 Ways Cybercriminals Are Leveraging AI. There are four main ways adversaries are using commonly available AI tools like ChatGPT, Dall-E, and Midjourney: automated phishing attacks, impersonation ...
The Internet, computers, cell phones, and other forms of technology have revolutionized every aspect of human life over the last several decades, including how we communicate, bank, shop, obtain the news, and entertain ourselves (Holt and Bossler Citation 2016).These technological advancements have also created myriad opportunities for offenders to commit various forms of crime.
The rise of AI-powered criminals: Identifying threats and opportunities. AI's influence is growing across the security space, bringing with it major implications for cybercriminals and defenders. The recent adoption of AI has raised significant concerns for cybersecurity due to the many ways that criminals can use AI for disruption and profit ...
1. Introduction. The development of information and communication technology (ICT) makes modern life more convenient [1, 2].However, increases in cybercrimes exploiting such technology have emerged as a severe social issue [1, 3].Since the onset of the COVID-19 pandemic, more internet users worldwide have become dependent on the internet in all areas, including education, financial ...
Anti-cyber-attack Technology ——the Thinking and Practice of the Enterprise Dr. LiyunHAN 360 Dipper Research, the Future Security Labs 2020.07.29 @ UN IEG Conference. 02. The Overall Scale of Cyber Underground Economy $ 2.9 million /min Global economic loss per minute
Artificial intelligence in the hands of cybercriminals poses an existential threat to organizations—IT security teams need "defensive AI" to fight back.
The development and increasing use of computing and data storage technologies could be exploited by criminals to gain access to and disseminate non-consensual recordings and illicit data. Technological advances could be used to enhance the anonymity, speed and capacity of criminal activities or to steal personal and sensitive data.
Learning outcomes. Define and describe basic concepts relating to computing. Describe and assess global connectivity and technology usage trends. Define cybercrime and discuss why cybercrime is scientifically studied. Discuss and analyse cybercrime trends. Identify, examine, and analyse the technical, legal, ethical, and operational challenges ...
Abstract. The extensive use of information technology systems and networks has delivered undoubted benefits to both individuals and organizations. Unfortunately, at the same time, it offers new opportunities for abuse and criminal activities. This chapter examines the nature of the problem, looking at the different guises that cybercrime can ...
technology cluster is expected to change or influence cybercrime in the timeframe considered, either from a defender or criminal perspective). • Relevance to Estonia (i.e. the extent to which a technology cluster is expected to bear implications for the Estonian context specifically in the next decade). The technology clusters considered and
cybercrime, the use of a computer as an instrument to further illegal ends, such as committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy. Cybercrime, especially through the Internet, has grown in importance as the computer has become central to commerce, entertainment, and ...
Technology drives modern day society. It has influenced everything from governments and market economies, to global trade, travel, and communications. Digital technologies have further revolutionized our world, and since the advent of the Internet and the World Wide Web, society has become more efficient and advanced (Graham & Dutton, 2014 ...
Although it is universally agreed that cybercrime exists, there is no universal definition of what it means (Holt and Bossler, 2014; Kshetri, 2010; Wall, 2017a).Terms including cybercrime, cyber-crime, computer crime, cloud-crime and computer misuse are often used interchangeably and can refer to any internet- or computer-related criminal activity (Goodman and Brenner, 2002).
The purpose of this paper is to assess whether current international instruments to counter cybercrime may apply in the context of Artificial Intelligence (AI) technologies and to provide a short analysis of the ongoing policy initiatives of international organizations that would have a relevant impact in the law-making process in the field of cybercrime in the near future. This paper ...
Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most cybercrime is committed by cybercriminals or hackers who want to make money. However, occasionally cybercrime aims to damage computers or networks for reasons other than profit. These could be political or personal.
Cybercrime, also called computer crime, is any illegal activity that involves a computer or network-connected device, such as a mobile phone. The Department of Justice divides cybercrime into three categories: crimes in which the computing device is the target, for example, to gain network access; crimes in which the computer is used as a ...
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or networks. These crimes involve the use of technology to commit fraud, identity theft, data breaches, computer viruses, scams, and expanded upon in other malicious acts. Cybercriminals exploit vulnerabilities in computer systems and ...
The FBI's cyber strategy is to impose risk and consequences on cyber adversaries. Our goal is to change the behavior of criminals and nation-states who believe they can compromise U.S. networks ...
Cybercriminals, motivated by profit, may attempt to develop proxy AI systems that mask their involvement, avoid risk, and direct attribution and responsibility. The malicious use of AI could threaten digital security, and machines could become as proficient at hacking and social engineering as human cybercriminals.
This is a summary of a presentation given by Dr Maria Bada, former research fellow at the Global Cyber Security Capacity Centre, and Dr Jason R. C. Nurse, former researcher at Cyber Security Oxford, during the International Crime and Intelligence Analysis Conference in February 2016.The purpose of the presentation was to reflect on the current research and practice in the field of cybercrime ...
Cyber-crime PPT - Download as a PDF or view online for free. Cyber-crime PPT - Download as a PDF or view online for free ... EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER. ... Conclusion The key to protecting yourself is being aware. Not all cybercriminals are "hackers." There is a whole other world that exists in cyberspace ...
In today's world, there is immense increase in the use of Internet in every field of the society and due to this increase in usage of Internet, a number of new crimes have evolved. Such crimes where use of computers coupled with the use of Internet is involved are broadly termed as Cyber Crimes. Download Free PDF. View PDF.
New York CNN —. OpenAI on Monday announced its latest artificial intelligence large language model that it says will be easier and more intuitive to use. The new model, called GPT-4o, is an ...
According to Harvard's School of Public Health, although it's early days for this use, using AI to make diagnoses may reduce treatment costs by up to 50% and improve health outcomes by 40%. One use case example is out of the University of Hawaii, where a research team found that deploying deep learning AI technology can improve breast cancer risk prediction.