

Cyber Risk Bachelor & Masterthesis Topics

We talked with Dr. Daniel Woods of the University of Innsbruck about our list of topics in February of 2021. Besides a short introduction of the topics, in the video we also rate them with regards to their feasibility and relevance for academia and the industry.
Getting into cyber insurance and risk quantification is not a straightforward process yet. Compared to varying degree well-established paths of starting a career in cyber security, established insurance lines of business, actuarial modeling, or insurance law, many current practitioners of the cyber insurance ecosystem are first exposed to the topic when they start their careers in the respective field, usually right out of university/college, or when they transition into it from their previous professional field.
While there are already a few dedicated degree university courses on cyber insurance, the majority of students that might have heard of cyber insurance will at most have had a single semester course on the topic and might have difficulties writing their bachelor or master thesis about cyber, be it for lack of awareness, availability of suitable academic chairs, or a lack of awareness for possible research topics. These difficulties are further magnified by the vastness and interdisciplinary nature of the topic, For example, a bachelor student of cyber security might be interested in cyber insurance, but not able to find access to the financial or law aspects of the topic during the completion of just three months.
While bachelor and master theses allow students to take a deep dive into a given topic and push the envelope (within reasonable constraints), cyber-economics.com wants to lower the barrier of entry for the cyber insurance and risk quantification industries and combat the chronic skill-shortage of quantitative cyber risk professionals by providing students and perhaps even academics with a list of topics that are suitable for a thesis and of ongoing interest for academic research community and industry.
As the quantification of cyber risk in an open field that touches many current and future industries and academic disciplines, we categorize the research topics broadly into qualitative and quantitative topics, with an occasional overlap of methods and thesis topics. In addition to the thesis topics, we provide the reader with literature recommendations that serve as a natural first step to dig deeper into a given topic.
Likely the first topic that was discussed in the academic cyber quantification literature, the insurability of cyber risks has been used by bachelor and master students as a thesis topic since the early 2000s. While the general question, if cyber risks are insurable given the current cyber insurance market with an estimated $5 to 8 Billion in worldwide written premiums today somewhat redundant, there are still a lot of derived questions that can provide a great thesis topic.
Possible Thesis Topics
- Coverage for breaches of third party systems contracted by the insured party, like cloud providers (currently partially insurable).
- Ransomware payments ( the actual ransom, as well as, the cleaning of systems is currently insurable. This also has a strong legal component).
- Next generation IoT devices and autonomous driving cars.
- Coverage for Intellectual property (currently not insurable in cyber directly, but there is intellectual property insurance).
Suggested Academic Reading
In the spirit of , , , and other papers, analyzing the contents of cyber insurance forms and policies provides tremendous insights for academics and the industry alike. The SERFF filling system ( ), which offers extensive up-to-date and historical documents of the US cyber insurance market, is a great source of primary information for this purpose.
- An update to the above-mentioned papers. For example, , while being published in 2019 in an academic journal (there are earlier draft versions available), and analyzed policies from 2009 to 2016. As the cyber insurance market has undergone tremendous growth and associated evolution in the last years, it would be interesting to see how the content of cyber insurance policies changed in the previous years and how carriers reacted, for example, to the increased damages through ransomware during the COVID-19 pandemic.
- In the context of a bachelor or master thesis, the analysis of cyber insurance forms from other countries is likely to the respective local market, e.g., a student at a German University analyzing German cyber insurance policies. Most of the content analysis of cyber insurance policies has been done for the US market, given the size and importance (an estimated 60-70% of global written cyber premiums are underwritten in the US), as well as the availability of policies via the SERFF system not surprising. An example of this is (starting from page 193), which analyzed Dutch cyber insurance policies and compared them to the US market. However, we are not aware of any system even remotely as complete as the SERFF system for other countries, which makes gathering of sufficient number of local cyber insurance policies a requirement.
Of special interest for insurers and brokers is the relationship between the coverage of cyber insurance and other related insurance types. Often the coverage of D&O (Link to cyber-economics.com page on cyber insurance), E&O, media liability, and general P&C (silent cyber, see below for a explicit discussion) , overlaps with the coverage of current cyber insurance policies. The question of how to structure cyber insurance with other insurance types is especially interesting, as there are two primary ways on how cyber insurance is currently sold, either as an addon on an existing P&C policy or as a standalone policy. The primary ways to investigate a question in this nexus are either via qualitative interviews or surveys with brokers, primary insurers, insurance lawyers, and risk owners, or by analyzing the wordings of cyber insurance and the (potential) overlap policies.
- How large/in or which scenarios does cyber insurance overlap with other insurance types? Is this overlap sizeable, i.e. could a combination of policies reduce premiums significantly? Does the overlap depend on the type of cyber insurance policy (addon or standalone)?
- What insurance policy gets priority in case of a cyber incident?
- If addon policies can mitigate the risk over double insurance, does this make them inherently better than standalone cyber insurance policies?
Standard research topics in microeconomics and contract theory, market failures induced by moral hazard and adverse selection can inhibit the efficient transfer of risks or prevent the formation of a functioning market for cyber insurance entirely. Linked to the insurability of cyber risks, the early academic literature on cyber of the 2000s and 2010s, in the absence of the sizeable cyber insurance market of today to empirically analyze, looked at these and other market failures as a consequence of asymmetric information or the inability for the cyber insurer to continuously monitor the cyber security maturity level of an insured entity. To setup a suitable, often agent-based model, agood way to start is to look at classical game theoretical games and adapt them to cyber as needed.
- Under which circumstances can a pooling/separate equilibrium exist when the insurer has only a little information about the cyber maturity level of a potential insured?
- Can an unusual combination of coverage sum and deductible (e.g. very high coverage for a firm with a relatively small turnover) be utilized to draw conclusions about the cyber security level of a firm seeking cyber insurance, i.e. to combat adverse selection in a signaling game?
The underwriting process is the gatekeeper for cyber insurance and shapes the insurance market in many ways. While there is an overlap with analyzing current cyber insurance policies (Topic #2), e.g. by comparing what security controls or other information are required in the underwriting process, a thesis about this topic should likely involve interviews with underwriters or other industry practitioners to get additional insights into the current sentiments of underwriters towards cyber risk. gives a good overview and methodological template to conduct qualitative research into the underwriting process.
- What does the current cyber insurance underwriting process look like? How does it differ for small or medium companies compared to large ones? Is there a significant difference in the undewriting requirements between industries?
- How does the reinsurance underwriting process differ from the primary underwriting process? How does this influence makeup current cyber portfolios?
- Which technical expedients (cyber security stores, external scans, audits) are utilized in the underwriting process? How does it change the decision to insure, coverage level, or premiums?
Cyber insurers have become an important principle for cyber security, law firms, PR firms and all other services or products that are involved in the claims management or underwriting process. Understanding the incentives of the various stakeholders, and perhaps even clearly mapping the current or future value chain in the first place, is important to understand and anticipate the future development of the cyber insurance market.
- Where is currently the market power (primary insurer, reinsurers) in the ecosystem and how is it going to change in the future?
- Does the cyber insurance industry have enough contracted capacity in case of a cyber catastrophe (Ransomware attack like NotPetya or a longer cloud outage) to service all claims? Where are likely bottle necks in the ecosystem?
- How does the cyber insurance ecosystem respond to COVID-19? Will certain services or products be in more demand in the future?
- How do certain parts of the cyber risk ecosystem look under the microscope? For example, what are possible incentive incompatibilities for a breach counsel to handle in case of a cyber incident?
Analogous to topic 6, the cybercrime value chain is the dark side of the cyber insurance value chain and “producer” of the underlying cyber risk. The incentives of cybercriminals are a key consideration when it comes to cyber insurance. From recent developments of cyber crime-as-a-service and the wholesaling of databases and sensitivity of information over the darknet, the cybercrime value chain is perhaps as organized as the cyber insurance one.
- Does cyber insurance increase the payout for cyber criminals and if so, is cyber insurance even a net welfare loss (See also the 8th topic on welfare below)?
- Does the shutdown of a darkmarket (like SilkRoad) correspond with measurable temporary declines in cybercrime activity?
- Does the activity of well-known bot networks, especially pauses in their activities like the one observed with Ryuk in 2019, allow conclusions about the perpetrators?
In economic terms, all insurance types provide utility by smoothing the consumption of risk-averse parties, which in turn are willing to pay an economic premium on top of the expected value of damages. In the case of cyber, there are additional factors that impact the overall welfare.
A key feature of cyber incidents is that the overall costs are most often not solely internalized by the directly affected party, but also cause collateral damages to other firms and entities: Firms using the affected party as a supplier are not able to receive their raw materials and ransomware and phishing attacks can spread more quickly to business partners as well. While the damages of the directly affected party are usually only slightly increased by these collateral damages, e.g. through fines for broken service level agreements, the social planner, usually the government, following standard economic welfare theory, should internalize all damages regardless of who suffers them. Cyber incidents are, therefore, a negative externality and its mitigation via cyber insurance or a better cyber security maturity level is a positive one.
Another factor that impacts the overall welfare effect of cyber are possible substitutions of the cyber security budget of a firm by cyber insurance: If the premiums for a cyber insurance policy are paid from the existing cyber security budget, the overall cyber maturity level of a company is likely to be adversely affected and the underlying risk could even increase.
Positive externalities for cyber include the minimum requirements to get a cyber insurance policy, which prompts poorly secured companies to invest more into cyber security as a prerequisite for cyber insurance, possible cross financing opportunities of cyber security measures with a premium reduction in insurance, the knowledge transfer between the insurer and insured, and the mitigating effects of a prompt incident response orchestrated by the insurer compared to the damages the insured suffers without premeditated external help.
- How is Cyber Insurance impacting the cyber maturity level of a company? Is there a difference in the size of the company? i.e. is the overall welfare gain of smaller companies stronger with a cyber insurance policy in place than for larger companies?
- What are the economic incentives for companies to invest in cyber security when it has an active cyber policy?
- Is the damage mitigation of incident response organized by the cyber insurer significant and on which factors (company size, policy structure, concrete damage scenario) does it depend?
- Can the exclusion of certain risk transfers, e.g. limiting the insurability of ransomware payments, be used to enhance the overall welfare of an economy?
- What are sensible policies for governments to adopt to cost-efficiently increase the cyber maturity level of their respective economy?
Insurers have to adhere to regulatory requirements such as Solvency II in the European Union. Solvency II consists of three pillars that define governance, reporting, and risk capital requirements. The Solvency II standard formula mandates an insurance company to have a maximum annual risk of ruin of 1-to-200 or 0.5%. Especially for cyber risks, the standard formula might be underestimating the fat tails of cyber and, therefore, underestimate the risk of ruin of insurers underwriting cyber, as discussed by .
An interesting possible research angle for this topic is the aforementioned SERFF filing system, which besides accepted rate schedules and documents also shows rejected and modified ones, as well as the correspondence between insurer and regulator. The unprecedented insights into how cyber insurance is regulated on an operative level have so far not been analyzed in the academic literature and might be a great thesis topic.
- Is the Solvency II standard formula adequately calibrated to determine the necessary risk capital for cyber? If not, what are possible stress tests that can be applied to capture the long tails of cyber?
- What are regulators looking for when approving rate schedules? What are common reasons to decline a cyber insurance rate schedule, i.e. an analysis of the correspondence between cyber insurers and regulators?
A great hurdle and growing concern for insurance carriers is silent cyber or non-affirmative cyber. In contrast to all affirmative cyber policies that explicitly provide protection against cyber incidents and their related causes, silent cyber describes the exposure of insurers to cyber damages in traditional property and casualty lines of business. A property example of a silent cyber claim is a fire that was started after a hacker manipulated the temperatures of a blast furnace in a steel mill or the loss of a week production of a food manufacturer because a ransomware attack has disrupted the cold chain by disabling the refrigerators. While these claims are a direct consequence of a cyber incident and would likely be covered by most affirmative cyber policies, they might be also be covered within an existing fire or loss of production insurance. This means that every P&C carrier is likely already incurring cyber-related losses, even though it might not even be offering affirmative cyber coverage.
One of the most important measures to combat silent cyber has been the silent cyber mandate by Lloyd’s of London, which requires all P&C policies underwritten in London to clearly state if they cover cyber damages. Mandatory for property policies since 2020 and 2021 for liability policies, it is perhaps a little bit too early to empirically analyze the effects of the silent cyber mandate. However it will become one of the most tangible sources for the market reaction and sentiments towards silent cyber.
- Did the Lloyds requirement declare the coverage of cyber damages increases the transparency of silent cyber in P&C portfolios?
- How large is the impeding effect of silent cyber on the affirmative cyber insurance market? One could approach this topic by interviews with industry practitioners or by modeling the correlation between silent cyber and affirmative cyber damages and joint impact on the mandatory risk capital (see also topic #9).
- How is silent cyber handled in local markets? , for example, analyzes German P&C Insurance policies after exclusions for silent cyber.
While cyber insurance has seen a sharp rise in awareness and market penetration, there is still a lot of misconceptions about it in the minds of risk owners. Anecdotally speaking, the willingness of risk owners to pay for cyber insurance is low unless they or someone in their immediate peer group is hit by a cyber attack. As these behavioral inefficiencies of cyber insurance also apply to cyber security as a whole, an important research topic is how to phrase and present the facts regarding cyber to the wider public. This of course, has a natural intersection with the commercial interests of brokers and primary insurers that are looking to increase their sales.
The European Union started the CYBECO Grant ( ) in 2018 to study the behavioral aspects of cyber. The programs website is a good starting point in the topic.
- Is the uptake of cyber insurance and/or security increased after big and media salient hacks such as NotPetya or Solarwinds?
- What wordings in marketing and policies can help to raise awareness for cyber insurance and cyber security and increase its uptake?
Of tremendous importance for cyber risk research is the modeling of cyber damages. While looking monolithic on the surface, cyber risk modeling actually encompasses a plethora of different questions and methods. In the context of cyber insurance, the three most important questions are the (1) pricing of cyber insurance policies based on factors such as industry type, security questions, requested coverage of a given applicant, (2) the modeling of cyber damages for a given entity (firms or natural persons), with or without cyber insurance, and (3) the modelling of cyber damages for a given industry sector or cyber insurance portfolio, which are highly dependent on the correlation between cyber damages. While these questions are deeply linked to each other, from an operative view they have varying relevance for different stakeholders of the cyber insurance value chain. For example, primary insurance underwriters are often looking at the pricing of a single policy, while reinsurance underwriters are more concerned with the correlation and performance of the entire portfolio.
The approaches to model cyber also differ. The straightforward to fit a distribution to a damage dataset can and is also be utilized to model cyber, for example, by . However, because of the evolving and hard to predict threat landscape, this method does not yield the same predictive value for more traditional risks. Additionally, in the context of a bachelor or master thesis, the above discussed limited availability of free datasets might be an additional hindrance.
Besides the tried and tested method in the actuarial sciences to fit distributions to damage datasets, which are classified under 1.2.1 in our cyber-economics.com library , there are other approaches that might be interesting for a thesis. Under 1.2.2 Scenario/Catastrophe Analysis , we have gathered studies and papers that look at possible economic and insurable losses arising from bad to worst-case scenarios, like a widespread ransomware attack or outage of a major cloud provider. Under 1.2.3 Network/Node Models , you can find modeling approaches that are based on computer systems based on atomic nodes and connected via edges, which have inherent similarities with the modelling of pandemics.
Quantitative topics often require empirical cyber damage datasets or distributions. These datasets are hard to come by in general, especially if they are free of charge. The following sources for data are freely available and most of them have been used in the academic literature. We add new datasets to the 3.1 Cyber-Damages/-breaches/-Incidents Dataset in our cyber-economics.com library .
A completely different approach to modeling cyber is employed by , which reverse engineers cyber damage loss distributions based on current rate schedules of insurers. From an epistemological standpoint, rather than modeling cyber damages directly, this method quantifies the sentiments of insurers towards cyber risk. While, of course, the rate schedules should be closely connected to the “real” cyber loss distributions, at the very least this approach captures the attitude of entities that put their money where their mouth is. The mentioned paper of woods et all averages out the reverse-engineered cyber distributions of 17 insurers to provide a consensus loss distribution. However, especially within the time constraints of a bachelor and master thesis, it is probably a better idea to apply the method of Woods to a single or few recent rate schedules of a major insurer, to get an up-to-date cyber loss distribution.
- Using a direct loss distribution fit, what are the cyber loss distribution and fair price of a cyber insurance contract for a given dataset?
- Using a direct loss distribution fit, what is the correlation between damages for a given dataset?
- Using a node model, how sensitive are the total damages of a hypothetical ransomware attack based on the “contagiousness” of the attack or the difficulty of removing it?
- Using a reverse-engineered loss distribution based on a current rate schedule of a major insurer, what is the sentiment of the respective insurer towards factors in the pricing of cyber insurance. For example, how are policies for small firms priced compared to large ones? How does the security standard of a company change the price? Does this allow a meaningful cross financing of security spending with reduced premiums (see also Topic 8)?
- Using a reverse-engineered loss distribution based on a current rate schedule of a major insurer, what is the sentiment of the respective insurer towards factors in the pricing of cyber insurance. For example, how are policies for small firms priced compared to large ones? How does the security standard of a company change the price? Does this allow a meaningful cross-financing of security spending with reduced premiums (see also Topic 8)?
Pricing higher cyber risk transfers via reinsurance within the insurance sector or with cyber bonds via the capital market is an important topic for the insurance industry, possible capital market investors, and academics. While for the pricing based on single risks the correlation between cyber damages can be neglected, it becomes the most consideration for higher risk transfers. Getting a suitable dataset to empirically model the correlation of cyber damages becomes even more difficult than getting one for cyber damages. Often the parameters guiding the correlation between damages are, therefore, exogenously imposed or derived from other parameters or assumptions within the model. A robustness analysis, i.e, changing the correlation parameters to simulate a low, medium, or high correlation, is then used to analyze the results with respect to their sensibility towards the model parameters.
- What is the distribution for the reinsurer or fair price for a reinsurance contract (be it proportional or excess-of-loss) for a given cyber damage distribution? How sensitive are prices and reinsurers payout distributions towards the underlying model assumptions?
- Are cyber bonds able to pay an on-par premium with natural catastrophe bonds (around 5% p.a. since their inception) for a given damage distribution?

Daniel Kasper
Daniel Kasper is the principal of Cyber Economics.

cyber-economics.com provides you with the newest developments and news about cyber risk from academia and the business sector.
- Privacy Policy
- Cookie Policy

- USF Research
- USF Libraries
Digital Commons @ USF > College of Arts and Sciences > Mathematics and Statistics > Theses and Dissertations
Mathematics and Statistics Theses and Dissertations
Theses/dissertations from 2023 2023.
Classification of Finite Topological Quandles and Shelves via Posets , Hitakshi Lahrani
Applied Analysis for Learning Architectures , Himanshu Singh
Rational Functions of Degree Five That Permute the Projective Line Over a Finite Field , Christopher Sze
Theses/Dissertations from 2022 2022
New Developments in Statistical Optimal Designs for Physical and Computer Experiments , Damola M. Akinlana
Advances and Applications of Optimal Polynomial Approximants , Raymond Centner
Data-Driven Analytical Predictive Modeling for Pancreatic Cancer, Financial & Social Systems , Aditya Chakraborty
On Simultaneous Similarity of d-tuples of Commuting Square Matrices , Corey Connelly
Symbolic Computation of Lump Solutions to a Combined (2+1)-dimensional Nonlinear Evolution Equation , Jingwei He
Boundary behavior of analytic functions and Approximation Theory , Spyros Pasias
Stability Analysis of Delay-Driven Coupled Cantilevers Using the Lambert W-Function , Daniel Siebel-Cortopassi
A Functional Optimization Approach to Stochastic Process Sampling , Ryan Matthew Thurman
Theses/Dissertations from 2021 2021
Riemann-Hilbert Problems for Nonlocal Reverse-Time Nonlinear Second-order and Fourth-order AKNS Systems of Multiple Components and Exact Soliton Solutions , Alle Adjiri
Zeros of Harmonic Polynomials and Related Applications , Azizah Alrajhi
Combination of Time Series Analysis and Sentiment Analysis for Stock Market Forecasting , Hsiao-Chuan Chou
Uncertainty Quantification in Deep and Statistical Learning with applications in Bio-Medical Image Analysis , K. Ruwani M. Fernando
Data-Driven Analytical Modeling of Multiple Myeloma Cancer, U.S. Crop Production and Monitoring Process , Lohuwa Mamudu
Long-time Asymptotics for mKdV Type Reduced Equations of the AKNS Hierarchy in Weighted L 2 Sobolev Spaces , Fudong Wang
Online and Adjusted Human Activities Recognition with Statistical Learning , Yanjia Zhang
Theses/Dissertations from 2020 2020
Bayesian Reliability Analysis of The Power Law Process and Statistical Modeling of Computer and Network Vulnerabilities with Cybersecurity Application , Freeh N. Alenezi
Discrete Models and Algorithms for Analyzing DNA Rearrangements , Jasper Braun
Bayesian Reliability Analysis for Optical Media Using Accelerated Degradation Test Data , Kun Bu
On the p(x)-Laplace equation in Carnot groups , Robert D. Freeman
Clustering methods for gene expression data of Oxytricha trifallax , Kyle Houfek
Gradient Boosting for Survival Analysis with Applications in Oncology , Nam Phuong Nguyen
Global and Stochastic Dynamics of Diffusive Hindmarsh-Rose Equations in Neurodynamics , Chi Phan
Restricted Isometric Projections for Differentiable Manifolds and Applications , Vasile Pop
On Some Problems on Polynomial Interpolation in Several Variables , Brian Jon Tuesink
Numerical Study of Gap Distributions in Determinantal Point Process on Low Dimensional Spheres: L -Ensemble of O ( n ) Model Type for n = 2 and n = 3 , Xiankui Yang
Non-Associative Algebraic Structures in Knot Theory , Emanuele Zappala
Theses/Dissertations from 2019 2019
Field Quantization for Radiative Decay of Plasmons in Finite and Infinite Geometries , Maryam Bagherian
Probabilistic Modeling of Democracy, Corruption, Hemophilia A and Prediabetes Data , A. K. M. Raquibul Bashar
Generalized Derivations of Ternary Lie Algebras and n-BiHom-Lie Algebras , Amine Ben Abdeljelil
Fractional Random Weighted Bootstrapping for Classification on Imbalanced Data with Ensemble Decision Tree Methods , Sean Charles Carter
Hierarchical Self-Assembly and Substitution Rules , Daniel Alejandro Cruz
Statistical Learning of Biomedical Non-Stationary Signals and Quality of Life Modeling , Mahdi Goudarzi
Probabilistic and Statistical Prediction Models for Alzheimer’s Disease and Statistical Analysis of Global Warming , Maryam Ibrahim Habadi
Essays on Time Series and Machine Learning Techniques for Risk Management , Michael Kotarinos
The Systems of Post and Post Algebras: A Demonstration of an Obvious Fact , Daviel Leyva
Reconstruction of Radar Images by Using Spherical Mean and Regular Radon Transforms , Ozan Pirbudak
Analyses of Unorthodox Overlapping Gene Segments in Oxytricha Trifallax , Shannon Stich
An Optimal Medium-Strength Regularity Algorithm for 3-uniform Hypergraphs , John Theado
Power Graphs of Quasigroups , DayVon L. Walker
Theses/Dissertations from 2018 2018
Groups Generated by Automata Arising from Transformations of the Boundaries of Rooted Trees , Elsayed Ahmed
Non-equilibrium Phase Transitions in Interacting Diffusions , Wael Al-Sawai
A Hybrid Dynamic Modeling of Time-to-event Processes and Applications , Emmanuel A. Appiah
Lump Solutions and Riemann-Hilbert Approach to Soliton Equations , Sumayah A. Batwa
Developing a Model to Predict Prevalence of Compulsive Behavior in Individuals with OCD , Lindsay D. Fields
Generalizations of Quandles and their cohomologies , Matthew J. Green
Hamiltonian structures and Riemann-Hilbert problems of integrable systems , Xiang Gu
Optimal Latin Hypercube Designs for Computer Experiments Based on Multiple Objectives , Ruizhe Hou
Human Activity Recognition Based on Transfer Learning , Jinyong Pang
Signal Detection of Adverse Drug Reaction using the Adverse Event Reporting System: Literature Review and Novel Methods , Minh H. Pham
Statistical Analysis and Modeling of Cyber Security and Health Sciences , Nawa Raj Pokhrel
Machine Learning Methods for Network Intrusion Detection and Intrusion Prevention Systems , Zheni Svetoslavova Stefanova
Orthogonal Polynomials With Respect to the Measure Supported Over the Whole Complex Plane , Meng Yang
Theses/Dissertations from 2017 2017
Modeling in Finance and Insurance With Levy-It'o Driven Dynamic Processes under Semi Markov-type Switching Regimes and Time Domains , Patrick Armand Assonken Tonfack
Prevalence of Typical Images in High School Geometry Textbooks , Megan N. Cannon
On Extending Hansel's Theorem to Hypergraphs , Gregory Sutton Churchill
Contributions to Quandle Theory: A Study of f-Quandles, Extensions, and Cohomology , Indu Rasika U. Churchill
Linear Extremal Problems in the Hardy Space H p for 0 p , Robert Christopher Connelly
Statistical Analysis and Modeling of Ovarian and Breast Cancer , Muditha V. Devamitta Perera
Statistical Analysis and Modeling of Stomach Cancer Data , Chao Gao
Structural Analysis of Poloidal and Toroidal Plasmons and Fields of Multilayer Nanorings , Kumar Vijay Garapati
Dynamics of Multicultural Social Networks , Kristina B. Hilton
Cybersecurity: Stochastic Analysis and Modelling of Vulnerabilities to Determine the Network Security and Attackers Behavior , Pubudu Kalpani Kaluarachchi
Generalized D-Kaup-Newell integrable systems and their integrable couplings and Darboux transformations , Morgan Ashley McAnally
Patterns in Words Related to DNA Rearrangements , Lukas Nabergall
Time Series Online Empirical Bayesian Kernel Density Segmentation: Applications in Real Time Activity Recognition Using Smartphone Accelerometer , Shuang Na
Schreier Graphs of Thompson's Group T , Allen Pennington
Cybersecurity: Probabilistic Behavior of Vulnerability and Life Cycle , Sasith Maduranga Rajasooriya
Bayesian Artificial Neural Networks in Health and Cybersecurity , Hansapani Sarasepa Rodrigo
Real-time Classification of Biomedical Signals, Parkinson’s Analytical Model , Abolfazl Saghafi
Lump, complexiton and algebro-geometric solutions to soliton equations , Yuan Zhou
Theses/Dissertations from 2016 2016
A Statistical Analysis of Hurricanes in the Atlantic Basin and Sinkholes in Florida , Joy Marie D'andrea
Statistical Analysis of a Risk Factor in Finance and Environmental Models for Belize , Sherlene Enriquez-Savery
Putnam's Inequality and Analytic Content in the Bergman Space , Matthew Fleeman
On the Number of Colors in Quandle Knot Colorings , Jeremy William Kerr
Statistical Modeling of Carbon Dioxide and Cluster Analysis of Time Dependent Information: Lag Target Time Series Clustering, Multi-Factor Time Series Clustering, and Multi-Level Time Series Clustering , Doo Young Kim
Some Results Concerning Permutation Polynomials over Finite Fields , Stephen Lappano
Hamiltonian Formulations and Symmetry Constraints of Soliton Hierarchies of (1+1)-Dimensional Nonlinear Evolution Equations , Solomon Manukure
Modeling and Survival Analysis of Breast Cancer: A Statistical, Artificial Neural Network, and Decision Tree Approach , Venkateswara Rao Mudunuru
Generalized Phase Retrieval: Isometries in Vector Spaces , Josiah Park
Leonard Systems and their Friends , Jonathan Spiewak
Resonant Solutions to (3+1)-dimensional Bilinear Differential Equations , Yue Sun
Statistical Analysis and Modeling Health Data: A Longitudinal Study , Bhikhari Prasad Tharu
Global Attractors and Random Attractors of Reaction-Diffusion Systems , Junyi Tu
Time Dependent Kernel Density Estimation: A New Parameter Estimation Algorithm, Applications in Time Series Classification and Clustering , Xing Wang
On Spectral Properties of Single Layer Potentials , Seyed Zoalroshd
Theses/Dissertations from 2015 2015
Analysis of Rheumatoid Arthritis Data using Logistic Regression and Penalized Approach , Wei Chen
Active Tile Self-assembly and Simulations of Computational Systems , Daria Karpenko
Nearest Neighbor Foreign Exchange Rate Forecasting with Mahalanobis Distance , Vindya Kumari Pathirana
Statistical Learning with Artificial Neural Network Applied to Health and Environmental Data , Taysseer Sharaf
Radial Versus Othogonal and Minimal Projections onto Hyperplanes in l_4^3 , Richard Alan Warner
Ensemble Learning Method on Machine Maintenance Data , Xiaochuang Zhao
Theses/Dissertations from 2014 2014
Properties of Graphs Used to Model DNA Recombination , Ryan Arredondo
Recursive Methods in Number Theory, Combinatorial Graph Theory, and Probability , Jonathan Burns
On the Classification of Groups Generated by Automata with 4 States over a 2-Letter Alphabet , Louis Caponi
Statistical Analysis, Modeling, and Algorithms for Pharmaceutical and Cancer Systems , Bong-Jin Choi
Topological Data Analysis of Properties of Four-Regular Rigid Vertex Graphs , Grant Mcneil Conine
Trend Analysis and Modeling of Health and Environmental Data: Joinpoint and Functional Approach , Ram C. Kafle
Advanced Search
- Email Notifications and RSS
- All Collections
- USF Faculty Publications
- Open Access Journals
- Conferences and Events
- Theses and Dissertations
- Textbooks Collection
Useful Links
- Mathematics and Statistics Department
- Rights Information
- SelectedWorks
- Submit Research
Home | About | Help | My Account | Accessibility Statement | Language and Diversity Statements
Privacy Copyright
10 risks in topic finding for the bachelor's and master's thesis
The topic of the bachelor's or master's thesis can make it easy or difficult to write the thesis. A good choice is a topic with as few risks as possible. The following tips will help you avoid risks when choosing a topic right from the start.
1. Bachelor's or master's thesis topics with few suitable sources are risky.
Of course, you need material to write a scientific text. So check at the beginning how many scientific sources you can find for the most important terms relevant to your topic. Use our search tips for Google.
2. If a topic requires very specific methods, it is risky.
Topics that can only be dealt with using very specific methods are not recommended. Such special methods are, for example, certain statistical methods for data evaluation such as logistic regression or conjoint analysis. Certainly you will be greatly rewarded when you work with such methods: the insight is often unique and the supervisor is beside himself with joy. But to do so, you must first master these methods. Under no circumstances should you start such a job without any prior knowledge and rely entirely on experts. First, they are expensive and difficult to find and second, you will have trouble explaining the approach to your supervisor.
3. If the topic requires very special or rare data, be careful!
Some questions can only be answered with very specific data. Your data must be retrievable! If that doesn't work, your subject is lapsed. Working on corruption is difficult because it is difficult to find people to talk about it. This applies both to empirical theses and to practical theses within a company. So always think about that before you decide on the topic of your thesis. If you can't find the data you need or are not allowed to share it publicly, you should think about another topic.
4. You should not focus on a taboo topic in your bachelor's or master's thesis.
While they may be very exciting topics, they are very difficult to work on. This is because either there is hardly any data available or data collection is practically impossible. This includes topics such as bullying, corruption, tax evasion, any use of violence, xenophobia and so on. I'm sure you can comprehend why nobody wants to give any information on these topics, but such topics can of course be dealt with if you work as a prison authority. If not, then you better think of another topic for your thesis.
5. A topic without elaborated models guarantees a struggle
It’s like building a house: building on a greenfield is not a good idea. There are no connections at all, no water, sewage, electricity or telephone network just to name a few - which is only noticeable when it is actually missing...
If there are hardly any definitions for the relevant terms of your topic, the topic is not recommended. Additionally, sometimes there are many discussions on a topic but no in-depth analyses.
6. If the personal contribution needs a lot of preliminary work, then choose a different subject.
Of course, you have to include your personal contribution otherwise your Bachelor's or Master's Thesis will simply be a compilation of other sources. Nevertheless, if you have to do a large amount of preparatory work, you’ll lose a lot of time. So avoid topics where you have to sift through the literature for weeks, develop your own model, sort through many definitions or discuss conflicting insight and opinions.
7. If the topic has already been exhausted in other works, choose another one.
At the same time, you should also avoid the exact opposite: writing about something that has already been covered dozens of times. Try suggesting a topic related to employee motivation, integration problems, reading difficulties or discrimination in the workplace to gain your supervisor’s interest. These are all topics that have already been dealt with many times. Only an empirical question can contribute something new in these areas.

8. The subject requires many sources other languages.
If you are writing your Bachelor's or Master's Thesis in English, you should consider whether the topic requires many foreign language sources. Even if your German, for example, is great, be aware that technical literature in German requires a lot more effort and concentration than everyday German.
9. You should not need sensitive data from a company if possible.
This can also be a problem. Receive written permission in advance stating that you may use and also partially publish the sensitive data. Some companies do not allow outsiders to do so. In any case, a blocking clause is necessary at the beginning of the work. Clarify this BEFORE you formulate the final topic for the thesis. Otherwise, you will not get the data...
10. Is your topic part of a complex research project for your supervisor?
Be extremely careful in this case!
With such a topic you are limited and confronted with very specific questions. You may also be dependent on the supervisors staff to get information and data. This must be cleared up beforehand. Many projects simply take more time.Think carefully whether you can implement such a topic.
- Be wise, check first!
- Check which of the mentioned risks could be relevant to you!
- Control these risks!
- Avoid them if possible!
Good luck writing your text!
Silvio and the Aristolo Team
PS: Check out the Thesis-ABC and the Thesis Guide for writing a bachelor or master thesis in 31 days.

CyberSecurity Risk Assessment Score Prediction
Dev Limbachia, Yuvraj Patel, Murtuza Mohammed, Anjali Patel, Harsh Shah
Artificial Intelligence
The cybersecurity risk assessment prediction initiative, backed by Technology Helps, has introduced a cutting-edge AI-powered web application. This solution seamlessly integrates staff training evaluations, phishing risk analyses, vulnerability assessments, and security controls and audit scores to generate weighted scores and automate risk categorizations.
Employing a Random Forest Classifier, the model achieves an impressive 95% accuracy rate and a weighted average F1 score of 0.91. Leveraging OutSystems, we've developed a user-friendly web application, which is further enhanced through integration with AWS for model training and development via Lambda and S3. This setup ensures dynamic risk score categorization based on industry standards, empowering enterprises with real-time insights for proactive cybersecurity risk management.
Capstone Project - The Decoders (CyberSecurity Risk Assessment Score Prediction)
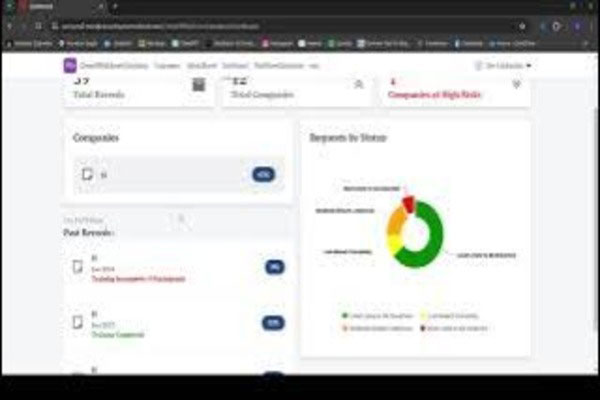
The cybersecurity risk assessment prediction initiative, backed by Technology Helps, has introduced a cutting-edge AI-powered web application. This solution seamlessly integrates staff training evaluations, phishing risk analyses, vulnerability assessments, and security controls and audit scores to generate weighted scores and automate risk categorizations. Employing a Random Forest Classifier, the model achieves an impressive 95% accuracy rate and a weighted average F1 score of 0.91. Leveraging OutSystems, we've developed a user-friendly web application, which is further enhanced through integration with AWS for model training and development via Lambda and S3. This setup ensures dynamic risk score categorization based on industry standards, empowering enterprises with real-time insights for proactive cybersecurity risk management.
Project Poster

EXPLORE OTHER CAPSTONE PROJECTS

Ilore AI powered property search system
Yatharth Thakur, Bavalpreet Singh, Yashi Sikligar, Vishnu Vinay, Anandsagar Shaji

Kaivalya Pandit, Deepak Chauhan, Mohammed Furqan Jeelani, Anuj Thapa
Artificial Intelligence , Big Data/Business Intelligence , Web App

Bespoke Jewelry Design With AI
Neha Singh Ghosh, Shalini Ivaturi, Sharmi Das, Siddhartha choudhary

Generative AI Innovation
Arshiya, Kennedy Dende, Saima Bareen Mirza, Jenith Bhaskaran Nadar
Artificial Intelligence , Deep Learning , Machine Learning , MySQL , Python

Semantic Segmentation And Object Detection For Sidewalk Analysis And Safety Enhancement
Prachi Khatri, Parul Batish, Mohammed Bilal Khan, Maharshi Mehta

Sidewalk Detection and Segmentation
Abdeali Harianawala, Bhavesh Waghela, Keyur Finaviya, Siri Karnala

AgriMonitoring
Nitesh Kumar, Alex Fontaine-Bolanos, Mi-Nam Alcantra, Taksim Islam

StrategistAl
Sagar Vaiyata, Hiral Shah, Ayushi Patel, Manankumar Patel

Text to Image synthesis
Adhish bhatia, Jasmeet kaur, Tarundeep singh, Sanjai kukreti
Artificial Intelligence , Machine Learning
- English Norsk
Master's Thesis in Risk Analysis (RISMAS)
The master thesis is an independent project in which the student shall apply the knowledge acquired during the studies to solve a given assignment. It is through this assignment that that the student shows his or her abilities and qualities as a master's degree holder. The assignment is normally carried out during the last semester of the studies. At this stage, the student will have acquired the knowledge and skills needed for accomplishing a relevant assignment related to the studies.
Course description for study year 2023-2024. Please note that changes may occur.
Course code
Credits (ects), semester tution start, number of semesters, exam semester, language of instruction.
English, Norwegian
View course schedule
Learning outcome
A candidate with a completed and passed master's thesis shall have the following learning outcomes:
- have thorough knowledge of relevant concepts, principles, frameworks, methods and/or models within the part of the field of study covered by the problem addressed
- have an overview of relevant scientific literature, other sources of information, and ethical standards in the field of study
- have an understanding of what constitutes a contribution to the part of the field of study that the problem addressed relates to
- demonstrate in-depth knowledge into and understanding of a more limited part of the field of study covered by the problem addressed
- carry out a literature search and write a scientific report
- master the terminology of the field of study
- can use relevant methods and work forms
- can describe the problem statement in a clear way
- can be critical of different sources of information
- can reflect on and critically evaluate own work
General competence
- can communicate in writing on a comprehensive independent work
- understand and follow the ethical standards for scientific work
Required prerequisite knowledge
Note that you primarily have only one attempt for writing the thesis, see section 3-10 number 4 in Regulations relating to studies and examinations at The University of Stavanger A bachelor´s or master´s thesis that is not submitted by the deadline is considered not passed.For more information, please see Thesis writing at Faculty of Science and Technology Deadline for withdrawal is April 1.
Course teacher(s)
Course teacher:, course coordinator:, head of department:, method of work, overlapping courses.
Master of Science in Risk Management
Master of Science in Risk Analysis and Governance
Master of Science in Risk Analysis
Course assessment
KBE: Regional Banks At Risk For Continued Underperformance
- SPDR S&P Bank ETF is a hold due to its heavy concentration in regional banks and the risk factors associated with them.
- KBE has underperformed broader financial sector funds such as VFH and XLF that have also seen lower volatility and lower expense ratios.
- Distinct risk factors remain for regional banks, including the risk of savings account outflows, reduced liquidity, reduced diversification, and interest rate sensitivity.

ilbusca/E+ via Getty Images
Investment Thesis
SPDR S&P Bank ETF ( NYSEARCA: KBE ) is a hold due to several concerning factors regarding the fund, including its heavy concentration on regional banks. While most regional banks have recovered from the early 2023 slew of failures, they still present multiple risk factors. By comparison, broader-based, diversified financial sector funds have seen better performance with lower volatility. This trend will likely continue given uncertainty regarding interest rate reductions, inflation control, and the elusive economic "soft landing."
Fund Overview and Compared ETFs
KBE is a low-cost passively managed ETF that seeks to track the S&P Banks Select Industry Index . The fund therefore utilizes a modified equal-weighted index with the goal of providing investors with non-concentrated exposure across large, mid, and small-cap companies. With its inception in 2005, the fund has 92 holdings and $1.51B in AUM. By sub-sector, the fund is heaviest on regional banks (66.28%), followed by diversified banks (14.38%) and commercial and residential mortgage finance (8.42%).
For comparison purposes, a similar fund examined is the Invesco KBW Bank ETF ( KBWB ) which is also focused on bank stocks but does not utilize the modified equal-weight index. It, therefore, is heavier on a large cap (56.49% weight) and lighter on a small cap (5.93% weight). To compare with the financial sector more broadly, Vanguard Financials Index Fund ETF Shares ( VFH ) and Financial Select Sector SPDR Fund ETF ( XLF ) were also examined. These broader-based funds are more diversified, including payment service companies, financial exchanges, insurance, and asset management companies.
Funds Compared: Performance, Expense Ratio, and Dividend Yield
KBE has seen a mediocre 10-year average annual return of 5.67% with a 10-year total price return of 43.8%. By comparison, KBWB performed slightly better, with a 10-year average annual return of 6.51%. Both funds have significantly underperformed broader financial sector funds, VFH and XLF, which have seen 10.44% and 10.63% average annual returns respectively. Looking forward, there are multiple reasons to believe that bank ETFs will continue to lag the broader financial sector, as I will discuss later.
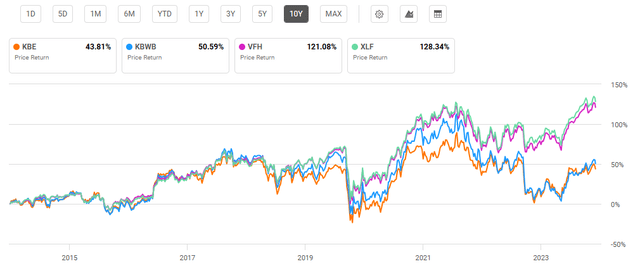
10-Year Total Price Return for KBE and Peer Financial Sector ETFs (Seeking Alpha)
In addition to stronger long-term performance, broader financial sector funds VFH and XLF also have lower expense ratios than KBE. At 0.35%, KBE ties Invesco's bank ETF for fees. One positive quality for KBE is its dividend yield at a solid 2.82% which has been growing with an 8.78% 5-year CAGR.
Expense Ratio, AUM, and Dividend Yield Comparison
Source: Seeking Alpha, 23 May 24
KBE Holdings and Key Outlook Factors
Due to its modified equal-weight strategy, KBE holds the least weight on its top holdings at just 15.98%. By comparison, all other funds have at least 40% weight on their top 10 holdings. Additionally, while KBE contains some large-cap financial stocks such as Bank of America Corporation ( BAC ) and Citigroup Inc. ( C ), it is heaviest on smaller holdings such as Jackson Financial Inc. ( JXN ), Corebridge Financial, Inc. ( CRBG ), and Equitable Holdings, Inc. ( EQH ).
Top 10 Holdings for KBE and Compared Bank and Financials Funds
Source: Multiple, compiled by author on 23 May 24
Looking forward, there are multiple headwinds for regional banks. This is problematic for KBE as it contains over 60% weight of regional banks. By comparison, VFH and XLF contain only 6.5% and 5.0% weight on regional banks respectively due to their broader indexes. These factors, discussed below, will likely continue to drag KBE back in performance compared to broader-based VFH and XLF.
Regional Bank Difficulties
In March 2023, Silicon Valley Bank, or SVB, collapsed, resulting in a significant decline in share prices for regional banks. Subsequently, Signature Bank and First Republic Bank also failed . SVB's failure was predominantly due to the bank keeping large amounts of cash in bonds that lost value as the Federal Reserve raised interest rates to combat inflation. Additionally, the bank invested heavily in tech startups, which saw steep losses during the COVID pandemic. Subsequently, while VFH saw an 11.2% decline in March 2023, KBE saw a 23.6% decline. While regional banks have generally recovered, they have lagged the broader financial sector since 2023.
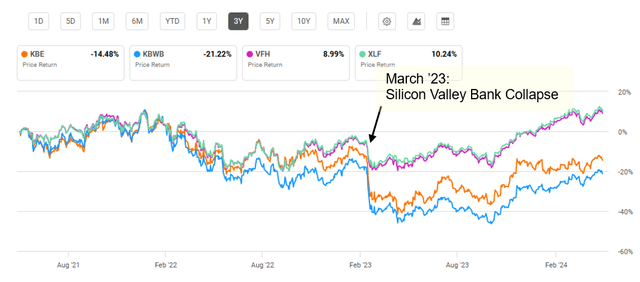
Timing of SVB Collapse With 3-Year ETF Performance (Seeking Alpha)
While there has been no widespread regional bank failure contagion, regional bank vulnerabilities have remained. Higher interest rates help bank profitability, as banks profit from the difference in the rates they offer to customers compared to the return rate of their investments. As interest rates will likely be lower in coming years, the profitability from these higher interest rates may be squeezed. In contrast to regional banks, large and more diversified financial companies are less sensitive to interest rate fluctuations, as indicated by the share prices for financial funds since early 2023.
Regional Problems Will Likely Persist
Looking ahead, there are two reasons why issues in the financial sector might persist. The first reason is that mortgage rates will remain elevated compared to pre-2022 levels. This has resulted in a "lock-in" effect on homeowners. A survey by realtor.com offered that 82% of home buyers surveyed stated they felt "locked in" by their existing lower mortgage rate. Banks, including KBE's holdings, profit from new home purchase transactions, which are likely to be muted given this elevated mortgage interest rate. While the average 30-year mortgage rate is just below 7.0% , it is not expected to fall anytime soon to levels seen a few years ago. Axos Financial, Inc. ( AX ), for example, one of KBE's top holdings, offers residential mortgages and will be directly impacted by this mortgage rate environment.
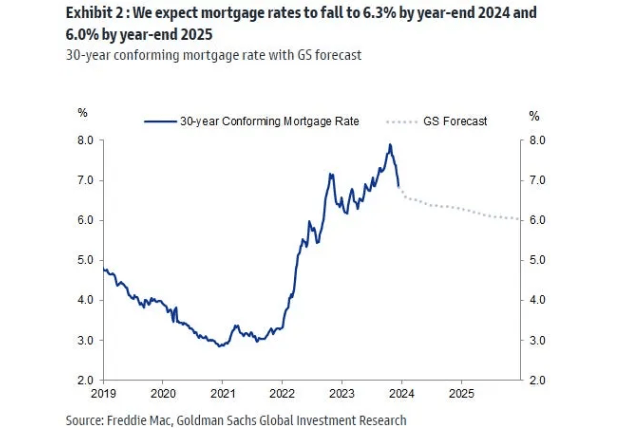
Forecast Mortgage Interest Rates (Freddie Mac, GS Global Investment Research)
The second factor impacting smaller banks is the number of deposits they receive in interest-bearing accounts. In early 2020, money market fund inflows went up over 10% month-on-month. Current yields greater than 5% have kept deposits in high-yield savings accounts, including those offered by regional banks. However, as interest rates inevitably come down, bank outflows will likely occur as bonds, REITs, and dividend-paying stocks become more attractive comparatively. Another top holding for KBE, Bank OZK ( OZK ), for example, offers savings and money market accounts to individuals and businesses which will be directly impacted by a reduced federal funds rate.
Comparative Strength of Broader Financial Sector
In contrast to bank-heavy KBE, VFH holds only 6% weight on regional banks. Importantly, larger, more diversified financial holdings have demonstrated greater strength to weather the storms of interest rate fluctuations and recessions. Two holdings that demonstrate this resiliency are Berkshire Hathaway Inc. ( BRK.A ), ( BRK.B ) and JPMorgan Chase & Co. ( JPM ).
While XLF holds 13% weight, Berkshire Hathaway, KBE does not have BRK.B as a holding. Few companies are as broadly diversified as Warren Buffett's multinational conglomerate. Berkshire Hathaway includes subsidiaries including Duracell, Dairy Queen, and Fruit of the Loom. From 1965 to 2022, Berkshire had a 19.8% compound annual growth rate . Therefore, the inclusion of BRK.B presents a distinct strength that is lacking from KBE.
The second example of a strong holding is JPMorgan. KBE holds JPM at only 1.44% weight, while VFH and XLF have over 8% weight each. With consumer banking, investment banking, commercial banking, and asset management business segments, JPMorgan is broadly diversified in the financial sector, presenting a distinctive strength. Additionally, the company has seen 16.2% YoY revenue growth and is highly profitable with a 33.6% net income margin. Therefore, XLF and VFH are also more strongly postured, with their greater weight on JPM.
Current Valuation
As the stock market rally has broadened recently beyond information technology holdings , equal-weighted indexes have performed well. This benefited KBE, which has seen a one-year performance of over 30%. By comparison, VFH and XLF, which saw better long-term performance, have fallen behind over the past year.
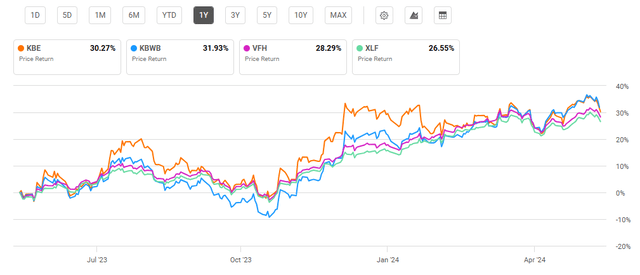
One Year Performance: KBE and Compared Financial Sector Funds (Seeking Alpha)
Despite recent outperformance, KBE and peer KBWB have more attractive valuations than VFH and XLF. However, I do not see this as a buy signal for KBE. KBE's heavy concentration of regional banks presents risk factors looking forward that do not outweigh a better valuation.
Valuation Metrics for KBE and Peer Banking and Financials ETFs
Source: Compiled by Author from Multiple Sources, 23 May 24
Risks to Investors
As discussed so far in this article, regional banks present multiple risks compared to larger, diversified financial holdings. While KBE has a modified equal-weighted approach, the fund still holds 66% of its weight on regional banks. As seen with Silicon Valley and Signature Banks, regional and smaller banks are more sensitive to interest rate fluctuations. While increased liquidity requirements are likely to aid in preventing future bank failures, risk factors that drive volatility remain. For an ETF, this volatility can be measured by standard deviation. KBE has a 5-year standard deviation of 31.14. By comparison, VFH has a 5-year standard deviation of 23.5, indicating that the more diversified fund experiences notably lower volatility.
Concluding Summary
KBE warrants a hold rating, at best, due to its relatively heavy weight on regional banks. While there have not been widespread regional bank failures beyond the early 2023 collapses, the fundamental risk factors remain including interest rate sensitivity, the potential for account outflows, and lack of diversification. In contrast, broader-based funds such as VFH and XLF have seen stronger performance, lower volatility, and more affordable expense ratios. Despite a more attractive valuation for KBE, I anticipate broader financial funds such as VFH and XLF will continue to outperform looking forward.
This article was written by
Analyst’s Disclosure: I/we have a beneficial long position in the shares of BRK.B either through stock ownership, options, or other derivatives. I wrote this article myself, and it expresses my own opinions. I am not receiving compensation for it (other than from Seeking Alpha). I have no business relationship with any company whose stock is mentioned in this article. This article is exclusive to Seeking Alpha. No duplication or reproduction of this article is allowed without consent of Seeking Alpha and the author. This article should not be misconstrued as individual financial advice. Always conduct your own due diligence prior to investing.
Seeking Alpha's Disclosure: Past performance is no guarantee of future results. No recommendation or advice is being given as to whether any investment is suitable for a particular investor. Any views or opinions expressed above may not reflect those of Seeking Alpha as a whole. Seeking Alpha is not a licensed securities dealer, broker or US investment adviser or investment bank. Our analysts are third party authors that include both professional investors and individual investors who may not be licensed or certified by any institute or regulatory body.
Recommended For You
About kbe etf, more on kbe, related stocks, trending analysis, trending news.

IMAGES
VIDEO
COMMENTS
This thesis was carried out to fulfill the master's degree in Risk Management at the Faculty of Science and Technology, University of Stavanger. ... industry, and involved parties. A decision needs support from risk-informed analysis for providing the overall picture and thereby leading to making a better choice. Accordingly, risk
A System-Theoretic Approach to Risk Analysis By Dro J. Gregorian Sam M. Yoo Bachelor of Science in Mechanical Engineering Master of Science in Engineering Management ... This thesis examines the DoD risk matrix's current use and then leverages STPA to improve the outputs. The authors' research is also widely applicable outside of the DoD.
Title of master's thesis: An empirical evaluation of risk assessment practices from a risk consistency perspective Credits: 30 SP Keywords: Risk assessment Number of pages: 80 Risk analysis Risk definition Risk description Risk metric Consistency Risk timeline + supplemental material/other:82 Stavanger, 06/2020 date/year
1. Introduction. The creation of quantitative tools for decision support is central in operations research and the management sciences. Decision support is often intertwined with a risk analysis or is a part of a decision analysis, with applications ranging from operational risk management in finance (Zhao & Huchzermeier, 2015), to supply chain risk assessment (Fahimnia, Tang, Davarzani ...
A risk assessment determines the likelihood, consequences and tolerances of possible incidents. "Risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk- related consequences." 1 The main purpose of risk assessment is to avoid negative consequences related to risk or to evaluate possible opportunities.
This Doctoral Thesis, A systems thinking approach to risk reduction and mitigation. for improving disaster management, presented by Anshu Shroff, and Submitted to the Faculty of The Harvard T.H. Chan School of Public Health. in Partial Fulfillment of the Requirements for the Degree of Doctor of Public.
effective risk management rather than trying to eliminate risk out of projects. These factors have guided this study to focus on understanding the way risk assessment is performed in international technology projects. It aims to identify the link between risk assessment and project categorization, drawing from the transaction cost economics
Bachelor's thesis Date Month Year 2021 Number of pages Language of publication: English ... The purpose of this thesis was to conduct a study on food safety risk assessment and suggest methods in managing potential risks in the field of risk management for industry stakeholders; notably food suppliers, processors, distributors, and consumers ...
WIND POWER - BACHELOR THESIS IN ENERGY TECHNOLOGY Uppsala University Department of Earth Sciences, Campus Gotland Dimitrios Liapodimitris 11-01-2016. ... quantitative risk analysis, and propose risk response strategies for each of the identified risks. For that purpose, a case-study in S. Euboea region was applied; ...
The study programme in Risk Analysis gives you a unique competence in understanding and relating to risk, including risk assessment, risk perception, risk communication, risk management and risk governance, policy related to risk, and risk science. Key topics related to safety, security and resilience are also covered, as well as topics related ...
In the context of a bachelor or master thesis, the analysis of cyber insurance forms from other countries is likely to the respective local market, e.g., a student at a German University analyzing German cyber insurance policies. ... Biener, Christian, Martin Eling, and Jan Hendrik Wirfs. 2015. "Insurability of Cyber Risk: An Empirical ...
The final product of the thesis is a contingency plan created to fit Traficom's regulation 308489 (Traficom, 2020) and a risk analysis model alongside. The contingency plan will be presented as a separate document found in ap-pendix 3 and the risk analysis model explained in chapter 6.
BACHELOR THESIS TITLE: "Analysis of risk and ... In the field of risk assessment there are differences of opinion regarding the use of qualitative or quantitative risk analysis methods. The qualitative-quantitative factor is the basic property of hazards analyses methods. Most of the analysis methods are
1 TOPICS IN FINANCIAL MARKET RISK MODELLING Zishun Ma A DISSERTATION in Quantitative Finance In partial fulfillment of the Requirements for the Degree of Doctor of ...
Risk on the supply chain consists in every risk that might affect the planned flow of material. (Waters, 2011, p. 48-49). Supply chain risk management involves four basic steps: • risk identification • risk assessment • risk mitigation • risk control This thesis will try to fulfill this lack of consistency between the researches,
A Statistical Analysis of Hurricanes in the Atlantic Basin and Sinkholes in Florida, Joy Marie D'andrea. PDF. Statistical Analysis of a Risk Factor in Finance and Environmental Models for Belize, Sherlene Enriquez-Savery. PDF. Putnam's Inequality and Analytic Content in the Bergman Space, Matthew Fleeman. PDF
bachelor thesis & colloquium - me141501 risk assessment of ship collision and grounding in surabaya west access channel due to the existence of shipwrecks joko sutrisno nrp. 04211441000010 supervisor a.a.b. dinariyana d.p. s.t., mes, ph.d double degree program department of marine enginering faculty of marine technology
This thesis will discuss the subject of legal risk analysis in the healthcare system. The motivation for this thesis will be described in section 1.1. The objective of this thesis will be explained in section 1.2. The methodology of this thesis will be discussed in section 1.3, and finally the structure will be described in section 1.4. 1-1 ...
The topic of the bachelor's or master's thesis can make it easy or difficult to write the thesis. A good choice is a topic with as few risks as possible. The following tips will help you avoid risks when choosing a topic right from the start. 1. Bachelor's or master's thesis topics with few suitable sources are risky.
Title of the thesis: Are women more risk-averse than men? A meta-analysis OVERALL ASSESSMENT (provided in English, Czech, or Slovak): Please provide a short summary of the thesis, your assessment of each of the four key categories, and an overall evaluation and suggested questions for the discussion. The minimum length of the report is 300 words.
Bachelor's Thesis Sijia Zhu Safety and security pre-planning for out-bounding student in Laurea University of applied science. Year 2018 Pages 31 This thesis was done in cooperation with Laurea University of Applied Science international study department. The main purpose of the thesis was to develop a risk-based pre-departure
Overview. The cybersecurity risk assessment prediction initiative, backed by Technology Helps, has introduced a cutting-edge AI-powered web application. This solution seamlessly integrates staff training evaluations, phishing risk analyses, vulnerability assessments, and security controls and audit scores to generate weighted scores and ...
Master's Thesis in Risk Analysis (RISMAS) The master thesis is an independent project in which the student shall apply the knowledge acquired during the studies to solve a given assignment. It is through this assignment that that the student shows his or her abilities and qualities as a master's degree holder. The assignment is normally carried ...
Funds Compared: Performance, Expense Ratio, and Dividend Yield. KBE has seen a mediocre 10-year average annual return of 5.67% with a 10-year total price return of 43.8%. By comparison, KBWB ...