Networking | Cloud | DevOps | IaC

IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
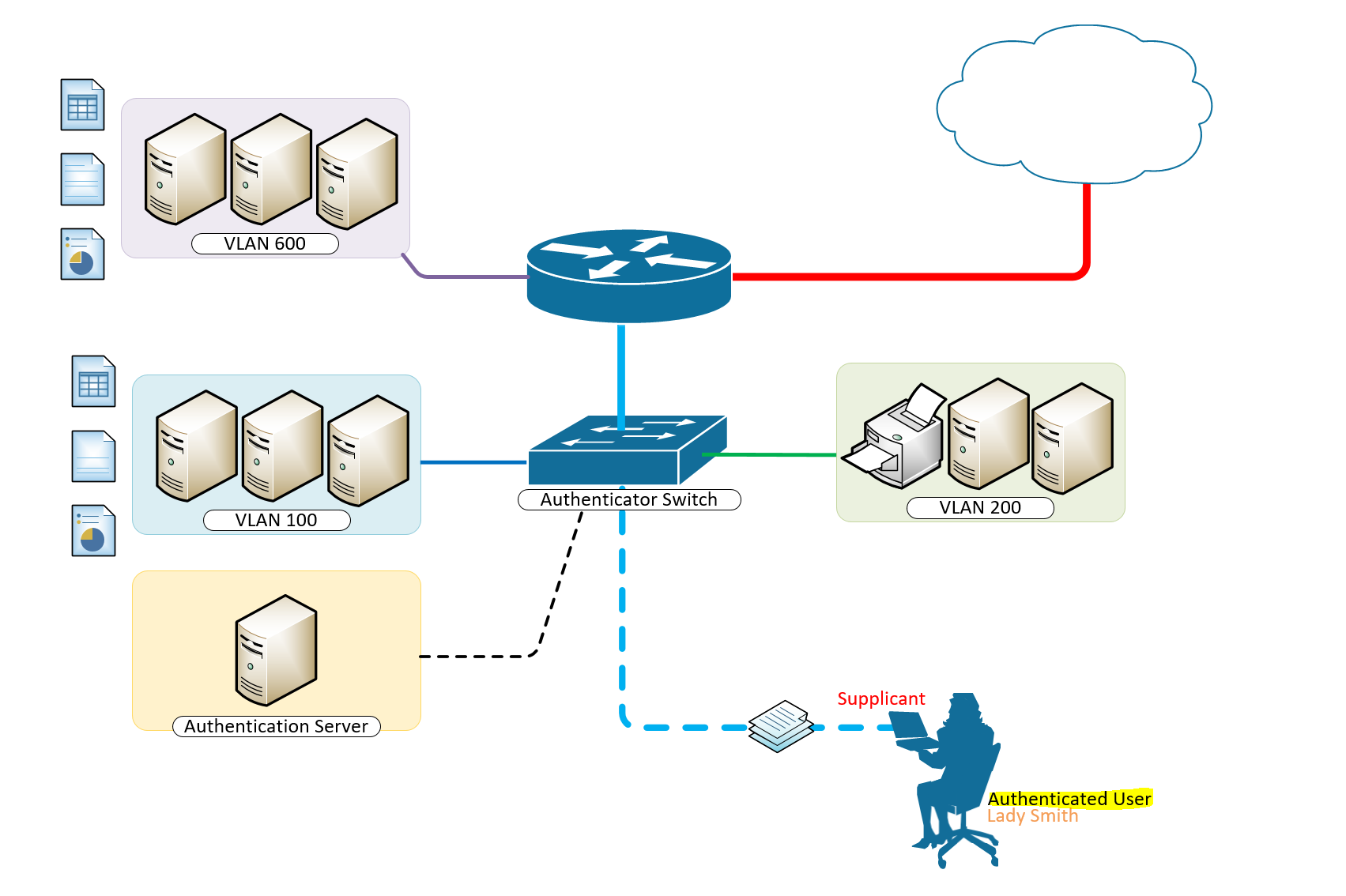
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802

For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server

COMMENTS
This document describes the concept of dynamic VLAN assignment and how to configure the Catalyst 9800 wireless LAN controller (WLC) and Cisco Identity Service Engine …
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server. Verify Port-Access with the following user groups – VLAN 100 and VLAN 200. …
Has anyone configured NPS and Cisco WLC to assign dynamic vlans to users? It appears that NPS supports the attributes but I recently switched my authentication to …
I have AD and Microsoft NPS 2016 configured (correctly i think) as authentication is successful (i.e. the Cisco shows a successful auth and the Windows 10 machine is waiting for …
This document introduces the concept of dynamic VLAN assignment. The document describes how to configure the wireless LAN controller (WLC) and a RADIUS server to assign wireless LAN (WLAN) …
This document describes the concept of dynamic VLAN assignment and how to configure the Catalyst 9800 wireless LAN controller (WLC) and Cisco Identity Service Engine (ISE) to …
Looking for ideas/opinions on how to dynamically assign VLANS to access ports. End goal would be to detect an interface going up, discover the Mac OUI and dynamically assign the …
In lieu of CoA, MS switches can still dynamically assign a VLAN to a device by assigned the VLAN passed in the Tunnel-Pvt-Group-ID attribute. It may be necessary to …